Digital Steganographic Schemes Based On Image Vector Quantization |
|
CONTENTS
12.2 Background for VQ-Based Image Steganographic Schemes
12.2.2 Search-Order-Coding Algorithm
12.2.3 Data Embedding by lsb Substitution
12.2.4 VQ-Based Image Steganographic Schemes
12.3 Image Steganographic Scheme Based on VQ Codebook Modification
12.3.1 Image Steganographic Scheme by VQ and LSB Modification
12.4 Image Steganographic Scheme in VQ-Compressed Domain of Image
12.4.1 Image Steganographic Scheme in VQ-Compressed Domain
12.5 Visually Imperceptible Image Steganographic Scheme Based on VQ
12.5.1 Visually Imperceptible Image Steganographic Scheme Based ON VQ
Along with the progress relating to computer hardware and software, the Internet has become the most popular channel for transmitting various forms of digital media. Since the environment of the Internet is open, the protection of digital data transmitted on the network has become an important research topic in recent years. Information hiding is a common technique to achieve the purpose of data protection. It involves embedding significant data into various forms of digital media such as text, audio, image, and video secretly. Information hiding can be further divided into two main branches: steganography and digital watermarking.
The popularity of the Internet and the increasing bandwidth of communications provide great convenience to the transmission of multimedia data via networks. However, data transmissions over the Internet still have to face some security problems, such as illegal access, data security, and copyright protection. To safely transmit data through the Internet, some mechanisms have been proposed to protect important data from illegal interception. One of the most important mechanisms is data encryption (Bourbakis and Alexopoulos, 1992; Rhee, 1994; Jan and Tseng, 1996; Highland, 1997), which refers to the process of encoding secret data in such a way that only the receiver with the right key can successfully decode it. However, as an encrypted data usually flags the importance of the data, it may also attract eavesdroppers’ attention. Another approach to increase the security of transmitted data, especially for digital images, is by hiding the secret data in images (Bender et al., 1996; Marvel and Retter, 1998; Petitcolas et al., 1999). The main purpose of image steganography is to embed a piece of secret information into a noncritical host image to distract opponents’ attention (Kohn, 1996; Stallings, 1999), whereas the major goal of image watermarking is to protect the copyright of the marked image itself.
Digital steganography is a feasible means for covert communications. It has been implemented successfully for many forms of digital content, especially for digital image. In this chapter, we introduce different types of image steganographic schemes based on vector quantization (VQ). The concept of VQ will be introduced first as the background of the steganographic schemes discussed in this chapter. The main components in the VQ compression system, such as the input image to be compressed, the VQ codebook, the VQ indices of input image, and the reconstructed image, can be used for applying digital steganography. Based on the components of VQ, various steganographic schemes have been designed and proposed in the literature.
12.2 BACKGROUND FOR VQ-BASED IMAGE STEGANOGRAPHIC SCHEMES
We first describe the detailed processes of VQ for image compression in 12.2.1. Then, an efficient lossless coding scheme that further compresses the VQ indexes of image based on the search order of index is reviewed in Section 12.2.2. Furthermore, the simplest data-embedding technique (the greedy least-significant- bit substitution method) is presented in Section 12.2.3. Finally, some of the VQ-based image steganographic schemes are briefly reviewed in Section 12.2.4.
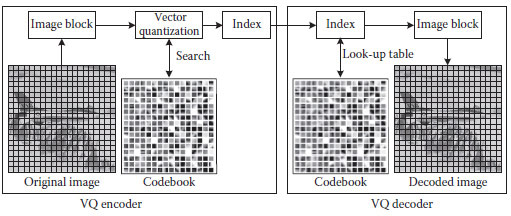
Image compression has become very essential for multimedia storage and transmission applications. Vector quantization technique has been extensively and successfully applied for image compression. One feature of VQ is that high compression ratios are possible with relatively small block sizes. The other attractiveness of VQ as source coding scheme derives from its optimality and the simplicity of the hardware implementation of the decoder. In a VQ coding system, the image to be coded is first divided into nonoverlapping blocks. Each image block is individually mapped to the closest codeword in the codebook based upon the minimum distortion rule. Compression is achieved by replacing these codewords with the corresponding indexes in transmission or storage applications. Reconstruction of image is then simply performed by table lookup using the index as an entry to the codebook.
FIGURE 12.1 The encoding and decoding modules of VQ for image compression.
A VQ coding system can be simply defined as a mapping from a k-dimensional Euclidean space Rk to a finite subset of space Rk. The finite subset C = {yi: yi∈ Rk and i = 0, 1, … Nc – 1} is called a codebook, where Nc is the size of this codebook. Each yi = (yi, 0, yi, 1, …, yi, k-1) in the codebook C is called a codeword or a codevector and is composed of k scalar elements. These codewords are generally generated, based on the Linde-Buzo-Gray (LBG) iterative clustering algorithm (Linde et al., 1980), from the training set. The compression performance is significantly dependent upon these codewords. An ordinary VQ system, as shown in Figure 12.1, has two parts: the encoder and the decoder, each of which is equipped with the same codebook. In the encoder, the closest codeword yt to the input block x can be found by searching the codebook, and the index i will be sent to the decoder. Consequently, in the decoder, the codeword yi can be found via the received index i, and the block x will be replaced by codeword yi. In this case, a quantization error is unavoidable. Therefore, VQ belongs to lossy compression scheme. The distortion between the input block x and its quantized block y can be obtained by the squared Euclidean distance measure criterion given as Equation 12.1. Moreover, the overall distortion between the original image and the reconstructed image can be obtained by summing up all the distortion caused by quantizing image blocks.
(12.1) |
12.2.2 SEARCH-ORDER-CODING ALGORITHM
In a traditional VQ system for images, each block of image is quantized independently and its corresponding index is sent to the decoder directly. To further improve the performance of compression, variable-length coding (VLC) techniques such as Huffman coding (Huffman, 1952) or arithmetic coding (Witten et al., 1987) can be applied to the VQ indices of image. However, this will introduce extra hardware cost in image compression. Therefore, Hsieh and Tsai (1996) proposed a lossless compression scheme for VQ index with search-order coding (SOC). The SOC algorithm exploits the interblock correlation in the index domain rather than in the pixel domain. The idea behind the SOC algorithm is that it searches the previous indices on the basis of a predefined search order and sends the corresponding search result to decoder to notify if any previous index is matched with the current index. Hsieh and Tsai pointed out that because the VQ index is a scalar, not a highdimensional vector, the SOC algorithm is much simpler than conventional memory VQ and, therefore, it may achieve better compression performance. The SOC algorithm can be summarized as follows:
Step 1. Determine the number of bits n for encoding the search order.
Step 2. Input a VQ index and use it as a search center.
Step 3. Try to find a search point (SP) with the same VQ index value as the search center in the predefined search path on the VQ index table until the currently searched index is not a repetition SP and cannot be encoded with any of the SOC codes, (0)2~ (2n – 1)2.
Step 4. If a matched SP is found, the currently searched index is encoded with a 1-bit indicator followed by the corresponding SOC code; otherwise, it is encoded with the indicator followed by its original index value (OIV).
Step 5. If there is another index to be processed, go to Step 2; otherwise, output the compressed index table of image to decoder.
12.2.3 DATA EMBEDDING BY LSB SUBSTITUTION
Many techniques concerning embedding significant data into the least significant bits (LSB) of image pixels have been proposed in earlier literatures. Wang et al. (2001) proposed an optimal LSB substitution method for embedding secret data into the selected LSBs of pixels in the cover image. The proof for the effectiveness of Wang et al.’s scheme in the worst-case condition is also described in Wang et al. (2001). In addition, a genetic algorithm that greatly reduces the huge computational time for finding the optimal selection of LSBs is developed as well. In order to find the optimal LSB substitution for pixels within an image, Chang et al. (2003) proposed another more efficient approach in which the dynamic programming strategy was applied. However, the most efficient and easiest substitution method for image data embedding in spatial domain is the greedy LSB substitution technique.
The general processes of data embedding based on the greedy LSB substitution method are given as follows. Let M be the binary representation of the secret data, and X be the image data where M will be embedded. Assume the length of M is l; therefore, M can be represented as Equation 12.2. Let x be an image with resolution u × v pixels and d bits per pixel. X can be represented as Equation 12.3.
(12.2) |
(12.3) |
Assume that M is to be embedded within the r rightmost LSBs of xij in X. Consequently, the following formula must be satisfied:
(12.4) |
The data-embedding procedure of the greedy LSB substitution method is processed by first replacing the first LSBs of all Xij in X with the first u × v bits of M (i.e., m0 to mu×v–1). Second, the second LSBs of all Xij in X are replaced with the next u × v bits of M(i.e., mu×vto m2×u×v–1). This procedure continues until all the binary bits of M are embedded into X.
12.2.4 VQ-BASED IMAGE STEGANOGRAPHIC SCHEMES
The purpose of image steganography is different from traditional cryptography (Davis, 1978; Rivest et al., 1978) and watermarking techniques (Cox et al., 1997; Barni et al., 2001). Cryptography encrypts messages into meaningless data while watermarking is used to protect the copyright. Image steganography covers the secret information with the host media as camouflage and is considered as an extension of traditional cryptography. Image steganography is mainly used for covert communication. It attempts to conceal the existence of secret data, whereas digital watermarking techniques try to maintain the existence of embedded data for future usage. Nevertheless, there is still some similarity between them. Both the embedded data may be images with certain purpose. Speaking of the requirements, digital watermarking techniques usually concentrate on the robustness, while image steganography may lay greater emphasis on the available capacity for hiding. In the prior researches, raw images without any compression are considered as cover media (Wu and Tsai, 2000). To solve the problems of inefficient capacity, Chen et al. (1998) proposed a solution that secret images should be compressed by VQ (Linde et al., 1980) and then encrypted before the embedding process, which is called virtual image cryptosystem. Hu (2003) proposed a revised algorithm of virtual image cryptosystem. Both the above-mentioned schemes have been simulated and proven that multiple images can be hidden concurrently while the quality of extracted images at the receiver is acceptable.
The algorithm of Hu’s scheme can be summarized as follows. The goal of Hu’s scheme is to hide multiple secret images into another meaningful cover image of the same size. To compress the secret images and reduce the volume of hidden information, secret images are first encoded using VQ. In this scheme, each pixel value of the cover image was split into two parts. The significant one is used for VQ codebook generation, and the insignificant one is used for information hiding based on greedy LSB substitution. Namely, the VQ codebook for secret image encoding is generated from the low-, middle-, and middle-high-frequency parts of the cover image. After the procedure of image encoding, the VQ indexes of secret images are encrypted and embedded into the high-frequency part of the cover image by greedy LSB modification. In the receiver, the same codebook can be generated from the stego-image since the low, middle, and middle-high-frequency parts of the received cover image is totally the same as the ones in the transmitter. And the VQ indexes of secret images can be directly extracted from the LSBs of the received cover image. Consequently, several secret images can be embedded into a meaningful cover image by Hu’s scheme. Hu’s scheme makes a good improvement when considering the proportion of the hiding capacity (the total file size of secret images) to the file size of the cover medium.
Image steganography can be implemented on the compressed domain of images as well. Under this circumstance, the hiding capacity for secret information is more restricted and the visual quality of cover images may be decreased as compared with those of the techniques applied on the noncompressed domain of images. Moreover, when secret information is hidden in the compressed domain of the host image, the bit rate of the compressed cover image becomes another major consideration. It should not cause apparent increase of the bit rate of compressed cover images after the secret information are hidden or embedded. In the following paragraphs, two recently proposed image steganography schemes that implemented on the compressed domain of images are briefly reviewed.
Chang et al. (2004) proposed an image steganographic scheme in which a reasonable amount of binary data can be embedded into the compressed codes of the host image. They pointed out that as compared with various image steganographic schemes applied on the spatial domain of image, VQ-based steganographic schemes have not been paid much attention. Therefore, they proposed an image steganographic scheme based on the SOC (Hsieh and Tsai, 1996) compression technique of VQ indices. In this scheme, a cover image is first compressed based on traditional VQ and an index table for the cover image is generated. After that, the SOC algorithm is applied on the index table and a more compact index table is obtained. The compact index table consists of two kinds of compression codes: the SOC and the OIV codes. Therefore, additional one bit has to be added in front of each SOC code and OIV code for distinguishing purpose. The receiver can distinguish these two different codes according to the one-bit indicator. Chang et al. found that based on this characteristic, secret data can be embedded into the compression codes without inducing additional coding distortion. Specifically, the receiver determines that each bit of secret data is “0” or “1” based on whether the received compression code is SOC or OIV. In the hiding process of Chang et al.’s scheme, there are four categories taken into consideration. Two of the four categories induce more additional bits for the compression codes that have to be translated according to the bits of secret data. Chang et al.’s scheme is the first one that technically and directly embeds secret information into the VQ-compressed codes of the host image. In addition, they also announced that a good and acceptable compression ratio of the image after the hiding procedure of secret information has been confirmed by the experiments. The details of the description are available in Chang et al. (2004).
Du and Hsu (2003) proposed an adaptive data-hiding method to embed secret data into VQ-compressed images. This method adaptively varies the embedding process according to the amount of hidden data. More specifically, the secret data were embedded into the VQ-compressed images by first rearranging all the codewords in the codebook into exclusive groups based on codeword’s similarity. And then, according to the secret bits to be hidden, a codeword was chosen from the group that contains the nearest codeword of the currently encoded block to replace the nearest one in the VQ encoding procedure. Accordingly, Du and Hsu’s method achieved good improvements both on the hiding capacity and on the visual quality of cover images as compared with ordinary fixed embedding methods such as the mean gray-level embedding (MGLE) method and the pair-wise nearest-neighbor embedding (PNNE) method. More details on this method can be found in Du and Hsu (2003).
12.3 IMAGE STEGANOGRAPHIC SCHEME BASED ON VQ CODEBOOK MODIFICATION
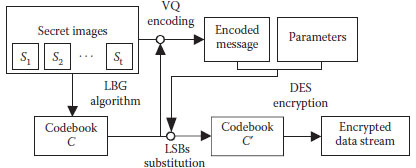
Secret image transmission or communication has attracted much attention in these years, and many researches about image steganography have been proposed in the literature (Du and Hsu, 2003; Hu, 2003; Thien and Lin, 2003; Chan and Cheng, 2004; Chang et al., 2004). Image steganography involves embedding a large amount of image data into another cover medium with minimal perceptible degradation. However, the embedding capacity and the distortion of the cover medium are a tradeoff since more embedded images always result in more degradation of the cover medium. Besides, the successful delivery for a large set of secret images becomes a challenge when the bandwidth of the communication channel is narrow. An image steganographic scheme suitable for a narrow communication channel is introduced in this section. A set of secret images can be simultaneously and efficiently delivered to the receiver via a small and meaningless data stream. To reduce the volume of secret images to be transmitted, a codebook is generated and these secret images are encoded into binary indexes based on the VQ technique. The compressed message of secret images is then embedded into this VQ codebook by an adaptive LSB modification technique. For the purpose of security, the slightly modified codebook is further encrypted into a meaningless data stream by the DES cryptosystem (National Bureau of Standards, 1997). Simulation results show that this image steganographic scheme provides an impressive improvement both in the visual quality of the extracted secret images at the receiver and in the hiding capacity of the cover medium.
In this section, a novel image steganographic scheme that focuses both on the hiding capacity of the cover medium and on the quality of extracted secret images at the receiver is introduced. To design a high-capacity and high-quality image steganographic scheme, we incorporate the VQ technique into our scheme to compact the volume of secret images. Moreover, to guarantee the visual quality of extracted secret images at the receiver, the VQ codebook utilized in the encoding procedure is adopted as the cover medium. This scheme provides a new approach to secretly transmit a set of images, especially for limited-bandwidth communication channel.
12.3.1 IMAGE STEGANOGRAPHIC SCHEME BY VQ AND LSB MODIFICATION
In this image steganographic scheme, the input of the transmitter is a set of secret images, and the output of the transmitter is a series of encrypted data stream. The goal of this scheme is to transmit a set of secret images via an encrypted meaningless data stream. The size of this encrypted data stream is relatively small as compared with the file size of all secret images.
Assume that there are t secret images to be transmitted and these images are gray- level images of w × h pixels. To compress the secret images with VQ, a codebook should be generated before the encoding procedure. Let the size of VQ codebook be Nc and the codeword be composed of m × n elements. These Nc codewords of codebook are generated based on the iterative LBG algorithm using the secret images as the training set. After the codebook C is generated, each of these secret images is partitioned into blocks of m × n pixels. Each image block is then encoded into a binary index of codeword. The compressed message of all secret images is obtained by merging these binary indexes. Therefore, the overall size l of the compressed message for secret images can be defined by
(12.5) |
In order to transmit a set of secret images via a small and encrypted data stream, we propose a novel idea to embed the compressed message of secret images into the codebook associated with these images. In addition, the parameters used in this scheme, t, w, h, m, n, and Nc, have to be preserved well for future use at the receiver. These parameters are also embedded into the codebook. The embedding procedure of this image steganographic scheme at the transmitter is accomplished based on the following steps:
Step 1. Sort the codewords of codebook into ascending order based on the referred frequency in the procedure of secret images’ encoding.
Step 2. Select the first p + q codewords of the sorted codebook based on the size of the compressed message for secret images. The first p codewords are taken for embedding the information of related parameters, while the rest q codewords are used for embedding the compressed message of secret images.
Step 3. Embed the parameters and the compressed message of secret images into the selected codewords by directly modifying the LSBs of codeword elements.
A modified codebook C′ is obtained after all the compressed message of secret images and the information of related parameters are embedded into the original codebook C. For security, the modified codebook C′ is then encrypted by the DES cryptosystem (National Bureau of Standards, 1997) to create an encrypted message. Finally, the encrypted data stream covering a set of secret images is generated. Figure 12.2 illustrates the flowchart for transmitting a set of secret images by this scheme. Note that only the parameter p and the arguments used in the procedure of DES encryption have to be sent to the receiver via another safe channel.
The procedure of secret images’ extraction is quite simple at the receiver. To reconstruct the secret images, the received data stream is first decrypted based on the DES decryption procedure. After the decryption process, the modified codebook C’ is directly obtained. Therefore, all the parameters, including the number of secret images t, the image size w and h, the codeword size m and n, and the codebook size Nc, can be easily extracted from the first p codewords of C’ According to the extracted parameters, the compressed message of secret images can be directly obtained from the next q codewords of C′ The compressed message is then decoded by performing table look-up operation on the modified codebook C′. Finally, all the secret images are reconstructed.
FIGURE 12.2 Flowcharts of the image steganographic scheme at the transmitter.
The image steganographic scheme introduced in this section has been performed on a set of five images (Lena, Pepper, Boats, Goldhill, and Toys) and a set of 10 images (Lena, Airplane, Boats, Girl, Goldhill, Lenna, Pepper, Tiffany, Toys, and Zelda), respectively. These test images are all with size 512 × 512 pixels and 256 levels per pixel. In order to apply the VQ compression on the test images, each image was divided into image blocks with 8 × 8 pixels. In addition, the size of the VQ codebook is 4096 and each codeword consists of 8 × 8 elements. Consequently, there are 262, 144 (4096 × 8 × 8) elements in this codebook and the length of each codeword inde× is 12 bits. Therefore, the compressed message for each secret image is 49, 152 (12 × (512 × 512)/(8 × 8)) bits.
In the first experiment, a set of five secret images has to be simultaneously embedded into the cover medium. Therefore, 3840 codewords were selected from the VQ codebook to embed the compressed message of five secret images. The least significant bits of the codeword elements in each selected codeword were directly replaced by the compressed message of secret images. Table 12.1 lists the quality of extracted secret images at the receiver, together with the original quality of VQ-compressed images at the transmitter. The extracted secret images at the receiver are shown in Figure 12.3. Note that the peak signal-to-noise ratio (PSNR) criterion is adopted to evaluate the image quality in our experiments. The PSNR criterion is defined as Digital Steganographic Schemes Based on Image Vector Quantization
TABLE 12.1
Quality (in dB) of Secret Images Before and After Secret Message Embedding

FIGURE 12.3 Five secret images simultaneously extracted at the receiver. (a) Lena, 32.513 dB (b) Pepper, 33.001 dB (c) Boats, 31.506 dB (d) Goldhill, 30.767 dB, and (e) Toys 34.136 dB.
(12.6) |
where Wi and Hi are the width and height of the cover image. Imn is the original pixel value of the coordinate (m, n) and is the altered pixel value of the coordinate (m, n). Emaxis the largest energy of the image pixels (e.g., Emax = 255 for 256 grayscale images). As shown in Table 12.1 and Figure 12.3, the experimental result shows that the degradation of image quality before and after secret image transmission is very small. It also reveals that the visual quality of these five secret images at the receiver is quite good.
In the second experiment, 10 secret images were simultaneously embedded into the cover medium and transmitted to the receiver. To embed the compressed message of 10 secret images, the first LSBs of all codeword elements and the second LSBs of some codeword elements in the codebook have to be modified. For evaluation by the human visual system, Figure 12.4 illustrates these 10 secret images simultaneously extracted at the receiver. The PSNR values of the secret images are also provided. Note that the final cover medium of this scheme is a meaningless data stream as shown in Figure 12.5
FIGURE 12.4 Ten secret images simultaneously extracted at the receiver. (a) Lena, 31.24 dB, (b) Airplane, 30.77 dB, (c) Boats, 29.63 dB, (d) Girl, 31.28 dB, (e) Goldhill, 29.89 dB, (f) Lenna, 29.65 dB, (g) Pepper, 31.72 dB, (h) Tiffany, 32.47 dB, (i) Toys, 32.24 dB, and (j) Zelda, 32.71 dB.
To verify the performance of the image steganographic scheme, the embedding capacity (the maximum number of secret images) with respect to the size of data stream (the file size of the cover medium) is listed in Table 12.2. Here, each secret image file is of size 256 kB. This table also illustrates that more embedding capacity can be provided by enlarging the codebook size or modifying more LSBs within a single codeword element in this scheme. However, to provide better visual quality for secret images at the receiver, it is suggested that the number of modified LSBs within each codeword element should not exceed three. Under these circumstances, in terms of mean-squared error (MSE), the degradation of image quality between the VQ-compressed secret image at the transmitter and the extracted secret image at the receiver is bounded by (2r- 1)2. Here, r is the number of modified LSBs within each codeword element.
FIGURE 12.5 The final encrypted cover medium of this scheme.
TABLE 12.2
Embedding Capacity (Maximum Number of Secret Images)
Modified LSBs |
||||
Codebook |
Size Size of Data Stream |
1 |
2 |
3 |
2048 |
128 kB |
2 |
5 |
8 |
4096 |
256 kB |
5 |
10 |
16 |
8192 |
512 kB |
9 |
19 |
29 |
A novel image steganographic scheme capable of delivering a set of secret images to the receiver at the same time has been introduced in this section. The proposed scheme provides impressive improvement both in the visual quality of extracted secret images and in the hiding capacity of the cover medium. The achievement of this scheme is based on the following reasons: (1) The secret images are included in the training set in the codebook generation procedure. (2) The volume of secret images to be delivered is greatly reduced by applying the VQ technique on these images. (3) The cover medium is composed of all the VQ codewords associated with these secret images. (4) The compressed message of secret images is embedded into the cover medium based on an adaptive greedy LSBs substitution technique. In addition, the modified cover medium is further encrypted into a meaningless data stream by the DES cryptosystem for more security. Moreover, the file size of the encrypted data stream that has to be transmitted to the receiver is quite small. That is, the image steganographic scheme introduced in this section is feasible for narrow communication channel.
12.4 IMAGE STEGANOGRAPHIC SCHEME IN VQ-COMPRESSED DOMAIN OF IMAGE
The VQ-based steganographic technique has not received much attention compared to various spatial domain-based steganographic techniques previously developed for digital image. In this section, we would like to introduce a new image steganographic scheme which was applied on the VQ-compressed domain of the host image. Image steganography involves embedding a large amount of secret data into a cover image with minimal perceptible degradation of the image quality. However, there is always a trade-off between the hiding capacity for secret data and the distortion of the cover image since more hidden data always result in more degradation of visual quality in the cover image. Moreover, when the image steganographic technique is implemented on compressed images, the hiding capacity and the visual quality of the cover images are even more restricted. Furthermore, the bit rate of the compressed cover image becomes another major consideration in image steganographic applications. Hiding secret data should not cause an apparent increase in the bit rate of the compressed cover images.
The image steganographic scheme introduced in this section focuses on the hiding capacity of the host image in the VQ-compressed domain. The major goal of this scheme is to embed secret data into the VQ-compressed codes of the host image such that the interceptors will not notice the existence of secret information. In addition, this scheme attempts to keep an acceptable bit rate for the compressed cover image after a large amount of secret data are embedded into the host image. To design a low-bit-rate image steganographic scheme, we incorporate the VQ technique (Linde et al., 1980) into our scheme to compress the host image. Moreover, to provide more hiding capacity for secret data and keep an acceptable bit rate for the compressed host images, the SOC algorithm (Hsieh and Tsai, 1996) is implemented to compress the VQ indices of the host image. During the process of data hiding, this scheme adaptively embeds secret data into the compressed VQ indices of image according to the amount of hidden data. To prevent the interceptors from being aware of the existence of secret data, the data is embedded into the compression codes of the host image directly. The embedding process induces no extra coding distortion and adjusts the bit rate according to the size of secret data for the compressed host image. The receiver can efficiently receive both the secret data and the compressed image with an acceptable bit rate at the same time.
12.4.1 IMAGE STEGANOGRAPHIC SCHEME IN VQ-COMPRESSED DOMAIN
The goal of this scheme is to transmit a set of binary information secretly via a VQ-compressed host image at an acceptable bit rate. Assume that the host image × is a gray-level image with w × h piels. To compress the host image with VQ, a codebook should be generated before image compression. Let the size of VQ codebook be Nc and a codeword be composed of m × n elements. These Nc codewords of codebook are generated based on the iterative LBG algorithm (Linde et al., 1980). After a codebook is generated, X is partitioned into nonoverlapping blocks of m × n piels. Each image block of X is then encoded into an index of codeword. Consequently, an index table T with elements is constructed after all the image blocks of X are encoded by VQ. T is then ready to be transmitted to the receiver for the purpose of image compression. The bit rate BRVQ of ordinary VQ compression can be obtained by
(12.7) |
In order to simultaneously hide secret information into the index table T and reduce the bit rate of the VQ-compressed host image, we further incorporate the SOC algorithm into this image steganographic scheme. The SOC algorithm takes advantages of the high correlation among adjacent indices in T to encode the traditional VQ indices with fewer bits. Here, the high correlation means that there may be many image blocks of X encoded with the same VQ indices in the neighborhood. The SOC algorithm encodes each index of T one by one in raster scan order. It tries to find the same index around the current processed index in a predefined search path. If the same index is found within the search path, the current processed index will be denoted as an SOC code and replaced with a d-bits code (d is much smaller than log2Nc. Otherwise, the current processed index will remain unchanged and be denoted as an OIV code. Note that a one-bit indicator is needed for each processed index in T to distinguish SOC code from OIV code. The performance of SOC algorithm depends on the amount of SOC codes it can determine in the index table. Let the amount of SOC codes in T be s; therefore, the bit rate BRvqsoc of the compressed host image after applying the SOC algorithm can be computed by
(12.8) |
To hide binary information secretly in the VQ-compressed domain of the host image, we introduce a novel idea to hide information while applying the SOC algorithm on T. In this scheme, an unfixed or fixed amount of secret bits can be hidden into each SOC code in T. In order to hide a randomly unfixed amount of secret bits into an SOC code, a seed key k and an integer i are needed to randomly generate the amount ranging from 1 to i. However, if a fixed amount p of secret bits is hidden in each SOC code, the bit rate BRvqsocdh of the compressed host image after information embedding can be calculated by
(12.9) |
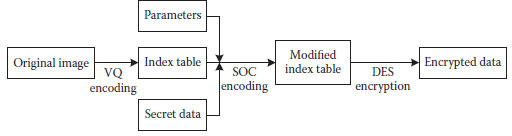
The following steps summarize the embedding procedure of this image steganographic scheme:
Step 1. Encode the host image X into its corresponding index table T by applying the VQ algorithm.
Step 2. Apply the SOC algorithm on the index table T. If the current processed index is encoded as an SOC code, then extract a number of bits from the secret information and embed these secret bits into the SOC code. Otherwise, the current processed index is encoded as an OIV code and it remains unchanged to preserve an acceptable bit rate for the compressed host image.
Step 3. Encrypt and transmit the modified index table and the associated parameters to the receiver.
FIGURE 12.6 Flowchart of the data-embedding procedure at the transmitter.
A modified index table T′ for the compressed host image X is obtained after the secret information has been embedded. To transmit the index table T′ to the receiver, all the SOC codes and OIV codes in T′ are merged into a binary bit stream based on the raster scan order. For more security, the bit stream can be further encrypted by the DES cryptosystem (National Bureau of Standards, 1997) to create an encrypted message. Finally, the encrypted data stream covering the secret information is generated. Note that the associated parameter set used in this scheme, d, k, and i for variable-length embedding or d and p for fixed-length embedding, has to be preserved well for future use at the receiver. These parameters can be embedded into T′ or transmitted to the receiver via a secure channel. Figure 12.6 illustrates the flowchart of the data-embedding procedure at the transmitter.
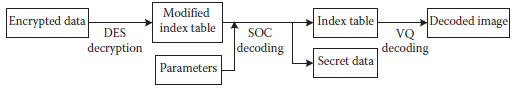
The procedure of secret information extraction is quite simple at the receiver. To reconstruct the compressed codes of the host image, the received data stream is first decrypted based on the DES decryption procedure. After the decryption process, the modified index table T of the compressed host image X is directly obtained. The parameters used in the information-embedding procedure can be extracted from T′ or obtained via a predefined secure channel. Moreover, the SOC codes in T′ can be easily specified with these parameters and the one-bit indicator that distinguishes the SOC code from OIV code. Finally, all the secret bits are extracted and the secret information is then reconstructed. Figure 12.7 illustrates the flowchart of the data extraction procedure at the receiver.
In the experiments, the image steganographic scheme introduced in this section has been performed on six host images (Airplane, Boat, Girl, Lena, Peppers, and Toys) with size 256 × 256 pixels and 256 levels per pixel, respectively. To simulate various types of secret information, the secret data used in this experiment are composed of randomly generated bit streams. The VQ codebook utilized in the simulation is generated by using the LBG algorithm and five standard images (Airplane, Boat, Lena, Sailboat, and Toys) with size 512 × 512 pixels and 256 gray levels. In addition, the codeword size is 4 × 4 pixels and the codebook size is 256. Consequently, each host image is partitioned into 4096 ((256 × 256)/(4 × 4)) image blocks with 4 × 4 pixels. And the bit rate of the primitive VQ-compressed image is 0.5 bits per pixel. In order to hide secret information while keeping an acceptable bit rate for the compressed host images, the SOC algorithm is applied on the VQ indices of the host image and the parameter d for the predefined search path is set to be 2 in the eperiment.
FIGURE 12.7 Flowchart of the data extraction procedure at the receiver.
To verify the performance of the image steganographic scheme introduced here, Table 12.3 lists the bit rates for embedding different-sized secret information into the host images. As shown in Table 12.3, the secret information with size 4–16 K bits can be embedded into the compression codes of the host image by the introduced image steganographic scheme. In fact, there is no limitation on the hiding capacity of this scheme. The reason is that the secret bits are directly embedded into the compression codes of the host image. Nevertheless, this image steganographic scheme decreases the compression rate of host image after secret information embedding. As for the bit rate of the compressed host image, the increase of the bit rate is steady with that of information size. In addition, the increase in the bit rate of the compressed host image is independent of the property of the binary information.
Recently, Shie et al. (2006) proposed another VQ-based data-hiding technique that takes advantages of the prediction property of the side-match VQ (SMVQ) state codebook. The major idea of this technique is to hide secret data in VQ-compressed codes of cover images based on a modified SMVQ-encoding process, taking advantage of the concept of prediction. To compare the image steganographic scheme introduced in this section with Shie et al.)s scheme, the benchmark images “Lena” and “F16” are utilized as cover images. The VQ-codebook utilized in this experiment is generated from the cover images themselves. In addition, the codeword size is 4 × 4 pi×els and the codebook size is 256. Consequently, each cover image is partitioned into 16, 384 ((512 × 512)/(4 × 4)) image blocks with 4 × 4 pixels. Note that this experimental environment is almost the same as that of Shie et al.’s scheme, except for the codebook size. The bit rate of the original VQ-compressed image is 0.5 bpp. In addition, the quality of the cover images is evaluated by the PSNR criterion defined in Equation 12.6.
TABLE 12.3
Bit Rates of the Compressed Cover Images Hidden with Different Amounts of Secret Data
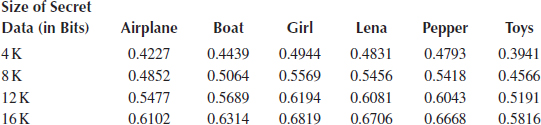
TABLE 12.4
Performance Comparison (in PSNR) of the Introduced Scheme and Shie et al.’s Scheme
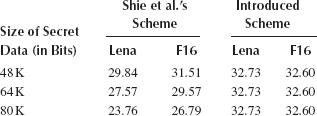
To compare the performance of the introduced scheme with Shie et al.’s scheme, we hide the same amounts of secret data in the compressed cover images. Before data hiding, the PSNR values of the compressed cover images, “Lena” and “F16, ” are 32.73 and 32.60 dB, respectively. For objective evaluation, Table 12.4 lists the performance comparison (in PSNR) of the introduced scheme and Shie et al.’s scheme, with the amounts of hidden data ranging from 48 to 80 kbit. As shown in Table 12.4, it demonstrates that the introduced scheme outperforms Shie et al.’s scheme when the same amounts of data are hidden in the cover images. For subjective evaluation by the human visual system, Figures 12.8 and 12.9 illustrate the original uncompressed cover images, the compressed cover images with different amounts of secret data hidden by the scheme of Shie et al. (2006) and the compressed cover images with secret data hidden by the scheme introduced in this section, respectively, for the test images “Lena” and “F16.” Note that the introduced scheme induces no extra coding distortion in the compressed cover images. The experimental results also demonstrate that the visual quality of the cover images is quite acceptable after hiding large amounts of secret data with the introduced scheme. For comparing the compression performance of the introduced scheme and Shie et al.’s scheme, the bit rates with respect to the amount of hidden data are listed in Table 12.5. It reveals that the compression performance of the introduced scheme is not so good as Shie et al.’s scheme. However, the increase in bit rate is acceptable under the conditions that the visual quality is quite good even when the hiding capacity is large for the compressed cover images.
As illustrated in Figures 12.8 and 12.9, the introduced scheme outperforms Shie et al.’s scheme in terms of the visual quality of the compressed cover image. The introduced scheme outperforms Shie et al.’s scheme for the following reasons. In Shie et al.’s scheme, the secret data are hidden in the compressed cover image based on a modified encoding procedure of SMVQ. In traditional SMVQ, a small state codebook is adaptively generated from the master codebook for each image block. The codewords in the state codebook are similar, and each one of these codewords may be a good candidate for representing the currently encoded image block. Based on this concept, Shie et al. proposed a method to hide a set of secret bits in each SMVQ index by encoding the currently processed image block into the codeword index equivalent to the set of secret bits. Consequently, most of the cover image blocks are not encoded into the indexes that represent the best-match codewords. Under these circumstances, the visual quality of the compressed cover image could be distorted seriously. In contrast, the introduced scheme introduces no extra coding distortion to the compressed cover image during the data-hiding procedure. Therefore, the visual quality of the compressed cover image obtained by the introduced scheme is quite acceptable.
FIGURE 12.8 Visual quality of the cover image “Lena” under Shie et al.’s scheme and the introduced scheme. (a) The original uncompressed cover image, (b) the compressed cover image with 48K secret bits by Shie et al.’s scheme, (c) the compressed cover image with 64K secret bits by Shie et al.’s scheme, (d) the compressed cover image with 80K secret bits by Shie et al.’s scheme, and (e) the compressed cover image by the introduced scheme.
A novel image steganographic scheme, applied on the VQ compressed domain of host image, has been introduced in this section. The introduced scheme remains an acceptable bit rate for the compressed host image after a large amount of secret information have been embedded into the compressed codes of the host image. Furthermore, the hiding of secret information does not introduce any distortion on the visual quality for the compressed host image. The receiver can efficiently receive both the hidden information and the compressed host image simultaneously. The new steganographic scheme outperforms the earlier-proposed schemes for the following reasons: (1) The SOC algorithm, efficient lossless compression technique for VQ index coding, is applied in the proposed scheme to reduce the bit rate of the cover image. (2) The secret data are hidden by technically embedding the secret bits into the compression codes of the cover image instead of modifying and translating these compression codes with other longer codes. (3) The hiding capacity of the cover image is not limited by the number of blocks partitioned from the cover image itself. (4) The proposed scheme does not introduce any visual distortion in the compressed cover image after secret data hiding.
FIGURE 12.9 Visual quality of the cover image “F16” under Shie et al.’s scheme and the introduced scheme. (a) The original uncompressed cover image, (b) the compressed cover image with 48K secret bits by Shie et al.’s scheme, (c) the compressed cover image with 64K secret bits by Shie et al.’s scheme, (d) the compressed cover image with 80K secret bits by Shie et al.’s scheme, and (e) the compressed cover image by the proposed scheme.
TABLE 12.5
Material parameters in macro-scale and mesoscale
12.5 VISUALLY IMPERCEPTIBLE IMAGE STEGANOGRAPHIC SCHEME BASED ON VQ
A novel visually imperceptible image steganographic scheme based on VQ is introduced in this section. Multiple secret images can be simultaneously and imperceptibly hidden into another cover image with the same image size by this scheme. In order to reduce the volume of secret images to be hidden, a codebook is first generated from the secret images and these images are encoded into binary indexes by the VQ technique. Then, the compressed data of secret images are embedded into the VQ codebook used in the encoding procedure by an adaptive LSB modification technique. For security purpose, the slightly modified codebook is further encrypted into a meaningless data stream by the DES cryptosystem. Finally, the encrypted codebook is embedded into the cover image using the greedy LSB modification technique. Simulation results show that this scheme provides a good improvement in the visual quality of the extracted secret images and the cover image at the receiver. In addition, it also provides a better hiding capacity for the cover image.
Visually imperceptible image steganography involves hiding one or more secret images into another noncritical image with minimal perceptible degradation. Recently, the technique of visually imperceptible image steganography has been widely studied and many researches have been proposed (Chen et al., 1998; Wang et al., 2001; Xuan et al., 2002; Chang et al., 2003; Hu, 2003; Thien and Lin, 2003; Chan and Cheng, 2004; Lin and Shie, 2004; Shie and Lin, 2009; Shie et al., 2010). Among these researches, a common technique for data embedding in image is on the basis of manipulating the LSB planes of image since LSB modification techniques usually achieve high-embedding capacity. Visually imperceptible image steganography can be used for covert communication. In the prior researches, raw images without any compression are directly embedded into the cover image. To solve the problem of inefficient hiding capacity, Chen et al. (1998) proposed an idea that secret images should be com-pressed by VQ and then encrypted before the hiding process, which is called virtual image cryptosystem. Hu (2003) proposed a revised algorithm of virtual image cryptosystem. In Hu’s scheme, each pixel value of the cover image was split into two parts. The significant one is used for VQ codebook training, and the insignificant one is used for data embedding by the greedy substitution. Consequently, several secret images can be hidden into another cover image by Hu’s scheme. ’ scheme provides more hiding capacity, lower computational cost, and better image quality than those of Chen et al.’s scheme (1998). In order to improve the efficiency of image steganography, Lin and Shie (2004) proposed an idea to transmit a set of secret images via its corresponding VQ codebook. This scheme focuses on both the hiding capacity of the cover medium and the quality of extracted secret images at the receiver. To achieve a high-capacity and high-quality image steganographic scheme, the VQ technique is applied in Lin and Shie’s scheme to compact the volume of secret images. Moreover, to guarantee the visual quality of extracted secret images at the receiver, the VQ codebook utilized in the encoding procedure is adopted as the cover medium. Lin and Shie’s scheme provides a new and original approach to transmit a set of secret images via network, especially for limited-bandwidth communication channel. Although the appearance of the embedded and encrypted cover medium looks like a meaningless data stream to the possible interceptors, the cover medium of Lin and Shie’s scheme (2004) is a VQ codebook, not a visually recognizable image. This may limit its practical utilization for the purpose of visual imperceptibility.
In this section, a novel visually imperceptible image steganographic scheme that improves Lin and Shie’s scheme (2004) is presented. To design a high-capacity and high-quality image steganographic scheme, the VQ technique is utilized to compact the volume of secret images. Moreover, to adaptively guarantee the visual quality of extracted secret images at the receiver, the VQ codebook utilized in the encoding procedure is slightly modified and totally embedded into the cover image. This scheme provides a visually imperceptible image steganographic approach for delivering a set of secret images to the receiver.
12.5.1 VISUALLY IMPERCEPTIBLE IMAGE STEGANOGRAPHIC SCHEME BASED ON VQ
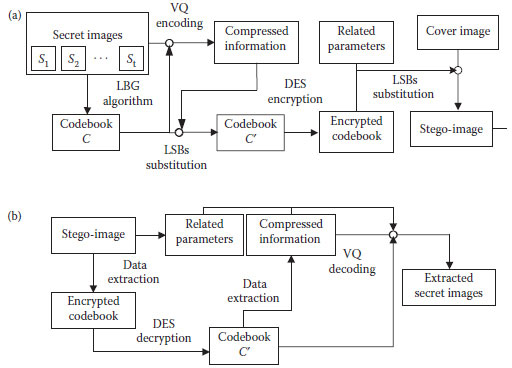
In the introduced visually imperceptible image steganographic scheme, the input of the transmitter is a set of secret images and a noncritical cover image, and the output of the transmitter is a stego-image with high visual quality. The goal of this scheme is to deliver a set of images secretly via a meaningful cover image of the same size.
Assume that there are t secret images to be delivered and these images are 8-bit gray-level images of w × h pixels. To compress the secret images with VQ, a codebook should be generated before the encoding procedure. Let the size of VQ codebook be Nc and the codeword be composed of m × n elements. These Nc codewords of codebook are generated based on the iterative LBG algorithm using the secret images as the training set. After the codebook C is generated, each of these secret images is partitioned into blocks of m × n pixels. Each image block is then encoded into a binary index of codeword. The compressed message of all secret images is obtained by merging these binary indexes. Therefore, the whole volume l (in the unit of bit) of the compressed information for secret images can be defined by the following equation:
(12.10) |
To embed multiple images into another cover image with minimal perceptible degradation and preserve good visual quality for secret images, the compressed information of secret images is first embedded into the VQ codebook associated with these images and the modified codebook is then embedded into the cover image. Let the number of modified LSBs for each codeword element and each cover image pixel be d and r, respectively. For 8-bit gray-level images, the following two formulas must be satisfied to accomplish the proposed image information-hiding scheme.
(12.11) |
(12.12) |
The flowcharts of the introduced image steganographic scheme are given in Figure 12.10. Figure 12.10 a describes the image-embedding procedures at the transmitter whereas the processes of image extraction at the receiver are presented in Figure 12.10b. The related parameters used in this scheme, t, w, h, m, n, Nc, d, and r, have to be preserved well for future use at the receiver. These parameters can also be embedded into the cover image. Note that the compressed information, the codeword indices, of secret images can be further compressed on the basis of some famous lossless compression techniques such as Huffman coding (Huffman, 1952), arithmetic coding (Witten et al., 1987), and SOC (Hsieh and Tsai, 1996) algorithms. For more security, the modified codebook is encrypted by the DES cryptosystem (National Bureau of Standards, 1997) to make it an encrypted and meaningless message. Furthermore, the encrypted codebook can also be losslessly compressed before it is embedded into the cover image. Finally, a stego-image covering a set of secret images is generated.
FIGURE 12.10 Flowcharts of the visually imperceptible image steganographic scheme. (a) Transmitter and (b) receiver.
The procedure of secret images’ extraction is quite simple at the receiver. To reconstruct the secret images, the encrypted modified codebook and the related parameters are directly fetched from the stego-image. The encrypted codebook is first decrypted based on the DES decryption procedure. After the decryption process, the modified codebook C′ is directly obtained. Therefore, the compressed information of secret images can be directly extracted from the codebook. With the parameters, including the number of secret images t, the image size w and h, the codeword size m and n, and the codebook size Nc, the compressed information of secret images can be decoded by performing table lookup operation on the modified codebook C′. Finally, all the secret images are reconstructed.
In the computer experiments, the introduced image steganographic scheme is performed on a set of four images (“Airplane, ” “Lena, ” “Pepper, ” and “Toys”). “Airplane” is used as a cover image and the other three images are used as secret images. These test images are all with size 512 × 512 pixels and 256 levels (8 bits) per pixel. To reduce the overall volume of image information to be embedded into the cover image, these three secret images are divided into image blocks with 8 × 8 pixels and the VQ codebook size is 1024. Consequently, there are 65, 536 (1024 × 8 × 8) elements and 524, 288 (1024 × 8 × 8 × 8) bits in this codebook. The length of each codeword index is 10 bits and the compressed information for each secret image is 40,960 (10 × (512 × 512)/(8 × 8)) bits.
In this experiment, the compressed information of the three secret images can be simultaneously embedded into the codebook, without the need of any further compression, by adaptively modifying the first and the second least significant bits of each codeword element. Under this circumstances, 960 codewords of the codebook are enough to embed the compressed information of three secret images. For more security, the modified codebook is further encrypted by the DES cryptosystem. The encrypted codebook is given in Figure 12.11. To accomplish visual imperceptibility, the encrypted codebook is directly and totally embedded into the cover image “Airplane, ” without the need of compression, by greedily modifying the first and the second least significant bits of each pixel in “Airplane” (512 × 512 × 2 = 5, 24, 288).
To demonstrate the performance of the described image steganographic scheme, Figure 12.12 shows the original image “Airplane” and the stego-Airplane with three hidden secret images. In addition, the original images of “Lena, ” “Pepper, ” and “Toys, ”and the corresponding secret images extracted at the receiver are given in Figures 12.13, 12.14, and 12.15, respectively.
FIGURE 12.11 The DES-encrypted codebook with codebook size 1024 and codeword size 8 × 8.
To verify the performance of the introduced image steganographic scheme, the hiding capacity (the maximum number of secret images) with respect to the size of the codebook, the modified LSBs in a codeword element, and the modified LSBs in a cover image pixel are listed in Table 12.6. This table illustrates that more hiding capacity can be provided by reducing the codebook size, modifying more LSBs in each codeword element, or modifying more LSBs in each cover image pixel by the proposed scheme. However, to provide better visual quality for secret images at the receiver, it is suggested that the number of modified LSBs within each codeword element should not exceed three. Under these circumstances, in terms of mean-squared error, the degradation of image quality between the VQ-compressed secret image at the transmitter and the extracted secret image at the receiver is bounded by (2d – 1)2. Here, d is the number of modified LSBs within each codeword element, and r is the number of modified LSBs in each cover image pixel. Note that in Table 12.6, which the codebook size equals 1024, the data volume (in bit) of codebook exceeds the available number of LSBs that can be modified in the cover image when r equals 1. Consequently, the hiding capacity of our scheme is not available (NA). In addition, the hiding capacity is identical when r equals 2 and 3. This is because we can embed only one codebook with size 1024 into the cover image when r equals 3, although the third LSB bit-plane of cover image remains unused. Under these circumstances, some smaller codebooks can be embedded into the unused LSBs. Table 12.7 lists the hiding capacity of the introduced scheme when several codebooks with different sizes are embedded into a cover image. Table 12.8 lists the hiding capacity of the introduced image steganographic scheme using only one codebook and modifying the rest available LSBs of cover image with more compressed information (VQ indices) of secret images.
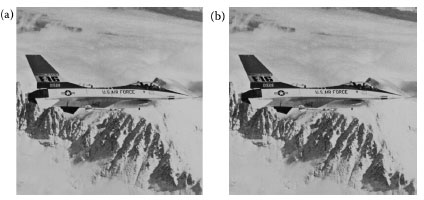
FIGURE 12.12 (a) Original “Airplane” and (b) stego-Airplane, PSNR = 45.883 dB.
FIGURE 12.13 (a) Original “Lena” and (b) extracted secret “Lena, ” PSNR = 31.573 dB.
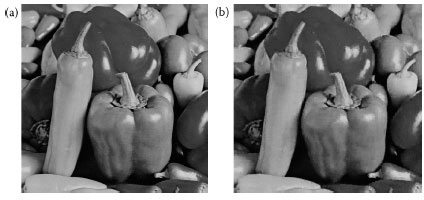
FIGURE 12.14 (a) Original “Pepper” and (b) extracted secret “Pepper, ” PSNR = 31.236 dB.
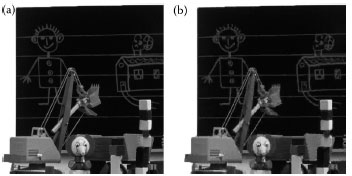
FIGURE 12.15 (a) Original “Toys” and (b) extracted secret “Toys, ” PSNR = 31.273 dB.
TABLE 12.6
Hiding Capacity (Maximum Number of Secret Images) of the Introduced Scheme Using Codebooks with the Same Size
Modified LS Bs of Cover Image |
||||
Codebook Size |
Modified LSBs of Codeword |
r = 1 |
r = 2 |
r = 3 |
64 |
d = 1 |
1 |
2 |
4 |
d = 2 |
2 |
5 |
8 |
|
d = 3 |
4 |
8 |
12 |
|
128 |
d = 1 |
1 |
2 |
3 |
d = 2 |
2 |
4 |
6 |
|
d = 3 |
3 |
6 |
10 |
|
256 |
d = 1 |
1 |
2 |
3 |
d = 2 |
2 |
4 |
6 |
|
d = 3 |
3 |
6 |
9 |
|
512 |
d = 1 |
0 |
1 |
2 |
d = 2 |
1 |
3 |
5 |
|
d = 3 |
2 |
5 |
8 |
|
1024 |
d = 1 |
NA |
1 |
1 |
d = 2 |
NA |
3 |
3 |
|
d = 3 |
NA |
4 |
4 |
|
To compare the proposed scheme with Lin and Shie’s scheme (2004), one example of the final appearance of cover medium, respectively, for these two schemes, is illustrated in Figure 12.16. The secret images are covered by a meaningless data stream, as shown in Figure 12.16a, in Lin and Shie’s scheme, whereas the secret images are under the protection of another high-quality image, as shown in Figure 12.16 b, in the proposed scheme. The hiding capacity with respect to the codebook size and the modified LSBs in a cover medium (codeword) element provided in Lin and Shie (2004) is listed in Table 12.9.
TABLE 12.7
Hiding Capacity (Maximum Number of Secret Images) of the Introduced Scheme Using Codebooks with Different Sizes
Modified LS Bs of Cover Image |
||||
Codebook Size |
Modified LSBs of Codeword |
r = 1 |
r = 2 |
r = 3 |
One 512 and multiple 256 |
d = 1 |
0 |
1 |
2 |
d = 2 |
1 |
3 |
5 |
|
d = 3 |
2 |
5 |
8 |
|
One 1024 and multiple 256 |
d = 1 |
NA |
1 |
2 |
d = 2 |
NA |
3 |
5 |
|
d = 3 |
NA |
4 |
7 |
|
TABLE 12.8
Hiding Capacity (Maximum Number of Secret Images) of the Introduced Scheme Using Only One Codebook and Modifying the Rest Available LS Bs of Cover Image with More Compressed Information of Secret Images
Modified LS Bs of Cover Image |
||||
Codebook Size |
Modified LSBs of Codeword |
r = 1 |
r = 2 |
r = 3 |
512 |
d = 1 |
0 |
8 |
15 |
d = 2 |
1 |
8 |
16 |
|
d = 3 |
2 |
9 |
16 |
|
1024 |
d = 1 |
NA |
1 |
8 |
d = 2 |
NA |
3 |
9 |
|
d = 3 |
NA |
4 |
11 |
|
A visually imperceptible image steganographic scheme capable of delivering multiple images secretly through another high-quality image has been introduced in this section. This scheme provides impressive improvement both in the visual quality of extracted secret images and in the hiding capacity of the cover image. Moreover, the visual quality of the stego-image is quite good when comparing it with the original cover image. This scheme outperforms Lin and Shie’s scheme because of the following reasons: (1) The secret images are included in the training set in the codebook generation procedure. (2) The volume of secret images to be transmitted is greatly reduced by applying the VQ technique on these images. (3) The codebook associated with these secret images is embedded into the cover image as well. (4) The cover medium is a meaningful image, not a meaningless data stream.
FIGURE 12.16 The final appearance of cover medium. (a) Lin and Shie’s scheme and (b) the introduced scheme.
TABLE 12.9
Hiding Capacity (Maximum Number of Secret Images) in Lin and Shie’s Scheme
Modified LS Bs of Cover Image |
||||
Codebook Size |
Data Stream Size |
m = 1 |
m = 2 |
m = 3 |
2048 |
128 kB |
2 |
5 |
8 |
4096 |
256kB |
5 |
10 |
16 |
Barni, M., Podilchuk, C. I., Bartolini, F., and Delp, E. J., Watermark embedding: Hiding a signal within a cover image, IEEE Communications Magazine, 39(8)1021082001
Bender, W., Gruhl, D., Morimoto, N., and Lu, A., Techniques for data hiding, IBM Systems Journal, 35(3&4)3033361996
Bourbakis, N. and Alexopoulos, C., Picture data encryption using scan patterns, Pattern Recognition, 25(6)5675811992
Chan, C. K.and Cheng, L. M., Hiding data in images by simple LSB substitution, Pattern Recognition, 374694742004
Chang, C. C., Chen, G. M., and Lin, M. H., Information hiding based on search-order coding for VQ indices, Pattern Recognition Letters, 25125312612004
Chang, C. C., Hsiao, J. Y., and Chan, C. S., Finding optimal least-significant-bit substitution in image hiding by dynamic programming strategy, Pattern Recognition, 36158315952003
Chen T. S., Chang, C. C., and Hwang, M. S., A virtual image cryptosystem based upon vector quantization, IEEE Transactions on Image Processing, 7(10)148514881998
Cox, I. J., Kilian, J., Leighton T., and Shamoon, T., Secure spread spectrum watermarking for multimedia, IEEE Transactions on Image Processing, 6(12)167316871997
Davis, R. M., The Data Encryption Standard in Perspective, Computer Security and the Data Encryption Standard, National Bureau of Standards Special Publication, February 1978
Du, W. C. and Hsu, W. J., Adaptive data hiding based on VQ compressed images, IEE Proceedings Vision, Image, and Signal Processing, 150(4)2332382003
Highland, H. J., Data encryption: A non-mathematical approach, Computer & Security, 163693861997
Hsieh, C. H.and Tsai, J. C., Lossless compression of VQ index with search-order coding, IEEE Transaction on Image Processing, 5(11)157915821996
Hu, Y. C., Grey-level image hiding scheme based on vector quantization, IEE Electronics Letters, 39(2)2022032003
Huffman, D. A., A method for the construction of minimum redundancy codes, Proceedings of the IRE, 40109811011952
Jan, J. K. and Tseng, Y. M., On the security of image encryption method, Information Processing Letters, 602612651996.
Kohn, D., The Codebreakers: The Story of Secret Writing, Scribner, New York, 1996
Lin, S. D.and Shie, S. C., Secret image communication scheme based on vector quantization, IEE Electronics Letters, 40(14)8598602004
Linde, Y., Buzo, A., and Gray, R. M., An algorithm for vector quantizer design, IEEE Transactions on Communications,288495
Marvel, L. M. and Retter, C. T., Hiding information in images, Proceedings of the IEEE International Conference on Image Processing, 23963981998
National Bureau of Standards (U.S.), DES Encryption Standard, Federal Information Processing Standards Publication, 46, National Technical Information Service, Springfield, VA, April 1997.
Petitcolas F. A. P., Anderson, R. J., and Kuhn, M. G., Information hiding—A survey, Proceedings of the IEEE, 87(7)10621078
Rhee, M. Y., Cryptography and Secure Communication, McGraw-Hill Book Company, Singapore, 1994
Rivest, R., Shamir, A., and Adleman, L. A. method for obtaining digital signatures and publickey cryptosystems, Communications ACM, 21(2)1201261978
Shie, S. C., Jiang, J. H., Chen, L. T., and Huang, Z. H., Secret image transmission scheme using secret codebook, IEICE Transactions on Information and Systems, E93–D(2), 3994022010
Shie, S. C., Lin, S. D., and Fang, C. M., Adaptive data hiding based on SMVQ prediction, IEICE Transactions on Information and Systems, E89-D(1)3583622006
Shie, S. C. and Lin, S. D., Data hiding based on compressed VQ indices of images, Computer Standards & Interfaces, 31(6)114311492009
Stallings, W., Cryptography and Network Security, Prentice Hall, New Jersey, 1999
Thien, C. C. and Lin, J. C., A simple and high-hiding capacity method for hiding digit-by-digit data in images based on modulus function, Pattern Recognition36287528812003
Wang, R. Z., Lin, C. F., and Lin, J. C., Image hiding by optimal LSB substitution and genetic algorithm, Pattern Recognition346716832001
Witten, I. H., Neal, R. M., and Cleary, J. G., Arithmetic coding for data compression, Communications ACM, 30(6)5205401987
Wu, D. C. and Tsai, W. H., Spatial-domain image hiding using image differencing, IEE Proceedings Vision, Image and Signal Processing, 147(1)29372002
Xuan, G., Zhu, J., Chen, J., Shi, Y. Q., Ni, Z., and Su W., Distortionless data hiding based on integer wavelet transform, IEE Electronics Letters, 38(25)164616482002