The Russian Federation’s cyber posture was one of President Putin’s highest priorities after taking office in December 1999. As a result, Russia probably has the most coherent state plan integrating private and government cyber sectors. The plan’s unclassified aspects are elaborated in documents available on Russian government websites. The plan’s implementation is seen through Russian laws, presidential decrees, and government regulations, contracts, and actions. The plan, however, also has classified annexes addressing perceived internal and external cyber threats, as well as the information operations (IO) capabilities needed to address those threats. Implementation can also be tracked, although with somewhat more difficulty.
The first Russian National Security Blueprint issued under President Yeltsin in December 1997 placed little emphasis on information warfare. Prime Minister Vladimir Putin chaired a fall 1999 series of Russian Security Council meetings to revise the document. The new National Security Concept, issued under President Putin in January 2000, pointed to “information warfare” and the disruptive threat to information, telecommunications, and data-storage systems. The new Military Doctrine issued in July 2000 discussed hostile information operations conducted through either technical or psychological means.[76]
In September 2000 the Security Council issued the first Russian Federation Information Security Doctrine.[77] The 46-page document provided the first authoritative summary of the Russian government’s views on information security in the public, government, and military sectors. The document also provided the strategic plan for future legal, organizational, and economic developments. The Security Council’s Department of Information Security,[78] one of seven Security Council Departments, drafted the document. Since September 2000, the Security Council has published additional supporting documents identifying research areas and Russia’s transition to an “Information Society.” The most recent presidential decree in May 2011 augmented the Security Council’s Interdepartmental Commission on Information Security’s capability to coordinate government action. As a body, these documents show a coherent government response to perceived information security threats.[79] Changes in government and military structures and procedures show the plan is being implemented aggressively.
The Information Security Doctrine stated that existing Russian law did not address Russia’s information security needs. As a result, the government passed a series of laws, and amendments to existing laws, addressing these deficiencies. However, certain laws also support information operations directed against perceived threats. For example, in 2009, amendments to Federal Law No. 149-FZ—On Information, Information Technologies, and Information Protection—mandated national identification numbers for Internet registration. The amendments also required that Russian operators provide authorities with registration information and other data needed for an investigation. The Russian press saw this as a threat to Internet freedom because the government could quickly identify who posted critical comments on a social media site.
At the same time, Federal Law No. 152-FZ, On Personal Data, prohibits Russian operators from releasing data to an “authority of a foreign state, a person or entity of a foreign state,” except under several limited and unlikely circumstances.[80] As a result, the law effectively prohibits Russian operators from passing data to foreign law enforcement agencies investigating cyber crimes or Distributed Denial of Service (DDoS) attacks. Inquires must be made from government to government. Thus by controlling the information they choose to release, the Russian government can protect Russian Internet operations from investigations by foreign states.
The amendments to the Russian Federal Security Service (FSB) Law are particularly worrisome. The FSB Law authorizes activities in counterintelligence, combating terrorism, crime, intelligence gathering, border security, and information security. The FSB is responsible for protecting critical infrastructure, including communication networks. Article 15 defines modalities for relations between the FSB and other Russian institutions in executing FSB responsibilities. Under Article 15:
Public authorities, as well as enterprises, institutions, and organizations, are obliged to provide assistance to the Federal Security Service in carrying out their assigned duties.
Individuals and legal entities in Russia providing postal services, telecommunications of all kinds, including systems, data communication, confidential, satellite communications are obliged at the request of the Federal Security Service to include in the extra hardware equipment and software, as well as create other conditions necessary for the operational and technical measures by the Federal Security Service.
In order to meet the challenges of RF, security forces of the Federal Security Service could be assigned to public authorities, enterprises, institution, and organizations irrespective of ownership, with the consent of their managers in the manner prescribed by the President of Russia, leaving their military service.
Russian law ensures that significant Internet infrastructure remains under Russian control. Under the provisions of Federal Law No 57-FZ, The Strategic Companies Law, foreign entities cannot acquire a controlling interest in a strategic company without prior approval from the Russian government. Through provisions specifying which entities can perform data-encryption services, the law covers the telecommunications sector directly and the Internet sector indirectly.
The Russian government controls the critical Russian Internet structure. The Russian fiber optic network, which is owned by national and regional communications companies that are Russian Railways subsidiaries, is normally routed along railroad right of ways. Russian Railways is the state-owned company run by Vladimir Yakunin, a former KGB officer who is in Putin’s St. Petersburg circle.
The primary organization overseeing Russian Internet development is the Russian Institute for Public Networks (RIPN/RosNIIROS). According to its website (www.ripn.net), RIPN was started in 1992 as a nonprofit organization by the Russian State Committee for Science and Education and Kurchatov’s Institute of Atomic Energy. RIPN founded another nonprofit, the Moscow Internet Exchange (full name: ANO TSVKS MSK-IX), in 2001.
According to its website (www.msk-ix.ru), MSK-IX provides vendor-neutral Internet infrastructure. However, MSK-IX’s website shows that customers sign two contracts: one for ANO TSVKS MSK-IX basic services and one for technical connection to the Internet. The technical connection contract states that MSK-IX’s M9 facility is located at a facility owned by Open Joint Stock Company MMTS-9 (OAO MMTS-9) at Butlerova 7. OAO MMTS-9 is a subsidiary of Russia’s nationally owned telecom company Rostelecom. Essentially, this means that the Russian government ultimately controls the Internet connections.
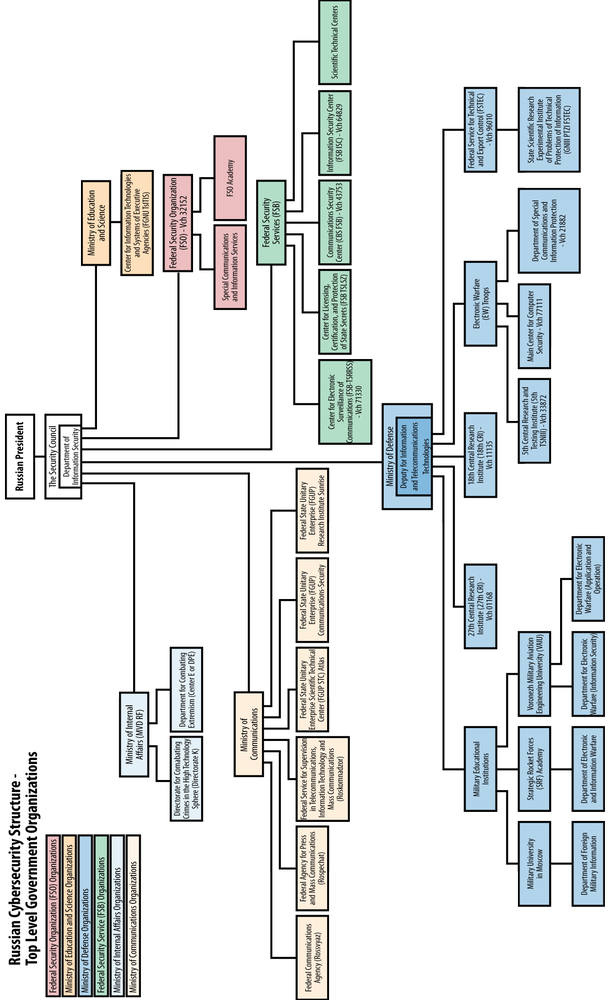
A March 2011 article in Finansovaya Gazeta, a publication of the Russian Finance Ministry, provided a tutorial on the top-level structure of Russia’s “Comprehensive Information Protection System (KSZI).” (See Figure 15-1.) According to the article, the KSZI starts with two organizations: the Federal Service for Technical and Export Control (FSTEC[81]), subordinate to the Ministry of Defense, and the Federal Security Service (FSB), subordinate to the Russian president. The FSTEC certifies technical equipment and issues licenses to both private and government organizations for work with classified information. The FSB issues licenses for work with cryptographic material, and it controls the dissemination of cryptographic material, including technical equipment and software. Federal Law No. 40-FZ, On the Federal Security Service, assigns the FSB overall responsibility for protecting Russia’s information security and critical infrastructure—including telecommunications and the Internet—placing the FSB above the Ministry of Defense in the KSZI food chain. Indeed, FSB authority over Russia’s cryptographic infrastructure is nearly absolute.[82] Even the Russian Academy of Cryptography, a prestigious academic institution, is subordinate to the FSB.
Russian Presidential Decree No. 351 identifies one additional organization critical to the Russian Internet, the Federal Security Organization (FSO)[83]—also subordinate to the president. Decree No. 351 tasks the FSO with developing secure Internet connections for the Russian government that deali with classified information. The KSZI starts with the Russian Federation Security Council’s Information Security Department, a Ministry of Defense body, and two security service components.
We now turn to changes in the Russian Ministry of Defense (MOD) driven by the Information Security Doctrine. These changes enhance the MOD’s ability to develop IO- relevant technology and rationalize IO force structures.
President Putin’s Edict No. 1477 in November 2007 mandated changes in the Russian Ministry of Defense. The edict created two new deputy defense ministers. The Deputy for Information and Telecommunications Technologies now handles automated control systems, telecommunications, and information technology. Russian press commentary stated that this transferred responsibilities from the Directorate of Communication Troops and the General Staff’s 8th Directorate (Information Security) to a civilian. Press commentary also stated that the General Staff was not pleased. Chief of General Staff Yuri Baluyevsky, his First Deputy, the chief of the Main Operations Directorate, the chairman of the General Staff Military Scientific Committee, and the chief of Armed Forces Communications all left their offices in protest over the diminution of their authority.[84] The first deputy minister was Major General (Reserves) Oleg Eskin, a former FSB officer.
While not stated specifically, the new deputy defense minister’s portfolio almost certainly includes IO.
The decade after the 2000 Information Security Doctrine saw an explosion of IO writing by Russian military officers and defense oriented academics (see the sidebar, Russian Information Technology (IT) Security Training). Some, such as Noncontact Wars by Major General (Ret.) Vladimir Ivanovich Slipchenko, attracted foreign comment.[85] By decade’s end, the Russian military was consolidating significant offensive and defensive IO capabilities in the Electronic Warfare (EW) Troops. Indeed, speaking at a conference in February 2008—before the August Russia-Georgia conflict—Deputy Chief of the General Staff Aleksandr Burutin stated that the military, and the security services, were creating appropriate units and conducting training. In an April 2010 Krasnaya Zvezda interview, Chief of Russian Electronic Warfare Troops Colonel Oleg Ivanov stated that the EW Troops had special equipment for operations against information management systems.[86]
The senior officer’s statements highlighted an ongoing process. In June 2001 Russian Public Television, ORT, presented a segment on the Voronezh Military Radio-Electronics Institute (VIRE). The ORT correspondent stated that the institute started one secret information security school in 1997, and then another secret school devoted to information warfare. The information warfare school began training professional hackers for the military in 2001. Both schools were located in the Department of Automatic Control Systems.
In 2008 Russian Federation Order No. 1951 restructured military higher education and established the Voronezh Military Aviation Engineering University (VAIU). The order authorized the university 15,092 total civilian and military personnel. According to a May 2009 article, the university was expanding, with the cadet body growing from 4,800 to 6,500.
The restructured university includes two schools covering information security and information warfare. The VAIU website shows departments for Electronic Warfare and Electronic Warfare (Information Security). The five-year program in Electronic Warfare (Information Security) leads to designation as Specialist Data Protection for both military and “law enforcement agencies.” The web page content for the Department of Electronic Warfare (Information Security) is quite sparse compared to other department pages, which suggests that the material is sensitive. The extremely high ratio of staff to students—approximately 15,000 total staff and 6,000 students—is strange unless VAIU’s role goes beyond training junior officers.
There is also a Department of Electronic and Information Warfare at the Strategic Rocket Forces (SRF) Academy. The web page for Dr. Anatoly Horev, the head of the Department of Information Security at the Moscow Institute of Electronic Technology (MIET), states that he headed that SRF Academy department from 2001 to 2007.[87] However, published articles show the previous department head, Colonel Vladimir Novikov, speaking on information warfare at a Moscow think tank in 2001.
There is little information on the specialized electronic and information warfare curriculum at VAIU and the SRF Academy. However, university-level training in various IT security specialties is taught at approximately 90 institutions (see the sidebar, ). Many, including the prestigious Moscow Engineering Physics Institute (MIFI), train students sponsored by the security services and military. Indeed, MIFI’s Department of Information Security “participates in military-scientific and scientific research work on military topics.”
Information warfare’s softer side is addressed at the Military University in Moscow. According to a 2000 Krasnaya Zvezda article, the university’s Department of Foreign Military Information—formerly the Department of Special Propaganda—had reorganized to include information security material.[88]
In 2004 two presidential edicts transformed the State Technical Commission (Gostekhkomissiya) into the Federal Service for Technical and Export Control (FSTEC), subordinate to the Russian Ministry of Defense. All federal and regional Gostekhkomissiya components transferred to the FSTEC. Edict No. 314 also transferred export control from the Russian Ministry of Economic Development and Trade to FSTEC.
FSTEC’s focus is information security and export control of sensitive technology. FSTEC is responsible for information security in Russia’s information and telecommunication networks,[89] and it directs technical intelligence countermeasures guarding networks from foreign penetration. FSTEC works closely with the FSB. The FSB retains sole responsibility for cryptographic technology.
FSTEC exercises its responsibilities by licensing organizations and technology, overseeing projects, and monitoring networks. The FSTEC website posts reference documents, such as information security-related laws and regulations. The site also posts lists of technologies and organizations certified for information security projects.
FSTEC also projects information security threats and develops countermeasures, including future training requirements for information security personnel. FSTEC’s State Scientific Research Experimental Institute of Problems of Technical Protection of Information (GNIII PTZI FSTEC), located in Voronezh, works with government laboratories, educational institutions, and certified contractors. GNIII PTZI FSTEC also works with government-owned Russian companies, such as Gazprom and Russian Railways. Several well-known information security companies, such as Informzashchita and Bezopasnost, are probably GNIII PTZI FSTEC spinoffs.
The Russian Duma is debating amendments to Federal Law No. 152-FZ, On Personal Data, which would expand FSTEC’s reach. Amendments to the current law, ostensibly written to protect personal privacy, would require FSTEC and FSB certification for organizations that store personal data. Russian press commentators point out that this includes social media. The Duma is also considering amendments to the Criminal Code, which would require social network operators to register users’ internal passport numbers. Because certification includes monitoring for compliance, FSTEC could quickly identify “problems” on social media sites and the persons involved.
Founded in 1960, the 5th TSNIII is the MOD’s lead institute for EW research. The 5th TSNIII has long been listed as an FSTEC-approved certification center for information security. Several official information security publications list the institute as author. Russian social media sites and posted resumes include employment at the institute and/or Vch 33872.[90]
The postings indicate that the institute employs 100 to 1,000 range, or 1,000 to 10,000. An unclassified article on MOD research institutes stated that the 5th TSNIII employs around 2,000 people, with approximately 200 of those personnel possessing PhDs.
The 5th TSNIII probably changed names during the 2010 MOD reorganization. The new name is Federal State Research and Test Center of Electronic Warfare and Evaluation of Low Observables (FSI FGNIITS EW OESZ).[91] The new center is located at the same Voronezh address as the 5th TSNIII, and is listed as an information certification center on the 2011 FSTEC list. For the first time since the late 1990s, the 5th TSNIII no longer appears. The VAIU website lists the new center as a VAIU component. However, while not mentioned specifically, Putin’s 2008 Russian government decree reorganizing the military educational system does allow for “subsequent formation of separate structural subunits.”[92] The center’s location under VAIU might explain the high ratio of staff to students, as mentioned previously.
Voronezh city documents and the VAIU website show VAIU’s Department of Electronic Warfare and Information Security and the center located at the same Voronezh address. The co-location of an FSTEC information security certification center and VAIU’s “hacker” training department is interesting (see the sidebar, ). A 2006 Russian military press article stated that VIRE—now a VAIU component—needed a unified teaching and research center for the quality EW training of personnel from the armed forces, FSB, and Interior Ministry (MVD). The co-location achieves that goal.
Subordinate to the General Staff’s Main Intelligence Directorate (GRU), the 18th CRI is the MOD’s main research center for signals intelligence. Originally focused on radio intercept and satellite communications, the 18th CRI also works on wireless devices, and it may have a role in Supervisory Control and Data Acquisition (SCADA) system security.[93] The FSTEC 2011 list on certified information security products lists Vch 11135 as a testing laboratory.[94] Russian press articles state that Vch 11135 developed the first electromagnetically shielded personal computer approved for use by the MOD, FSB, and MVD. The articles state the computer, produced in a Vch 11135 facility, is also used by financial institutions. The 18th CRI employed approximately 5,700 people in 2010.
The 27th CRI is the MOD’s lead institute on information technology and command and control systems. The 27th CRI’s full title includes the subtitle “Scientific and Research Testing Center Communication Systems,” reflecting the 2010 merger with the 16th Central Research and Testing Institute (16th TSNIII—Vch 25871) done under Ministry of Defense Order No. 551. The 27th CRI headquarters is in Moscow; the test center is in Mytishchi, northeast of Moscow.
According to an unclassified history, the 27th CRI was founded in 1954 as the MOD’s Computer Center No. 1. As the country’s first computer center, the 27th CRI recruited personnel from the military academies and from Russia’s most prestigious schools, including Moscow State University (MGU) and the Moscow State Engineering Physics Institute (MEPHI). 27th CRI software personnel worked on the Soviet space program and military missile programs. The 27th also provided support to the GRU. According to General of the Army Aleksandr Starovoytov (a KGB SIGINT officer), Vch 01168 examined ways to use computer networks to spread disinformation.
The 27th CRI also provided the Russian MOD’s initial Internet access. According to Russian press, prior to 2004 the 27th CRI formed the Strategiya Agency as an experimental Internet program for connecting the MOD. The connections provided service for a variety of MOD components, including the General Staff Main Operations Directorate and Electronic Warfare Directorate. The connections provided access to global information resources for research purposes. The 27th CRI works closely with Vch 49456, a MOD center for automation listed on MOD computer contracts. Vch 49456 might be directly subordinate to the 27th CRI; however, we cannot be certain.
The 27th CRI employed at least 1,700 personnel in 2010. Vch 49456 employed at least another 700.
Russia’s Information Security Doctrine shows a tension between the government’s assessment that the Internet drives technical progress while spreading ideas threatening “Russia’s spiritual revival.” As a result, the FSB and the MVD have developed Internet-oriented components. These components are direct first at the internal threat to domestic stability. However, they also have offensive potential.
The FSB’s Information Security Center (FSB ISC) is the FSB’s component for counterintelligence operations involving Russia’s Internet (RuNET). FSB ISC operations include monitoring RuNET and analyzing Internet content. However, FSB ISC also plays a role in offensive IO.
The FSB’s Information Security Center was formed in 2002 when FSB Director Nikolay Patrushev reorganized the Department of Computer and Information Security. The reorganization transferred some administrative and developmental functions to other FSB components—including the Center for Communications Security; the Center for Licensing, Certification, and Protection of State Secrets; and the Scientific Technical Center—while focusing FSB ISC on counterintelligence operations on RuNET. FSB ISC is also designated as an FSB expert investigative center, performing forensic investigations for criminal prosecution. Russian law authorizes FSB ISC to conduct legal investigations and take action against Russian citizens. FSB ISC works closely with the Russian Ministry of the Interior Directorate K—the cyber crime directorate—headed by Lieutenant-General Boris Nikolayevich Miroshnikov, who transferred to the MVD after heading FSB ISC.
FSB ISC First Deputy Director Dmitri Frolov speaks frequently, stressing FSB ISC’s role in preventing terrorist and criminal activity on RuNET. Frolov also speaks on the FSB’s need for improved technical capabilities and increased legal authority to counter cyber terrorism and cyber crime.
The FSB monitors Internet traffic using hardware and software installed at Russian Internet Service Providers (ISPs), Internet access points, and Internet exchanges. The Internet monitoring system—known as SORM—was first established in the 1990s. The existing system began a major upgrade with contracts let during 2007 and 2008. The upgrade will enhance FSB ISC’s ability to remotely task the Internet monitoring system and analyze collected information offline in a dedicated center located at the FSB ISC building. The upgrade also enhances FSB ISC nonattributable Internet operations.
FSB ISC capabilities can be used for offensive purposes. In 2008 Cnews.ru quoted deputy head of the Russian Armed Force General Staff Major-General Aleksandr Burutin on Russian Information Operations. General Burutin stated that the FSB, along with the Ministry of Defense, was developing “special methods of conducting information warfare.” Websites named by FSB ISC First Deputy Director Frolov as supporting terrorist and extremist activity—such as Chechen-oriented Kavkazcenter.org—have suffered disruptive attacks. Russian press attributes the attacks to patriotic hackers, although they note FSB’s tacit approval.[95] After Wikileaks threatened to publish embarrassing information on Russia, including possible Russian intelligence service operations, a November 2010 article by Aleksey Mukhin stated that the FSB ISC had informed Russian leadership that Wikileaks could be rendered inaccessible forever “given the appropriate command.”
The FSB Center for Electronic Surveillance of Communications (FSB TSRRSS) is responsible for the interception, decryption, and processing of electronic communications. The center—also known as the 16th Center (Directorate) FSB—is directly subordinate to the FSB Director.
In 1991 Russian President Yeltsin broke up the KGB, transferring the 16th Directorate to the Federal Agency of Government Communications and Information (FAPSI). The 16th Directorate became FAPSI’s Main Directorate for Communications Systems Signals Intelligence (GURRSS). The KGB’s 8th Main Directorate—responsible for communications security—also went to FAPSI. In 2003 Russian President Putin disestablished FAPSI, with many communications security and intercept functions going to the FSB. Responsibility for government communication networks went to the Federal Security Organization (FSO).
The internal structure and size of the FSB 16th Center is uncertain. However, an unclassified history states that in 2003 FAPSI had 38,500 servicemen and 14,900 civilian employees. A 2003 Kommersant article estimated that most would transfer to the FSB, with the rest going to the FSO and Ministry of Defense.
Vch 71330 registered a small block of IP numbers with the European Internet authority, RIPE. The block is on Autonomous System Number 12695 (AS12695) registered to a Russian Closed Joint Stock Company (JSC) Digital Network (www.di-net.ru/). According to the RIPE database, JSC Digital Network is a major service provider hosting networks for government and private entities. JSC Digital Network also maintains a small block of IP numbers for Vch 43753, the FSB Communications Security Center.
The FSB oversees Russian government and private entities handling sensitive technologies and information, including financial transactions. The FSB executes administrative oversight through two centers directly subordinate to the FSB Director: The Center for Licensing, Certification, and Protection of State Secrets, and The Communications Security Center. Both centers are at the main FSB Lubyanka headquarters building.
FSB’s Center for Licensing, Certification, and Protection of State Secrets (FSB TSLSZ) is the lead Russian department for licensing enterprises, institutions, and organizations for work with state-secret information. FSB TSLSZ, along with the Federal Service for Technical and Export Control (FSTEC), also regulates the import and export of cryptographic technology and technical surveillance equipment.[96]
The FSB exercises tight control over encryption technology. By Russian law and presidential decree, no public organization or private enterprise can use encryption technology without an FSB license. The FSB publishes a list of FSB approved testing laboratories that TSLSZ recognizes. The FSB list includes government organizations—including three directly subordinate to the FSB—one military unit, and private companies.
The FSB Communications Security Center (CBS FSB)—Military Unit (Vch) 43753 or 8th Directorate FSB—ensures that government communication systems use approved products. The center also ensures government communication projects meet security standards. While TSLSZ licenses a company for work with state-secret information, the Communications Security Center approves specific products developed by the company. Russian advertisements for software products frequently list their CBS FSB license so customers know they can be used in secure systems. Russian contracts for government communication projects are subject to CBS FSB approval if they involve state-secret information or financial transactions. The Russian press frequently quote CBS FSB personnel on information security topics. CBS FSB personnel also attend and give presentations at information security conferences; by contrast, TSLSZ personnel are less visible.
Government Decree N-1316 reorganized the Russian Interior Ministry (MVD), establishing the Department for Combating Extremism (Center E, or DPE). In a 2009 Vremya Novostey interview, MVD Major-General Valery Kozhokar—Chief of the Main Administration Directorate—detailed the new department’s mission:
As for Center “E,” it works in several fields: suppressing extremist organizations and associations, including youth groups, and counteracting religious extremism and ethnic extremism. In short, it fights terrorism.
Independent Russian press, however, claim that Center E is focused on political dissent—especially critics of Prime Minister Putin—and vice extremism. The press draws analogies between Center E and the Ministry of State Security (KGB) 5th Directorate, targeting ideological crime and dissent.
Russian government opponents and supporters both state that Center E is aggressively using the Internet to identify targets. MVD Lieutenant-General Yuri Kokov currently heads Center E. Kokov’s press spokesman Yevgeniy Artemov detailed the methods available to Center E under Russian law:
According to the law On Operational Investigative Activities, the list of operational investigative measures includes: interrogation; making inquires; surveillance; the searching of structures, buildings, facilities, parcels of land and transportation assets; the control of mail, telegraph and other communications; monitoring of telephone conversations; as well as operational penetration.
General Yuri Kokov stated that Center E maintains an extremist database, which integrates existing databases from the MVD, FSB, and FSO. The existing databases include near real-time information on train and airline ticket purchases. MVD officers can access the database via desktop and handheld devices.
The Directorate for Combating Crimes in the High Technology Sphere (Directorate K) of the Russian Federation Ministry of Internal Affairs (MVD RF) investigates cyber crimes and illegal activity related to information technology in Russia. Directorate K works closely with Russia’s Federal Security Service (FSB) and with foreign law enforcement agencies.
Directorate K’s current responsibilities include:
Computer crime
Illegal access to computer information
Manufacture, distribution, and use of malicious software
Fraudulent use of the electronic payment system
Child pornography
Telecommunications and Internet crime
Illegal use of either cellular or wired telecommunications networks
Fraud executed through either telecommunications networks or Internet
Illegal access to commercial satellite and cable television
Illegal sale of electronic and special technical equipment (monitoring equipment)
Copyright violations and pirating of equipment and software
International crime in the information technology sector
Cooperation with foreign law enforcement agencies
International cooperation against any crime committed with information technology
Russian press, however, states that Directorate K works with the FSB and MVD Center E to suppress domestic political dissent. In December 2007 Novaya Gazeta stated that major Russian hosting service Masterhost blocked access to opposition websites after receiving a letter from Directorate K. Sergey Kopylov, head of Masterhost’s legal department, acknowledged that Masterhost had received an MVD communication about suspending service. Novaya Gazeta wrote to Directorate K’s press service—normally eager to place stories concerning Directorate K activity—without receiving a reply.
Opposition party leaders also detailed DDoS attacks on their websites and disruptions in cell phone service. They complained that the authorities displayed little interest in their problems, stating Internet activity would probably move to foreign servers. In March 2010 Solidarity member Olga Kurnosova told Ekho Moskvy Radio that Directorate K shut down the 20March website for being extremist. According to Ms. Kurnosova, opposition activists used the site for communication and coordination of protests.
Russian officials are concerned that opposition forces will use foreign social networking sites to coordinate activity. Since 2005, the major Russian social networking sites VKontakte and Odnoklassniki have come under financial control of pro-Kremlin oligarchs, including DST Global’s Yuri Milner.[97] According to Moscow Vedomosti Online, in November 2010 Russian social networking activity was shifting to Facebook and Twitter. As a result, Russian telecommunication companies MTS and Vympelkom reached agreements with Facebook, providing free Facebook access for subscribers. Anticipating continued growth in Russia, Facebook is developing a Russian interface. The Russian search engine Yandex—monitored by FSB ISC—is also indexing Facebook internal pages.
The growing links between Russian companies and Facebook helps the FSB and MVD Directorate K monitor possible opposition group Facebook activities. The FSB can monitor Internet activity originating in Russia because all outbound traffic passes through gateways controlled by government entities. MVD Directorate K can exercise authority over Russian telecommunications companies and instruct them to cut off access during internal disturbances. Day-to-day monitoring allows both the FSB and MVD Directorate K to identify possible “extremists” for inclusion in MVD Center E’s extremist database.[98]
Russian internal security concerns create potential problems for Western companies and law enforcement. The Russian government is concerned that the Internet provides dissident movements a way to organize anti-government actions and reach a worldwide audience. The government is particularly concerned about a Russian equivalent of the Ukrainian and Georgian “color revolutions,” which helped topple their governments. The Russian government sees social networking sites as especially threatening. As a result, major Russian social networking sites are now controlled by Russian businesses, which are controlled by pro-government figures. As discussed in Chapter 14, the 2011 Middle East revolutions, and the prominent role of social media attributed to their success, only increase those concerns.
If it sees a significant threat, the MVD will approach Western companies and law enforcement to get information on dissident groups that are using Western social networking sites. Indeed, the creation of MVD Center E helps lower the profile by moving inquiries from the intelligence services to the police. Inquiries will almost certainly be supported with evidence linking these groups to extremist activity. The MVD could also approach companies directly.
The FSB, however, could also exploit social networking sites through covert means because Russian law allows for “operational penetration.” Russian law also requires Russian companies and organizations—both government and private—to cooperate with the FSB. As a result, the FSB could request assistance in penetrating “extremist” groups using social networking sites partially owned by Russian companies.
President Yeltsin established the FSO[99] in 1991—then named the Main Protection Directorate—from the KGB’s 9th Directorate responsible for leadership security.[100] As mentioned previously, President Putin disestablished the Federal Government Communications and Information Agency (FAPSI) in 2003, transferring the Special Communications and Information Service to the FSO, with other FAPSI elements transferred to the FSB. The FSO retained leadership protection responsibilities.
The Russian law assigns the FSO responsibility for organizing and running secure communications for state structures, and protecting them from foreign intelligence services. The FSO exercises these responsibilities through the Special Communications and Information Service. The Special Communications and Information Service runs the network of situation centers, which serves the president and state structures.[101] As noted earlier, in 2008 President Putin tasked the FSO with developing secure Internet connections for state structures working with classified information. The FSB retains overall state authority for cryptography; however, the FSO runs the cryptographic system on its networks and retains the keys.[102] Russian contracts show that the FSO works closely with Vch 43753—8th Directorate FSB—and the FSTEC.
The Special Communications and Information Service situation centers, shown in Figure 15-3, also provide the Russian leadership analytic support. General of the Army Aleksandr Starovoytov, former FAPSI director, stated in a 2010 interview that the analytic support included cutting-edge work on decision support systems, as well as information retrieval from large documentary databases, including “grey” literature on research and development projects.
General Starovoytov now heads the Center for Information Technologies and Systems of Executive Agencies (FGNU TsITiS) under the Ministry of Education and Science and the International Center of Informatics and Electronics (InterEVM). According to Starovoytov, TsITiS transferred from FAPSI to the Ministry of Education and Science. It continues to work on decision support systems and new technologies, including voice-recognition software. The FSB, according to contract data, is also interested in voice-recognition software. Given General Starovoytov’s intelligence background and writings on IO, TsITiS and InterEVM[103] may be covers for intelligence activities.
The FSO Academy,[104] shown in Figure 15-4, is in Orel. According to its website, the FSO Academy commissions new officers through a university-level program and does continuing training and research (which probably include signals intelligence training, long done in Orel). The five-year commissioning program leads to degrees in network technology, communications, information systems, information security in telecommunications, and law. According to Russian press, the FSO Academy commissioned more than 400 officers in 2009. The FSO Academy also trains FSB officers.
Minsvyaz is not considered a Russian power ministry because its portfolio covers unclassified public networks. Nevertheless, Minsvyaz—included on the Security Council’s Interdepartmental Committee on Information Security—works with law enforcement agencies and the security services to suppress political dissent on public networks. Its regulatory body, Roskomnadzor, is particularly useful because it can suppress dissent through administrative actions that carry less baggage than a security service visit.
Presidential Decree No. 724 in May 2008 established Minsvyaz’s current structure and responsibilities. Minsvyaz is responsible for developing and implementing government policy and regulations covering:
Information technology (including state information technology for public access)
Telecommunications (including the use of radio frequency spectrum) and postal services
Mass communications and media, including electronic media (Internet, television [including digital], radio broadcasting, and new technologies)
Publishing and printing
Processing of personal data
Minsvyaz exercises these responsibilities through several subordinate agencies:
- Federal Communications Agency (Rossvyaz)
Responsible for managing state property, providing public telecommunication and postal services, and developing communication networks, satellite communications systems, television broadcasting, and radio broadcasting.
- Federal Agency for Press and Mass Communications (Rospechat)
Responsible for providing public services and managing state property in print media and mass communications, including computer networks, electronic media, and publishing and printing.
- Federal Service for Supervision in Telecommunications, Information Technology and Mass Communications (Roskomnadzor)
Responsible for compliance and supervision of the media—including electronic, mass media, and information technology—and for processing of personal data and managing the radio frequency spectrum. See the next section, , for more information.
- Federal State Unitary Enterprise Scientific Technical Center (FGUP STC) Atlas
Responsible for developing and certifying information security and cryptographic technology for the government.[105]
- Federal State Unitary Enterprise (FGUP) Communication-Security
Responsible for information security of communication systems used by the government and others by contract.
- Federal State Unitary Enterprise (FGUP) Research Institute Sunrise
Responsible for system integration and development of major federal automated information systems, including systems for special applications.
Roskomnadzor issues licenses for telecommunications services, information technology services, and media operations. Roskomnadzor also monitors Russian media for compliance with the Federal Law On Mass Media. Roskomnadzor’s website (www.rsoc.ru) lists enforcement actions against media organizations. The majority of enforcement actions concern media violations of Article 4, which forbids media incitement or justification of terrorist activity. However, the prohibition includes a nebulous category of “other extremist materials.” Enforcement details show most Article 4 violations result from the media questioning government statements concerning terrorist events. Because Article 4 violations can lead to license revocation, Roskomnadzor can suppress political dissent through administrative action.
Roskomnadzor’s posted enforcement actions history is mainly directed against traditional print and broadcast media. However, amendments made in 2006 and 2007 extend the Federal Law On Mass Media’s reach to the Internet. Article 4 now covers “information in computer files and programs.” Article 24 defines any Internet site receiving one thousand visits as mass media subject to the law. The Russian press points out that this makes popular Internet forums and social media sites “mass media,” subjecting journalists to Roskomnadzor oversight. Article 49 requires journalists to verify information’s accuracy before publication, providing Roskomnadzor with additional ways to suppress Internet comment.[106] Indeed, Russian press states that Roskomnadzor let a contract in April 2011 for a system to monitor extremist content in online media.
Roskomnadzor efforts to control extremist Internet content is assisted by the public minded citizens of the Safe Internet League (Liga Bezopasnogo Interneta). Its symbol is shown in Figure 15-5.
A nonprofit partnership, the Safe Internet League was registered in mid-February 2011, with Igor Shchegolev, Minister of Communications and Mass Media, as Trustee Board Chairman. The League’s address is a box number at Minsvyaz’s Moscow headquarters. The Board of Trustees includes the head of the FSB Information Security Center, Mail.ru’s Chief Executive Officer (CEO), Roskomnadzor’s Director, the heads of the major Russian telecommunications companies, and other Russian Internet figures. The League’s membership includes:
- Rostelecom
Russia’s national telecommunications and Internet provider
- MTS
Telecommunication component of AFK Sistema
- Vimpelcom
Telecommunication provider
- Megaphone
Mobile telecommunication provider
- Mail.ru Group
Russia’s largest Internet company and social media host
- Kaspersky Labs
Russia’s largest Internet security company
- Axis-TD
Group of programmers and psychologists devoted to safe Internet
- Entensys
Russian Internet security company
- Internet Development Fund
Nonprofit supporting Internet development
- ROCIT
Russia’s oldest Internet industry organization
- Friendly Runet
Internet promotion organization
According to its website, the Safe Internet League is a voluntary association of citizens devoted to helping law enforcement organizations. Its volunteers monitor the Internet for violations, and report those violations to law enforcement. The site posts detailed information on the Ministry of Internal Affairs (MVD) Directorate K—the MVD component responsible for Internet crime—and provides a direct email link for reporting violations. In the league’s view, violations include child pornography, pornography accessible to children, promotion of drug and alcohol abuse, and violent or “extremist” content.
Despite the prominent role assigned to countering child pornography, the league’s actual focus is social media.[107] The league’s website awards its members ranks based on the social networking sites they identify that contain malicious content. Social networking sites are already heavily monitored for pornographic content; however, political comment runs rampant. Indeed, Russian press points out that the Safe Internet League’s creation coincides with the prominent role assigned to social media during the 2011 Arab Spring uprisings. In the press’ view, the league is actually an attempt to extend law enforcement’s monitoring to match social media’s expansion.
Ostensibly, the Safe Internet League is funded by the Saint Basil the Great Foundation (www.ruscharity.ru), which is headed by Konstantin Malofeyev. Mr. Malofeyev is also managing partner for the Russian private equity fund Marshall Capital Partners. Marshall Capital Partners’ major accomplishment is losing millions of dollars for Western private equity funds investing in Russia. In recognition, Mr. Malofeyev was appointed to Rostelecom’s board. When interviewed by Russian press, Mr. Malofeyev declined to name the ultimate funding source for the Safe Internet League.
The Safe Internet League is probably created and backed by Russian security services. The Russian Law On Operational Search Activities, NZ 144-03, details the methods available to Russian law enforcement and security services in “obtaining information about events or actions that threaten the state.” Article 6 states that search activities on technical communication channels “are carried out using the operational and technical capabilities of the Federal Security Service.” Article 15 states that bodies authorized to conduct search activities can establish “on a free or paid basis, collaborative relationships with persons who have agreed to assist the authorities on a confidential basis, carrying out operative-search activity.” In short, the MVD and FSB can back the Safe Internet League and remain entirely within the bounds of Russian law.
So far we have discussed only the top-line structure of Russia’s information security apparatus. Operating beneath is a robust network of technical centers, academic entities, and commercial companies—many spinoffs of state structures—working on information security. At the national level, Scientific Technical Center (STC) Atlas,[108] formerly subordinate to the FSB, maintains a network of facilities across the country with major development centers in St. Petersburg, Moscow, and Nizhniy Novgorod. The MOD’s Scientific Research Institute for Automation (NIIA) works on information security for strategic command and control. The FSB also maintains several Scientific Technical Centers focused on information security.
And then there are the unacknowledged components. The network of youth groups, institutes, and pseudo-NGOs that spawn bloggers and websites supporting the government and protecting Russia’s “spiritual life.” These are the people who can form cyber mobs and conduct DDoS attacks when needed, the ones who will fill Facebook and Twitter with pro-Putin pages and tweets.
[76] The unclassified Russian Military Doctrine is accompanied by classified annexes with implementation instructions. Russian government and Russian military personnel comment on the unclassified documents; however, references to the classified annexes are infrequent. Nevertheless, they led to changes in force structure and training that can be tracked.
[77] The Russian Federation Security Council operates as an operational staff both coordinating and implementing policy through a system of Interdepartmental Commissions. It exercises more authority than the US National Security Council (NSC), which is a policy coordination body.
[78] Career intelligence officer Colonel-General (Ret.) Vladislav Petrovich Sherstyuk has headed the Information Security Department since 1999. Sherstyuk started in the signals intelligence components of the Committee on State Security (KGB). He is a cryptologist by training.
[79] The doctrine’s threat definitions, especially technical threats, are similar to those found in US documents. However, there are differences. For example, the doctrine repeatedly defines threats posed by “disinformation” and “propaganda” that threaten citizens’ “spiritual life” and the Russian government’s ability to communicate with domestic and foreign audiences. Foreign ownership of networks and media is defined as a threat. Monopolies—whether foreign or domestic—controlling dissemination of information are defined as threats. The “unlawful use of special techniques influencing the individual, group, and social consciousness” is also perceived as a threat.
[80] For example, the operator could release the data to “protect the life, health and other vital interests of the personal data subject or others if you cannot obtain the written consent of the subject of personal data.”
[81] Frequently translated as FSTEK. However, they are the same organization.
[82] Under Russian law, even the Ministry of Defense uses cryptography that the FSB can monitor. The Federal Security Organization (FSO) provides presidential communications using FSB-approved cryptographic technology—however, the FSO maintains the keys.
[83] Depending on the translation source, this can also appear as the Federal Protection Service. They are the same organization.
[84] There is an unstated tension between the FSB and MOD on IO responsibility. Russian law assigns the FSB lead information security responsibility. The MOD, however, sees IO as a military responsibility. MOD and government structures related to IO are usually filled by former FSB/KGB officers. During the 2008 Russia-Georgia conflict, the MOD Press Officer was transferred from the FSB. It seems that the FSB is making sure MOD plans don’t hinder FSB prerogatives.
[85] Noncontact Wars was published in January 2000 while the Security Council was working on the new doctrine.
[86] Russian military commentators, including Ivanov, have speculated since 2005 that the EW Troops would become a separate combat arm. This had not occurred as of July 2011. Ivanov, whose last rank was Major-General, and who as a 2006 General Staff Academy Honors Graduate was seen as a rising star, was one of three General Staff officers who requested retirement in July 2011 for as-yet unspecified reasons.
[87] Dr. Horev’s web page also states he received an award from FSTEC in 2003 while serving in this position.
[88] Moscow Military University’s distinguished alumni include arms dealer Viktor Bout and “former” FSB officers Andrey Lugovoy and Dmitriy Kovtun, implicated in the Alexander Litvinenko assassination.
[89] FSTEC states that responsibilities include only “key” networks. However, the definition of key is broad enough to allow FSTEC to operate anywhere.
[90] The same postings normally list VAIU and VAIU predecessors under education.
[91] The English translation is approximate. The Cyrillic name is ФeдepaльHый гocyдapcTBeHHый HayчHo-иccлeдoBaTeльcкий иcпыTaTeльHый цeHTp paдиoэлeкTpoHHoй бopьбы и oцeHки эффeкTиBHocTи cHижeHия зaMeTHocTи (ФГHИИЦ РЭБ ОЭСЗ).
[92] It seems the ambiguity was designed to avoid drawing attention to the merger between VAIU and the 5th TSNIII.
[93] A former Vch 11135 employee is now a prominent Russian IT security expert who writes frequently on SCADA security. FSTEC documents show its role in SCADA security.
[94] The FSTEC list tries to obfuscate by listing the 18th CRI as the organization requesting certification and Vch 11135 as the testing laboratory. However, the Russian tax identification number is the same for both, showing that they are the same organization. In short, the 18th CRI is certifying itself.
[95] One Chechen site stated it traced attacks to the IP addresses registered to Vch 71330.
[96] The FSB, FSTEC, MOD, and the Russian Foreign Intelligence Service (SVR) are authorized to undertake projects involving state-secret information—including those involving information security systems—using licensed entities. The FSB and FSTEC publish lists of approved entities (the lists include government and private enterprises), with the FSTEC list covering work for the MOD.
[97] DST Global owns approximately 10 percent of Facebook.
[98] Syrian security services used Facebook to identify and detain activists during Syria’s internal disturbances. Russian security service capability is vastly greater.
[99] The Cyrillic name is frequently translated as Federal Protection Service. They are the same organization.
[100] The KGB 9th Directorate was complicit in the August 1991 coup attempt against Gorbachev. President Yeltsin sought to minimize future threats by creating a protection service subordinate only to the president. The name was officially changed to FSO in 1996.
[101] The FSO provides presidential communications during foreign trips.
[102] In short, the FSB certifies the cryptographic technology used by the FSO but cannot read traffic on FSO networks. The FSO, however, can read the traffic. The division of responsibilities is another legacy of KGB involvement in past coups. The 1993 film The Grey Wolves about the 1964 coup against Khrushchev is illustrative. The film, co-written by Krushchev’s son, strives for historical accuracy.
[103] InterEVM’s website (www.inevm.ru) states it is an international organization working on the development of advanced information and communication systems. According to Russian press, InterEVM attended a Cuban trade fair in 2009.
[104] The FSO Academy was founded as the KGB Military Technical School, transitioning from the KGB to the FAPSI to the FSO.
[105] FGUP STC Atlas was formerly subordinate to the Federal Security Service (FSB). The FSB has legislative responsibility for Russia’s overall information security, and it controls cryptographic technology. As a result, STC Atlas and the FSB continue a close relationship. STC Atlas also certifies foreign technology for Russian use.
[106] The Federal Law On Mass Media provides numerous ways for the creative mind to suppress dissent. Article 43 establishes a right of reply, allowing citizens to refute media allegations. Article 44 establishes the modalities for publishing refutations.
[107] Russian press interviewed the League’s financial backer Konstantin Malofeyev and pointed out that his business websites hosted erotic content.
[108] STC Atlas receives source code on Microsoft products from Microsoft for certification so Microsoft products.