![]()
Real-World Scenarios
Previous chapters provided a detailed introduction to the more than 1,500 Microsoft Azure services, in order to give you a good foundation in Azure’s capabilities. To complete this first part of the book, this chapter examines some real-world scenarios in which Azure is being used, although the customers and organizations remain anonymous.
The goal of this chapter is to tie Azure’s capabilities together in order to solve business problems. This sets the stage for the next part of the book, which dives into these selected Azure services in detail. The scenarios discussed here are designed to help you visualize how Azure can help you to meet similar business needs in your organization.
At the time of writing, these are some of the common workloads being deployed in Azure:
- Identity management and authentication
- Rich content storage and processing, specifically audio and video files
- Testing and development environment
Identity Management and Authentication
Microsoft Active Directory (AD) is the long-standing identity management (IDM) platform for Microsoft Windows servers and networks. It is a mature technology that has been in use for nearly two decades. There are many AD roles, such as Active Directory Domain Services (AD DS), Active Directory Federation Services (AD FS), Active Directory Lightweight Domain Services (AD LDS), and Active Directory Certificate Services (AD CS). There are also AD tools and dependencies, such as Microsoft Identity Manager (MIM), AD Domain Name Services (AD DNS), and so on. Collectively, these technologies provide for management of identities, networked resources, locations, and access to applications and services.
In the scenario addressed here, the specific AD capability you examine is authentication. This is important because without the ability to authenticate, users can’t access resources on the corporate network. Without the proper trusts in place, users may be overwhelmed by the incessant need for redundant authentication as they traverse from one service to another.
Business Drivers: Building a Claims-Based Authentication Infrastructure
Because software as a service (SaaS) is provisioned from external networks and datacenters that are not part of the corporate IT environment, they need to be integrated with AD in order for the customer not to have to re-authenticate to the SaaS if they have already been authenticated by AD. You can do this by using claims-based authentication capabilities such as AD FS, which provides a single sign-on (SSO) experience for users. Furthermore, organizations do not want to trade the benefits of SaaS for the burden of managing multiple IDM systems, which increases cost and risks.
Building an AD FS infrastructure, or adopting a third-party solution to provide claims-based authentication and using traditional AD, is already a mature approach. However, one of the benefits of SaaS solutions like Office 365 is the service-level agreement (SLA) that provides guaranteed availability and uptime beyond the reach of most organizations. Relying on on-premises authentication availability means the SLA for the SaaS can be only as good as the availability of the claims-based authentication infrastructure.
Organizations that have deployed Office 365 with SSO have occasionally discovered that an outage with AD FS hosted on-premises resulted in users being unable to log in to Office 365. And in setting up AD FS for the first time, some organizations realize that they lack the necessary claims-based authentication infrastructure and must acquire additional hardware.
Solution Description
Building or moving a claims-based authentication infrastructure such as AD FS from on-premises datacenters to Azure improves the SLA for SaaS solutions. This assumes that Azure’s SLA provides higher availability than the on-premises SLA, which is often the case. In addition to higher availability, the claims-based authentication infrastructure benefits from better georedundancy, and therefore it meets or exceeds many disaster-recovery (DR) requirements.
For organizations that are considering acquiring new hardware in order to implement AD FS or a third-party claims-based authentication infrastructure, alternatively building the environment up in Azure enables these organizations to avoid hardware acquisition and future hardware-refresh cycles. Building a georedundant and highly available claims-based architecture using this approach uses the Azure infrastructure as a service (IaaS) offering.
In addition to IaaS, Azure offers identity as a service (IDaaS) in the form of Azure Active Directory (AAD), which provides claims-based authentication to Office 365 and other SaaS solutions. AAD allows organizations to manage users in AD, and it creates such users in SaaS if needed. Therefore, you no longer need to manage users manually in a fragmented SaaS environment where each SaaS may require its own IDM.
Solution Reference
Chapter 11, “Clusters, Regional VNets, High Availability, and Disaster Recovery,” provides detailed information about Azure IaaS to assist you in building a high-availability, georedundant AD FS infrastructure. Detailed information about AAD as an IDaaS extension for AD is covered in Chapter 10, “Extending Azure Active Directory.”
Rich Content Storage and Processing
Rich content refers to video, audio, and high-quality graphic files. Generally, these types of files differ from documents because they can consume large amounts of network bandwidth, storage space, or both.
Business Drivers: Body-Worn Video Cameras
At the time of this writing, one rich content real-world scenario is the trend to require police officers to wear body-worn video cameras in order to make law-enforcement activities more transparent. Body-worn video cameras create a new source for content that needs to be stored, processed, and viewed on different types of devices.
Organizations that have to store audio and video files may find it difficult to estimate the amount of content that will be generated and thus the amount of storage space required. In this scenario, the audio and video content generated may vary based on the volume and frequency of incidents, and thus the storage needs are difficult to predict. Furthermore, once content is created, there is a potential need to convert it into other compatible formats for playback purposes, and the level of effort required to convert content may be significant.
Solution Description
Azure provides two types of services with respect to audio and video files:
- A scalable, elastic, and redundant storage medium
- Processing and streaming of audio and video content
At the minimum and most simplistic level, Azure as a scalable and elastic storage medium is very well suited for unpredictable workloads. Azure’s default locally redundant storage (LRS) provides a level of redundancy that meets or exceeds many organizations’ requirements. Alternatively, if more redundancy is required, organizations can elect to use geographically redundant storage (GRS).
Once the audio and video content is stored in Azure, you can use additional value-added capabilities. This takes the form of Azure Media Services. Azure Media Services is a set of video-processing and analyzing capabilities that includes
- Conversion of videos into streaming formats for ease of consumption
- Speech-to-text transcription, known as the Indexing Service
Figure 3-1 shows all the supported streaming formats into which Azure Media Services can convert an audio/video file.
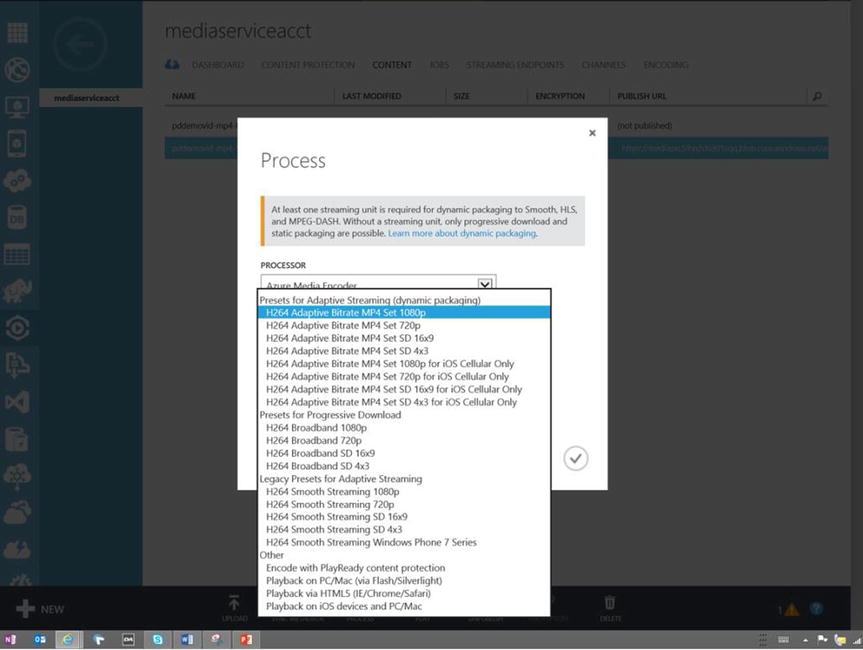
Figure 3-1. Streamable formats to which Azure Media Services can convert a media file
When the Indexing Service processes a video, an XML-based file, also known as a text transcription markup language (TTML) file, is created. Figure 3-2 shows a TTML file created by the Indexing Service. Notice that the first and second columns are the start and stop times of the transcribed speech.
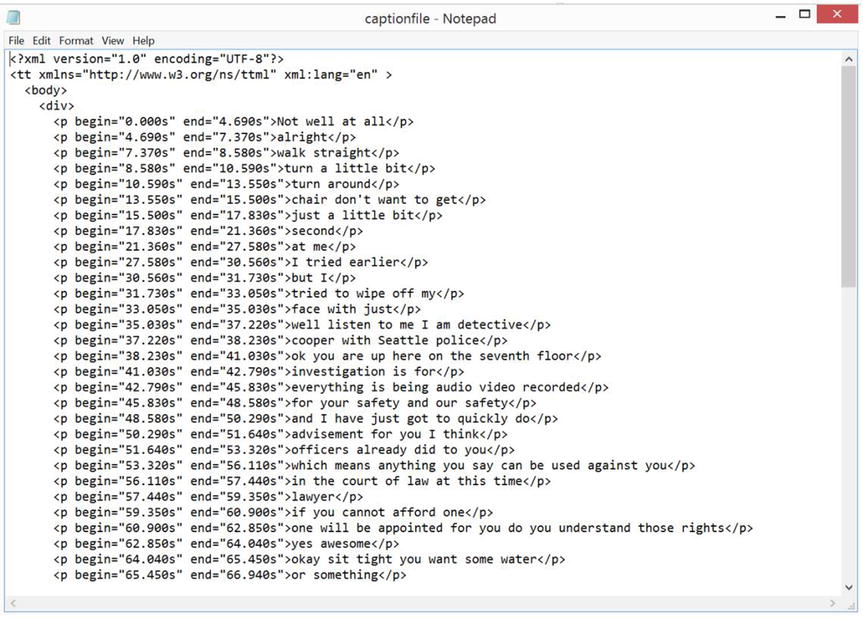
Figure 3-2. TTML file created by the Indexing Service
In this case, the TTML file can be used for captioning in order to meet American Disabilities Act (ADA) requirements for the hearing impaired or to search in the audio or video file, because the start and end times of the transcribed text are also produced in the TTML. Figure 3-3 shows a simple HTML 5 player that uses the TTML file along with the associated video file.
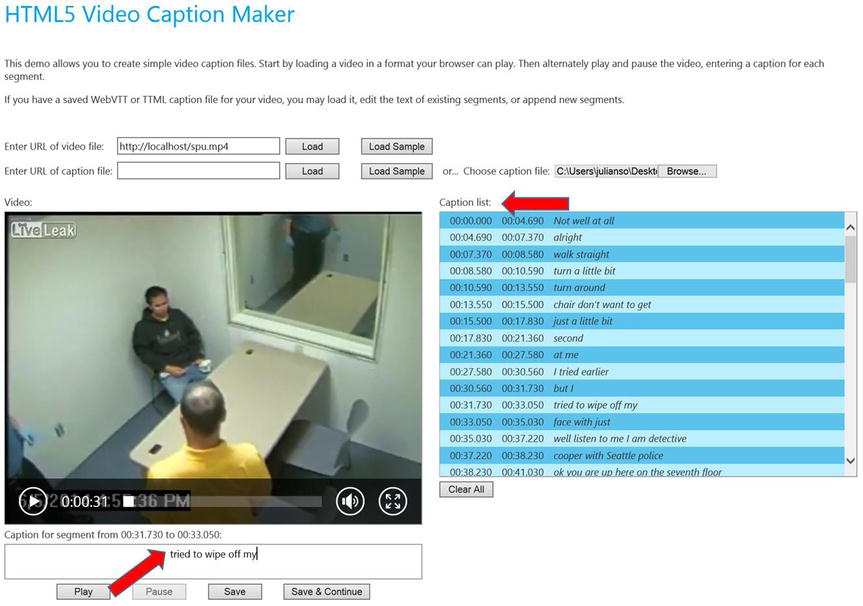
Figure 3-3. HTML 5 video player with caption file
![]() Note You can see the HTML 5 player used in the example in Figure 3-3 and other standards at http://dev.modern.ie/testdrive.
Note You can see the HTML 5 player used in the example in Figure 3-3 and other standards at http://dev.modern.ie/testdrive.
Microsoft Azure datacenters in Canada are now available to support the greater security requirements for video and other workloads for the Canadian Government and Canadian citizens. You can read more about Azure in Canada at the Microsoft Blog: http://blogs.msdn.com/b/make_it_better/archive/2015/06/02/microsoft-azure-canada-datacenters-yay.aspx.
Solution Reference
Azure Storage is covered in detail in Chapter 7, “Understanding Azure Storage and Databases.” You can find more information about Azure Media Services at http://azure.microsoft.com/en-us/services/media-services.
Creating a Preproduction Sandbox
Any organization that undertakes custom in-house software development provisions its architecture for development and testing purposes. Even if no custom in-house software development activities are involved, it is not uncommon for organizations to have a testing environment to check configuration changes to commercial off-the-shelf software (COTS) prior to implementing the changes in the production environment.
Business Drivers: Creating a Testing and Development Architecture
Building a testing and development architecture requires the acquisition and maintenance of hardware. Sometimes the testing and development environments are separate. When added to the production environment, this translates to three separate environments that an organization must manage and maintain. Whenever there is a hardware upgrade in the production environment, the old production environment may trickle down into the testing and development environments.
Nonetheless, there may be instances when the hardware in the testing and/or development environments needs to be kept up-to-date along with the production environment. If such a need exists, then the testing and development environments must go through an upgrade whenever the production environment is upgraded. Most organizations try to keep the testing environment identical to the production environment; the only difference between the two is that the production environment may have greater redundancy and be larger in scale.
The primary business driver when there is a need to maintain testing and development environments is the cost of acquiring and maintaining hardware in the two or three separate environments.
In addition to the cost of maintaining hardware in two or three separate environments, there is also the challenge of agility and scalability. Agility describes the ability to provision hardware quickly for the testing and development environments. Scalability describes the ability to add more hardware in order to expand the testing and development environments.
The traditional approach to acquiring hardware usually takes a lot of time, and thus it is not an agile or cost-effective method. Furthermore, if hardware is acquired in order to scale out a testing or development environment, it is a permanent action. Unless an organization is leasing or can return the hardware, it is usually not easy to scale back down if the need for the larger environment is temporary and no longer required.
Solution Description
Using Azure Virtual Machines and Virtual Networks for testing and development purposes is one of the most popular reasons for adopting IaaS:
- Organizations new to IaaS feel more comfortable experimenting with the cloud in their testing and development environments because these are usually less mission-critical.
- The flexibility to scale up and down quickly in Azure, which is based on consumption, provides a compelling cost model.
- Each Microsoft Developer Network (MSDN) subscription comes with a monthly Azure allowance. This is ideal for developers who need to have an environment with servers for development projects.
Solution Reference
Using and migrating to Azure Virtual Machines is covered in detail in Chapter 6, “Getting Started with Azure Virtual Machines,” Chapter 11, “Clusters, Regional VNets, High Availability, and Disaster Recovery,” and Chapter 12, “Migrating Your Virtual Machines to Azure.” For more information about using MSDN with Azure, visit http://msdn.microsoft.com.
Small and Mid-Sized Businesses
According to the US government, businesses with fewer than 250 employees fall into the small business category; medium-sized businesses have fewer than 500 total employees. Small and mid-sized businesses (SMB) focus on providing goods and services for their “niche markets,” which many big corporations are not willing to supply. These businesses may struggle to ensure that they achieve sufficient sales, more than break-even, and possibly have a greater profit. Even if the yearly sales and number of employees are less than those of a “big box” store, many SMB owners are faced with IT challenges similar to those of the larger corporations.
The almost-daily IT challenges faced by SMB organizations are just as critical to the longevity of the business as those of larger organizations, even though the business owners may not have a budget to support one or more IT staff employees.
Business Driver: We’re Not in the Datacenter Business
One example is a local real estate services team that has very little invested in datacenter infrastructure. Employees are mobile with phones and laptops, and the few servers the company uses an email from their local service provider ([email protected]) needs are located in an office closet and under the desks of office workers. With more than one office, there are servers in each office storing all the customer data, property listings, contracts, and payroll information. Microsoft Azure provides the necessary infrastructure for businesses including:
- High Speed TCP/IP Networking
- Virtual Machines on demand
- Email as a service (Office 365)
- Cross Collaboration as a service (SharePoint)
For email communication, the company previously used an email service provided by a local Internet service provider (ISP), but it recently moved to Microsoft Office 365 to share documents with OneDrive. The company can now view sales employee calendars to confirm appointment times.
Another example is a small printing company that produces customized notecard stock used by amateur photographers. The company has grown over the years to include products like display stands, plastic sleeves, and personalized stamps for customers. This company has two major storefront locations in the United States: one in Denver, Colorado and one in Portland, Oregon. Each location has servers tucked away in corners of the rented storefronts, and the company use leased network lines from the phone company to link the two locations together to share business data. In the Portland location, a web server provides Internet sales and marketing services for the store. It is consistently unresponsive due to either network traffic or power issues in the building. Data on the servers includes sales transactions, employee information, product inventory, and raw materials used to build the notecard stock.
Both of these companies focus on sales, products, and employees, but not on IT infrastructure. They may never have prepared for the effects of a natural disaster or a catastrophe created by a disgruntled employee. They don’t have the funding to invest in building out the necessary data networks, purchasing servers for redundancy, and implementing a disaster recovery (DR) plan—they simply back up servers to tape. They both use Microsoft Hyper-V server for virtualization because it is included as a server role in the Windows Server operating system. The business owners may have contacted a local ISP to rent space in their colocation facility, but the long-term contract and high up-front cost were not in their budgets.
Many SMB owners know they should invest in core business IT infrastructure, but they lack the in-house expertise and up-front funding needed to purchase redundant servers for their business. Small Businesses need to improve disaster preparedness, server redundancy, and application-recovery systems.
Businesses need to perform datacenter-level recovery for critical business workloads in the event of a server failure. Backups need to be automated and easily managed so that they remain in order without manual intervention.
DR plans need to be created in case a natural disaster or manmade disaster destroys critical server operations at any location. The need to perform multi-tier application and individual server-level recovery of critical workloads should be part of the DR plan.
Both of the example businesses need to minimize capital and operational expenses. They should consider reducing the number of aging existing on-premises servers by using Azure Virtual Machine services and move other applications, such as web servers, into a robust environment that expands automatically based on customer traffic.
The nature of sensitive data, including customer data, partner data, and payroll information, and the security and privacy of their infrastructure is critical. Data is highly sensitive and competitive in nature for each business.
Both business examples are cost conservative in terms of the overall solution, but they want to create a process that is automated and provides redundant services, quick testing, and validation for recovery plans.
Solution Description
The Azure pay-as-you-go model can help these two example businesses invest in IT by taking advantage of services as commodities. Azure provides two key areas for companies to use for business strategies when it comes to daily backups and DR preparedness—Azure Site Recovery and Azure Backup:
- Azure Site Recovery with Azure as a DR site
- Planned, unplanned, test failover, and failback on the servers, application, and data with Microsoft System Center VMM
- Azure Backup agent installed for all on-premises Windows servers
- Restore of both physical servers and virtual servers without relying on offline tape storage
- Site-to-site VPN between the servers in the offices or datacenter to the Azure virtual network
Azure Site Recovery with a recovery site in Azure offers the ability to perform planned and unplanned recovery and testing with minimal disruption to production. It provides orchestration and failover and failback processes to support the applications starting in the correct order.
Security is a priority for Azure, and many processes have been put in place in support of the many security-compliance requirements, such as PCI, HIPAA, FedRAMP, and ISO 27001 to name just a few:
- Data replicated to Azure as part of Azure Site Recovery is encrypted during transit, and businesses have the option to enable encryption at rest.
- VPN hardware is not an expense, because an SMB may look at enabling Microsoft Server RRAS, which is included in the server OS.
- Azure supports SMB virtual servers to be copied up to Azure, providing connectivity so that local aging server hardware is never an issue.
Applications running in Azure provide additional benefits that address redundancy, auto-scaling, and cost factors:
- Web sites running in Azure provide auto-scale-out based on performance metrics, and they auto-scale-down when no longer needed.
- Applications, VMs, and other servers are locally redundant in Azure, and businesses with critical applications have options to enable georedundancy to another Azure datacenter.
Figure 3-4 shows the network connectivity required to support Azure Site Recovery for mid-sized companies and Azure Backup for small or medium-sized businesses that require DR options.

Figure 3-4. Azure Site Recovery and Azure Backup diagram
Solution Reference
Exercises covering the Azure services described in these real-world examples are provided in Chapter 5, “Getting Started with Azure Web Apps,” Chapter 6, “Getting Stared with Azure Virtual Machines,” Chapter 8, “Extending Your Network with Azure,” and Chapter 11, “Clusters, Regional VNets, High Availability, and Disaster Recovery.” Additionally, you can find the step-by-step deployment processes for VPN devices and Windows Server 2012R2 RRAS on the MSDN network, with detailed guidance at http://msdn.microsoft.com/en-us/library/azure/jj156075.aspx.
Large Business, Corporations, and Government Agencies
Multinational corporations and government agencies with locations both in the United States and across Europe have a global reach and are supported by large IT departments. Often, very large organizations have teams of IT personal who specialize either in given functions or in separate areas, such as networking, operating systems, applications, monitoring, and security.
One of the major IT challenges for large corporations is a global mobile workforce. A robust communications infrastructure and secure network connectivity into the corporate network are always at the forefront of any change in architecture. Mobile users who are based all over the world also have home offices. They take their work home with them and on the road. These users often have more than one mobile device, and most have residents across the country, not in the region in which they work, live, and support local businesses.
Corporations often host systems at colocation facilities in different world geographies, and the business model often requires all IT operations to have specific security compliance. In the United Sates, companies are continuously providing resources to achieve SOC1, SOC2, PCI, and other compliance to protect both intellectual property (PI) and personally identifiable information (PII) data.
As government agencies and large corporations grow both in the United States and Europe, there is a need to scale, automate, and simplify IT management. As these large organizations move to Azure, they focus on associated IT spending, minimizing cost, greater utilization of flexible resources, and reducing up-front capital expenditures. Moreover, every corporation is singularly focused on IT and network security.
Business Driver: Grow the Business, Scale Out Infrastructure, Reduce IT Budgets, and Maintain Security
Large corporations may have 15,000 to 50,000 or more employees on multiple continents. The products and services they sell vary based on their business and customer base. As the companies continue to grow, both the business divisions themselves and IT require the ability to scale up quickly as different system loads increase and to reduce spending based on customer activity.
Division and department managers are challenged to deliver contained hosting and operational costs for both IT and business facilities. With so many employee devices, there is a need to isolate corporate systems from Internet-facing systems. As the demand for laptops, tablets, and mobile phones increases, corporate access requires continued support for virtual private network (VPN) access.
As IT networks expand into different states, regions, and countries, best practices are used to simplify the duplication of successful processes and to maintain current security compliances. However, in countries across Europe and Asia, different security compliance requirements need to be put in place and processes designed to address the security statutes of the particular country. New datacenter locations require different security configurations and more IT auditing to provide services for customers and employees in those locations.
The EU’s Article 29 Working Party for contractual commitments is part of the EU’s Standard Contractual Clauses to protect all data for EU countries. Japan requires IT datacenters to maintain standards for financial industry information systems (FISC) for banking, computer systems, information system audits, contingency planning, and security policy development.
Businesses expanding into Australia require digital data storage to be certified by the Australian Signals Directorate (ASD) for the processing of “unclassified” data. The Ministry of Public Security in China requires auditing compliance with a multi-level protection scheme (MPLS) for data pertaining to Chinese businesses or citizens. In addition, businesses in China are required to maintain the Trusted Cloud Service certification developed by the China Cloud Computing Promotion and Policy Forum (CCCPPF).
Corporations expanding datacenters into the United Kingdom are required to achieve and maintain the UK Government G-Cloud certification. Meanwhile, back in the United States, any company that provides products or services to federal or local law enforcement agencies accessing the FBI’s Criminal Justice Information Services (CJIS) database must adhere to the Criminal Justice Information Services (CJIS) Security Policy.
Azure maintains rigorous third-party audits to enable Azure services to meet a very broad set of international and industry-specific compliance standards, so corporations may quickly and globally extend IT services globally using an Azure tenant, all with a simple mouse click.
Large corporations expanding into new markets and foreign countries have evaluated the business drivers for their corporate growth. Extending the business IT network and datacenter presence requires extensive planning and focused attention on the compliance and privacy requirements of each nation.
Datacenter colocations and expanding into existing buildings for new IT network connectivity may not be ideal because of specific datacenter needs, such as structural integrity to maintain the weight of racks of servers; uninterruptible power distribution units (PDU), which channel electricity to power the servers; and the need for physical security. In the event of a power outage at large organizations, the datacenter requires additional facilities storage for fixed-position backup batteries in order to maintain power to the servers while the diesel backup generators start up, reach capacity, and then enable electricity network failover.
Other global businesses may decide to build a new datacenter, which could involve a very lengthy time period for construction that impedes the business from growing quickly. New building construction requires the purchase of land for the datacenter, with a variable cost per square foot for the new building based on the country’s available land. Other considerations include local construction company experts for datacenters—not just any residential builder or commercial builder is qualified to build a datacenter. Some countries require a percentage of the workers to be local citizens, so bringing in a complete seasoned construction crew on visas may not be permitted.
As the construction of the datacenter approaches a finished and usable facility, additional key support structures are needed, such as large humidifiers and separate air-conditioning units for maintaining constant cooling required for the server hardware to run optimally. Businesses are required to limit physical access to these facilities based on full-time employees and contractors who have validated security background checks, in order to adhere to the specific country’s security compliance requirements. Only after the miles of copper or fiber network are in place, servers are racked and stacked, and the operating systems and applications are installed can the IT auditing process begin.
Solution Description
Large global corporations are moving their workloads to Azure in order to expand into new business markets quickly, because all compliance with privacy laws in the US, UK, EU, and Asia are satisfied by Azure. US corporations migrate their business services to Azure Virtual Machines (VMs) using a topology that secures data at rest and in transit. In addition, note the following:
- The corporate IT deployment experience is unchanged by implementing independent Azure VMs, enabling migration directly in a process called lift and shift.
- VMs in Azure have firewall rules allowing specific TCP connections and TLS needs to be configured using the appropriate security certificates installed for web sites.
- Azure web sites can be enabled to host external data collection, whereas internal web sites are enabled with the most recent release of the corporate web application. The internal web sites are configured with a network security group to prevent external traffic.
- Company web applications used to access data should use Active Directory domain credentials so that passwords are not stored in web configuration files on the application servers.
- Corporate web sites are restricted to traffic in the virtual network, and no public endpoint is exposed to the Internet.
- Access to public websites listening for Transport Layer Security (TLS) connections on port 443 can be directly supported by Azure load balancers.
Communications are secured from the corporation’s current on-premises datacenter by enabling a VPN that is configured for site-to-site connections. As with local datacenter networks, similar configurations are used:
- Azure virtual networks (VNets) use industry standard Internet Protocol Security (IPsec) to secure all communication traffic between a corporate VPN gateway and Azure.
- Application tiers of service can be separated by networking subnets.
- Web front-end VMs can be placed in one subnetwork and the database back-end VMs can be placed in a different subnetwork.
- Multiple networks enable security boundaries that can be further enhanced with firewalls and intrusion-detection systems used to spot suspicious traffic.
Customers new to Azure are often surprised at the number of infrastructure-automation conveniences built into the Azure services:
- VMs created using the Azure portal wizard provide a step to enable anti-malware extensions for Microsoft, Symantec, and Trend Micro.
- Anti-malware extensions include antivirus, anti-malware, firewalls, and intrusion detection.
- Additional security features may be enabled by third-party services, such as data encrypting using SecureVM by CloudLink.
Additional benefits for customers using Azure are included with all the Azure subscriptions and tenant access. Customers that need to scale up or scale out IT network services can take advantage of the following:
- The Azure VM auto-scale feature is based on a number of different metrics such as CPU utilization, network connectivity, and so on.
- PowerShell automation is supported through the Azure Portal.
- End-to-end compliance is achieved by using Azure in addition to the current corporate IT compliance processes and procedures.
- Azure regional datacenters support data sovereignty by maintaining sensitive data in the network boundaries of the corporation. They only exchange data with third-party counters that meet the data-protection requirements of the country of origin.
- Microsoft does not transfer customer data outside of the geography of the customer’s network enablement, with the exception of providing customer support, troubleshooting issues, and complying with legal requirements.
- Corporations have complete control over their data and their customer’s data in specific geographic areas and regions supported by the Microsoft datacenters.
- The Azure platform undergoes rigorous regular auditing to maintain and support new compliance requirements for different industries.
- Validations for US businesses include government (FISMA and FedRAMP), financial services (SCO1, SCO2, PCI, and DSS), healthcare (HIPAA), and many more.
The reference example, shown in in Figure 3-5, provides high-level considerations for security that separates public properties from back-end corporate VMs and services. Figure 3-5 shows the network overview and one of the possible ways to increase security with parameter fencing using more than one network security group (NSG).
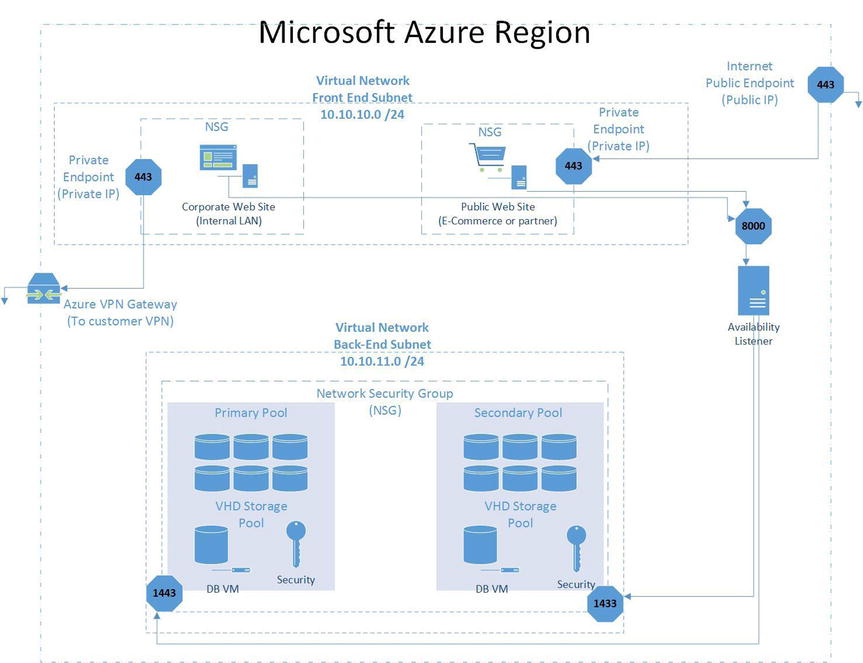
Figure 3-5. Azure security separates front-end and back-end IP subnets
Solution Reference
This book provides many examples that are directly applicable to creating network boundaries in large corporations in the step-by-step exercises covering Azure services. Detailed information and guidance can be found in Chapter 5, “Getting Started with Azure Web Apps,” Chapter 6, “Getting Started with Azure Virtual Machines,” Chapter 7, “Understanding Azure Storage and Databases,” and Chapter 8, “Extending Your Network with Azure.” If you have additional questions regarding current Azure compliance standards, visit the Azure Trust Center at http://azure.microsoft.com/en-us/support/trust-center/compliance.
Summary
This chapter described several real-world scenarios of how Azure is used. It also provides a foundation through several examples of customer scenarios for your consideration. Guidance to the relevant chapter exercises is provided at the end of each example.
The next chapter builds on the information you’ve learned in the previous chapters. Chapter 4 ends Part 1, “Introducing Azure.” Part 2, “Microsoft Azure Quick Start,” provides you with hands-on exercises that let you start using some of the major Azure workloads, including web sites, VMs, and storage.
