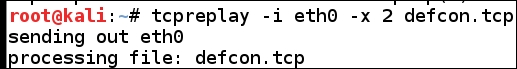
Once you have built and attacked the range, it is highly recommended that you record the attacks so that you can use them to practice with and, more importantly, for training purposes. Each time you carry out attacks, you are creating extremely valuable data that should be captured and used again. One of the easiest ways to capture the data is to use Wireshark. Once you have captured the data, save it, and then you can use a tool to replay the captured traffic. There are a number of ways in which you can accomplish this. One of the easiest ways is to use the tcpreplay tool; it is part of the Kali Linux distribution. Additionally, there are a number of packet traces you can download that cover many different attacks if you prefer to not create your own. An example of the command used to replay the file from one of the earlier DEFCON conferences is shown in the following screenshot:
For those of you who want to use a GUI tool, there are a number of them to choose from. A free one that works very well is Colasoft Packet Player from Colasoft; you can download it from http://www.colasoft.com.
An example of this tool being used to replay the DEFCON packet capture is shown in the following screenshot:
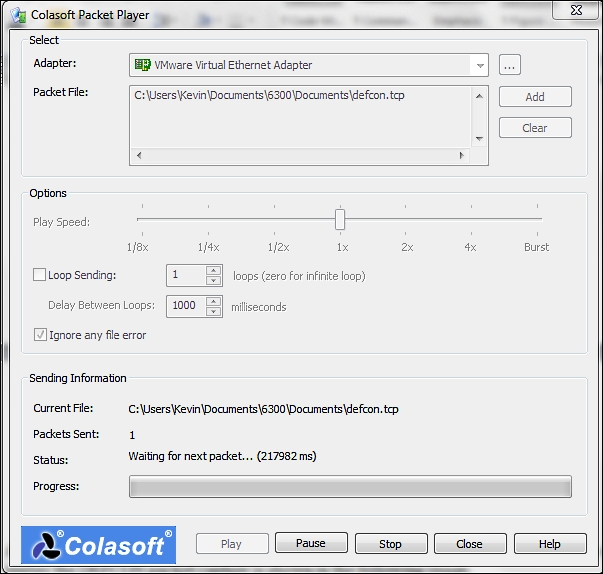
As the previous screenshot shows, you can set a number of different playback speeds, and in the Burst mode, the playback will be as fast as the network card can handle.
