![]()
While APEX offers a number of controls to limit user access to its components, it offers few components to protect the data itself. That may seem like a shortcoming on the surface, but it is not. Protecting data at the application layer can be potentially short-sighted because it protects only that single avenue to the data. If developers spent all of their time building in controls to their APEX application to restrict what users could see, then users could circumvent those controls by accessing the data via another application or directly.
Thus, data is best secured at the database layer, not within the application. Oracle provides a couple of features to assist with this task: Oracle Virtual Private Database and Oracle Label Security. Both of these tools require the Enterprise Edition of the Oracle Database, and Oracle Label Security is a for-cost option. Fortunately, if you’re running Oracle Standard Edition One or Standard Edition, you can still secure your data at the database layer using nothing more than a smartly designed view.
This chapter will outline the benefits of using such views as a layer of security in your APEX and other Oracle applications. It will illustrate some techniques for where and how to use secured views and their associated components. It concludes with a summary of the benefits and potential drawbacks to using this approach.
In general, most Oracle developers are quite familiar with views. Views are very powerful and are often an underappreciated and underused construct in any database. They allow developers to mask the complexity of a sophisticated SQL statement in a much easier-to-use format. Additionally, they can obfuscate columns or data that should not be seen by specific applications. If the definition of the view needs to change, it can do so without any application code changes in many cases, thus making applications easier to manage over the course of their lifetime.
All of the traditional benefits of views are good for nothing if they don’t get used in APEX applications. And chances are, most APEX applications are built to interact directly with tables and make little, if any, use of views at all.
The use of views in your application should be something that is considered during the design phase. Designing an application based on views from the ground up is a lot faster than trying to retrofit an existing application with views. Like most facets of application development, a little bit of planning will go a long way.
Using a view in APEX is quite simple. Simply create the view in the same schema that the APEX application parses as and then reference that view in a report, form, chart, and so on, just as if it was a table. That’s all there is to it! Take, for example, the view in Listing 11-1.
Listing 11-1. SQL to Create a simple Simple view View on the EMP tableTable
CREATE OR REPLACE VIEW emp_v
AS
SELECT
empno,
ename,
job,
deptno
FROM
emp
/
This simple view will return the EMPNO, ENAME, JOB, and DEPTNO columns from all the rows from the EMP table. To use this view when creating a component in APEX, simply select from EMP_V instead of EMP, and your component will be based on the rows and columns referenced in the view. If business conditions dictated a change in how this view were constructed, the definition of the view could be rewritten, and little to no code changes in the application would be required.
If a simple APEX application were created using the EMP_V view, the results would look similar to Figure 11-1.

Figure 11-1 . A simple APEX report based on EMP_V
Secure View Components
A secure view is not an actual database object or APEX component type but rather a term used to describe the techniques of using a view to provide data security for an application. Secure views provide both the traditional benefits of views combined with an added layer of both data security and functionality that can be used in any application – APEX or otherwise.
In the following example, you will create a secure view based on the EMP table that restricts users from seeing records from other departments. When you build the APEX report on top of this view, you will pay little to no attention to data security there because it will all be addressed via the secure view. Not only does this decrease the time it takes to develop applications, but it also makes them a lot easier to manage over time because of their minimalistic design and sparse use of sophisticated SQL queries.
Because secure views are not an actual object type, there are a few components that need to be in place before they will actually work. Secure views rely on application contexts to act as the filter in their predicate. Application contexts are the most efficient and effective way to create a secure view, because their values are stored in memory and take almost no measurable time to reference.
The values of application contexts can be set only by a specific PL/SQL procedure, so you will have to create one of them. And since application contexts are based on database sessions, not APEX sessions, you need to augment your APEX application with some PL/SQL code to call both before and after a page is rendered.
Application Contexts
An application contextis a database object type that simply stores name-value pairs in memory. Setting the values of an application context is controlled by a specific procedure, not by the user. Furthermore, the values stored in an application context can be modified or removed only by this same procedure.
In APEX, application items are also components that can store a value that can be referenced throughout the APEX session. Application items can be configured to either allow or prohibit users from directly making changes to their values. Application contexts work in a similar fashion but are applied to a database session, not an APEX session.
To create an application context, a database user needs to have the CREATE ANY CONTEXT system privilege. Alternatively, an alternate schema with DBA privileges and the CREATE ANY CONTEXT system privilege can create a context that references a procedure from any schema. Listing 11-2 outlines the SQL required to create a simple application context that is secured by a procedure called SET_CTX that is owned by SCOTT
Listing 11-2. SQL Used to Create an Application Context
CREATE CONTEXT emp_ctx USING SCOTT.emp_ctx_pkg;
It is important to note that when an application context is created, there is no verification as to whether the associated procedure used to secure it exists. Thus, the order in which you create the application and corresponding procedure does not matter.
PL/SQL Procedure
The PL/SQL package referenced in Listing 11-2 needs to be created next. The purpose of this package is to set and unset a value or set of values associated with the EMP_CTX application context. The methods or business rules used to set these values are up to the developer and will be vastly different from application to application. Despite this, they will all reference the same API used to set the application context values: DBMS_SESSION.SET_CONTEXT.
As outlined in Listing 11-3, the SET_CTX procedure simply looks up the department number of the currently logged in user. It then uses that value to set the DEPTNO attribute of the EMP_CTX application context. This value will be used later in the actual SQL of the secure view. The UNSET_CTX procedure clears all values of the context so that they do not get inadvertently reused by another APEX session.
Listing 11-3. The Procedure SET_CTX, Which Is Used by the EMP_CTX Application Context
CREATE OR REPLACE PACKAGE emp_ctx_pkg
AS
PROCEDURE set_ctx
(
p_user_name IN VARCHAR2
);
PROCEDURE unset_ctx;
END emp_ctx_pkg;
/
CREATE OR REPLACE PACKAGE BODY emp_ctx_pkg
AS
PROCEDURE set_ctx
(
p_user_name IN VARCHAR2
)
IS
l_deptno NUMBER;
BEGIN
-- Fetch the DEPTNO based on the currently signed on APP_USER
SELECT deptno INTO l_deptno FROM emp
WHERE ename = p_user_name;
-- Set the Context
dbms_session.set_context(
namespace => 'EMP_CTX',
attribute => 'DEPTNO',
value => l_deptno);
EXCEPTION
WHEN no_data_found THEN
-- If no data is found, then clear the context
dbms_session.clear_context('EMP_CTX'),
END set_ctx;
PROCEDURE unset_ctx
IS
BEGIN
-- Clear the context
dbms_session.clear_context('EMP_CTX'),
END unset_ctx;
END emp_ctx_pkg;
/
Secure View SQL
Now that you have your application context and associated PL/SQL package in place, you can re-create the EMP_V view with a reference to the application context. The SYS_CONTEXT procedure is provided by Oracle to return the value of an application context namespace and parameter. It can be used in the predicate of a SQL statement in the same manner as a bind variable or literal can be.
Listing 11-4 outlines the updated EMP_V SQL. There is only one difference between this version and the one used in Listing 11-1: the WHERE clause in this version is used and refers to the application context. The rest of the SQL is identical between the two versions.
Listing 11-4. SQL for the EMP_V Using the SYS_CONTEXT Procedure
CREATE OR REPLACE VIEW emp_v AS
SELECT
empno,
ename,
job,
deptno
FROM
emp
WHERE
deptno = SYS_CONTEXT('EMP_CTX', 'DEPTNO')
/
Back in the APEX application, if you were to rerun your report, you would get the results illustrated in Figure 11-2.
Figure 11-2 . Results of the updated version of EMP_V
The reason that no records are returned is that the application context has not been properly set for the APEX application. Remember, the only way to set the value of an application context is to call the procedure that was associated with it when it was created. Since no such call to that procedure has been made, the value of the application context is not set, and thus the report does not return any records.
Setting, as well as unsetting, the application context is a critical step in creating a secure view. Setting an application context is as simple as calling the procedure associated with it. In a stateful environment, such as SQL*Plus, the context can be set one time and remain set for the duration of that session. Since APEX sessions are stateless and distinct from database sessions, setting the application context once is not sufficient. It must be set for each and every distinct page view in an APEX application.
To do this, many developers will instinctually gravitate towards using either a page or an application PL/SQL process to set the application context. While this would technically work, it is not an ideal place to set our the application context, as because the application context should be set before any application or page process executes. Furthermore, application and page processes will not fire when using asynchronous components such as dynamic actions.
Fortunately, APEX provides a process point designed for just such a scenario. It’s called the Initialization PL/SQL Ccode, and can be found in the Database Session region of the Security Attributes, one of APEX’s shared components. This attribute will execute whatever PL/SQL code is entered there before any other APEX component is executed. This ensures that when using application contexts, they will be set before any business rules execute.
To prove this, a simple test case was set up that compared three execution points: Initialization PL/SQL code, an application process, and a page process. All three execution points were set with a call to the procedure named apex_debug_message.log_message. When called from within an APEX session, the apex_debug_message.log_message call will write a message to the APEX debug log. Those messages can be viewed inline with all of the other built-in debug entries that APEX records during a debug capture.
As illustrated in Figure 11-3, it is clear that the initialization PL/SQL code is executed well before either the application or page process.
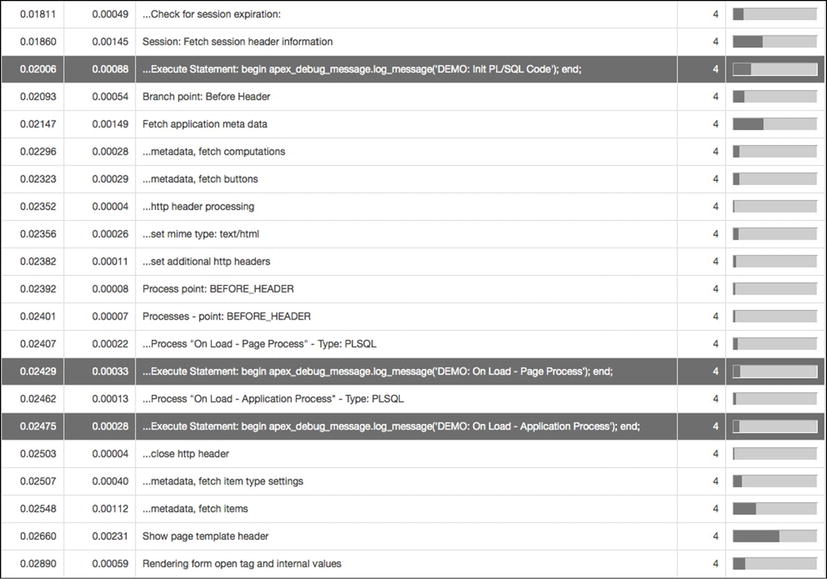
Figure 11-3 . The APEX debug report highlighting the execution points of the initialization PL/SQL code, an application process, and a page process
This test case reinforces the recommendation that application contexts should be set via the Initialization PL/SQL Code attribute, not an application or page process. Thus, in this example, you need to make a simple call to both set and unset the application context so that it will be set for the application.
To configure the application to set the application context, navigate to the shared components, and under Security, click Security Attributes. In the last region on the page called Database Session are the two attributes required for setting the application context, as illustrated in Figure 11-4.

Figure 11-4 . The Initialization PL/SQL Code and Cleanup PL/SQL Code attributes
Enter the code in Listing 11-5 into the Initialization PL/SQL Code box, and enter the code in Listing 11-6 into the Cleanup PL/SQL Code box. Then save your changes.
Listing 11-5. PL/SQL Call to Set Application Context
emp_ctx_pkg.set_ctx(p_username => :APP_USER);
Listing 11-6. PL/SQL Call to Unset Application Context
emp_ctx_pkg.unset_ctx;
![]() Note The attribute Initialization PL/SQL Code was called Virtual Private Database call to set security context in APEX 4.0 and previous versions. Despite the reference to Virtual Private Database in the old title, you do not need to use that feature or have a version of the database that even supports it to use this attribute to execute PL/SQL code before any application process or computation.
Note The attribute Initialization PL/SQL Code was called Virtual Private Database call to set security context in APEX 4.0 and previous versions. Despite the reference to Virtual Private Database in the old title, you do not need to use that feature or have a version of the database that even supports it to use this attribute to execute PL/SQL code before any application process or computation.
Now that the application context is being properly set, when you run the APEX application, you should see some records (as long as you log in to the APEX application with a username that has the same username as any value of ENAME in the EMP table does). Remember, the set_ctx procedure is fetching the DEPTNO associated with a record in EMP that matches ENAME to the currently signed on APEX user. If your username does not yield a match, then you will continue to see no records returned from the report.
To ensure that your secure view is working, simply create a user whose username is the same as any value of ENAME in the EMP table, and run your application while logged in as that user. In Figure 11-5, the report was run while logged on as a user with the username of KING. All three records from department 10 are displayed because KING is directly associated with department 10 in the EMP table.

Figure 11-5 . Results of the report on EMP_V when logged in as KING
One of the biggest benefits of using secure views in an APEX environment is that they will neutralize most types of URL tampering attacks. Since the view itself is filtering the data at the data layer, it matters little if a user passes a different ID via the URL to an APEX page. In fact, if a malicious user does pass an ID that he does not have access to see, a “no data found” message will be displayed, which may lead users to believe that the record they are trying to access simply does not exists.
It is important to keep in mind that any Automated Row Fetch and Get Next/Previous Primary Key processes also reference the secure views, not the base tables. Failure to reference the secure view will allow a user to see records that they are not supposed to see by manipulating the URL or simply clicking the Next/Previous Record buttons, if they exist on a form.
Another benefit of using secure views is that the total time to develop an application will decrease. If all the data security is taken care of at the data level, then developers don’t need to be concerned with ensuring that all queries are secured with the proper predicates. This will also simplify the SQL used in reports, thus making it easier to understand and maintain over the life cycle of the application.
Centralizing the data security also makes it a lot easier to change the business rules, should the need arise. Making a change to the application context procedure will impact any view that references that application context instantly. If the rule for determining which department a user is associated with changes, a single change to the procedure would instantly change how the entire application worked without making a single change to the application itself. This obviously saves a great deal of time and money and makes the application much more flexible.
Lastly, secure views also carry with them all of the benefits of standard views. Complex joins between multiple tables can easily be masked by a view. Columns that are not necessary for an application can be omitted, providing the developer with just those columns that are needed for a specific application. And if core business rules change, the definition of the view itself can be changed without impacting the application in many cases.
Nothing comes without a cost, and secure views are no exception. While they are quite robust and can be configured in a number of ways, they do have their shortcomings and potential drawbacks.
Secure views protect data only from a SELECT. They do nothing when it comes to INSERTs, UPDATEs, and/or DELETEs. In some scenarios, this drawback does not make much of a difference because the requirement is to simply filter data in reports and forms. However, if additional controls are required to also prevent users from updating or deleting specific records, then secure views may not offer enough functionality, and you should consider Virtual Private Database, which provides protection for all DML transactions.
If a secure view is created with the READ ONLY option enabled, either a separate set of PL/SQL APIs or INSTEAD OF triggers will have to be developed to facilitate any DML transaction. While there is no additional risk with using either of these approaches, it will take extra time to design and develop the extra code required versus using the APEX built-in DML processes.
Summary
Using secure views, you can easily and affordably secure the data in your APEX application, no matter which version of the Oracle Database you are running on. The techniques described in this chapter use both core APEX and database functionality and can be set up and configured quickly and easily. In addition to the benefits of the secure views, using views in general will result in a more manageable and easier-to-understand application.
Although secure views provide an adequate layer of security in many cases, they may not provide enough. Carefully consider your security requirements before starting any development to ensure that your application won’t soon outgrow what secure views can provide.
