 THE TURN OF THE ANALYTICAL WHEEL
THE TURN OF THE ANALYTICAL WHEEL
The analytical process is used to create never-ending accurate analytics. The process begins with questions, the answers to which inevitably lead back to more questions. So the cycle never ends but instead continues to spiral in directions where the analysis process is yet to be unmasked. With proper planning and direction, the process converts raw data and/or information that has been acquired into precise information that could potentially lead to further analysis.
The analytical process involves substantive issues and concerns related to information that needs clarification. Analytics is then used to guide the collection strategies and the production of the appropriate analytical product. Analytics is the process whereby information is obtained from all sources that are pertinent to the areas of collection, collation, dissemination, evaluation, description, and analysis.
Professionals in the analytical community absorb incoming information, evaluate it, produce an assessment of the current state of affairs, and create a strategic methodology. A large part of the analytical process is devoted to the processing and exploitation of raw data into a form usable by those who seek to detect fraud and the anomalies that correlate within a fraudulent entity.
The analytical process is rigorous, timely, and relevant to the needs and concerns of everyone involved. As we continue in our efforts, it is imperative that we understand the nature and importance of the analytical process in any fraud-related matter. The transformation of data and the summary of results are critical elements in the decision-making process of fraud analytics. Once the task has been completed, we can attempt to understand the nature of the analytical process. Fraud analytics processing involves performing specified data transformations and generating relevant results. Analytical processing includes gathering data and performing the analytical process on the data.
The results of any fraud analysis or financial analysis should be clear and concise, easy to understand, and easily transferrable to others involved in the case. Accurate identification is the most critical step in the fraud analysis process. It can positively impact detection, reporting, and resolution. We cannot ignore the fact that there are times when we may be subjected to or taken for granted as the process unfolds in detection and prevention of fraud.
The fraud analysis process involves these stages:
- Brainstorm the schemes and symptoms.
- Ensure that reengineered methods are effective.
- Learn new methodologies, software tools, and analysis techniques.
- Establish a hypothesis-testing approach.
A significant component of fraud analysis is detecting fraud anomalies and discovering if there are other patterns and/or trends that should be considered. Fraud is intentional; it is found in very few data sets, and finding it is like finding a needle in a haystack. As we work through the analytical process, we need a broader understanding to decipher the six-step analytical process that is critical to all.
 IT TAKES MORE THAN ONE STEP
IT TAKES MORE THAN ONE STEP
The fraud analysis process is not a series of steps that are processed in a strict order; rather, the processes represent a recipe for accurate and concise analysis and information sharing that will change according to the red flags that are detected (see Figure 3.1).
FIGURE 3.1 The Six-Step Analysis Process
Source: Central Intelligence Agency.
Step One. The direction process involves establishing the boundaries of the analysis and what will be discovered during the process. This is also the step where analytical gaps are determined, the effectiveness of the analysis is determined, and the significance of the analysis is established.
Step Two. The collection process involves the gathering of raw data from which a finished analysis is produced. The collection process seeks to establish a criminal or fraudulent nexus with a person or organization. (The nexus is referred to as a “criminal predicate.”) The analytics process also seeks to collect information on trends, patterns, and methods of anomalies that help to describe the phenomena of fraud analytics.
Step Three. The evaluation process involves the conversion of large amounts of data into a finished analytical product. The evaluation process is done through a variety of methods to ascertain the most effective analysis, including decryption and data reduction. Evaluation includes entering raw data into databases (fraud analysis) where the data can be used in the analysis process. It includes recommendations, findings, and interpretation of information stored in the fraud summary reports, investigative reports, and the like.
Step Four. The collation/description process has four distinct stages in the fraud analytical process:
- Evaluating raw data from the information gathered to detect its utility for analysis.
- Examining the validity of raw data for cleanliness.
- Clearly defining the analysis process in order to collect additional resources that will assist in gaining the most accurate raw information for robust analysis.
- Utilizing other activities in the collation/description process: assessing the method by which the information was collected and integrating the new information with existing data for further analysis. Collation also forces the questioning of information to confirm truths and probabilities.
In sum, the collation/description process is critical for two reasons:
- It seeks to provide the control of information through the process.
- It provides important insights into defining the requirements of analysis.
Step Five. The analysis process is the heart of the analytical process. It is essentially the approach to problem solving. It uses established methodologies that are qualitative and quantitative—that seek to integrate correlated variables in a section of raw data in order to understand their meaning.
Step Six. The dissemination process is essentially an analytical product that has virtually no value unless the system is able to get the right information. Dissemination—or information sharing—seeks to accomplish this goal. One critical question to include in the dissemination process may be: “Who is considered an authorized person?”
The results of any analysis process should be:
- Easy to understand
- Clear and concise
- Easily transferrable to others involved in the fraud examination and/or financial investigation
- Accurate
Accurate identification is most critical in the fraud analysis process. It can positively impact detection, reporting, and resolution.
It is necessary to use the key points in analytics in the analytic strategy. Using the key points heightens users' awareness of the importance of knowing the process that will steer them in the right direction and offer accurate results.
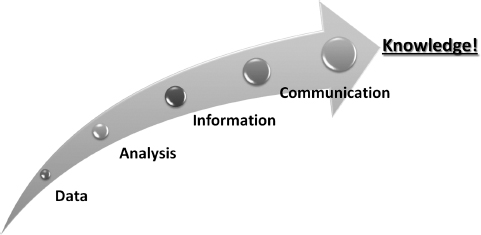
FIGURE 3.2 The Five Keys to Analysis
Source: Delena D. Spann, “Advanced Fraud Analysis,” Utica College, Economic Crime Management Graduate Program.
Keep in mind that the analytical cycle is not a substitute for any other method concerned with how the analysis should take place. It is always necessary to implement the steps in processing analysis. It's simple: The process noted in Figure 3.2 is vital. To ensure that the most effective analysis is coupled with positive results, we must allow the cycle to take control.
The wisdom of analytics focuses on data, information, and knowledge. Raw material is data, the “gold key” to analysis, which might come from numerous sources.
Two processes in analysis are at work:
- Data becomes information when it is effectively analyzed.
- Information becomes knowledge when it is effectively communicated.
The next list emphasizes the importance of incorporating a strategic method to cover all bases at the onset of any type of analysis. The strategies are not geared toward one specific type of analysis; however, it is strongly suggested that you implement the list routinely in all analysis, whether it is trend analysis, financial analysis, or predictive analysis.1
Fraud and Data Analytics Strategies
- Create a plan to collect records.
- Develop spreadsheets or databases.
- Enter data.
- Review data for leads.
- Analyze, analyze, analyze.
- Create reports, charts, summaries.
- Develop conclusions.
- Make recommendations.
- Manage the case.
The analytical process is quick moving; organizations will have to maintain the pace technologically. As analysis products are improved, persons from every spectrum who depend on the analytical techniques will be eager to respond to critical inquiries from their fields. The increased response will enable the analytical community to allocate and decipher complex data appropriately, make well-rounded decisions, and prevent frauds before they occur.
The aim of the process is to understand the complexity of data and how fraud analytics can assist in deterring actual fraud and the likelihood of potential fraud.
In the scheme of things, the analytical process and its techniques are long overdue; however, as technology progresses, there are times that we still need to go back to the drawing board—the old way of determining where the discrepancies may appear in the data. Here are a few additional points that are critical to fraud analytics:
- Import different formats of data.
- Perform complex comparisons of different data sources.
- Identify duplicates and gaps.
- Perform quick analysis of large volumes of data to produce information.
The analytical process can be used not only to make the meaning of data clear but also to make recommendations on the basis of the transactions uncovered. Analysis continues to evolve in various directions. Fraud examiners, analysts, CPAs, and investigators must make an effort to enhance their knowledge in the area of analysis and the processes that define an industry that thrives on growth.
 PROBABILITIES OF FRAUD AND WHERE IT ALL BEGINS
PROBABILITIES OF FRAUD AND WHERE IT ALL BEGINS
From an article by Michael Rosplock, here are a few analytical processes that can be used to detect the probabilities of fraud:
- Perform a subjective analysis of the history and operations of the company. Obtain credit and bank reference information to determine changes in payment habits, relationship with the bank in regards to experience, savings account balances, short- and long-term credit line exposures, and bank compliance.
- Analyze the financial condition by performing a horizontal and vertical analysis of the balance sheet and income statement. The use of industry standard statistics is essential in the analytical process, as a means of verifying the condition of ratios and financials in relation to standards.
- Once the conditions of ratios and statistics have been determined, trending analysis is the next step in the analysis process. This process will assist you in detecting inconsistent patterns in the ratios and statistics, which should be regarded as red flags.
- The detection of trending inconsistencies requires further analysis to determine the factors that impacted the changes in the condition of ratios or financial statistics. The detection of imperfections or inaccurate statistics is essential during this analytical process.
- When analyzing the condition and trend of the income statement and balance sheet, it's important to evaluate the gross margin, operating margin, and net profit margin as a percentage of sales. This will determine if the changes in condition of the income statement and balance sheet were accordant.
- In-depth knowledge of the balance sheet, income statement, and statement of cash flow requires an understanding of how changes of consistent or inconsistent trending patterns impact the income statement and cash flow.
Your ability to determine inconsistencies or unexplainable changes in the income statement and balance sheet will assist you in the beginning stage of forensic financial analysis. Your ability to acquire an investigative perseverance requires an ability to analyze below the surface.2
 WHAT SHOULD THE FRAUD ANALYTICS PROCESS LOOK LIKE?
WHAT SHOULD THE FRAUD ANALYTICS PROCESS LOOK LIKE?
Robert Tie, in an article, recommends designing a data analytics process that clearly identifies and fully explains:
- What organizational data to collect
- When and how to obtain the organizational data
- How to integrate the process into the organization's fraud risk assessment program
- What tools and techniques to use for evaluating the potential existence of fraud
- How to evaluate the process's effectiveness in detecting and preventing fraud
- How to report findings and recommendations
- Standards for tracking the timeliness and effectiveness of remedial actions3
A four-step fraud analytics approach takes us from data to insight:
- Data identification. Pick the wrong data and you won't find what you're looking for; pick too much and you'll be sifting through it for no reason.
- Forensic data collection. When conducting fraud analytics in an investigation, it's essential you follow well-defined forensic preservation standards, which include maintaining the data's chain of custody and performing data integrity validation to ensure that you've captured all transactions and ensured the absence of tampering.
- Data normalization and structuring. You'll have to normalize and structure all collected data so it can be linked, as it may originate internally or from third parties. Some will be structured, such as that originating from databases, while others will be unstructured, such as text-heavy data. Only when data is normalized and structured will you be able to derive all possible insight from the data you have collected.
- Data analysis. You must now determine how to best analyze the collected data. Strategies include simple queries, relationship mapping, link analysis, and visual analysis, as well as more advanced models to identify previously unknown patterns.
If you're having trouble convincing senior-level management that you need to use fraud data analytic tools to find fraud, you can emphasize that the need is great and that all the methods indicated are useful to the success of capturing fraud at the inception.
Getting from data to insight can be a challenge the first time around, but a well-established fraud analytics approach can save you time and money in the long run.
Here are some common categories of fraud analytic approaches:
- Rule-based: Detect fraudulent transactions based on known behaviors.
- Anomaly detection: Identify aggregate abnormal patterns that don't conform to established normal behaviors.
- Predictive modeling: Statistical analysis of current and historical data to assess future behavior.
- Neural networks: Unsupervised learning based on historical data for the purpose of identifying unknown patterns.
- Visual analytics: Graphical representation of relationships found within data.4
According to Peter Millar,
The results of any data analysis techniques are only as good as the underlying data that is examined. Data analysis is used to formulate an overarching methodology for building a data analytics program—from data identification and acquisition through reporting the analysis results—and how to tie the process to the organization's fraud risk assessment to most effectively detect fraud.5
 DATA ANALYTICS EXPOSED
DATA ANALYTICS EXPOSED
According to Sunder Gee:
Fraud analytics is the process used to analyze data that can identify anomalies, trends, patterns, and concerns. It is highly effective when applied to situations that involve large volumes of electronic data.
Traditional analytical methods include:
- Extract.
- Sort.
- Use statistics.
- Identify gaps.
- Identify duplicates.
- Perform aging.
- Develop samples.
- Summarize.
- Stratify.
- Join (match).
- Compare.
In order to effectively apply and interpret the results using traditional and advanced statistical methods, the auditor or investigator must have a good understanding of the business and industry involved, as well as be familiar with the software used for the analysis.6
A few factors remain to ensure effective fraud detection strategies and to understand the complexities of the information that must be analyzed:
- Fraud analytics, when used correctly, is a powerful tool for identifying suspect accounts or amounts for further analysis.
- Fraud data analytics is a tool to complement additional tests and tools.
- Users have to gain expertise in interpreting results.
Even with the most sophisticated approaches and despite the best efforts of those responsible for preventing fraud, one inevitable reality remains: Fraud happens.
Although fraud prevention and detection are related concepts, they are not the same. As stated in an ACFE article: “Prevention encompasses policies, procedures, training, and communication; detection involves activities and programs designed to identify fraud or misconduct that is occurring or has occurred.”7
 NOTES
NOTES
1. Delena D. Spann, “Advanced Fraud Analysis,” Utica College, Economic Crime Management Graduate Program, PowerPoint Presentation, 2010.
2. Michael F. Rosplock, “Advanced Forensic Financial Analysis,” Fraud Magazine (November/December 2001). Reprinted with permission of the Association of Certified Fraud Examiners.
3. Robert Tie, “Devil in the Details: Anti-Fraud Data Analytics,” Fraud Magazine (January 2013). Reprinted with permission of the Association of Certified Fraud Examiners.
4. Spann, “Advanced Fraud Analysis.”
5. Peter Millar, “Using Data Analysis to Detect Fraud,” ACFE Seminar, Chicago, March 2013.
6. Sunder Gee, “Bringing Sophistication to Data Analytics,” ACFE Pacific Fraud Conference, 2012. Reprinted with permission of Sunder Gee.
7. IIA, AICPA, and ACFE, “Managing the Business Risk of Fraud: A Practical Guide,” 2012, pp. x–x. www.acfe.com/uploadedFiles/ACFE_Website/Content/documents/managing-business-risk.pdf. Reprinted with permission of the Association of Certified Fraud Examiners.


