CHAPTER 8
Denial of Service Attacks
In this chapter you will learn about
• Categories of DoS/DDoS attacks
• Bots, botnets, and pulsing zombies
• Tools like Hulk, HOIC, and LOIC
Denial of service (DoS) and distributed denial of service (DDoS) attacks can target various corporate resources and focus on not allowing legitimate requests to be served. That can cause significant service disruption and tremendous monetary losses, depending on the type of organization and associated resource under attack. Based on the locality, a DoS attack can be launched locally or remotely.
Local DoS Attacks
When an attacker launches a local DoS attack, the target might be a specific system process or the underlying host. For example, if there’s a MySQL service running, the attacker can choose to stop the service or change its configuration in a way that it will no longer serve legitimate users that try to query the database.
If there’s inadequate access to perform this action, an attacker may choose to cause the service to crash, something that can commonly happen using a script or a tool like Metasploit. An example is CVE-2018-3174, which describes a vulnerability allowing an unauthenticated entity to exploit the MySQL service and cause a DoS attack due to it hanging or constantly crashing.
Another method of leveraging a local attack would be to overwhelm the hardware resources with specific tasks and overutilize the memory, CPU, and hard disk. Anything that has an effect on system resources can do the trick. Imagine how many times you tried to run a program that was too much for your hardware configuration or the tasks proved to be too resource intensive. Examples of resource-intensive tasks are
• Rainbow table creation
• Brute-force password cracking
• Multiple large files being constantly accessed or copied
An attacker can deliberately execute tasks like these in an effort to exhaust resources on a target machine and can often use specific types of malware to perform such activities, like a virus or worm.
Remote DoS Attacks
During a remote DoS attack scenario, a protocol attack (like a SYN/ACK flood) or application-layer attack (like a HTTP GET or HTTP POST) can be leveraged to exhaust resources, while a volumetric attack (like an ICMP or UDP flood) can be used to consume network bandwidth or cause service disruption.
Protocol Attacks
The main types of protocol attacks are SYN and ACK floods, as well as fragmentation attacks.
SYN Flood Attack
During a SYN flood, the attacker aims at overwhelming a target system with multiple SYN packets so it won’t be able to process legitimate requests, as seen in Figure 8-1.

Figure 8-1 SYN flood attack
Each time the target server receives a new SYN packet, it responds with a SYN/ACK and sets a timer, as it will expect a final ACK packet to be received from the source to conclude the three-way handshake. However, the attacker will never send any final ACK packets. Instead, SYN packets will continue to be sent in an effort to fill the destination server’s connection queue and not allow it to accept any other SYN packets from legitimate users intending to establish new connections.
Attackers often use spoofed source IP addresses, which ensures that response traffic from target devices doesn’t reach a working system that will reset a connection for which it didn’t send an initial SYN request. If that’s the case, it just allows the target system to remove entries from its connection queue faster, which makes the attack less effective.
ACK Flood Attack
The primary target of an ACK flood attack is any device that is stateful in nature, like a firewall or a server. As such, devices like switches, routers, and load balancers aren’t good candidates for this attack. The ACK packets don’t really need to have any payload, since the attacker’s goal is just to generate traffic (in the form of ACK packets) that will overwhelm the target. Since ACK traffic is very common in any network, it’s difficult to distinguish valid ACK traffic from illegitimate packets. Similar to a SYN flood, an attacker can also use spoofed source IP addresses during an ACK flood.
Fragmentation Attack
A fragmentation attack aims at occupying the target with reassembly of multiple fragmented packets that are received. Intermediary devices (like routers and firewalls) will pass that traffic across the network and expect reassembly to be performed at the receiving device. However, if reassembly of packets is constantly being performed, the device will start getting overutilized by that process. This can have even more of an impact if the packet content is randomized by an attacker, which will tie up additional resources for processing and may sometimes cause targets to crash.
Application-Layer Attacks
The most common application-layer attacks are HTTP GET and POST. The attacker interacts with a target web server, sending HTTP GET or POST requests in an effort to overwhelm the server as it responds to those. Multiple requests can be submitted for text, images, graphics, or a form submission that passes data to the server for further processing. This can become more effective if there’s a backend database (like MySQL) that the web server needs to constantly interact with. Attackers use botnets (discussed later in this chapter) to submit thousands of such requests and easily overwhelm target servers.
Volumetric Attacks
The most common volumetric attacks are UDP and ICMP floods, ping of death, and smurf attacks.
UDP Flood Attack
Similar to a SYN flood attack, the attacker uses UDP packets during a UDP flood attack. Again, the source IP address can be spoofed to make the attack more effective. Packets are destined to random UDP ports at the target in an effort to force it to check for any available services on those ports and, if none are listening, to send an “ICMP destination unreachable” message back to the source. The more UDP packets the target receives for nonexistent services, the more ICMP responses will need to be sent. That gradually overwhelms the target as resources are increased to perform this activity and the related network bandwidth is also starting to get consumed by the associated traffic.
DNS Amplification Attack A typical example of a UDP flood is DNS amplification, where the attacker tries to take advantage of open DNS resolver functionality to overwhelm a target with traffic, as seen in Figure 8-2.

Figure 8-2 DNS amplification attack
The attacker uses a spoofed source IP address (matching the victim’s real IP address) and sends a large volume of DNS requests to various open DNS resolvers (which accept DNS requests from any source). Those will respond with DNS reply packets, which will all be destined for the victim. As DNS reply traffic increases, the victim experiences a UDP flood attack.
Another method of performing this attack is one where the attacker first sends a DNS request for a domain he controls (which means the attacker has access to the authoritative DNS server for that domain). Once that server receives the request, it will try to resolve the request, and the attacker’s DNS server will eventually be reached to provide an authoritative response. A large file will then be provided, which the DNS server will cache. This step can be repeated for various open DNS servers.
After that, the process discussed in Figure 8-2 takes place again, where multiple DNS requests for the attacker’s website are sent. Only this time, the attacker has ensured that the related DNS replies will be much bigger in size, since a large file has been provided earlier to the various DNS servers. Therefore, the target victim will get an exponential increase in DNS responses from all of them.
ICMP Flood
If ICMP is allowed to reach corporate devices (meaning it’s not blocked by a firewall or other security device), an attacker can leverage it to cause a DoS attack. That can be done by sending multiple ICMP ECHO request packets to a target in order to constantly elicit ICMP ECHO reply messages, which gradually consume the target network’s bandwidth. The attack can often originate from specific machines or even a whole network of devices that the attacker has compromised. Spoofed source IP addresses can also be used, as the attacker only cares about eliciting ICMP responses from the target and doesn’t need to receive any actual information from it. The following two types of attacks both leverage ICMP.
Ping of Death The attacker uses malformed or large ping command packets (greater than 64KB) in an effort to crash a target system. This can be effective against specific end systems with OS versions that are susceptible to memory buffer overflow issues when reassembling fragmented packets. Note that this attack dates back to the ’90s and is very rarely effective today, especially if a firewall or IPS device is present that can easily detect this and drop offending traffic.
Smurf Attack During a smurf attack, multiple ICMP ECHO request packets sourced from a spoofed IP address matching the victim’s are sent to a network’s broadcast IP address. That causes all the active devices in that network to send ECHO response messages to the victim. The only thing an attacker needs to do is identify a network that will accept the ECHO request traffic and allow for the associated responses to be sent. That can be the target’s local network or any network over the Internet that allows for this attack to take place.
Botnets
Botnets are networks composed of compromised machines (known as bots) that the attacker controls and can use at will. Various tasks can be performed by botnets, such as promoting fake ads to victims and enticing them to click on an advertisement, sending spam e-mails, performing brute-force attacks on target accounts, or launching any of the previously mentioned DoS attacks, but this time in an enhanced manner, since a whole network of machines will be used. It is also important to highlight that various attackers can be using a botnet at the same time while performing multiple attacks. Command and control (CnC or C&C) servers are used to issue commands to the bots, commonly using Internet Relay Chat (IRC) channels or peer-to-peer (P2P) networks.
Typical operation starts by installing some type of malware on target systems or launching an exploit against them after a vulnerability is found. For example, the attacker might place malware on a web server and entice a victim to download it using a phishing e-mail. Alternatively, a scan can be performed to identify a vulnerable target, and after that has been found, the malware residing on the attacker’s machine can be copied to the target. Regardless of the method, the goal is to allow for the target machines to become part of the compromised botnet. With the expansion of Internet of Things (IoT) devices, any device can be a part of a botnet, including smart refrigerators, cameras, Supervisory Control and Data Acquisition (SCADA) sensors, and anything similar. Figure 8-3 shows an example of a botnet’s topology.

Figure 8-3 Botnet topology
Multiple C&C servers are in place, and all compromised devices (laptops, smartphones, servers, desktops) are used to attack unsuspecting victims.
DDoS Attacks
DDoS attacks take place when multiple source machines are used to launch traffic toward a victim. The logic is the same with that of a DoS attack, but during a DDoS, multiple devices are used to generate traffic, which typically happens by leveraging a botnet to launch the attack. As seen in Figure 8-4, the attacker is using a botnet to target multiple victims and cause a DDoS attack.
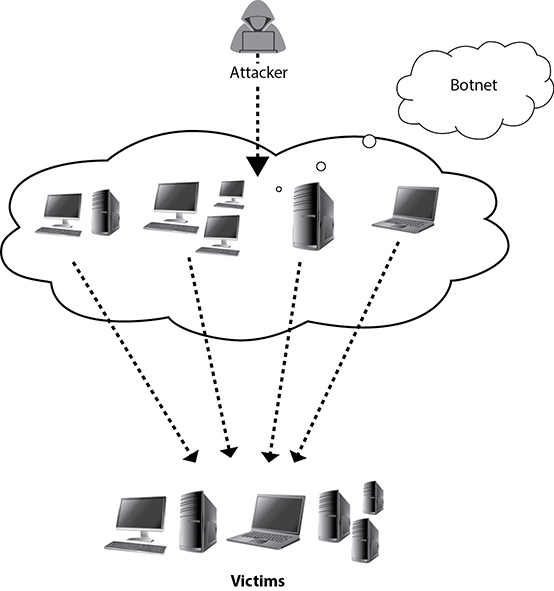
Figure 8-4 DDoS attack
Reflected DDoS
During a reflected DDoS attack, the attacker uses a botnet to send spoofed SYN packets (spoofing the source IP address to match that of the victim’s) to various entities that act as intermediary machines during the attack, as seen in Figure 8-5.

Figure 8-5 Reflected DDoS
The response SYN/ACK traffic relating to those SYN requests is then directed to the real machines, which are overwhelmed with traffic.
Pulsing Zombies
In an effort to make the attack more difficult to trace, pulsing zombies can be used. They do the same job as traditional zombies (compromised machines), but they work intermittently, which makes detecting and stopping them much harder. For example, a pulsing zombie may be alive and sending DoS-related traffic for 10 minutes and then go down for 40 minutes. The same pattern repeats across different machines, which makes the attack much more difficult to stop. When the devices are alive, detection is easy (as lots of traffic is sourcing from them), but when they go silent, that can be much harder to do.
DoS/DDoS Tools
Depending on the attack goal and level of sophistication, anything from a simple script generating ICMP requests to specifically purposed DoS/DDoS tools can be used.
Hping3
Hping3 was already mentioned earlier in the book and was used for crafting packets and spoofing the source of the traffic, but it can also easily be used to perform a DoS attack. You can try attacking your Metasploitable FTP or web servers from Kali Linux using the following commands:

As a reference, the following parameters were used:
• -c specifies the number of packets that will be sent (try to increase this gradually and see when a threshold will be reached that will make the servers unavailable or decrease their performance).
• -S designates SYN packets are being sent.
• -p specifies which port will be targeted.
• --flood specifies that flood mode will be enabled, allowing hping3 to send packets faster, without showing incoming replies.
• 172.16.197.136 specifies the target, which can be an IP address or a hostname.
Hulk
Hulk (https://github.com/grafov/hulk) can use thousands of threads in order to launch an efficient attack against a web server. If you want to try this out on your Kali machine, just download a copy of the GitHub repository content and decompress it. You can then use the hulk.py Python script to launch an attack against Metasploitable’s web server or any other web server you own and have permission to test against.
![]()
As the attack progresses, the target website will become unavailable and you will see the following messages being displayed in your terminal, indicating the target website has become unavailable:

Additional Tools
LOIC (Low Orbit Ion Cannon) and HOIC (High Orbit Ion Cannon) are some of the most commonly used tools to perform DDoS attacks across the Internet. LOIC supports UDP, TCP, and HTTP GET packet floods, while HOIC only supports HTTP GET and POST attacks. Both can be easily controlled by IRC. Note that you don’t even need to install the client application, since the tools can be made available on various websites, which can then be used to launch an attack. Slowloris can be used against web servers, and Tor’s hammer (also known as Torshammer) is a tool that can use the TOR network to also launch an attack against web servers. Tsunami combines layer 4 and layer 7 attacks in a simple-to-use GUI. All these tools are available at https://sourceforge.net if you are interested in using them to test any of your servers.
Defending Against DoS/DDoS Attacks
In order to ensure your devices aren’t used to attack other networks, it’s advisable to enhance your endpoint protection. That will make it more difficult for attackers to infect them with malware or exploit any vulnerabilities that will give them control and turn your machines into zombies. Performing host hardening and installing host AVs, firewalls, and HIPSs in addition to upgrading and patching the underlying operating systems are all highly recommended. Also remember that using a good WAF can greatly help protect your servers against application-related DDoS attacks.
Although a lot of companies mostly care about inbound traffic, egress filtering is key to preventing malicious traffic from leaving your network, as that can be dropped at the perimeter.
If you use Cisco devices, the TCP intercept feature can aid in preventing SYN floods, as it allows interception and validation of all connection requests. Limiting the rate of traffic can also help stop (or at least slow down) a DoS attack quite significantly, so consider implementing rate limitation on your network devices.
Using the Center for Internet Security (CIS) benchmarks is a great method to start hardening your endpoints and servers to keep them protected. Related documents are available at https://www.cisecurity.org/cis-benchmarks.
To ensure your network isn’t affected by DoS attacks, consider using specific hardware DoS protection and mitigation devices or any related service your Internet Service Provider (ISP) offers in addition to asking them to help block any malicious sources from sending you their traffic. Vendors like Akamai, Cloudflare, Arbor Networks, and F5 Networks, to name a few, all offer solutions to help protect against DoS attacks. Using load balancers can greatly help you cope with increased traffic, as they will automatically distribute the load among your servers in an effort to keep services running as much as possible. You can also consider having redundant servers available that can be activated in the event of increased traffic, which can also help with service availability.
Configuring rate limiting on incoming traffic is quite crucial, as you can limit how much traffic a server receives. If you proactively test that device to identify what its limits are, you can set appropriate traffic thresholds to protect it from crashing or having its performance degraded.
If you think one of your machines is being affected by a DoS attack, you can use some of the useful commands discussed in Chapter 2 as a starting point to help you identify and mitigate these suspicious activities. Examples include checking network connections and their state (using netstat), identifying specific processes that may be overutilizing resources and checking the resource state (using tasklist, ps aux, top, free, and df), and terminating anything suspicious (using wmic and kill).
Chapter Review
DoS attacks are quite easy to launch, and with the spread of botnets any attacker can just rent their resources to launch attacks that can bring down whole countries. Many companies have found themselves being threatened by attackers claiming they have the ability to bring their networks to a halt unless they receive money to look the other way.
Attackers can launch local or remote attacks. Common examples include protocol (SYN or ACK flood) and application-layer attacks (like a HTTP GET or HTTP POST) that target resources and ICMP or UDP floods that target network bandwidth and cause service disruption. Pulsing zombies are also used by attackers to make identifying an attack’s source more difficult, while amplification attacks are leveraged to exponentially increase the traffic a victim receives.
Host hardening and egress filtering are crucial to avoid becoming a DoS source, while ingress filtering, rate limitation, load balancing, and using specifically purposed hardware can help protect your infrastructure against DoS attacks.
Questions
1. Which of the following would most likely be the target of an ACK flood?
A. Router
B. Load balancer
C. Switch
D. Server
2. Which of the following attack types best describes a UDP flood?
A. Volumetric
B. Protocol
C. Application layer
D. Reconnaissance
3. Which of the following tools would be most suitable to help prevent an HTTP GET DoS attack?
A. Stateful inspection firewall
B. Web proxy
C. NIDS
D. WAF
4. Which of the following tools would be suitable for a UDP flood?
A. HOIC
B. Slowloris
C. LOIC
D. Torshammer
5. What size of ping requests would an attacker use during a ping of death attack?
A. 66KB
B. 65 bytes
C. 63KB
D. 70 bytes
6. Which of the following statements regarding a smurf attack is accurate?
A. Attacker sends ICMP ECHO reply packets sourced from a spoofed IP address matching the victim’s.
B. Attacker sends ICMP ECHO request packets sourced from a spoofed IP address matching the victim’s.
C. It uses UDP packets.
D. Attacker sends SYN packets destined for the target network’s broadcast IP address.
7. Review the following command output:
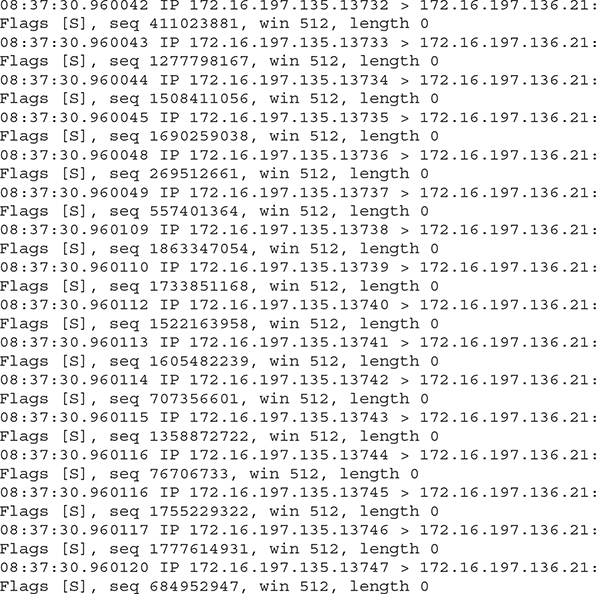
Which of the following statements seems to be the most accurate?
A. There’s a DDoS attack in progress.
B. Someone is running a port scan.
C. There’s a DoS attack in progress.
D. Standard traffic.
8. Why would a pulsing zombie be commonly used during a DDoS attack?
A. To enhance the attack
B. To control additional machines
C. To replace CnC servers
D. To make detection of the attack’s source harder
9. Which of the following would be most suitable to protect a server from being used as a DoS attack source?
A. Installing an up-to-date AV
B. Ingress filtering
C. Using a load balancer
D. Using a NIPS
10. During a DNS amplification attack, which of the following does the attacker take advantage of?
A. DNSSEC
B. Open DNS resolver functionality
C. ICMP redirection
D. Pulsing zombies
Answers
1. D. The primary target of an ACK flood is any device that is stateful in nature, like a firewall or a server. Remember that devices like switches, routers, and load balancers aren’t good candidates for this attack.
2. A. A UDP flood is a volumetric attack in which an attacker sends UDP packets destined for random UDP ports on the target in an effort to force it to check for any available services on those ports, and if there are none, to send “ICMP destination unreachable” messages back to the source.
3. D. From the provided options, a web application firewall would be the most suitable one, since the HTTP GET attack is an application-layer attack. Note that if this was a SYN flood, a stateful inspection firewall would be adequate, as it can inspect layer 4 (SYN) traffic. However, an HTTP GET DoS attack is an application-layer attack, so a WAF is required to inspect packets at that layer.
4. C. From the provided options, LOIC is the only tool that can perform a UDP flood, since all other tools are only able to perform application (HTTP-type) DoS attacks.
5. A. During a ping of death attack, the goal is to try and crash a target system by sending malformed ping packets that exceed the maximum packet size, which is 65,536 bytes (as per RFC 791). Some targets can’t cope with these unexpected packets and may crash upon reception and subsequent processing of them.
6. B. During a smurf attack, multiple ICMP ECHO request packets (sourced from a spoofed IP address matching the victim’s) are sent to a network’s broadcast IP address. That causes all the active devices in that network to send ECHO response messages to the victim.
7. C. All traffic is sourcing from IP address 172.16.197.135 and destined for 172.16.197.136 (TCP port 21). All packets are SYN requests, and the source ports are in succession, starting from 13732 all the way to 13747. If you notice the timestamps, you will see that the first packet is sent at 08:37:30.960042 and the last one at 08:37:30.960120, meaning only milliseconds apart. So this doesn’t really seem to be standard traffic. If an attacker was running a port scan against TCP port 21, one SYN request would be enough to check that the port is open, but here 16 requests are present. As such, this most likely looks like a DoS attack (since there’s a single IP address where all packets are coming from). Note that in a real-life scenario you would see thousands (or even millions) of packets, but in the context of the question, a small number is used for the packet capture to be adequately clear for your review.
8. D. Pulsing zombies work intermittently, as they are operational for a period of time and then they stop their operation for a specific time frame. For example, a pulsing zombie may be running for 5 minutes and then be inactive for 30 minutes before resuming operation. That behavior makes detecting and stopping them much harder.
9. A. Before an attacker uses a host as a DoS source, malware is commonly installed on it so the attacker can take control and allow the machine to participate in a botnet for later attacks. Using an up-to-date AV solution can aid in not allowing the attacker’s malware to compromise it and use it for malicious purposes.
10. B. In a DNS amplification attack, the attacker uses a spoofed source IP address (matching the victim’s IP address) and sends a large volume of DNS requests to various open DNS resolvers (which accept DNS requests from any source). Those will respond with DNS reply packets, which will all be destined for the victim. As DNS reply traffic increases, the victim experiences a UDP flood attack.
References and Further Reading