CHAPTER 10
Maintaining Access
In this chapter, you will learn about
• Malware categories
• Trojan horses
• Backdoors
• Rootkits
• Tools like Rekall and Volatility
Malware is commonly categorized depending on the function it has and operation it performs. As such, a piece of code that monitors a user’s browsing history can be classified as spyware, while software that keeps displaying advertisements against the user’s desire is known as adware. Regardless of the category, there’s a common goal: perform some action that will harm a machine or access it without user consent, with an intention of performing tasks against the user’s will, like data theft.
Malware Categories
Attackers can do all sorts of things and use different types of tools to execute their tasks. Similarly, different malware types allow them to achieve different goals. An overview of the most common malware categories follows.
Virus
A virus is a type of program that requires human intervention to perform its operation. Most people think that if they get an e-mail containing a virus in the form of an executable file being attached, their system is automatically infected with it. However, that’s not the case. In that particular scenario, for the machine to become infected, the user would need to open and run the file contained in that attachment. Some of the most common types are
• Macro virus Can infect files that contain macro commands, like Microsoft Word or Excel.
• Boot sector Runs each time the system is started, as it stores itself on the boot sector of the hard disk.
• Stealth Attempts to hide from any AV software that exists on the machine.
• Polymorphic Alters its encrypted code (using an internal morphing engine) in an effort to evade signature-based detection. Note that its core function (and corresponding programming code) remains the same between propagations, which may allow security researchers to create signatures based on that code corresponding to that core function.
• Metamorphic Has the ability to change its code and perform different functions on the various systems it infects, thus making detection quite difficult.
• Multipartite Combines different functions, allowing it to attack executable files in addition to the system’s boot sector.
Worm
A worm is able to self-propagate within a target network, constantly looking to infect new systems. In contrast to viruses, worms don’t require a host program or any human intervention to propagate, and they consume a lot of system (for example, CPU, RAM, and hard disk read/write operations) and network recourses (bandwidth and file share space) in the process. Worms are discussed in detail in Chapter 12.
Spyware
Spyware allows an attacker to get valuable information about a victim, like browsing habits, system activity, and sensitive user information (like banking account details). That can take place using a keylogger (recording all user keystrokes) or other software like Trojans (discussed later in this chapter) or adware, which is used to display advertisements to the victim during a program’s execution, commonly in the form of a window popping up or a banner on a browser. Adware authors gain monetary rewards by displaying advertisements for specific products in addition to victims clicking on those to review their content.
Scareware
Aims at “scaring” a victim by stating there’s some type of security issue with his machine and a particular software needs to be downloaded to resolve that issue. Common examples include victims browsing to various websites and getting a pop-up window displaying the machine is infected by 50 viruses, which can be fully removed if the victim purchases a recommended AV software at a given price. When that happens, the victim not only pays the price for the supposed AV but also downloads additional malware on his machine.
Ransomware
Requires an amount of ransom to be paid to the attacker, to allow the legitimate user to access his data. When this process is accompanied by encrypting the user’s data and providing him with a decryption key when the ransom is paid, crypto-ransomware is in use.
Backdoors and Trojans
A backdoor allows access to an application or a system in a covert way (bypassing the usual access control restrictions). Do you remember the 2010 movie Tron: Legacy? In the early scenes, Flynn uses a backdoor account to access his dad’s application. A backdoor doesn’t necessarily have a bad meaning, as programmers use them all the time to be able to access systems when issues are present and they need to log in promptly to troubleshoot and restore productivity. However, attackers can use those to access the system at will. In addition, attackers often use all sorts of malware, and once that allows them access to a compromised system, they install a backdoor to allow uninterrupted future access while trying to erase any other traces. That’s the malicious use of a backdoor, and this is how the concept is used by attackers.
A Trojan horse is an application that usually performs a benign operation that the victim is aware of but at the same time additional tasks take place covertly, which the victim is totally oblivious to. For example, a victim is trying to download a third-party application that decompresses files. She searches for such a program using a search engine, and once that is identified, it’s downloaded and installed on the system. If that unverified program is a Trojan horse, it may appear to be performing file compression and decompression in the foreground but in the background may be doing all sorts of other things, like monitoring user keystrokes, stealing credentials, obtaining sensitive information, or installing a backdoor for later uninterrupted access.
Examples of Backdoors and Trojans
Some examples of known malicious applications include
• Back Orifice, Poison Ivy, Dark Comet, AlienSpy, DameWare, and NjRAT (used as remote access tools)
• Sub7, Beast, Gh0st RAT, Doom, SpySender, Deep Throat, WinHole, and Flashback (used as Trojan horses)
• Third-party distributed Joomla and WordPress plugins containing backdoors
• macOS cryptocurrency application named CoinTicker, which used two specific backdoors once installed (EvilOSX and EggShell)
Hardware backdoors have also surfaced in recent years. Examples include
• ZTE devices, which allowed root access using a unique password
• Supermicro purportedly implementing hardware backdoors on devices later being used by Amazon, Apple, and Facebook (among other affected companies)
• Various x86 processor backdoors
Legitimate Tools Used by Attackers for Remote Control
As you have undoubtedly noticed so far, the most effective way for attackers to perform any type of activity, from reconnaissance, to data exfiltration, to remote access control, is to use the same tools that a target organization uses. That makes it quite difficult to distinguish illegitimate from benign traffic, thus allowing attackers to go by unnoticed. Common tools that are used by IT personnel for network administration and remote support that are often abused by attackers include
• RDP (default TCP port 3389)
• VNC/RealVNC/WinVNC (default client TCP port 5500 and server TCP port 5900)
• Nmap
• PowerShell
• Psexec
• TeamViewer (default TCP port 5938)
• LogMeIn Rescue (default TCP ports 80 and 443)
• SSH/Telnet (default TCP ports 22 and 23)
• Windows Credential Editor
• Google Drive/Dropbox (default TCP ports 80 and 443)
• SecureCRT
• ConnectWise (default TCP ports 8040 and 8041)
• Bomgar (default TCP ports 80, 443 and 8200)
An attacker that finds any of these tools or protocols present on a compromised machine or target network will be overjoyed. Now you might think that there’s an easy solution. Don’t use these tools. If you want to invoke the wrath and hatred of all company network and IT teams, you can feel free to try. The fact of the matter is that these tools have legitimate purposes, and most organizations will use them to manage their networks and devices. At the end of the day, you can’t stop remotely administering machines just because an attacker may also be doing that instead of you. You should, however, try to do so in a safe and secure manner. For example, not everyone in the company needs to have nmap installed for testing. When a port scan needs to take place, let your security team know about it so they can disregard the related alerts sourcing from a specific machine or subnet within that time frame of interest.
When administrators use RDP to remotely support machines, they should only be doing it via a handful of machines. RDP shouldn’t be allowed everywhere in the environment.
If you need to securely share files, is a free solution (like a free Dropbox account) the best way to go? In the event any machine is compromised, you can pretty much bet an attacker would use that same tool to exfiltrate data, and the security team might think it’s just a company employee going about his regular day, just sharing files. To make matters worse, various companies use free file sharing services and send out publicly accessible links to third parties, which means that an attacker doesn’t even need to do anything apart from using that link to download files of interest. That’s what an easy day looks like for an attacker.
Another thing to note is that attackers love all these remote access tools because they give them free rein on the machine. They can pretty much perform any task an administrator normally would, like copy/delete files, install applications (if administrator access is available; if not, portable applications can always be used), and drop various backdoors, and the beauty is that most of these tools (like TeamViewer, LogMeIn Rescue, RealVNC, and SecureCRT) run across various platforms.
If you combine the knowledge from this section with some good old-fashioned Shodan reconnaissance, you can see how things can get really bad really quick. Figure 10-1 shows an example of available VNC servers with no authentication enabled, while Figure 10-2 shows various RDP servers exposed to the Internet.
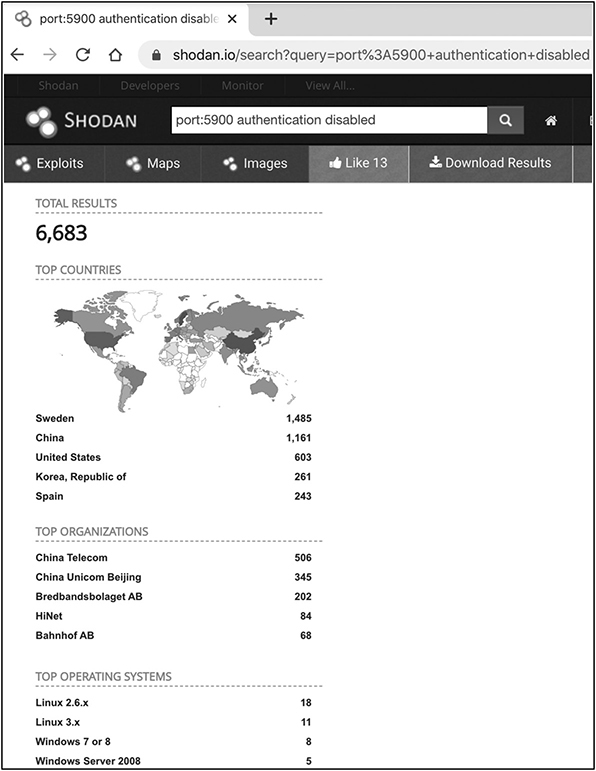
Figure 10-1 VNC servers with no authentication enabled
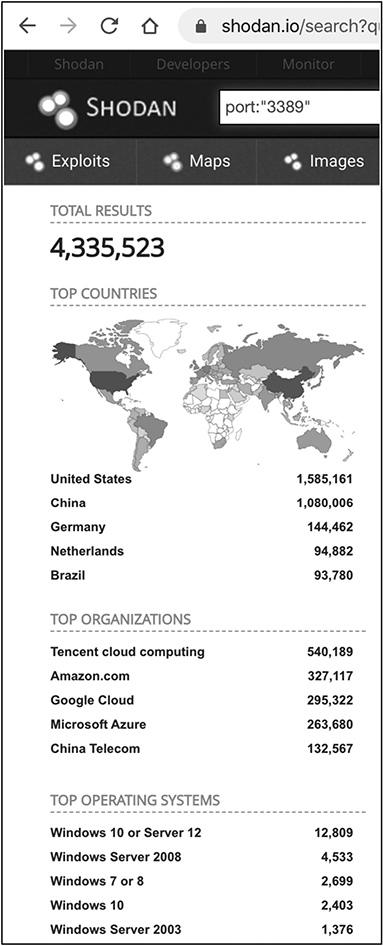
Figure 10-2 Internet-facing RDP servers
The numbers in Figure 10-1 and Figure 10-2 depict a really bleak landscape: almost 7,000 VNC servers with no authentication enabled (meaning those machines are directly accessible from the Internet) and millions of RDP servers exposed online.
If an attacker wants to leverage social engineering to pose as a legitimate IT member, he can contact one of the company employees via phone or e-mail (leveraging OSINT information to identify those) and convince the victim to allow him to install a remote administration tool to apply a critical patch or update guaranteeing to protect against future threats. Figure 10-3 shows an example of politely persuading the victim to browse to www.logmein123.com and download LogMeIn Rescue to allow a remote connection to the system. No administrator access is required for the tool to grant someone remote system access.

Figure 10-3 LogMeIn Rescue download
Other times, attackers install these tools and rename the executables or hide the processes in an effort to get remote access in a more covert way (discussed in more detail in the next section about rootkits) or just use Metasploit’s modules (like Meterpreter’s getgui script, which allows use of Remote Desktop).
Rootkits
Rootkits aim at providing an attacker a covert and continuous presence on a compromised system. They’re very hard to detect, as their primary objectives are covert operation and trace masking. They will try to remove the presence of any files that are used in addition to processes and connections that are generated. Rootkits are very hard to remove, as they can embed themselves deep into a system (like in the case of kernel mode rootkits), and the only way you can really be certain a rootkit is actually removed is by fully erasing and overwriting the hard drive and rebuilding the whole system. The most common distinction of rootkits is user mode and kernel mode rootkits.
OS Rings
Operating systems have operating rings, which designate how applications work, what types of permissions they have over data, and how they interact with the CPU, memory, and various other resources. Figure 10-4 shows a general depiction of the various rings.

Figure 10-4 Operating system rings
The kernel, which is the most restricted part of the operating system and the one with the most privileges, is placed at the center. As you move toward ring 3, privileges decrease and programs have less and less control over the system. Ring 3 is used for any user process. Common Windows and Linux implementations only use rings 0 (kernel applications) and 3 (user applications). That creates an abstraction level which shields the kernel from exposure to applications that shouldn’t be able to access it and interact directly with the underlying hardware.
User Mode Rootkits
User mode rootkits operate at ring 3, where user applications also reside. That means they have limited privileges in comparison to something like kernel drivers. A user mode rootkit runs at the particular user’s level and as such has limited capability. Having said that, though, things drastically change in the case of a compromised administrator account. In that scenario, the rootkit would operate with administrator access over the compromised machine, which is one of the main reasons for not performing any functions as administrator unless explicitly required to do so. And even then, provide temporary administrator access to perform the task at hand and then return to a standard user account.
Windows Rootkits
Windows user mode rootkits use code injection and subsequently hooking to change a function’s regular path of execution so the arbitrary attacker’s code is executed.
The first step for the rootkit (for example, an executable file named HackApp.exe) is to identify a target process (for example, notepad.exe with a PID of 1425). The next step is to allocate the target process memory, using VirtualAllocEx. For that to happen, DLL injection can be used, which is commonly done by one of two methods:
• CreateRemoteThread and LoadLibrary
• CreateRemoteThread and WriteProcessMemory
Either of the two methods will result in a new thread being generated, which will be used to run the injected DLL. Note that using WriteProcessMemory is more covert and is often preferred by attackers.
After code has been successfully injected, attackers commonly employ two main techniques to perform API hooking:
• Import Address Table (IAT) hooking The IAT table is used to load libraries from specific memory locations when API calls are made. The rootkit alters the IAT entries so the program ends up executing the rootkit’s functions instead of the legitimate ones being initially present in the IAT.
• Inline function hooking Entails altering the starting bytes of the destination API functions with code redirecting to malicious instructions.
Linux/Unix Rootkits
Linux user mode rootkits aim at replacing system files and intercepting calls to the system libraries. An attacker can try to replace critical system files with her own malicious versions. Common targets are
• top
• ps
• ifconfig
• netstat
• ls
• crontab
• login
• inetd
• su
• passwd
• pidof
• finger
• find
The result of this activity will be to fool system administrators and security analysts that use any of these utilities to check the system for signs of compromise. For example, how are you going to identify suspicious open ports or hidden files if you’re not actually using the legitimate Linux netstat and ls utilities, but rather the ones that the attacker has loaded on the system? You might say you will replace critical system files with their legitimate versions you keep on a secure location, but the challenge begins with even being aware of anything suspicious taking place.
Kernel Mode Rootkits
Kernel mode rootkits operate at ring 0, which gives them the ability to really embed themselves deep in the system and makes detection and full removal really difficult. Remember that the kernel controls system resources and hardware/software interactions. That means the rootkit doesn’t have to rely on replacing system files, since the attacker has a direct line into the kernel, allowing him to manipulate the system at will. That allows him to perform any task he needs to mask his presence, like hiding files and processes being used or network connections being established. To achieve this, an attacker can modify the kernel and insert malicious system calls, which allow him to direct execution to them, depending on what the originating requests are. Some common techniques used to alter the kernel are
• Device drivers Windows uses device drivers to allow hardware to interact with the operating system. Attackers can install malicious device drivers that allow them to take control of the system. Have you ever had difficulty in finding a driver to accompany some new piece of hardware you recently purchased, like a new network card? Of course you have—we all have. When scouring the Internet to find a driver for that component, you might come across all sorts of software available on third-party websites that actually proves to be a rootkit. That’s why you should never use drivers that aren’t digitally signed by the company that created the hardware in question.
• Kernel modules Linux/Unix uses kernel modules for hardware/OS interaction. Attackers can create new modules (commonly developed in C) that, once loaded on the OS, allow kernel access.
• Direct kernel object manipulation (DKOM) This is a technique used in Windows machines, where the attacker can modify kernel objects residing in memory. Common tasks an attacker can perform include hiding processes and elevating process privileges.
• Memory and hard disk kernel alteration:
• Memory based In Linux, the kernel memory space is located in /dev/kmem and /dev/mem, which is what an attacker would commonly target. In a Windows machine, the system memory map object can be used.
• Hard disk based In Linux, vmlinuz can be altered, since it stores the kernel information (as long as there’s root access). In Windows, ntoskrnl.exe and win32k.sys can be used, but the attacker needs to figure out a way to defeat NT loader (NTDLR) integrity checks taking place each time the system boots.
• Network Driver Interface Specification (NDIS) NDIS works at the data link layer and provides abstraction between network hardware and drivers in addition to the ability to process raw packets. Attackers can take advantage of that to hide any network traffic the rootkit generates.
Table 10-1 shows some examples of known rootkits, along with the affected OS and a short description regarding their operation.

Table 10-1 Rootkit Examples
Malware Wrapping, Packing, and Obfuscation
Malware authors use all sorts of tools and techniques to create malware and evade detection. Some of the most well-known ones are wrapping, encoding, packing, and obfuscation.
• Wrapping A commonly used technique to create Trojan horses. The attacker can use all sorts of wrappers (the software performing the wrapping) and create a trojanized version of various legitimate applications. For example, an attacker can take a legitimate spreadsheet application and use a wrapper to add a keylogger or backdoor into it and send you a file over an e-mail. That e-mail can contain a benign spreadsheet file in addition to the trojanized spreadsheet software. The attacker would then entice you to use that software to open the file, and once that happens the malicious application will be run on the target system.
• Packing Attackers use packers to perform AV evasion, as that makes detection harder. Vmprotect, UPX, and Petite are a few common ones, while SFXCAB can be used to create self-extracting cabinet files.
• Obfuscation This is another technique used to mask malware’s operation and make it hard to detect in addition to allow it to evade certain security tool detection. Examples include
• Base64 encoding Chunks of binary data (3 bytes long) get converted into four characters, with each one being 6 bits. Note that “=” is used for padding, so it’s fairly indicative of base64 encoding being present.
• XOR encoding Logical XOR operation is performed on binary strings.
• Random character addition (' ' , ~) Allows the breaking of key words in malware source code.
• Combinations of these techniques Sometimes malware authors combine techniques to make detection even harder. For example, they apply base64 encoding twice and then XOR on top of it.
Malware Analysis
Security researches working in AV companies usually “eat” malware for breakfast, lunch, and dinner. They have clients all over the world that feed them with suspicious samples that require speedy analysis and detection signature creation, which is where a malware lab comes in handy so you can perform static and dynamic analysis. However, just performing analysis on suspicious files is not always enough. Sometimes, a combination of techniques is required where a full forensic host image needs to be obtained and analyzed, in addition to the machine’s memory artifacts and network traffic in the form of packet captures, in order to get a full picture of what has happened. Then you can effectively use all those indicators of compromise that you just collected and search for them in the rest of your environment.
Static Analysis
Static analysis entails various steps, including
• Verifying a file’s type.
The simplest method would be to use the file command:

As you can see, although the file is supposed to be an executable, file states it’s a text file, so clearly something is not right there.
• Generating file hashes and searching for those in publicly available analysis tools, like Virustotal.com.
The easiest way is to use md5sum in Kali:

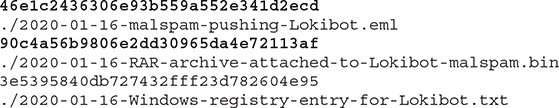
The results are as follows:
• 809605e1089b9a8652f3e381852e93bc 51/71 AV engines identify this file as malicious
• 46e1c2436306e93b559a552e341d2ecd No matches
• 90c4a56b9806e2dd30965da4e72113af 30/58 AV engines identify this file as malicious
How about that file hash that didn’t generate any matches? I have uploaded that file in Virustotal.com and the results are depicted in the following illustration, where you can see that 28/58 AV vendors flag that as malicious.
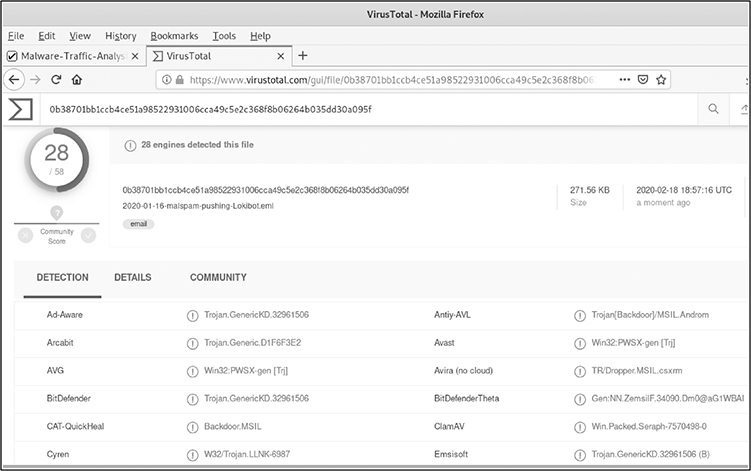
• Inspect any strings that are included in the suspicious files, which often give you an indication of functions, domains, IP addresses, and anything else the malware is using.
You can achieve this by using the string command (note that I have included just the last six lines in the following output):
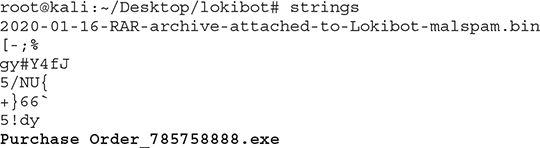
Even if you don’t have that file (Purchase Order_785758888.exe), you can still look around for anything suspicious. A quick online OSINT search returned a malicious sample existing in anyrun and located at https://app.any.run/tasks/939ff4d7-074e-4727-85a7-018c422836c0. That gives you all you need to fully analyze the behavior and verify this is indeed malicious.
You can continue further analysis by identifying indicators of compromise from all files, possibly submitting them to a sandbox and performing various other tasks. In fact, if you want to perform dynamic analysis, you can get much more information, as you would be running malicious files on a machine and can monitor a sample’s behavior, including files, processes, network connections, registry, and everything else taking place on the targeted host.
Traffic Analysis
A packet capture is also contained in the previously mentioned location (https://www.malware-traffic-analysis.net/2020/01/16/index.html) so you can download and load that file in Wireshark for further analysis.
There are three ways you can analyze packet captures. The choice depends on your restrictions, desired outcomes, and how much time you actually have.
• Use Wireshark and perform all analysis manually. (If the packet capture is large and composite, this can be very tedious if you don’t know what to look for.)
• Use tools like Xplico or Network Miner, which have been mentioned earlier in the book. (This is really good if you want to have full control of the process, meaning no online tool is used, and at the same time you want to get quick results.)
• Use an online tool like https://packettotal.com. (This is probably the fastest method, but you are using an online tool, which means you don’t have control over the data.)
Since these samples are publicly available, I will use https://packettotal.com and import the previously mentioned packet capture, which results in the output shown in Figure 10-5.

Figure 10-5 Packet capture uploaded to https://packettotal.com
As you can see, LokiBot was positively identified in the sample. In fact, you can navigate to the rest of the tabs and inspect the network connections, traffic per protocol, and files that were transferred, which is really great information to have in the couple of minutes it took to upload a packet capture.
Memory Analysis
Memory analysis can be performed by all major forensic tools, like FTK, Encase, Blacklight, and X-Ways Forensics. That means you can install any of those tools on a machine and get its memory for further analysis. However, that means you interact with the machine in question, so the usual approach is to take a full forensic image (or just a memory snapshot), which will then be imported into a tool for analysis. If you prefer using an open-source tool to analyze the memory image, you can choose between Rekall and Volatility, which are by far the two most commonly used open-source tools. Let’s look at a combination of tools, which incident responders tend to use.
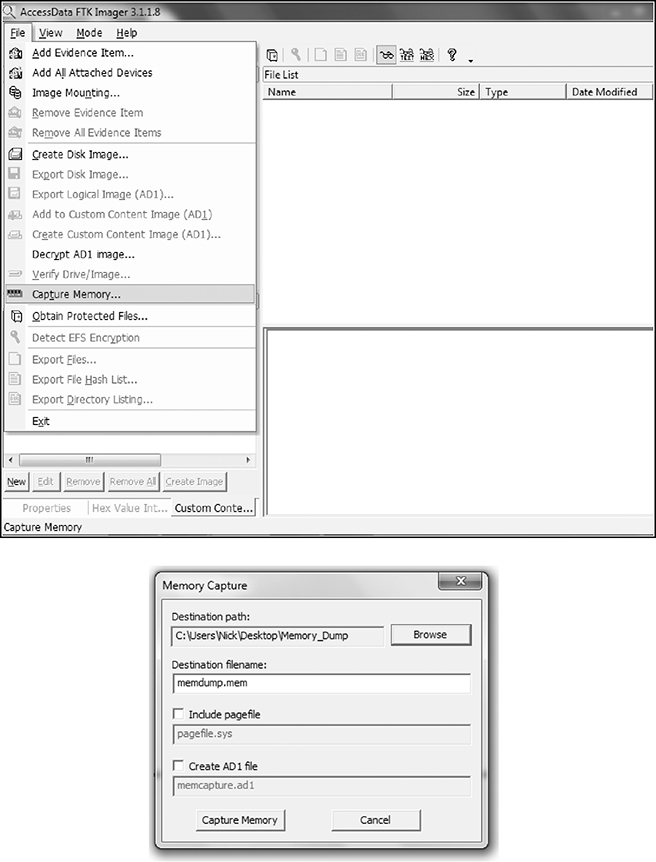
Download FTK Imager Lite (which is freely available from Access Data) and install it on your Windows machine.
After you start the application, select File | Capture Memory and designate a file where the memory dump will be stored, as seen in the following illustrations.
As soon as the memory dump is ready, you can use any tool of your choice to analyze it. Tools like Rekall and Volatility allow you to scan that file and use their modules and plugins to detect anything that might be suspicious and produce results equivalent to running the commands mentioned in Chapter 2, so you can perform in-depth investigations regarding the incident. Let’s see some examples using Volatility.
To install it in Kali, use command apt-get install volatility. After the application is started, a list of available plugins is provided.
imageinfo imageinfo can provide valuable insight about the particular memory dump you’re trying to analyze. Of course, you already know the details of your Windows VM, but sometimes this is very useful to run when working in multiple images or when you’re not sure about the details of each memory dump. In addition, Volatility suggests particular profiles you can use with its plugins.

pslist pslist displays the process name, PID, parent PID, number of threads, and related time frames.
![]()

pstree pstree shows the process tree structure and can aid in easily identifying how a particular process may have been started.

For example, the previous output shows that the command prompt was used to execute ncat.exe (which is the netcat binary) on February 19, 2020, at 09:50:43 UTC. That’s something that you would normally want to analyze and verify if it’s legitimate activity or not.
cmdscan This plugin scans the memory of conhost.exe on Windows 7 to identify commands that attackers may have entered through a console shell. The following example shows three netcat listeners being set up on the machine.

iehistory This plugin can be used to get insight into Internet Explorer and Windows Explorer items, as per the following output:
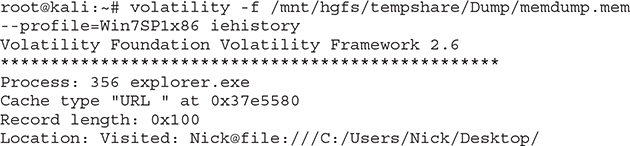
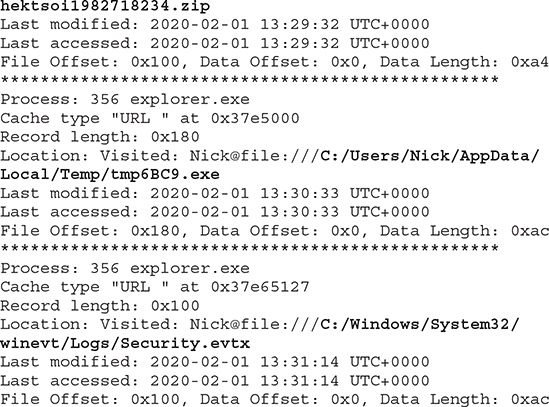
Part of the command output shows a file with an uncommon name being present on the user’s desktop, which was last accessed on 2020-02-01 at 13:29:32. Shortly after that, an executable seems to be present in the Temp folder, while the Security.evtx log is being accessed. This sequence of events would definitely need to be investigated further.
netscan To get a list of network connections and used ports, you can use netscan.
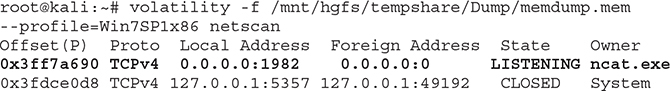
The output shows a netcat listener on the local system’s TCP port 1982.
Defending Against Backdoors, Trojans, and Rootkits
Since rootkits often manipulate critical files, using file integrity checking is paramount to being able to defend against them. Of course, it doesn’t guarantee that each and every file modification will be identified, since any files modified or replaced by the rootkit need to be in the collection of those being verified by the file integrity tool, but it’s still a good start. Examples of tools that support file integrity verification include QualysGuard FIM, Tripwire, Rapid7 InsightIDR, Tanium Integrity Monitor, and LogRhythm.
Host hardening and applying the latest OS updates and patches are also paramount, as not only do they help your systems stay up-to-date regarding any security issues the vendors have identified but also help reduce your overall attack surface, thus limiting the options an attacker has to compromise a system. Those can be combined with enforcing strong security policies about removable devices and remote connectivity (for example, not using any insecure networks) in addition to local/domain administrator access, which should only be used by specific people and only when explicitly required to perform particular tasks. The rule of thumb should be to use standard accounts when standard tasks are being performed.
Using anti-rootkit tools can also help, although their success is really dependent on what checks they perform. Most vendors (like Malwarebytes, Kaspersky, Sophos, and Avast) have such tools that are often available free of charge. Some open-source tools of interest include Lynis (Linux/Unix/macOS/FreeBSD), GMER (Windows), LMD (Linux), and Rkhunter (Unix; also known as rootkit hunter). You can use these tools to periodically scan any machine you think might be acting suspiciously, and even in the case of a verified incident, you can easily obtain a forensic image of the affected machine and, among your other checks, mount its hard drive and run it through some of these tools to see if they uncover anything of note.
Employing endpoint and network behavioral analytics tools is also very useful, as user activity is constantly monitored and compared against pre-established baselines, in addition to any events that don’t align with standard user behavior, which can be indicative of rootkits. Supplementing those with additional tools like up-to-date AV and HIDS/HIPS is also really important to make sure the system is as protected as possible.
Performing a port scan of the affected host from another machine is also a good method, as it allows you to get an external view of the victim host. Even if an attacker tries to hide listening ports and not allow them to be displayed to someone accessing the target locally, an attempt to perform a port scan of that machine from another one on the network has a good chance of displaying those.
If you do identify a rootkit’s presence on a machine, it is highly advisable to get a full forensic image (including the machine’s memory) so you can perform a detailed investigation and thoroughly delete the machine before reinstalling the operating system. Equally enough, it’s also important to determine the root cause of the incident so the same just doesn’t happen all over again.
Chapter Review
Malware comes in various forms, including
• Viruses (macro virus, boot sector, stealth, polymorphic, metamorphic, and multipartite)
• Worms (able to self-propagate within target networks and consume resources)
• Spyware (aiming to get information from a target machine)
• Scareware (attempting to make a user believe malware is already present on the machine)
• Ransomware (not allowing access to a victim’s machine without a ransom being paid)
• Backdoors (allowing access to a system while circumventing access control protocols)
• Trojan horses (performing a seemingly benign operation in the foreground while something malicious is taking place in the background)
Attackers try to use legitimate tools and protocols commonly utilized by IT in an effort to go by unnoticed. Examples include RDP, VNC, Psexec, PowerShell, SSH, Telnet, and various others.
User mode rootkits operate in ring 3 and commonly work by replacing critical system files to mask the attacker’s presence. Kernel mode rootkits operate in ring 0 and are one of the most dangerous types of malware in existence, since they embed themselves deep in a compromised system and allow the attacker to gain full control and mask any traces of his presence. Some methods of performing this include using device drivers and kernel modules, DKOM, memory-based and hard disk–based kernel alteration, and NDIS.
Attackers use wrappers to create Trojan horses and in an effort to make detection harder, also utilize packers and obfuscate malware. On the other hand, the defense uses static and dynamic malware analysis in addition to network and memory forensics to identify and analyze the behavior of malware and extract indicators of compromise that can be used to defend networks against it.
Questions
1. Which of the following viruses commonly attacks executable files in addition to a system’s boot sector?
A. Boot sector
B. Stealth
C. Macro
D. Multipartite
2. Which of the following legitimate tools is often used by attackers as a remote access tool?
A. DameWare
B. LogMeIn Rescue
C. Sub7
D. RDP
3. You try to browse to www.example.com and are presented with a security warning stating 20 security issues have been identified that require your prompt action. Which of the following statements most accurately describes what is going on?
A. Browser warning upon navigating to a potentially suspicious website
B. Trojan is attempting to download on the machine
C. Scareware is present
D. Ransomware infection
4. Which ring do user mode rootkits operate in?
A. 3
B. 5
C. 0
D. 2
5. Which of the following statements about worms is inaccurate?
A. Metamorphic worms are difficult to detect.
B. A worm is unable to self-propagate without human intervention.
C. Worms rapidly consume resources.
D. Winhole isn’t a worm.
6. Which of the following would you use to scan a Windows machine’s hard drive for rootkits?
A. GMER
B. LMD
C. Rootkit Hunter
D. Lynis
7. Which of the following would a kernel mode rootkit use to alter the kernel stored on a Linux machine’s hard disk?
A. /dev/kmem
B. /dev/mem
C. vmlinuz
D. ntoskrnl.exe
8. Which of the following types of malware would be least affected by signature-based AV detection?
A. Polymorphic worm
B. Keylogger
C. Spyware
D. Metamorphic virus
9. Which of the following tools would you use for network traffic analysis if you need to maintain data privacy?
B. Xplico
C. Volatility
D. FTK
10. A Unix-based user mode rootkit needs to mask its network connections. Which of the following would be the most covert way of achieving that?
A. Kernel module manipulation
B. DCOM
C. Remove /bin/netstat
D. Replace /bin/netstat
Answers
1. D. A multipartite virus combines different functions, allowing it to attack executable files in addition to a system’s boot sector.
2. B. LogMeIn Rescue has often been used by attackers to establish remote connections to compromised systems. Note that although RDP was provided as an option, that’s not correct because this is a Microsoft protocol, not a tool. So, although attackers do often use RDP to establish connections to systems, that doesn’t constitute a tool and, as such, makes it a wrong answer to this question.
3. C. Scareware aims at trying to scare a victim by stating there’s some type of security issue with his machine.
4. A. User mode rootkits operate in ring 3, where user applications also reside.
5. B. This statement is incorrect, as a worm is certainly able to self-propagate without human intervention. Remember that viruses are the ones that require human intervention.
6. A. Although all the provided tools can be used for scanning a hard drive for rootkits, only GMER works on Windows.
7. C. A kernel mode rootkit that manipulates a Linux machine’s kernel, stored on the hard disk, will need to manipulate or replace vmlinuz, since that’s where the kernel information is stored.
8. D. A metamorphic virus has the ability to change its code completely and perform different functions each time it infects a new system, thus making signature-based AV detection really inefficient.
9. B. Xplico is really good if you want to have full control of the data, meaning no online tool like packettotal.com is used to allow third-party access to possibly sensitive data.
10. D. Replacing /bin/netstat with a version of netstat the attacker has created will allow her to mask the presence of her rootkit’s network connections while still providing false output to an administrator trying to use netstat. Note that if the binary file is removed altogether, an administrator will be alerted to the fact that something’s wrong, since he won’t be able to use netstat at all.
References and Further Reading