Once the user is validated in terms of who they claim to be, the next aspect, what the user has access to, needs to be ascertained. This process of making sure what the user is allowed to do within the application is called authorization.
In line with authentication architecture, as seen earlier, authorization also has a manager, AccessDecisionManager. Spring Security has three built-in implementations for this: AffirmativeBased, ConsensusBased, and UnanimousBased. AccessDecisionManager works by delegating to a chain of AccessDecisionVoter. Authorization-related Spring Security classes/interfaces are shown in the following diagram:
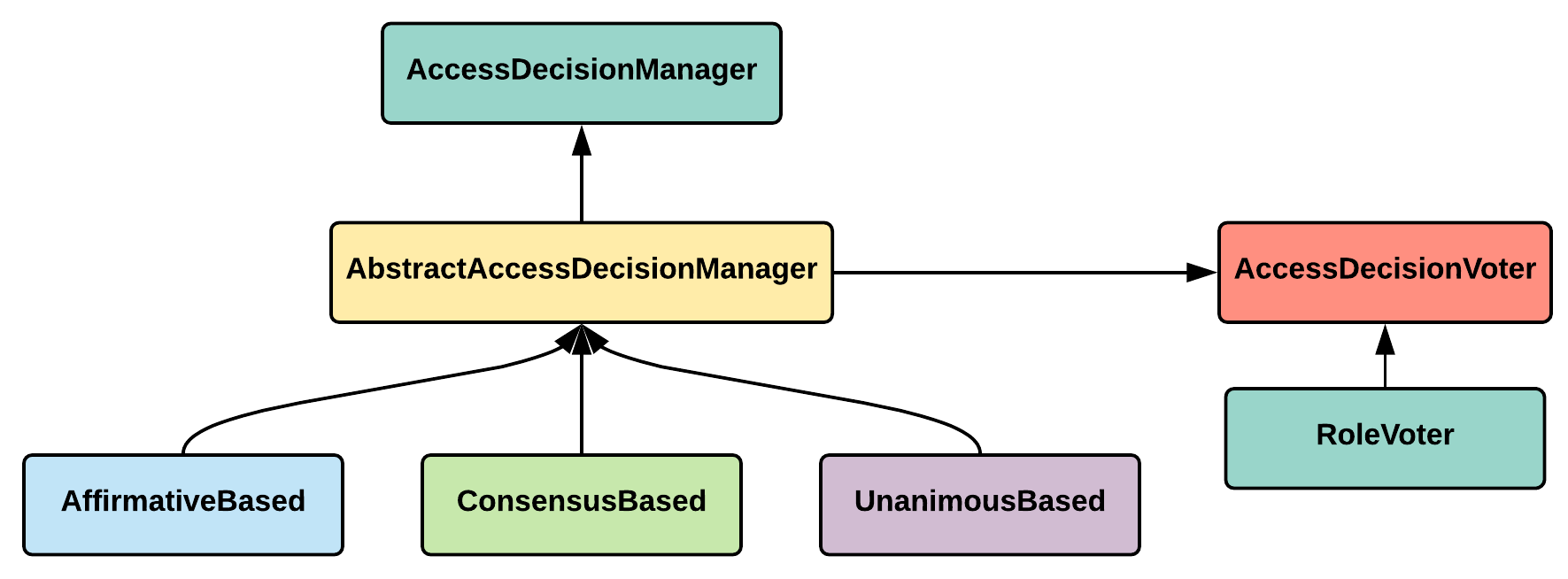
In Spring Security, authorization to a secured resource is granted by invoking voters and then tallying the votes received. The three built-in implementations tally the votes received in different manners:
- AffirmativeBased: If at least one voter votes, the user is given access to the secured resource
- ConsensusBased: If a clear consensus is reached between the voters and their votes, then the user is given access to the secured resource
- UnanimousBased: If all the voters vote, then the user is given access to the secured resource
Spring Security provides two authorization approaches:
- Web URL: Incoming URL (specific URL or regular expression)-based authorization
- Method: Method signature based on which access is controlled
If your serving layer exposes only RESTful endpoints and the data in your application is properly categorized as resources (complying with REST principles), using a Web URL approach can be considered. If your application just exposes endpoints (REST-based, I would call) not really complying with REST principles, you can consider using method-based authorization.
