Chapter 6. Using a firewall and securing EWLM 157
Stateful inspection firewall
A stateful inspection firewall is the most recent firewall technology. It is a combination of the
packet inspection firewall and proxy firewall along with state tables.
State tables are used to
make the firewall aware about related connections. For example, a simple ftp connection has
two parts: the command connection and the data connection. Packet filter firewalls had
problems with ftp, because they had to handle those two connections as separate
connections. Stateful inspection firewalls use state tables to keep track of open connections
and their relationship with other connections. A stateful inspection firewall would know
whether it has an open ftp command connection, then it can allow the data connection to
come back from the server without any additional rules in the firewall.
A stateful inspection firewall has the following advantages:
? Transparency: The application does not have to care about the existence of the firewall.
? High security: State tables add connection awareness for the firewall.
? Performance: It is closer to the packet filter firewall.
A stateful inspection firewall has the following disadvantage:
? Limited application layer awareness: It does not have proxy level capabilities.
The StoneGate firewall is a stateful inspection type of firewall that has some application layer
awareness. One of the StoneGate features is the Protocol Agent, which enables it to see the
application layer data stream and perform actions based on that. The Protocol Agent can
check that the traffic actually is HTTP traffic and not something else—like a hacker trying to
pipe some other traffic to that port. In such a case, the Protocol Agent can disconnect the
hacker traffic.
We chose StoneGate as our example firewall because it does not require any additional
configuration from the EWLM side. Statistics also show that most modern firewalls are
stateful inspection firewalls. Since there are still many existing proxy firewalls, we also explain
how to configure EWLM to work with a proxy firewall.
StoneGate is also the only commercial firewall available that can be used across IBM
xSeries, iSeries, and zSeries machines. If the WebSphere environment or other parts of the
environment are consolidated inside an iSeries or zSeries machine, you can use StoneGate
firewall on those machines too. You do not need an external firewall, because StoneGate
firewall operates as a virtual firewall inside iSeries or zSeries machine.
6.1.2 EWLM firewall support
EWLM supports stateful inspection firewalls, HTTP Proxy, and SOCKS. HTTP Tunneling is
not supported. For stateful inspection firewalls, no additional configuration is required at the
domain manager or managed server. HTTP Proxy requires a configuration change to the
managed server. SOCKS server requires a configuration change to the managed server and
an additional EWLM component called the
Firewall Broker needs to be installed and
configured.
We focus here on stateful inspection and HTTP Proxy since these are the most modern
firewalls and we discuss the SOCKS server since it requires modifications to the EWLM
configuration. In all cases, though, it is important to understand what you need to think about
when placing EWLM into an existing or new firewall environment. In “EWLM configuration in
our ITSO environment” on page 32, we described how to configure the domain manager.
There are three sets of parameters that are important to know when setting up the firewall for
EWLM traffic:
? Domain manager address: -ma

158 IBM Enterprise Workload Manager
? Domain manager port: -mp
? WebSphere Application Server starting port: -wasPort
For the EWLM environment these are the required communication parameters that support
traffic between the managed server and domain manager, traffic between a browser and
EWLM Control Center, and traffic between a browser and WebSphere Admin Console. Since
the wasPort parameter is a starting port for up to fifteen ports that WebSphere Application
Server uses, you need to execute the displayCC command at the domain manager as shown
in Example 6-1, after the createDM command is successful. This provides you with the four
ports assigned to the Admin Console and Control Center traffic.
Example 6-1 displayCC to get assigned ports
$ ./displayCC.sh -ports /opt/EWLMDM -adminUser ibmewlm -adminPW 111111
Processing displayCC -ports request. Please be patient as this may
take a while...
...processing 33% complete
...processing 66% complete
...Ports assigned to EWLM Control Center:
- HTTP 20003
- HTTPS 20004
...Use -changeCC -controlCenterPorts to change these ports if desired.
...Ports assigned to WebSphere Admin Console
- HTTP 20001
- HTTPS 20000
...Use -changeCC -adminConsolePorts to change these ports if desired.
...Port assigned to WebSphere Admin: 20009
...Use -changeCC -adminPort to change this port if desired.
PROCESSING COMPLETE
If you need to check the domain manager port, the displayDM command will show this in the
DomainManagerPort/mp as shown in Example 6-2.
Example 6-2 displayDM command to get assigned ports
# cd /opt/IBM/VE/EWLM/bin
# ./displayDM.sh /opt/EWLMDM
Processing displayDM request. Please be patient as this may take a while...
WLMConfig - configurable property settings:
ViaProxyPort/vp(null)
TracePlugin/tlog(Off)
InterBrokerPort/dp(null)
InterBrokerAddress/da(null)
JmxPort/jp(9092)
FirewallBrokerList/fb(null)
ReportingTrace/rt(250)
ViaProxyHost/va(null)
DomainName/dn(itsoewlm)
JniTrace/jt(250)
SSLKeystore/sslks(null)
ComponentTrace/ct(250)
DomainManagerPort/mp(3333)
MessageLog/ml(250)
Chapter 6. Using a firewall and securing EWLM 159
CommunicationTrace/nt(250)
TraceDistHubBroker/tcomm(0)
SocksPort/sp(null)
FirewallBrokerPort/fp(null)
FailureLimit/fl(50)
SSLKeystorePassword/sslpw(password suppressed)
DomainManagerAddress/ma(9.12.4.142)
AuthorityLevel/auth(None)
ProcessMode/mode(DomainManager)
LBPublicPort/lbp(Off)
LBSecurePort/lbs(Off)
EventTrace/et(250)
TraceLevel/tl(Min)
TestComponent/t(null)
DumpRetentionQuantity/dpn(25)
DumpRetentionAge/dpa(30)
SocksHost/sa(null)
WLMConfig - non-configurable property settings:
ManagedServerFailureTime(null)
ManagedServerIdentity(b05b63dad0404b3a5f460829852701c6)
ManagedServerId(-1)
StatisticsInterval(10)
DomainManagerIdentity(null)
PROCESSING COMPLETE
If using a stateful inspection firewall, rules may need to be added to the firewall for this
additional http traffic. When using a proxy, only the proxy rules needs to be added. Figure 6-1
on page 160 shows an EWLM Management Domain that resides across four security zones.
The highlighted traffic with the domain manager is the only traffic that we need to be
concerned with when considering impacts to firewall setup from an EWLM perspective.
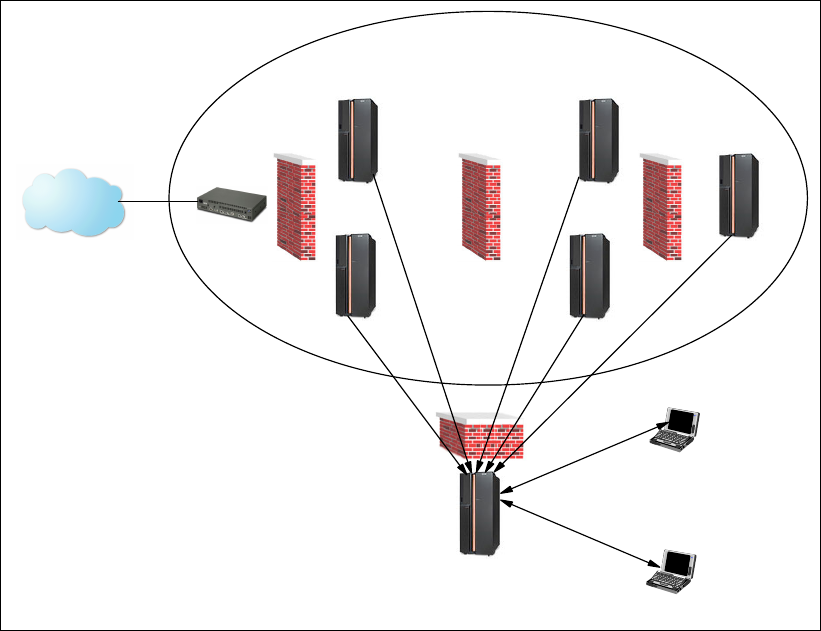
160 IBM Enterprise Workload Manager
Figure 6-1 EWLM network traffic
Stateful inspection and EWLM
In Figure 6-1, if we assume first that the domain manager is in a System Management
security zone protected by a firewall, then from an EWLM perspective, no changes need to be
made to the EWLM configuration. Rules may need to be added to the firewall to allow the
following traffic; we use the ports and addresses discovered from the displayCC and
displayDM commands in Example 6-1 and Example 6-2 respectively:
? Managed server(s) to domain manager at address/port, ewlmdm1.itso.ibm.com/3333
? Control Center browser to UI server at address/port(s),
ewlmdm1.itso.ibm.com/20003,20004
? Admin Console browser to WebSphere Application Server at address/port(s),
ewlmdm1.itso.ibm.com/20001,20002
Proxy and EWLM
Now if we assume that the domain manager is in a System Management security zone
protected by a proxy firewall, EWLM configuration changes must be made for any managed
server that must traverse the proxy before reaching the domain manager. In addition, rules
may need to be added to the proxy for the Control Center and Admin Console as described in
the stateful inspections firewall set up.
The configuration changes that must be made to the managed server are shown in
Figure 6-2. The managed server must be configured with two additional parameters, -va and
-vp, using the changeMS command.
Management Domain
Domain Manager
Control Center
Admin Console
Internet

Chapter 6. Using a firewall and securing EWLM 161
Figure 6-2 HTTP Proxy example
Figure 6-2 shows the managed server communicating with the Proxy server, then the Proxy
communicating with the domain manager on the managed server’s behalf. In order for this
communication to occur, the command shown in Example 6-3 needs to be executed at the
managed server if you add the Proxy server after you configure the managed server for the
first time.
Example 6-3 changeMS command for Windows, Solaris, AIX
changeMS <workingDir>
[-auth [None : ServerSSL : ClientServerSSL]]
[-sslks [path] -sslpw [password]]
[-ma address] [-mp port]
[-va address] [-vp port]
[-nt [value]] [-ct [value]]
[-et [value]] [-ml [value]]
[-tl [value]] [-tlog [class]]
[-dpa [value]] [-dpn [value]]
[-fl [value]]
For i5/OS, you need to use the STRWLM command.
In order to add the Proxy address and port, Example 6-4 shows the custom changeMS
command that would be used based on the addresses and ports in Figure 6-2. To alter the
configuration you need to stop the managed server, issue the changeMS command, and then
restart the managed server with the startMS command.
Example 6-4 changeMS for Proxy support, Windows example
changeMS c:ewlmMS -va 10.2.1.2 -vp 8080
HTTP Proxy
Address: 10.2.1.2
Port of proxy: 8080
Domain Manager
Address: ewlmdm1.itso.ibm.com
Port used by directly connecting
Managed servers:3333
Managed Server
Address: ewlm1.itso.ibm.com
Port used by directly connecting
Managed servers:3333
Properties
-ma ewlmdm1.itso.ibm.com
-mp 3333
-ma ewlmdm1.itso.ibm.com
-mp 3333
-va 10.2.1.2
-vp 8080
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
