Chapter 14
The IT Professional
Objectives
Upon completion of this chapter, you will be able to answer the following questions:
What is the relationship between good communication skills, troubleshooting, and professional behavior?
What are appropriate communication skills and professional behavior while working with a customer?
Why is professional behavior at work important?
What are good customer communications while on a call?
What are the differences between IT and business documentation?
How is change managed in an IT environment?
What are the measures taken by IT organizations to reduce the impact of unplanned outages or data loss?
What are the ethical and legal issues in the IT industry?
What are the procedures for dealing with inappropriate content?
What are the responsibilities of different types of call center technicians?
What are the basic commands and operation of scripts in different environments?
Key Terms
This chapter uses the following key terms. You can find the definitions in the glossary at the end of the book.
active listening skills page 918
change management process page 928
closed-ended questions page 919
conditional statement page 953
digital rights management (DRM) page 940
disaster recovery plan page 931
electronic protected health information (ePHI) page 937
end user license agreement (EULA) page 938
environmental variables page 953
EU General Data Protection Regulation (GDPR) page 936
Health Insurance Portability and Accountability Act (HIPAA) page 937
integrated development environment (IDE) page 949
NIST Special Publication 800-122 page 935
open source licensing page 939
operation and planning documents page 927
Payment Card Industry (PCI) page 936
personally identifiable information (PII) page 935
Phase 1: Network design recovery strategy page 933
Phase 2: Inventory and documentation page 934
Phase 3: Verification page 934
Phase 4: Approval and implementation page 934
protected health information (PHI) page 936
regulatory and compliance policies page 927
Introduction (14.0)
An IT professional must be familiar with the legal and ethical issues that are inherent in the IT industry. There are privacy and confidentiality concerns that you must take into consideration during every customer encounter as you interact with customers in the field, in the office, or over the phone. If you become a bench technician, although you might not interact with customers directly, you will have access to their private and confidential data. This chapter discusses some common legal and ethical issues.
Call center technicians work exclusively over the phone with customers. This chapter covers general call center procedures and the process of working with customers.
As an IT professional, you will troubleshoot and fix computers, and you will frequently communicate with customers and coworkers. In fact, troubleshooting is as much about communicating with the customer as it is about knowing how to fix a computer. In this chapter, you learn to use good communication skills as confidently as you use a screwdriver.
You will also learn about scripting to automate processes and tasks on various operating systems. For example, a script file might be used to automate the process of performing a backup of a customer’s data or run a list of standard diagnostics on a broken computer. A script file can save a technician a lot of time, especially when the same tasks need to be performed on many different computers. You will learn about scripting languages and some basic Windows and Linux script commands. You will also learn key scripting terms such as conditional variables, conditional statements, and loops. You will perform a lab writing very basic scripts.
Communication Skills and the IT Professional (14.1)
This section addresses proper communication techniques for working with customers. It is necessary to explore these topics as a technician because they affect customer service. Developing a rapport and establishing a professional relationship with the customer will be beneficial to your information gathering and problem-solving abilities.
Communication Skills, Troubleshooting, and Professional Behavior (14.1.1)
The ability to communicate well with people at all levels of an enterprise, from IT personnel to the CEO, is essential, and it is just as important in client-facing roles, such as those at an IT help desk or call center. Whether you’re troubleshooting computer issues or managing a team, it’s important to know how to interact and communicate well with others at all levels of the organization. You need to be proficient at explaining issues, talking people through solutions, and managing a team efficiently. This section addresses proper communication techniques for working with customers both internal and external to an organization.
Relationship Between Communication Skills and Troubleshooting (14.1.1.1)
Think of a time when you had to call a repair person to get something fixed. Did it feel like an emergency to you? Perhaps you had a bad experience with a repair person. Are you likely to call that same person to fix a problem again? What could that technician have done differently in his or her communication with you? Did you have a good experience with a repair person? Did that person listen to you as you explained your problem and then ask you questions to get more information? Are you likely to call that person to fix a problem again?
Speaking directly with the customer is usually the first step in resolving a computer problem. To troubleshoot a computer, you need to learn the details of the problem from the customer. Most people who need a computer problem fixed are likely to be feeling some stress. If you establish a good rapport with the customer, the customer might relax a bit. A relaxed customer is more likely to be able to provide the information you need to determine the source of the problem and then fix it.
Follow these guidelines to provide great customer service:
Set and meet expectations, adhere to the agreed upon timeline, and communicate the status with the customer.
If necessary, offer different repair or replacement options.
Provide documentation on the services provided.
Follow up with customers and users after services are rendered to verify their satisfaction.
14.1.1.2 Lab - Technician Resources
![]()
In this lab, you will use the Internet to find resources for a specific computer component. Search online for resources that can help you troubleshoot the component. Refer to the online course to perform this lab.
A technician’s good communication skills are an aid in the troubleshooting process. It takes time and experience to develop good communication and troubleshooting skills. As you gain more hardware, software, and OS knowledge, your ability to quickly identify a problem and find a solution will improve. The same idea applies to developing communication skills: The more you practice good communication skills, the more effective you will become at working with customers. A knowledgeable technician who uses good communication skills will always be in demand in the job market.
As a technician, you have access to several communication and research tools. All these resources can be used to help gather information for the troubleshooting process.
Relationship Between Communication Skills and Professional Behavior (14.1.1.3)
Whether you are talking with a customer on the phone or in person, it is important to communicate well and to present yourself professionally.
If you are talking with a customer in person, the customer can see your body language. If you are talking with a customer over the phone, the customer can hear your tone and inflection. Customers can also sense whether you are smiling when you are speaking with them on the phone. Many call center technicians use a mirror at their desk to monitor their facial expressions.
Successful technicians control their own reactions and emotions from one customer call to the next. A good rule for all technicians to follow is that a new customer call means a fresh start. Never carry your frustration from one call to the next.
Working with a Customer (14.1.2)
Customers who seek support from a computer technician are generally doing so because they are experiencing problems. It is the responsibility of the technician to determine the problem while providing a positive customer experience with consideration, respect, and empathy. Listening is an essential part of communication. Ensure that you listen attentively. This section discusses how to identify customer types and relate to customers to provide quality support.
Know, Relate, and Understand (14.1.2.1)
One of your first tasks as a technician is to identify your customer’s computer problem. Table 14-1 lists the three general rules for talking with a customer: know, relate, and understand.
Table 14-1 The Know, Relate, and Understand Rules of Customer Service
Rule |
Definition |
Example |
Know |
Call the customer by his or her name. Ask if there is any name in particular that the customer prefers you use. |
If the customer tells you her name is Mrs. Johnson, ask if that is what she prefers that you call her. She may say yes, or she may give you her first name. In any case, only use the preferred name with the customer. |
Relate |
Create a one-to-one connection with the customer. |
Find something you may have in common (without giving too much information). If you hear a dog barking in the background of the call and you have a dog, briefly ask about the customer’s dog. If you have had to call customer support for your own computer, mention that you understand how frustrating this can be and that you will do everything you can to help the customer. Do not lose control of the call. |
Understand |
Determine the customer’s level of knowledge about the computer so you can determine how best to communicate with the customer. |
A customer who is very new to computers will not be likely to know all of the jargon that you use every day, so you should use the most common words you can think of to describe aspects of their computer. A more experienced customer probably knows some of the same jargon that you use. |
Active Listening (14.1.2.2)
To better enable you to determine the customer’s problem, practice active listening skills. Allow the customer to tell the whole story. During the time that the customer is explaining the problem, occasionally interject some small words or phrases, such as “I understand,” “Yes,” “I see,” or “Okay.” This behavior lets the customer know that you are there, and that you are listening.
However, a technician should not interrupt s customer to ask a question or make a statement. Doing so would be rude and disrespectful, and it would create tension. Many times in a conversation, you might find yourself thinking of what to say before the other person finishes talking. When you do this, you are not actively listening. Instead, listen carefully when your customers speak, and let them finish their thoughts.
When you ask the customer to explain the problem to you, you are asking an open-ended question. An open-ended question rarely has a simple answer. In explaining the problem to you, the customer probably provided information about what he or she was doing, what he or she was trying to do, and why he or she is frustrated.
After you have listened to the customer explain the whole problem, summarize what the customer has said. This helps the customer know that you have heard and understand the situation. A good practice for clarification is to paraphrase the customer’s explanation by beginning with the words “Let me see if I understand what you have told me.” This is a very effective tool that demonstrates to the customer that you have listened and that you understand.
After you have assured the customer that you understand the problem, you will probably have to ask some follow-up questions. Make sure that these questions are pertinent. Do not ask questions that the customer has already answered while describing the problem. Doing so would irritate the customer and show that you were not listening.
Follow-up questions should be targeted, closed-ended questions based on the information that you have already gathered. Closed-ended questions should focus on obtaining specific information. The customer should be able to answer a closed-ended question with a simple “yes” or “no” or with a factual response, such as “Windows 10.”
Use all the information that you have gathered from the customer to complete a work order.
14.1.2.3 Check Your Understanding - Closed-Ended and Open-Ended Questions

Refer to the online course to complete this activity.
14.1.2.4 Video Demonstration - Active Listening and Summarizing

Refer to the online course to view this video.
Professional Behavior (14.1.3)
Courteous and respectful conduct is always expected in the workplace. This is part of what it means to be a professional. Having a well-groomed appearance and exhibiting a positive attitude are other traits of professional behavior. Customers are put at ease by and prefer to deal with people who display professionalism.
Using Professional Behavior with the Customer (14.1.3.1)
Be positive when communicating with a customer. Tell the customer what you can do. Do not focus on what you cannot do. Be prepared to explain alternative ways that you can help, such as by emailing information and step-by-step instructions or using remote control software to solve the problem.
When dealing with customers, it is sometimes easier to explain what you should not do. The following list describes things that you should not do when talking with a customer:
Do not minimize a customer’s problems.
Do not use jargon, abbreviations, acronyms, and slang.
Do not use a negative attitude or tone of voice.
Do not argue with customers or become defensive.
Do not make culturally insensitive remarks.
Do not disclose any experiences with customers on social media.
Do not be judgmental or insulting or call the customer names.
Avoid distractions and do not interrupt when talking with customers.
Do not take personal calls when talking with customers.
Do not talk to coworkers about unrelated subjects when talking with the customer.
Avoid unnecessary and abrupt phone holds.
Do not transfer a call without explaining the purpose of the transfer and getting customer consent.
Do not make negative remarks about other technicians to the customer.
If a technician is not going to be on time, the customer should be informed as soon as possible.
Tips for Hold and Transfer (14.1.3.2)
When dealing with customers, it is necessary to be professional in all aspects of your role. You must handle customers with respect and prompt attention. When on a telephone call, make sure that you know how to place a customer on hold, as well as how to transfer a customer without losing the call, using the tips in Table 14-2 and Table 14-3.
Table 14-2 How to Put a Customer on Hold
Do |
Do Not |
Let the customer finish explaining the problem. Say that you must put the customer on hold and explain why. Ask the customer for permission to put the call on hold. When the customer agrees, thank the customer and explain that you expect to be back in just a few minutes. Explain what you will be doing during that time. If, after placing the call on hold, it takes longer to return to the customer than expected, quickly get back on the call to explain the situation to the customer. Always thank the customer for his or her patience as you work to fix the problem. |
Interrupt the customer. Put a customer on hold without an explanation. Put a customer on hold without the customer’s consent. Assume that or act as if your time is more valuable than the customer’s time. |
Table 14-3 How to Transfer a Call
Do |
Do Not |
Let the customer finish explaining the problem. Say that you must transfer the call and briefly explain why. Tell the customer the name and number of the person he or she will be speaking with. Ask the customer for permission to transfer the call. When the customer agrees, thank the customer and begin the transfer. Tell the new technician who will be receiving the transfer your name, the ticket number, and the customer’s name. |
Interrupt the customer. Transfer the call without an explanation. Transfer the call without the customer’s consent. Assume that or act as if your time is more valuable than the customer’s time. |
14.1.3.3 Video Demonstration - Hold and Transfer

Refer to the online course to view this video.
14.1.3.4 What Do You Already Know? - Netiquette (14.1.3.4)
As a technician, you should be professional in all communications with customers: respecting people’s time and their privacy, being forgiving of other’s mistakes, and sharing your expert knowledge. For email and text communications, there is a set of personal and business etiquette rules called netiquette. The following list describes some common netiquette dos and don’ts:
Do be pleasant and polite, even if someone is not being pleasant or polite with you.
Do begin emails with an appropriate greeting, even within a thread.
Do check grammar and spelling before you send an email or a text. This is always a good idea. You never know what serious mistake you might have missed.
Do be ethical. This is true for email and texts, just as it is in all your other interactions with people.
Do not send or forward chain letters via email.
Do not send anger-filled, accusatory emails, called “flames.”
Do not reply to flames. Flames never solve a problem but only make it worse.
Do not use all uppercase in email. Using all uppercase letters is considered SHOUTING.
Do not email or text anything you would not say to someone’s face. Not only is doing so unethical, your emails and texts could possibly be traced back to you.
The Customer Call (14.1.4)
Ensuring a good experience for the customer is essential to you, to them, and to your company because you are the initial link between the customer and the company. Good listening and communication skills are necessary to enhance the customer experience while you answer questions and help to resolve the customer’s problems.
Keeping the Customer Call Focused (14.1.4.1)
Part of your job is to focus the customer on the problem during the phone call. When you focus the customer on the problem, you can control the call. The following practices make the best use of your time and the customer’s time:
Use proper language: Be clear and avoid technical language that the customer might not understand.
Listen and question: Listen carefully to the customer and let him or her speak. Use open- and closed-ended questions to learn details about the customer’s problem.
Give feedback: Let the customer know that you understand the problem and develop a friendly and positive conversational manner.
Just as there are many different computer problems, there are many different types of customers. By using active listening skills, you may get some hints about what type of customer is on the phone with you. Is this person very new to computers? Is the person very knowledgeable about computers? Is your customer angry? Do not take any comments personally and do not retaliate with any comments or criticism. If you stay calm with the customer, finding a solution to the problem will remain the focal point of the call. Recognizing certain customer traits can help you manage the call accordingly.
Videos 14.1.4.2 through 14.1.4.6 demonstrate strategies for dealing with different types of difficult customers. The list is not comprehensive, and often, a customer will display a combination of traits. Each video contains a recording of a technician handling a difficult customer type incorrectly, followed by a recording of the same technician handling the customer professionally. A quiz follows each example.
14.1.4.2 Video Demonstration - The Talkative Customer

Refer to the online course to view this video.
14.1.4.3 Video Demonstration - The Rude Customer

Tips for helping a rude customer:
Do listen very carefully, as you do not want to ask the customer to repeat any information.
Do follow a step-by-step approach to determining and solving the problem.
Do try to contact the customer’s favorite technician, if he or she has one, to see if that technician can take the call. Tell the customer, “I can help you right now, or I can see if your preferred technician is available.” If the customer wants the preferred technician and that tech is available, politely transfer the call. If the technician is not available, ask the customer if he or she will wait. If the customer will wait, note that in the ticket.
Do apologize for the wait time and the inconvenience, even if there has been no wait time.
Do reiterate that you want to solve the customer’s problem as quickly as possible.
Do not ask the customer to do any obvious steps if there is any way you can determine the problem without that information.
Do not be rude to the customer, even if he or she is rude to you.
Refer to the online course to view this video.
14.1.4.4 Video Demonstration - The Knowledgeable Customer

Tips for helping a knowledgeable customer:
Do consider setting up a call with a level two technician if you are a level one technician.
Do describe to the customer the overall approach to what you are trying to verify.
Do not follow a step-by-step process with the customer.
Do not ask the customer to check the obvious, such as the power cord or the power switch. Consider suggesting a reboot instead.
Refer to the online course to view this video.
14.1.4.5 Video Demonstration - The Angry Customer

Tips for helping an angry customer:
Do let the customer tell you his or her problem without interrupting, even if the person is angry. This allows the customer to release some of his or her anger before you proceed.
Do sympathize with the customer’s problem.
Do apologize for the wait time or inconvenience.
Do not, if at all possible, put the customer on hold or transfer the call.
Do not spend the call time talking about what caused the problem. It is better to redirect the conversation to solving the problem.
Refer to the online course to view this video.
14.1.4.6 Video Demonstration - The Inexperienced Customer

Tips for helping an inexperienced customer:
Do allow the customer to talk for about one minute.
Do gather as much information about the problem as possible.
Do politely step in to refocus the customer. This is the one exception to the rule of never interrupting a customer.
Do ask as many closed-ended questions as you need to.
Do not encourage non-problem-related conversation by asking social questions such as “How are you today?”
Refer to the online course to view this video.
Operational Procedures (14.2)
Operational procedures are guidelines that companies provide employees to give them the specifics of how a task is to be accomplished. They help employees understand the company’s expectations of what needs to happen to ensure that work gets done efficiently and with predictability.
Documentation (14.2.1)
Documentation has a multitude of purposes, including but not limited to providing a mechanism for relaying information to coworkers. It can be used in legal matters, it is a way to record problems and the solutions for future use, and more. Documentation is another way to provide a good communication channel.
Documentation Overview (14.2.1.1)
Different types of organizations have different operating procedures and processes that govern business functions. Documentation is the main way of communicating these processes and procedures to employees, customers, suppliers, and others.
Purposes for documentation include
Providing descriptions for how products, software, and hardware function through the use of diagrams, descriptions, manual pages, and knowledge base articles
Standardizing procedures and practices so that they can be repeated accurately in the future
Establishing rules and restrictions on the use of the organization’s assets, including acceptable use policies for Internet, network, and computer usage
Reducing confusion and mistakes, saving time and resources
Complying with governmental or industry regulations
Training new employees or customers
Keeping documentation up to date is just as important as creating it. Updates to policies and procedures are inevitable, especially in the constantly changing environment of information technology. Establishing a standard timeframe for reviewing documents, diagrams, and compliance policies ensures that the correct information is available when it is needed.
IT Department Documentation (14.2.1.2)
Keeping documentation current is challenging for even the best-managed IT departments. IT documentation can come in many different forms, including diagrams, manuals, configurations, and source code. In general, IT documentation falls into four broad categories:
-
Acceptable use policies that describe how technology is to be used within the organization
Security policies that outline all aspects of information security, including password policies and security incident response methods
Regulatory compliance policies that describe all federal, state, local, and industry regulations that apply to the organization
Disaster recovery policies and procedures that provide detailed plans for what must be done to restore services in the event of an outage
Operation and planning documents:
IT strategy and planning documents that outline the near- and long-term goals of the department
Proposals for future projects and project approvals
Meeting presentations and minutes
Budgets and purchasing records
Inventory management, including hardware and software inventories, licenses, and management methods, such as the use of asset tags and bar codes
-
User requests for changes, updates, or new services
Software design and functional requirements, including flow diagrams and source code
Logical and physical network topology diagrams, equipment specifications, and device configurations
Change management forms
User testing and acceptance forms
-
Features, functions, and operation of software, hardware, and services provided by the IT department
End-user manuals for hardware and software
Help desk ticket database with ticket resolutions
Searchable knowledge base articles and FAQs
Regulatory Compliance Requirements (14.2.1.3)
Federal, state, local, and industry regulations can have documentation requirements over and above what is normally documented in the company’s records. Regulatory and compliance policies often specify what data must be collected and how long it must be retained. A few of the regulations may have implications on internal company processes and procedures. Some regulations require keeping extensive records regarding how the data is accessed and used.
Failure to comply with laws and regulations can have severe consequences, including fines, termination of employment, and even incarceration of offenders. It is important to know how laws and regulations apply to your organization and to the work you perform.
14.2.1.4 Check Your Understanding - Documentation

Refer to the online course to complete this activity.
Change Management (14.2.2)
Change management in the context of this section refers to IT change management. IT change events are a regular function of the IT infrastructure not because of things like unplanned outages, problems, or mandatory design adjustments to increase efficiency and performance but because of all the system dependencies within the infrastructure. Careful planning needs to take place so a change happens with the least possible impact on network service or business operations.
Change Control Process (14.2.2.1)
Controlling changes in an IT environment can be difficult. Changes can be as minor as replacing a printer or as important as upgrading all the enterprise servers to the latest operating system version. Most larger enterprises and organizations have change management procedures in place to ensure that installations and upgrades go smoothly.
A good change management process can prevent business functions from being negatively impacted by the updates, upgrades, replacements, and reconfigurations that are a normally part of IT operations. Change management usually starts with a change request from a stakeholder or from within the IT organization itself. Most change management processes include the following:
Identification: What is the change? Why is it needed? Who are the stakeholders?
Assessment: What business processes are impacted by this change? What are the costs related to and resources necessary for implementation? What risks are associated with making (or not making) this change?
Planning: How long will it take to implement this change? Will there be downtime involved? What rollback or recovery process will be used if the change fails?
Approval: Who must authorize this change? Has approval to proceed with the change been obtained?
Implementation: How are stakeholders notified? What are the steps to complete the change, and how will the results be tested?
Acceptance: What are the acceptance criteria, and who is responsible for accepting the results of the change?
Documentation: What updates are required to change logs, implementation steps, or IT documents because of this change?
All the results of the process are recorded on a change request or change control document that becomes part of the IT documentation. Some expensive or complex changes that impact necessary business functions may require the approval of a change board or committee before work can begin.
Figure 14-1 is an example of a change control worksheet.


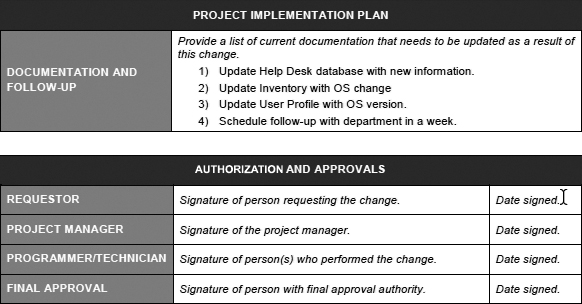
Figure 14-1 Change Control Worksheet Example
Disaster Prevention and Recovery (14.2.3)
Businesses increasingly rely on information systems to function. An IT disaster recovery plan (IT DRP) should describe the strategy for protecting the business IT infrastructure from negative events of any type. There should be procedures to follow to allow the IT infrastructure and operations to get back up and running quickly.
Disaster Recovery Overview (14.2.3.1)
We often think of a disaster as being something catastrophic, such as the destruction caused by an earthquake, a tsunami, or a wildfire. In information technology, a disaster can include anything from natural disasters that affect the network structure to malicious attacks on the network itself. The impact of data loss or corruption due to unplanned outages caused by hardware failure, human error, hacking, or malware can be significant.
A disaster recovery plan is a comprehensive document that describes how to restore operation quickly and keep critical IT functions running during or after a disaster occurs. The disaster recovery plan can include information such as offsite locations where services can be moved, information on replacing network devices and servers, and backup connectivity options.
Some services may even need to be available during the disaster in order to provide information to IT personnel and updates to others in the organization. Services that might need to be available during or immediately after a disaster include:
Web services and Internet connectivity
Data stores and backup files
Directory and authentication services
Database and application servers
Telephone, email, and other communication services
In addition to having a disaster recovery plan, most organizations take steps to ensure that they are ready in case a disaster occurs. These preventive measures can ease the impact of unplanned outages on the operation of the organization.
Preventing Downtime and Data Loss (14.2.3.2)
Some business applications cannot tolerate any downtime. Such businesses use multiple data centers capable of handling all data processing needs, which run in parallel and have data mirrored or synchronized between the centers. Often, these businesses run their applications from cloud servers to minimize the impact of physical damage to their sites.
Data and Operating System Backup
Even the best disaster recovery procedures cannot restore services quickly if there are no current backups of data and operating system environments. It is much easier to restore data from a reliable backup than it would be to re-create it. There are generally two types of backup done for disaster recovery purposes: image backups and file backups. Image backups record all the information stored on the computer at the time the image is created, and file backups store only the specific files indicated at the time the backup is run. No matter which type of backup is made, it is critical that the restore process be tested frequently to ensure that it will function when it is needed.
Backup files need to be available to the people who will be responsible for restoring and recovering the systems after an unplanned outage. Backup media can be stored securely offsite, or backup files can be stored in an online location, such as a cloud service provider. Locally stored files may be accessible if communication service outages prevent Internet access. Backup files stored online have the benefit of being accessible from anywhere the Internet is available. Table 14-4 outlines the advantages and disadvantages of cloud and local backups.
Table 14-4 Cloud and Local Backups Comparison
Backup Storage Method |
Advantages |
Disadvantages |
Cloud backups |
Reliability: Cloud providers use the latest technology and can offer other related services, such as compression and encryption. Scalability: Cloud backups scale easily, so a business doesn’t need to worry that it doesn’t have the storage capacity or media if the data files increase in size. Accessibility: Cloud backup files are available anywhere the Internet is accessible. |
Time: Backing up data and restoring files are dependent on the speed and reliability of the Internet connectivity. In the event of a regional natural disaster, network congestion may cause intermittent loss of connectivity. Discontinuation of service or increase in pricing. |
Local control of where data files reside and who has access to them. Accessibility: In the event of a disaster that impacts network connectivity, locally stored backup media may be more accessible. Speed of file restores: Locally attached media restore times are usually faster than over the Internet. |
Scalability: Keeping local backups often requires manual intervention and handling of the media. The media itself has storage limitations that may cause issues as data file sizes increase. Offsite storage requirements, fire protection, and environmental controls. |
Power and Environment Controls
Keeping the power on for a data center or for critical communications infrastructure can prevent data loss caused by interruptions or spikes in electrical power delivery. Sometimes even minor natural disasters can cause power outages that last longer than 24 hours. Small surge protectors and uninterruptible power supplies (UPSs) can prevent damage from minor power problems, but for larger outages, a generator might be required. Data centers require power not only for the computing equipment but also for air conditioning and fire suppression. Large UPS units can keep a data center operational until a fuel-powered generator comes online.
Elements of a Disaster Recovery Plan (14.2.3.3)
The first step in creating a disaster recovery plan is to identify the most critical services and applications that will need to be restored quickly. That information should be used to create a disaster recovery plan. Creating and implementing a disaster recovery plan consists of five major phases, as shown in Figure 14-2 and described in the list that follows.

Figure 14-2 Elements of a Disaster Recovery Plan
Phase 1: Network design recovery strategy: Analyze the network design. Some aspects of the network design that should be included in the disaster recovery are:
Whether the network is designed to survive a major disaster, whether there are backup connectivity options, and whether there is redundancy in the network design
Availability of offsite servers or cloud providers that can support applications such as email and database services
Availability of backup routers, switches, and other network devices
Location of services and resources that the network needs, whether they are spread over a wide geography, and whether backups are easily accessible in an emergency
Phase 2: Inventory and documentation: Create an inventory of all locations, devices, vendors, services used, and contact names. Verify cost estimates that are created in the risk assessment step.
Phase 3: Verification: Create a verification process to prove that the disaster recovery strategy works. Practice disaster recovery exercises to ensure that the plan is up to date and workable.
Phase 4: Approval and implementation: Obtain senior management approval and develop a budget to implement and maintain the disaster recovery plan.
Phase 5: Review: After the disaster recovery plan has been implemented for a year, review the plan. Information in the plan must be kept up to date, or critical services may not be restored in the event of a disaster.
14.2.3.4 Check Your Understanding - Disaster Recovery

Refer to the online course to complete this activity.
Ethical and Legal Considerations (14.3)
Many legal and ethical issues arise as companies use computers and computer networks in all aspects of business. All types of data are collected and stored about business processes as well as customers and employees. During criminal investigations, audits, and litigation, that data may be required as part of a legal action. This section discusses different ways of handling data for legal purposes.
IT personnel often have access to confidential data and knowledge about individuals’ and companies’ networks and systems. The work of an IT professional puts him or her in a position that involves many ethical decisions and challenges, especially involving privacy and confidentiality issues.
Ethical and Legal Considerations in the IT Profession (14.3.1)
For information technology professionals, it is just as important to study ethical and legal concerns as technical skills. It is important to recognize the responsibility and ethical obligations that come from having access to customers’ personal and professional information.
Ethical and Legal Considerations in IT (14.3.1.1)
When you are working with customers and their equipment, you should observe some general ethical customs and legal rules. These customs and rules often overlap.
You should always have respect for your customers, as well as for their property. Computers and monitors are property, and property also includes any information or data that might be accessible, including:
Emails
Phone lists and contact lists
Records or data on the computer
Hard copies of files, information, or data left on a desk
Before accessing computer accounts, including the administrator account, get the permission of the customer. During the troubleshooting process, you might have gathered some private information, such as usernames and passwords. If you document this type of private information, you must keep it confidential. Divulging customer information to anyone else is unethical and might also be illegal. Do not send unsolicited messages to a customer. Do not send unsolicited mass mailings or chain letters to customers. Never send forged or anonymous emails. Legal details of customer information are usually covered under the service-level agreement (SLA). The SLA is a contract between a customer and a service provider that defines the service or goods the customer will receive and the standards with which the provider must comply.
Personally Identifiable Information (PII) (14.3.1.2)
Take particular care to keep personally identifiable information (PII) confidential. PII is any data that could potentially identify a specific individual. NIST Special Publication 800-122 defines PII as “any information about an individual maintained by an agency, including (1) any information that can be used to distinguish or trace an individual’s identity, such as name, social security number, date and place of birth, mother’s maiden name, or biometric records; and (2) any other information that is linked or linkable to an individual, such as medical, educational, financial, and employment information.”
Examples of PII include, but are not limited to
Names, such as full name, maiden name, mother’s maiden name, or alias
Personal identification numbers, such as Social Security number (SSN), passport number, driver’s license number, taxpayer identification number, financial account or credit card number, and address information, such as street address or email address
Personal characteristics, including photographic images (especially of the face or other identifying characteristics), fingerprints, handwriting, or other biometric data (for example, retina scan, voice signature, facial geometry)
PII violations are regulated by several organizations in the United States, depending on the type of data. The EU General Data Protection Regulation (GDPR) also regulates how data is handled for personal data, including financial and healthcare information.
Payment Card Industry (PCI) (14.3.1.3)
Payment Card Industry (PCI) information is considered personal information that needs to be protected. We often hear news about breaches of credit card information that impact millions of users. Often it is days or weeks before a merchant realizes a breach has occurred. All businesses and organizations, large or small, need to adhere to strict standards to protect consumer information.
The PCI Security Standards Council was formed in 2005 by the five major credit card companies in an effort to protect account numbers, expiration dates, and magnetic strip and chip data for transactions around the globe. The PCI Security Standards Council partners with organizations, including NIST, to develop standards and security procedures around these transactions.
In one of the worst breaches in history, malware infected the point-of-sale system of a major retailer, impacting millions of consumers. This breach could potentially have been prevented with adequate software and policies for data breach prevention. As an IT professional, you should be aware of PCI compliance standards.
For more information on the PCI Security Standards Council, visit www.pcisecuritystandards.org.
Protected Health Information (PHI) (14.3.1.4)
Protected health information (PHI) is a particular form of PII that needs to be secured and protected. PHI includes patient names, addresses, dates of visits, telephone and fax numbers, and email addresses. With the move from paper records to electronic records, electronic protected health information (ePHI) is also regulated. Penalties for breaches of PHI and ePHI are very severe and are subject to the Health Insurance Portability and Accountability Act (HIPAA).
Examples of ePHI breaches are easily found with an Internet search. Unfortunately, a breach may be undetected for months. Some breaches have occurred from one person giving out information to an unauthorized person. Human error can cause violations. For example, accidentally faxing health information to the wrong party is a violation. Sophisticated attacks also lead to violations. Recent phishing attacks on a California-based health plan went undetected for almost a month before the plan recognized it and then notified 37,000 patients that their data had been breached. As an IT professional, you should be aware of protecting PHI and ePHI.
For more information about PHI and ePHI, visit www.hhs.gov and search for PHI.
Search the Internet for the regulatory agencies in your state, country, or province.
14.3.1.5 Lab - Investigate Breaches of PII, PHI, PCI
![]()
In this lab, you will investigate breaches of PII, PHI, and PCI.
Legal Considerations in IT (14.3.1.6)
The laws in different countries and legal jurisdictions vary, but generally, actions such as the following are considered to be illegal:
It is not permissible to make any changes to system software or hardware configurations without customer permission.
It is not permissible to access a customer’s or coworker’s accounts, private files, or email messages without permission.
It is not permissible to install, copy, or share digital content (including software, music, text, images, and video) in violation of copyright and software agreements or applicable law. Copyright and trademark laws vary between states, countries, and regions.
It is not permissible to use a customer’s company IT resources for commercial purposes.
It is not permissible to make a customer’s IT resources available to unauthorized users.
It is not permissible to knowingly use a customer’s company resources for illegal activities. Criminal or illegal use typically includes obscenity, child pornography, threats, harassment, copyright infringement, Internet piracy, university trademark infringement, defamation, theft, identity theft, and unauthorized access.
It is not permissible to share sensitive customer information. You are required to maintain the confidentiality of this data.
This list is not exhaustive. All businesses and their employees must know and comply with all applicable laws of the jurisdiction in which they operate.
Licensing (14.3.1.7)
As an IT technician, you might encounter customers who are using software illegally. It is important that you understand the purposes and types of common software licenses in case you determine that a crime has been committed. Your responsibilities are usually covered in your company’s corporate end-user policy. In all instances, you must follow security best practices, including documentation and chain of custody procedures.
A software license is a contract that outlines the legal use or redistribution of a piece of software. Most software licenses grant end-user permission to use one or more copies of the software. They also specify the end user’s rights and restrictions. This ensures that the software owner’s copyright is maintained. It is illegal to use licensed software without an appropriate license.
Personal License
Most software is licensed rather than sold. Some personal software licenses regulate how many computers can run a copy of the software. Other licenses specify the number of users who can access the software. Most personal software licenses allow you to run the program on only one machine. Some personal software licenses allow you to copy the software onto multiple computers. These licenses usually specify that the copies cannot be used at the same time.
One example of a personal software license is an end user license agreement (EULA). A EULA is a license between the software owner and an individual end user. The end user must agree to accept the terms of the EULA. Sometimes, accepting a EULA is as simple as opening the physical package that holds a CD of the software or downloading and installing the software. A common example of agreeing to a EULA occurs when updating the software on tablets and smartphones. The end user must agree to accept the EULA when updating the operating system or installing or updating software found on the device by selecting I Accept the License Terms and clicking Accept, as shown in Figure 14-3.
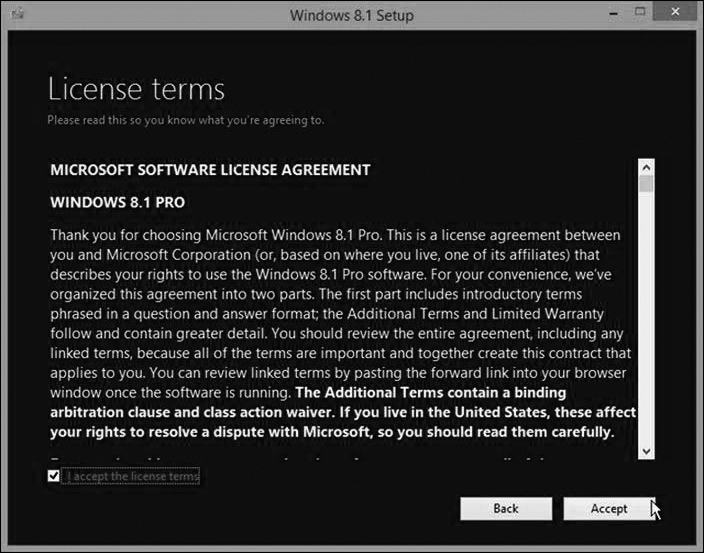
Figure 14-3 Windows 8.1 License Agreement
Enterprise License
An enterprise license is a software site license held by a company. Typically with an enterprise license, the company pays for its employees to use the software. This software does not need to be registered every time it is installed on another employee’s computer. In some cases, the employees may need to use a password to activate each copy of the license.
Open Source License
Open source licensing is a copyright license for software that allows developers to modify and share the source code that runs the software. In some cases, an open source license means that the software is free to all users. In other cases, it means that the software can be purchased. In both instances, users have access to the source code. Some examples of open source software are Linux, WordPress, and Firefox.
If the open source licensed software is being used by an individual who is not using it to make money, that person would have a personal license for that software. Personal software licenses are often free or low cost.
Commercial Software License
If a person uses software to make money, that person needs to pay for a commercial license. Commercial software licenses are usually more expensive than personal licenses.
Digital Rights Management
In addition to licensing, there is also software that helps control the illegal use of software and content. Digital rights management (DRM) software is designed to prevent illegal access to digital content and devices. DRM is used by hardware and software manufacturers, publishers, copyright holders, and individuals. Their purpose for using DRM is to prevent copyrighted content from being copied freely. This helps the copyright holder to maintain control of the content and to be paid for access to that content.
14.3.1.8 Check Your Understanding - Licensing

Refer to the online course to complete this activity.
Legal Procedures Overview (14.3.2)
The laws in different countries and legal jurisdictions vary, but there are many issues considered to be illegal that are held in common. Understanding the laws within the jurisdiction you are working in is paramount to performing your job properly.
Computer Forensics (14.3.2.1)
Data from computer systems, networks, wireless communications, and storage devices may need to be collected and analyzed in the course of a criminal investigation. The collection and analysis of data for this purpose is called computer forensics. The process of computer forensics encompasses both IT and specific laws to ensure that any data collected is admissible as evidence in court.
Depending on the country, illegal computer or network usage may include
Identity theft
Using a computer to sell counterfeit goods
Using pirated software on a computer or network
Using a computer or network to create unauthorized copies of copyrighted materials, such as movies, television programs, music, and video games
Using a computer or network to sell unauthorized copies of copyrighted materials
Pornography
This is not an exhaustive list. Becoming familiar with the signs of illegal computer or network usage can help you identify situations where you suspect illegal activity and report them to the authorities.
Data Collected in Computer Forensics (14.3.2.2)
Two basic types of data are collected when conducting computer forensics procedures:
Persistent data: Persistent data is stored on a local drive, such as an internal or external hard drive, or an optical drive. When the computer is turned off, this data is preserved.
Volatile data: RAM, cache, and the Registry contain volatile data. Data in transit between a storage medium and a CPU is also volatile data. If you are reporting illegal activity or are part of an incident response team, it is important to know how to capture this data because it disappears as soon as the computer is turned off.
In Figure 14-4, the computer forensic expert is examining a hard drive for damage before inspecting it for persistent data.

Figure 14-4 Computer Forensics
Cyber Law (14.3.2.3)
There is no single law known as a cyber law. Cyber law is a term used to describe the international, regional, country, and state laws that affect computer security professionals. IT professionals must be aware of cyber law so that they understand their responsibility and their liability in relation to cybercrimes.
Cyber law explains the circumstances under which data (evidence) can be collected from computers, data storage devices, networks, and wireless communications. It can also specify the manner in which this data can be collected. In the United States, cyber law has three primary elements:
Wiretap Act
Pen/Trap and Trace Statute
Stored Electronic Communication Act
IT professionals should be aware of the cyber law in their country, region, or state.
First Response (14.3.2.4)
First response is the term used to describe the official procedures employed by people who are qualified to collect evidence. System administrators, like law enforcement officers, are usually the first responders at potential crime scenes. Computer forensics experts are brought in when it is apparent that there has been illegal activity.
Routine administrative tasks can affect the forensic process. If the forensic process is improperly performed, evidence that has been collected might not be admissible in court.
As a field or bench technician, you may be the person who discovers illegal computer or network activity. If this happens, do not turn off the computer. Volatile data about the current state of the computer can include programs that are running, network connections that are open, and users who are logged in to the network or to the computer. This data helps determine a logical timeline of the security incident. It may also help to identify those responsible for the illegal activity. This data could be lost when the computer is powered off.
Be familiar with your company’s policy regarding cybercrimes. Know who to call, what to do and, just as importantly, know what not to do.
Documentation (14.3.2.5)
The documentation required by a system administrator and a computer forensics expert is extremely detailed. They must document not only what evidence was gathered but how it was gathered and with what tools. Incident documentation should use consistent naming conventions for forensic tool output. Stamp logs with the time, date, and identity of the person performing the forensic collection. Document as much information about the security incident as possible. These best practices provide an audit trail for the information collection process.
Even if you are not a system administrator or computer forensics expert, it is a good habit to create detailed documentation of all the work you do. If you discover illegal activity on a computer or network on which you are working, at a minimum, document the following:
Initial reason for accessing the computer or network
Time and date
Peripherals that are connected to the computer
All network connections
Physical area where the computer is located
Illegal material that you have found
Illegal activity that you have witnessed (or that you suspect has occurred)
Which procedures you have executed on the computer or network
First responders want to know what you have done and what you have not done. Your documentation may become part of the evidence in the prosecution of a crime. If you make additions or changes to this documentation, it is critical that you inform all interested parties.
Chain of Custody (14.3.2.6)
For evidence to be admitted in legal proceedings, it must be authenticated. A system administrator may testify about the evidence that was collected. He or she must also be able to prove how this evidence was collected, where it has been physically stored, and who has had access to it between the time of collection and its entry into the court proceedings. This is known as the chain of custody. To prove the chain of custody, first responders have documentation procedures in place to track the collected evidence, such as evidence bags, as shown in Figure 14-5. These procedures also prevent evidence tampering so that the integrity of the evidence can be ensured.

Figure 14-5 Evidence Bag
Incorporate computer forensics procedures into your approach to computer and network security to ensure the integrity of the data. These procedures help you capture necessary data in the event of a network breach. Ensuring the viability and integrity of the captured data helps you prosecute the intruder.
14.3.2.7 Check Your Understanding - Legal Procedures Overview

Refer to the online course to complete this activity.
Call Center Technicians (14.4)
Call center technicians are required to have strong written and verbal communication skills in addition to technical skills. This section describes the call center environment and the responsibilities of a call center technician.
Call Centers, Level One and Level Two Technicians (14.4.1)
Call center technicians answer customer calls and analyze, troubleshoot, and resolve technical issues for customers. Different types of calls are handled by different levels of technicians, providing a basic level to an intermediate level of technical support.
Call Centers (14.4.1.1)
A call center environment is usually very organized and professional. Customers call in to receive help for a specific computer-related problem. The typical workflow of a call center starts with calls from customers displayed on a callboard. Level one technicians answer these calls in the order in which the calls arrive. If the level one technician cannot solve the problem, it is escalated to a level two technician. In all instances, the technician must supply the level of support that is outlined in the customer’s service-level agreement (SLA).
A call center might exist within a company and offer service to the employees of that company as well as to the customers of that company’s products. Alternatively, a call center might be an independent business that sells computer support as a service to outside customers. In either case, a call center is a busy, fast-paced work environment, often operating 24 hours a day.
Call centers tend to have a large number of cubicles, as shown in Figure 14-6. Each cubicle has a chair, at least one computer, a phone, and a headset. The technicians working at these cubicles have varied levels of experience with computers, and some specialize in certain types of computers, hardware, software, or operating systems.

Figure 14-6 Call Center Illustration
As calls come in to the call center, they must be prioritized so that the most urgent calls are resolved first. Table 14-5 is an example of a call prioritization system.
Table 14-5 Call Prioritization
Name |
Definition |
Priority |
Down |
The company cannot operate any of its computer equipment. |
1 (Most urgent) |
Hardware |
One (or more) of the company’s computers is not functioning correctly. |
2 (Urgent) |
Software |
One (or more) of the company’s computers is experiencing software or operating system errors. |
2 (Urgent) |
Network |
One (or more) of the company’s computers cannot access the network. |
2 (Urgent) |
Enhancement |
There has been a request from the company for additional computer functionality. |
3 (Important) |
All the computers in a call center have support software. The technicians use this software to manage many of their job functions. Technicians use support software to complete the following tasks:
Log and track incidents: The software might manage call queues, set call priorities, assign calls, and escalate calls.
Record contact information: The software might store, edit, and recall customer names, email addresses, phone numbers, location, websites, fax numbers, and other information in a database.
Research product information: The software might provide technicians with information regarding the products supported, including features, limitations, new versions, configuration constraints, known bugs, product availability, links to online help files, and other information.
Run diagnostic utilities: The software might have several diagnostic utilities, including remote diagnostic software, in which the technician can take over a customer’s computer while sitting at a desk in the call center.
Research a knowledge base: The software might contain a knowledge database that is programmed with common problems and their solutions. This database might grow as technicians add their own records of problems and solutions.
Collect customer feedback: The software might collect customer feedback regarding satisfaction with the call center’s products and services.
Level One Technician Responsibilities (14.4.1.2)
Call centers sometimes have different names for level one technicians. These technicians might be known as level one analysts, dispatchers, or incident screeners. Regardless of the title, the responsibilities of a level one technician are fairly similar from one call center to the next.
The primary responsibility of a level one technician is to gather pertinent information from the customer. The technician has to accurately enter all information into the ticket or work order. Examples of the type of information that the level one technician must obtain are as follows:
Contact information
What are the manufacturer and model of computer?
What OS is the computer using?
Is the computer plugged in to the wall or running on battery power?
Is the computer on a network? If so, is it a wired or wireless connection?
Was any specific application being used when the problem occurred?
Have any new drivers or updates been installed recently? If so, what are they?
Description of the problem
Priority of problem
Some problems are very simple to resolve, and a level one technician can usually take care of these without escalating the work order to a level two technician.
When a problem requires the expertise of a level two technician, the level one technician must describe a customer’s problem on a work order, using a succinct sentence or two. An accurate description is important because it helps other technicians quickly understand the situation without having to ask the customer the same questions again.
Level Two Technician Responsibilities (14.4.1.3)
As with level one technicians, call centers sometimes have different names for level two technicians. These technicians might be known as product specialists or technical-support personnel. The level two technician’s responsibilities are generally the same from one call center to the next.
The level two technician is usually more knowledgeable and experienced than the level one technician or has been working for the company for a longer period of time. When a problem cannot be resolved within a predetermined amount of time, the level one technician prepares an escalated work order, as shown in Figure 14-7. The level two technician receives the escalated work order with the description of the problem and then calls the customer back to ask any additional questions and resolve the problem.
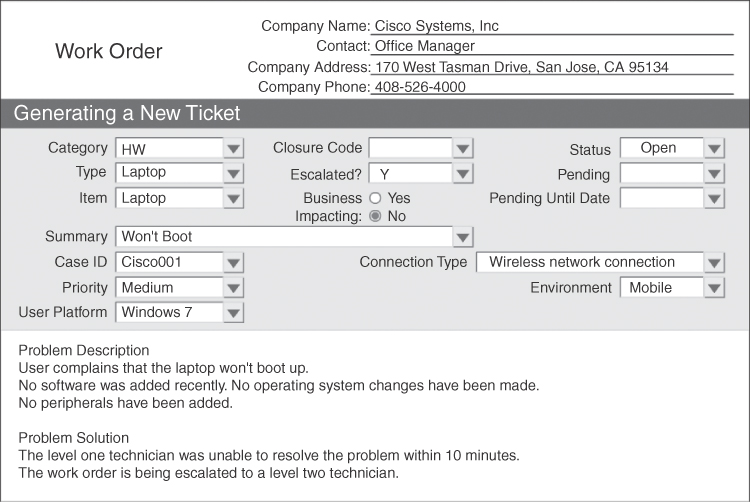
Figure 14-7 Example of a Work Order
Level two technicians can also use remote access software to connect to a customer’s computer to update drivers and software, access the operating system, check the BIOS, and gather other diagnostic information to solve the problem.
14.4.1.4 Lab -Remote Technician - Fix a Hardware Problem
![]()
In this lab, you will gather data from the customer and instruct the customer to fix a computer that does not boot.
14.4.1.5 Lab - Remote Technician - Fix an Operating System Problem
![]()
In this lab, you will gather data from the customer and instruct the customer to fix a computer that does not connect to the network.
14.4.1.6 Lab - Remote Technician - Fix a Network Problem
![]()
In this lab, you will gather data from the customer and instruct the customer to fix a computer that does not connect to the network.
14.4.1.7 Lab - Remote Technician - Fix a Security Problem
![]()
In this lab, you will gather data from the customer and instruct the customer to fix a computer that cannot connect to a workplace wireless network.
Basic Scripting and the IT Professional (14.4.2)
This section examines how to write script files that can automate various tasks to save time for a technician or an administrator.
Script Examples (14.4.2.1)
As an IT professional, you will be exposed to many different types of files. One very important type of file is a script file, a simple text file written in a scripting language to automate a process or tasks on an operating system. In the field, a script file might be used to automate the process of performing a backup of a customer’s data or to run a list of standard diagnostics on a broken computer. The script file can save the technician a lot of time, especially when the same tasks need to be performed on many different computers. You should also be able to identify the many different types of script files because a script file may be causing a problem at startup or during a specific event. Often, preventing the script file from running may eliminate the problem that is occurring.
The commands in a script file might be written on the command line one at a time, but it is more effective to use a script file. The script is designed to be executed line by line, using a command line interpreter in order to perform various commands. A script can be created using a text editor such as Notepad, but an integrated development environment (IDE) is often used to write and execute scripts. A Windows batch script is shown in Example 14-1.
Example 14-1 Windows Batch Script
@echo off echo My first batch script!! echo My hostname is: %computername% pause
The four lines of this Windows batch script do the following:
Turn off automatic echoing output at the terminal.
Echo the sentence “My first batch script!!” to the terminal.
Echo “My hostname is:” followed by the variable %computername% to the terminal.
Pause the script with the prompt of “Press any key to continue...”
Example 14-2 shows a Linux shell script.
Example 14-2 Linux Shell Script
#!/bin/bash echo My first batch script!! echo My hostname is: $(hostname) sleep 2
The four lines of this Linux shell script do the following:
Identify the shell that the script will be using.
Echo the sentence “My first batch script!!” to the terminal.
Echo “My hostname is:” followed by the variable $(hostname) to the terminal.
Pause the script for 2 seconds.
Scripting Languages (14.4.2.2)
A scripting language is different from a compiled language because each line is interpreted and then executed when the script is run. Examples of scripting languages include Windows batch files, PowerShell, Linux shell script, VBScript, JavaScript, and Python. Compiled languages such as C, C++, C#, and Java need to be converted into executable code by a compiler. Executable code is directly readable by the CPU, and scripting languages are interpreted into code that the CPU can read one line at a time by a command interpreter or by the operating system. This makes scripting languages unsuitable for situations in which performance is a significant factor. Table 14-6 lists scripting languages and their extensions.
Table 14-6 Script Types
Scripting Language |
Extension |
Description |
Windows batch file |
.bat |
Windows command-line interpreted language |
.ps1 |
Windows task-based command-line shell and scripting language |
|
.sh |
Linux shell interpreted language |
|
.vbs |
Windows Visual Basic script |
|
.js |
Client-side scripting language that runs in the browser |
|
.py |
An interpreted, object-oriented, high-level language |
Table 14-7 shows the comment styles used in various scripting languages.
Table 14-7 Script Styles
Scripting Language |
Comment Style |
Windows batch file |
REM comment |
PowerShell |
# comment or <# comment #> |
Linux shell script |
# comment |
VBScript |
' comment |
JavaScript |
// comment |
Python |
# comment |
Basic Script Commands (14.4.2.3)
Various commands are available at the terminal of each operating system. Some Windows commands are based on DOS and are accessible through the command prompt. Other Windows commands are accessible through PowerShell. The Windows commands in Table 14-8 were inherited from DOS and work at the Windows command prompt as well as in batch scripts.
Table 14-8 Basic Windows Commands
Command |
Output |
dir |
View the contents of the current directory |
cd |
Change directories |
mkdir |
Make a directory |
cls |
Clear the screen |
date |
Display/set the date |
copy |
Copy a file or files |
Linux commands are written to be compatible with Unix commands and are often accessed through BASH (Bourne Again shell). The Unix-compatible commands in Table 14-9 are available in most Linux distributions. Note that some of these commands are the same as their DOS counterparts.
Table 14-9 Basic Linux Commands
Command |
Output |
ls |
View the contents of the current directory |
cd |
Change directories |
mkdir |
Make a directory |
clear |
Clear the screen |
date |
Display/set the date |
cp |
Copy a file or files |
Variables/Environmental Variables (14.4.2.4)
Variables and environmental variables are unique memory locations used by programs.
Variables
Variables are designated places to store information within a computer. A primary function of computers is to manipulate variables. Example 14-3 shows a script in which a user is prompted for his or her last name (LNAME) and where he or she is from (PLACE). The script then shows the execution and output of the script.
Example 14-3 Scripting and Using Variables
User@Linux:~$ cat ./script1.sh #1/bin/bash echo -n "What is your last name? " read LNAME echo -n "Where are you from? " read PLACE echo Hello, $LNAME from $PLACE User@Linux:~$ ./script1.sh What is your last name? Smith Where are you from? Michigan Hello, Smith from Michigan
Variable Types
Table 14-10 shows common data types used by variables. Some scripting languages require that variables be defined as being integers (numbers), characters, strings, or something else. In code, a string usually contains multiple characters but can also use numbers and spaces. Often, when defining a string, quotes are used to denote the beginning and end of the string (for example, “Dan sold 3 cars yesterday”).
Table 14-10 Common Data Type Use by Variables
Data Type |
Description |
Example |
int |
Integer numbers |
-1,0,1,2,3 |
float |
Numbers with decimals |
1234.5678 |
char |
A single character |
S |
string |
Multiple characters |
He77o! |
bool |
True or false |
True |
Environmental Variables
Some variables are environmental, which means the operating system uses them to keep track of important details such as username, home directory, and language. Example 14-4 shows a shell script with environmental variables.
Example 14-4 Calling Environmental Variables
User@Linux:~$ cat ./script2.sh #1/bin/bash echo The current directory is $PWD echo The language used is $LANGUAGE echo The shell being used is $SHELL User@Linux:~$ ./script1.sh The current directory is /home/User The language used is en_US The shell being used is /bin/bash
The Linux variables PWD, LANGUAGE, and SHELL were preset when the user logged into this terminal. To view a list of all environmental variables, use the env command. Some useful Windows environmental variables are %SystemDrive% (the drive where the system folder is) and %WinDir% (exactly where the Windows folder is).
Conditional Statements (14.4.2.5)
Conditional statements are needed for scripts to make decisions. These statements usually come in the form of if-else or case statements. In order for a conditional statement to make a decision, a comparison must be made by using operators. The syntax of these commands varies depending on the operator language.
Table 14-11 shows a list of relational operators in various scripts. When making a mathematical comparison, use relational operators. Other types of operators include arithmetic (+, -, *, /, %), logical (and, or, not), assignment (+=, -+, *=), and bitwise (&, |, ^) operators.
Table 14-11 Relational Operators
Operator |
Batch |
PowerShell |
BASH |
Python |
Equal |
== or EQU |
-eq |
-eq |
== |
Not equal |
!= or NEQ |
-ne |
-ne |
!= |
Less than |
< or LSS |
-lt |
-lt |
< |
Greater than |
> or GTR |
-gt |
-gt |
> |
Less than or equal to |
<= or LEQ |
-le |
-le |
<= |
Greater than or equal to |
>= or GEQ |
-ge |
-ge |
>= |
If-Then Statements
Example 14-5 is shell script that determines whether it is currently morning or afternoon.
Example 14-5 If-Then Script
User@Linux:~$ date | cut -f 4 -d ' ' 09:36:24 User@Linux:~$ cat ./script3.sh #!/bin/bash TIME=$(date | cut -f 4 -d ' ' | cut -f 1 -d ':') declare NOON=12 if [ $TIME -ge $NOON ] then echo "Afternoon" else echo "Morning" fi User@Linux:~$ ./script3.sh Morning
In this script, the date command is piped to cut until only the hour remains, and the result is placed in a variable. The if statement compares the variables $TIME and $NOON by using the -ge operator to determine if the output is going to say “Afternoon” or “Morning.”
Case Statements
Example 14-6 is a shell script that determines whether a vowel or a consonant is used.
Example 14-6 case Statement Script
User@Linux:~$ cat ./script4.sh #!/bin/bash read -p "Give me a letter. " LETTER case $LETTER in a|e|i|o|u) echo "$LETTER is a vowel." ;; *) echo "$LETTER is a consonant." ;; esac User@Linux:~$ ./script4.sh Give me a letter. e e is a vowel. User@Linux:~$ ./script4.sh Give me a letter. b b is a consonant
The case statement is able to lump various comparisons into categories. Note that the letter b is not mentioned in the script.
Loops (14.4.2.6)
A loop can be used to repeat commands or tasks. The three main types of loops used in scripts are the for loop, the while loop, and the do-while loop.
A for loop repeats a section of code a specified number of times. A while loop checks a variable to verify whether it is true (or false) before repeating a section of code; this is known as a pre-test loop. Finally, a do-while loop repeats a section of code and then checks a variable to verify whether it is true (or false); this is known as a post-test loop.
For Loops
Example 14-7 is a shell script that outputs five randomly generated binary numbers.
Example 14-7 For Loop Script
User@Linux:~$ cat ./script5.sh #!/bin/bash for COUNT in 'seq 1 5'; do let NUMBER1 = "$RANDOM % 256" let NUMBER2 = "$(echo "obase=2; $NUMBER1" | bc)" echo $NUMBER1 = $NUMBER2 done User@Linux:~$ ./script5.sh 160 = 10100000 71 = 1000111 43 = 101011 187 = 10111011 7 = 111
The for loop in this script repeats a sequence exactly five times. The variable NUMBER1 is randomly generated to be between 0 and 255. The variable NUMBER2 is the binary conversion of NUMBER1. The spacing between the commands for and done is optional in some languages, but it helps a programmer understand what code is contained in the loop.
While Loops
Example 14-8 is a shell script that runs until a randomly chosen number is greater than 8.
Example 14-8 While Loop Script
User@Linux:~$ cat ./script6.sh #!/bin/bash NUMBER=1 while [ $NUMBER -le 8 ]; do let NUMBER="$RANDOM % 10+1" echo -n "$NUMBER " done echo "> 8 .. loop broken." User@Linux:~$ ./script6.sh 5 7 9 > .. loop broken.
In this script, the loop keeps running until a random number that is chosen is greater than eight. Notice that the variable NUMBER was set to 1 before the loop started. This was done to prevent the test [ $NUMBER -le 8 ] in the next line from failing.
Do-While Loops
Example 14-9 is a shell script that determines whether a vowel or a consonant is used.
Example 14-9 Do While Loops
User@Linux:~$ cat ./script7.sh #!/bin/bash while true ; do let NUMBER="$RANDOM % 10+1" echo -n "$NUMBER " if [ $NUMBER -gt 8 ]; then break; fi done echo "> 8 .. loop broken." User@Linux:~$ ./script7.sh 3 7 4 1 5 7 6 7 1 7 9 > 8 .. loop broken.
Unlike most compiled languages, several scripting languages lack do-while loops. Such languages emulate the post-test function by using an if statement within the loop followed by a break statement.
14.4.2.7 Lab - Write Basic Scripts in Windows and Linux
![]()
In this lab, you will write some basic scripts in different scripting languages to learn how each language handles automating tasks.
Summary (14.5)
In this chapter, you learned about the relationship between communication skills and troubleshooting skills. You need to combine these skills to become a successful IT technician. You learned about the legal aspects and ethics of dealing with computer technology and the property of the customer.
You learned that you should always conduct yourself in a professional manner with your customers and coworkers. Professional behavior increases customer confidence and enhances your credibility. You learned how to recognize the signs of a difficult customer and what to do and what not to do when you are on a call with such a customer.
You must understand and comply with your customer’s SLA. If a problem falls outside the parameters of the SLA, find positive ways of telling the customer what you can do to help rather than what you cannot do. In addition to complying with the SLA, you must follow the business policies of the company. These policies include how the company prioritizes calls, how and when to escalate a call to management, and when you can take breaks and lunch. You performed several labs on fixing hardware, operating system, network, and security problems.
You learned about the ethical and legal aspects of working in computer technology. You should be aware of your company’s policies and practices. In addition, you might need to familiarize yourself with your local or country’s trademark and copyright laws. A software license is a contract that outlines the legal use or redistribution of that software. You learned about the many different types of software licenses, including personal, enterprise, open source, and commercial.
Cyber law explains the circumstances under which data (evidence) can be collected from computers, data storage devices, networks, and wireless communications. First response is the term used to describe the official procedures employed by people who are qualified to collect evidence. You learned that even if you are not a system administrator or computer forensics expert, it is a good habit to create detailed documentation of all the work that you do. Being able to prove how evidence was collected and where it has been between the time of collection and its entry into the court proceeding is known as the chain of custody.
Finally, you learned about script files, which are files written in scripting languages to automate processes and tasks on various operating systems. A script file can save a technician a lot of time, especially when the same tasks need to be performed on many different computers. You learned about scripting languages and some basic Windows and Linux script commands. You learned about variables, which are designated places to store information within a computer, conditional statements, which are needed for scripts to make decisions, and loops, which repeat commands or tasks.
Learning about scripting is important, and so is experience practicing writing scripts. In this chapter you performed a lab writing some very basic scripts in different scripting languages to learn how each language handles automating tasks.
Practice
The following activities provide practice with the topics introduced in this chapter. The labs are available in the companion IT Essentials v7 Labs & Study Guide (ISBN 9780135612033).
![]()
Labs
14.1.1.2 Lab - Technician Resources
14.3.1.5 Lab - Investigate Breaches of PII, PHI, PCI
14.4.1.4 Lab - Remote Technician - Fix a Hardware Problem
14.4.1.5 Lab - Remote Technician - Fix an Operating System Problem
14.4.1.6 Lab - Remote Technician - Fix a Network Problem
14.4.1.7 Lab - Remote Technician - Fix a Security Problem
14.4.2.7 Lab - Write Basic Scripts in Windows and Linux
Check Your Understanding Questions
Complete all the review questions listed here to test your understanding of the topics and concepts in this chapter. The appendix “Answers to ‘Check Your Understanding’ Questions” lists the answers.
1. A programmer is building a script to calculate the corporate bank account balance within two decimal places. Which data type would be used in the script to represent the balance?
Bool
int
float
char
2. What category of technician uses remote access software to update a computer belonging to a customer?
level one technicians
level two technicians
field technicians
bench technicians
3. What is the correct way to conduct a telephone call to troubleshoot a computer problem?
Ask personal questions to get better acquainted with the customer.
Maintain professional behavior at all times.
Explain each step to help the customer understand the troubleshooting process.
Always gather information from the customer and escalate the problem.
4. A supervisor receives a complaint that a technician was rude and disrespectful. Which action by the technician most likely caused the customer to complain?
The customer was escalated to a level two technician.
The technician interrupted a number of times to ask questions.
The technician occasionally confirmed an understanding of the problem.
The technician ended the call without saying “Have a nice day.”
5. What approach should a technician take when receiving a call from a stressed customer?
Transfer the customer to a level two technician who will ask the customer to explain the problem again.
Try to establish a rapport with the customer.
Ask the customer to telephone back when the customer is feeling less stressed.
Ask the customer to hold and then wait five minutes for the customer to calm down.
6. Which statement best describes a call center?
It is a help desk environment where customers go with their computers to have them fixed.
It is a place to provide computer support to customers.
It is a help desk that customers use to make appointments to report their computer problems.
It is a busy, fast-paced work environment that documents computer problems after they have been repaired by technicians.
7. In which situation would it be appropriate for a technician to back up personal and confidential data from a computer belonging to a customer?
if the technician feels it necessary to back it up
if the customer forgets to sign the work order
if illegal content is discovered on the customer computer
if the customer permits it
8. Which programming language utilizes scripts that are interpreted and executed line by line when the scripts are run?
C++
Java
PowerShell
C#
9. Which of the following are examples of displaying professional communication skills while talking to a customer? (Choose two.)
the use of active listening, with occasional interjections such as “I see” or “I understand”
interrupting customers with questions to gather more information
asking customers to paraphrase their explanations
focusing on what you cannot do to give customers an idea of the magnitude of the problem
clarifying what customers say after they have finished their explanations
10. Once a technician understands a customer complaint, it is common to ask closed-ended questions. Which question is a close-ended one?
What error messages were displayed when the error occurred?
Is this the first time the error occurred?
What happened after the error occurred?
What happened before the error occurred?
11. A technician working on a computer discovers what is suspected to be illegal activity. Which pieces of information should be immediately documented? (Choose three.)
details of all past users of the computer
location of the computer
technical specifications of the computer
why the computer was accessed by the technician
evidence of the suspected illegal activity
duration of the suspected illegal activity
12. A customer is explaining a problem with a computer to a technician. The technician recognizes the problem before the customer finishes the explanation. What should the technician do?
Ask the customer to repeat the problem so that the technician can document it and verify all the facts.
Interrupt the customer and let the customer know that the technician knows what the problem is.
Wait politely for the customer to finish explaining the problem.
Start working on the PC while listening to the customer at the same time.
13. A customer is upset and wants to speak to a specific technician to resolve a problem immediately. The requested technician is away from the office for the next hour. What is the best way to handle this call?
Ignore the request for the specific technician by walking through a step-by-step process with the customer in an attempt to refocus the customer and solve the problem.
Advise the customer that the requested technician is out of the office and insist on trying to resolve the problem.
Refer the angry customer to a supervisor.
Make an offer to help the customer immediately and advise the customer that otherwise the requested technician will call the customer back within two hours.
14. What is considered ethical behavior by a technician when communicating with a customer?
A technician can send mass emails to customers.
A technician must send only solicited emails.
A technician can send forged emails to customers.
It is normal to send chain emails to customers.
15. Which situation would require that a support desk call be given the highest priority?
A couple of computers have operating system errors.
Some computers cannot log in to the network.
The company cannot operate because of a system failure.
Two users are requesting an application enhancement.
A user is requesting a RAM memory upgrade.
16. What action should a technician avoid when dealing with a talkative customer?
stepping in and attempting to refocus the customer
asking closed-ended questions to regain control of the conversation
asking social questions such as “How are you today?”
giving the customer a full minute to talk
17. Which of the following roles or tasks are associated with a level two technician? (Choose two.)
editing a shell script to run when the server starts
installing the new BIOS update when it is available
scheduling a task to run at a specific time and date
deleting caches and cookies after the web browser closes
18. A programmer uses an operator to compare two variable values within a program. The variable A is assigned a value of 5, and the valuable B is assigned a value of 7. Which condition test syntax would provide the result true?
A == B
A > B
A != B
A >= B
