3 Understand Retail Operation
Towards Internal Information Theft Prevention
3.1. Introduction
This chapter looks into retail business operation by exploring the key components—people, process, and technology—which affect information processing and data security. One thing is fascinating when working with information security professionals and retail business owners in implementing strategies to prevention internal information theft. They rarely know retail business operation. Yet they pretend to understand retail operation so they can tell business owners how to do things. Security professionals cannot tell the retail companies how to run their internal information security systems if there is a lack of thorough knowledge of retail operation. The knowledge explored in this chapter equips the reader to support and advise retail businesses on how to achieve their internal information security objectives with an acceptable level of risk. It is important that you have a far broader scope of retail operation: information transaction, technology, people and process—the four pillars of information security for effective prevention of internal information theft.
By necessity, in this guide, we must focus on all four pillars. The truth is, however, that many people ignore one or more. But this book bridges these gaps in knowledge and explains the role of people in preventing internal information theft. This is done by exploring the contribution of organisational theory and the use of people-centred strategy as the basis for management roles in the prevention of internal information theft in retail business.
Case Study 3.1 A Case of UK Online Retail Industry and Internal Information Theft
The UK online retail industry is a £9.4 billion industry, accounting for approximately 5 per cent of Gross Domestic Product, with more than 10 per cent of all employment (Gambin et al., 2012). UK online retailing comprises beauty and personal care Internet retailing, consumer electronics, consumer healthcare Internet retailing, media products Internet retailing, and other Internet retailing. According to the Centre for Retail Research, 2008–2012, UK online retailing, combined with Germany and France, accounted for 71 per cent of European online sales (Nicklin et al., 2013). Thus, the experience of UK’s retail sector can be taken as an important indicator of experiences of other Organisation for Economic Co-operation and Development (OECD) countries.
UK online retailing has been one of the early adopters of electronic trading operations. UK online retailing has a long tradition of Internet-based focus. The trend for the digitisation of online retail operations and their business transactions using credit/debit cards necessitates sharing of consumers’ sensitive personal identifiable data. However, the Internet offers UK retailers opportunities to match this trend but not without the problems of internal information theft to contend with.
In socio-economic terms, this industry shapes the livelihood of UK consumers and affects online consumers’ ability to respond to e-commerce challenges like information theft. The UK retail sector has been characterised as one of the sectors where most of the consumers are vulnerable to information theft and information security breaches with less investment on the prevention (Forrester and Seeburger, 2013; National Fraud Authority Report, 2013). Therefore, the retail sector provides a unique setting to understand issues of internal information theft prevention, which can be used as basis for designing guides to prevent information theft in other e-businesses.
3.2. People: Platform for Information Processing in Retail Business
Several years ago, the Trustworthy Computing project by Microsoft claimed that security is people, process, and technology. Some security analysts were sceptical and criticised that Microsoft was trying to shift focus from poor security loopholes (identified in their tools) to factors it may not control. This can be an unfair analysis, considering that Microsoft’s recent solutions, particularly Windows 10 and Windows Server 2012, are actually quite good when it comes to security and rate high amongst other security solutions. Hence, the need to explore the importance of people (retailers as users, suppliers and customers) as the fundamental pillar that holds up other elements—information, process and technology—that make up retail operation. This analysis can be explained thus: retail business process is how people use technology to turn data into information so that they can make informed decisions in retail operations.
Information processing in retail business operation is a complex task, and in most cases nebulous because of the network of users involved—customers, retailers and suppliers. A process may provide competitive advantage to retail business only when the channel is free from hitches of information theft. Information security professionals must focus on securing critical business information, and this can be achieved by securing information processing in retail operations. Hence, attention should be given to the nature of the information processed, the owners of the information, reasons/purpose of information processing and who shares the information. These interactions in information processing create various avenues and mechanisms to use and store information. Consequently, these elements represent possible areas of weakness, as well as weak points that reduce the user’s ability to visualise the process and the challenges it may pose to retail operation. The less complex or more streamlined a process, the easier to manage and secure.
In fact, inability to understand the scope of information processing in retail operation is one of the key causes of internal information theft and accidental/unintentional information leakages. As information security professionals, we must thoroughly understand the role management plays in information processing to direct retail internal information theft prevention strategies. Figure 3.1 illustrates people as the platform for information processing in retail business operation.
Table 3.1 below summarises the processing of data in retail business. This table provides a description of forms of information that are processed in retail businesses, owners of information that are being processed, reasons/purpose for processing the information and who shares the information.
3.3. Role of People in the Prevention of Internal Information Theft
Some internal information theft prevention guides are not designed based on people-oriented security, or, rather, integration of both technology-based software security and human contributions. In other cases, companies have depended solely on implementation of software-based security and have neglected to consider integrating people, process, and technology.
Some information prevention strategies failed due to overdependence of information security professionals on software-based security. Software-based security grounded in technology can be the most reliable in providing information availability, confidentiality and integrity, but cannot be a substitute for people-oriented security. People are indispensable, as information owners, custodians and users. These insights justify the need for integrating process and technology, with people as the central focus. Hence, it is necessary to discuss organisational role theory to explore the human role—the employees in integrating other essential elements needed for effective internal information theft prevention guides.
|
Forms of information |
Customer/business name, date of birth, house address, job status, financial status, social circumstances, marriage status, lifestyle, visual images, race/ethnicity, health status, age, religion, etc. |
|
Owners of information |
Customers, suppliers, employers, employees, outsourcing companies, consultants, complainants, donors, lenders, clients, enquirers, victims of crimes, suspected offenders, vulnerable people, service providers, representatives, educators, trade unions, business associates, advisers, etc. |
|
Reasons/ purpose
|
Marketing, business promotion, advertisement, account maintenance, records keeping, sharing, business research, identify offenders, crime prevention and detection, membership records, staff records, criminal proceeding, order forms, warranty cards, customer rewards programmes, customer satisfaction survey, feedback, customer competition, etc. |
|
Who shares the information |
Suppliers, law enforcement agencies, credit reference agencies, financial companies, debt collection agencies, tracing agencies, business associates, police officers, security organisations, charity organisation, past/present/prospective employers, recruitment agencies, etc. |
3.3.1 Organisational Role Theory
The concept of organisational role theory (ORT) is one of the five major models of role theory developed by Biddle (1986) to examine role development in organisations. The concept of ORT describes and provides insight into the purposive actions of individual employees, management and organisations, as they relate to the field in which they operate. The ORT concept has been applied by researchers in behavioural science, management, sociology, and psychology for modelling authority, responsibility, functions, and interactions associated with management positions.
In their study of how organisations can prevent crimes in their respective business domain, Ekblom (2010) and Sarnecki (2005) looked into the concepts of ORT and suggested that employees in business organisations should in some way complement the shared roles and responsibilities, supporting each other in the environment where they operate. Ekblom (2010) argues that it might be helpful to conceptualise people’s roles in crime prevention to provide an integration platform for software-based technology, process and people, because it focuses on the ‘root causes’—lack of clarity of integrated internal information prevention practices.
Biegelman (2009) agrees with Ekblom (2010) and suggests a need for interdependence of roles of the complementary management team for them to thrive in crime prevention in business organisations. Savirimuthu and Savirimuthu (2007) and Luhmann (2004) agree with these suggestions and argue that a deeper understanding of interdependence of management roles in business organisations is an important prerequisite to development of a strategic and coherent crime prevention guideline. The effective analysis of people’s roles in retail operation can provide in-depth understanding of how the efforts of information security professionals could be directed toward preventing internal information theft. The interaction of security professionals and retail management becomes a role-based process in which each party begins to share the roles of the other, with a clear view of the value of effective internal information theft prevention. The interaction of various roles of human resources involved in internal information theft prevention can help to explain the management roles and the implication of their relationship with other management (IT security, data compliance, law enforcement agencies, etc.) and how it can help to minimise employee engagement in internal information theft. In addition, it can to help explain the impact of the clarity of management roles/responsibilities and how it can help to maximise management performance in providing effective internal data security.
3.3.2 People-Centred Strategy in the Prevention of Internal Information Theft
It has been understood from Chapter 1 that it is the people aspect of information processing that gets online retail organisations into most of the security loopholes. Thus, it is necessary to equip people by building their intelligence and decision-making capabilities to achieve the goal of internal information theft prevention. Retail companies can invest on physical and technical measures, such as authentication mechanisms, firewalls, and penetration and intrusion detection systems to defend against external cyber-attacks. However, the insiders who have authorisation can bypass those measures to steal critical information from a business.
Insiders are familiar with internal policies, process and procedures, which could be bypassed and exploited to carry out internal information theft. Anderson et al. (2005) suggest that information theft risk management should involve a comprehensive combination of behavioural, organisational and technical issues. Since internal identity theft criminals utilise both technology and human techniques to perpetrate their threats, it is important to consider a combination of behavioural, organisational process and technical issues to prevent them. Anderson et al. (2005, p. 8), who worked on the Preliminary System Dynamics Maps of the Insider Cyber-threat Problem, reaffirmed that;
…because insiders are legitimate users of their organisation’s networks and systems, sophisticated technical capability is not necessarily required to carry out an insider attack. On the other hand, technically capable insiders are able, and have, carried out more sophisticated attacks, that can have more immediate, widespread impact,…these technical insiders also sometimes have the capability to “cover their tracks” so that identification of the perpetrator is more difficult…
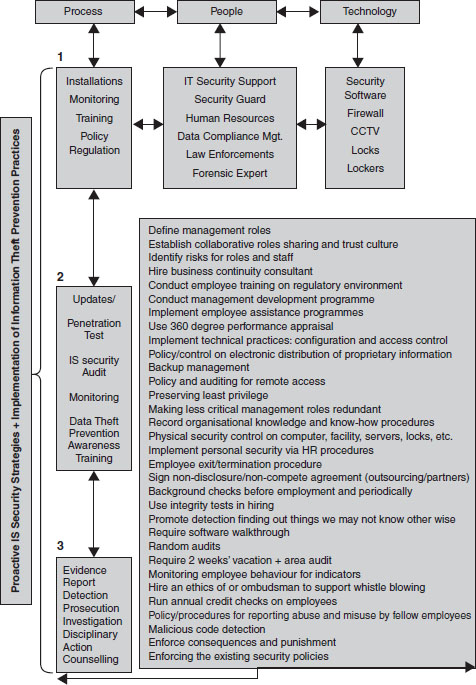
This statement suggests that it is important to understand the basic need of employee roles in implementing retail information systems security to mitigate internal information theft risks. That is, it is important to understand the roles of the offender and users to regulate the way process and technology interacts. Since IS security management is processed by the use of procedure driven by people, the major focus of internal information theft prevention guide should be on people. Procedure, as described by ISO 9001:2000, is a way in which people—the IS security management—work to accomplish a task. The task here, as shown in Figure 3.2, is the sequence of steps and actions that are essential for prevention of internal information theft in retail businesses.
The structured tasks are designed to function as a continuous process which shows how the IS security management can implement the recommended practices to reduce internal information theft risks. The recommended practices are synthesised from the suggested internal information theft prevention practices. The practices synthesised in this section are not a comprehensive list of all the applicable information theft prevention practices. However, the practices are summarised to meet the scope of this book, which is to provide an internal information theft prevention guideline. This aim extends to clarify the task of internal information prevention and identify how the roles of management can be aligned to meet the goal of preventing information theft in retail businesses.
This task of getting people, process and technology to interact and cooperate is difficult to achieve. This is why the human vector—people—has remained the weakest link in maintaining strategic retail information systems security. This is why most internal information theft modus operandi— social engineering, abetted collusion and collaboration— build their attack strategies on human foibles. The human being, with lack of awareness and human desire for money or ‘just wanting to help out’, would always be a prime target of information theft perpetrators.
Based on the structure of Figure 3.2 above, it is important that direct relationships exist with each management role. Each of the separate boxes linked with thin arrows are indirectly related; those linked with thick arrows are directly related. The arrow links depict the level of priority given to the labelled boxes: ‘box 1’ and ‘box 2’; if those roles, in relation to the responsibilities under the process, fail, then ‘box 3’ would be required. For instance, ‘box 1’, which is linked to ‘people’ with a thick arrow, comprises: IT security, data compliance, security guards and HR. It contains IS security management roles that have the possibility of sharing similar roles with each other. Figure 3.2 demonstrates the holistic interaction of both offender-oriented (people-focused) and situation-oriented (technology-focused) approaches to preventing internal information theft.
3.3.3 Management Roles in the Prevention of Internal Information Theft
This concept can improve retail information security management approaches by providing the capacity to control and monitor the technological aspects of security, as well as management adherence to established processes and procedures. In addition, it enhances the ability of IS security governance to leverage human factors by regulating their interactions with technology. It would promote intelligent workflows and process IS security management against potential internal information theft risks by aligning the skills with management roles and functions.
There are three specific constructs that explain what management does: roles, functions and skills. Although these constructs are directly or indirectly related, they can be used to analyse employees and cross management behaviour. For instance, management roles are described based on different interrelated categories: decision-making, interpersonal relationship, transfer of information, reflection, taking actions, etc.
The combination of these categories has direct influence on the responsibility of information security professional in relation to the tasks of internal information theft prevention. In implementing task of internal information theft prevention, as noted above, it is important for every security management team to have a clear role for the management to collaborate. Collaboration of management roles is vital for a comprehensive internal information theft prevention framework since the tasks and roles are the basis for the control of retail information security operations. So it is important that management roles interact and work together to support other cross-functional management. Table 3.2 below summarises the descriptions of the key management roles common in online retail companies. The interrelated steps shown in Figure 3.2 above have already described how the processes and technology can be centred on these management roles.
|
Roles |
Roles description in relation to internal information prevention |
|
Operational Management |
Those that work in retail call centres and use screening techniques to process customers’ order for possible abnormality or mismatch of identity attributes—name, date of birth, account detail, etc. It requires the management to ensure that personal identifiable information documents—customer and business—are cross-shredded before their disposal. For effective operation of this management, it is the role of HR to ensure that proper and essential training is provided. |
|
Technical management |
These are the software engineers, web designers and data miners that use software security tools such as authentication kits, address verification system, digital signature, and encryption. This management depends on IS/T support to protect the IS security infrastructure from potential information theft risks. |
|
Managerial and Policy |
This is the role of the management that ensures the development of explicit policy regarding protection of security and privacy of business and customers. This involves implementation of policy strategy for safe preservation of business and consumers’ data. This should emphasise the ethic of the company and reinforce rewarding of employees. This would encourage and promote honesty in the workplace. |
|
Risk Management |
This role involves use of intelligent and strategic techniques to identify information theft risks such as inconsistencies in the transaction or customer’s order pattern. It compares a consumer’s past and present history for inconsistencies, such as case of irregularity in use of credit card within short period of time. |
|
Resource and Control Management |
This role demands the contribution of HR in counselling and training of employees. Since employees are the prime vector of information theft, there should be effective employee control. In addition, this role manages vetting and screening of employees. |
3.3 Summary of Chapter 3
This chapter has provided knowledge of the roles management plays as people in the prevention of internal information theft. It has analysed how the role of people, as managers of information, can be considered as the basis for implementing effective internal information security while using technology for information processing in retail operations. A more technologically advanced retail company with better information processing guided by effective security management is more capable of preventing internal information theft than one without. From an information security perspective, processing information through the complex technology-oriented operations of modern retail business is problematic. But an in-depth understanding of the role of people in information processing could boost the security of retail business operation. Technology in retail business operations often adds complexity, and complexity can breed insecurity. Thus, people, process and technology must interact, and the smoothness of this interaction, in relation to security of information, is totally dependent on the role of people—the management. The management should ensure the effective security of all possible points of interaction in information-processing channels, irrespective of who owns/shares/stores the information.
However, sometimes it is impossible to provide ‘effective’ security for technical reasons. In such situations in retail business operations, the only way is to minimise the chances of internal information theft by adopting strategies that are applicable in retail businesses. The next discussion of this guide, Chapter 4, provides knowledge of internal information theft prevention frameworks and their practical setbacks.
References
Anderson, D., Cappelli, D., Gonzalez, J., Mojahedzdeh, M., Moore, A. and Rich, E. (2005). ‘Preliminary system dynamics maps of the insider cyber-threat problem’. Group Modelling Workshop at Software Engineering Institute, pp. 8–36.
Biddle, B.J. (1986). ‘Recent developments in role theory’. Annual Review of Sociology, 12, pp. 67–92.
Biegelman, M.T. (Ed.). (2009). Identity Theft Handbook: Detection, Prevention and Security. Hoboken, NJ: John Wiley and Sons, Inc.
Ekblom, P. (2010). Crime Prevention, Security and Community Safety with the 5Is Framework. Basingstoke, UK: Palgrave Macmillan.
Forrester and Seeburger. (2013). ‘The future of data security and privacy: Controlling big data’. In: The WebCast, The Silent Enemy: Preventing Data Breaches from Insiders, 13 March 2013 at 13:00–14:00 EDT.
Gambin, L., Hogarth, T., Atfield, G., Li, Y., Breuer, Z. and Richard, G. (2012). ‘Sector skills insights: Retail. UK Commission for employment and skills’. Joint Research Report, pp. 1–89.
Luhmann N. (2004). Law as a Social System. Oxford: Blackwell, pp. 64–66.
National Fraud Authority Report. (2013). Annual Fraud Indicator. London: NFA, pp. 7–32.
Nicklin, T., Meyer, K., Hardy, R. and Wilkins, N. (2013). Cambridge Marketing Handbook: Digital—Cambridge Marketing Handbooks. London: Kogan Page Publishers, pp. 12–15.
Sarnecki, J. (2005). Knowledge-Based Crime Prevention, Theoretical Points of Departure for Practical Crime Prevention. Thailand: UN Congress on Crime Prevention and Criminal Justice, pp. 1–11.
Savirimuthu, A. and Savirimuthu, J. (2007). ‘Identity theft and systems theory: The Fraud Act 2006 in perspective’. Unscripted, UK.