6 Collaborative Internal Information Theft Prevention
Towards Innovative Security
6.1. Introduction
The need for security and crime prevention management to work collaboratively in updating security tools has been identified to have a huge impact on information theft prevention. In recent years, advances (e.g., Internet Engineering Task Force, Keeping Internet Routing Secure, Mutually Agreed Norms for Routing Security, etc.) in the use of computer technology have provided significant opportunity for collaboration in the crime and security decision-making process. The concept of collaboration provides strategies required to integrate cross-functional management and their tasks in retail operation. However, for the technology to have a significant impact on crime prevention, human, institutional and organisational barriers (identified in Chapter 5) need to be eliminated (Gilling, 2009). The collaborative approach streamlines IS security practices by dynamically helping management to create and align essential roles to eliminate potential management conflicts in their effort to prevent internal information theft in retail businesses.
As defined by Wenger et al. (2002), practice refers to the knowledge and the competencies of members, as well as to the specific things that they do. ‘Members’ in this guide refers to the security and crime prevention management. Interestingly, there are few or no books on the ‘actual practical guide’ for internal information theft prevention. The ‘practice’ of information theft prevention management has been a contested terrain, unsettled in the minds of security and crime prevention management, academics and policy makers (Wenger, 1998). This chapter will, as far as is possible within the confines of this guide, put together the ‘best practices’ of information theft prevention and develop a framework for how they can be applied together by management in retail companies.
6.2. Attributes of Collaborative Information Theft Prevention
The collaborative concept in prevention of internal information theft needs to be embedded with essential elements for its effective implementation. These elements are basic structures that would enhance management workflows in relation to security and crime prevention practices in preventing internal information theft. The three essential attributes for effective crime prevention and security management collaboration are:
- Agility,
- Interoperability, and
- Vigilance.
Agility: Both the security and crime prevention management need to be agile, responsive and available to enable adaptive planning and delivery of IS/T security roles. This attribute would encourage evolutionary, flexible and rapid response to change in evolving information theft trends in retail businesses. It would enable IS security management to prevent known risks, and provide a platform for effective responses to potential security loopholes.
Vigilance: Security strategies should be designed to provide management with the capability to integrate security intelligence to anticipate data security threats. This attribute would enable the management to evaluate risks and make informed decisions; enhance the adoption and collaboration of role sharing concepts; and to balance the technical controls with a process for applying security to employees, partners and third parties that contributes to internal information theft prevention.
Interoperability: By adopting the people, process and technology (PPT) approach, IS security management becomes a single system with the unified goal of internal information prevention. The collaborative role allows for easier monitoring and measurements. Importantly, it would give management control, which would minimise the impact of benign mistakes from employees’ actions and on processes related to internal information theft-related risks.
6.3. Collaborative Security Management: A Role-Based Framework (RBF)
This framework is conceptualised as a role-based framework (RBF). It incorporates internal information theft prevention practices recommended by IS security management from various business contexts. The prevention practices in this context are a set of documents, frameworks, ideas, information, languages, stories, styles and tools that both the security and crime prevention management share. Gercke et al. (2011) suggest that the cross-functional partnership that incorporates interdependent coordination of roles with skill sharing is the most effective prevention practice in any areas of information theft-related crimes. This suggestion could be practicable only in a defined business operation, online retail in this context, which may enable understanding of the issues of internal information theft.
Sharing of roles in relation to prevention of information theft is required in order to encourage leveraging, expanding of skills as appropriate, and support for external relationships with agencies. Role sharing brings together expertise from diverse management backgrounds, HR, law enforcement, and IS security. Each management background holds information linked to IS security, which, if shared, can provide comprehensive prevention views of criminal activity. This, in most cases, can be evidence-based practice. When these practices are based on equal sharing, an equal level of power, mutual respect and understanding, then the prevention strategies are implementable. This collaborative concept emphasises that information theft prevention should not be mere technological fixes but integrated IS/T security strategies—which are explicitly or implicitly held by practitioners.
It is important for security and crime prevention management to work together to harmonise common strategies for internal information prevention in businesses, primarily, to reduce the complexity in their analysis and application. Although some information theft prevention practices and frameworks have attempted to clarify their contextual analysis, as discussed in Chapter 4, the use of the concept of collaborative management has sought to provide clear role-based concepts of what could and should be implemented.
This concept of RBF underpins the suggestions of scholars and, more importantly, of practitioners’ need to increasingly work in information theft prevention. Ekblom (2010) and Sarnecki (2005), proponents of the intra-organisational management integration that underpins the theoretical analysis of collaborative security management, did not view their suggestions as being solely about improving the interaction of management roles in their business environments in relation to crime prevention. In particular, Ekblom (2010) suggests that numerous conceptualisations of crime prevention practices and theories delineate the degree to which it might be applied by the management.
The need for change in the paradigm of information theft prevention that was identified in Chapter 4—the shift from software-based and generic models of information theft prevention to analysis of the integration of shared management roles—is attempted to be bridged with this concept of role-based framework (RBF). This analysis of the role integration approach is important in this guide, as it is through this new framework that management can be enlightened and prepared to tackle emerging security threats in retail operation. Thus, understanding of the attributes of RBF and the diffusion of the responsibility for internal information theft prevention beyond either software-based or generic models is an explicit critique of the very idea of collaborative crime prevention and security management.
6.3.1. The Key Attributes of the Role-Based Framework
The four key attributes of the role-based framework are synthesised to ensure that management efforts and strategies are directed toward effective internal information theft prevention. The key attributes include:
- Collaborative role-based monitoring;
- Support capabilities;
- Service-level agreements;
- Flexible support.
Collaborative role-based monitoring: Collaboration between security and crime prevention management provides continuum and optimum roles/responsibilities across functional management team from the foundation and is proactive to prevent information theft risks;
Foundation: IS/T security warranty and remote support to law enforcements and outsourcing companies, and establishes their requirements with respect to service line agreements;
Preventive: Multi-management IS/T security support, clearly defined roles at the respective management level, dynamic and available management support.
Support capabilities: Collaborative security improves both the effectiveness and efficiency of IT/S maintenance and support. It provides opportunities for the Information security management systems (ISMS) to leverage the competency and best results which may come from out-tasking the cross-functions to strengthen IS/T security strategy. It makes it possible for an informed, effective maintenance and technical expertise to be shared in a dynamic process.
Service-level agreements: RBF is a customisable schema at hierarchical management levels to meet business information security management system budgets, needs and strategies.
This means that service-level agreements (SLAs) can now be linked dynamically to shifting roles, responsibilities and workloads. Rather than being defined by static roles that do not reflect changing internal information security demands, the internal information theft prevention service level can fluctuate in response to internal security risks; meets businesses’ expectations for real-time role-oriented information security management; assures data security processes and business continuity through clear management roles.
Flexible Support: Collaborative security help (information security management systems) ISMS to accomplish complex internal security tasks, manage or out-task IS/T security. It provides flexible knowledge transfer to address a range of information theft prevention complexities that might be beyond the expertise of management support. It provides the option to choose management roles and services that better suit the business data security operation and structure; creates information security optimised maintenance and dynamic prevention; minimises the ISMS service and roles that seem to clash; provides integrated information security service management, optimisation, and flexible delivery choices and leverages the expertise of cross-functional management to reduce the cost of IS platform as a service (PaaS) and infrastructure as a service (IaaS).
Collaborative management enhances implementation of prevention strategies to create structure that can help to effectively deliver the following retail business security objectives:
- Internal information theft prevention policy design and implementation,
- Encourage best practice to minimise internal information theft risks,
- Maximise internal security performance, and
- Align management roles and responsibilities
6.3.2. Structure of Role-Based Framework
The knowledge of collaborative information theft prevention requires that management should be designed as the body that encompasses complementary management team members—crime prevention, IT security, human resources and law enforcement agency. It classifies management roles in a hierarchical level from the top management to the front line management. It follows the stages of crime prevention processes, which include intervention, intelligence, implementation, collaboration and remediation measures. Intervention in this context refers to a combination of internal information prevention strategies designed to change or improve the employees’ behaviour or perception towards information theft. The elements of intervention include but are not limited to information theft prevention awareness training, data protection training, information theft incident reporting and whistle blowing.
These elements can contribute immensely by promoting employee support, influencing their IS security knowledge and skills, and creating supportive working environments, policies and resources. Intelligence is referred to as operations undertaken by IS security and crime prevention management to gather information that provides a better understanding of internal information theft characteristics—causes and methods of propagation (Karn, 2013). Remediation measures in relation to information theft prevention are the actions that management takes to correct the damage done by perpetrators.
In this guide, it is effective implementation and efficient collaboration by the management that can minimise the chance for a remediation process. While implementation is the translation of the chosen IS security strategy into action to achieve information theft prevention goals and objectives, collaboration is the key for achieving it. Hence, collaborative security management defines working together towards a goal of preventing information theft (Gercke et al., 2011).
Collaborative security management can be either inter-organisational, when it involves external agents (e.g., law enforcements, partners, outsourcing companies), or intra-organisational, when the roles of security and crime prevention managers are shared within the same organisation. Intra- and inter-organisation collaboration in preventing information theft can affect the effectiveness of IS security strategies in retail businesses. The impact can be significant on information theft prevention strategies such as information security policy, employee information theft awareness programmes, consumer data protection, identity management, law enforcement, employees training, reporting procedures, data compliance management and victims support.
6.3.3. Role-Based Information Theft Prevention: Cross-Functional Management
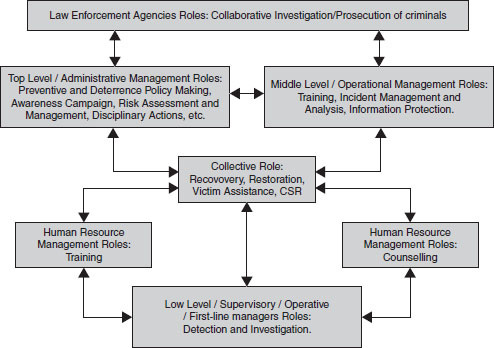
To ensure that the impact of collaborative security management is significant in every aspect of internal information prevention strategies, RBF should be organised, as shown in Figure 6.1 above, as a sequence of management levels which emphasise the clarification of roles—IS/T security, IS audit, crime prevention, HR and law enforcement. The arrows, as shown in the figure, depict the interdependence of shared roles through monitoring, reporting, and collaboration between management levels. The roles identified in this figure have their foundations in criminology (crime deterrence theory, Pearson theory and Cressey’s fraud triangle theory), IS and management perspective (policy and risk management) and sociology (staff fraud, white collar crimes and corporate frauds).
6.3.3.1. Top Management
The role of the top-level management for prevention of internal information theft includes making preventive and deterrent policies, risk assessment and management, disciplinary actions, etc. An effective information theft prevention policy within any business organisation is a necessary first step towards the development of strategic information security for integrated management. The policy should also include other components, such as definitive objectives, assumptions and directives which could increase the possibilities of discovery or decrease the probability of committing information theft in the organisation. There should be policy guides, clear procedures and internal rules for reporting and investigating cases of identity theft. Good policy statements are the basis for other steps to be built upon. Without prudent policy from the management of the organisation, other steps like risk assessment and management would not be effective.
Top managers should play hands-on roles in ensuring effective information protection, detection of fraud, investigations and incident management, so that prevention policies are taken seriously by all levels of an organisation. In doing so, their front-line experience would help them to develop more effective policies.
6.3.3.2. Middle Management
The middle-level management in a typical retail company comprises departmental heads and regional managers, etc. They are answerable to the top-level management for functioning of their departments/teams while ensuring organising and directing roles, which include training, incident management and analysis and information protection. They implement the organisational goals, objectives and plans according to the directions/policies of the top management. They should be able to clarify and explain internal information theft deterrent policies and guidelines from the top management to lower level management, thus acting as a mediator between the two levels. The governing policies discussed above are supported by the technical policies, thus they cover most rules and regulations in more detail by adding to these rules the areas that are relevant to the technology. These policies are meant for the technical custodians, as they carry out routine security responsibilities within the business.
The system and database administrators need to be kept abreast of the current technical policies within and outside the retail domain. As internal fraud threats are becoming more dynamic, with fraudsters continuing to devise new techniques to exploit the easiest target, crime specialists suggested that retail industry should continue to invest in systems and controls to avoid being targeted as the weakest link (Financial Crime and Service Authority, 2009). The advancement in the use of information technology has enabled criminals to continue to refine and update their techniques.
However, some of the new complex technologies that have been noted to have proven data and information security are biometric technologies, cryptography, authentication and certification and single sign-on technologies. It has been proven that a combination of these technologies built on a well designed and enforced set of security rules and regulations always deters internal criminals from fraud (Schneier, 2004).
Nevertheless, technical employees should know the technical guidelines and policies, along with the effective application of the security software, to increase their likelihood of preventing cases of information theft in online retail. Guidelines are procedural document lists and strategies adopted by business organisations. In most retail companies, the guidelines are developed based on the policy of the individual department. Employees pay less attention to these guidelines perhaps because of the light consequences of their violations. More attention should be given to the preventive guidelines on information theft prevention and other common data recovery plan guidelines. The management at this level should be responsible for the coordination of different aspects, such as the training of staff, incident management and rule-enforcement policies and guidelines.
The training of the employees in areas of information protection and data security should be their priority. They can organise seminars for the training of employees, while ensuring effective incident management and analysis. This involves the management and analysis of the aftermath of identity fraud occurrences. The ability of the companies to implement rigorous incident management procedures relies heavily on the effectiveness of the middle management. Without such cooperation of the middle management and top management, information theft would be difficult to manage.
6.3.3.3. Supervisory Management
Also known as the first-line management, supervisory management usually consists of store managers, shift supervisors, foreperson and team leaders. Their basic role is the supervision of everyday business operations. Since first-line managers have a strong influence over the employees and interact with them on a daily basis, they can play a vital role in the detection and investigation of identity theft related crimes. The major problem facing investigation of these crimes still boils down to lack of clarity of responsibility and less interaction or flow of communication between management and employees, thus making cases of internal information theft difficult to prove when the perpetrators are caught. Supervisors can help address this problem by facilitating constant communication with employees.
6.3.3.4. Roles of Human Resource Management
One of the most effective ways to mitigate the threat of internal information theft schemes (e.g., collusion and coercion) is for human resource managers to raise the level of awareness among all employees. It is important to let all the employees know the consequences of colluding or involving themselves in any form of internal identity related crimes. Organisations, through human resources, need to ensure that staff members are aware of where to report the cases of fraudulent activities within the organisations. There should also be the provision for the employees to feel confident that the matter would be treated professionally. Based on this consideration that the role of human resource management is very vital in prevention of information theft, the structure of RBF (see Figure 6.1 above) depicts two loops in which the top and the middle level management roles and responsibilities are hinged.
6.3.3.5. Roles of Law Enforcement Agencies
These are agencies that have a vital role to play in retail operations, as they may have essential access to employees and skills to tackle internal information theft cases beyond the reporting of incidents. Outsourcing specialist teams to deal with these crimes is recommended. They can also play a major role in educating businesses on best practices for effective internal information prevention measures. Retail managements can assist law enforcement and regulatory authorities in the fight against internal employee fraud by providing them with vital information regarding business organisations, given that taking legal action against the fraudster might be expensive and also an effective deterrent for others (ACAS, 2008). It is the role of retail management to create awareness of policies of data protection and the role of law enforcement agencies to enforce the policies. The policy for prevention of information theft in retail industry should include these purposes:
- Protection of stakeholders and information;
- Set of rules for expected behaviour of employees, management, system administrators, security personnel, and users;
- Authorise and define the consequences of violation of rules, authorise security personnel to investigate, monitor and probe;
- Help to minimise security risks, define industry consensus stance on information and data security.
These policies and legislations can be deployed and made available across management, technical and employees’ levels. In addition, other governing policies, technical policies and guidelines should be adapted to cover information and related proprietary data security. In doing so, the government data protection data and other important legislations should also be incorporated into the overall company’s security policy.
However, in the UK, for instance, some retail companies still neglect the integration of the government’s data protection acts, such as the Data Protection Act (1998), Freedom of Information 2000, and Computer Misuse Act 1990. Sommer (2012) has advised that raising awareness among all employees about this relevant legislation relating to data security has proved to be one of the effective ways to mitigate the threat of information theft in businesses.
6.3.3.6. Collective Roles
The employees and stakeholders in online retail are expected to make more than just economic contributions. Both parties need to see and begin to recognise their responsibility to secure and promote information management in their companies (Listermann and Romesberg, 2009). This responsibility should not be limited to the level required by law, but should extend to protection of identity proprietary information in order to achieve secure retail business operations. The application of the concepts of Corporate Social Responsibility (CSR) in the context of prevention of internal information theft in retail information systems security is still scarce in practice. Although CSR has been applied extensively in many business sectors, retail information security management in particular is still behind (Tsiakis, 2009). The Basel Committee on Banking Supervision encourages senior management to promote their organisational culture by exemplary life through integrity. There is a need for online retail companies to stress the importance of trust between the managers and employees. This would assist in monitoring employees’ suspicious lifestyles, which may pose potential detrimental effects to both the employee and employer. Intelligence agencies and top human resource managers have listed various policies which could create a desired culture in every organisation.
Some of these include fraud management policy, employee fraud prevention policy, code of conduct or business ethics, disciplinary policy, fraud reporting policy whistle blowing policy, staff assistance policy and fraud specialist policy, etc.
Prevention of internal information theft in retail companies can also be provided through a company’s CSR—a voluntary commitment to internalise in corporate pivotal decisions and strategy practices that contribute to social development. There is need for the security managers to incorporate CSR activities into a corporate strategy of information security practices. Lewis (2006) suggests that incorporation of motivation in the workplace for the employees who promote honesty has contributed towards the development of ethical company cultures, which in turn reduces the cases of information theft in retail businesses.
6.4. Summary of Chapter 6
This chapter has provided knowledge on how collaborative security and crime prevention management can be structured to maximise the management roles in the prevention of internal information theft. As earlier discussed in Chapter 5, the orientation of management in relation to the organisational culture of retail companies may not be separated from the security management. For an effective prevention of internal information theft in retail companies, there is a need for change in the cultural orientation from independent security to collaborative security. Braithwaithe (1989) suggests that the increased emphasis on collaborative managerial responsibility embedded in an understanding of cultural influence aimed at ensuring compliance is more likely to have long-lasting benefits in preventing corporate or business crimes than other deterrence measures.
Based on this argument, Dahler-Larsen (1997) concludes that all the management and employees have their ‘share’ of responsibilities to play in the way their operations justify their decisions and actions regarding security and crime prevention practices.
The knowledge of collaborative management on the prevention of internal information theft in retail companies would equip security and crime prevention managers with a valuable tool in managing the multicultural dimension of the management work force. This knowledge would also equip the management to develop a strategic cross-functional and socio-cultural skills needed for preventing and investigating internal information theft incidents. However, management role sharing can be affected by a number of factors, including people, operations, processes, organisational roles, and technology and management characteristics. These factors can be relevant to the success of information systems (IS) security in organisations. If there is clarity of roles by the management, then the adoption of collaborative management can be beneficial to retail companies. The ways of improving collaborative management strategies can be simplified by asking these key questions:
- What are the key roles that can clearly impact security management performance in the prevention of internal information theft?
- What practices are likely to improve collaborative management between security and crime prevention in the prevention of information theft?
Attempts to answer these questions would provide insights into the applicability of collaborative management in the prevention of internal information theft. The next discussion, in Chapter 7, provides knowledge of the practical application of collaborative management in the case of data compliance audits of selected companies in the UK.
References
ACAS. (2008). ‘Advisory handbook: Discipline and grievances at work’. Available: http://www.acas.org.uk/media/pdf/s/o/Acas-Guide-on-discipline-andgrievances_at_work_(April_11)-accessible-version-may-2012.pdf, Accessed 7 December 2011.
Braithwaite, J. (1989). Crime, Shame and Reintegration. Cambridge: Cambridge University Press.
Dahler-Larsen, P. (1997). Organizational Identity as “Crowded Category”: A Case of Multiple and Quickly Shifting We-typifications. In: Sackmann, S. (ed.): Cultural Complexity in Organizations (p. 367–90). Thousand Oaks: Sage.
Data Protection Act. (1998). ‘Part VI (Miscellaneous and General), Section 55, Office of Public Sector Information’. Available: http://www.legislation.gov.uk/ukpga/1998/29/section/4, Accessed 14 January 2014.
Ekblom, P. (2010). Crime Prevention, Security and Community Safety with the 5Is Framework. Basingstoke, UK: Palgrave Macmillan.
Financial Crime and Service Authority (FCSA). (2009). ‘Consumer Financial Education: Money Made Clear’.
Gercke, M., de Almeida, G.M., Lawson, P., Callanan, C. and Simion, R. (2011). Handbook on Identity Theft Related Crimes (3rd edn.). United Nations Office on Drugs and Crimes, Vienna, Publishing and Library Section, pp. 107–169.
Gilling, D.J. (2009). Multi-Agency Crime Prevention: Some Barriers to Collaboration, The Howard Journal of Criminal Justice, 33(3), pp.246–257.
Karn, J. (2013). ‘Policing and crime reduction: The evidence and its implications for practice’. Police Effectiveness in a Changing World Project, pp. 1–36. Available: http://www.police-foundation.org.uk/uploads/catalogerfiles/policing-and-crime-reduction/police-foundation-police-effectiveness-report.pdf, Accessed 24 June 2014.
Lewis, G. (2006). Organisational Crisis Management: The Human Factor, Auerbach Publications-Taylor and Francis Group: Boca Raton, New York.
Listerman, R.A. and Romesberg, J. (2009). ‘Creating a culture of security is key to stopping a data breach. Are we safe yet?’ Strategic Finance, pp. 27–33.
Sarnecki, J. (2005). ‘Knowledge-based crime prevention, theoretical points of departure for practical crime prevention’. Paper presented at the Eleventh United Nations Congress on Crime Prevention and Criminal Justice, 18–25 April 2005, Bangkok, Thailand, pp. 1–11.
Schneier, B. (2004). Secrets and Lies: Digital Security in a Networked. Hoboken, NJ: John Wiley and Sons, p. 432.
Sommer, P. (2012). Digital Evidence, Digital Investigations and E-Disclosure: A Guide to Forensic Readiness for Organisations, Security Advisers and Lawyers (3rd edn.). London: Information Assurance Advisory Council.
Tsiakis, T. (2009). ‘Contribution of corporate social responsibility to information security management’. Information Security Technical Report, 14 (4), pp. 217–222.
Wenger, E. (1998). Communities of Practice: Learning, Meaning, and Identity. Cambridge: Cambridge University Press.
Wenger, E., McDermott, R. and Snyder, W. (2002). Cultivating Communities of Practice: A Guide to Managing Knowledge. Boston: Harvard Business School Press.