Using Online Investigative Tools
This chapter introduces various online tools that can be used in the Internet investigations to aid in documentation, identification, and collection of Electronically Stored Information (ESI). Many of the tools described are free or inexpensive. They are also very user friendly. Additionally, this chapter contains numerous investigative website resources. The initial focus is on the free utility, the Internet Investigators Toolbar by Vere Software. The toolbar is broken into five drop-down menus, each with different investigative website resources. Readers are exposed to the Internet Investigators Toolkit, also by Vere Software. The Toolkit contains 11 action buttons containing important investigative utilities.
Key words
Internet crime; Internet evidence; Internet Investigative Toolbar; IP Traceroute; Whois; MX; Netstat; Ping; Resolve; TCIP/IP; Stats; Lexis-Nexis; TLO
It’s not the tools that you have faith in—tools are just tools. They work, or they don’t work. It’s people you have faith in or not. Yeah, sure, I’m still optimistic I mean, I get pessimistic sometimes but not for long.
Steve Jobs (1955–2011, American Businessman and founder of Apple)
Tools for the investigator are no different on the Internet than in the real world. Tools allow the investigator to understand and act within the environment and document what he sees within that environment. The tools available for his use are sometimes complicated and require a greater understanding of the tool’s effects on the environment. Effectively using a tool will help the investigator not only collect online ESI but possibly ascertain the motivations or intentions behind the person who created the data. The tools and websites described in this chapter will aid the investigator in identifying when, how, and where offenders have added ESI to websites as well as data found ancillary to the offender as recorded by third party websites. This chapter will explore some of the tool options that the Internet investigator has to assist in his evaluation of the Internet and its potential for finding online ESI data that is evidence of criminal or civil violations.
Investigative toolbars
One of the most useful developments in online investigations was the creation of toolbars specific to investigator needs. These toolbars have been designed around the needs of average Internet investigators and provide them with direct access to resources to enable them to quickly further their investigations. Two such examples of these toolbars are SEARCHinvestigative Community Toolbar by SEARCH.org and the Internet Investigators Toolbar by Vere Software. Both of these toolbars are free, available for download, and can be installed on the investigator’s choice of browsers, such as Explorer, Firefox, or Chrome. These toolbars provide various drop-down menus that give access to numerous investigative utilities and sites on the Internet. The SEARCH toolbar can be downloaded at http://searchinvestigative.ourtoolbar.com/. The Vere Software Toolbar can be downloaded from their website at www.veresoftware.com (Figure 6.1).
![]()
Figure 6.1 Snapshot of SEARCH.org toolbar.
Vere Software Investigative Toolbar
Of the two, we like Vere Software Investigative Toolbar because along with some of the same basic features of SEARCH’s toolbar, it also includes options for searching anonymously and is solely focused on Internet investigations tools. The SEARCH.org tool includes forensic references not usually germane to the Internet investigator. The Vere Software Investigative Toolbar provides resources for assisting in securing the investigator’s computer for Internet investigative activities. As such we will focus on navigating the features of Vere Software Investigative Toolbar. This toolbar allows easy access for the investigator directly from the browser to useful sites, such as Internet Protocol (IP) tracing tools and websites to search for people. Investigators can easily track IP addresses or search the various parts of the web. The toolbar also provides WebCase® the Online Evidence Tool users, access to Vere Software’s online training and forums associated with WebCase®. Downloading this toolbar can be done from the Vere Software website at www.veresoftware.com (Figures 6.1 and 6.2).
From left to right on the toolbar are the available resources for the investigator. The first drop down allows the investigator to access information about the toolbar. The next block gives the investigator quick access to the Bing search engine. The next drop downs are tools that provide the investigators access to the most used websites to assist them in their Internet investigations. We will discuss some of the more common sites. We won’t discuss them all because as everything on the web, things change frequently. Some sites change their locations and some sites just disappear.
IP Trace
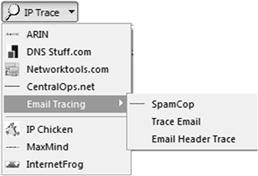
The IP Trace drop down provides the investigator with access to Internet resources that assist in the investigation and identification of IP addresses. The first resources include tools to identify the domain ownership of IP addresses included ARIN, DNS Stuff, Network Tools, and Central Ops. The next resources are to assist the investigator trace emails and identify the sender of an email. The remaining resources help to identify the geolocation of IP addresses (Figure 6.3).
The web links to ARIN, DNS Stuff, Network Tools, and Central Ops are tools that allow the investigator to determine information about the ownership of domain addresses and IP addresses. Each of the websites provides some of the same basic information such as the Domain registration information. Each site presents other options for identifying additional information about the domain name or IP address. The investigator uses these sites to identify ownership, addresses, and telephone numbers associated with domains and IP addresses. With this information one can begin an investigation into a targeted domain or IP address.
The email tracing features provide the investigator with links to websites to assist in tracing emails. Spamcop is a great resource for identifying how to access email headers on various email programs. The email tracing references allow the investigator to cut and paste the email headers into the website, which parses out the IP addresses and other information in the header. The remaining sites, IPChicken, MaxMind, and InterentFrog, are used to geolocate an IP address. Geolocation is the locating of a physical location associated with the IP address. Now, for the investigator this does not necessarily mean the actual location of the suspect. It often only means the city. In some circumstances it can mean a physical address, but this is generally where the server of an Internet service provider (ISP) is that uses the IP address.
Web Find
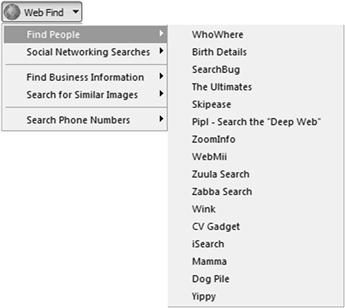
The Web Find drop down provides the investigator with access to Internet resources that assist in the investigation and identification of people and businesses on the Internet. The first resources under “Find People” include numerous resources to research people on the Internet. The next section is resources to search social media sites. The following sections include business search resources, sites to search for similar images, and sites to research telephone numbers (Figure 6.4).
The Web Find resources include five general categories of online resources: Find people, Social Networking site searches, Find Business Information, Search Similar Images, and Search Phone Numbers. Each of the categories contains several different resources for the investigator. The Find People category has numerous sites of interest to the investigator. Each site has a variety of information and can individually provide the investigator with a start to identifying additional information on the target. Collecting information from multiple sites can provide a clearer picture of the target, their family members, and even addresses. Some of the sites include:
1. ZabaSearch: This site is a search engine that means it indexes information and does not store it. Zaba search indexes only information on people that is found on the Internet and collated. They collect information from various places on the web, including phone directories, public records, and social networking sites.
2. Pipl: This site searches multiple search engines and produces what they call information from the “Deep web.” The site is able to identify large amounts of data and produces it on an easily to follow manner. The identified data is linked to its source and quickly reviewable.
Website Info
This drop down provides the investigator with access to Internet resources that assist in website investigation and identification. The resources include websites to identify information on specific sites, including archived information found on the Internet about those websites.
The Website Info resources include five general categories of online resources: Find Information on websites, Find Old Webpages, WebServer Information, Safe Surfing Checks, and Translate a website or text. Each of the categories contains several different resources for the investigator. The Find Information on websites has several sites of interest to the investigator to ascertain website information. The Find Old Webpages links provide resources to identify what a webpage looked like in previous iterations. WebServer Information links give the investigator access to several resources to determine the communication between the investigator’s browser and the webpage and servers he is connected. Also in this section are resources to help check websites for malware, translate websites and a tool to save videos from websites (Figure 6.5).
Internet service provider
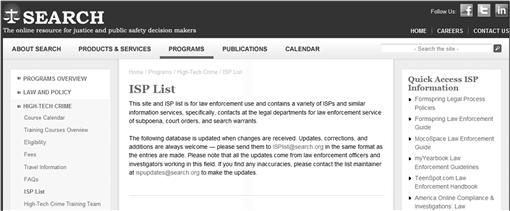
The ISP drop down provides access to one of the most important Investigative resources on the Internet, the SEARCH ISP list. This resource provides a list of the legal contacts for Internet Service Providers and various websites to expedite the service of subpoena, court orders, and search warrants. The ISP list was originally started by James Nerlinger, who still maintains the Computer Forensic Investigators Digest (CFID) list server, as a service to the forensic community. In 2005, Todd G. Shipley, then the Director of the SEARCH High Tech training program, arranged to take over the list to continue its existence as a resource. The High Tech training staff at SEARCH has continued to update the list to provide the digital forensics community with a much needed resource. The information is updated as newer information is identified and shared with SEARCH. Additionally on the site can be found the publically available law enforcement guides for various ISPs and popular social media sites (Figure 6.6).
Secure
The Secure drop down provides access to Internet resources that assist in securing the investigator’s computer systems. The resources include websites to help the investigator identify potential security breaches in the computer they use to access the Internet. These tools can assist in determining the need for updating and securing investigative machines (Figure 6.7).
Additional toolbar functions
On the toolbar there are several other functions available to the Internet investigator that may be of interest. This includes a button to identify the current outward facing IP address as recognized by the browser. This allows the investigator to quickly identify what IP address he is using that is exposed to the Internet. Additional buttons include a tool to identify the speed of the Internet connection and one to allow the investigator access to a proxy website to allow temporary hiding capabilities for the investigator. Included in the toolbar is also access to Vere Software’s training material, including videos on WebCase® and other documents.
The Internet Investigators Toolkit
Specifically built for the online investigators needs, the Internet Investigators Toolkit is a quick desktop application that allows you to obtain information about web ownership and domain information. The Toolkit is a compact Java tool that enables quick assessment, from the online investigator’s desktop, of information about websites and other online activities. The tool is free to law enforcement investigators and can be downloaded from the Vere Software website www.veresoftware.com (Figure 6.8; Table 6.1).
All of the tools in the Internet Investigators Toolkit are common utilities found on various websites regularly used to conduct online investigations. Each of these programs has the option to save the results into a document file to allow the recording of the information later in the investigator’s report. Let’s take a look at each of the tools and what function they serve in the Internet investigation.
Whois
Whois serves the Internet investigator as the basic tool for identifying the domain registration of a website. Domain registration, if legitimate, can provide the investigator with the next step in the identification of a website owner. Commonly we can find tools such as those on the Internet Investigators Toolbar that serve the same function. The domain registration for a website can detail significant information as to the operation of the website and the person or company that owns it. Table 6.2 details the type of information that is found in the domain registration of a website.
MX function
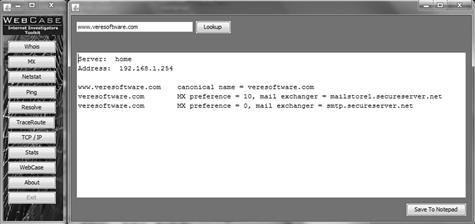
MX serves as a tool to identify the mail server records of an email address. It researches the email address provided and returns the following records as shown in Figure 6.9.
The MX records include three specific pieces of important information about the domain investigated (Table 6.3). They are:
| www.veresoftware.com | canonical name=veresoftware.com |
| veresoftware.com | MX preference=10, mail exchanger=mailstore1.secureserver.net |
| veresoftware.com | MX preference=0, mail exchanger=smtp.secureserver.net |
Table 6.3
| Record Name | Record | Explanation |
| canonical name= | veresoftware.com | Proper name for address |
| MX preference= | 10 | The priority by which the mail agent handling the mail routes the mail to a particular server. Mail is routed to the server with the lowest number |
| mail exchanger= | mailstore1.secureserver.net | Server location to actually route the mail |
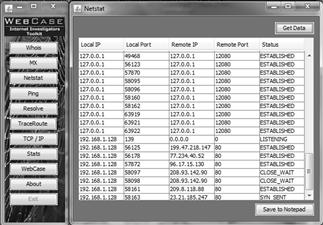
Netstat
Netstat serves as a tool to identify the real-time connection of IP addresses between two computers. What this means during the Internet investigation is that during chat sessions certain chat program functions allow the user to send documents or pictures between two people communicating through the chat program. When this occurs the two chatters make a direct connection between their computers through their IP addresses. (Chat programs will be further explained in Chapter 15.) Netstat is a program when running that can capture this traffic and record the incoming IP address of the target of the investigation (Figure 6.10).
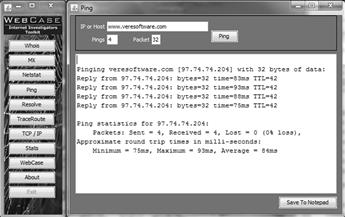
Ping
Ping is utility to identify if a particular IP address is accessible through the Internet (or intranet). Ping sends a series of packets to the specific address and waits to see if there is a reply from the computer behind the IP address. In the networking world, Ping was commonly used to identify problems in a network. Today many servers and computers on the Internet ignore the requests thinking that it might be a hacking attempt (Figure 6.11).
Resolve
Resolve serves as a tool to enter a web address, such as www.veresoftware.com, and identifies the corresponding IP address that represents that URL: 97.74.74.204. It will also do the reverse, turning an IP address into a URL. This program provides the investigator further information as to the potential owner of an IP address (Figure 6.12).
Traceroute
Traceroute identifies the route a packet travels from the IP address of your computer to another IP address. The Traceroute tool records each hop, or server it goes through, as it travels across the Internet and the time each hop takes to move to the next. This can be informative as to possible paths an email of packet may have travelled, but because of the Internet’s make-up it can only provide the path at that time the Traceroute was run and not the path a previous packet took, or will take in the future (Figure 6.13).
TCP/IP function
The TCP/IP function identifies the current configuration of the investigators network connections. This includes IPv4 and IPv6 addresses of the local machine, its MAC address, the machines default gateway (the router address of the device they access the Internet through and other connection information) (Figure 6.14).
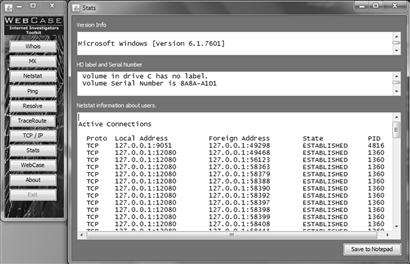
Stats function
The Stats tool documents certain information about the computer that it is run on. This includes identifying information about the computer, including the Microsoft Windows version, the hard drive descriptive information as provided through the operating system, active TCP/IP connections, and other routing information (Figure 6.15).
Other buttons
The remaining functions of the Internet Investigators Toolkit are buttons that open WebCase®, if the user has a licensed version on the machine it is running on. The About button identifies the maker of the tools and the Exit button closes the tool.
Paid online services
To add in the investigation and location of online criminals, there are numerous pay for services that are available to assist in locating suspects. These services all provide a variety of information based on a name, an email address, telephone/cell number, or other descriptive personal identifying information. These services are unique to the United States based on the limited privacy laws. Most of the information recorded comes from various purchased databases and then are collated with other databases to form a picture and background of an individual or company. The database information is often purchased from government agencies that sell the collected information about its contacts with citizens, such as property records or marriage records. Of course this is individual to each state and its regulations. Some locales may not sell this information. There are many online services that for a simple credit card charge provide you the information you are requesting on a person or business. No background on the purchaser is normally required other than to complete the request and provide a credit card number.
Be aware that the time this book is being written, the Federal Trade Commission (FTC) issued orders to the following nine data brokerage companies: (1) Acxiom, (2) Corelogic, (3) Datalogix, (4) eBureau, (5) ID Analytics, (6) Intelius, (7) Peekyou, (8) Rapleaf, and (9) Recorded Future. The orders are seeking information about how these companies collect and use data about consumers. There is a concern about the transparency in the collection of consumer information and that many consumers don’t even know the information is being sold, and/or have the ability to correct erroneous data that is contained in these records. The FTC is currently in the process of studying privacy practices in the data broker industry and is going to use this information to “make recommendations on whether, and how, the data broker industry could improve its privacy practices” (FTC, 2012).
Much of this increased scrutiny is no doubt due to apparent inaccuracies or incomplete information maintained by some in the data broker industry. The situation is aggregated when erroneous information cannot be corrected or purged easily by consumers. The increased FTC scrutiny will likely increase the quality of these records. It, however, may limit the ability to get access to these records in the future. The caveat for the Internet investigators is to only use records maintained by data broker company as a starting point. For instance, if a data broker record was to reflect an individual had a criminal record, the original source of that information should be sought, such as the court maintaining the conviction information. Relying solely on data broker records without independent inquiry could result in inaccuracies or investigative missteps.
One of the greatest strengths of using large data broker services, such as Lexis-Nexis or TLO, is they frequently have the ability to point out patterns in the data, reflecting relationships between individuals and/or companies, that might be overlooked if using individual investigative resources. This can be very important in tying together parties involved in criminal acts that literally span the Internet and the world.
Lexis-Nexis®
Lexis-Nexis is one of oldest, largest, and respected data brokers. It was originally founded in Ohio in 1973 through the collaborative efforts of a Jerome Rubin and Donald Wilson on behalf of the Mead Corporation (Miller, 2012; UPI, 2006). Initially it was focused on legal documents and journalism, which were made available online, over telephone lines via a dedicated terminal the size of a washing machine (Miller, 2012). As record management digitalization grew so did Lexis-Nexis researching capabilities. The company reports providing its customers with access to billions of searchable documents and records from more than 45,000 legal, news, and business sources (LexisNexis, 2013). Additionally, they note they have a “…comprehensive collection of over 36 billion public records for comprehensive information on individuals and businesses—including names, addresses, places of employment, cellular and unpublished phone numbers, licenses, property records, and much more” (LexisNexis, 2013).
Lexis-Nexis provides a variety of online investigative products, including those targeted to serve law firms, corporate legal, government, corporations, and the media. There are two pricing options, transactional and flat rate. Transactional pricing falls under two plans, hourly and per search, both of which operate as “pay as you go.” Flat rate pricing has two plans, Volume Bonus and Authorized User. Each of these flat rate plans has pricing based on a monthly fixed commitment usage in exchange for discounted rates (LexisNexis Pricing Plans, 2013).
TLO®
TLO® was founded in 2009 by Hank Asher, an innovative and colorful technical entrepreneur of over 25 years. TLO was not Asher’s first entry into the database brokerage business. He had developed Database Technologies, which he sold in 1999 and later Seisint, which he sold to Lexis-Nexis, in 2006. Asher named TLO®, which stands for “The Last One”, as an indication that it would be his last business venture, which it was as he died in 2013. At the time of his death, Asher was reportedly the largest financial donor in the history of the National Center for Missing and Exploited Children and provided TLO® child protection software at no charge to law enforcement in 40 countries (Gale, 2013).
TLO® notes there are “no sign-up fees, no monthly minimums, no long-term contracts required.” It also has two fee structures, either flat rate or transactional structure (TLO®—General Pricing, 2013). TLO® provides the ability to search for information on individuals or businesses. Search reports include the following:
• Individuals: Names, Aliases, and SSNs; Bankruptcies, Foreclosures, Liens, Judgments, and Criminal History; Current and Historical Addresses; Phone Numbers including Listed and Unlisted Landlines, Cell Phones, and Utilities Data; Relatives, Neighbors and Associates; Assets including Property and Vehicles; Licenses including Professional, Driver’s, and Email addresses and Social Networks.
• Businesses: Current and Previous Employees, Officers, and Directors; Assets Bankruptcies, Liens, and Judgments; UCC Filings; Current and Historical Phones, Addresses, and DBAs; Branches, Subsidiaries, Parent Companies, and Headquarters (TLO® People Searches & Business Searches, 2013).
Conclusion
This chapter was designed to provide the reader with a basic understanding of some of the tools available to the Internet investigator for identifying and recording evidence found on the Internet during an investigation. Discussed were basic tools and resources the investigator can employ to assist during an investigation. As with any tools employed during Internet investigations, the investigator should become familiar with the concepts and output of the tools prior to use. Process and tool validation are also important and should be conducted before employing during real investigations.
Further reading
1. FTC to Study Data Broker Industry’s Collection and Use of Consumer Data. (2012, December 18). Federal Trade Commission. Retrieved from <http://www.ftc.gov/opa/2012/12/databrokers.shtm>.
2. Gale K. TLO’s Hank Asher: A one of a kind technology pioneer, dead at 61. South Florida Business Journal 2013, January 14; Retrieved from <http://www.bizjournals.com/southflorida/blog/2013/01/tlos-hank-asher-a-one-of-a-kind.html?page=all/>.
3. Internet Investigators Toolbar. (2013). Vere Software. Retrieved from <http://www.veresoftware.ourtoolbar.com/>.
4. LexisNexis. (2013). Public record search tool, LexisNexis. Business solutions & software for legal, education and government. Retrieved from <http://www.lexisnexis.com/en-us/products/public-records.page/>.
5. LexisNexis Pricing Plans. (2013). Business solutions & software for legal, education and government. LexisNexis. Retrieved from <http://www.lexisnexis.com/gsa/76/plans.asp/>.
6. Miller S. For future reference, a pioneer in online reading. Wall Street Journal 2012, January 12; Retrieved from <http://online.wsj.com/article/SB10001424052970203721704577157211501855648.html?KEYWORDS=lexisnexis/>.
7. Request for Comments: 5321 Simple Mail Transfer Protocol. Retrieved from <http://tools.ietf.org/html/rfc5321/>.
8. SEARCH. (2013). SEARCHinvestigative toolbar download. Retrieved from <http://searchinvestigative.ourtoolbar.com/>.
9. TLO®—General Pricing. (2013). Investigative research & risk management tools—TLO®. Retrieved February 7, 2013, from <http://www.tlo.com/general_pricing.html/>.
10. TLO® People Searches & Business Searches (2013). Investigative research & risk management tools—TLO®. Retrieved from <http://www.tlo.com/reports.html/>.
11. UPI. Lexis-Nexis founder Don Wilson dies Retrieved from United Press International 2006, December 1; Retrieved from <http://www.upi.com/Top_News/2006/12/01/Lexis-Nexis-founder-Don-Wilson-dies/UPI-36121164992489/>.
12. Vere Software—Online Evidence Collection & Documentation. (2013). Vere Software Internet Investigator’s Toolbar. Retrieved from <http://veresoftware.com/>.