Online Digital Officer Safety
This chapter introduces the reader to the various tools needed to protect the Internet investigator’s computer system during the course of their activities. This includes how to set up the computer, the various utilities available to the investigator to secure the computer, and methods to test that security. Firewalls, anti-malware, encryption, and wiping tools will be discussed, including some vendor suggestions. General computer security fundamentals are stressed, such as installing and keeping protective utilities up to date, as well as patches for operating systems and investigative tools. Additionally, this chapter discusses various browsers and their configuration for optimum safety and security. Finally, this chapter also gives advice on how to set up and protect a wireless Internet connection.
Keywords
Digital officer safety; firewalls; routers; malware; malicious websites; antivirus; anti-spyware; rootkits
Man is a tool-using animal. Without tools he is nothing, with tools he is all.
Thomas Carlyle (Scottish Philosopher, 1795–1881)
Digital officer safety
Conducting Internet investigations is not without computer security problems. Anyone going online should take basic precautions to prevent the problems associated with viruses, spyware, and/or other malware (Figure 7.1). This chapter will not deal with undercover situations which will be discussed at length in Chapter 10. Instead, it will prepare the new investigator with the various tools needed to ensure successful investigations by limiting exposure to Internet dangers.
All products mentioned in this chapter are property of their respective companies. This is not an exhaustive list of potential software applications available in each category, but merely suggestions for the investigator who is new to online investigations. We have found the noted products useful in safeguarding your investigative computer from compromise by either a virus or other malware.
The intent of this chapter is to provide the investigator with some consideration for the various protective utilities available. Obviously, tool installation will depend on the investigator’s administrative control over the operating system used for online investigations. Many government-owned computers require the user to obtain permission to load any additional software onto an agency-owned system and require administrative access to do so. In most cases, an agency’s IT department will be protecting their system and the attached computers will have many of these same application types. These suggestions are for the investigative computer not generally attached to an agency’s network or behind existing firewalls. The online investigator needs to be aware of the potential Internet threats in order to help protect against data leakage, loss, and potential system compromise. The online threats to an investigator continue to be those commonly reported, such as viruses, malware, and other malicious code and external attempts to access your computers. Each of the thousands of threat types can be protected against if the investigator understands the requirements and the tools to do so. It is important for the investigator to protect his system to keep viruses and other threats from spreading to other agency-controlled systems. It is also important to protect the validity of the investigation conducted and ensure that any Internet electronically stored information ultimately collected is protected from these potential threats .
Online investigative computer protection process
Protecting your investigative computer is a continuing process that requires constant attention. Generally, government and corporate systems are protected by an Information Security section that has mandates to protect the network from intrusion. Federal agencies and certain contractors have to comply with the Federal Information Security Management Act of 2002 (FISM) (OBM, 2010). This United State legislation … “defines a comprehensive framework to protect government information, operations and assets against natural or man-made threats” (Rouse, 2011). The US Department of Homeland Security … “exercises primary responsibility within the executive branch for the operational aspects of Federal agency cybersecurity with respect to the Federal information systems that fall within FISMA” (FISMA, 2013). In general, FISMA does not exempt the undercover use of computers or the investigative needs of investigators (OBM, 2010). A federal agency’s consideration of this chapter’s recommendations needs to take FISMA into account.
Security protocols may include certain restrictive functions that can prevent the Internet investigator from successfully accessing areas on the World Wide Web or other protocols to conduct required research and investigations. This is obviously a necessary function within large-networked environments. The Internet investigator may be required to have a machine or machines that are outside of the organizational network to prevent any contamination of the network through accessing websites. These machines would also allow the accessing of Internet protocols such as IRC, P2P, or newsgroups that would normally not be allowed in a networked environment. Legislative mandates and organization policy will dictate the approach the Internet investigator takes in this regard. Setting up the investigative computer will be of course also depend on its purpose. The investigator should prepare their computer with the tools required for the investigation. Having additional ports1 open that are unnecessary for the investigation’s purpose may put the computer at risk.
Additionally, separate machines for accessing the Internet along with a separately purchased Internet access account may be required. This provides the Internet investigator the ability to have access to IP addresses that do not return to the organization. This prevents anyone that does research on the investigator’s IP addresses from immediately being able to identify their organization. Purchase of such “clean” accounts should not be done with a credit card that comes back immediately to the organization either. There could be a possibility that the organization’s information is tied to the account or the IP address if a static IP is used.
The question that is bound to be raised by many of you is which operating system should an investigator use for their investigative machine. Specifically, is a Windows-based system, a Linux or a Macintosh system more secure? There are more viruses and other malware out there that target Windows-based systems. However, Macintosh systems also can be attacked by malware and this trend is growing. Linux is not generally a system used by new users. Windows machines have a larger share of the market, including among government agencies. As a result, more folks are accustom to their use. Additionally, vendors, aware of this larger market share, provide more programs, including those that can be used for investigative purposes, for Windows-based systems. As such, the question becomes not only which system is more secure but which system can be made secure and provide more options for the online investigator. In the end, both operating systems can be attacked. We are providing procedures that may seem to have a Window’s bias. In reality, these protective measures should be employed regardless of which operating system an individual or agency decides is the best investigative option and value for them.
The process of protecting your online activities will depend on your current computer configuration and the protection you already have employed. We can break the process down into two main categories and then into subsections of each of the two main sections. These two main sections include basic preparation and protection of the investigative computer and continuing security maintenance for keeping the investigative computer secure. The following are the steps for each:
1. Basic preparation and protection
• Firewall installation and updates
• Antivirus program installation and updates
• Spyware detection software installation and updates
• Installation of browsers and browser updates
• Configuring the system’s operating system and making sure it is up to date
2. Continuing security maintenance
• The potential for using encryption
• Software updates, tools, system, antivirus, anti-spyware programs, etc
• Testing the security of the system
• Regular or programmed backups. (See figure 7.2).

Figure 7.2 Online investigative computer protection process.
Basic investigative computer protection
Protecting the investigative computer is sometimes overlooked or not given the required attention. An investigator’s priority can be to get online, collect the evidence, research the bad guy, and solve the crime. However, not doing the basics in protecting one’s self from Internet dangers is no different than a policeman going to work without a bullet resistant vest and gun. The following sections are intended to outline some basic procedural steps in securing the investigator’s computer.
Firewall installation
One of the most important aspects of controlling, wanted or unwanted, traffic to and from your computer is through a firewall’s use. The Information Assurance Technology Analysis Center defines a firewall as:
… “is an application (or set of applications) that create a barrier between two domains, in whatever way ‘domain’ is defined (i.e., physical domain, logical domain, virtual domain). All firewalls enforce an ingress control policy that is based, at least in part, on traffic filtering. Many firewalls provide other security features, but these are not necessary for an application(s) to be deemed a firewall. In all cases, the purpose of the firewall is to protect entities in one domain from threats originating in another domain” (pg. 6).
Firewalls can be either software or hardware and provide a barrier between computers or networks and untrusted areas, such as the Internet. Firewalls can also be set up between networks inside an organization, creating an additional barrier between sensitive information and the rest of the organization’s network. Firewalls operate as gatekeepers, allowing only approved communication to occur with the protected area. As gatekeepers, they can prohibit communication with predetermined malicious websites or blacklisted URL. Additionally, they can check packet traffic for malicious code or activity and stop it from reaching the protected area. They also operate to prevent communication from occurring from inside protected areas that should not be happening, such as the transmission of confidential data or communication being attempted beyond approved protocols. If you do not install firewalls, your system may be compromised by viruses or other attacks and cease to function properly. Firewalls are therefore clearly an essential tool in controlling what happens to your computer while conducting online investigations.
You should have both software and hardware firewalls running in place. They protect against different things and each has their strengths/weaknesses. When setting them up, make sure to check the box to be notified for updates; otherwise, check their websites regularly for periodic updates. These updates can mean the difference between blocking an attack (intentional or otherwise) and having to restore to a clean machine state to halt any possible intrusion. Often the software programs will alert when a new version is available, but don’t rely on the vendor’s tool to provide update notifications. Plan your investigative schedule to check for hardware and software updates regularly.
Hardware firewalls
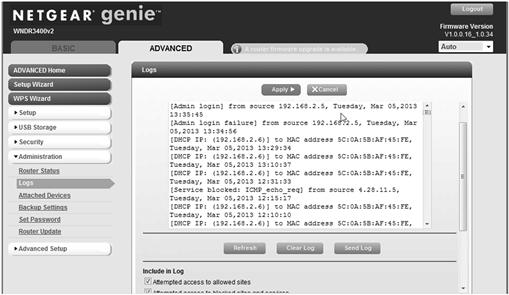
Hardware firewalls come in a variety of types. There are commercially available systems that can cost thousands of dollars and are used by network administrators to control any size network. The most commonly available routers for general use are the types that connect to the average Small Office/Home Office (SOHO) network. They are small, easily configurable routers which contain firmware that allow for simple user configuration. They are specifically intended for SOHO use with DSL or cable modem connections. Most have a wireless capability installed as a feature on the router which allows the use of a laptop, or other device, anywhere within the range of the wireless router. Range from which a device can connect through the wireless function depends greatly on the make and model of the firewall. Routers also allow the investigator to distribute their broadband Internet connection between multiple computers. Putting together a SOHO network allows your investigative team to back up computer’s files on networked computers or storage devices in case an infected machine needs to be restored. Additionally, routers often have features that can be of potential use to the online investigator such as logging (Figure 7.3).
The logging feature can assist the investigator in the identification of attempted, or successful, intrusions into their investigative system or network. The logs can also identify when investigative systems accessed the Internet and potentially where on the Internet the systems went. Each router and its configuration are different. Be sure to read the manufacturers’ manual to identify individual device features. At a minimum, the following common steps should be considered for router security:
1. Enable encryption: Current SOHO routers generally have Wired Equivelent Privacy (WEP) (an older hackable encryption system), Wi-Fi Protected Access (WPA) preferable, or WPA2 encryption. Ensure you turn on the encryption and use a strong password/passkey; otherwise, anyone with a wireless card could connect to your wireless access. If available, choose WPA-PSK (pre-shared key) and use a strong password/key.
2. Change the service set identifier (SSID)/disable broadcast: If you enable the wireless function, the default SSID (or wireless name for your access point) for your router needs to be changed to something unique to your system and does not identify the organization. The default SSID name makes it easier for hackers to identify and exploit your system. Disable the SSID broadcast so it cannot be seen. This will make your system stealthier and harder to discover. Simply turning off this function can prevent attack issues from the wireless feature.
3. Remote management: Turn off remote management. Sometimes called Wide Area Network (WAN) Management. This feature lets you change the router’s settings from the Internet. It’s an excessive risk and one that does not need to be taken.
4. Change the access password to your router: The default password for your router can probably be found on the Internet. Select a strong password of at least eight characters, using a combination of letters, numbers, and symbols. The password selected should not be a word easily found in the dictionary.
5. Disable Universal Plug and Play on the router.
6. Media Access Control (MAC): A good security option is MAC addressing. This ties hardware device addresses for each computer to a specific network subnet address (as assigned by your router) associated with your machine in order to validate the devices. It prevents unauthorized access to your network by unknown hardware.
7. Ping: Uncheck any options that allow the router to respond to a ping command from the Internet. No need to let anyone know your router is online.
The inclusion of the software mentioned here is for the reader’s use. The authors have no interest in the software referenced in this chapter. Many software packages of a similar nature exist and new products are deployed regularly. Many of the vendors provide applications that provide blended protection, such as including a firewall, anti-malware, and data backup functions in one package. The reader should use the software mentioned as a starting point and research current versions and other software for potential use on the investigative computer system. Good research sites for reviews on protective tools are CNET (http://www.cnet.com), PC World (http://www.pcworld.com), and SC Magazine (http://www.scmagazine.com). These sites routinely evaluate, compare, and publish the results on protective software and hardware. Be careful with “free” versions of anything. Most of them come with some adware or tracking software which could expose an investigator.
Software firewalls
The Windows operating systems since Windows XP SP2 (Service Pack 2) have each come with a built-in software firewall. If you use them, ensure that you have the latest version and updates installed. There are also many commercial software firewalls that offer different features and functionality than the Windows firewall. Often the use of something other than the Windows firewall is a matter of preference. If you use another commercial firewall, be sure to check its compatibility with Windows firewall. The Windows firewall may need to be turned off to allow the proper operation of the added firewall. Often the Windows operating systems do not operate well when two software firewalls, or antivirus programs, are running at the same time. Be sure to disable the Windows firewall before loading any other firewall to prevent any conflict between the software firewalls. Firewalls should obviously be configured to prevent malicious intrusion into the investigative system. However, they should not be set so restrictively that individuals can’t access certain sites, such as social networking sites, that may be needed for investigative purposes.
Malware protection
Protecting your investigative computer from malware is another required basic step toward protecting your Internet investigations systems. A running antivirus application will help to prevent viruses and other potential attacks from compromising the investigator’s equipment and evidence collected. Antivirus application manufacturers provide products that assist the user in the prevention of computer virus infections. Generally, these products involve two techniques for detecting virus. The first and most prevalent technique uses antivirus signatures, which are … “a string of characters or numbers that makes up the signature that anti-virus programs are designed to detect. One signature may contain several virus signatures, which are algorithms or hashes that uniquely identify a specific virus” (Janssen, 2013). Antivirus software searches for these signatures on the hard drive and removable media (including the boot sectors of the disks) and Random Access Memory. If it finds a virus signature, it quarantines the file, with the anticipation of removing it from the system. The application vendor updates their virus signature database, which their software periodically checks for updates. The pitfall to this detection method is its vulnerability to a “zero-day threat.” For instance, a newly created virus’s signature takes time to be discovered and uploaded to the database. If the signature is not in the database, the antivirus application will not identify the virus if its only detection is through signatures.
Another method is heuristic analysis. In this approach, the antivirus software allows a suspected program to run in a controlled environment on the system before allowing it run on the user’s system (see Investigative Tips, Virtual Machines and Sandboxes in this chapter). If the suspected program performs any functions that are associated with malware, the antivirus application stops the program and notifies the user (Security News, 2013). The problem with this technique is it can lead to false positives. Because of these issues, many vendors have applications that blend the two approaches together.
Be sure to update the programs (and their virus definitions) periodically. Setting the program to check for updates that you can manually install is a good idea. Set up a policy within the investigative team environment about when to do full system scans; otherwise, the programs may not provide you with the complete protection they can offer. Some of the programs require a system reboot and can run the antivirus program for hours to ensure a hard drive is virus clean. This is best down at night so as not to impact investigations. It is not recommended that these tools do automatic update installations. This prevents an update from forcing a reboot during the middle of an investigation. During set up of the software, ensure to select not to update automatically.
Spyware protection
Spyware has become one of the most pervasive Internet threats and has become a common method to attack a computer. The simple act of accessing a website can result in the spyware installation. Besides tracking and reporting back on a user’s Internet history, some can capture personal data and login credentials. Some monitoring software, deployed covertly as spyware, can take and transmit screen shots and even activate a user’s webcam. Hyppönen (2012) recently described the capabilities of malware, known as Flame, to include keyloggers, screengrabbers, and the ability to turn on the microphone of an infected computer. Spyware therefore represents a serious data leakage threat. Additionally, spyware infestations can slow a computer to a crawl, with numerous pop-up ads, and browser redirects to malicious websites, which further compromise security. Infections can get so bad that sometimes the only recourse is to reformat the hard drive to remove the offending programs.
As with virus protection, you should update the programs/definitions periodically and do full manual scans; otherwise, the programs are as worthless as if they were never installed. Installing and using the listed software will remove most malware and keep a system clean. Most of the listed software offers the same functions. Running them all on the same machine would undoubtedly cause conflicts on the investigative machine. The investigator needs to review the software that best suits their needs and install only the needed tools for the investigation.
Installing and updating browsers
A browser is an application that provides a method for users to access and interact with text documents, graphics, and other computer files on the World Wide Web. Three of the most popular browsers are Microsoft’s Internet Explorer, Mozilla’s Firefox, and Google’s Chrome. It is very important to keep the browser updated and when appropriate to move to a more recent version.
Internet Explorer (microsoft.com/downloads): Internet Explorer is the web browser that comes standard with Windows Operating System. The current version of Internet Explorer that is available from Microsoft is version 10. This version is much better at protecting the online user than previous versions.
Firefox (www.mozilla.com/). Firefox is a free, open source Web browser for Windows, Linux, and Mac OS X. It offers customization options and various features including pop-up blocking, tabbed browsing, privacy and security measures. The Firefox user interface is designed to be easily customizable by adding “extensions.” Firefox is one of the most popular browsers and has many extensions to expand its functionality.
Chrome (https://www.google.com/intl/en/chrome/browser/): Chrome is a browser produced by Google that is simple and fast. It was recently rated as the best overall browsers (Mediati, 2012). It allows for the addition of extensions to add third-party functionality. For the investigator, it also has a built-in “Developer” function that allows the user to easily access the source code of a webpage and view its various parts.
Useful browser-investigative extensions
A browser extension extends the usefulness of a browser. Many companies have developed these add-on software extensions for specific function for the user. A search for “extension” and your browser of choice will provide the investigator with a significant number of options. In Table 7.1, we provide a small list of tools that could be useful to the investigator.
Blocking cookies
The purpose of cookies is to identify website users and prepare customized Web pages when the user returns. A website using cookies may ask the user to complete certain information about themselves or simply record information about their computer and their incoming Internet address. This information is saved in a “cookie,” sent through your browser, and then stored on your computer. The next time you go to the same website, your browser will send the cookie previously downloaded to the Web server. This Web server can then use this previous information to present you with custom Web pages, such as “Hello Bob, thanks for returning to our web site”.
Cookies really personalize a user’s browsing experience. The type of cookies that accomplishes this are called, First-party cookies. These cookies do record your viewing on a particular website. However, they do not follow your browsing beyond that particular website. Some websites will not allow your browser to function properly unless you allow first-party cookies. The problem comes in with what are called “third-party cookies.” These cookies are not placed on your computer by the site you are actually visiting. As you explore a website and access different pages, the data on those pages may come from other website servers. These other website servers, which you never actually visited, place their own cookies on your machine. These third-party cookies report back to these other servers your browsing habits, even though you never actually visited them. Third-party cookies can be disabled. To make matters a bit more complicated, cookies can also be set to be either session specifically, which only operate during the browsing sessions, and persistent cookies, which remain after the browsing session ends (Gibson, 2005).
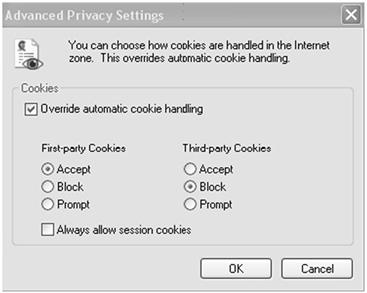
Selecting block all cookies in your browser setting prevents first-party cookies from being placed on your machine, which can adversely affect access to some sites. Browsers can be adjusted to selectively block third-party cookies. Reportedly, Firefox 22 will automatically block third-party cookies (Keizer, 2013). Other browsers require you to make the change yourself. With Internet Explorer, it is not as simple as just going to Tools > Internet Options > Privacy Settings and moving the bar up to most restrictively. Doing so will restrict first-party cookies too. Instead select the Advanced tab. This allows the user to permit first-party cookies but block third-party cookies. Do not select the option enabling session cookies as that will also permit third-party cookies to be installed. Google Chrome is much easier. Select settings and then Privacy. Under Cookies, select “Block third-party cookies and site data”. Obviously, these various options can change as browsers are updated. The important thing to understand is to look for options that block third-party cookies (Figure 7.4).
Windows operating systems and application changes
Disable file sharing
File sharing for computers running Microsoft Operating systems allows other computers on a network to access your computer. According to Microsoft’s support website, Windows XP computers by default has file sharing enabled. When the file sharing is enabled, anyone with access in the network and proper permissions can access the shared files. If you do enable it to share between two or more computers, be sure to enable tight permission to afford only access by authorized persons. Also make sure you have a strong password. A strong password is at least 8+ characters of random letters, numbers, and symbols. Never open up more folders than you need and never share the c: (root) drive.
Windows updates
Make sure you have patched all critical Windows exploits. You can check at the following Microsoft website for those updates:
Enable automatic checking and manually check often for critical updates.
If you use Microsoft Office, Word, Outlook, or Express here’s the link for critical patches:
Cloning or image the investigator’s computer
Cloning a hard drive refers to making a copy of the working system as not only a backup, but as a clean copy that can be used to overwrite the existing system with a clean unaltered or infected system. The technique of cloning the drive is copying the data on the investigators drive to the exact same position on another hard drive or the clone. This is a common technique applied by Information Technology personnel and System Administrators during the general maintenance of computers under their control. This gives the investigator the ability to put a new copy of the system back on the investigative machine if it has been compromised by malware or hackers. Similarly, imaging refers to a process of copying the data on the investigators hard drive but taking that same data the clone makes and placing it into a large file. This file can be stored on another drive with other image copies of the investigator’s computer hard drives.
So how does the investigator do this? There are many programs out there to assist the investigator to accomplish this task. In the Investigative Tips Sidebar, Commonly Used Cloning Utilities, we provide several free and commercially available tools to accomplish this task. Each of these tools helps the investigator through a process of copying the investigative computer hard drive either to another hard drive or to an image file.
Keeping your investigative computer secure
Encryption
Encryption of your working files is a recommended practice for the online investigator. Encryption prevents the unauthorized access of sensitive information. However, investigators new to using encryption should practice with the encryption tool they decide to use before ever using it on real case files. Once encrypted, if you lose the key, you have lost the files. An additional issue is that backups need to be made on a regular basis if encryption is employed. A significant limitation of encryption is not its implementation but the electromechanical devices it is stored on. If an encrypted hard drive fails, the investigator may never get the data back.
Keeping your system clean
Your operating system needs regular maintenance to keep working at its peak efficiency. The Windows operating system and your browser store many bits of information that over time can affect the computer’s functioning. Periodically, purge your browser’s Internet cache, history, and cookies. A simple Google search will locate step-by-step cleaning procedures for any particular browser in use.
Windows has also two tools that are very useful for helping to optimize your Windows system. Both tools are located in Start Menu/Accessories/System Tools. There you will find Disk Cleanup and Disk Defragmenter. Both are tools that should be used on a regular basis to maintain the performance of your system.
There are many third-party products to assist you in keeping your system running smoothly. These tools will locate cache, cookies, history, temporary files, etc. and delete it from your computer. Some tools also include “wiping” functions that not only delete the information but also make it impossible to recover.
Testing your security
Now that your computer is secured, it’s time to test its defenses. Shields Up!! and Leak Test by Gibson Research Corporation (https://www.grc.com), test your investigative system to determine its security level and how much information it may be leaking. To check how stealthy your machine is on the Internet, go to www.grc.com. Use the Shields Up test to check your investigative system for open ports and other potential security risks. If interested in further information about securing computer systems, the author Steve Gibson’s site (www.grc.com/SecurityNow.htm) is a good one to explore and learn about additional things to do in order to secure your computer. Other web locations for testing your system are:
www.dslreports.com/tools and omicron.hackerwhacker.com/freetools.php. Both sites have various tools to test the security of your investigative computer system.
Conclusion
This chapter has provided the Internet investigator with a guide to securing their investigative computer. The tools references provided here are a guide only and not the absolute software required. The investigator should look to the comments made here as a continuing process. Follow the process and you will help to ensure that you are protected. Don’t follow the process and you can be assured that you will be vulnerable. The current crop of malware and virii is indiscriminate in their application. The Internet investigator will always be at risk when going online. However, using the guidance provided in this chapter can assure the investigator will be better prepared to defend against the growing threats presented by investigating crimes on the Internet.
Further reading
1. Ad-Aware Free Antivirus and Antispyware, Protection from Virus, Spyware & Malware, Top Internet Security for Windows. (n.d.). Lavasoft. Retrieved from <http://www.lavasoftusa.com/>.
2. Antispyware, Antivirus, Endpoint Protection & Mobile Security. (n.d.). Webroot. Retrieved from <http://www.webroot.com>.
3. Antivirus Software, Firewall, Spyware Removal, Virus Scan: Computer Security. (n.d.). ZoneAlarm. Retrieved from <http://www.zonelabs.com>.
4. Antivirus Software Internet Security & Cloud Security. (n.d.). Trend micro USA. Retrieved from <http://trendmicro.com>.
5. Avast! Download Free Antivirus Software or Internet Security. (n.d.). Avast!. Retrieved from <http://www.avast.com>.
6. AVG, Antivirus and Internet Security, Virus Protection. (n.d.). AVG. Retrieved from <http://www.grisoft.com>.
7. Backup Software for Data Backup and Disaster Recovery in Windows and Linux. (n.d.). Acronis. Retrieved from <http://www.acronis.com>.
8. Basic Digital Officer Safety. (n.d.). Vere software. Retrieved from <www.veresoftware.com>.
9. Bitdefender Antivirus Software. (n.d.). Bitdefender antivirus software. Retrieved from <http://www.bitdefender.com>.
10. Carlyle T. (n.d.). BrainyQuote.com. Retrieved from <http://www.brainyquote.com/quotes/quotes/t/thomascarl399446.html>.
11. CCleaner—PC Optimization and Cleaning—Free Download. (n.d.). Piriform. Retrieved from <http://www.piriform.com/ccleaner>.
12. Chrome Browser. (n.d.). Google Chrome browser. Retrieved from <https://www.google.com/intl/en/chrome/browser/>.
13. Cogswell, B., & Russinovich, M. (n.d.). RootkitRevealer. Microsoft Corporation. Retrieved from <www.microsoft.com/technet/sysinternals/Security/RootkitRevealer.mspx>.
14. Cooney, M. (2012, September 21). 10 Common mobile security problems to attack. PC World. Retrieved from <http://www.pcworld.com/article/2010278/10-common-mobile-security-problems-to-attack.html>.
15. Default Router Passwords—The Internet’s Most Comprehensive Router Password Database. (n.d.). Retrieved from <http://routerpasswords.com/>.
16. DOM Inspector 2.0.13. (n.d.). DOM Inspector 2.0.13. Retrieved from <https://addons.mozilla.org/en-US/firefox/addon/dom-inspector-6622>.
17. Download Free Firewall Software From Comodo. (n.d.). Comodo. Retrieved from <http://www.comodo.com>.
18. DriveImage XML Backup Software—Data Recovery Product. (n.d.). Runtime software. Retrieved from <http://www.runtime.org/driveimage-xml.htm>.
19. Encryption Software, Symantec. (n.d.). Symantec. Retrieved from <http://www.pgp.com>.
20. Endpoint, Cloud, Mobile & Virtual Security Solutions. (n.d.). Symantec. Retrieved from <http://www.symantec.com>.
21. Federal Information Security Management Act (FISMA). (2013). Retrieved from <www.dhs.gov/federal-information-security-management-act-fisma>.
22. Fiddler Web Debugger—A Free Web Debugging Tool. (n.d.). Fiddler web debugger. Retrieved from <http://www.fiddler2.com>.
23. Fix-it™ Utilities. (n.d.). Avanquest. Retrieved from <https://www.vcom.com>.
24. Free Hard Disk Copy/Clone Software for PC & Server Hard Drive. (n.d.). EaseUS. Retrieved from <http://www.easeus.com/disk-copy>.
25. Gibson, S. (2005). Misfortune cookies. Gibson Research Corporation. Retrieved from <http://www.grc.com/cookies.htm>.
26. Gibson Research Corporation. (n.d.). Retrieved from <https://www.grc.com>.
27. Hackwhacker Firewall Test, Security News, Free Security Scan. (n.d.). Hackwhacker.com. Retrieved from <http://omicron.hackerwhacker.com/freetools.php>.
28. Hyppönen, M. (2012, September 4). Flame is lame? Not so much. SC Magazine. Retrieved from <http://www.scmagazine.com/flame-is-lame-not-so-much/article/254684>.
29. Information assurance tools report (7th ed.). (2011). Herndon, Virginia: Information Assurance Technology Analysis Center. Retrieved from <http://iac.dtic.mil/csiac/download/firewalls.pdf>.
30. Internet Explorer—Microsoft Windows. (n.d.). Microsoft Windows. Retrieved from <http://windows.microsoft.com/en-us/internet-explorer/download-ie>.
31. IP Blacklist Check and Monitor. (n.d.). Adminkit.net. Retrieved from <http://www.adminkit.net/>.
32. IT Security News and Security Product Reviews. (n.d.). SC magazine. Retrieved from <http://www.scmagazine.com>.
33. Janssen, C. (2013). What is a virus signature?—Definition from techopedia. Techopedia Information Technology and Business Meet. Retrieved from <http://www.techopedia.com/definition/4158/virus-signature>.
34. Jetico. (n.d.). Jetico software. Retrieved from <http://www.jetico.com>.
35. Kaspersky Lab US, Antivirus & Internet Security Protection Software. (n.d.). Kaspersky lab. Retrieved from <http://usa.kaspersky.com>.
36. Keizer, G. (2013). Firefox to auto-block third-party ad cookies by summer. Computerworld. Retrieved from <http://www.computerworld.com/s/article/9237105/Firefox_to_auto_block_third_party_ad_cookies_by_summer>.
37. Malware Bytes. (n.d). Retrieved from <http://www.malwarebytes.org>.
38. McAfee, Antivirus, Encryption, Firewall, Email Security, Web Security, Risk & Compliance. (n.d.). McAfee. Retrieved from <http://www.mcafee.com>.
39. McAfee SiteAdvisor Software—Website Safety Ratings and Secure Search. (n.d.). McAfee. Retrieved from <http://www.siteadvisor.com>.
40. Mediati, N. (2012, September 19). Web browser showdown: Which windows app is really the best? PC World. Retrieved from <http://www.pcworld.com/article/2009768/web-browser-showdown-which-windows-app-is-really-the-best.html>.
41. Microsoft Security Essentials—Microsoft Windows. (n.d.). Microsoft Windows. Retrieved from <http://windows.microsoft.com/en-us/windows/security-essentials-download>.
42. Microsoft Update. (n.d.). Microsoft. Retrieved from <www.update.microsoft.com/windowsupdate>.
43. Miray Software—HDClone—Hard Disk Copy, Hard Disk Backup, Hard Disk Rescue!. (n.d.). Miray software. Retrieved from <http://www.miray.de/products/sat.hdclone.html#free>.
44. Mozilla Firefox Web Browser—Free Download—mozilla.org. (n.d.). Mozilla Firefox web browser. Retrieved from <http://www.mozilla.com>.
45. OD. (n.d.). Critical start. Retrieved from <http://www.criticalstart.com>.
46. Office of Budget and Management, (OBM) Office of the President, Clarifying cybersecurity responsibilities and activities, M-10-28 (July 6, 2010). Retrieved from <http://www.whitehouse.gov/sites/default/files/omb/assets/memoranda_2010/m10-28.pdf>.
47. Outpost Security Suite Free—The first Free Complete Internet Security Suite. (n.d.). Agnitum. Retrieved from <http://free.agnitum.com>.
48. PCWorld—News, tips and reviews from the experts on PCs, Windows, and more. (n.d.). PC World. Retrieved from <http://www.pcworld.com>.
49. Product Reviews and Prices, Software Downloads, and Tech News. (n.d.) CNET. Retrieved from <http://www.cnet.com>.
50. Proxy2k. (n.d.). Company2k. Retrieved from <https://company2k.net>.
51. Redo Backup Bare Metal Restore Solution GUI Backup Open Source GPL Recovery. (n.d.). Redo backup and recovery. Retrieved from <http://redobackup.org>.
52. Rouse, M. (2011). What is Federal Information Security Management Act (FISMA)? Definition from WhatIs.com. Information Security Information, News and Tips—SearchSecurity.com. Retrieved from <http://searchsecurity.techtarget.com/definition/Federal-Information-Security-Management-Act>.
53. Safe Browsing Tool, WOT (Web of Trust). (n.d.). WOT (Web of Trust). Retrieved from <http://www.mywot.com>.
54. Security News. (2013). “Heuristic Virus Definition” PC Tools. Retrieved from <http://www.pctools.com/security-news/heuristic-virus-definition>.
55. Security Now. (n.d.). Gibson Research Corporation. Retrieved from <http://www.grc.com/SecurityNow.htm>.
56. Security Solutions for Mobility, Cloud Apps and Social Media. (n.d.). Zscaler. Retrieved from <http://zscaler.com>.
57. Speed Tests and Problem Diagnosis Tools, DSLReports.com, ISP Information. (n.d.). DSLReports home: Broadband ISP reviews news tools and forums. Retrieved from <http://www.dslreports.com/tools>.
58. Spybot—Search & Destroy from Safer-Networking Ltd. (n.d.). Safer-Networking Ltd. Retrieved from <http://www.safer-networking.org>.
59. SpywareBlaster®, Prevent Spyware and Malware. Free download. (n.d.). BrightFort. Retrieved from <http://www.brightfort.com/spywareblaster.html>.
60. Tactical Panda IT Services—Spoofstick. (n.d.). Tactical panda IT services. Retrieved from <http://www.tacticalpanda.co.uk/spoofstick.html>.
61. The App Maker, Tejji. (n.d.). Tejji. Retrieved from <http://tejji.com>.
62. The Encrypting File System. (n.d.). Resources and tools for IT professionals TechNet. Retrieved from <http://technet.microsoft.com/en-us/library/cc700811.aspx>.
63. TrueCrypt—Free Open-Source On-The-Fly Disk Encryption Software for Windows 7/Vista/XP, Mac OS X and Linux. (n.d.). TrueCrypt. Retrieved from <http://www.truecrypt.org>.
64. Wilson, D. (n.d.). How to remove your personal information from Google and the Internet. Retrieved from <http://www.wilsonsecurityagency.com/Remove%20Your%20Personal%20Information.pdf>.
65. Windows® Defender from Official Microsoft Download Center. (n.d.). Microsoft Corporation. Retrieved March 10, 2013, from <http://www.microsoft.com/en-us/download/details.aspx?id=17>.
66. XXCLONE, A New Way of Cloning the Windows System Disk. (n.d.). XXCLONE. Retrieved from <http://www.xxclone.com/index.htm>.
67. How to disable simple file sharing and how to set permissions on a shared folder in Windows XP. Retrieved from <http://support.microsoft.com/kb/307874>.
68. Help protect your files using BitLocker Drive Encryption. (n.d.). Microsoft Windows. Retrieved from <http://windows.microsoft.com/en-us/windows-vista/help-protect-your-files-using-bitlocker-drive-encryption>.
69. What’s the difference Between BitLocker Drive Encryption and Encrypting File System? (n.d.). Microsoft Windows. Retrieved from <http://windows.microsoft.com/en-us/windows-vista/whats-the-difference-between-bitlocker-drive-encryption-and-encrypting-file-system>.
1A Port is a “logical connection place” specifically referring to the Internet protocol TCP/IP.