Investigating Methods of Communication
This chapter is intended to assist the investigator new to Internet investigation understand several of the different protocols that can be used to communicate over the Internet. The different methods include various chat programs, Instant Messaging, and bulletin boards. Each of these communication protocols has a different method of investigation and requires separate applications to access. This chapter will describe the various protocols and common applications that use these protocols.
Keywords
IRC; IM; Yahoo IM; Skype; client server networks; peer-to-peer (P2P) networks; Usenet; free agent; Fserve; bulletin board (BBS); Craigslist; 4chan; 2ch; eBay
USENET is like a herd of performing elephants with diarrhea – massive, difficult to redirect, awe-inspiring, entertaining, and a source of mind-boggling amounts of excrement when you least expect it.
(Gene Spafford, Computer Science at Purdue University, Computer Science Professor)
Communicating on the Internet
There are various Internet protocols available that can be used to communicate online with other users. Most of us are familiar with the Instant Messaging as a communication tool. Some of the other traditional tools, such as Internet relay chat (IRC) and Usenet, popular ages ago, are not as known or used as they once were. This does not mean these protocols are not used by millions of people. A little known fact to most on the Internet, USENET has been increasing in use since the mid-1990s. According to TechSono Engineering, Inc., a USENET software tool manufacturer, 8 terabytes of data daily were moving through the USENET system in 2011. The communication methods are not limited to just voice and chat but also include data transfers. The methods we are going to discuss are based on the protocol and design of the specific communication system. We are going to break these methods into three separate categories based on the type of communication protocol utilized. These are broad and not individually descriptive of each technology, but help us to categorize the technology into understandable forms. These categories are: client server, peer-to-peer (P2P), and bulletin boards. The application of these tools and protocols are not dependant on a specific operating system.
Client server: protocols and tools
The client server model is one where connections and data are controlled through a server or series of servers that a user connects with through a software client. The communications are guided by the server processing connections to connect one or more users together (Figure 15.1). The common types of communication protocols and programs in this category include:
Instant Messaging
Instant Messaging, a real-time technology, has existed as an Internet protocol for some time. It’s a way of communicating which requires immediate feedback or response. It is an alternative to email and newsgroups. Instant Messaging programs work independent of your computer’s browser and allow the users to communicate with each other without interrupting other applications. Instant messaging allows two people to communicate over the Internet just as if they were having a face-to-face conversation. The programs allow the creation of contact lists, sometimes referred to as a “buddy list.” Contacts are generated by contacting another user on the network and asking to be connected to that user. The user contacted has to accept the user as a contact to make a connection. This adds them as a contact in the Instant Message application for later use. Most Instant Messaging software allows you to track when another “friend” logs on or logs off of the Internet. There also is usually an option to not provide these notifications to the user(s). Video Instant Messaging allows for real-time video communication between users.
Instant Messaging configuration
Instant Messaging is generally configured in a peer-to-network configuration (this is also called client/server model). Peer-to-network configurations require a central server. This central server acts as the connector between users. When a user adds a connection, the central server alerts the user when that connection comes onto the network. This allows the two users to make a connection. The connection is through the central server which forwards the communications between the users. Examples include: AOL Instant Messenger, Yahoo!, ICQ, and Skype.
Instant Messaging can allow for P2P connections but only when transferring files. The P2P connections made through Instant Messaging allow users to connect directly to one another user without relying on a central server. These connections could expose each user’s Internet Protocol (IP) address of the users. Each of the Instant Messaging services have developed their protocols independently. This causes an inability of the messaging services to interoperate. Open-source protocols were eventually developed under the Extensible Messaging and Presence Protocol (XMPP). There are several software programs, such as Pidgin or Trillian, that have brought several of the Instant Messaging protocols together in one application that allow the users to communicate between services.
Instant Messaging works by the user logging into the messaging server, i.e., Yahoo, AOL, or through the user’s software on the local machine. The messaging server acknowledges the user's buddy list and advises which of the contacts are currently logged into the server. The user selects an online contact to chat with and tells the system to connect to the contact. The users then chat with each other by typing their communications back and forth between themselves (Figure 15.2).
Instant messages historically have been sent in plain text with no inherent encryption unless enabled by the user. This can make sessions vulnerable to packet sniffing, especially if the connection is not encrypted. Instant Messaging allows the transfers of files between users. This file transfer method, however, does not allow files to be scanned by antivirus programs as they arrive which creates a real risk for an attack. Instant Messaging differs from IRC as the latter is communication on a one-to-one basis where IRC is one-to-many communication. There are many popular Instant Messaging software applications that have little to no interoperability. Examples: of this include, AOL Instant Messenger, Yahoo! Messenger, ICQ, and Skype.
• AOL Instant Messenger® (AIM), http://www.aim.com/
• ICQ®, http://www.icq.com/
• Yahoo! Messenger®, http://messenger.yahoo.com.
There are other protocol independent instant messenger programs that allow communication between multiple Instant Messaging services. These can be useful to the investigator that is tracking targets and communicating with persons across multiple Instant Messaging platforms. Several of these cross platform tools are:
• Digsby, http://www.digsby.com/
• Miranda, http://www.miranda-im.org/
• Pidgin, http://www.pidgin.im/
• Trillian, https://www.trillian.im/.
Web-based chat
Web-based chat program allows access to IM protocols through a web interface. Social media sites have integrated chat into their services and so have web-based email programs like Gmail. There are several web-based services the investigator can use to further their investigations. These make using Instant Messaging possible without having to install an application. They include:
• Communication Tube, http://www.communicationtube.net/
• EBuddy, http://www.ebuddy.com/
• IMO, https://imo.im/.
Internet Relay Chat
IRC relies on the existence of “channels,” communication spaces dedicated to dialogue among a specific group of participants. This method involves a multiuser system of servers that are connected to each other to create networks. IRC is a well-documented protocol with several Requests for Comments guiding the systems. IRC was created in the late 1980s at the University of Finland (IRC, n.d.).
It is a real-time chat between two individuals or many individuals discussing a topic in a channel or room. Users can exchange files with each other and set up file servers to provide files to many users. The advantage to this communication method is that IRC usernames and “nicknames” are not verified by any central authority. An individual can truly be who they want to be on IRC. Why does the investigator care about IRC? Over 500,000 people a day connect to IRC channels (IRC, n.d.). With that many people using one protocol there is bound to be a victim somewhere and there surely will be a criminal to catch.
IRC participants communicate in user-created rooms. Any user can open a room and control the room. Individuals can send or trade photos or other files with other users. IRC participants can also set up a server to automatically trade/or distribute photos or files commonly referred to as an Fserve. In the chatrooms, multiple users can be in the same chat room at the same time. Each users is identified by a screen or “nick” name. Public chatrooms cover a broad range of topics, such as sports, cooking, and children. Each chatroom content is accessible by everyone in the chatroom while the conversation is taking place. Private chatrooms between users can be created and require an invitation by the channel owner to gain access (Figure 15.3).
Connecting to an IRC
The IRC network is a collection of servers linked together using the IRC protocol. Connecting to IRC requires using an IRC application. Users are then connected to an IRC server. The connecting IRC server is determined by the IRC network the user selects. The server knows who is on the network and what channel (room) users are in as they chat. The IRC server feeds the channels and the chatted text to the users connected to the server. The servers pass the user’s chat in the various channels between the servers connected throughout IRC. User's can then chat with anyone in a channel anywhere in the IRC network. Internet latency and speed when using IRC depends on the location of the server in conjunction with the user. It is best to connect to a server geographically close to the user for a faster response. Some channels are open to anyone to access and chat with other channel members. Others are private and only accessible by invitation of the channel owner. Channels have topics set which are generally descriptive by the channel name. Investigators looking for a particular type of room can usually find them by a particular channel title.
Chat language
IRC early on in its existence began to build its own language. To make conversations faster users shortened up the words used by making acronyms out of terms and short sentences. “brb” or Be Right Back is an example of the shortening of the language used in the chatrooms. Over time a significant number of acronyms came into use and lists of the acronyms used were needed to identify what was being said. Table 15.1 contains a few of the more common acronyms developed to facilitate communicating over IRC. You’ll recognize that many of them have come into mainstream use, especially in texting on cell phones.
Table 15.1
| brb=be right back | :-^) with flu |
| bbl=be back later | :-)^ choking |
| btw=by the way | :'-( crying |
| np=no problem | :-@ shouting |
| lol=laughing out loud | :-& can’t talk |
| re=hi again, as in ‘re hi’ | -:-) punk |
| rotfl=rolling on the floor laughing | |:-) fall sleep |
| bbiaf=be back in a flash | :-O waking up |
| ttfn=ta ta for now | 0:-) angel |
| imho=in my humble opinion | :-D laughing |
| j/k=just kidding | :-X lips seal |
| wb=welcome back | :-Q smoker |
| Emoticons | :-/ skeptic |
| :) Smile | C=:-) chef |
| :-) Basic Smile | @= nuclear bomb |
| ;-) eye wink | *:O) clown |
| :-( sad | [:-) using walkman |
| :-I Indifference | (:I egghead |
| :-> Sarcastic | @:-) with turban |
| >:-> Diabolic | X-( just died |
| (-: left handed | :] friendly smile |
| %-) Drunk | :D laugh |
| 8-) Uses glasses | :( again sad |
| B:-) Sunglasses on head | :O shouting |
| B-) dark sunglasses | [] hugs |
| 8:-) little girl | :* kisses |
| :-{) Mustache | :*,;* more kisses |
| :-{}painted mouth | :*,:*,:*,:*, more and more kisses |
| {:-)with hair |
Logging onto an IRC server
Fully accessing the IRC requires the investigator use a software application referred to as a client. IRC clients depend on the operating systems used. There are many applications to gain access to IRC. Both Windows and Apple Macintosh systems have software available for accessing IRC. Common on Windows systems is mIRC (http://www.mirc.com/) and on Macintosh is Ircle (http://www.ircle.com/). Both applications give the investigator access to the many features of the IRC protocol and the various servers containing the channels that might be of investigative interest. Two popular IRC server networks are DALnet (www.dal.net) and Undernet (www.undernet.org). The location the investigator actually goes to will ultimately depend on the facts of the case and the channel in use related to the investigation. mIRC has a logging feature that allows the investigator to select automatic logging of the channels and the chat.
Joining a channel (chatroom)
Effective access to IRC requires a desktop application. One of the most popular as mentioned is mIRC. This application allows access to all of the IRC servers. mIRC allows easy access to the IRC system through its user panel.
Channel operators, referred to as the “Bosses” or “ops,” maintain absolute control of the channel. The “Ops” decide who gets to enter the channel, who gets kicked out, and who may talk. The Channel operators will have the “@” in front of their nickname. There are two ways to become a channel operator: (1) create a channel and (2) be made an operator by an existing channel operator. Users in the channel are designated by the “#” sign preceding their channel names. Channel names are not case sensitive.
Hiding in IRC
IRC can be accessed using a proxy server or through the Tor network. Using a proxy allows users to connect to chat servers sending the traffic through the proxy server. The proxy server forwards the chat messages from the user through the proxy server to the IRC server and channel. What is exposed is the IP address of the proxy server on the IRC server. This helps to hide the investigator’s real IP address from others on the IRC channels investigated. Obviously the reverse is possible and the investigator should be aware that IP addresses found on IRC should not be immediately thought of as the target’s actual IP address without significant investigation to determine that the IP is the target’s actual IP address. You can find an updated list of proxy servers intended just for IRC at http://irc-proxies.blogspot.com/. The investigator can also use the list to determine if an IP address identified on IRC is potentially a proxy. You can connect to IRC through a proxy while using mIRC. You can set up a proxy in mIRC’s Proxy settings section of the options dialog box (ALT+O>Connect>Proxy). The investigator needs to be aware that some IRC servers may ban the use of proxies and Tor if found.
Web browser access to IRC
Access to some IRC servers can be done through web interfaces. There are several websites that provide the investigator with access to some IRC servers. The investigator can use these as a quick means of accessing these IRC servers and channels of interest. Some of these websites include:
• freenode Web IRC, https://webchat.freenode.net/
• IRC.NETSPLIT.DE, http://irc.netsplit.de/about/
• irc2go, http://irc2go.com/
• Mibbit Chat Network, http://www.mibbit.com/
• The DALnet IRC Network, http://www.dal.net/
• Undernet IRC Network, http://www.undernet.org/webchat.php.
Tracking criminals in IRC
IP addresses can be identified for users while in IRC. The investigator can use the whois command to gain information about a possible target. Depending on the IRC server, the IP address can appear in the user’s chat messages after their nickname. However, some IRC networks hide the user’s IP address or hostname automatically on connection. For those that don’t the IP address of users is exposed for everyone on the channel to see or query. This is of course if the user is not attempting to hide his address from others on the IRC channel.
When using mIRC as your IRC investigative tool, you can right click on the username and select “who is” or “info.” This will provide the investigator with the IP address of the user, the server in use and channels where they are channel operators. An investigator who can act as a channel operator can monitor habits and methodologies of users which can be extremely useful in investigations. This of course means that the investigator spends enough time on the channel or channels in questions to become a well-respected member of the channel. The investigator has also to spent the time developing an undercover persona and preplanning the operational aspects of the investigation as we have discussed in previous chapters (Figure 15.4).
IRC resources
The following are some general resources that can assist the investigator understand IRC further:
• An IRC Tutorial, http://www.irchelp.org/irchelp/irctutorial.html
• IRC Beginner, http://www.ircbeginner.com
• #IRChelp, http://www.irchelp.org/
• mIRC, http://www.mirc.com/
• The IRC Prelude http://www.irchelp.org/irchelp/new2irc.html.
Identifying targets through communication protocols
Identifying targets on the Internet using the various communication protocols is somewhat of an investigative challenge. The investigator has to have an understanding of the communication protocol used and how the investigator’s local machine communicates through that protocol to the target. However, there are opportunities for identification of a target which are discussed below.
Netstat
Netstat is a common TCP/IP networking utility command line available in most versions of Windows, Linux, Unix, and other operating systems. Netstat provides information and statistics about protocols in use and current TCP/IP network connections. It can be used to trap the target’s IP address from incoming applications like Instant Messaging when sending a file between users. Something to remember when doing this technique is that it may not work due to networking complications. Additionally, the file transferred usually needs to be large enough to allow for Netstat to capture the IP address of the system transferring the file. Also with Client/Server applications, you may capture the Server’s IP used with the application and not the client computer actually sending the file.
On Microsoft Windows (Vista, Windows 7 and 8), the investigator using Netstat can reveal active transmission control protocol (TCP) connections sent and received on the local machine. Close all tabs in your browser and all active connections except the chat application the investigator is using. Additionally delete all cookies from browser to prevent your browser from making previous connections. Doing these actions will limit the number of items making a connection so it will be easier to identify the connections of interest. Open a command prompt in Windows by clicking on the start button and in the “Search Programs and File” box type “CMD” and hit enter. Be sure you are accessing the local machine as an Administrator to have the tool work properly. Executing the following Netstat command line, “netstat -o 3” displays active TCP connections. The 3 tells Netstat to run the command every 3 seconds. To display active TCP connections and the process IDs using numerical form, type the following command netstat -no. Table 15.2 provides numerous Netstat command options (Figure 15.5).
Table 15.2
| -a | Displays all connections and listening ports |
| -b | Displays the executable involved in creating each connection or listening port |
| -e | Displays Ethernet statistics. This may be combined with the -s option |
| -f | Displays Fully Qualified Domain Names for foreign addresses (in Windows Vista/7 only) |
| -n | Displays addresses and port numbers in numerical form |
| -o | Displays the owning process ID associated with each connection |
| -p | Shows connections for the protocol specified. May be TCP or UDP. If used with the -s option to display per-protocol statistics, protocol may be TCP, UDP, or IP |
| -r | Displays the routing table |
| -s | Displays per-protocol statistics. By default, statistics are shown for TCP, UDP, and IP; the -p option may be used to specify a subset of the default |
| -t | Displays the current connection offload state (Windows Vista/7) |
| -v | When used in conjunction with -b, will display sequence of components involved in creating the connection or listening port for all executables (Windows XP SP2, SP3) |
| interval | Redisplays selected statistics, pausing interval seconds between each display. Press Ctrl+C to stop redisplaying statistics. If omitted, netstat will print the current configuration information once |
| Example | netstat [-a] [-b] [-e] [-f] [-n] [-o] [-p proto] [-r] [-s] [-t] [-v] [interval] |
| Data Copy | Adding the following to the example » C:connections.txt dumps the data to a text file |
Netstat to identify applications connected to an IP address
Netstat can be used to get IPs of anything and anyone, as long as there is a direct connection between you and the target (i.e., direct messages, file transfers, or ICQ chats in ICQ, DCC (Direct Client Connection) chat, and file transfers in IRC). This is of course also depends on the target not using any anonymous IP hiding technique. To get an IP address of an application using Netstat first identify the IP addresses of the local machine before connecting with the target. This will be a baseline of the IP addresses the local machine applications are already using and communicating with. Open a command prompt and run the Netstat command “netstat -bano”. Copy and paste the data into a Notepad document and save the file. Open a new command prompt and run the command “netstat -bano 2.” The “2” tells Netstat to run the command every 2 seconds. This is to allow for the capture of short-lived IP address connections.
Run the application being used in the investigation and communicate with the target using the application. Client/Server applications will be using the applications server to relay messages and any attempts to capture the IP address of a target require that a direct connection be made with the target. This direct connection can possibly allow for the recording of the target’s IP address. Once the communication is over, stop Netsat. In the open command window, type Ctrl+C to stop the function. Again copy and paste the data into Notepad and save. Compare the Initial Notepad collection of the baseline of the local machine with the communication capture. The differences should be the IP addresses of the connections made with the application you are using. (Be sure to pay attention to the fact that other applications on the system will be making calls out too. Your antivirus and firewall programs regularly call out to update servers). With the unknown IP addresses, you can identify the ownership information and follow up as previously discussed.
Netstat the easy way
There are other tools available for collecting the TCP/IP connections of a local machine and the connections that it makes. Using these tools can make identifying a local machine’s connections easier for the investigator. They each collect the TCP/IP traffic of the local machine and show connections in real time. Additionally, they identify the programs that made them and the current traffic on the local machine. Finally, they also display the returned data in an easier to view graphical user interface. Several of the available tools for this purpose are:
• CurrPorts, http://www.nirsoft.net/utils/cports.html
• X-Netstat – Professional, http://www.freshsoftware.com/
• TCPView, http://technet.microsoft.com/en-us/sysinternals/bb897437.aspx.
P2P: protocols and tools
The P2P protocol is a system of communication that uses a sharing of data and files amongst the users of the network. A software client is used to connect a user to the network and then the members of the network can share data between themselves (Figure 15.6). The common types of communication protocols and programs in this category include:
• Bit Torrent Networks: BitTorrent, Inc., http://www.bittorrent.com/, and FrostWire, http://www.frostwire.com/
• eMule, http://www.emule-project.net/home
• Gnutella P2P Networks: Bearshare, http://www.bearshare.com/ and Limeware variations
• Shareaza, http://shareaza.sourceforge.net/: Supports the following P2P networks, Gnutella, Gnutella2, eDonkey, and BitTorrent).
Peer to Peer
P2P technology is one that uses multiple computers to share the data. Data is transferred between the participating users. Each of the users participates as a sharing partner in the system. The networked system depends on the participation of the user’s computers to process and forwards data among the network. This process is handled by the user’s downloaded application which is installed to gain access to the network. P2P is used by many people on the Internet for legitimate purposes. File transferring is one of the most popular uses on the Internet for P2P technology. P2P technology became famous in 2001 when the then music file sharing company Napster was sued for violating the copyrights of records companies by allowing users to access the copyrighted music from Napster’s servers (A&M Records Inc. v. Napster, Inc., 239F.3d 1004 (9th Cir. 2001)). What this did for the P2P sharing community was to move the use of P2P technology from one that had centralized servers to a network technology that was decentralized. No longer could you stop illegal activity simply by taking out a master server with an index of data and users.
This presents an issue now for the investigator of P2P networks as no one person or server is responsible for the content being shared over the network. The data is spread over the network and not stored in one location. There are different P2P network variations in use today. The most popular is the Gnutella and Ares networks. Other P2P networks have appeared over the last decade and have been investigated, including Limewire, FastTrack, BitTorrent, eDonkey, and GigaTribe. Skype which is probably one of the most popular messaging programs on the Internet also uses P2P techniques for sharing of its user’s communications. This technology changes all the time and applications come and go. Investigating P2P networks has become a mainstay of child pornography investigators. These investigations initially were a very tightly held investigative technique. Law enforcement early on identified that the P2P sharing concept was a protocol that could be successfully investigated. The use of the Peer Spectre software came to public knowledge after Flint Waters, then a Special Agent for the State of Wyoming, testified before Congress in 2007 about law enforcements investigations into the P2P networks. The use of P2P investigative software began in 2005 under the name Operation Fairplay. Waters (2007) stated in his testimony regarding law enforcement investigations into the trading of child pornography that the numbers of identified traders included:
There have been 1,519,791 unique IP addresses identified in the United States. If the breakdown were constant with the results in Wyoming that would indicate 504,947 individuals identified throughout the United States in the last 3 years. This is a rough estimate but again, it only pertains to one of many P2P systems and does not include other methods of trading child sexual abuse material.
Investigating P2P networks
Investigating P2P is a complicated process that involves understanding the protocol and its operation. The function of the file sharing is based on the sharing of data files. The sharing is accomplished through the networks by identifying the hash values of the files traded. The programs then know if the file is on a particular user’s computer (the file has the same hash value) and can then make that file available for sharing among the users connected to the network. The investigation of P2P is done through the collection and examination of these hashes and identifying which hash value matches known contraband. Some might think this collection of data is a violation of the 4th amendment. According to United States v. Willard, 2010 U.S. Dist. LEXIS 98216 (E.D. Va. September 20, 2010), the Peer Spectre program used to identify P2P downloaders of child pornography is not a wiretap nor does it violate the Fourth Amendment. The court noted: “Peer Spectre does not acquire communications contemporaneously with the transfer of data from one IP address to another. Instead, it reads publicly available advertisements from computers identified as offering images of child pornography for distribution and identifies their IP addresses.”
Accessing P2P sites
Accessing a P2P network requires downloading the software for that network. The investigator should follow all the steps we suggest in Chapter 7 regarding setting up an investigative computer. Access these sites is not without possible exposure of the investigation to others on the network. Using the P2P software requires that the investigation connects to the network. Depending on the option of the software, the premise behind P2P is that the users share the resources of their attached computers to the benefit of the network. If the investigator installs the P2P software on his work machine, he could potentially be exposing the agency/company network to the P2P network and users. Be aware what options are being selected during the installation process and document them.
Each of the programs provides the user access to the network and provides access to the available files. This is usually done by a search function or a listing of files that the users can select which files are of interest and download the files. The software identifies the files of interest and downloads the files from other computers sharing space with the network. The shared files are contained on the user’s local machine and available for others to access. Investigators can download the files and determine the file contents. Additionally, the investigative tools mentioned above work through the unique hash of the files stored throughout the network on the user’s shared space. The networks know the individual files based on this file hash. This enables the file to be uniquely identified on the network. Law enforcement tools like Peer Spectre track the unique file hash for contraband files previously identified as child pornography. A similar process is also used by investigators tracking pirated software, music, and movies being traded on P2P networks.
Bulletin boards
Bulletin boards are similar to the client server model in that a server controls the communication, but in this instance the data is stored on a server and accessed by users. The data is posted for everyone to see and download through a web browser or a software client. Users do not make direct connections with each other but post information on the server that is accessible by other users (Figure 15.7). The common types of communication protocols and programs in this category include:
Bulletin boards prior to the advent of the public Internet in 1994 were one of the most popular means of communication. They still hold a fascination with Internet users and many bulletin board style websites have developed and matured the concept over the intervening years. Still in existence and use is the USENET more commonly referred to as Newsgroups Protocol RFC 3877 describes the Network News Transfer Protocol (NNTP).
Usenet along with various sites used to post information are still popular places among Internet users. Google has Google Groups, Craigslist is extremely popular and even the various auction sites such as eBay are as popular as ever. Across the world, sites like 4Chan give the Internet users a certain amount of freedom to post and say what they want and provide a rich field of information for the investigator. All of these various sites can have a huge impact on an investigation. Any place where people hang out there are going to be crimes and evidence of the crimes. Posting sites have become places for prostitution and those that prey on prostitutes. In Boston, the infamous Craigslist killer looked to that site for his targets. Fraud has also been a common theme on bulletin board sites. Criminals have offered for sale items that don’t exist and collected money from their victims without delivering the goods. Investigators can’t overlook these sites as a source of information and investigation.
USENET newsgroups or bulletin boards
The traditional bulletin board protocol is USENET, which USENET uses the NNTP as its communication standard. These newsgroups are public discussion groups that generally require a client software to access the newsgroup feeds. There is a variety of newsgroup readers that the investigator can use to access newsgroups. The group discussion is in a hierarchical setup. The user subscribes to a group they are interested in and can then post and retrieve messages and attachments from the discussion board. The boards allow users to post a message and this permits every reader in that specific group to read the message and download any attachments. The topics range from computer certifications, newborn babies to very bazaar sexual related topics. Most ISPs have access to tens of thousands of different newsgroups. Each newsgroup can hold thousands of postings, which can contain just text, images, and other files. Anyone accessing a public newsgroup can view the postings and/or post their own responses. Private newsgroups can be created between users and require an invitation to gain access. These newsgroups can be moderated or unmoderated. Most are unmoderated with no control over what is said or posted.
Understanding USENET as an investigative tool
Prior to going onto newsgroups, investigators should thoroughly research their protocol. Choose a category and then select a topic. Be aware that “ALT,” standing for alternative is where the nonstandard material is, i.e., “bad stuff”, or in the investigator's case the most interesting. Users have no requirement or approval methods for forming a group. You will see variously named groups based on their content. Moderators name the group something attractive to get users into their rooms. This is much like an old-time carnival barker trying to attract patrons to a sideshow. These groups are unorganized, huge, and not suitable for minors (the Wild West of Usenet). For simple research on newsgroups, the investigator can go to Google Groups (http://groups.google.com/) to locate and review basic groups and information. However, Google Groups may not have all of the “Alt” content that may be required in your investigation. A serious investigation would require a USENET client to access all of the available sites possibly having the information the investigator is looking for as evidence. Generally, your ISP will have a news or NNTP server so you can access and investigate newsgroups.
Investigate all newsgroups and chatrooms carefully before subscribing. Are you investigating a particular user or just trolling for crime? There are advantages and disadvantages with the exploring of Usenet. The investigator can quickly connect to a global network of individuals with similar interests. It can be a springboard for ideas and facts. Users can say nearly anything (very little you can’t). Moderated groups could boot a user if the content was not appropriate. The disadvantages are that it is a global group. This can sometimes put the targets well out of the investigator’s jurisdiction. It can also be very difficult to ascertain the quality of the information posted in a site. Anything goes and that includes telling the truth or not. USENET postings and users can easily be abusive in their posts. On unmoderated sites there is little in the way of repercussions for misconduct. The groups are complex and loosely organized. They also have had an ongoing frustration level with bots and spammers filling up groups with nothing.
Newsgroup had a lot to do with the origination of the terms “Netiquette” or “network etiquette.” They are the unofficial rules defining the proper Internet behavior, e.g., sending spam and unwanted emails is bad netiquette. A “Flame” is an insult or derogatory message sent via email, USENET, or mailing lists to a person or group. Emoticons (smileys), “emotion icons,” are used to represent human facial expressions and convey an emotion on the Internet. They are created from typing certain characters on your keyboard, e.g., “:-)” is a smile. Acronyms and abbreviation or Internet slang was first defined on USENET and is now in use as common parlance amongst many in the real world.
With the advent of instant messaging, AOL and Yahoo groups, blogs and other social networking, USENET isn’t used by much of the Internet population. In fact many ISPs don’t support USENET any longer. This is partly due to the fact that there are no controls and denying access USENET gave them a sense of control over the bad content. Accessing newsgroups now is usually done through one of the pay services, which is probably the best option for the investigator. These services provide better access to the newsgroups and most of them have browser interfaces. Below are a few such pay services:
• Astraweb, http://www.giganews.com
• GigaNews, http://astraweb.com/
• Newshosting, http://www.newshosting.com/.
Google Groups
Google Groups might look like it has the USENET all in one place, but it doesn’t. It is a small subset of the data that passes through the USENET each day. It can be useful for some purposes and may contain the investigative data you are looking for but don’t bet on it. Searching Google Groups does not require a login. Making your own group does, however, require the user to login using a Gmail account. Simply go to www.google.com, click on “More” drop down, access the Google products page and select “Groups.” Google Groups have a search function that will provide a list of search term matches similar to their normal search engine (Figure 15.8).
Locating free Usenet servers
Free Usenet/News servers are still available. They are slow and may not be there tomorrow when you go back. Most of these servers are located outside of the United States and accessible from anywhere in the world. The following sites have been around for a significant amount of time and provide the investigator with a resource for finding USENET servers that can be accessed without a fee.
• List of Free NNTP News Servers, http://www.elfqrin.com/mine/nntpserv.html
• Newsbot, http://www.newzbot.com/
• Open Directory Free Server Listing, http://dmoz.org/Computers/Usenet/Public_News_Servers/
• Premium-news (German site), http://www.premium-news.com/public.htm
• Public USENET Servers, http://usenet__servers.tripod.com/.
Investigative tools for USENET
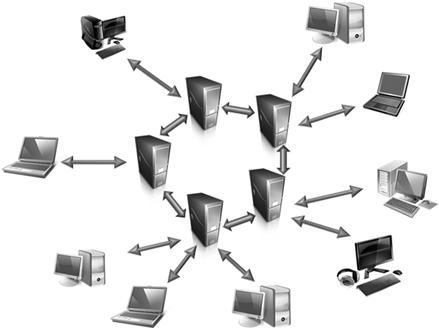
Investigative accessing the USENET can be done using any of the freely available tools on the Internet. However, they all have a variety of user interfaces and your personal preference will drive what you use. Forte Agent News Reader (http://www.forteinc.com/) (Figure 15.9), Newsbin Pro (http://www.newsbin.com/), and Thunderbird Mail (http://www.mozilla.org/en-US/thunderbird/) are a few of the available news readers that can be employed by the investigator. USENET is an anonymous service and posts containing information such as the user’s name and email can be false. Users can also access the newsgroup services through anonymization tools and Virtual Private Networks to hide their information and true IP addresses. In the USENET message is a header similar to an email header. The information has the email like received line and a line with the IP address of the poster at “NNTP-Posting Host.” There is the user's email address which is self-reported (Figure 15.10).
Online bulletin boards
Online bulletin boards have developed into popular online location for trading information, products, and personal contacts. Many of these sites started as small local or regional places to connect with other people. Some have grown into large corporations providing services to Internet users worldwide. These services can have very different methods of engaging their users. Auction sites like eBay (http://www.ebay.com/) have developed into regular places for users to purchase items and have facilitated some small business entry into worldwide market. Sites like Craigslist (http://www.craigslist.org/) have found a market to engage users at the community level. It facilitates the trading and connecting of users within their communities. Other sites like 4Chan (http://www.4chan.org/) have developed into communication mediums for the users in geographic regions that might not allow the freedom of speech that most western countries enjoy. Investigatively each of these sites has its own issues. The larger commercial sites have legal service sections that can be contacted to assist with identifying users who may have committed a crime on the service. They each will require legal service to obtain the user data (Figure 15.11).
As we mentioned in previous chapters, Exif data can still be an investigative tool used in bulletin board investigations. The investigator should attempt to identify if there is any Exif metadata available in postings that they are investigating. Sites like 4Chan that allow user’s postings of images do not delete the Exif data of user’s uploaded images.
Craigslist
Craigslist is a centralized network of online communities, which features free online classified advertisements of jobs, housing, personal ads, for sale/barter/ wanted items, services, pet categories and forums on various topics. To search Craigslist, you don’t need to make an account. Go to the Craigslist website, enter the geographic location (state and city) to search and enter the search term and select area to search (Figure 15.12). There are third party tools to assist with searching Craigslist like:
• CraigsList Notifier, http://craigslistnotifier.net/
• CraigsList Search, http://www.craigslistsearch.org/
• List-Alert, http://www.list-alert.com/
• TinkOmatic, http://www.tinkomatic.com/.
Conclusion
This chapter has introduced to the investigator several different communication methods over the Internet. This introduction is intended to provide a basic understanding of messaging, chatting, and newsgroups. The amount of information available through these communication means require that investigators be familiar with them and understand their potential to contain useful information. What is important for the investigator to understand is that each of these Internet communication methods can be investigated. However, it takes some time and planning on the investigator’s part to understand the technology and prepare for the investigation.
Further reading
1. A&M Records Inc. v. Napster, Inc., 239F.3d 1004 (9th Cir. 2001). Retrieved from <http://www.law.cornell.edu/copyright/cases/239_F3d_1004.htm/>.
2. Agent=Usenet+Email. (n.d.). Agent=Usenet+Email. Retrieved from <http://www.forteinc.com/>.
3. AIM Chat, Share, Connect. (n.d.). AIM. Retrieved from <www.aim.com/>.
4. Baloc’s Public News Servers. (n.d.). Baloc’s Public News Servers. Retrieved from <http://usenet__servers.tripod.com/>.
5. #Beginner—IRC Commands, the Basics. (n.d.). #Beginner Website, Undernet—2003. Retrieved from <http://www.ircbeginner.com/ircinfo/ircc-commands.html/>.
6. #Beginner Website, Undernet— 2003. (n.d.). #Beginner Website, Undernet—2003. Retrieved from <http://www.ircbeginner.com/>.
7. Beginner’s Guide to Newsgroup Newsreaders. (n.d.). Beginner’s Guide to Newsgroup Newsreaders. Retrieved from <http://www.newsreaders.info/>.
8. BitTorrent—Delivering the World’s Content. (n.d.). BitTorrent. Retrieved from <www.bittorrent.com/>.
9. Caraballo, D. & Lo, J. (n.d.). IRCHelp.org: Internet relay chat help. Retrieved from http://www.irchelp.org/irchelp/new2irc.html/>.
10. 4chan. (n.d.). 4chan. Retrieved from <http://www.4chan.org/>.
11. Communication Tube—icq/gtalk/irc/msn Web-based Messenger!. (n.d.). Communication Tube. Retrieved from <http://www.communicationtube.net/>.
12. Craigslist Alerts at List-Alert.com. (n.d.). Craigslist Alerts at List-Alert.com. Retrieved from <http://www.list-alert.com/>.
13. Craigslist classifieds. (n.d.). Craigslist. Retrieved from <www.craigslist.org/>.
14. CraigslistNotifier.net. (n.d.). CraigslistNotifier.net. Retrieved from <http://craigslistnotifier.net/>.
15. CurrPorts: Monitoring TCP/IP Network Connections on Windows. (n.d.). CurrPorts: NirSoft. Retrieved from <http://www.nirsoft.net/utils/cports.html/>.
16. Digsby=IM+Email+Social Networks. (n.d.). Digsby. Retrieved from <http://www.digsby.com/>.
17. Electronics, Cars, Fashion, Collectibles, Coupons and More Online Shopping: eBay. (n.d.). eBay. Retrieved from <http://www.ebay.com/>.
18. eMule-Project.net—Official eMule Homepage. (n.d.). eMule-Project.net. Retrieved from <www.emule-project.net/home/>.
19. Extensible Messaging and Presence Protocol (XMPP): Core. (n.d.). The XMPP Standards Foundation. Retrieved from <http://xmpp.org/rfcs/rfc3920.html/>.
20. Fagundes, P. (n.d.). Fighting Internet child pornography: The Brazilian experience. Police Chief Magazine. Retrieved from <www.policechiefmagazine.org/magazine/index.cfm?fuseaction=display_arch&article_id=1892&issue_id=92009/>.
21. File-sharing programs peer-to-peer networks provide ready access to child pornography: Report to the Chairman and Ranking Minority Member, Committee on Government Reform, House of Representatives. (2003). Washington, DC: U.S. General Accounting Office.
22. Free music downloads—Download free music today with BearShare. (n.d.). BearShare. Retrieved from <http://www.bearshare.com/>.
23. Freenode IRC. (n.d.). Freenode IRC. Retrieved from <https://webchat.freenode.net/>.
24. Fresh Software. (n.d.). Fresh Software. Retrieved from <http://www.freshsoftware.com/>.
25. Frosted limes: The unintended consequences of shutting down LimeWire. (n.d.). DFI News. Retrieved from <http://www.dfinews.com/articles/2010/11/frosted-limes-unintended-consequences-shutting-down-limewire#.UgiCA5LVDpU/>.
26. FrostWire.com—Share Big Files—BitTorrent App, Media Player, Wi-Fi Sharing. Official Website. (n.d.). FrostWire.com. Retrieved from <http://www.frostwire.com/>.
27. Google Groups. (n.d.). Google. Retrieved from <groups.google.com/>.
28. History of IRC (Internet relay chat). (n.d.). Daniel.haxx.se—Daniel Stenberg. Retrieved from <http://daniel.haxx.se/irchistory.html/>.
29. How to find someone’s IP address. (n.d.). How to find someone’s IP address. Retrieved from <http://whatstheirip.com/>.
30. ICQ. (n.d.). ICQ. Retrieved from <http://www.icq.com/>.
31. Index of /history_docs/. (n.d.). IRC.org—Home of IRC. Retrieved from <http://www.irc.org/history_docs/>.
32. Instant Messaging and Group Chat App imo Messenger. (n.d.). imo messenger. Retrieved from <https://imo.im/>.
33. Internet Relay Chat—IRC—irc.netsplit.de. (n.d.). IRC.NETSPLIT.DE. Retrieved from <http://irc.netsplit.de/>.
34. Internet Relay Chat Help. (n.d.). Internet Relay Chat Help. Retrieved from <www.irchelp.org/>.
35. IRC Proxy Servers. (n.d.). IRC Proxy Servers. Retrieved from <http://irc-proxies.blogspot.com/>.
36. IRC.org. (n.d.). IRC.org—Home of IRC. Retrieved from <http://www.irc.org/history_docs/jarkko.html/>.
37. irc2go—Chat Rooms—Online Chat—irc2go.com. (n.d.). irc2go. Retrieved from <http://irc2go.com/>.
38. IRCHelp.org: An IRC Tutorial. (n.d.). Internet relay chat help. Retrieved from <http://www.irchelp.org/irchelp/irctutorial.html/>.
39. ircle.com. (n.d.). ircle.com. Retrieved from <http://www.ircle.com/>.
40. Laurie, V. (n.d.). Netstat command and its application in Windows. Retrieved from <http://commandwindows.com/netstat.htm/>.
41. Mibbit Chat Network. (n.d.). Mibbit Chat Network. Retrieved from <http://www.mibbit.com/>.
42. Microsoft Windows XP—Netstat (n.d.). Microsoft Windows. Retrieved from <www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/netstat.mspx?mfr=true>, <http://commandwindows.com/netstat.htm/>.
43. Miranda IM—Home of the Miranda IM client. Smaller, Faster, Easier. (n.d.). Miranda IM. Retrieved from <http://www.miranda-im.org/>.
44. mIRC: Internet Relay Chat Client. (n.d.). mIRC. Retrieved from <http://www.mirc.com/>.
45. mIRC: Personal FAQ. (n.d.). mIRC: Internet relay chat client. Retrieved from <http://www.mirc.com/khaled/faq.html/>.
46. Mozilla Thunderbird. (n.d.). Mozilla. Retrieved from <http://www.mozilla.org/en-US/thunderbird/>.
47. Multiple Craigslist Search; Monitor eBay, Kijiji, Oodle Classifieds. (n.d.). Multiple Craigslist Search. Retrieved from <http://www.tinkomatic.com/>.
48. Netstat. (n.d.). Resources and tools for IT professionals: TechNet. Retrieved from <http://technet.microsoft.com/en-us/library/ff961504.aspx/>.
49. News.astraweb.com—Usenet News Server. (n.d.). News.astraweb.com. Retrieved from <http://astraweb.com/>.
50. Newsbin Pro Software, Usenet Downloading Tool | NNTP Usenet Binary Newsgroup Robot. (n.d.). Newsbin Pro Software. Retrieved from <http://www.newsbin.com/>.
51. Newzbot! Public USENET Resources for the Masses. (n.d.). Newzbot! Retrieved from <www.newzbot.com/>.
52. Open Directory—Computers Usenet Public News Servers. (n.d.). Open Directory—Computers Usenet Public News Servers. Retrieved from dmoz.org/Computers/Usenet/Public_News_Servers/>.
53. Pidgin, the Universal Chat Client. (n.d.). Pidgin. Retrieved from <http://www.pidgin.im/>.
54. PortableApps.com—Portable software for USB, Portable and Cloud Drives. (n.d.). PortableApps.com. Retrieved from <http://portableapps.com/>.
55. Premium News—Premium Usenet Binaries Newsserver, Weltweit, Unzensiert, Anonym. (n.d.). Premium News. Retrieved from <www.premium-news.com/public.htm/>.
56. RadiusIM. (n.d.). RadiusIM. Retrieved from <http://www.radiusim.com/>.
57. RFC 1459—Internet Relay Chat Protocol. (n.d.). RFC 1459—Internet Relay Chat Protocol. Retrieved from <tools.ietf.org/html/rfc1459/>.
58. RFC 2779—Instant Messaging Presence Protocol Requirements. (n.d.). RFC 2779—Instant Messaging Presence Protocol Requirements. Retrieved from <tools.ietf.org/html/rfc2779/>.
59. RFC 2810—Internet Relay Chat Architecture. (n.d.). RFC 2810—Internet Relay Chat Architecture. Retrieved from <tools.ietf.org/html/rfc2810/>.
60. RFC 2811—Internet Relay Chat Channel Management. (n.d.). RFC 2811—Internet Relay Chat Channel Management. Retrieved from <http://tools.ietf.org/html/rfc2811/>.
61. RFC 2812—Internet Relay Chat Client Protocol (n.d.). RFC 2812—Internet Relay Chat Client Protocol. Retrieved from <http://tools.ietf.org/html/rfc2812/>.
62. RFC 2813—Internet Relay Chat Server Protocol. (n.d.). RFC 2813—Internet Relay Chat Server Protocol. Retrieved from <http://tools.ietf.org/html/rfc2813/>.
63. Russinovich, M. (n.d.). TCPView for Windows. Resources and tools for IT professionals. TechNet. Retrieved from <http://technet.microsoft.com/en-us/sysinternals/bb897437.aspx/>.
64. Search All of Craigslist: Tips and Tools, Advanced Searches. (n.d.). craigslistSearch.org. Retrieved from <www.craigslistsearch.org/>.
65. Shareaza—Bringing P2P Together. (n.d.). Shareaza. Retrieved from <http://shareaza.sourceforge.net/>.
66. Souza, J. and Silva, E.(2009) EspiaMule and Wyoming Toolkit: Tools repression of sexual exploitation of children and adolescents in peer-to-peer. The International Conference on Forensic Computer Science. Retrieved from <www.icofcs.org/2009/ICoFCS2009-PP14.pdf/>.
67. Spafford, G. (n.d.). Gene Spafford’s Personal Pages Quotable Spaf. Retrieved from <spaf.cerias.purdue.edu/quotes.html/>.
68. State v. Mahan, 2011 WL 4600044 (Ohio Court of Appeals 2011) United State vs. Matthew Joseph Collins, Case Case 1:09-CR-00010-JEG-CFB, Southern District of Iowa, Court Order, November 24, 2009.
69. The DALnet IRC Network. (n.d.). Retrieved from <http://www.dal.net/>.
70. The Largest List of Text Message Shorthand (IM, SMS) and Internet Acronyms Found of the Web—Kept Current and Up-to-Date by NetLingo The Internet Dictionary: Online Dictionary of Computer and Internet Terms, Acronyms, Text Messaging, Smileys;-). (n.d.). NetLingo The Internet Dictionary. Retrieved from <http://www.netlingo.com/acronyms.php/>.
71. Trillian. (n.d.). Trillian. Retrieved from <https://www.trillian.im/>.
72. United State vs. Matthew Joseph Collins, Case Case 1:09-CR-00010-JEG-CFB, Southern District of Iowa, Court Order, November 24, 2009.
73. United States v. Willard, 2010 U.S. Dist. LEXIS 98216 (E.D. Va. September 20, 2010).
74. Usenet Free Newsgroups. (n.d.). Newshosting. Retrieved from <http://www.newshosting.com/>.
75. Usenet Newsgroups Service, News Servers, Usenet Access—Giganews. (n.d.). Giganews. Retrieved from <http://www.giganews.com/>.
76. Usenet Pumping 8 Terabytes per Day!. (n.d.). TechSono Engineering, Inc. Retrieved from <http://www.techsono.com/usenet/faq/usenet-traffic/>.
77. Waters, F. (2007) Child sex crimes on the Internet. Prepared for House Judiciary Committee. Retrieved from <judiciary.house.gov/hearings/pdf/Waters071017.pdf/>.
78. Web and Mobile Messenger for MSN, Yahoo, ICQ, AIM, Google Talk, Facebook. (n.d.). ebuddy.com. Retrieved from <http://www.ebuddy.com/>.
79. Welcome to the Undernet IRC Network. (n.d.). Undernet IRC network. Retrieved from <http://www.undernet.org/webchat.php/>.
80. www.ElfQrin.com—List of open NNTP servers. (n.d.). ElfQrin.com Hacking Lab. Retrieved from <http://www.elfqrin.com/mine/nntpserv.html/>.
81. Yahoo! Messenger—Chat, Instant message, SMS, Video Call, PC Calls. (n.d.). Yahoo! Messenger. Retrieved from <http://messenger.yahoo.com/>.