The prince who relies upon their words, without having otherwise provided for his security, is ruined— Niccoló Machiavelli (The Prince).
Today, networks provide a potential avenue of attack to any computer hooked to them and thus, security is a fundamental part of any Enterprise application. The Java platform was designed from the ground up with a strong emphasis on security. Its security APIs span a wide range of areas—interfaces for performing authentication and access control that protect applications against unauthorized access to protected resources, and cryptographic infrastructures that supply the underlying basis for developing secure applications.
A necessary preamble of this chapter will be an introduction to the Java Security API and how these interfaces are implemented in JBoss Security Extension (JBossSX). Then, in the core section of the chapter, we will deliver:
- A systematic guide for configuring JBoss security domains that can be used for providing standard authentication and authorization
- The cryptographic interfaces and tools available in the Java SE to secure the communication between users and the application server
Java EE security services provide a robust and easily configured security mechanism for authenticating users and authorizing access to application functions and associated data.
Authentication is the process by which the user of an application (any type of Java program, including EJB, servlets, and so forth) is verified.
Authorization is about managing access to protected system resources based on the rights of a user or class of users. Authorization, therefore, assumes that authentication has occurred; otherwise it would be impossible to grant any access control if you don't know who the user is.
In Java EE, the component containers are responsible for providing application security. A container, basically, provides two types of security— declarative and programmatic. Let's see them:
- Declarative security: This expresses an application component's security requirements by means of deployment descriptors, whose information is contained in an external file, and can be changed without the need to modify the source code.
For example, Enterprise JavaBeans components use an EJB deployment descriptor that must be named
ejb-jar.xmland placed in theMETA-INFfolder of the EJB JAR file.Web components use a web application deployment descriptor named
web.xmllocated in theWEB-INFdirectory.Web Services components use a
jaxrpc-mapping-info.xmldeployment descriptor defined in JSR 109. This deployment descriptor provides deployment time mapping functionality between Java and WSDL and needs to be placed in theMETA-INFfolder of your JAR file.Tip
Since Java EE 1.5 you can apply declarative security by means of annotations. Annotations are specified within a class file and, when the application is deployed, this information is translated internally by the Application Server.
By using annotations, you are exempted from writing boilerplate useless code, as this can be generated by external tools from the source code. This leads to a declarative programming style, where the programmer says what should be done and tools emit the code to do it. It also eliminates the need for maintaining side files that must be kept up-to-date with changes in source files. Instead, the information is maintained in the source file.
- Programmatic security: This is embedded in an application and is used to make security decisions. It can be used when declarative security alone is not sufficient to express the security model of an application. The Java EE security API allows the developer to test whether the current user has access to a specific role using these calls:
isUserInRole()for servlets, JSPsisCallerInRole()for EJBsAdditionally, there are other API calls that provide access to the user's identity:
getUserPrincipal()for Servlets, JSPsgetCallerPrincipal()for EJBsUsing these APIs, you can develop arbitrarily complex authorization models.
- Annotation security encompasses both the declarative and programmatic security concepts.
The framework that provides an API for the authentication and authorization of users is called Java Authentication and Authorization Service (JAAS).
JAAS uses a service provider approach for its authentication features, meaning that it is possible to configure different login modules for an application without changing any code. The application remains unaware of the underlying authentication logic. It's even possible for an application to contain multiple login modules, somewhat like a stack of authentication procedures.
The Login Module is the key element of JAAS authentication, which is based on information provided through CallbackHandler. Custom login modules must implement the methods defined by the javax.security.auth.spi.LoginModule interface.
Clients interact with JAAS through a LoginContext object that provides a way to develop applications independent of the underlying authentication technology. The LoginContext class describes the methods used to authenticate subjects. A Subject is an identity in a system that you want to authenticate and assign access rights to.
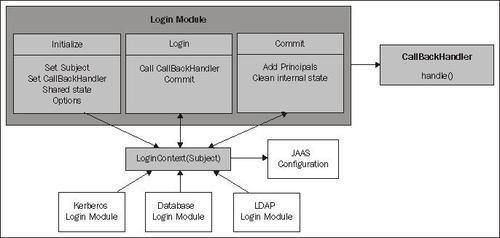
In the following example, a LoginContext is created by using the login module name as the first argument of the constructor and the callback handler as the second argument for passing login information to the Login Module.
Each CallbackHandler implements a handle method that transfers the required information to the Login Module. The login method in the LoginContext is used to start the login process. Following is a sample servlet that challenges the JAAS authentication process:
public class LoginServlet extends HttpServlet {
public void doGet (HttpServletRequest req,
HttpServletResponse res)
throws ServletException, IOException
{
PrintWriter out = res.getWriter();
LoginContext ctx = null;
try {
ctx = new LoginContext("SampleLogin", new MyCallbackHandler());
} catch(LoginException le) {
throw new RuntimeException("Login failed!");
}
try {
ctx.login();
} catch(LoginException le) {
throw new RuntimeException("Authentication failed!");
}
out.println("Authentication succeeded.");
}
After its successful completion, LoginModules add instances of java.security.Principal to the Subject, and the application can retrieve the Subject from the LoginContext using the getSubject() method.
