John the Ripper (http://www.openwall.com/john/) is a tool that can be used to crack the password hash. Currently, it can crack more than 40 password hash types, such as DES, MD5, LM, NT, crypt, NETLM, and NETNTLM. One of the reasons to use John instead of the other password-cracking tools described in this chapter is that John is able to work with the DES and crypt encryption algorithms.
To start the John tool, use the console to execute the following command:
# john
This will display the John usage instructions on your screen.
John supports the following four password-cracking modes:
- Wordlist mode: In this mode, you only need to supply the wordlist file and the password file to be cracked. A wordlist file is a text file containing the possible passwords. There is only one word on each line. You can also use a rule to instruct John to modify the words contained in the wordlist according to the rule. To use wordlist, just use the --wordlist=<wordlist_name> option. You can create your own wordlist or you can obtain one from other people. There are many sites that provide wordlists. For example, there is the wordlist from the Openwall Project, which can be downloaded from http://download.openwall.net/pub/wordlists/.
- Single-crack mode: This mode has been suggested by the author of John and is to be tried first. In this mode, John will use the login names, Full Name field, and user's home directory as the password candidates. These password candidates are then used to crack the password of the account they were taken from or to crack the password hash with the same salt. As a result, it is much faster than the wordlist mode.
- Incremental mode: In this mode, John will try all of the possible character combinations as the password. Although it is the most powerful cracking method, if you don't set the termination condition, the process will take a very long time. Examples of termination conditions are setting a short password limit and using a small character set. To use this mode, you need to assign the incremental mode in the configuration file of John. The predefined modes are All, Alnum, Alpha, Digits, and Lanman or you can define your own mode.
- External mode: With this mode, you can use the external cracking mode used by John. You need to create a configuration file section called [List.External:MODE], where MODE is the name you assign. This section should contain functions programmed in a subset the of the C programming language. Later, John will compile and use this mode. You can read more about this mode at http://www.openwall.com/john/doc/EXTERNAL.shtml.
If you don't give the cracking mode as an argument to John in the command line, it will use the default order. First, it will use the single-crack mode, then the wordlist mode, and after that it will use the incremental mode.
Before you can use John, you need to obtain the password files. In the Unix world, most systems use the shadow and passwd files. You may need to log in as root to be able to read the shadow file.
After you get the password files, you need to combine these files so that John can use them. To help you, John provides you with a tool called unshadow.
The following is the command to combine the shadow and passwd files. For this, I use the /etc/shadow and /etc/passwd files from the Metasploitable 2 virtual machine and put them in a directory called pwd with the names etc-shadow and etc-passwd, respectively:
# unshadow etc-passwd etc-shadow > pass
The following is a snippet of the pass file content:
root:$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:0:0:root:/root:/bin/bash
sys:$1$fUX6BPOt$Miyc3UpOzQJqz4s5wFD9l0:3:3:sys:/dev:/bin/sh
klog:$1$f2ZVMS4K$R9XkI.CmLdHhdUE3X9jqP0:103:104::/home/klog:/bin/false
msfadmin:$1$XN10Zj2c$Rt/zzCW3mLtUWA.ihZjA5/:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash
postgres:$1$Rw35ik.x$MgQgZUuO5pAoUvfJhfcYe/:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
user:$1$HESu9xrH$k.o3G93DGoXIiQKkPmUgZ0:1001:1001:just a user,111,,:/home/user:/bin/bash
service:$1$kR3ue7JZ$7GxELDupr5Ohp6cjZ3Bu//:1002:1002:,,,:/home/service:/bin/bash
To crack the password file, just give the following command, where pass is the password list file you have just generated:
john pass
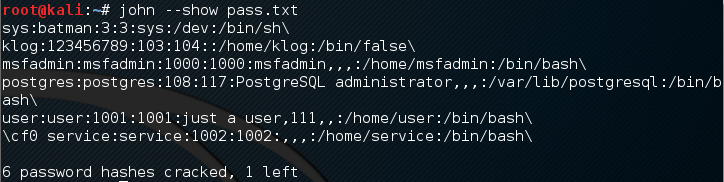
If John managed to crack the passwords, it will store those passwords in the john.pot file. To see the passwords, you can issue the following command:
john --show pass
In this case, John cracks the passwords quickly, as shown in the following screenshot:
The following table is the list of cracked passwords:
|
Username |
Password |
|
postgres |
postgres |
|
user |
user |
|
msfadmin |
msfadmin |
|
service |
service |
|
klog |
123456789 |
|
sys |
batman |
Of the seven passwords listed in the pass file, John managed to crack six passwords. Only the password of root cannot be cracked instantly.
If you want to crack the Windows password, first you need to extract the Windows password hashes (LM and/or NTLM) in the pwdump output format from the Windows system and SAM files. You can consult http://www.openwall.com/passwords/microsoft-windows-nt-2000-xp-2003-vista-7#pwdump to see several of these utilities. One of them is samdump2, provided in Kali Linux.
To crack the Windows hash obtained from samdump2 using a password.lst wordlist, you can use the following command and the obtained output is displayed on the following screenshot:
# john test-sam.txt --wordlist=password.lst --format=nt
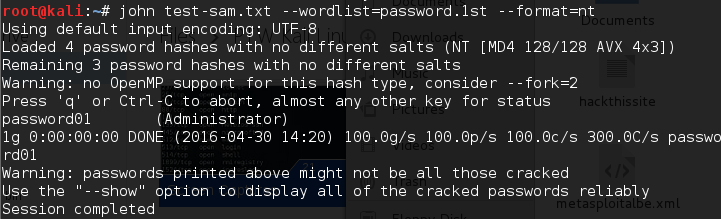
The password.lst file content is as follows:
password01
To see the result, give the following command:
# john test-sam.txt --format=nt --show
The following screenshot shows a snippet of the password obtained:
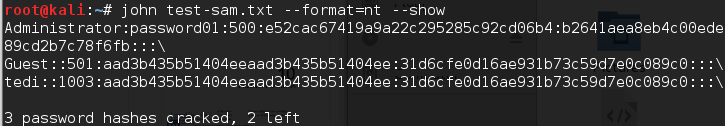
John was able to obtain the administrator password of a Windows machine, but was unable to crack the password for the tedi user.
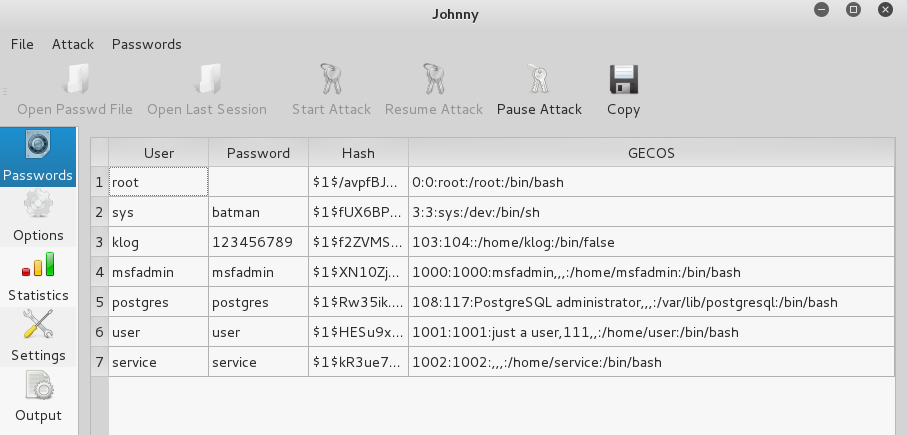
If a GUI is more your thing, there's a graphical interface for John and it's called Johnny.
To start Johnny, open a console and type the following command:
# johnny
You will then see the Johnny window.
The following screenshot shows the result of cracking the same Metasploitable 2 hashes: