In This Chapter
Adding, modifying, and deleting users
Establishing Parental Controls
Configuring FileVault
Avoiding keychains
In Chapter 4 of this minibook, I introduce you to the different Mac OS X multiuser account levels and the login process. In this chapter, if you're ready to share your MacBook with others, you can discover how to add new accounts and edit existing accounts. Oh, and yes, I also show you how to frag — that's multiplayer game-speak for delete — accounts that you no longer need. I also demonstrate how to add optional limitations to an individual user account and how to avoid using a keychain (which is supposed to make it easier to store that pocketful of passwords that you've created on the Internet).
Yes, you read correctly. By all that's good and righteous, Mac OS X actually has a feature that I don't want you to use. Read on to find out more.
All multiuser account chores take place in a single System Preferences pane. (Cue James Bond theme song.) The Accounts pane is the star of this chapter, so open System Preferences and click the Accounts icon.
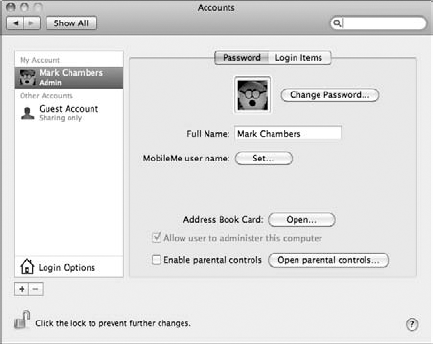
If you haven't added any users to your system yet, the Users list should look like Figure 5-1. You should see your account, which you set up when you installed Mac OS X, set to administrator (admin) level.
Tip
You also have an entry for a Guest account, which anyone can use on an as-needed basis. To enable the Guest account, click the Guest entry in the list and click the Allow Guests to Log In to This Computer check box to select it. Note that any files created inside the Guest Home folder or settings changed by the Guest user are automatically deleted when the Guest user logs out (or you restart or reboot your Mac).
To add a new user account, follow these steps:
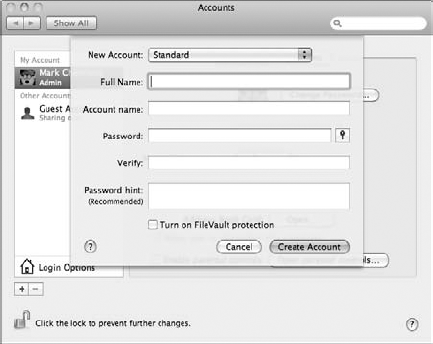
In the Accounts pane in System Preferences, click the New User button — which carries a plus sign — to display an empty user record sheet that you see in Figure 5-2.
Tip
If the New User button is disabled and you can't click it, click the lock at the bottom left of the System Preferences pane and provide your password to unlock the Accounts pane.
Select the access level for this user from the New Account pop-up menu.
By default, the user receives a standard level account. You can also choose an Administrator account, a sharing-only account (with access only to shared files), or a Managed standard account with Parental Controls already enabled.
In the Name text box, type the name that you want to display for this account (both in the Accounts list and on the Login screen) and then press Tab to move to the next field.
Tip
Mac OS X automatically generates an Account (or short) name for use as your screen and Buddy name in iChat and various network applications. The short name is also the name of the folder that Mac OS X creates on the computer's hard drive for this user. You can keep the default short name or type a new one, but it must not contain any spaces. Choose the short name carefully, for it can't be changed within the Finder. For more on iChat, jump to Book VI, Chapter 3. (I'll wait for you here.)
Press Tab again.
In the Password text box, type the password for the new account.
Click the button with the key icon next to the Password field, and Snow Leopard is happy to display the Password Assistant, complete with a suggestion. Click the Suggestion pop-up menu to see additional suggestions. You can choose the length of the password and select from several types: letters and numbers, numbers only, memorable, completely random, or even government-quality. The Assistant automatically copies the current password you're considering to the Password text box.
As always, when you enter a password or its verification, Mac OS X displays bullet characters for security.
Press Tab, type the password in the Verify text box, and press Tab again.
(Optional) If you decide to use the password hint feature that I describe in Book II, Chapter 4, you can enter a short sentence or question in the Password Hint text box.
The hint is displayed after three unsuccessful attempts at entering the account password.
Warning
I recommend that you do not use this option. Think about it: Any hack could type in anything three times to get your hint to pop up! If you do use this option, at least make sure that the hint is sufficiently vague!
Press Tab to continue.
To automatically turn on the FileVault encryption feature for this new account, select the Turn On FileVault protection check box.
For more information on FileVault, see the sidebar later in this chapter entitled "So you like your privacy..."
Click the Create Account button to finish and create the account.
The new account shows up in the Accounts list and in the Login screen.
If you have administrator access, it's a cinch to make changes to an existing account from the Accounts pane in System Preferences. (Often, this is to assign a personalized account picture, so I demonstrate that here.) Follow these steps:
Click the account that you want to change in the Accounts list.
Don't forget, if the accounts in the list are disabled and you can't select one, you must unlock the Accounts pane. Click the lock at the bottom left of the System Preferences window and type your password.
Edit the settings that you need to change.
Click the square Picture well to specify the thumbnail image that appears in the Login list next to the account name.
Apple provides a number of good images in the preview collection — just click a thumbnail to select it.
To add your own picture, click Edit Picture. You can drag a new image from the Finder or iPhoto into the icon placeholder, or click Choose to select one from an Open File dialog; then click Set.
Alternatively, you can click the Take a Video Snapshot button to grab a picture from your MacBook's iSight video camera. Most cool.
After you make the changes (and you select just the right image to capture the user's personality — a more difficult task than you might think), press
To wipe an account from the face of the Earth, follow these steps:
Click the account that you want to delete in the Accounts list.
Click the Delete User button (which is smartly marked with a minus sign).
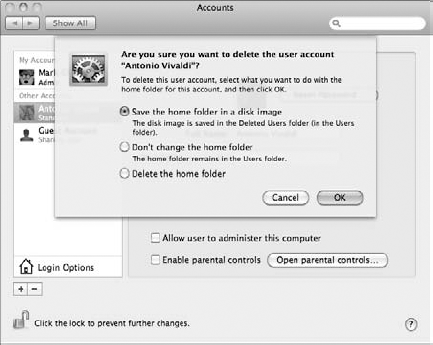
Mac OS X displays the confirmation sheet that you see in Figure 5-3.
Tip
Note that the contents of the user's Home folder can be saved in a disk image in the Deleted Users folder (just in case you need to retrieve something). Alternatively, you can choose to leave the deleted user's home folder as is, without removing it.
If you're absolutely sure you won't be dating that person again, click the Delete the Home Folder option (which doesn't save anything in the Deleted Users folder). You regain all the hard drive space that was being occupied by the contents of the deleted user's home folder.
Click OK to verify and delete the account. Click the Cancel button to abort and return to the Accounts list.
Administrators are special people. Just ask one; you'll see. Anyway, when an administrator creates or edits the account for a standard-level user, Mac OS X offers a number of levels of specific rights — Parental Controls — that can be assigned on an individual account basis. When an account has Parental Controls assigned, it becomes a managed account.
Parental Controls are available only for standard-level users; administrators aren't affected by them because an administrator-level account already has access to everything covered by Parental Controls.
When do you need Parental Controls? Here are three likely scenarios:
You're creating accounts for corporate or educational users, and you want to disable certain features of Mac OS X to prevent those folks from doing something dumb. Just tell 'em you're streamlining the operating system. (Yeah, that's it.) For example, you might not want that one particular kid making CD copies of The Illustrated Anarchist's Cookbook in the classroom while you're gone. Therefore, you disable the ability for that account to burn CDs or DVDs.
In the same environment, you might want to give a specific standard-level account the ability to administer printers. If Roger in Accounting is both helpful and knowledgeable — oh, and add trustworthy in there, too — you might want to give him this capability so that he can handle the print queues while you're on vacation.
You want one or more users to access one — and only one — application on the system, or perhaps just two or three applications. To illustrate: In my years as a hospital hardware technician, we had a number of computers that were used solely to display patient records. No Word, no e-mail, nothing but the one program that accessed the medical records database. We called these machines dumb terminals although they were actually personal computers. (This trick also works well if you're a parent and you want to give your kids access without endangering your valuable files. Just don't call your computer a dumb terminal lest your kids take offense. That's experience talking there.) If you want to allow access to a specified selection of applications, you can set them in that account's Controls.
Time to review what each of the settings does. To display the controls for a standard account, click the account in the list and then click the Open Parental Controls button. Click the Enable Parental Controls button, and click the Lock icon in the lower-left corner to confirm your access (if necessary). Snow Leopard includes five different categories of controls, as shown in Figure 5-4:
System: These settings (which I discuss in more detail in a second) affect what the user can do within Snow Leopard as well as what the Finder itself looks like to that user.
Content: These settings control the Dictionary and Safari applications. If you prefer that profane terms be hidden within the Dictionary for this user, click the Hide Profanity in Dictionary check box to enable it. Snow Leopard also offers three levels of control for Web sites:
Allow Unrestricted Access: Select this radio button to allow unfettered access for this user.
Try to Limit Access: You can allow Safari to automatically block Web sites it deems adult. To specify particular sites that Snow Leopard should allow or deny, click the Customize button.
Allow Access to Only These Websites: Choose this radio button to specify which Web sites the user can view. To add a Web site, click the Add button (which bears a plus sign) — Snow Leopard prompts you for a title and the Web site address.
Mail & iChat: Click the Limit Mail and Limit iChat check boxes to specify the e-mail and instant messaging addresses that this user can communicate with. (Note that this affects only Apple Mail and iChat, so other mail clients, Web-based mail, and instant messaging applications aren't controlled.) To add an address that the user can e-mail or chat with, click the Add button.
Tip
Do you want a notification if the user is attempting to send an e-mail to someone not in the list? Click the Send Permission Requests To check box to select it and then type your e-mail address in the text box.
Time Limits: Parents, click the Time Limits button, and you'll shout with pure joy — check out the options on this pane in Figure 5-5! You can limit an account to a certain number of hours of usage per weekday (Weekday Time Limits), limit to a specified number of hours of usage per weekend day (Weekend Time Limits), and set a bedtime computer curfew time for both weekdays and weekend days. (Note that vacations and school holidays aren't recognized within Time Limits, so you'll have to manage them manually!)
Logs: Snow Leopard keeps a number of different types of text log files (which track where the user goes on the Internet, which applications are launched by the account, and the contents of any iChat conversations where the user was a participant). From this central pane, you can monitor all the logs for a particular account. Note that these logs are enabled or disabled from other locations within Snow Leopard: For example, the log showing the Web sites visited and blocked is enabled from the Content pane that I describe a little earlier, whereas the applications log is enabled when on the System pane. iChat logging is turned on from the Preferences dialog within the iChat application.
Note
You can always tell whether an account has been assigned Parental Controls because the account description changes from Standard to Managed in the Accounts list.
Of particular importance are the System controls. Click the System tab to modify these settings:
Use Simple Finder: I discuss the Simple Finder in the following section because it's a great idea for families and classrooms with smaller children.
Only Allow Selected Applications: When this option is selected, you can select the specific applications that appear to the user. These restrictions are in effect whether the user has access to the Full Finder or just the Simple Finder.
To allow access to all the applications of a specific type — iLife, iWork, Internet, Widgets, Other, and Utilities — click the check box next to the desired group heading to select it. To restrict access to all applications within a group, click the check box next to the heading to deselect it. You can also toggle the restriction on and off for specific applications in these groups; click the triangle icon next to each group heading to expand the list and then either mark or clear the check box next to the desired applications. (If you see a minus sign in the check box, some subordinate items are selected.) To locate a specific application, click in the Search box and type the application name.
Tip
To add a new application to the Allow list, drag its icon from the Finder and drop it in the list within the Other group. After you add an application, it appears in the Other group, and you can toggle access to it on and off like the applications in the named groups.
Can Administer Printers: With this check box selected, the user can modify the printers and printer queues within the Print & Fax pane in System Preferences. If this option is disabled, the user can still print to the default printer and switch to other assigned printers but can't add or delete printers or manage the Mac OS X print queue.
Can Burn CDs and DVDs: Deselect this check box to prevent the user from recording CDs or DVDs via the built-in disc recording features in the Mac OS X Finder. (Note, however, that if you load a third-party recording program, such as Toast, the user can still record discs with it.)
Can Change Password: Select this check box to allow the user to change the account password.
Tip
If you're creating a single standard-level account for an entire group of people to use — for example, if you want to leave your laptop in kiosk mode in one corner of the office or if everyone in a classroom will use the same account on the machine — I recommend disabling the ability to change the account password. (Oh, and please do me a favor...don't create a system with just one admin-level account that everyone is supposed to use! Instead, keep your one admin-level account close to your bosom and create a standard-level account for the Unwashed Horde.)
Can Modify the Dock: Select this check box, and the user can remove applications, documents, and folders from the Dock in the Full Finder. (If you don't want the contents of the Dock changing according to the whims of other users, it's a good idea to deselect this check box.)
You can restrict your standard-level users even further by assigning them the Simple Finder set of limitations. The default Simple Finder, as shown in Figure 5-6, is a highly simplified version of the regular Mac OS X Finder. The simplified Dock contains only the Finder icon, the Trash, and the folders for the user's approved applications, documents, and shared files.
This is the network administrator's idea of a foolproof interface for Mac OS X: A user can access only those system files and resources needed to do a job, with no room for tinkering or goofing off.
Tip
A Simple Finder user can still make the jump to the full version of the Finder by clicking Finder and choosing Run Full Finder. The user has to enter a correct admin-level username and password.
Tip
You can also change the Auto Login account from the Accounts pane. Click the Login Options button under the Accounts list and then click the Automatic Login pop-up menu to choose the account that automatically logs in when Mac OS X starts up. Enter the account password on the confirmation sheet that appears and click OK. Although I've made it clear elsewhere that Automatic Login is not a good security feature in many cases (such as when you're on the road with a laptop), it can be a good feature for those preparing a MacBook for public use. If you set the Automatic Login to your public standard-access account, Mac OS X automatically uses the right account if the MacBook is rebooted or restarted.
Don't forget, you can always choose Log Out from the Apple menu to log in under your own account.
Before I leave this chapter, I want to discuss a Mac OS X feature that's been around since the days of Mac OS 8: the keychain. Your account keychain stores all the username/password combinations for Web sites, file servers, File Transfer Protocol (FTP) servers, and the like, allowing you to simply waltz in and start using the service (whatever it is). Sounds handy, doesn't it? And it can be, but you had better watch your step.
I'm perfectly honest here: I hate account keychains. With a passion, mind you. As a consultant, Webmaster, and the SYSOP (an ancient Bulletin Board Service acronym meaning System Operator) of an Internet-based online system, I know what a hassle it is for users to remember separate passwords, and I feel that pain. (I use separate passwords for everything.) However, three massively big problems are inherent with using keychains:
Anyone can log on as you. If your keychain is unlocked, which happens automatically when you log in, all someone has to do is sit at your desk, visit a site or connect with a server, and bam! They're on. As you. Think about that. And then think how many times you get up from your desk, just for a second, to grab another Diet Coke or a doughnut.
You'll forget your passwords. If the keychain file is corrupted — and it can happen — your passwords have gone to Detroit without you. Either you've got them on paper hidden somewhere, they're on your recent backup, or it's time to change your online persona.
Keychains need yet another stinkin' password. Yep, that's right — your keychain can be locked (either manually or, with the right settings, automatically), and you have to remember yet another password/passphrase to unlock your keychain. "When, oh when will the madness end?"
Warning
From a security standpoint, keychains should be completely off-limits for anyone who's interested in maintaining a well-locked-down machine. After all, most folks can completely take care of all their Internet and network connections with a handful of passwords, and that's no big deal for anyone to remember. Unfortunately, Snow Leopard creates a keychain automatically for every user, so you have to monitor (and delete) your keychain data manually. (Sigh.)
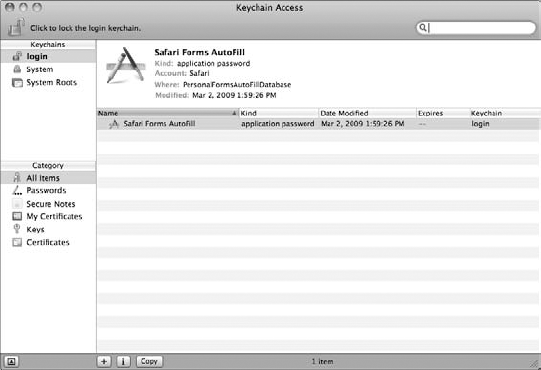
However, if you're the only person using your MacBook and it resides in your home — personally, I'd prefer a bank vault — and you absolutely must use keychains, you can display them all for the current account from the Keychain Access application (see Figure 5-7), conveniently located in Utilities within your Applications folder. Click the Category tab and then click an item in the keychain list to display or edit all its information.
Warning
Heck, just think about what I just wrote — anyone can display and edit server and site information just by launching this application! That includes your nephew Damien — you know, the one who considers himself the hacker extraordinaire. (While I'm at it, I should mention that it's just as bad to set the Automatic Login feature — which I discuss earlier in this chapter — to an admin-level account. One reboot, and you're rolling out the red carpet for the little rascal. For the inside information on Automatic Login, visit Chapter 4 in this very minibook.)
To help lock things down — at least when it comes to your Internet communications — follow this path:
To display your Internet passwords, click the Passwords category (upper-left).
Click each Internet password to select it in the list and then click the lowercase i button at the bottom of the window to display the information on that password.
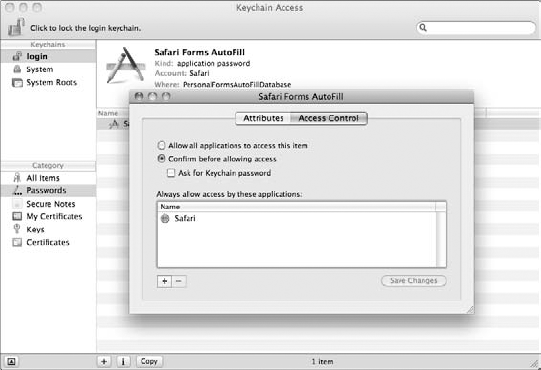
Click the Access Control tab to display the settings that you see in Figure 5-8, one of which I strongly recommend.
To minimize the damage that someone can do with this password, you can select the Confirm before Allowing Access radio button. And for yet another level of security, select the Ask for Keychain Password check box.
Of course, you're probably thinking, "Well, Mark, that pretty much eliminates the purpose of quick, convenient access without passwords, doesn't it?" Yes, indeed it does, but at least your online identity is somewhat safeguarded.
Click the plus sign button at the bottom of the Keychain Access window to add a new password. Type a name for the item, the username that you typically type to gain access, and the password for that server or site. Then click Add and cross your fingers.
To display all the keychains you can access, choose Edit
To lock or unlock your login keychain, click the Lock icon at the top-left of the Keychain Access window. (Unlocking your keychain requires you to enter your login password. Go figure.)
You might be saying to yourself, "Geez, this guy is more than a little paranoid." And yes, dear reader, I suppose I am. But then again, who's been uploading all those questionable images and MP3 files to the company server ...using your account?