IPv6 will be the largest overhaul of the Internet since its commercialization. It is due to arrive in 2005 and will incrementally replace the Internet protocol (IP). Many existing network programs will become obsolete as they become incompatible with the emerging networks. This will inevitably create a great opportunity for network programmers who are familiar with the new protocol.
Such a large overhaul is extremely expensive, but the simple fact is that the IP cannot accommodate the explosion in market demand for Internet access. In the long run, the migration to IPv6 makes perfect sense and is inevitable. IPv6 will create a bigger, faster Internet that will continue to accommodate the world’s bandwidth-hungry population into the twenty-second century. Making your application IPv6 compatible from the outset will ensure that you will not have to go through a costly overhaul once IPv6 becomes mainstream.
This chapter is divided into two sections, beginning with a discussion of IPv6 in general and the utilities you can use to manage IPv6 on your network. The chapter concludes with an example of how to communicate over IPv6 from within a .NET application.
IP addresses are 32 bits long, which provides four billion unique addresses. The number of assigned IP addresses is fast approaching this mark. Contributing to this consumption of IP addresses are professionals in the developed world who may have several computers dedicated for their use. The largest source of IP wastage is the way in which addresses are assigned in blocks of 256 or 65,355, which could be hundreds or thousands more addresses than are required by one organization.
IPv6 addresses this issue by extending the address to 128 bits, which provides 3 billion billion billion billion unique addresses. Even if the world’s computer usage were to double every year, it would take 100 years for the same problem to occur again.
There is no provision in IPv4 for storing routing information. It is possible for a router to predict the fastest route for a packet many hops in advance, but the IPv4 packet can only hold the next-hop address, so the receiving router has to recalculate the fastest route. This consumes router processing power and delays packets unnecessarily.
IPv6 can hold routing information in its header and can, therefore, be forwarded through routers with minimal time wastage. Furthermore, the header is expandable with optional fields, such that it could hold the routing information the whole way from a computer in Europe to a server in the United States.
IPX was once a strong contender to IP, but it was unfortunately not adopted by router vendors and, thus, cannot be used for Internet communications; however, its unique identifier was based on the hardware (MAC) address and, thus, was easily configurable, with no need for assignation protocols such as DHCP, unlike IP. A MAC address is 48 bits long, and therefore can be contained within the IPv6 address. This then negates the need for ARP and DHCP, thus simplifying the job of the network administrator.
Systems that implement security features, such as HTTP-form authentication, are built on top of IP. This leaves security holes open for people who have the resources to perform IP spoofing (i.e., the impersonation of IP addresses). IPv6 contains built-in headers to protect against IP spoofing, with encryption, authentication, and privacy.
The final difference between IPv6 and IPv4 is the quality-of-service (QoS) provision. In this way, data with absolute priority, such as voice over IP (VOIP) will be forwarded through routers before emails, where it doesn’t matter if they’re a few seconds late.
In 1993, the IETF issued RFC 1550, “IP: Next Generation (IPng) White Paper Solicitation.” This could almost be described as a request for tenders for a replacement of IP. This was followed by a requirements document in RFC 1726, “Technical Criteria for Choosing IP: The Next Generation (IPng).” In January 1995, the initial specification for IPng, RFC 1752, was issued as “The Recommendations for the IP Next Generation Protocol.” Despite the best efforts of the IETF, IPng became commonly known as IPv6 with the release of its final specification in RFC 1883.
The first layer 3 protocol to support large addresses was CLNP, more commonly known as TUBA (TCP and UDP over bigger addresses). This had huge 160-bit addresses and was well-established within certain fields; however, it was inefficient in comparison to IP and lacked the ability to multicast.
In 1993, two new protocols emerged: simple IP (SIP) and policy IP (PIP), both of which were extensions on IP. SIP addressed the scalability issue, proposing a 64-bit address, whereas PIP addressed policy routing for efficiency. The two protocols were merged to form SIPP and extended to 128-bit addressing. The findings were published in 1994. This led to the development of an experimental protocol, IPv5. This protocol was designed to coexist with IPv4, but used the same addressing scheme. When the limitations in IPv5 were addressed, a new protocol, IPv6, emerged.
IPv6 will have knock-on effects to routing and auxiliary protocols such as OSPF, BGP, IDRP, and SNMP. It is predicted that RIP will be replaced by RIP-2 with the rollout of IPv6.
IPv6 is backward compatible with IPv4, so there will be a gradual migration toward the technology. When the last block of IP addresses is assigned, organizations will be given the chance to use IPv6 instead. This may involve buying more expensive IPv6-compatible routers, hubs, and switches. The higher-level protocols, such as TCP and UDP, will not change, although some higher-level protocols may have some compatibility problems (e.g., the PASV command in FTP).
Many applications designed for IPv4 will not work on IPv6, producing a market void in IPv6-compatible software. Because some large firms, such as Microsoft, IBM, and Digital Equipment Corporation (DEC), have developed their own IPv6 implementation, it is unlikely that the changeover will affect their software.
The first and most obvious difference is the change in the format of the IP address. IPv6 addresses consist of a combination of six identifiers: (1) a 3-bit format prefix (FP), which is always 001 for aggregatable unicast addresses; (2) the 13-bit top-level aggregator (TLA), which would be a number assigned to a backbone service provider; (3) an 8-bit reserved field, set to 0; (4) the 24-bit next-level aggregator (NLA), which would represent an ISP; (5) the 16-bit site-level aggregator (SLA), which would represent the subnet; and (6) the 64-bit interface ID, which identifies a specific interface on a host. The definitive description of this format is described in RFC 2374.
A global IPv6 address, therefore, takes the following form:
[FP][TLA]:[Reserved][NLA]:[SLA]:[Interface ID]
With Ipv4 addresses, it was practical to write each byte in decimal format, such as 195.233.254.33; however, with a 128-bit address, it becomes awkward to write 16 three-digit numbers to represent a single IP address. Therefore, a new naming convention is used to quote IPv6 addresses. IPv6 addresses are quoted in hexadecimal, not decimal. They are broken into 16-bit segments, rather than 8 bits, as was the case with IPv4. Therefore, one would write FFFF:FFFF rather than 255.255.255.255.
To abbreviate long sequences of zeros, the double colon (::) is used. Sequential blocks of 16 zero bits are replaced with the double colon for brevity. The IPv6 address 2001:0db8:1000:0000:0000:0000:0000:0027 is abbreviated to 2001:db8:1000::27.
When an IPv6 address encapsulates an IPv4 address, the IPv4 address is represented in its standard form within the IPv6 address. An example of this would be ::192.44.75.70 ::ffff:192.44.75.70.
In order to separate the IPv6 prefix from the IPv6 interface identifier, it is common practice to append a forward slash followed by the length of the prefix to the end of an IPv6 address. For example, in the case of
2001:db8:2000:240:290:27ff:fe24:c19f/64,
the prefix is
2001:db8:2000:240.
If you have Windows XP, you can install IPv6 by simply typing IPv6 install at the command prompt. To test IPv6 on Windows 2000 (Service Pack 1) or later, you need to download an add-on from www.microsoft.com/windowsserver2003/technologies/ipv6/default.mspx. You will need an Ethernet Network adapter, and TCP/IP must be installed.
To install IPv6 on Windows 2000, follow these steps:
Download the add-on from Microsoft.com.
Click Start→Settings→Network and Dial-up Connections.
Right-click on your Ethernet card and click Properties.
Click Install.
In the Select Network Component Type box, click Protocol and then click Add.
In the Select Network Protocol box, click Microsoft IPv5 Protocol.
Click OK and then Close.
To install IPv6 on previous versions of Windows, links to third-party vendors are located at www.ipv6.com.
To uninstall IPv6 from a host, in Windows XP, you simply type Ipv6 uninstall at the command line and reboot the computer.
Similar to the loopback address in IPv4 (127.0.0.1), you will always be given an IP address whether you are online or not. In IPv6, the equivalent of the loopback address is the link-local address. This is FE80::1.
Non-link-local addresses, such as site-local addresses or global addresses, are automatically assigned based on the receipt of IPv6 router advertisements (akin to DHCP in IPv4). An IPv6-compatible router is required to issue router advertisements.
If you have Windows XP, you will be happy to know that several handy IPv6 utilities come preinstalled, which is helpful for implementing IPv6 applications.
IPv6 is a command-line-based utility that is similar, in some ways, to ipconfig. To use this application in a meaningful way, you should install the IPv6 protocol thus:
IPv6 install
After a few seconds, it should report “succeeded.” At this point, you can view your IPv6 address and other technical information about the IPv6 stack. You will be allocated several interfaces, through which you can access the Internet. This includes the physical network interface and hybrid interfaces. You can list the interfaces on your system by typing the following:
IPv6 if
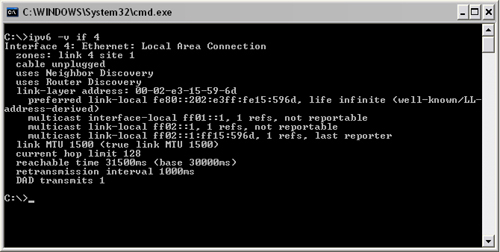
To specify an interface, you can type IPv6 if <number>, such as in Figure 16.1, where interface 4 was a network card.
Global configuration parameters for the IPv6 stack can be viewed by typing IPv6 gp. A typical response would be:
DefaultCurHopLimit = 128 UseAnonymousAddresses = yes MaxAnonDADAttempts = 5 MaxAnonLifetime = 7d/24h AnonRegenerateTime = 5s MaxAnonRandomTime = 10m AnonRandomTime = 2m21s NeighborCacheLimit = 8 RouteCacheLimit = 32 BindingCacheLimit = 32 ReassemblyLimit = 262144 MobilitySecurity = on
To view the prefix policy table for the IPv6 stack, you can use IPv6 ppt, typical response being the following:
::ffff:0:0/96 -> precedence 10 srclabel 4 dstlabel 4 ::/96 -> precedence 20 srclabel 3 dstlabel 3 2002::/16 -> precedence 30 srclabel 2 dstlabel 2 ::/0 -> precedence 40 srclabel 1 dstlabel 1 ::1/128 -> precedence 50 srclabel 0 dstlabel 0
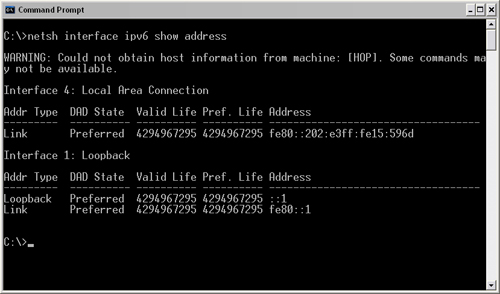
This useful utility can be used to read information from the IPv6 stack, as well as to perform many of the tasks of the previous utility. It is more user-friendly than the IPv6 utility and provides much the same level of information (Figure 16.2).
To view your IPv6 address using NETSH, type the following at the command line:
Netsh interface ipv6 show address
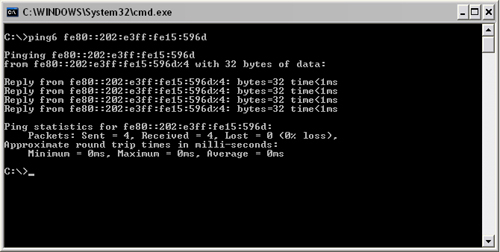
There are no prizes for guessing what ping6 does. It is simply an IPv6 implementation of the ping utility. It is a stripped-down version of ping, but it uses IPv6 addresses rather than IPv4 addresses (Figure 16.3). Parameters that are not supported by the Ping6 utility (but not necessarily IPv6) are TTL, fragment flag, type of service (TOS), and loose and strict routing. The parameters that are supported are listed in Table 16.1.
Table 16.1. Command-line parameters for Ping6.
Parameter | Purpose |
|---|---|
| Pings the host until the user presses CTRL + C |
| Resolves IP addresses to host names |
| Sends a specified number of pings |
| Sends buffer size; default is 32 bytes |
| Uses the routing header to test the reverse route as well as the forward route |
| Uses the specified source address in the ping requests |
| Discards any replies delayed longer than the specified time |
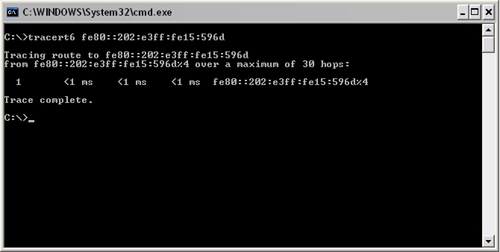
This program is a migration of the tracert utility from IPv4 to IPv6 (Figure 16.4). Some command-line parameters have changed from the original version, including the j, s, and r command-line parameters. Like ping6, tracert6 no longer supports loose and strict routing (j parameter), although it does support the parameters in Table 16.2.
Table 16.2. Command-line parameters for Tracert6.
Parameter | Purpose |
|---|---|
| Suppresses the resolving of IP addresses to domain names |
| Specifies the maximum number of hops between source and destination |
| Discards any replies delayed longer than the specified time |
| Uses the specified source address in the ping requests |
| Uses the routing header to test the reverse route as well as the forward route |
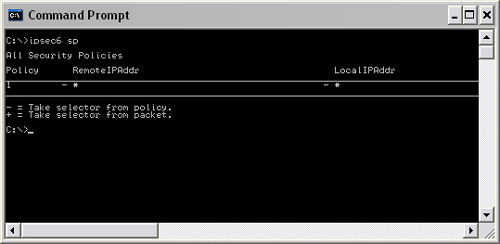
IPSec6 is a utility that manages IP-level security. This is a long-awaited security feature that effectively makes it impossible for hackers to forge IP addresses. To view the security policies on your system, you can type IPSec6 sp at the command prompt. This displays the contents of the IPSec6 security policies database (illustrated in Figure 16.5; described in Table 16.3). You can also view the security associations database (Table 16.4) by typing IPSec6 sa at the command prompt.
Table 16.3. Fields in the IPv6 security policies database.
Purpose | |
|---|---|
| An identifier for the policy, similar to a primary key in a database |
| The IP address from which the packet has originated |
| The IP address at which the packet is arriving |
| The higher-level protocol in use |
| The port from which the packet came |
| The port at which the packet arrived |
| The version of the IPSec protocol in use; default is |
| The mode of operation of IPSec |
| The remote gateway IP address |
| The security association bundle index; default is |
| The direction of travel of the packet. The default is |
| The action to be taken on any particular packet; default is |
| The interface on which the packet arrives |
Table 16.4. Fields in the IPv6 security associations database.
Field | Purpose |
|---|---|
| An identifier for the policy, similar to a primary key in a database |
| The destination IP address of the packet |
| The source IP address of the packet |
| The higher-level protocol in use |
| The destination port of the packet |
| The source port of the packet |
| The authorization algorithm in use |
| The symmetric or public key in use |
| The direction of travel of the packet |
| The security policy index |
The IPv6 implementation comes with some extra utilities, such as 6to4cfg and checkv 4. The first of those two utilities is for use on hybrid IPv6/IPv4 networks. The latter is used to help migrate C++ Windows socket code to IPv6 compliance. C++ network programming code was concerned mainly with interfacing directly into wsock32.dll, which luckily C# or VB.NET programmers are not obliged to do.
Every device that runs IPv6 will maintain a routing table, opposed to all routing information being stored in routers. It is logical that PCs should provide some of the processing power to route packets, rather than leaving it up to routers.
When a router encounters an IPv6 packet, it will match the destination IPv6 address with entries in the destination cache to determine the next-hop address and forwarding interface. If no matching entry is found in the cache, then the destination IPv6 address is compared against the prefixes in the routing table. The closest match with the lowest cost (as determined from the preference or metrics field) is used.
A routing table consists of eight different fields:
The address prefix, similar to a subnet mask, will match specific IPv6 addresses to particular routes. The prefix can be any length between 0 to 128 bits long. This column is named
Prefixin the Windows XP routing table.The network interface for each prefix contains an index of the interface over which the packet should be retransmitted. This column is named
Idxin the Windows XP routing table.The next-hop address holds the IPv6 address of the host or router to which the packet is to be forwarded. This column is named
Gateway/Interface Namein the Windows XP routing table.A preference or metric for any particular route is used to provide routers with a means to select what route to send packets when two routes are available. The preference value could be set manually to reduce the cost of bandwidth billable connections.
The route lifetime is an optional field that can be used to provide for automatic routing cache purges.
The availability of a routing advertisement is, once again, an optional field, but it can be used to determine if the connecting network is IPv6 compliant.
The aging of the route is an optional field that aids in keeping router caches up to date.
The type of route is an optional field that can determine if a destination is directly attached, remote, an endpoint host, or the default route.
The routing table is constructed automatically and does not require manual input, in the same way as the ARP cache of IPv4 computers is not accessible to users. It is not mandatory for every IPv6 device to maintain a routing table; in fact, it is quite likely that many computers will store only the default route (::/0, i.e., an IPv6 address consisting only of zeros) to the nearest router.
To go into a little more detail on the route type field, four different types of routes can be stored in the routing table: directly attached, remote, endpoint host, or the default route. It can be estimated from the route type how far the destination is from the router.
A directly attached route is where a subnet is physically attached to the router. In this case, the prefix length would typically be 64 bits, and the distance between the router and the destination would typically only be two hops.
A remote route is where the packet is forwarded to a subnet or address space that is not physically connected. In this case, the prefix would be 64 bits or less, and the distance to the destination would typically be over two hops.
A host route is where the packet is being routed to an endpoint host, such as a computer. In this case, the prefix length is 128 bits long, and the distance would typically be one hop or less.
When the sending host does not specify the source address, then the entire routing table is checked for matches. If a source address is specified, then only entries for interfaces designated to handle that source address are checked.
The IPv6 destination address is compared against each entry in the table, looking for matches between the prefix and the high-order bits in the IPv6 destination address. Where a prefix is only 64 bits long, and therefore shorter than the IPv6 address, only the highest 64 bits of the IPv6 address are relevant for this comparison process.
If there is more than one match between the IPv6 destination addresses and the prefixes held in the routing table, the prefix with the longest length is selected. When two matching prefixes have the same length, the route with the lowest cost (as determined from the metrics or preference field) is selected. The default route is used only in the case where there are no successful matches.
The route selection provides a next-hop address and a forwarding interface. In the case where the next-hop address is not the endpoint host, but another router, then the next-hop address is stored in the next-hop address field in the packet.
In the case where the destination host or subnet is unreachable, then the router returns an ICMPv6 packet to the sender of the packet, stating that the host was unreachable. This is analogous to the action of ICMP in IPv4.
The IPv6 routing table is mostly self-maintaining. It builds entries from routing advertisements from other routers and phases out out-of-date or out-of-service routes over time. In the case where the network infrastructure has changed significantly, however, or for experimentation purposes, it may be necessary to configure the routing table of an IPv6 router manually, or in this case, a Windows XP server running the Internet connection sharing (ICS) service.
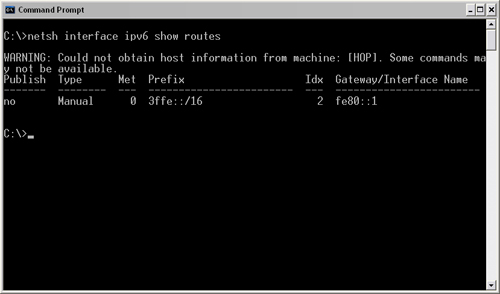
To show the IPv6 routing table (Figure 16.6) on your PC, type the following at the command line:
netsh interface ipv6 show routes
If any routes are stored in the routing table, information will follow the form described in Table 16.5.
Table 16.5. Fields in the IPv6 routing table.
Purpose | |
|---|---|
| Specifies whether the route is advertised in a routing advertisement message. |
| Specifies the metric or preference used to select between multiple routes with the same prefix. The lowest metric is the best matching route. |
| Specifies the address prefix; it can have a length between 0 and 128 bits. |
| Specifies the interface index, over which packets that match the address prefix may be transferred. Interface indexes can be viewed by typing |
| Specifies either an interface name or a next-hop IPv6 address. Remote network routes list a next-hop IPv6. Directly attached network routes list the name of the relevant interface. |
| Specifies the type of the route. Routes configured by user applications are listed with a route type of |
Assume that you wish to add a route to the routing table, where you want packets with a destination IPv6 address starting with 3ffe to be forwarded to the loopback address (fe80::1). For debugging purposes, we can name this route a. Therefore, you may use the following syntax:
netsh interface ipv6 add route 3ffe::/16 "a" fe80::1
To remove this link, you can use the following command:
netsh interface ipv6 delete route 3ffe::/16 "a" fe80::1
The IPv6 addresses assigned to interfaces can also be changed. Extra IPv6 addresses can be added to each interface if required. To give a quick example, if you ping6 the IPv6 address fe80::10, it will fail, but if the address is assigned to your local computer thus:
netsh interface ipv6 add address "loopback" fe80::10
if you ping6 fe80::10, the ping will succeed because your computer is now multihomed with a second IPv6 address. To remove this address, you can use the command:
netsh interface ipv6 delete address "loopback" fe80::10
As previously mentioned, the IPv6 routing table is generally populated from received advertisements from other routers. These advertisements contain information about the advertising router’s subnet and optional information such as the prefix information option and the route information option.
The prefix information option is described definitively in RFC 2461. It provides the receiving router with the address prefix from which the auto-configured addresses derive.
The route information option is specified in an Internet draft entitled “Default Router Preferences and More-Specific Routes.” This optional data contains prefix and routing information for subnets accessible from the advertising router. This provides a redundancy mechanism, such that if the router that sent the advertisement ever goes offline, it may still be possible to communicate with subnets behind that router if an alternative route exists.
A Windows XP machine will not send routing advertisements on the network by default, but it can be set to do so with the following command:
netsh interface ipv6 set interface <interface id>
forwarding=enabled advertise=enabledwhere the interface ID can be determined from the following command, under the Idx field:
Netsh interface ipv6 show interface
IPv6 will not replace IPv4 overnight. Instead, there will be a considerable period when both IPv6 and IPv4 will coexist on the Internet. In time, IPv4 will be phased out entirely. This transitional period is important for developers of mass-market software where the network infrastructure of the end-user can be one of several different hybrid systems.
IPv6 deployment will take place in a much more organized way than the MBONE project did. The ad hoc deployment of MBONE created islands of multicast supporting infrastructure and left entire countries with no access to multicast networks. With IPv6, networks that have not yet migrated to IPv6 will still be capable of transporting IPv6 data, once it is encapsulated within IPv4 packets.
The encapsulation of IPv6 data within IPv4 packets can take place using one of two mechanisms: the intrasite automatic tunnel addressing protocol (ISATAP) or 6to4. The crucial difference between these two systems is the IPv4 address that each uses to represent the destination. An IPv6 address consists of an interface and subnet identifier. With 6to4, this subnet identifier is created from a public IPv4 address, whereas ISATAP uses a local IPv4 address to create the subnet identifier. Regardless of the mechanism used, the IPv4 packet will contain enough information to determine the source and destination of the packet. Having said that, there will be designated pockets of the Internet that natively support IPv6, known as the 6bone. This region of the Internet will support more efficient and faster transfer of IPv6 data, but IPv6 accessibility will not be limited only to this region.
The 6to4 mechanism is an elegant solution to ferry IPv6 data across IPv4 networks. It is described definitively in RFC 3056. Although hosts employing 6to4 address assignment would not require any manual configuration, it is likely that 6to4-compliant routers will require some level of configuration.
6to4 generates a global IPv6 address from an IPv4 address by suffixing the IPv4 address with a global address prefix (2002 hex), appending the IPv4 address, and retaining the subnet and interface identifier. This creates an IPv6 address of the form:
2002 : HIGH IPv4 : LOW IPv4 : SUBNET : INTERFACE
where high IPv4 is the high-order 16 bits from the IPv4 address and low IPv4 is the low-order 16 bits from the IPv4 address. This type of address is not suited to multicast applications.
The high 64 bits of the 6to4 address (which includes the subnet) are used to provide routing information between 6to4-compliant routers. Routers advertise this route to other routers within the IPv6 intranet and also to 6to4 routers outside the network.
Any 6to4 network traffic that does not belong within the intranet is forwarded to a router on the border of the intranet. This data then has to be encapsulated into an IPv4 packet because non-IPv6-compliant routers would simply discard native IPv6 packets. The 6to4 router would extract the IPv4 address from the IPv6 address and use it in the header to direct the packet.
In Windows XP, the 6to4 service is included with the IPv6 protocol. This service can be administered from Administrative Tools→Services→6to4. This service automatically generates 6to4 addresses for all IPv4 addresses assigned to the local computer. It also provides a facility to encapsulate IPv6 packets with IPv4 headers when required and attempts to locate a 6to4 relay router on the Internet using a DNS query.
If ICS were enabled on that computer, as it would be with many home or small office networks, the computer will enable IPv6 forwarding on the private interface and broadcast router advertisements, such that any other IPv6 hosts on the network could communicate natively. This effectively configures that computer to become a 6to4 router.
Note
Technically, neither the ICS nor 6to4 service provides IPv4/IPv6 address translation, but for all practical purposes, it can be seen as such.
In situations where you cannot or do not want to run ICS on the server, it is possible to configure the machine as a 6to4 router without using ICS. In order to configure the computer as a 6to4 router, it must have a publicly accessible IPv4 address and must not have a 6to4 pseudointerface in its routing table. A 6to4 pseudointerface is created when a host computer receives a routing advertisement from an IPv6 or ISATAP router. This generates an entry in the routing table, prefixed 2002::/16 and pointing to a 6to4 relay router on the IPv4 Internet.
Enable forwarding and advertising on all interfaces connected to the Internet, and enable forwarding on the 6to4 pseudointerface using the following command (with the interface ID substituted accordingly):
netsh interface ipv6 set interface <interface id>
forwarding=enabled advertise=enabledAdd routes to the 6to4 pseudointerface using the following command (with interface ID, subnet ID, and the IPv4 address substituted accordingly):
Netsh interface ipv6 add route 2002:<High bytes IPv4>:<Low bytes IPv4>:<Subnet ID>::/64 <interface ID> publish=yes
The subnet ID is, by convention, the index of the interface being used, but it can be any two-byte hex number.
ISATAP serves much the same purpose as 6to4 in providing a means to transport IPv6 data over the existing IPv4 architecture. It has not gained the same level of support as 6to4, but it still remains a valid and usable technology. An ISATAP address uses the following form:
::0:5EFE:[IPv4 Address]
The ISATAP address can be combined with an IPv6 prefix, including 6to4 prefixes if required. Again, ISATAP is not suited to multicast applications.
On Windows XP, the ISATAP address for each local interface is automatically configured. This address enables ISATAP hosts to communicate over IPv4 within the same intranet. To allow communication over the Internet, the host must have previously received a router advertisement from the border router from the foreign network. Once this advertisement has been received, the host can then determine other ISATAP addresses from within that network.
ISATAP uses an IPv4 address to derive the interface ID. Because it defeats the purpose to have the uniqueness of an IPv6 address depend on the availability of a unique IPv4 address, it is possible to have two identical ISATAP interface IDs for two hosts in separate sites because they would both have different IPv6 addresses, thanks to the unique subnet ID.
To configure a computer as an ISATAP router, it must have at least two LAN connections, one of which is connected to the IPv6 network and another connected to the IPv4 network. The first step in configuring a Windows XP machine as an ISATAP router is to enable forwarding on all interfaces connected to the Internet and enable both forwarding and advertising on the automatic tunneling pseudointerface, using the following command (with the interface ID substituted accordingly):
netsh interface ipv6 set interface <interface id>
forwarding=enabled advertise=enabledAdd routes to the automatic tunneling pseudointerface using the following command (with interface ID, subnet ID, and the IPv4 address substituted accordingly):
Netsh interface ipv6 add route 2002:<High bytes IPv4>:<Low bytes IPv4>:<Subnet ID>::/64 <interface ID> publish=yes
Add a default route to the physical LAN interface using the following command (with interface ID and the IPv6 address substituted accordingly):
Netsh interface ipv6 add route ::/0 <interface id> nexthop=<IPv6> publish=yes
ISATAP hosts use DNS to discover the ISATAP router by resolving the name ISATAP (Windows Server 2003) or _ISATAP (Windows XP). It is therefore necessary either to name the router computer ISATAP or to enter the record into the local DNS server(s). If this cannot be done, you must run the following command on all ISATAP hosts and the router computer itself:
Netsh interface ipv6 isatap set state router=<IPv4 Address>6over4 and 6to4 are similar protocols, but they are different in some significant respects. They are both used to ferry IPv6 data over IPv4 networks; however, 6over4 is designed for use in multicast environments, unlike 6to4 or ISATAP. 6over4 is defined definitively in RFC 2529.
6over4 is disabled by default on Windows XP, but it can be enabled with the command line (substituting the IPv4 address with that of the local computer):
netsh interface ipv6 add 6over4tunnel "6over4" <ipv4 address>
From this point, 6over4 can be configured in an identical way to ISATAP; however, it should be noted that the underlying IPv4 network must already support multicasting for IPv6 multicasting to be functional.
IPv6 is supported in version 1.1 of .NET. Migrating code to support IPv6 isn’t difficult. All that is required is a new parameter to be passed to the socket constructor AddressFamily.InterNetworkV6. Locally bound endpoints are created differently, too, using IPAddress.IPv6Any as the loop-back address.
Support for IPv6 in .NET 1.1 is disabled by default, so before you can begin programming, you need to adjust the configuration for .NET. Using a text editor, open the machine.config file, located in the C:WINDOWSMicrosoft.NETFrameworkv1.1.4322 folder. Replace the XML <!--<ipv6 enabled="false "/> --> with <ipv6 enabled="true"/>.
The following example demonstrates how to transmit some text via TCP/IPv6. There are two parts to this example: a client and a server. We shall start by first implementing the server. Create a new project in Visual Studio .NET. Draw a textbox on the form, named tbMessages, with multiline set to true.
First, add a public variable named port. This variable will hold the port number on which the server will listen:
C#
public class Form1 : System.Windows.Forms.Form
{
public static int port;Public Class Form1
Inherits System.Windows.Forms.Form
Public Shared port As IntegerThis server is dual threaded, where the main thread is used to keep the UI responsive, and a secondary “worker” thread is used to accept and handle incoming connections. This server would be incapable of handling more than one connection at a time. In the form Load event, the port is set to 9999, and the worker thread is started.
C#
private void Form1_Load(object sender, System.EventArgs e)
{
port = 9999;
Thread thdListener = new Thread(new ThreadStart(listener));
thdListener.Start();
}VB.NET
Private Sub Form1_Load(ByVal sender As System.Object, _
ByVal e As System.EventArgs) Handles MyBase.Load
port = 9999
Dim thdListener As Thread = New Thread( _
New ThreadStart(AddressOf listener))
thdListener.Start()
End SubThe Listener function works by binding a socket to the IPv6 loopback address on port 9999. It uses Socket.SupportsIPv6 to determine if the .NET run time is capable of handling IPv6. If so, the socket is bound to the address and begins listening. Once a connection is received, a new socket is created, which will read data from the network in 256-byte chunks. It outputs all data to the screen immediately. Once there is no more data, both sockets close, and the server will no longer accept connections.
C#
public void listener()
{
Socket sckListener;
Socket clientSocket;
IPEndPoint ipepLocal =
new IPEndPoint(IPAddress.IPv6Any, port);
byte[] RecvBytes = new byte[Byte.MaxValue];
Int32 bytes;
if(!Socket.SupportsIPv6)
{
MessageBox.Show("Cannot support IPv6");
return;
}
sckListener = new Socket(
AddressFamily.InterNetworkV6, SocketType.Stream,
ProtocolType.Tcp
);
sckListener.Bind(ipepLocal);
sckListener.Listen(0);
clientSocket = sckListener.Accept();
while(true)
{
bytes = clientSocket.Receive(RecvBytes);
if (bytes<=0) break;
tbMessages.Text += Encoding.ASCII.GetString(RecvBytes);
}
tbMessages.Text += "
";
clientSocket.Close();
sckListener.Close();
}Public Sub listener()
Dim sckListener As Socket
Dim clientSocket As Socket
Dim ipepLocal As IPEndPoint = New _
IPEndPoint(IPAddress.IPv6Any, port)
Dim RecvBytes() As Byte = New Byte(Byte.MaxValue) {}
Dim bytes As Int32
If (Not Socket.SupportsIPv6) Then
MessageBox.Show("Cannot support IPv6")
Return
End If
sckListener = New Socket( _
AddressFamily.InterNetworkV6, SocketType.Stream, _
ProtocolType.Tcp)
sckListener.Bind(ipepLocal)
sckListener.Listen(0)
clientSocket = sckListener.Accept()
Do
bytes = clientSocket.Receive(RecvBytes)
If bytes <= 0 Then Exit Do
tbMessages.Text += Encoding.ASCII.GetString(RecvBytes)
Loop
tbMessages.Text += vbCrLf
clientSocket.Close()
sckListener.Close()
End SubYou will also need to add the following namespaces to your code:
C#
using System.Net; using System.Net.Sockets; using System.Threading; using System.Text;
VB.NET
Imports System.Net Imports System.Net.Sockets Imports System.Threading Imports System.Text
Once the server is written, let us turn our attention to implementing the client. Open a new project in Visual Studio .NET. Draw two textboxes on the form: tbIPv6Addr and tbMessage. Then add a button named btnSend.
First, add a public variable named port. This variable will hold the port number, on which the server will listen:
C#
public class Form1 : System.Windows.Forms.Form
{
public static int port;Public Class Form1
Inherits System.Windows.Forms.Form
Public Shared port As IntegerAs in the server, the port needs to be set to 9999. This is set from within the form Load event.
C#
private void Form1_Load(object sender, System.EventArgs e)
{
port = 9999;
}VB.NET
Private Sub Form1_Load(ByVal sender As System.Object, _ ByVal e As System.EventArgs) Handles MyBase.Load port = 9999 End Sub
Now, double-click on the Send button, and enter the code below. This works by creating a socket with an address type of IPv6. This socket establishes a connection with the remote server in the normal way and transfers the string by converting it to a byte array.
C#
private void btnSend_Click(object sender, System.EventArgs e)
{
byte[] msg;
if(!Socket.SupportsIPv6)
{
MessageBox.Show("Cannot support IPv6");
return;
}
IPAddress ipAddrv6 = IPAddress.Parse(tbIPv6Addr.Text);
IPEndPoint ipEPv6 = new IPEndPoint(ipAddrv6, port);
Socket socket = new Socket(
AddressFamily.InterNetworkV6, SocketType.Stream,
ProtocolType.Tcp
);
socket.Connect(ipEPv6);
msg = Encoding.ASCII.GetBytes(tbMessage.Text);
socket.Send(msg);
socket.Close();
}Private Sub btnSend_Click(ByVal sender As System.Object, _
ByVal e As System.EventArgs) Handles btnSend.Click
Dim msg() As Byte
If Not Socket.SupportsIPv6 Then
MessageBox.Show("Cannot support IPv6")
Return
End If
Dim ipAddrv6 As IPAddress = _
IPAddress.Parse(tbIPv6Addr.Text)
Dim ipEPv6 As IPEndPoint = New IPEndPoint(ipAddrv6, port)
Dim ipv6Socket As Socket
ipv6Socket = New Socket( _
AddressFamily.InterNetworkV6, SocketType.Stream, _
ProtocolType.Tcp)
ipv6Socket.Connect(ipEPv6)
msg = Encoding.ASCII.GetBytes(tbMessage.Text)
ipv6Socket.Send(msg)
ipv6Socket.Close()
End SubYou will also need to add the following namespaces to your code:
C#
using System.Net; using System.Net.Sockets; using System.Text;
VB.NET
Imports System.Net Imports System.Net.Sockets Imports System.Text
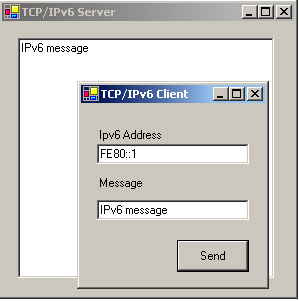
To test this example, run the server from Visual Studio .NET. Find the IPv6 address of the server computer, using the Ipv6 if command. If you are using only one computer, then this is FE80::1. Now run the client program, enter the server IPv6 address into the box provided, and type a message into the second box. Press Send, and the message should appear in the text window of the server, as depicted in Figure 16.7.
IPv6 compliance may not be a big issue today, but in the near future it will be key and may be an absolute requirement in certain software products. This chapter should provide enough information for you to set up an experimental IPv6 network and provide a test platform for IPv6 compliance in software. It should also give insight into how to upgrade legacy protocols without alienating existing clients.
IPv6 may be a headache for network administrators, but it is a gold mine of opportunity for developers. When IPv4 begins to make its exit from the Internet, it is almost certain that people will start looking at other protocols. FTP, for instance, is incompatible with IPv6 because of IPv4-dependent features of the protocol, such as the PASV command. Another example is X.25, which currently forms the backbone of financial institutions, but has no native mechanism to tunnel over IPv6, so it may also be replaced. The list is virtually endless.
The final chapter deals with two of the technologies introduced with .NET that have been heralded as a revolution in distributed computing: remoting and Web services.