CHAPTER 5
Designing a Network for AV Systems
In this chapter, you will learn about
• Conducting a needs analysis
• Physical and logical network design
• Ensuring network security
• Ensuring quality of service
• Network implementation
No two customers are the same. As an AV professional, you know this. Every customer has a different set of communication needs. They have different policies regarding site access. And each has their own set of security requirements. Physical spaces are unique, too, with their own acoustic properties, lighting, ambient noise levels, and more. As a result, no two AV systems are the same. This is true of networked AV systems as well. That’s because all customers have unique networking needs. Their networks, including their physical and logical topology, architecture, and policies, are tailored to meet those needs.
This chapter explores how new networks are designed and implemented. If your AV systems are going to be allowed to join the network, you must understand a customer’s networking needs and how they determine the way the network functions. That way you can make sure your gear operates safely within the network design, and you’ll be able to demonstrate to your IT stakeholders that you understand their needs.
Keep in mind that this chapter includes a broad overview of the network design process, but comprehensive training on how to design an Ethernet or TCP/IP network is beyond the scope of this book. Network design training is offered as a four-year program of study at many institutes of higher learning. Networking equipment manufacturers, such as Cisco Systems and Juniper Networks, also offer manufacturer-specific network design training and certification.
The Needs Analysis
Both AV and IT professionals struggle to balance system security and availability. In order to make a networked AV system as useful a communication tool as possible, lots of users need to be able to access it. On the other hand, in order to keep the
network safe from viruses and intruders, access may have to be limited to the people who really need it.
All those involved in a system design must be aware that AV devices, if managed incorrectly, can make the network vulnerable to attack or clog network pipes with too much data. At the same time, everyone must work together to ensure that users have the best media experience possible. In the end there is common ground between security and availability, and it is defined by customer needs.
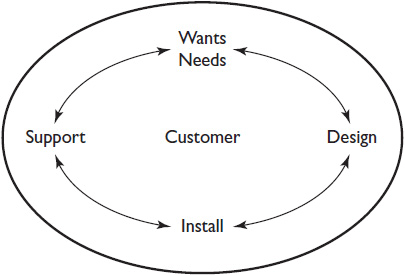
If you’ve ever taken an InfoComm International training course, you’re probably familiar with the illustration shown here. It represents both the flow of an AV project and the customer-centric nature of the AV industry. The outer ring divides a typical AV project into four parts:
• First, the customer’s wants and needs are identified.
• Next, the design package is created, detailing what the system will include, how it will be built, and when the system will be complete.
• Next, the system is installed, set up, and verified.
• Finally, the system receives ongoing support.
These activities form a cycle in which each activity supports the next activity—even system support. The support records should illuminate system shortcomings and usage patterns, making the next needs analysis process easier. The goal is for each stage to be completed and documented so thoroughly that the people involved in the next stage don’t need to go back and ask questions. The needs analysis documentation should be so good that the designer doesn’t need to ask the salesperson questions; the design documentation should be so good that the installer doesn’t need to ask the designer questions; and so forth.
The customer is at the center of these activities. The system is only successful if the customer’s needs are met. “Customer” is a fluid term, though. It applies to the system end users and the people paying for the systems. It also applies to everyone who depends on you to do your job correctly. This includes your colleagues and members of allied trades affected by the AV system.
Network design conforms to the same cycle. Like AV design, network design is customer driven. Stakeholder buy-in must be sought early and maintained throughout the design and installation process. This is achieved through open communication with the customer—just like in AV. The design team documents every aspect of the system. The design and installation teams give the customer and other stakeholders regular status reports. Any issues that arise are documented and addressed through a system of requests for information (RFIs), change requests (CRs), and change orders (COs). Even though the cultures of AV and IT are different, their design processes are very similar.
The Network Needs Analysis
The first step in planning a new network is a needs analysis, sometimes known as a needs assessment (NA). As illustrated in Figure 5-1, the customer’s needs determine the applications, tasks, and functions and features of the system. You may be accustomed to needs analysis as it’s done in the AV industry. Now put yourself in the shoes of a network engineer. A networking needs analysis should not only reveal how the customer will use the network, it should also help you set priorities for and make decisions about the network’s design. The process has three phases:
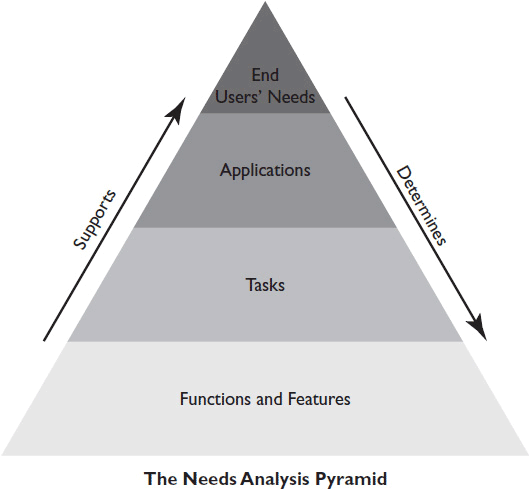
Figure 5-1 In the classic needs analysis pyramid, the customer’s needs determine applications, tasks, and system functions.
• Pre-assessment—the exploration phase
• Assessment—the data-gathering phase
• Post-assessment—the utilization phase
The first two phases must be completed and documented before design can begin.
Pre-assessment
During the pre-assessment phase, the first question to ask is, “Do you need a network to support your business objectives?” Then, “What business objectives will the network support?”
These questions may seem unnecessary. After all, today networks are as crucial to operating a business as oxygen is to live. But they are important questions because they reveal what the customer needs the network to do—and how quickly and reliably it must be done. Some business applications require a lot more resources, bandwidth, and reliability than others.
Once it’s established that the customer needs a new network, you must determine what limitations and regulations it will be subject to. What authorities will have jurisdiction over this new network? Does the customer have internal policies and standards you need to follow? Are there any laws or regulations the network must adhere to? For example, there may be laws regarding the security of networks carrying certain types of data, such as financial records, health records, or government-classified information. Familiarize yourself with all authorities having jurisdiction (AHJs) over networking in your customer’s geographical region. Work with your customer to identify any AHJs that apply to the customer’s specific field.
Assessment
During the assessment phase, you’ll work with people throughout the customer organization to discover how the network will be designed, built, used, and managed. In the assessment phase, you conduct a gap analysis to determine the scope of the project. First, you determine what state the customer’s network—if any—is in now. Once that baseline is established, you determine what state the customer needs the network to be in once the project is complete.
If the customer organization is large or complex, you’ll need to work with representatives of every business unit that will use the network. The marketing department has a different mission than the research and development team. How will each unit use the network to meet its business objectives? How does the organization as a whole prioritize the mission of each unit? You can collect this data through surveys, interviews, and focus groups.
Post-assessment
The final phase of the needs analysis—post-assessment—takes place after the project is completed and the customer is using the network. This is where you gauge the success of the project. Is the network successfully supporting the users’ needs?
During this phase, you can employ some of the same research methods that you used during the assessment phase—surveys, interviews, and focus groups—to gauge customer satisfaction. You should also gather hard data during this phase: How much is the customer using the network? Is there enough bandwidth to accomplish the required tasks? How much downtime does the network experience? Is the network performing as you expected and promised it would?
The post-assessment phase allows you to address any lingering issues that arise after the new network is implemented. It also helps you improve your needs analysis procedures for next time by showing you where your assumptions and decisions were right and wrong.
The Customer Is Not Always Right
Arthur C. Clarke wrote, “Any sufficiently advanced technology is indistinguishable from magic.” As a professional who designs, builds, or maintains modern networks and networked AV systems, you are the magician. You provide the everyday magic. Your customers depend on these systems, but they may not really understand how they work. To them, they’re magic.
Unfortunately, like magic, customers sometimes believe that networks and networked systems can do anything, without any extra work or cost. Why can’t the CEO control the videoconferencing system from her iPad? Why can’t she hold a high-definition multipoint conference with colleagues in Asia, Australia, and Europe? Why can’t everyone at all the branch offices watch a live video stream of a major announcement from headquarters at their desktops? And if they can, why should it cost any extra?
The IT industry has recognized for a long time that the customer is not always right. The needs analysis process is not about discovering your customer’s wish list or imaginary perfect system. It’s about determining what the customer actually needs the system to do in order to meet business objectives. This may mean scaling back customer expectations that can’t be met within the current budget or project scope. Every network has limitations. During the needs analysis process, it’s very important to establish what the network won’t do as well as what it will. What traffic is the network not designed to handle? What user behaviors might cause it to fail? What kind of attacks is the network vulnerable to?
Your customers may decide they can’t live with some risks or limitations, and open their wallets to pay for a more comprehensive—and expensive—solution. Other limitations will remain in place. You must document the fact that the customer knows about and agrees to these limitations. Then, if the network is ever pushed to its limits, it’s a documented opportunity for future expansion of the project—not a mistake or failure on your part.
Customer Readiness
Creating a network requires time, budget, and resources, and determining customer readiness is a major factor in estimating the time, money, and equipment needed to implement a new network. You need to find out how ready the customer is to support the new network; in doing so, you will also reveal what the customer can do in-house and what ongoing services they might need to contract for—preferably from you.
Questions regarding network readiness span design, installation, and network management. Here is a sampling:
• Has the customer allocated enough money to pay for the required personnel and equipment needed for design, installation, and management?
• Are network and security engineers available on the customer’s staff? How about on your staff?
• Does the customer have adequate in-house IT management and support staff? If not, can you offer management as a service?
• Do you have access to the network design tools you need?
• Does the customer already own any of the equipment needed for implementation, or will it all have to be purchased?
• Is the customer prepared to replace equipment in a timely fashion? Will replacement gear be kept in stock or purchased as needed?
Physical and Logical Design
Once the needs analysis is complete, the network and security engineers can move on to network design. As with the needs analysis process, there are many parallels between the broad considerations of AV and network design, such as
• What applications will be included?
• Where will equipment be physically located?
• What infrastructure is required to establish communication between devices?
• What are the electrical and HVAC requirements?
Of course, AV design has many unique considerations, specific to the types of systems being deployed. So does IT. When designing a new network, you must also consider logical topology, network architecture, and a host of other network-specific concerns. In the end, although there are elements common to all networks—nodes and connections, switches and routers—every individual network is unique.
AV designers often design systems in a compartmentalized fashion, first considering display size and viewer position, then audio system design, and so forth. They know, though, that AV design is also iterative—each design decision affects other parts of the system. You may have to make visual system design changes based on subsequent audio system design decisions, and vice versa, until the whole system functions together in harmony.
Network design can be approached in much the same way. There are several categories of design concerns that must be examined individually but also viewed interdependently. Each part impacts the others and must be adjusted until you achieve a harmonious whole.
Physical Topology
One of the first considerations in designing a new network is topology—both physical and logical. For a preview, see Figure 5-2. Where will equipment be located? What type of cabling will you use? How will your networking devices connect to each other and to the outside world?
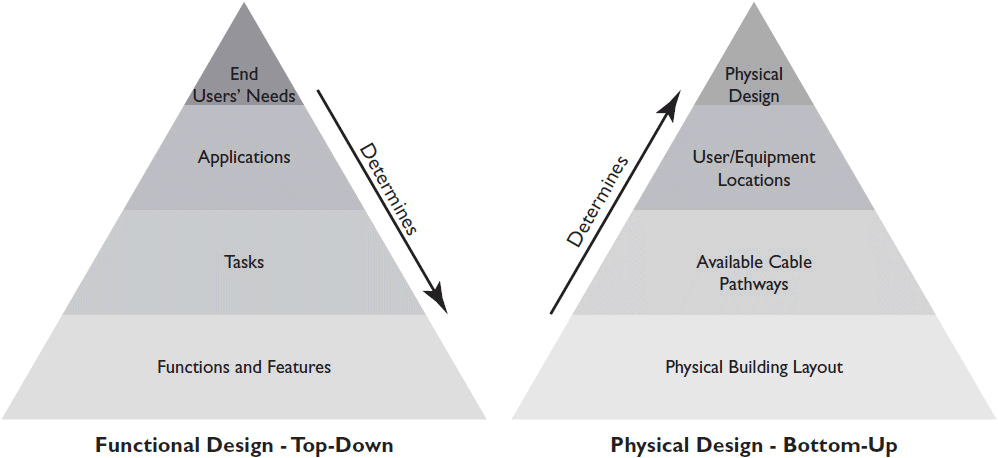
Figure 5-2 The difference between functional and physical design.
The functional design of the network—what it is designed to do—is determined by top-down design. You need to ask things like
• What are the users’ needs?
• What applications support those needs?
• What tasks are included in those applications?
• What equipment is required to support those tasks?
Conversely, a network’s physical structure is designed through a bottom-up approach. In this case, you need to ask
• What are the physical characteristics of the building(s) that will house network nodes?
• What cable pathways are available between equipment sites?
• Where will users and network devices be located?
• How far apart are the network nodes?
The physical layout of the network will depend largely on architectural constraints. You will also have to comply with local building codes and safety requirements. Whenever you’re planning any type of infrastructure, always consult your AHJ(s).
Locating wireless access points (WAPs) is also part of designing the physical topology. You need to ensure that you have enough WAPs to provide access to the estimated number of wireless devices and volume of traffic. You also want to ensure that the WAPs’ transmission lobes cover the required area without giving unwanted access to outsiders. You’ll need in-depth knowledge of wave propagation to plan optimal positions for WAPs.
Remember, though, that those wireless access points still require physical connectivity. Also, many networked AV applications, including videoconferencing and high-quality networked audio, require physical connectivity. Although modern users are accustomed to streaming videos wirelessly from the Internet, video streaming works better with the higher bandwidth of a physical cable.
As with every aspect of design, IT or AV, documentation is important. You should document the logical topology of the network using network design tools, such as Microsoft Visio or Dia, the latter being an open-source diagramming program inspired by the former. Physical device locations should be documented in system drawings, including floor plans and rack elevations. Cable routes may be documented in a database or even a simple table. At the very least, you should label each cable and document what nodes it connects to at each end.
Planning Structured Cabling
The most complex aspect of planning the physical topology of a network is plotting cable runs. This is where bottom-up physical design meets top-down functional design. The physical layout of the building will determine how long the cable runs must be (see Figure 5-3). The users’ needs will determine how much bandwidth they need on each connection. Both of these will inform the physical media type used to connect devices: optical fiber, twisted-pair copper cabling, wireless RF, and so on.
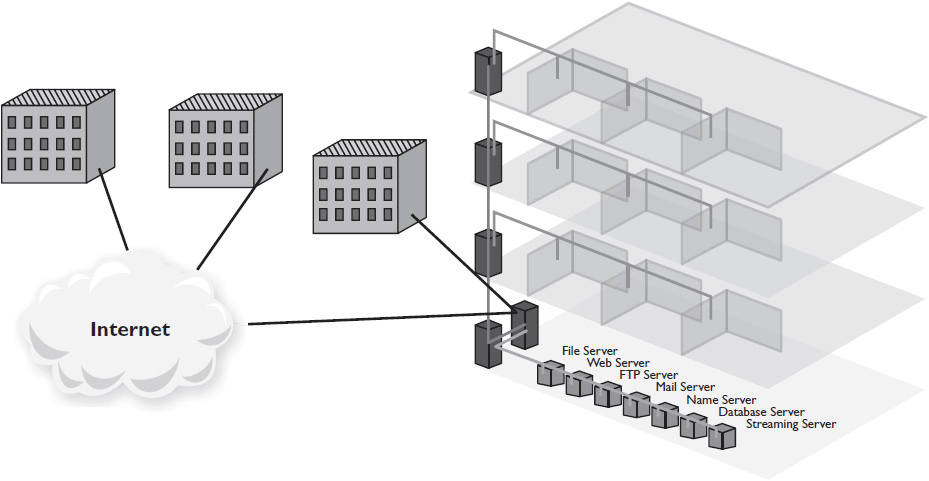
Figure 5-3 Planning for structured cabling based on physical layout.
Logical topology also intersects with physical topology. Unless you’re implementing a fully meshed LAN, every device does not physically connect to every other device. The network’s logical topology will help you determine which cables you need and which you don’t. However, it’s always wise to project into the future during your planning. For example, it can be a good idea to pull additional cable to each planned endpoint to allow for future growth. When possible, these cables should be longer than necessary for the planned endpoint, allowing you to extend them to a new adjacent endpoint if the need arises. These long reserve cables help you create a flexible, scalable network. For more on network cabling and wireless connection technologies—the Physical Layer of a network—you can review Chapter 2.
Organizational Structure
Many factors determine the design of a network’s logical topology. You want to eliminate or reduce single points of failure. You want to make sure each part of the network has adequate bandwidth. You want to make communication between certain nodes fast and easy by keeping them within the same local area network (LAN). You want to control access to other nodes by isolating them on their own LAN. You want to manage carefully what outside devices, if any, are allowed to exchange data with nodes on the LAN. So the question is, How do you determine the best way to divide and organize a new network?
Understanding the structure of your customer’s organization can help you design the logical topology. Organizations are typically divided into logical business units, such as marketing, finance, and human resources (see Figure 5-4). It’s often a good idea to mirror this logical separation in the network design, creating a different LAN—or virtual LAN—for each business unit. This can improve productivity by making intradepartmental communication as efficient as possible. It can also help you separate and protect devices that hold sensitive data, such as human resources records, financial data, or classified research.
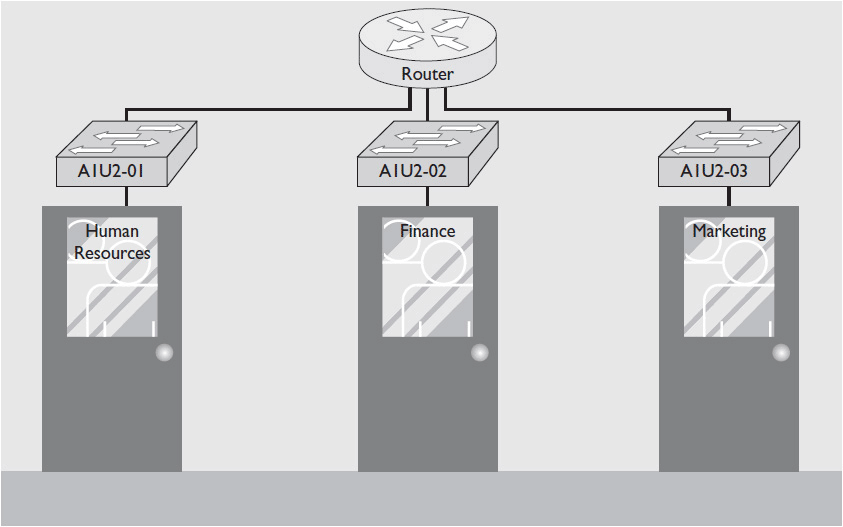
Figure 5-4 A company’s organizational structure can help determine a network’s logical topology.
You should assign each business unit’s LAN its own naming convention and logical address range. This simplifies maintenance and troubleshooting. When you use consistent naming conventions and addresses for each LAN, it’s easier to trace problems to their sources.
 TIP Even though it makes sense to mirror network divisions and business unit divisions, you shouldn’t mirror network names and business unit names. Leading practices suggest using abstract names instead. For example, you might be tempted to call an organization’s research and development network R&D_001. But everyone knows what R&D stands for, therefore that LAN might be a target for corporate espionage. It’s better to give the LAN an abstract name, such as A1U2_001, and then keep track of what the name stands for in the network documentation. You can then use a spreadsheet to map abstract names to the business units or groups of devices they represent.
TIP Even though it makes sense to mirror network divisions and business unit divisions, you shouldn’t mirror network names and business unit names. Leading practices suggest using abstract names instead. For example, you might be tempted to call an organization’s research and development network R&D_001. But everyone knows what R&D stands for, therefore that LAN might be a target for corporate espionage. It’s better to give the LAN an abstract name, such as A1U2_001, and then keep track of what the name stands for in the network documentation. You can then use a spreadsheet to map abstract names to the business units or groups of devices they represent.
Electrical and HVAC Considerations
When you determine where your network resources will be physically stored, you’ll need to make sure that space is prepared to house those resources. A data center or telecommunications closet has a lot in common with an AV rack. In either case, you’re housing a lot of delicate electronics in one place. These devices require power to operate and produce a lot of heat when in use. They must have a stable, cool environment to run at peak efficiency. Network engineers, like AV designers, need to work with members of the electrical and HVAC allied trades to ensure that electrical and cooling requirements are met.
A qualified electrical engineer should be consulted to determine the electrical requirements for telecommunication closets and data centers. Adequate power and redundant power sources are the primary concern when addressing electrical requirements for a networked system.
A qualified HVAC engineer should be consulted to determine the cooling requirements for the telecommunication closets and data centers. Heat dissipation and humidity are the primary concern when addressing cooling requirements for a networked system.
The electrical and HVAC engineers must work together to achieve an appropriate balance of power and cooling requirements. This is critical because cooling and humidity control equipment will have additional power requirements beyond the network equipment.
 NOTE Many manufacturers now offer energy-efficient, “green” network devices. Green devices typically cost more than less energy-efficient competitors. The cost of purchasing these more expensive devices should be measured against the long-term energy savings. Up-front investment may save your customer money over the long term. Your customer may also have a policy of using green technologies when possible, regardless of cost.
NOTE Many manufacturers now offer energy-efficient, “green” network devices. Green devices typically cost more than less energy-efficient competitors. The cost of purchasing these more expensive devices should be measured against the long-term energy savings. Up-front investment may save your customer money over the long term. Your customer may also have a policy of using green technologies when possible, regardless of cost.
Ensuring Security
As any network is built or expanded, security is a top concern. A network creates exposure. It gives users the ability to access one device from another, or to tap into organizational resources. But increased availability and efficiency have a price: potential exposure. Throughout the network design process, network and security engineers will analyze potential risks. Typically, they use a risk-management framework (RMF) to determine which risks are acceptable and which must be guarded against.
There are risks to every system and project. And every jobsite implements security measures to mitigate risk. Failure to identify risks and appropriate security measures will cost time, money, and frustration.
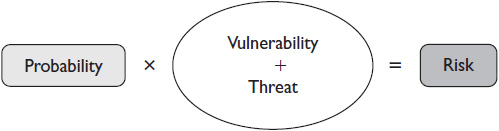
A risk is the potential for a problem when there is a chance that some threat will exploit a weakness in your system. A risk involves three factors: vulnerability, threat, and probability or likelihood. Vulnerability is the specific weakness in a system; a threat is an entity that might exploit the vulnerability. Any risk can be described as “there is X likelihood that Y threat may take advantage of Z vulnerability.” The likelihood of a risk must be balanced against its associated cost, or consequence, if it does happen.
Risk-Management Frameworks
There are many available risk-management frameworks, several of which are free. The US National Institute of Standards and Technology (NIST) publishes an extensive, free suite of computer security guidelines, the Special Publication 800 series (SP 800). SP 800-37 deals specifically with applying a risk-management framework to IT systems.
Control Objectives for Information and Related Technology (COBIT), a family of internationally recognized IT governance publications developed by ISACA (previously the Information Systems Audit and Control Association), also provides a risk-management framework. COBIT 5, the most recent version, incorporates the framework known as Risk IT, which you can download from the ISACAwebsite (isaca.org).
There are even risk-management standards. ISO/IEC 25005:2011, a standard from the International Organization for Standardization and the International Electrotechnical Commission, offers guidelines for ensuring information security through risk management.
At the end of the day, you should always use whatever risk-management framework your customer prefers.
Mitigation
Once you’ve identified the risks your system presents, you need to figure out how to address them. The next step is to research best practices for mitigating the vulnerabilities in the system. Mitigation is an action taken to lessen or eliminate the impact of a risk.
For networked systems, common ways of mitigating security risks include
• Changing the default passwords on equipment so unauthorized users cannot access them
• Turning off unused features on servers
• Setting switches and routers to only allow traffic from specific ports or protocols
Unexpected risks will require unexpected mitigation. Set aside a contingency reserve of funds to protect your schedule and final deliverables.
Risk Analysis
No matter how much time and money you put into it, a system will always present residual risk and vulnerability. When faced with risk, there are three things you can do about it:
• Mitigate the risk.
• Accept it and do nothing.
• Obtain a formal exception when mitigation is deemed too costly.
The fact is, you’ll probably have to do all three to deal with every risk associated with a project. You know you can’t fix everything, all mitigation comes at a cost, and all projects have a finite budget. The risk-analysis process should reveal which risks you should prioritize.
Risk analysis is really a cost-benefit analysis. A risk will have an impact if it occurs. The mitigation that prevents that risk should cost less than the impact. Therefore, you want to prioritize risks that have a high probability of occurring and a significant cost of impact.
There are many methods of analyzing risk. Start by creating a document that records all the risks that a system faces, assigning values for vulnerability and probability. If you can chart a risk in the upper left corner of the matrix in Figure 5-5, then it is a high priority and should be mitigated at the earliest opportunity.
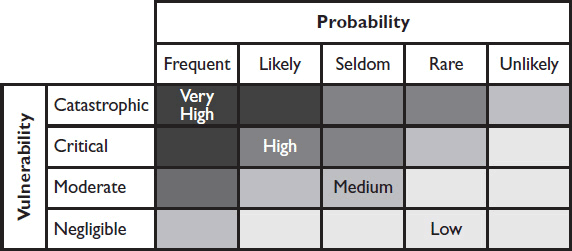
Figure 5-5 A sample risk matrix.
There are many names for this type of document, such as risk register, risk roster, or risk matrix. Some matrices are simple best estimates, while others are complex computer models. If your customer has a method of risk analysis, or any other guidelines, use them.
Confidentiality, Integrity, and Availability
Your customers’ tolerance for risk always depends on what kind of data is on the network. Some data must be kept secure, even if that makes it difficult to access. Other data should always be accessible, even if that means possibly exposing it to outsiders. During the network design phase, network engineers work with stakeholders to discover the confidentiality, integrity, and availability (CIA) requirements of each type of network traffic. The CIA requirements form the foundation of the network security requirements.
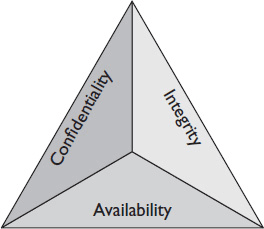
When you consider how important data is to your customer, you must also consider what makes it important. Is it important that the data be kept confidential? Is it important that the data be preserved without errors? Is it important that your customer always have access to the data? Balancing these three concerns is known as the CIA triad.
• Confidentiality addresses who is allowed to access information. The level of confidentiality will generally correspond to a protection plan for the information. Should the information be password locked? Can the information be stored on a desktop machine, or does it need to be a secure location?
• Integrity defines who is allowed to alter data or information systems. For example, restricting editing rights protects the fidelity of information. Do you think that CNN allows just anyone who works for them to edit the scrolling news at the bottom of the screen? Can you install any program you want on your computer at work, or do you need to seek permission from the IT department? The answers to questions like these speak to a company’s stance on data integrity.
• Availability defines how tolerant people will be if they can’t access their information. Can you tolerate an email outage at work? What about when closing a deal?
In most projects, you’ll need to prioritize two of these, depending on the preferences of your customer. No security system is perfect. Each organization weighs threats differently. Some organizations don’t care about keeping secrets as long as their files are safe and accessible. Others can tolerate downtime if it means keeping their data secure. Typically, you will have to pick which two of the three components of the CIA triad are most important to protect.
Building security into the network from the outset will reduce long-term cost and create a more secure network. In considering security, it is important to include protective devices such as firewalls to defend the network from outside intruders, as well as monitoring devices such as intrusion detection systems (IDSs). You should also address data-in-transit security through encryption. Consult with your customer’s IT staff to determine preferred methods of ensuring network security.
Ensuring Quality
Once users are accustomed to having access to a network, they become dependent on it. They feel the same about networked AV systems: the network can’t break; downtime can bring the whole company to a screeching halt. In reality, though, network components fail. One of the goals of network design is to ensure that device failures and other errors can’t bring the entire network down.
Fault Tolerance
The network’s ability to withstand errors is known as fault tolerance. The theory behind fault tolerance is to maintain network operations at an acceptable level regardless of subcomponent failures. Major network devices, such as firewalls, routers, and switches, create single points of failure. If they fail, entire portions of the network can fail or prevent access to important resources.
One way to avoid this is to install redundant network components to eliminate single points of failure. Some components, such as extra switches, you can keep on standby, sitting in boxes on a shelf. Other components, such as firewalls, should be configured for hot failover, which is to say, when one device fails, another device is already configured to take over. A hot failover device automatically assumes the functions of the failed device so that there is no interruption of service.
You should also plan for fault tolerance in the event of a power outage. Many network devices can be damaged or lose data if they’re powered down improperly. Consider using alternate power sources, such as uninterruptible power supplies (UPSs) and emergency generators, to maintain power to critical network devices.
Having extra connections in place also improves redundancy. As noted earlier, when pulling network cables or fiber, pull additional cables to each location.
 NOTE When designing a system and setting up redundancies for availability, the IT industry accepts as a best practice that no single point of failure should affect more than 20 users. At a minimum, your system should include redundancies to prevent loss of availability to groups greater than 20, even if availability is not a top priority.
NOTE When designing a system and setting up redundancies for availability, the IT industry accepts as a best practice that no single point of failure should affect more than 20 users. At a minimum, your system should include redundancies to prevent loss of availability to groups greater than 20, even if availability is not a top priority.
Quality of Service
As we’ve discussed, a network’s physical design is largely determined by the architecture of a building, while its functional design is determined by the needs analysis. What does the customer need the network to do? Usually, it’s more than one thing.
Customers send different kinds of data across their networks. Some of that traffic is more important than other traffic, and some is more time-sensitive. For example, do you care if an email arrives five seconds after you send it? Probably not. Do you care if people in a videoconference hear what you say five seconds after you say it? Definitely. The network needs a way to intelligently prioritize different types of traffic traveling on the same network. This is where quality of service (QoS) comes in.
QoS refers to any method of managing data traffic to preserve system usefulness and provide the best possible user experience. Typically, QoS refers to some combination of bandwidth allocation and data prioritization.
Many different network components have built-in QoS features. For example, videoconferencing codecs sometimes have built-in QoS features that allow various devices on the call to negotiate necessary bandwidth. Network management software may allow you to set QoS rules for particular users or domain names. During the network design stage, however, you’re mostly concerned with network-based QoS—that is, QoS policies that are configured directly on all network switches and routers.
Differentiated Service Categories
The underlying strategy of network-based QoS is to prioritize time-sensitive data traffic over other kinds of traffic. One way to accomplish this is to assign each type of traffic on the network a particular QoS differentiated service (DiffServ) class. Each class is handled differently by the network switches and routers, hence “differentiated service.”
Some classes are designed to preserve data without losing any packets (low loss). Some classes are designed to transport data as quickly as possible (low latency). Some classes prioritize data arriving in the exact order in which it was sent (low jitter). And the lowest-priority class (best effort) is data that will arrive when and how it arrives, with no guarantees of integrity or timeliness.
Each networked application your customer uses is assigned a DiffServ class on the network routers and switches. When traffic enters the network, these devices automatically detect which application it comes from and tag it with a DiffServ service class. The DiffServ service class then defines how the network devices prioritize the traffic.
There are ten categories of DiffServ service classes defined in the IETF standard RFC 4594. These classes are divided into four application categories. Figure 5-6 shows the ten classes and four application categories.
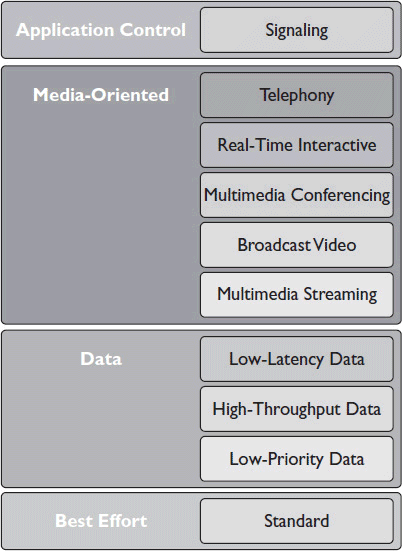
Figure 5-6 The ten categories of DiffServ classes.
Here is a quick description of the ten service classes:
1. The signaling service class is for traffic that controls applications or user endpoints. For example, signals that set up and terminate a connection between conference call endpoints would belong in this class.
2. The telephony service class is intended for VoIP traffic. It can be used for any traffic that transmits at a constant rate and requires very low latency.
3. The real-time interactive service class is for interactive applications that transmit at a variable rate and require low jitter and loss and very low delay. Examples include interactive gaming and some types of videoconferencing.
4. The multimedia conferencing service class is for conferencing solutions that can dynamically reduce their transmission rates if they detect congestion. If a conferencing class can’t detect and adapt to network congestion, the real-time interactive class should be used instead.
5. The broadcast video service class is for inelastic, noninteractive media—that is, media streams that can’t change their transmission rate based on network congestion. This class is used for live-events AV streaming as well as broadcast video.
6. The multimedia streaming service class is for noninteractive streaming media that can detect network congestion and/or packet loss and respond by reducing its transmission rate. This class is used for video-on-demand services—video that is stored before it is sent and buffered when it is received to compensate for any variation in transmission rate.
7. The low-latency data service class is for applications that require low latency, where data arrives in big, short-lived bursts.
8. The high-throughput data service class is for longer, high-volume traffic flows. It’s used by applications that store data and then forward it, like FTP and email.
9. The low-priority data service class is used for any applications that can tolerate long interruptions. This is for data you don’t care about.
10. The standard service class provides best-effort delivery. Any applications that are not specifically assigned to another class fall into the standard class.
Most organizations will not use all of these categories. Also, each organization will prioritize the DiffServ classes they use differently. For example, it’s generally considered best practice to assign Voice over Internet Protocol (VoIP) telephony the highest priority. VoIP traffic is very susceptible to loss and latency. A little of either can destroy call quality. However, a stockbroker might prefer poor VoIP quality to a tiny delay in a stock ticker feed. Table 5-1 spells out each class’s tolerance for loss, latency, and jitter.
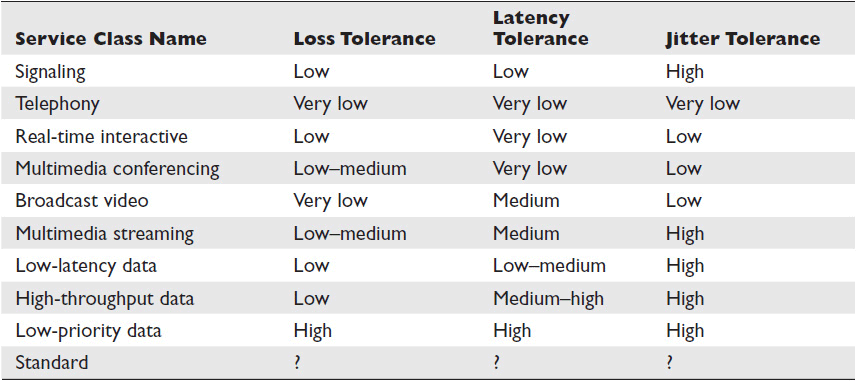
Table 5-1 DiffServ Classes and Tolerance Levels for Loss, Latency, and Jitter
Implementation
Once the network’s design is complete, it must be implemented according to plan. A nonnetworked organization transitioning to a networked organization will probably lack the capabilities to fully implement and configure every network component. Therefore, portions of the implementation will be outsourced, such as pulling cable, wiring the telecommunication closets, and configuring critical network components.
Developing a Timeline
With so many parties contributing to network implementation, it’s critical to adhere to a shared timeline. Timelines are critical to monitoring the progress of the implementation and keeping it on track and within budget. Timelines help establish priorities and orchestrate task implementation order. Many of the tasks associated with designing a network can be conducted simultaneously.
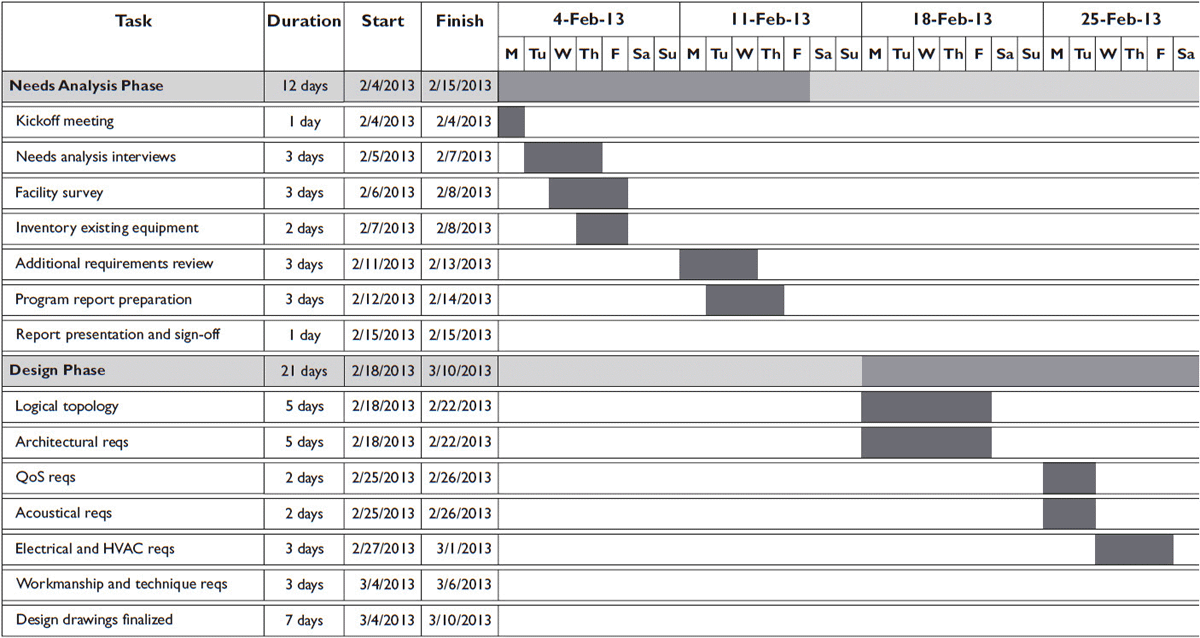
A Gantt chart (see Figure 5-7) is used to track resources and establish timelines. Commercial products such as Microsoft Project, or open-source programs such as Gantt Project, are perfect for managing projects. The Gantt chart provides a work breakdown structure tied to a project schedule.
Training
Training is critical to the long-term success of maintaining a network. At a minimum, all users should be trained in security awareness, basic network operation (e.g., account login, file sharing, and network resource usage), and policy awareness. This basic training should become part of the organizational annual refresher training and part of the employment process. Training can be conducted in-house if the organization has a professional, knowledgeable staff. Otherwise, training should be outsourced to a qualified agency.
Network engineers, system administrators, and security engineers should receive additional and ongoing training to support changes in technology.
Documentation
The key to successful implementation of a new network is detailed planning. Good risk and program/project management are also critical. Stakeholder buy-in must be achieved and maintained throughout the process. Communication, in the form of progress reports, status updates, and other documentation, is essential to keep the program on track.
Many people will contribute to documenting the new network. Project managers will provide scheduling reports; network engineers will provide physical and logical topology maps; security engineers will provide information systems control reports; integrators will track cables, equipment, and IP address allocations in spreadsheets; auditors will provide audit reports; and quality assurance personnel will provide QA reports.
All personnel involved in the network implementation will provide working notes and other documents as requested by the program manager. Leading practices suggest that everything should be documented. In addition, version control is critical to keep everyone on track and reduce scope creep. It’s important to know for sure that everybody on the team is looking at the latest version of all plans, designs, and other documentation.
Chapter Review
This chapter gave you a bird’s-eye view of the process and primary considerations of network design. You should now have a better understanding of what’s important to networking professionals when they set out to design a new network: security, reliability, and quality. You should also have some insight into how they make design decisions, such as subdividing the network by organizational department or classifying network traffic by type. Finally, you should begin to see some of the common ground between IT and AV: focus on customer needs, reliance on allied trades, and a complex, iterative design process that’s as much art as science. You’ll be returning to each of the technical topics discussed here in later chapters—for now, you should have a better understanding of where networks come from.
Now that you’ve completed this chapter, you should be able to
• Describe the needs analysis process as it relates to network design
• List the considerations involved in network topology design
• Describe the security concerns addressed during the network design process
• Describe the quality concerns addressed during the network design process
• Describe the implementation process for a new network
Review Questions
1. When addressing electrical requirements for network devices, _____ are the primary concerns.
A. noise and signal degradation
B. phase and transformer type
C. adequate power and redundant power sources
D. signal separation and equipment grounding
2. At a minimum, what information should be documented regarding each network cable? Check all that apply.
A. The date the cable was installed
B. The cable label or name
C. The devices each cable connects
D. The cable and connector manufacturer
3. Which of the following aspects of a network’s design is typically determined using a “bottom-up” approach?
A. The physical layout of the network
B. The type of cabling used
C. The functions and features of the network
D. The applications that the network will support
4. Which DiffServ class is typically assigned to email and FTP?
A. Low-priority data
B. Low-latency data
C. High-throughput data
D. Standard
5. If the customer’s expectations cannot be met within the current budget or project scope, you should _____.
A. complete only the work within the scope and provide an exhaustive list of project functionality
B. strive to meet those expectations anyway in hopes of obtaining future business from the customer
C. do whatever is necessary to meet business requirements and bill for the extra expenses during the project closeout
D. document the project’s current limitations and obtain customer sign-off
6. You have a videoconferencing codec that can dynamically reduce its transmission rate if it detects network congestion. What DiffServ class should you assign to this device?
A. Telephony
B. Multimedia conferencing
C. Real-time interactive
D. Multimedia streaming
7. During the pre-assessment phase of a network design project, you must determine _____.
A. the overall success of the project, including what aspects of the system the customer is dissatisfied with
B. how the network will be physically laid out within the customer site
C. what laws and regulations the project will be subject to
D. what applications the customer needs to support the organization’s business objectives
8. Which of the following aspects of a network’s design is typically determined using a “top-down” approach?
A. The physical layout of the network
B. The type of cabling used
C. The functions and features of the network
D. The location of cable pathways
9. At a minimum, all network end users should be trained in _____.
A. quality of service, risk analysis, and the CIA triad
B. security awareness, basic network operation, and policy awareness
C. physical topology, logical topology, and network architecture
D. plotting cable runs, cable labeling, and cable documentation
10. During the assessment phase of a network design project, you must determine _____.
A. what applications the customer needs to support the organization’s business objectives
B. the overall success of the project, including what aspects of the system the customer is dissatisfied with
C. how the network will be physically laid out within the customer site
D. what laws and regulations the project will be subject to
11. No single point of failure should affect more than _____ users.
A. 5
B. 10
C. 20
D. 50
12. When subdividing a local area network (LAN) according to business unit, you should name each network _____.
A. after the technician primarily responsible for servicing and maintaining that network
B. after the physical location of the business unit or devices
C. after the business unit it is assigned to
D. using an abstract name whose meaning is documented elsewhere
13. Network-based quality of service is typically based on a strategy of prioritizing _____.
A. time-sensitive traffic over other traffic
B. high-level end-users over low-level end users
C. video traffic over audio traffic
D. high-bandwidth data over low-bandwidth data
14. A hot failover device is one that _____.
A. will cause the entire network to fail if it fails
B. automatically assumes the functions of a failed device
C. is kept in storage in case it is needed to replace another device
D. will fail if the ambient temperature rises above a specified point
Answers
1. C. When addressing electrical requirements for network devices, adequate power and redundant power sources are the primary concerns.
2. B, C. You should document each network cable with the cable label or name and the devices each cable connects.
3. A. The physical layout of the network is typically determined using a bottom-up approach.
4. C. The DiffServ class typically assigned to email and FTP is high-throughput data.
5. D. If the customer’s expectations cannot be met within the current budget or project scope, you should document the project’s current limitations and obtain customer sign-off.
6. B. A videoconferencing codec that can dynamically reduce its transmission rate if it detects network congestion should be assigned a DiffServ of multimedia conferencing.
7. C. During the pre-assessment phase of a network design project, you must determine what laws and regulations the project will be subject to.
8. C. The functions and features of a network are typically determined using a top-down approach.
9. B. At a minimum, all network end users should be trained in security awareness, basic network operation, and policy awareness.
10. A. During the assessment phase of a network design project, you must determine what applications the customer needs to support the organization’s business objectives.
11. C. No single point of failure should affect more than 20 users.
12. D. When subdividing a local area network (LAN) according to business unit, you should name each network using an abstract name whose meaning is documented elsewhere.
13. A. Network-based quality of service is typically based on a strategy of prioritizing time-sensitive traffic over other traffic.
14. B. A hot failover device is one that automatically assumes the functions of a failed device.