CHAPTER 9
Protocols, Ports, and Documenting AV Devices and Protocols
In this chapter, you will learn about
• Protocols and ports and how they factor into networked AV systems
• The most common ports used for AV applications
• The considerations for allowing or disallowing the use of a port
• Using a networked device inventory to document networked AV device ports, protocols, and other information relevant to network management
The further you get into this book, the more you delve into the aspects of networking that directly impact AV professionals. It’s important to understand all the concepts of earlier chapters so that you can communicate with your IT counterparts about the nature of their networks and how your systems might run on them. In this chapter, you will begin to learn about the intersection of networks and networked AV systems—namely, where your AV applications start to interface with the network via protocols and ports.
In Chapter 7, you learned about network addressing and subnetting—how devices identify themselves on the network. In this chapter, we discuss how data actually gets from one device to another, whether across a WAN or the Internet. How a data packet gets from here to there depends on transport and routing protocols. And there are certain protocols that networked AV systems require that IT systems might not.
We also discuss ports, which are more specific destinations than IP addresses and determine what the device on the receiving end of a data stream should do with your information. As you set up networked AV systems, you will need to document the types of traffic those systems will generate and the ports they’ll need access to.
Transport Layer Protocols
Layer 3, the Network Layer, is responsible for assigning IP addresses to network devices and identifying paths from one network to another. The actual end-to-end transportation of data, however, is handled by Layer 4, the Transport Layer.
In the lower layers of the OSI model, each layer carries the layer above it. Physical Layer technologies (Layer 1) carry Ethernet frames (Layer 2), which carry IP packets (Layer 3). This is called encapsulation.
However, Transport Layer protocols are not encapsulated inside IP packets. Instead, Transport Layer protocols fragment IP packets into smaller chunks that fall within the maximum transmission unit (MTU) of the network connection. This process is known as segmentation. The transport protocol is responsible for segmenting data for transmission and reassembling it at its destination.
A transport protocol may be connection oriented or connectionless. Connection-oriented transport protocols are bidirectional. The source device waits for acknowledgment from the destination before sending data. It checks to see if data has arrived before sending more. Connection-oriented transport includes things like error checking and flow control to make sure data arrives as it should.
Connectionless communication is one-way. The source device sends data, which the destination device may or may not receive. Connectionless protocols are less reliable than connection-oriented protocols, but they are also faster. Many media-oriented applications, including practically all real-time protocols, use connectionless transport protocols.
In the TCP/IP protocol stack, Transmission Control Protocol (TCP) is the most commonly used connection-oriented transport protocol; Universal Datagram Protocol (UDP) is the most commonly use connectionless protocol. The two methods differ in speed and reliability. You must be able to identify—and in many cases decide—what kind of transport protocol your AV devices will use to send information over the network.
TCP Transport
TCP transport uses two-way communication to provide guaranteed delivery of data to a remote host. It is connection oriented, meaning it creates and verifies a connection with the remote host before sending any data. It is reliable because it tracks each packet and ensures that it arrives intact. TCP is the most common transport protocol for sending data across the Internet.
Because TCP is reliable and connection oriented, it is used for most Internet services, including such application protocols as Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP).
TCP data transfer involves the following steps (see Figure 9-1 for a graphical representation):
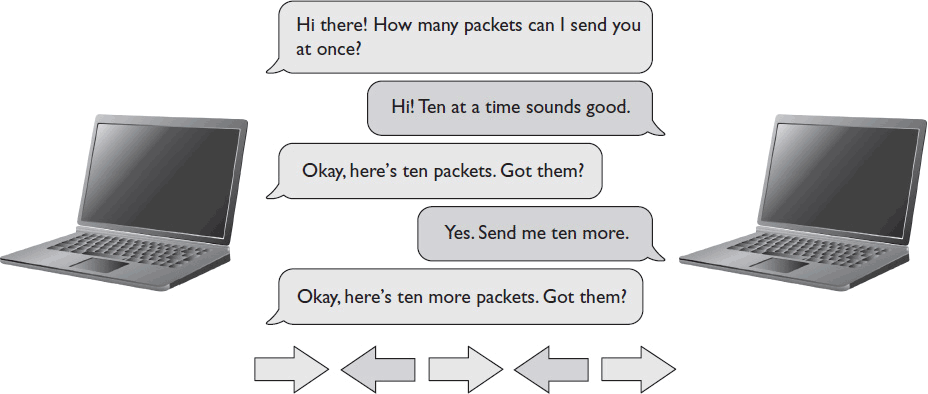
Figure 9-1 TCP data transfer between two networked devices.
1. TCP communication begins with a “handshake,” which establishes that a remote device is on the other end and negotiates the terms of the connection (i.e., how many packets the sending device can send at one time). The number of packets that can be sent together are referred to as a “sliding window.”
2. The sending device sends one sliding window at a time to the destination device.
3. The destination device acknowledges receipt of each sliding window, prompting the sending device to send the next one.
4. The sliding window can’t move past a packet that hasn’t been received and acknowledged. If any packets are damaged or lost in transmission, the sending device resends them before sending any new packets.
UDP Transport
TCP, the most common IP transport protocol, is reliable, but it can also be slow. That’s because with TCP transport, the sending device waits to receive acknowledgment that the last packet was received before sending the next packet.
 NOTE Many enterprises have policies against UDP traffic because hackers can use UDP streams to launch malicious attacks on networks. If you want to use UDP for something like a streaming media system, be prepared to defend your request.
NOTE Many enterprises have policies against UDP traffic because hackers can use UDP streams to launch malicious attacks on networks. If you want to use UDP for something like a streaming media system, be prepared to defend your request.
UDP transport, on the other hand, doesn’t wait. There’s no handshake to speak of. UDP begins sending data without attempting to verify the connection to the destination device, and it continues sending data packets without waiting for acknowledgment of receipt (see Figure 9-2). In other words, UDP is well suited to transmit data when it’s more important that packets arrive quickly rather than in perfect condition.
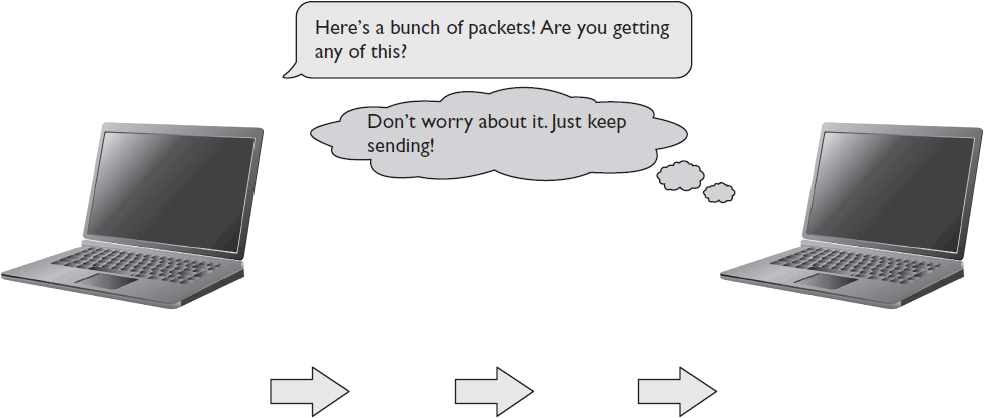
Figure 9-2 UDP data transfer between two networked devices.
Data packets moving quickly over an IP network? Does that sound like a networked AV system to you? It should.
Although UDP lacks TCP’s inherent reliability, that doesn’t mean all data transmitted using UDP is unreliable. Systems that use UDP often manage reliability at a higher level of the OSI model, such as the Application Layer, which is to say the application takes over certain functions, such as error checking, thereby removing that processing from the network and ensuring rapid performance.
As you might have guessed, UDP is commonly used for streaming audio and video, as well as for VoIP, online games, and other networked applications for which dropping packets is better than waiting around for missing packets. When packets get lost in transport, UDP just skips over the missing bits, inserting a split second of silence or a scrambled image instead of stopping and waiting for the packets to be re-sent.
Of course, UDP isn’t only a networked AV transport protocol. It’s also used to exchange very small pieces of information, such as retrieving a DNS name.
 NOTE Real-time Transport Protocol (RTP) is commonly used for streaming media, and most RTP systems are built on UDP.
NOTE Real-time Transport Protocol (RTP) is commonly used for streaming media, and most RTP systems are built on UDP.
Routing Protocols
Getting data from source to destination is easy on a LAN because the switches are connected directly to the nodes and networked devices. Routers have a much more complex task, as they send data to different networks or the Internet. Often, there are hundreds of paths data could take across a WAN. It’s up to routers to decide the best path, and routing protocols help with that determination.
Neighboring routers send each other route maps using special routing protocol packets. Routing protocols fall into two main categories: link-state and distance-vector.
Link-state routing is like a GPS navigation system. It knows every possible road from point A to point B. The route it chooses may be based on speed limits, traffic, overall distance, and so on. Link-state protocols build route maps by analyzing the logical topology of the entire WAN, looking at every possible path from one LAN to another. Each path is analyzed for “cost,” which is based on connection bandwidth, number of hops, traffic congestion, and a number of other factors that can be configured by the network administrator. The router uses the lowest-cost path between source and destination.
Distance-vector routing is more like asking for directions. You might ask which way you need to go, where you need to turn, and how long it will take you to get to your destination. Distance-vector routing protocols don’t look at the entire WAN topology. Instead, they ask, “Which way and how far to the target network?” Or in geekier terms, “Out of which port should I send the data and how many hops will it take to arrive on the target LAN?” Using these two factors, distance-vector routing protocols build an array of direction and distance called a vector.
The following common routing protocols, also known as interior gateway protocols, are used by routers within private WANs to exchange routing information:
• Open Shortest Path First (OSPF) is a link-state routing protocol. An OSPF router builds a topological map of routes by collecting information from all its neighboring routers. OSPF only works with Internet Protocol (IP). It cannot route Ethernet frames or other Data Link or Network Layer packets. OSPF attempts to determine at least two paths to every destination—a primary and a backup route.
• Intermediate System–to–Intermediate System Protocol (IS-IS) is also a link-state routing protocol. Like OSPF, IS-IS uses a network topology map to identify the best paths between LANs. It differs from other link-state protocols in that it’s not tied to the TCP/IP protocol stack. IS-IS was written as a native Layer 3 routing protocol under the OSI model. Therefore, IS-IS can transport any Network Layer protocol, not just IP. Most other link-state protocols were written to support the TCP/IP model.
• Routing Information Protocol (RIP) is a distance-vector protocol for classful networks that runs over UDP. RIP does not use a topology map like a link-state routing protocol does. Instead, it uses vectors—a combination of direction and number of hops between routers. Basically, RIP answers the question, “How many routers will the data have to pass through before it reaches its destination?”
RIP limits hops to 16, numbered 0–15. The limited hop count means RIP is best used in smaller networks. A router using RIP builds its own routing table based on information gathered from its interfaces. It then shares the routing table with other routers via broadcasts. RIP sends these broadcasts every 30 seconds, creating a lot of network traffic. On a network carrying AV data, it’s best to keep the pipes as clear as possible.
 NOTE The Routing Information Protocol has no way to authenticate routers on a network, which may make it vulnerable to hackers.
NOTE The Routing Information Protocol has no way to authenticate routers on a network, which may make it vulnerable to hackers.
• Routing Information Protocol Version 2 (RIPv2) is a distance-vector protocol that supports classless interdomain routing (CIDR)—unlike RIP. Therefore, if your network is divided into subnets, you have to use RIPv2 instead of RIP.
• Enhanced Interior Gateway Routing Protocol (EIGRP) is a proprietary Cisco distance-vector protocol. Like RIPv2, EIGRP can be used on CIDR networks. It uses hops to determine the best path from one network to another. However, EIGRP allows up to 255 hops, instead of the 16 allowed by the RIP protocols. EIGRP also sends its broadcast updates every 90 seconds instead of every 30, which significantly reduces traffic on the network.
Although EIGRP is considered a distance-vector protocol, it uses more than just distance and direction to evaluate routes. EIGRP uses three tables to store routing information—a basic routing table, a neighbor table with addresses of neighboring routers, and a topology table, similar to a link-state routing protocol. This allows EIGRP to use additional data, such as bandwidth, delay, load, MTU, and reliability, to determine the best paths.
• Border Gateway Protocol (BGP) does not fall into one of the two standard categories. Instead, BGP displays traits of both distance-vector and link-state protocols and is therefore considered a “path-vector” routing protocol. BGP can be used as an interior gateway protocol, but it is mostly deployed as an exterior gateway protocol. It is used to route data across the Internet. Unless an organization has a dedicated block of publicly routed IP addresses, or it functions as an ISP, or it has a multihomed presence on the Internet, it is unlikely to ever use BGP.
 NOTE When a networking device such as a server is multihomed, it means it is connected to more than one network. Such a setup might be used to ensure that network connectivity doesn’t become a single point of failure.
NOTE When a networking device such as a server is multihomed, it means it is connected to more than one network. Such a setup might be used to ensure that network connectivity doesn’t become a single point of failure.
Ports
Network Layer routing and Data Link Layer switching are responsible for making sure data reaches its intended network device. Once the data arrives, however, the device needs to know what to do with the data. This is where we get into the Application Layer of the OSI model.
The Transport Layer protocol—either TCP or UDP—includes a port number in its header. If an IP address is like the address of an apartment building, the port number is like the door of the apartment where the data needs to enter.
In a TCP/IP network, a port is a 16-bit number included in the TCP or UDP Transport Layer header. The port number typically indicates the Application Layer protocol that generated a data packet. A port may also be called by its associated service (e.g., port 80 may be called HTTP, or port 23 may be called Telnet).
Basically, the port number indicates what the system expects the data to do. The Internet Assigned Numbers Authority (IANA) permanently assigns many port numbers to standardized, well-known services. Every TCP/IP system has a “services” file that contains a list of permanently assigned ports and their associated services. In general:
• System ports (0–1023) are assigned to Internet standard protocols. These are also known as “well-known ports.”
• User ports (1024–49151) are assigned by IANA upon request from application developers.
• Dynamic ports (49152–65535) cannot be assigned or reserved. Applications can use any dynamic port that is available on the local host. However, an application can’t assume a port will always be available. Dynamic ports are also known as “ephemeral” ports.
Although you can often identify an originating application by a data packet’s port number, it’s not always possible. Sometimes, a service with a permanently assigned port has to open one or more dynamic ports in order to run several instances of the service on the same host. Many applications choose a port from the dynamic port range at random.
 NOTE In a TCP/IP network, a socket is the combined port number and IP address of communicating end systems. A socket uniquely identifies a session of a given transport protocol.
NOTE In a TCP/IP network, a socket is the combined port number and IP address of communicating end systems. A socket uniquely identifies a session of a given transport protocol.
Table 9-1 shows a list of common IP ports. Ports that are particularly common for AV applications are shown in boldface type. You can find a comprehensive list of published port numbers at www.iana.org/assignments/port-numbers.
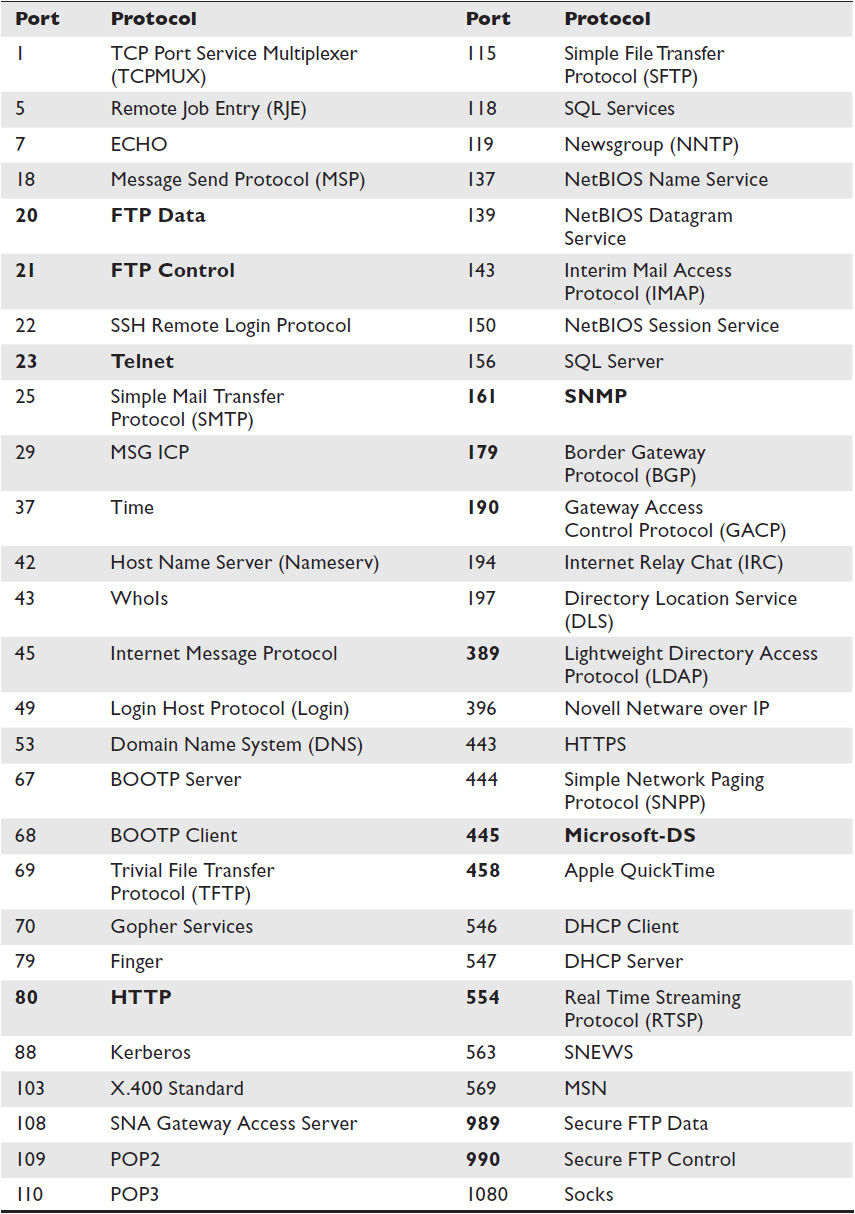
Table 9-1 Common IP Ports
Identifying Protocols and Ports
When installing a networked AV system, AV and IT professionals must coordinate which ports need to be opened on routers and firewalls and which protocols will be allowed to travel through each port. In fact, one of the most important factors in whether AV network traffic reaches its intended destination is the configuration of firewalls. The firewall is the ultimate arbiter of what kinds of traffic can access the network through what ports. Because the firewall must protect the entire network, firewall configuration is a crucial area of coordination between AV and IT.
The decision to allow a protocol or open a port is a security concern. The more types of traffic allowed on a network, the higher the network’s vulnerability. An AV design must list the ports and protocols that need to pass through the firewall as specifically and narrowly as possible so that network managers can support the system. If as an AV integrator or designer you anticipate a specific data stream for your AV application, then you need to ensure its port will be open. Hopefully, you will be able to determine which ports and protocols are required for a given AV application from the manufacturers of the devices used. The manufacturer specifications of any networked device should list the protocols and port ranges the device employs. Still, it’s a good idea to ensure through observation that the actual network traffic matches the specifications.
Think carefully about how you can employ firewall strategies, such as port forwarding, to give you the access you need without endangering the network. Document as much of the ports and protocols information as you can as early as possible. The more time you have to work out a firewall transversal strategy, the likelier you are to arrive at an approach that satisfies all network stakeholders. For more on firewalls and strategies such as port forwarding see Chapter 15.
 NOTE Always verify your ports and protocols. Using a network protocol analyzer tool, such as Wireshark (available at http://www.wireshark.org), you can capture, dissect, and observe network traffic to detect the protocols and applications present.
NOTE Always verify your ports and protocols. Using a network protocol analyzer tool, such as Wireshark (available at http://www.wireshark.org), you can capture, dissect, and observe network traffic to detect the protocols and applications present.
Networked Device Inventory
In order to define accurate service targets and ensure that AV devices will be compatible with a customer’s network environment, AV and IT professionals should develop a ports and protocols document. The ports and protocols document is an inventory of networked devices in an AV system. It’s a means of starting discussions (and resolving conflicts) between AV and IT at the earliest possible stages of the networked AV system design process. It will also serve to inform service-level agreements (SLAs) later in the process. You will learn about SLAs in Chapter 14.
You can put as much useful information as you want in the ports and protocols document, but at least include the following:
• Device narrative Record what devices need to connect to the network and why. What information do they need to send and receive? What other devices do they need to communicate with?
• Interdevice communication Record the transport protocols each device will use. Will the traffic be unicast or multicast? What codecs will it use? What bandwidth will it consume?
• Device properties As actual components are selected, record their relevant specifications, including manufacturer, model number, MAC address, and software and firmware versions.
• Routing and addressing As you select components, record the information needed to address each device and route data to and from its address. This section of the document includes the devices’ physical location, as well as all applicable IP addressing, subnet masks, DNS information, and ports and protocols.
• SNMP monitoring If applicable, record the Simple Network Management Protocol (SNMP) server, community name, and administrator login information. SNMP is used to monitor devices on a network—provided those devices support SNMP and can report back on their status. Check your networked AV gear for SNMP support.
• Conferencing addressing If you will be installing conferencing devices (videoconferencing codecs, VoIP phones, etc.), record the gatekeeper addresses, system names, and E.164 addresses for all conferencing devices. A gatekeeper handles call control and translates E.164 IDs (often phone numbers) into IP addresses.
• Passwords If requested by the customer or the customer’s IT department, provide username and password information for each networked AV device.
Recording all this information in one document allows discussions between system designers and network managers—or internal and external service providers—to start quickly and with greater clarity than if neither side knew what AV devices might need network access. Remember, though, you are not expected to discover all of each device’s requirements at once. Some will be determined throughout the needs assessment, conceptual design, product selection, and installation processes. The goal is to provide as much information as you can, as soon as you can provide it.
Correctly identifying and documenting the ports and protocols used by an AV system will make or break your networked application. If the ports aren’t opened, or the protocols are forbidden, your AV traffic will not pass through the network. Allowing certain ports and protocols on an IT network is likely to be the biggest point of contention between the AV designer and the network manager, so start planning early.
Chapter Review
In this chapter, you learned how data is transported from one network to another. Both transport and routing protocols can affect network latency, which can have a significant impact on most networked AV systems. You may be responsible for choosing the transport protocol your devices use. Different transport protocols support different applications. For example, you may want to use TCP for control and UDP for AV. It is important to work closely with your IT counterparts to ensure that UDP traffic is allowed on network segments where it is required for AV applications.
When it comes to routing protocols, in general, more hops mean more latency. For streaming media applications, you may prefer a routing protocol that limits the number of hops. Many routing protocols can help deliver time-sensitive data, such as AV streams, by weighing bandwidth and traffic congestion when identifying network paths.
Finally, close coordination, and sometimes negotiation, with IT is necessary to ensure that the ports your AV applications require will be open throughout the network. Make sure you inventory all AV devices and the ports and protocols they may need so that AV data gets to where it needs to go.
Now that you’ve completed this chapter, you should be able to
• Compare and contrast TCP and UDP transport protocols
• Compare and contrast routing protocols
• Prepare a simple networked device inventory for your IT counterparts
• Describe the roles of the upper layers of the OSI model in networked AV systems
Review Questions
1. Link-state protocols choose routes by _______.
A. querying a root server that stores optimum paths between networks
B. looking up the path in a manually maintained file known as a “routes file”
C. analyzing which port router should send data out of, and how many hops it will take to arrive at its destination
D. analyzing every possible path from one LAN to another and choosing the “lowest-cost” path
2. Distance-vector protocols choose routes by ____ ____.
A. analyzing which port router should send data out of, and how many hops it will take to arrive at its destination
B. analyzing every possible path from one LAN to another and choosing the “lowest-cost” path
C. querying a root server that stores optimum paths between networks
D. looking up the path in a manually maintained file known as a “routes file”
3. A(n) _______protocol is a routing protocol used by routers within private WANs.
A. interior gateway
B. exterior gateway
C. wide area routing
D. local area routing
4. ____ _____ is a proprietary Cisco routing protocol that allows up to 255 hops on CIDR networks.
A. Routing Information Protocol Version 2 (RIPv2)
B. Open Shortest Path First (OSPF)
C. Intermediate System–to–Intermediate System (IS-IS)
D. Enhanced Interior Gateway Routing Protocol (EIGRP)
5. ____ ____ is an exterior gateway protocol used to route data across the Internet.
A. Open Shortest Path First (OSPF)
B. Intermediate System–to–Intermediate System (IS-IS)
C. Border Gateway Protocol (BGP)
D. Routing Information Protocol Version 2 (RIPv2)
6. A Transport Layer protocol is connection oriented if it _______.
A. can only transport data to devices to which the sending device is directly connected
B. sends data only along certain manually configured connections
C. transports data only over wired physical media
D. verifies its connection to the remote host before sending any data
7. UDP is used for _______. Select all that apply.
A. exchange of small pieces of information, like DNS name retrieval
B. time-sensitive applications, such as live streaming audio or video
C. transporting web page content over the Internet
D. transporting data files over a network, using technologies such as FTP and FTPS
8. TCP transport should be used instead of UDP transport when _______.
A. speed and continuity of transmission are more important than guaranteed delivery or accuracy of data
B. data accessibility is more important than security of the data transmission
C. security of the data transmission is more important than data accessibility
D. guaranteed delivery and quality of the data is more important than the speed or continuity of the transmission
9. _______ Layer protocols are particularly important to streaming media and conferencing applications because they regulate sustained communication among devices.
A. Session
B. Application
C. Presentation
D. Network
10. In a TCP/IP network, the port number ____ ____.
A. indicates where to connect an input/output for a networked AV system
B. indicates the Application Layer protocol used to generate a data packet
C. provides guaranteed delivery of data to a remote host
D. cannot be assigned or reserved
11. Which of the following ports is used for HTTP traffic?
A. 23
B. 45
C. 80
D. 110
E. 161
Answers
1. D. Link-state protocols choose routes by analyzing every possible path from one LAN to another and choosing the “lowest-cost” path.
2. A. Distance-vector protocols choose routes by analyzing which port router should send data out of, and how many hops it will take to arrive at its destination.
3. A. An interior gateway protocol is a routing protocol used by routers within private WANs.
4. D. Enhanced Interior Gateway Routing Protocol (EIGRP) is a proprietary Cisco routing protocol that allows up to 255 hops on CIDR networks.
5. C. Border Gateway Protocol (BGP) is an exterior gateway protocol used to route data across the Internet.
6. D. A Transport Layer protocol is connection oriented if it verifies its connection to the remote host before sending any data.
7. B. UDP is used for time-sensitive applications, such as live streaming audio or video.
8. D. TCP transport should be used instead of UDP transport when guaranteed delivery and quality of the data is more important than the speed or continuity of the transmission.
9. A. Session Layer protocols are particularly important to streaming media and conferencing applications because they regulate sustained communication among devices.
10. B. In a TCP/IP network, the port number indicates the Application Layer protocol used to generate a data packet.
11. C. Port 80 is assigned to HTTP traffic.
