This is the most important section of this chapter, because it will allow you to structure your tests. A challenge that a typical pen tester will face is everyone telling them to refer to the OWASP checklist for web intrusion tests. But, the big questions that all testers will ask themselves are, where do I start? How do I proceed with the checklist? Before I get into the steps, let's take a look at an image of this workflow, a picture worth a thousand words. My workflow is based on a proxy-based tool: Burp Pro. Please refer to Chapter 4, All About Using Burp Suite at the beginning of this book for more details:
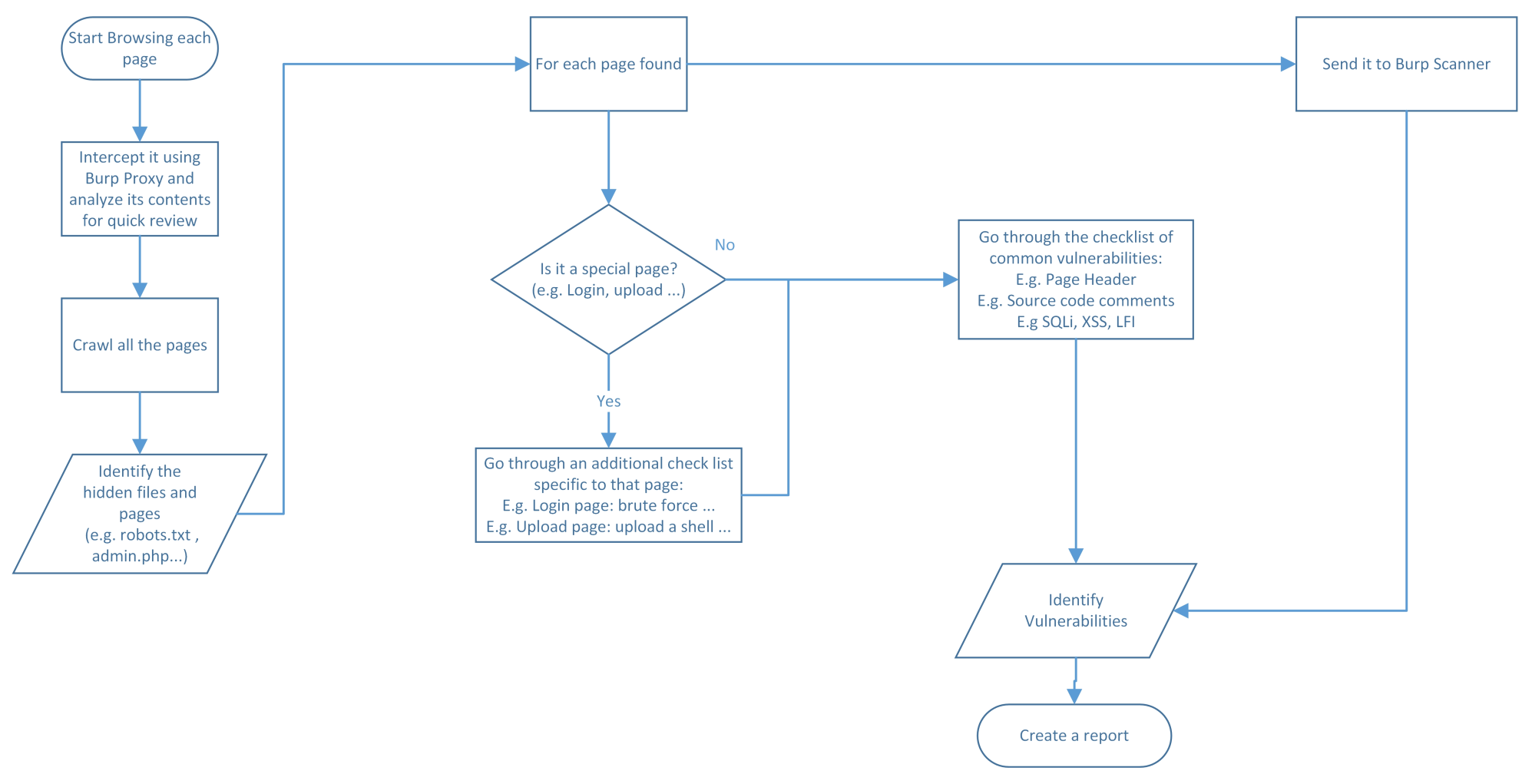
- The first step is not mentioned in the preceding diagram; it's the web server vulnerability assessment, which we discussed in the previous chapter.
- The second step is to fire Burp and make sure that the intercept is on in the Proxy tab. Next, start browsing each page separately, and check the contents through the proxy Request/Response details. While you're browsing, try to interact with each page, manually sending form post requests with data. Also, try to use the search button on the search page. You get the idea; don't just click around blindly.
- Crawl the pages using Burp Spider and Burp Content Discovery. You can use other tools for crawling, as well; check the previous chapter, in the HTTP enumeration section.
- Identify any hidden contents, such as the robots.txt file. We will show the checklist later in this chapter (for the time being, work on getting the big picture).
- Burp will list all of the pages and files found in the Target tab. For each page found, perform the steps that follow.
- Send each request to the Burp Scanner to scan for issues automatically.
- For manual scanning, you will need to ask the following question: is it a special page? (For example, a login page; again, don't worry. I will list all of the details later.)
- If it's a special page, we will go through the checklist specific to that page. For example, if it's a login page, we will test the default credentials. After that, we will go through the common checklist.
- If it's not a special page, we will go straight to the common checklist (checking comments, input testing for SQLi, and so on).
- Gather all of the vulnerabilities found and create a report from them.
