Another interesting example that I would like to share with you is using the header to inject JavaScript into the page. Tricky right? But don't be surprised to see that the nature of web applications will allow us to manipulate the web page through the header.
Let's visualize this case so you can understand things better:
- Go to the homepage of Mutillidae then on the left menu, choose OWASP 2017 | Cross Site Scripting | Persistent| Show Log:

- This page records every visit to the Mutillidae application. The third column stores the Browser Agent value of the visitor. What if that visitor is malicious and replaces his browser agent with JavaScript using Burp?

- So, I will intercept the page using the Proxy tab in Burp, then modify the Browser Agent with a JavaScript alert and forward it to the server (using the Forward button):
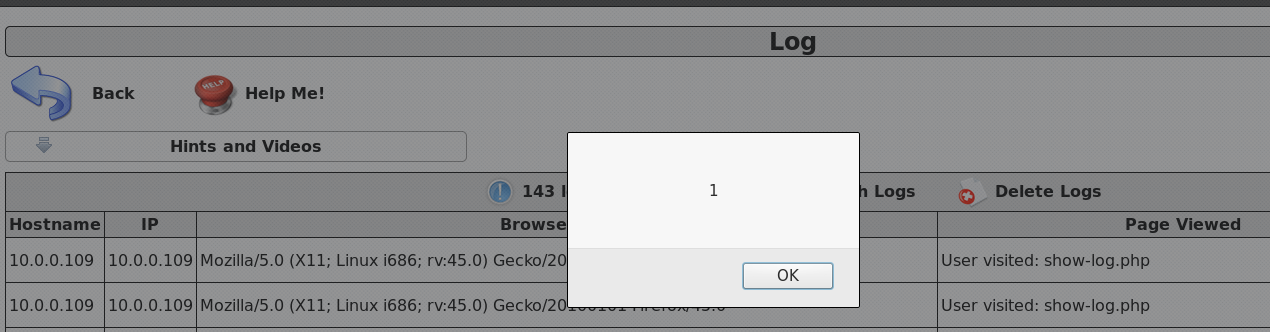
Voila! This is the result of changing the user agent of our browser using our XSS trick in Burp. Again, this is a persistent XSS and every time the admin of the site visits this page, he or she will be prompted with our payload.
