Chapter 10: Purple Teaming the ATT&CK Tactics
The MITRE ATT&CK framework has become the de facto standard knowledge base regarding adversary tactics and techniques. This repository is continuously evolving and offers classified tactics and techniques that could be used by both red and blue teams for security assessments. An interesting part of this framework is that these technical references can be used directly in security devices such as Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), Breach Attack Simulation (BAS), Sigma rules (where most of the detection rules contain MITRE ATT&CK tags), and so on. Security professionals can now build a full coverage mapping of all techniques to get an overall view of the global security resilience of the company and represent them using the nice MITRE ATT&CK Navigator (https://mitre-attack.github.io/attack-navigator/). This framework offers a real bridge between technical integrations and operations to the management side so that they can assess their strategy in terms of risks and investments.
In this chapter, we will analyze the most common and trendy attacks techniques, mapping them to the MITRE ATT&CK framework and providing you with practical purple team strategies for each tactic and techniques layers for attacks replay, detections, and preventions. The following topics will be covered:
- Initial access
- Execution
- Persistence
- Privilege escalation
- Defense evasion
- Credential access
- Discovery
- Lateral movement
- Collection
- Command and Control (C2)
- Exfiltration
- Impact
Technical requirements
The previous chapters covered most of the different approaches that will be described in this chapter for both attack and defense. Therefore, no additional requirements are necessary for this chapter.
The pseudocode that you will encounter in this chapter was written to be as understandable as possible and allow you to convert it into your favorite SIEM language.
Methodology
This chapter aims to be the bedtime reading part of this book. We initially wanted to create this chapter by following a particular threat actor, but it wouldn't be relevant for everyone and may also become less and less relevant over time. Instead, we thought it might be more useful to make an inventory of the most common TTPs any organization could face today and in the future. For that, we based our top TTPs on various reports, some of which were already mentioned at the beginning of this book, such as Crowdstrike 2021 Threat Hunting Report, Red Canary 2021 Threat Detection Report, and McAfee Advanced Threat Research Report October 2021 (now Trellix).
We will mainly depict the top TTPs that have been encountered and identified by security vendors, regardless of the region, industry, and types of threat actors. Of course, it is always better to have a refined and targeted intelligence to help focus on what matters to us. But as we have seen, it is not easy to mature an intelligence program, and we may want to start right away by assessing our security maturity against what is the trendiest and therefore potentially most likely to hit us.
It is important to note that MITRE ATT&CK merged with the PRE-ATT&CK matrix into ATT&CK in 2020 by adding two new tactics to the latter: reconnaissance and resource development. Interestingly, few reports have updated their ATT&CK matrixes with these two new tactics. So, it is a bit more difficult to identify trends, typically because it is harder to collect data on behavior not directly hitting our organization and relying on public information.
The rest of this chapter will be split into sections that follow the MITRE ATT&CK tactics. Each section will cover the selected techniques and the CTI, red, and blue parts of it. In particular, we will cover the following:
- A CTI introduction that covers the description and goal of the technique, the trend around it, such as the relevant threat actors and software related to it, as well as the victimology, if relevant.
- A purple teaming table containing references and tips on how to emulate the same behavior by leveraging the Atomic Red Team project. We will also inventory detection (both alerting and hunting) and hardening techniques from various projects such as SIGMA (https://github.com/SigmaHQ/sigma), MITRE CAR (Cyber Analytics Repository: https://car.mitre.org/analytics/), Awesome Hardening (https://github.com/decalage2/awesome-security-hardening), and others.
In the blue team part, we will focus on detection as it is the more agile way of getting things done. Prevention measures often require time and effort and must be assessed to ensure we are not breaking things. But of course, the ultimate goal is to be able to prevent a malicious action and not just detect it. That is why we will also list some prevention ideas that should be explored and implemented on a more medium- to long-term timeline. We recommend the following resource, which helps with mapping MITRE ATT&CK techniques to security frameworks such as NIST: https://github.com/center-for-threat-informed-defense/attack-control-framework-mappings.
This should help anyone who's starting to test TTPs in an atomic way. We have tried to stick to a minimum requirement level when it comes to testing a technique by mostly relying on the Atomic Red Team project.
Reconnaissance and resource development
The reconnaissance tactic is the first step that's performed by the threat actor. It consists of collecting information on the target to prepare for the next steps.
As its name suggests, the resource development step's goal is to develop the necessary resources to perform the rest of the operations.
As we've explained previously, these tactics and their techniques are mostly used outside our organization's visibility, so difficult for a defender to do something about it. Let's look at the most commonly used reconnaissance and resource development techniques by threat actors:
- Reconnaissance:
- T1595 Active Scanning
- T1596 Search Open Technical Databases
- Resource Development:
- T1583 Acquire Infrastructure
- T1584 Compromise Infrastructure
- T1587 Develop Capabilities
- T1588 Obtain Capabilities
As we can see, except for the scanning activities, it may be almost impossible to do anything about those techniques. That is why we recommend, just like MITRE does, focusing the detection effort on later related stages such as C2, Defense Evasion, and so on.
Nevertheless, there are still some actions that can be performed if we've reached a mature level with regards to the later kill chain steps. Similar to what we presented in Chapter 7, Blue Team – Detect, we can implement various kinds of monitoring to try and predict where attackers will strike, whether it is related to public infrastructure, the domain that's been registered, or TLS certificates. The possibilities are endless and will depend on the skills, time, and budget we can allocate to such activities. As an example, we could focus our public monitoring activities on tracking Cobalt Strike servers, which are, as we know, being leveraged by attackers. Here is a great resource from Michael Koczwara so that you can start hunting Cobalt Strike servers: https://github.com/MichaelKoczwara/Awesome-CobaltStrike-Defence.
Initial access
This is usually the first step of the kill chain where we, as defenders, have a chance to stop the attackers trying to get a first foothold in our network.
As we discussed in Chapter 1, Contextualizing Threats and Today's Challenges, phishing and exploiting remote services are used to get initial access to an information system. These are the two techniques we will explore in this section.
T1566 – Phishing
It is impossible to go through the initial access tactics without talking about phishing techniques. This technique is one of the most common techniques to gain the first foothold in an internal network, for several reasons. The first one could be the success rate linked to this technique because many people – especially non-technical users – lack awareness and therefore can be oriented and manipulated to click or open a document that will allow external attackers to move on to the next step of the kill chain. There's also the exploitation potential, as there are always users in companies with access to a corporate mailbox. This technique does not require a publicly exposed service or anything else to be executed. In the case of success, this technique will probably not give direct access to highly privileged accounts or key infrastructure elements such as being able to use an RCE on an Exchange server, but it will not be detected or even reported by fooled users.
Let's see how we can set up and simulate a phishing campaign. We introduced and discussed this topic in Chapter 5, Red Team Infrastructure, when we presented GoPhish. As we explained there, the platform is very simple to deploy and run, but in this section, we will list additional tools and tips that you can use to perform a successful campaign:
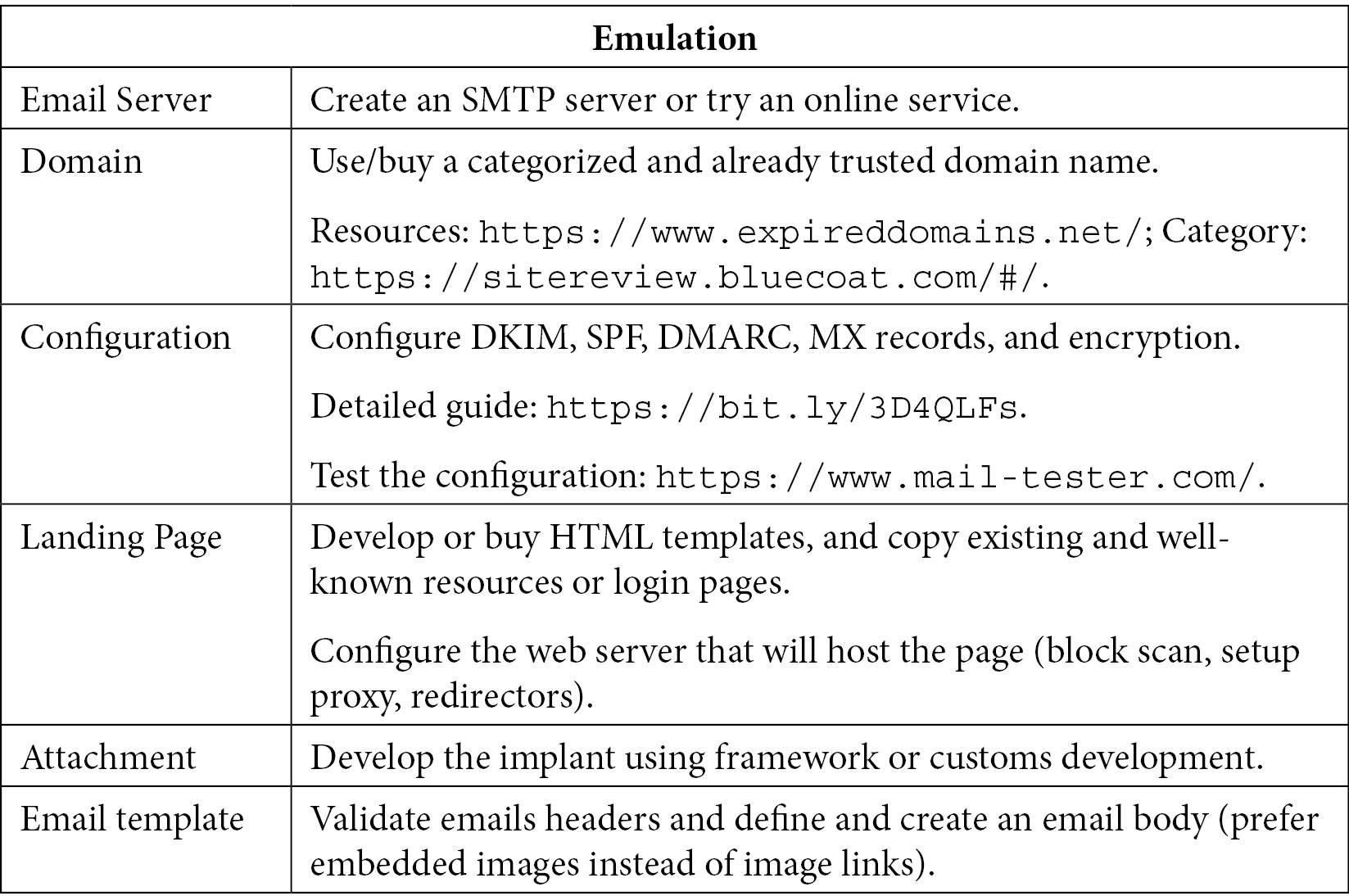
Table 10.1 – Phishing emulation tips and tricks
Here are two other links that can help us in building a phishing exercise: https://github.com/yeyintminthuhtut/Awesome-Red-Teaming#-initial-access and https://github.com/infosecn1nja/Red-Teaming-Toolkit. Setting up a perfect phishing infrastructure can be a very time-consuming task and requires a lot of knowledge in multiple fields. In the previous table, we learned about the steps that could be taken to simulate this technique. More advanced technical configurations and techniques can be used and found on the internet. Now, let's discuss how to detect the usage or attempted usage of this technique. This should occur at different levels, thus maximizing your chance of countering the techniques that have been deployed by attackers to remain under the radar:
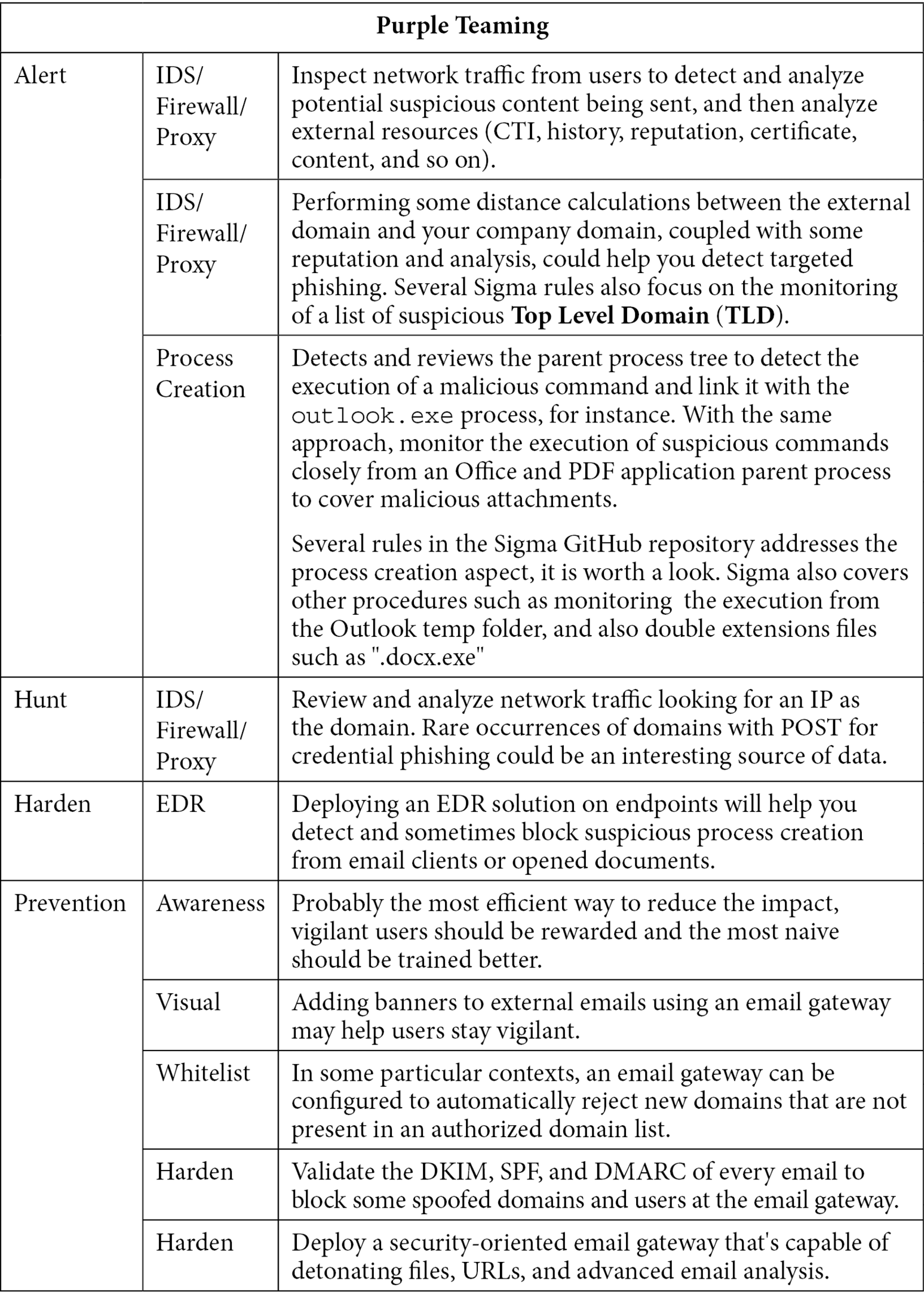
Table 10.2 – Purple Teaming T1566
All these prevention methods have been classified from the simplest to the hardest but also with regards to efficiency. If you deploy EDR or any agents on local machines or if you harden the email gateway but you do not train your users, they will still click on the 0.01% of malicious emails that will be delivered to them.
Phishing can be very difficult to block or detect since emails are required for every business. Nevertheless, adding security detection layers at different levels, coupled with some prevention methods, can drastically reduce the impact and the flow of such a threat.
Now, let's look at the next technique. This one has been used for a very long time and is often devastating and creates a tsunami in the InfoSec community when published.
T1190 – Exploit public-facing application
Most companies and information systems, even the most secure, need to expose some services and applications to the internet. This is even more true due to the COVID-19 pandemic, which has forced remote working, but also by the appearance of cloud computing and containers. Abusing or finding bugs and flaws in a publicly exposed application is often used by opportunistic threat actors when published. But sometimes, these flaws are kept secret by people so that they can capitalize on this advantage and achieve their objectives. From SQL injection in a website to remote code execution (RCE) on Exchange, handling and managing this technique and its consequences is often costly and time-consuming, but only for the defensive side. Nevertheless, well-known exploits such as SQL flaws are now well documented and can be discovered by tools and penetration testers, as well as addressed by applying some guidelines. But this technique also regroups other types of exploits – ones that have not been discovered yet.
So, providing an emulation plan for this technique is very difficult, even impossible. It is almost the same for detection and alerting. Nevertheless, even if the exploitation itself can be difficult to detect in the case of non-publicly disclosed vulnerabilities, the publicly exposed server and application should be monitored to detect the next steps and commands that will be issued by the intruder. Let's take, for instance, the case of ProxyShell and ProxyLogon. These two chains of vulnerabilities impacted most versions of Exchange servers and allowed unauthenticated people to execute code. Thanks to Sysmon and use cases based on process command lines and arguments, it is possible to trigger and detect the web shell being installed and launched by the web server process:
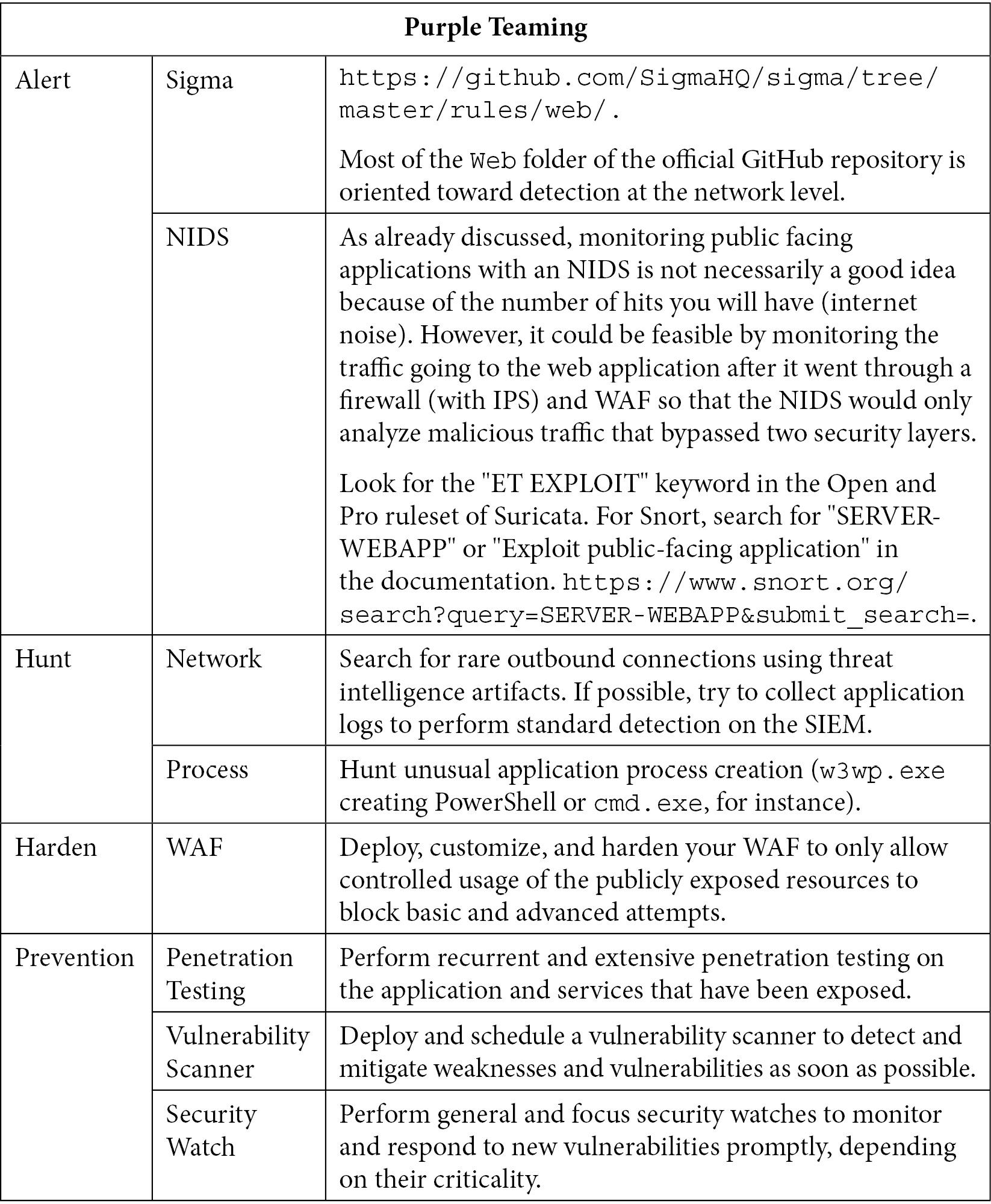
Table 10.3 – Purple Teaming T1190
As we can see, the most used techniques related to initial access are very difficult to emulate and detect. Nevertheless, some products and solutions may help us block but also simulate phishing attempts to validate our security controls. Regarding T1190, the detection mostly relies on layered security defense in the case of undisclosed vulnerabilities. We must also rely on the fact that we have other rules that can help detect the attacker's next moves. As in a real attack, once the attacker has access to our internal network, they will move on to the execution phase.
Execution
This part of the ATT&CK framework is when an attacker already has some foothold in a network. For example, the victim has opened a malicious attachment that's been received by email and is moving their mouse to click on execute macros, or when attackers have sent a payload to a vulnerable server and the payload is being processed by the engine before sending the shell back to the threat actor.
This phase will occur when malicious code needs to be executed again and again until the attacker has reached their objectives. The famous motto from SANS, Malware can hide but it must run, illustrates these techniques perfectly. We will start by looking at built-in methods as they represent the simplest and fastest way to run code.
T1059 – Command and scripting interpreter
The easiest way to interact with a remote host is to use the tools that are already installed. This is why so many malware and attacks rely on the usage of built-in interpreters. Most of them are rarely hardened and configured properly to avoid misuse and they come pre-packaged with all the capabilities an attacker may need to achieve their goal. If we think of cmd.exe and powershell.exe, they are almost, if not always, used to execute commands on a breached host from execution to exfiltration and even sometimes to launch the ransomware payload. Thus, at first glance, it could seem very difficult to detect or even block suspicious command lines and not block production work from system administrators. But at the same time, implementing this layer of detection will allow us to cover several techniques:
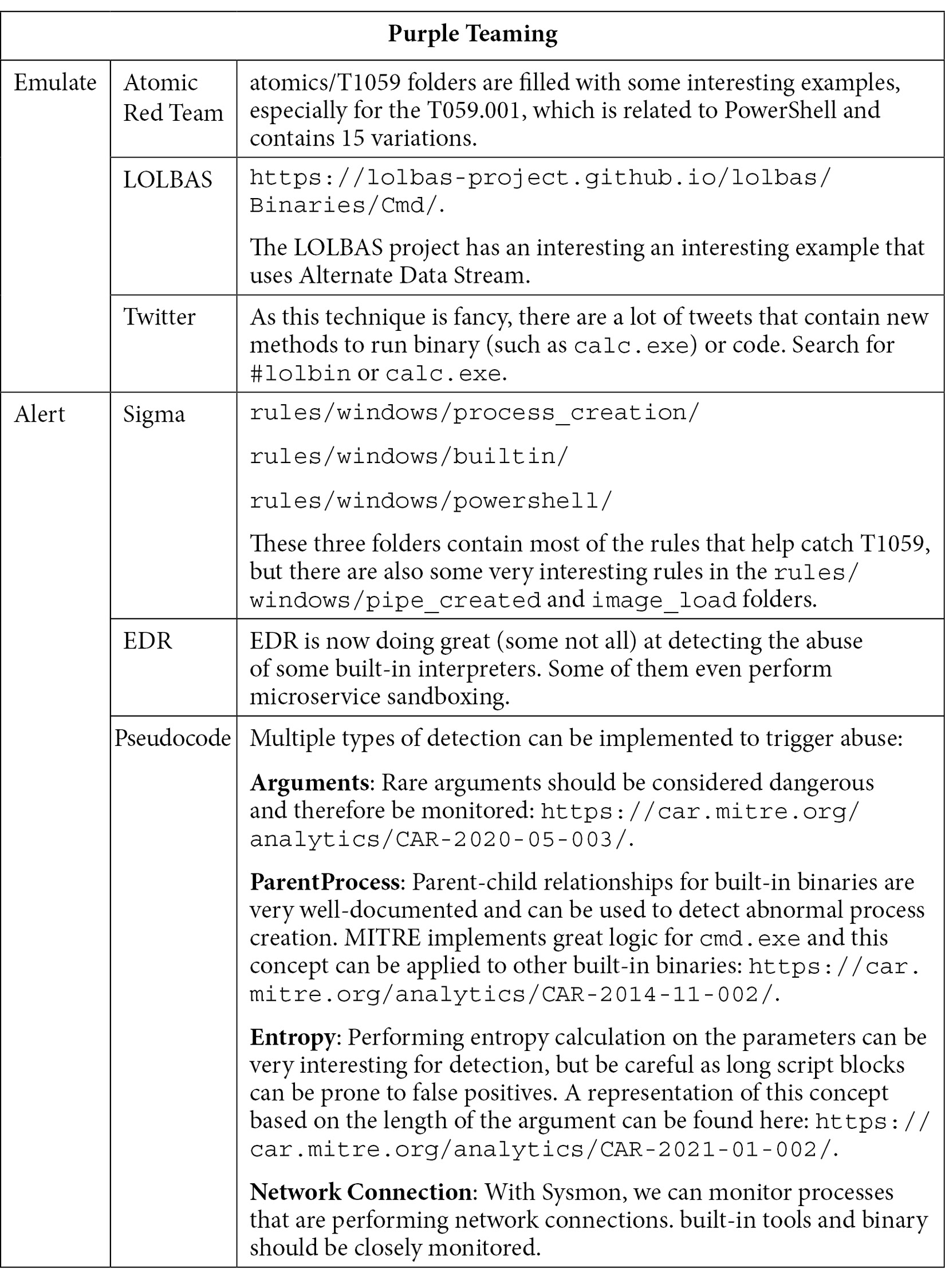
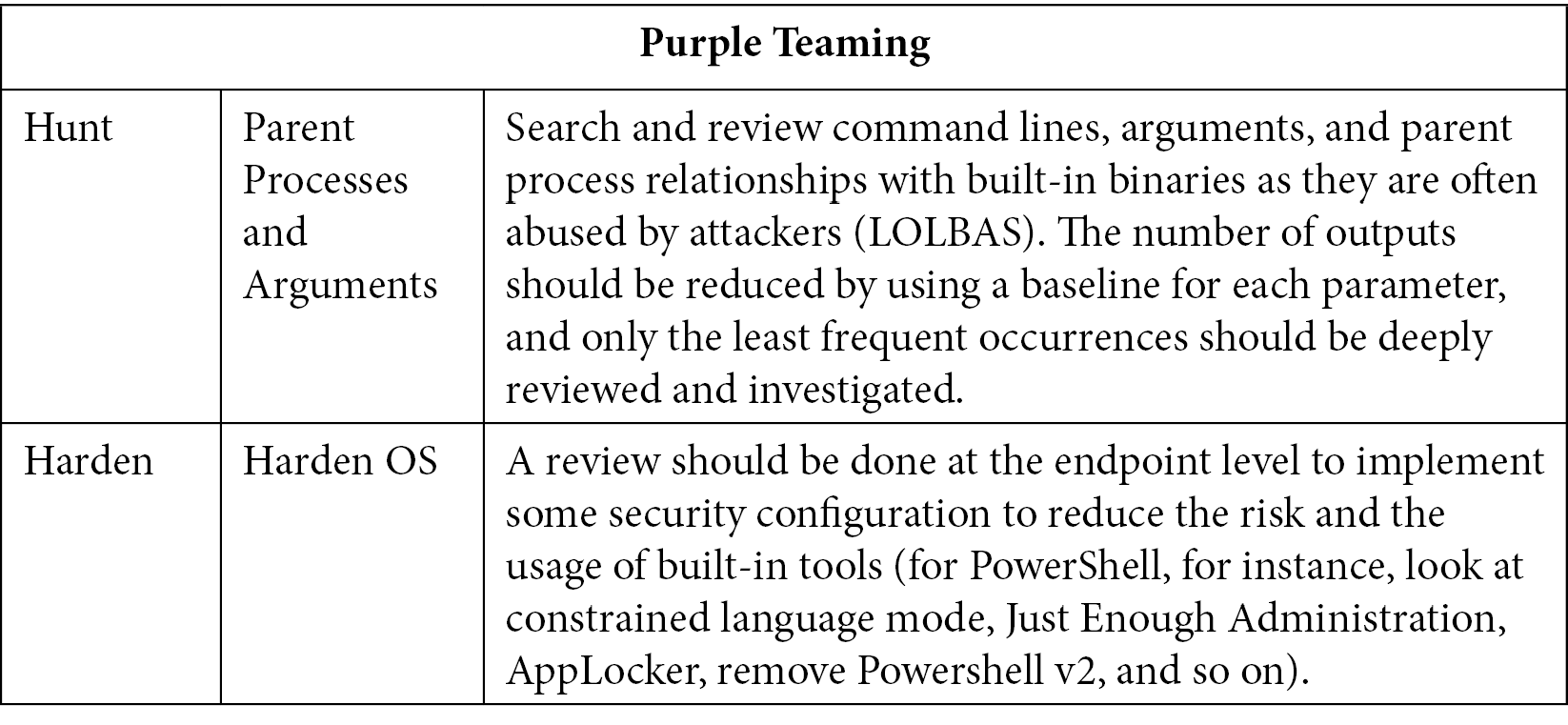 Table 10.4 – Purple Teaming T1059
Table 10.4 – Purple Teaming T1059
For this tactic, we only decided to cover the command and scripting techniques since the two other main techniques (scheduled task and user execution), most of the time, end up being used in the built-in capabilities of the infected host. (Malicious Word documents containing macros that will trick a user to execute them will often launch a suspicious powershell.exe or cmd.exe file to download additional payloads.) This statement is also true for the next phase since persistence mechanisms can be deployed using a system interpreter and scripting.
Persistence
Persistence is the kill chain step that represents a key mechanism during an attack. It allows an attacker to capitalize on all the previous steps and efforts they have made. Its goal consists of deploying mechanisms to maintain control over the breached assets inside a network to be resistant to a reboot or credential change. During the investigation, we often see this technique being used after the initial malware execution (often preceded by execution, privilege escalation, and defense evasion) and is the starting point for manual operations and internal discovery.
T1053 – Scheduled task/job
Creating scheduled tasks or jobs is the most simple and flexible sub-technique you can deploy. In this section, we will discuss most of Windows's methods for creating tasks that will execute code at a specific condition or time (this technique is also classified in the execution and privileges escalation parts of the ATT&CK framework). This technique is also applicable to Linux systems by using cron or at (T1053.003 and T1053.001, respectively).
Often, these techniques abuse a feature of the operating systems (OSs) that allows them to perform specific tasks at a given time or for specific conditions (user logon, for instance). On Windows, it uses the schtasks utility, which has the benefit of being used by software or enterprise administrators. This is why deploying this kind of method can often blend in with normal behavior and artifacts on a system.
So, combining all the previous arguments (simplicity, code execution, escalating privileges, native features on Windows, and stealthiness) made these techniques very well-known that can be used by attackers to reach several kinds of objectives. But by chance, these techniques can also be detected and prevented quite simply.
First of all, let's learn how to run and execute commands to create simple and advanced scheduled tasks:
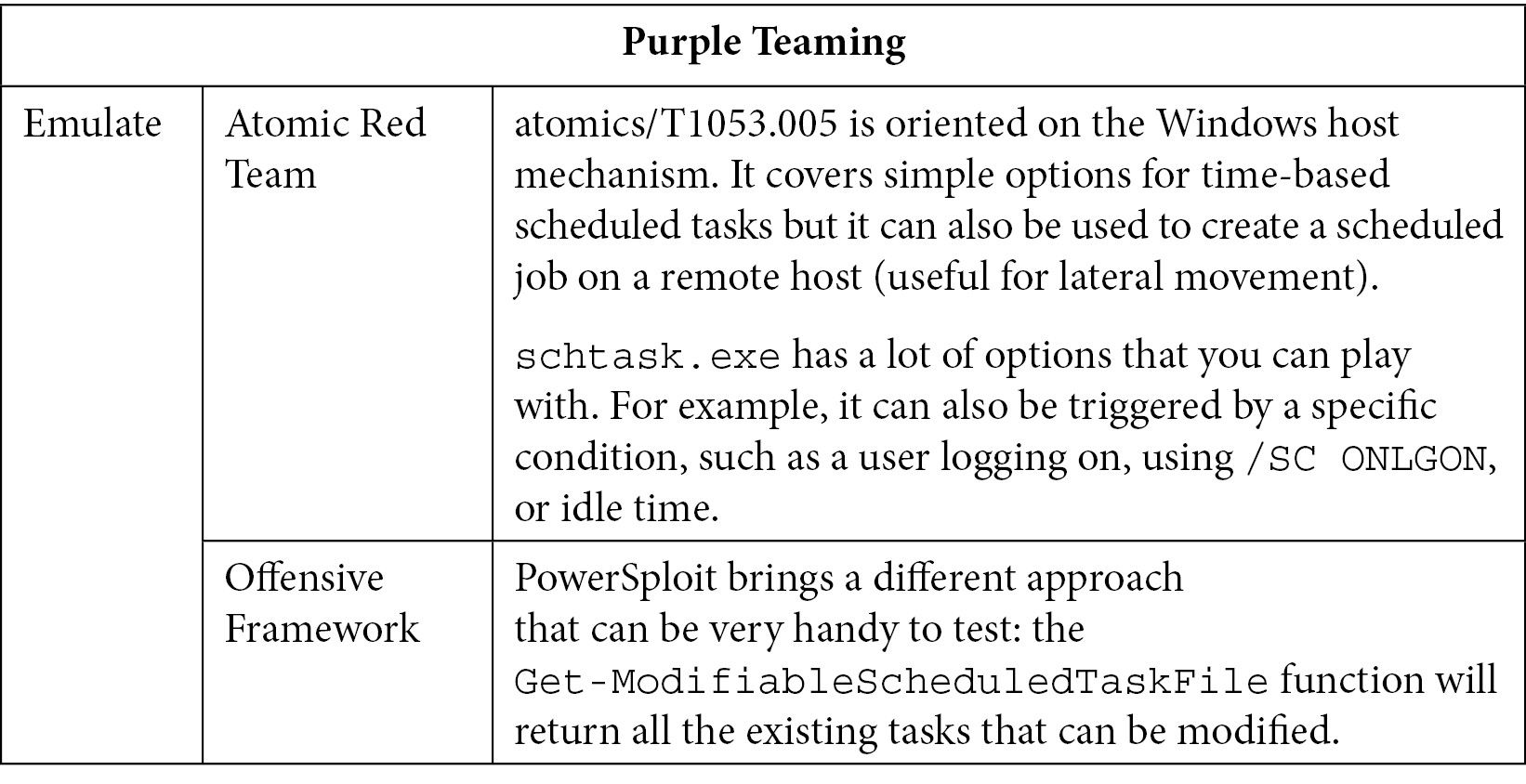
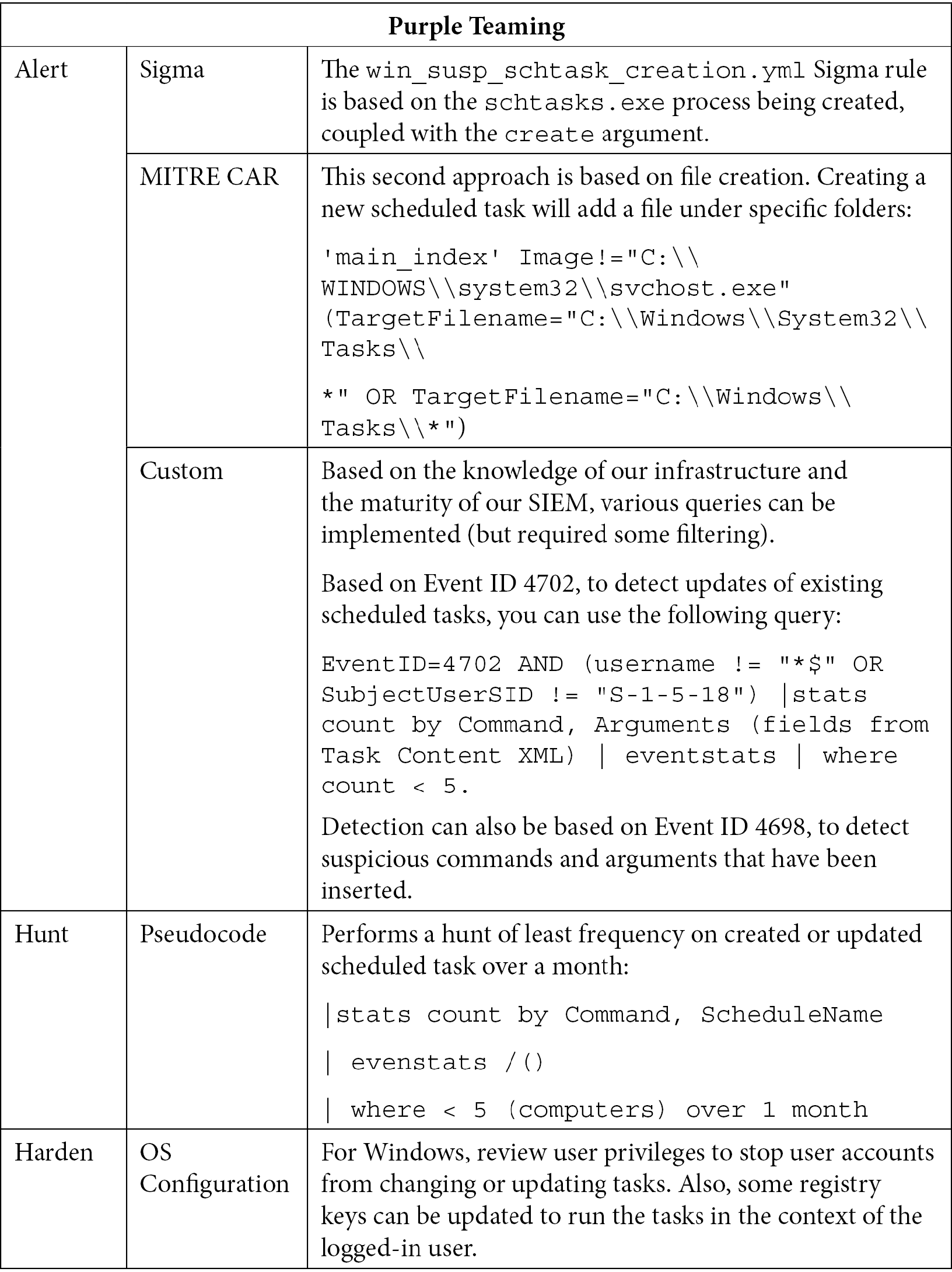
Table 10.5 – Purple Teaming T1053
As we can see, multiple variations based on conditions can be applied to create malicious scheduled tasks (in Windows but also in Linux environments). Hopefully, the logging policy can be updated so that interesting detection events can be logged. Also, tools such as Sysmon do a great job of adding visibility to catch this technique. Finally, some EDRs are also capable of detecting such techniques, but they mostly rely on parent-child process creation. Now, let's look at another technique that's widely used by attackers and malware: boot or logon autostart execution.
T1547 – Boot or logon autostart execution
This technique relies on the fact that, during boot or logon, most OSs will load and execute specific programs or actions to load applications or change settings, and so on. This is interesting because most of the actions that need to be done are often linked to specific objects. Therefore, by simply adding their malware to the list of predefined programs, attackers can create persistence and execute code when the endpoint is starting; it will also allow them to blend their malicious actions with legitimate ones.
From moving a file to a simple folder or even changing a registry key to a more advanced shellcode injection to start an application dynamic-link library (DLL), this technique can be found in tens and tens of methods – MITRE ATT&CK has identified 15 different techniques. So, first, we will mostly focus on emulating and validating the registry key and startup locations since both represent the most used sub-techniques, from automated malware mechanisms to APT groups:
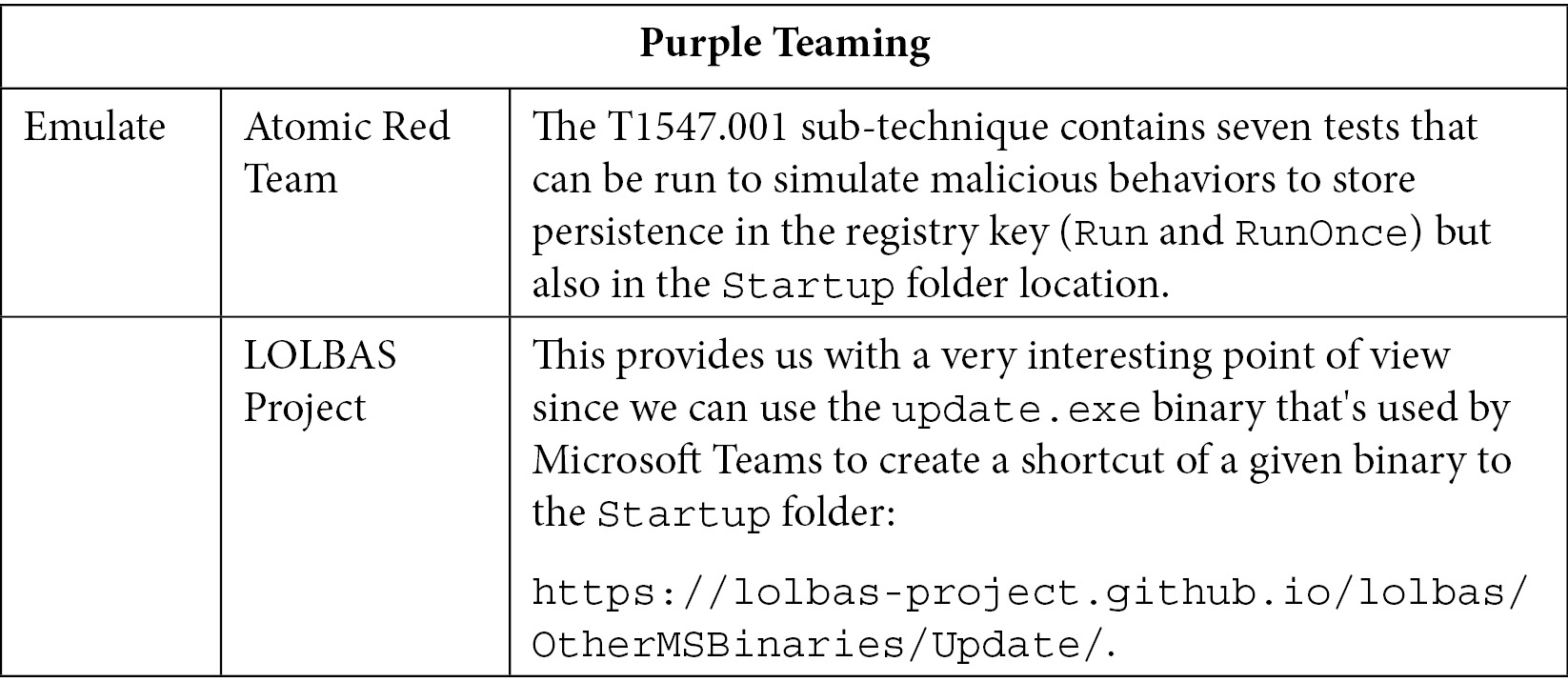
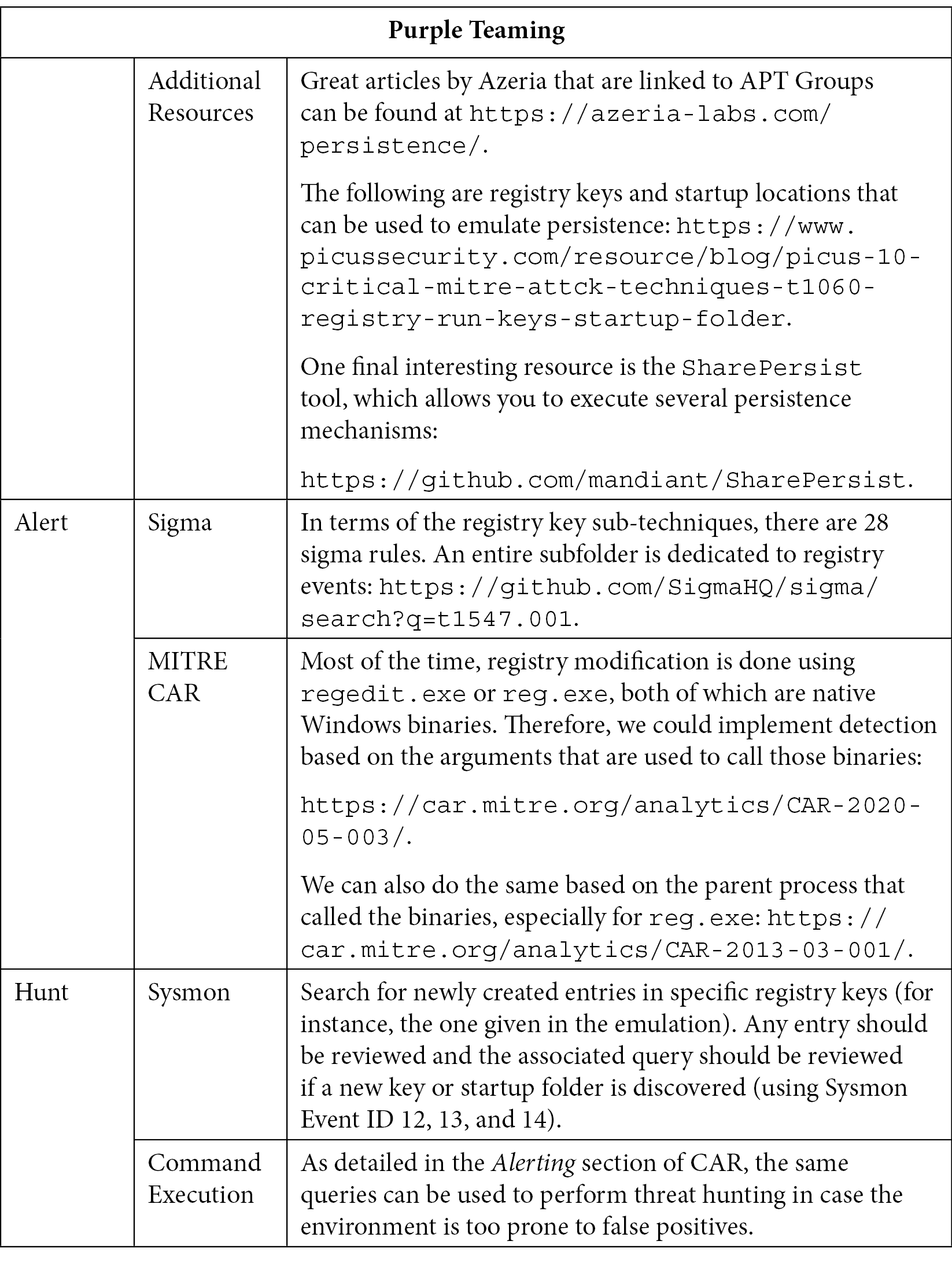
Table 10.6 – Purple Teaming T1547
Unfortunately, we cannot find methods to prevent the abuse of registry keys and startup folders as both are OS features. Monitoring registry key modifications and command-line execution are very helpful and powerful for detecting malicious usage of such features. Several Sysmon configurations exist to reduce the noise of the legitimate usage of registry keys, but as always, testing and fine-tuning should be done for each environment.
Once the attackers can persist inside the initially compromised hosts, the next thing they will do is elevate their privileges inside the infrastructure.
Privilege escalation
This step of the kill chain aims at gaining higher permissions on the compromised system. High privileges on a system allow the user – in our case, the attacker – to perform any kind of desired actions, typically to gain access to sensitive information such as credentials or to disable security solutions. To perform a privilege escalation, an attacker will leverage different kinds of techniques, such as exploiting a vulnerability, obtaining the credentials of an administrator user, taking advantage of the system's weak configuration, and so on.
In this section, we will explore a trendy technique called T1055 – Process injection, which has many different sub-techniques. Another great technique that we will not cover but is worth looking at is the MITRE ATT&CK technique known as T1543 – Create or modify system process and, more specifically, its sub-technique, T1543.003 – Windows service. This sub-technique is worth understanding more deeply and should be less complex to detect than T1055 – Process injection.
T1055 – Process injection
Process injection is an interesting technique from an attacker's point of view as it can be used to escalate privileges but also bypass defenses. Therefore, this technique is listed twice in the MITRE ATT&CK framework – once in the privilege escalation tactic and once in the defense evasion tactic. We will focus on the first objective here, which is to elevate privileges.
We will not dive deeply into Windows and Linux internals to fully understand how files are executed inside the OS's memory. But, we still need a quick introduction to understand this technique. Executable files are designated a dedicated memory space to be loaded and executed. Once running, they can use this address space to perform actions and interact with other processes and objects.
Process injection is used to inject code within the address space of another process so that the targeted process will make it run for us. This can help bypass defenses as the behavior will appear to come from a legitimate process. As we mentioned previously, it can also escalate privileges as the code is executed in the memory address space of a process that has potentially higher privileges.
As MITRE explained on its Techniques web page (https://attack.mitre.org/techniques/T1055/), T1055 has various sub-techniques, as follows:
- DLL Injection
- Portable Executable Injection
- Thread Execution Hijacking
- Asynchronous Procedure Call
- Thread Local Storage
- Ptrace System Calls
- Proc Memory
- Extra Windows Memory Injection
- Process Hollowing
- Process Doppelgänging
- VDSO Hijacking
There are other techniques besides these, but it is outside the scope of this book to go through the aforementioned sub-techniques. Again, there are a lot of resources on the internet to help us. One that is worth mentioning is an inventory of Windows APIs that are leveraged by malware for different types of actions such as injection: https://malapi.io/. Not all of them can, alone, perform process injection, but rather a combination of them. This is useful when you're reverse-engineering malware to quickly identify API calls that may indicate process injection. One last resource we would like to mention is this article from the Elastic Security team, which depicts 10 different ways of performing process injection: https://www.elastic.co/blog/ten-process-injection-techniques-technical-survey-common-and-trending-process.
From a CTI perspective, MITRE has highlighted the fact that around 40 different kinds of software/malware use this technique. The famous downloaders/droppers known as Trickbot, IcedID, and Qakbot are part of this list and are known to inject themselves into legitimate processes such as explorer.exe, iexplorer.exe, and so on. We can also list known ransomware such as Ryuk and REvil or the Powershell Framework Empire, which has a known module named Invoke-PSInject. Cobalt Strike also has process injection capabilities that are leveraged by attackers.
Now, let's go through the Purple Teaming table for this attack. For ease of reading, this table has been split into two parts. First, let's look at the red team part:
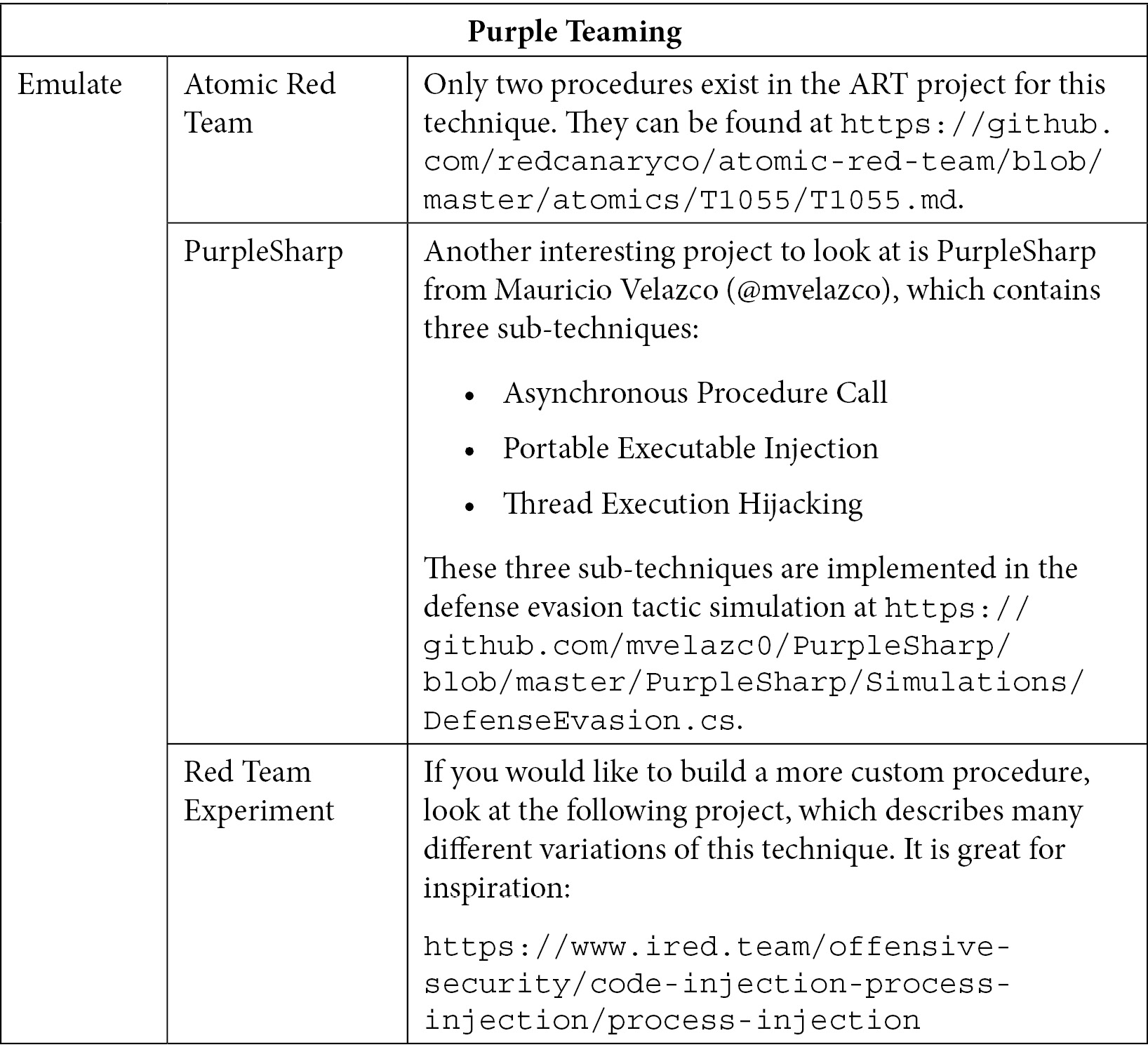
Table 10.7 – Purple Teaming T1055 – Red
Now, let's look at the blue team part:
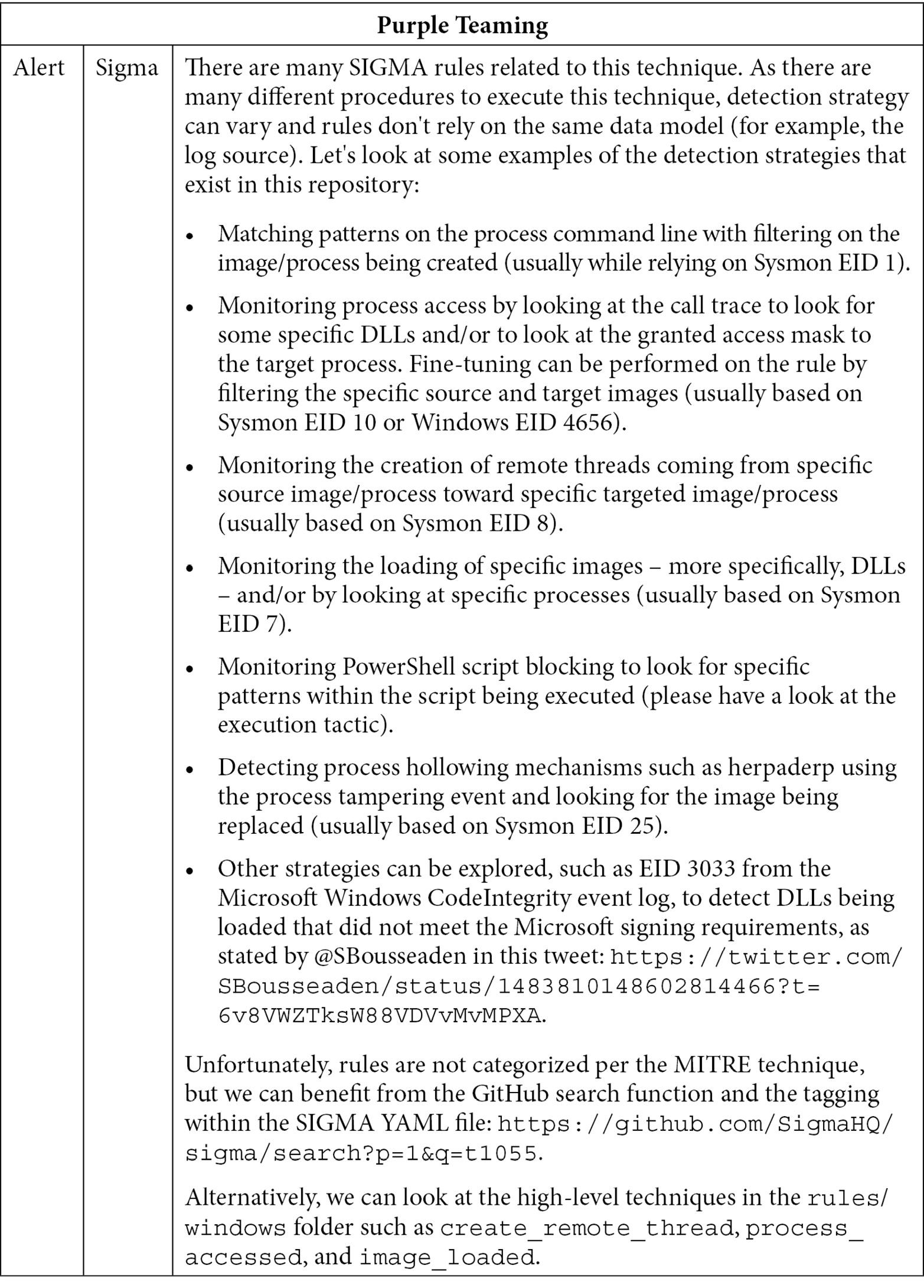
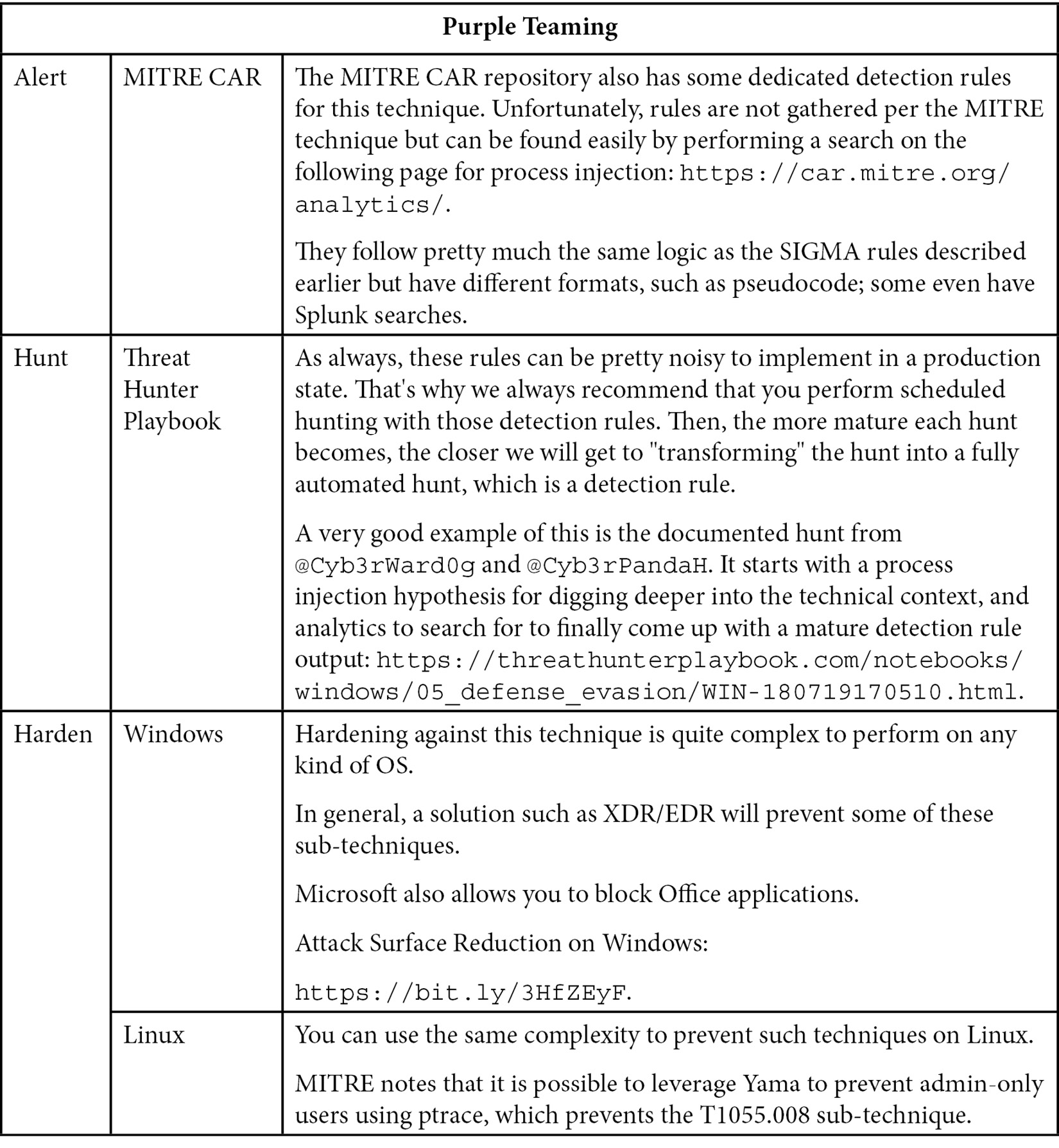
Table 10.8 – Purple Teaming T1055 – Blue
Next, we will deep dive into a very popular technique known as T1218 – Signed binary proxy execution from the defense evasion tactic. But first, let's briefly introduce the goal of this tactic.
Defense evasion
This step of the kill chain refers to the fact that attackers may leverage different techniques to bypass prevention mechanisms and avoid being detected by security systems and the blue team. It is a key component of any threat actor's campaign.
Now, let's look at one very common defense evasion technique that's used by different malware – the signed binary proxy execution technique.
T1218 – Signed binary proxy execution
As tools are becoming more and more sensitive, editors must be careful while whitelisting legitimate OSs and application behavior, processes, and files as this may open a window of opportunities for the attackers. For this technique, digitally signed Microsoft binaries are leveraged on the Windows operating system to avoid prevention and detection. This is also known as Living Off the Land Binaries and Scripts (LOLBAS). The following GitHub project documents all of these: https://github.com/LOLBAS-Project/LOLBAS.
As an example, it involves the Windows signed binaries for the sub-techniques related to mshta.exe, msiexec.exe, regsvr32.exe, and rundll32.exe, to mention a few.
In this section, we will mainly focus on rundll32.exe, which is the Windows host process of the Windows operating system. This binary will execute DLLs, which are shared code libraries that can be used (loaded) by any application. As we will see, attackers have become very creative, and this technique is quite popular among them.
According to MITRE, around 15 identified threat actors are using this sub-technique, as well as around 50 different software and tools, to bypass antivirus, application control, and digital certificate validation. Some famous ransomware threat actors such as Egregor, Ryuk, and Conti but also Hafnium, which is known for its campaign targeting Microsoft Exchange and also the allegedly Iranian MuddyWater Group. The Cobalt Strike software can also use this technique as some of its modules have been developed as DLLs.
Now that we understand its tactics, techniques, and sub-techniques, let's look at the various types of procedures that exist and how we can emulate some of them using the Atomic Red Team project.
But first, let's have a quick deep dive into how rundll32.exe works. Its command line is quite simple as rundll32 will take a DLL as an argument. However, more advanced variations exist, which we will look at shortly. Let's have a look:
- Executing a DLL:
rundll32 myDLL
- Calling a specific function by its name within the selected DLL with no arguments:
rundll32 myDLL,myFunction1
- Calling a specific function by its name within the selected DLL with arguments:
rundll32 myDLL,myFunction2 arg1,arg2,arg3
- Calling a specific function by its ordinal within the selected DLL:
rundll32 myDLL,#1 arg1,arg2,arg3
The MITRE page for this sub-technique (https://attack.mitre.org/techniques/T1218/011/) mentions various procedures that have been used by different attackers. We could go through all of them and try to pick up the trendier procedures, but fortunately for us, we don't need to. Olaf Hartong (@olafhartong) presented his research called "Who littered the sandbox? Scooping up new malware behavior" at HITB Cyberweek in the United Arab Emirates in November 2021. This talk is a great example of how malware analysis can help build a CTI that then feeds back to the blue team for detection and prevention purposes. Olaf managed to analyze more than 800,000 samples of malware from more than 4,000 malware families and was able to extract interesting trends. One in particular concerns this sub-technique and describes the most common function names that can be called with rundll32 by these malware samples. Here are the top five:
- DLLRegisterServer
- TestRasm12
- Control_RunDLL
- Connectdark
- RunDLL
Function names are specific to the DLL, so some of the names don't give us much information unless we reverse-engineer the DLL. However, this research highlights that the DLLRegisterServer function name is by far the most used and has been used, at least at one period in time, by malware such as Qakbot, Trickbot, Ashadow, Dridex, and Zloader.
This name allows attackers to leverage the Windows Component Object Model COM), which is an Application Binary Interface (ABI) that acts as an interface between binaries. More specifically, DLLRegisterServer must be an export of the called DLL and is normally used to register a COM object in the Windows registry (so that other applications can interact with this object). Since the function is called DLLRegisterServer, it looks legit, and it also allows an attacker to have a second bypass opportunity. Indeed, one last important point to mention is that this rundll32 command line is equivalent to calling regsvr32.exe with the DLL as an argument (only that regsvr32 requires a mandatory export function named "DLLRegisterServer"). Therefore, you may wish to investigate the T1218.010 sub-technique to be able to catch more variations of the same technique.
Other procedures are worth looking at as well, such as rundll32 using JavaScript, VBScript, and so on. The following is the Purple Teaming summary table for this technique. For ease of reading, this table has been split into two parts. Let's look at the Red Team part first:
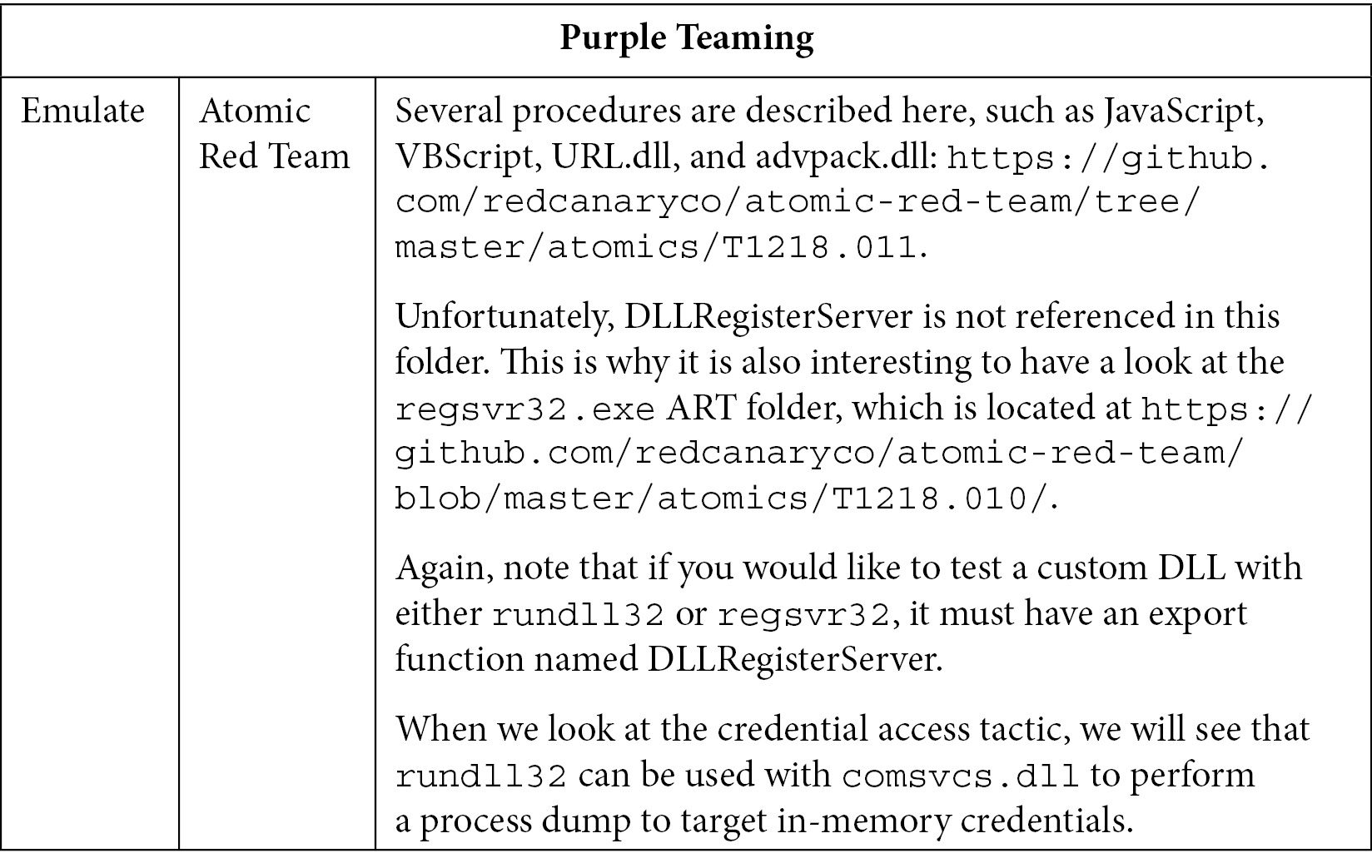
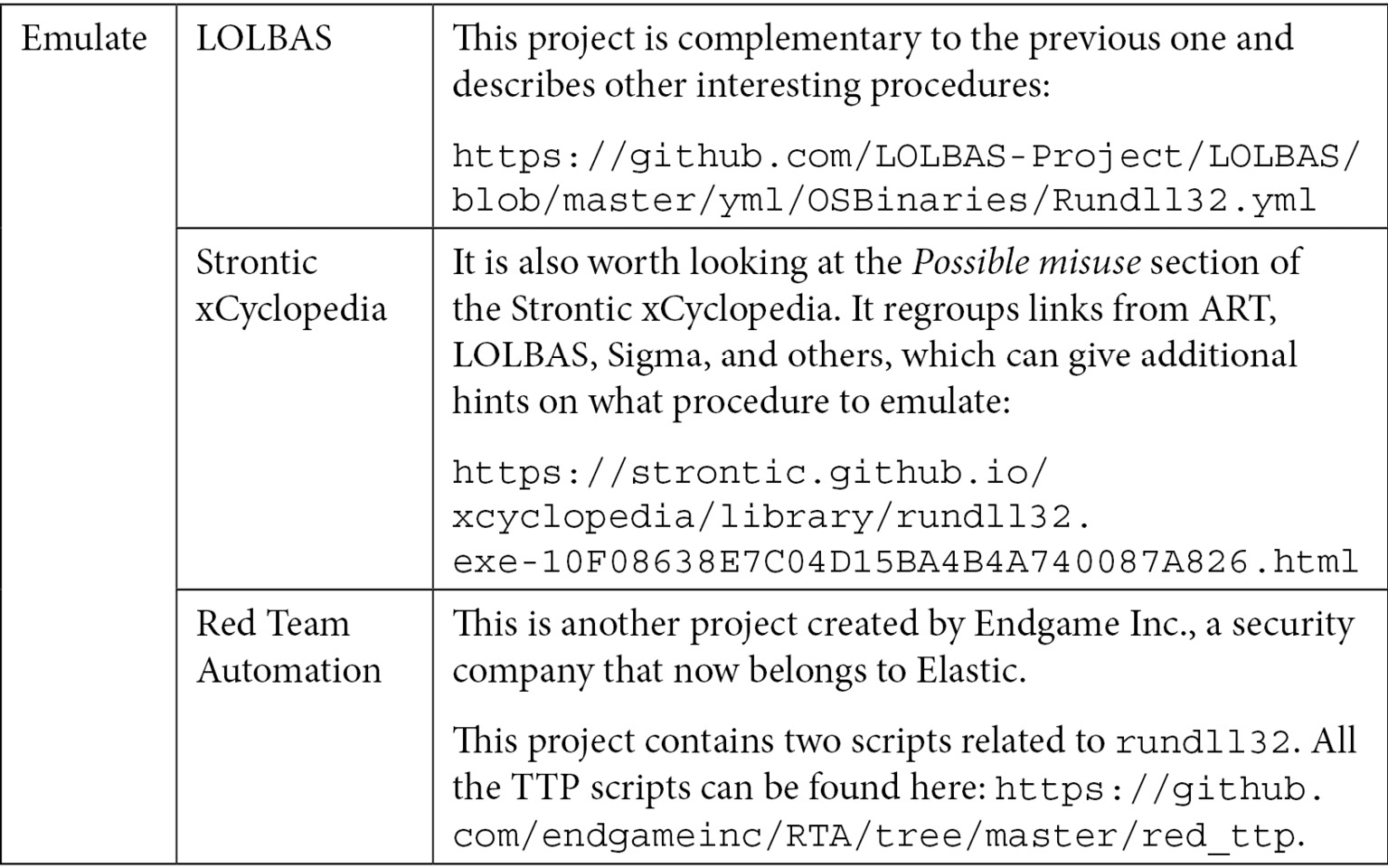
Table 10.9 – Purple Teaming T1218 – Red
Now, let's look at the blue team part:

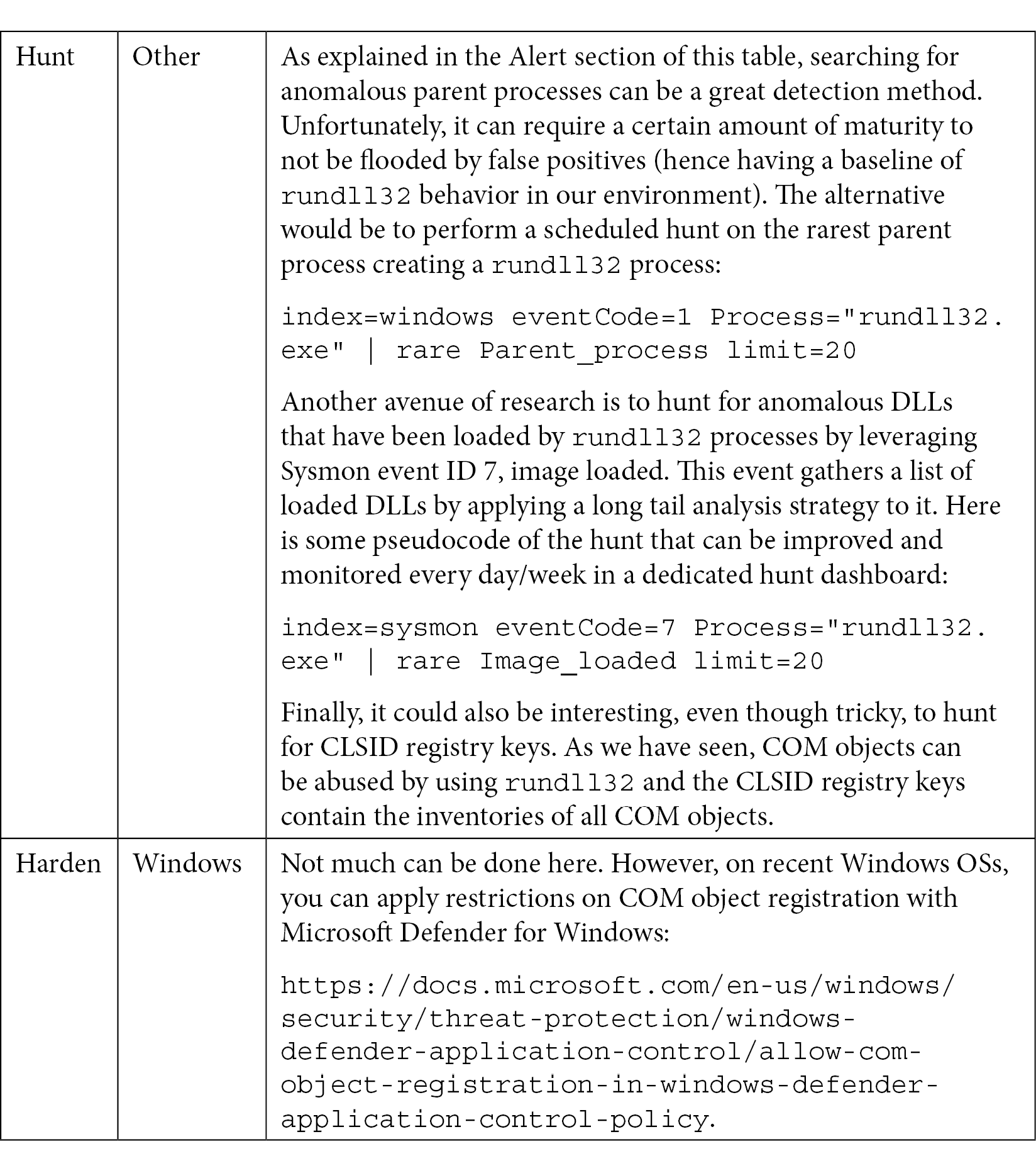
Table 10.10 – Purple Teaming T1218 – Blue
Now, let's look at the credential access tactic, which is pretty much always performed by attackers.
Credential access
Once an attacker gets remote access within an organization's network and has enough privileges on that machine, there are extremely few chances that it will stop there and try not to compromise other assets. Its objective is likely located in other assets. But to move laterally on other systems, it will often need to possess the relevant credentials. That is when the credential access tactic occurs.
Credential access is a key step within the kill chain and can be used many times, depending on the need of the cyber operations that are being conducted by the threat actor. Its goal is to retrieve credentials in the form of username and passwords, tokens, or password hashes.
In this section, we will look at one of the most famous sub-techniques that's leveraged by threat actors called T1003.001 – OS Credential dumping: LSASS memory. Another technique that will not be covered but that is also quite trendy among threat actors is the T1555 – Credentials from password stores technique, as well as its sub-technique, T1555.003 – Credentials from web browsers.
T1003 – OS credential dumping
As we mentioned previously, the goal of this technique is to retrieve credentials on a system (more specifically, from the Windows LSASS process memory) when dealing with the T1003.001 – OS Credential dumping: LSASS memory sub-technique. Since this is one of the trendiest credential access techniques, we will explore it here.
First, LSASS refers to the Local Security Authority Subsystem Service, which is responsible for the local authentication of a user on a local system. We will not go too much into the details of the authentication mechanisms provided by LSASS, but it is worth noting that it can rely on so-called authentication packages (APs), sub-authentication packages, or security support providers (SSPs). Two well-known APs are provided by default by Microsoft on Windows, Kerberos, and MSV1_0. A combined SSP/AP can provide its own authentication mechanism, as well as an authentication protocol, with the most famous examples being NTLM and Kerberos.
As we saw regarding the privilege escalation tactic, each process has its own address space where it will perform its work. As we can imagine, accessing the memory of the LSASS process can be quite handy when an attacker needs to gather credentials information from a Windows system. Well, this sub-technique covers exactly this type of action – accessing the LSASS memory. As we will see in the purple teaming table, there are many different ways of achieving this objective.
MITRE states that around 30 actors are leveraging this technique, making it one of the most critical techniques and therefore an important path walk to monitor. Famous threat actors are using it, such as the allegedly Iranian groups MuddyWater and OilRig, as well as Hafnium and APT1. It also inventories around 20 different software and malware that leverage this sub-technique. Again, we can mention pentesting tools such as Powershell Empire, Impacket, and Cobalt Strike, as well as the famous Mimikatz. Legitimate Windows binaries can be used for that purpose too, with the most obvious being procdump.
Now, let's look at the purple teaming table. First, we will look at the red team part:
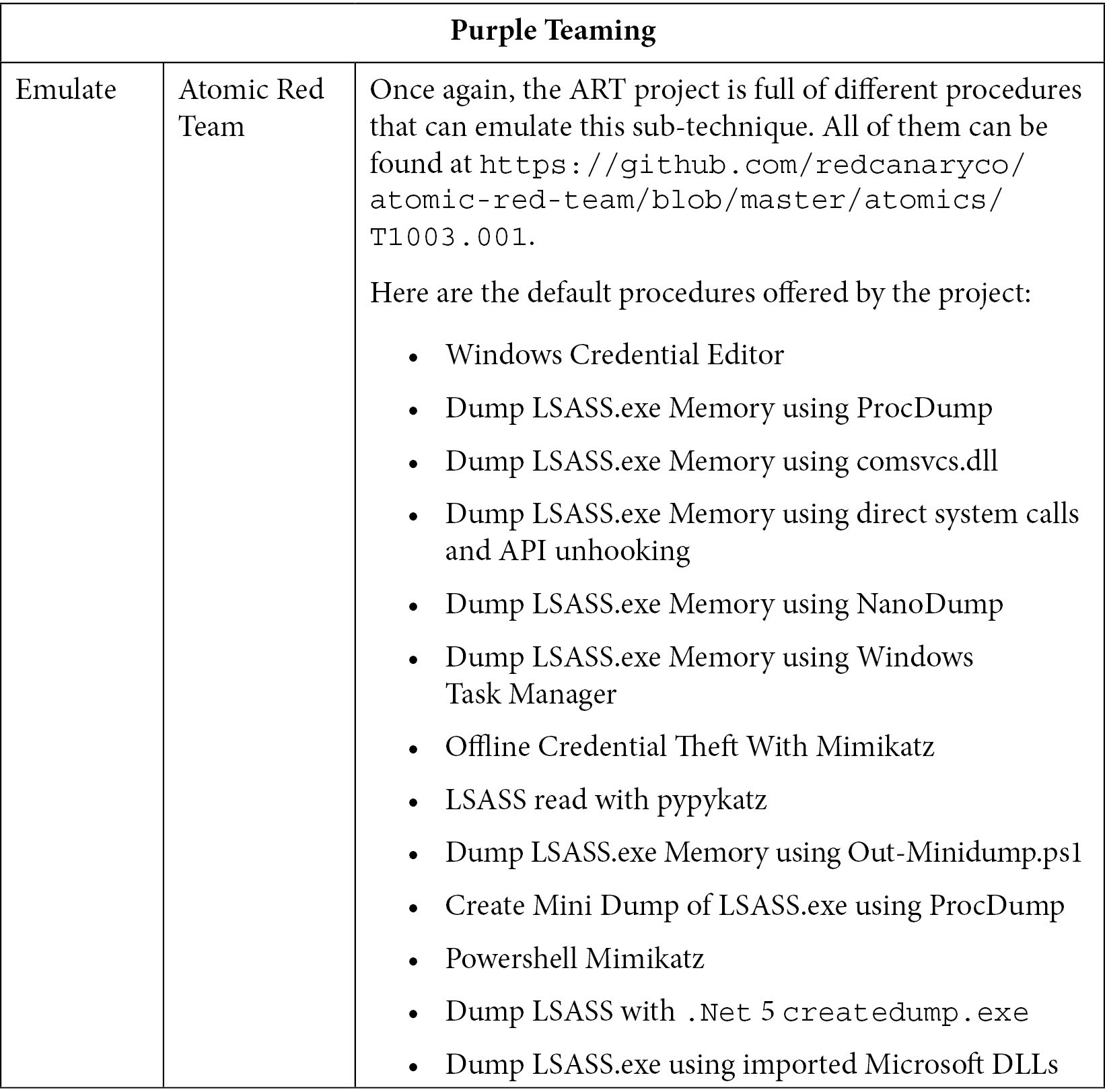
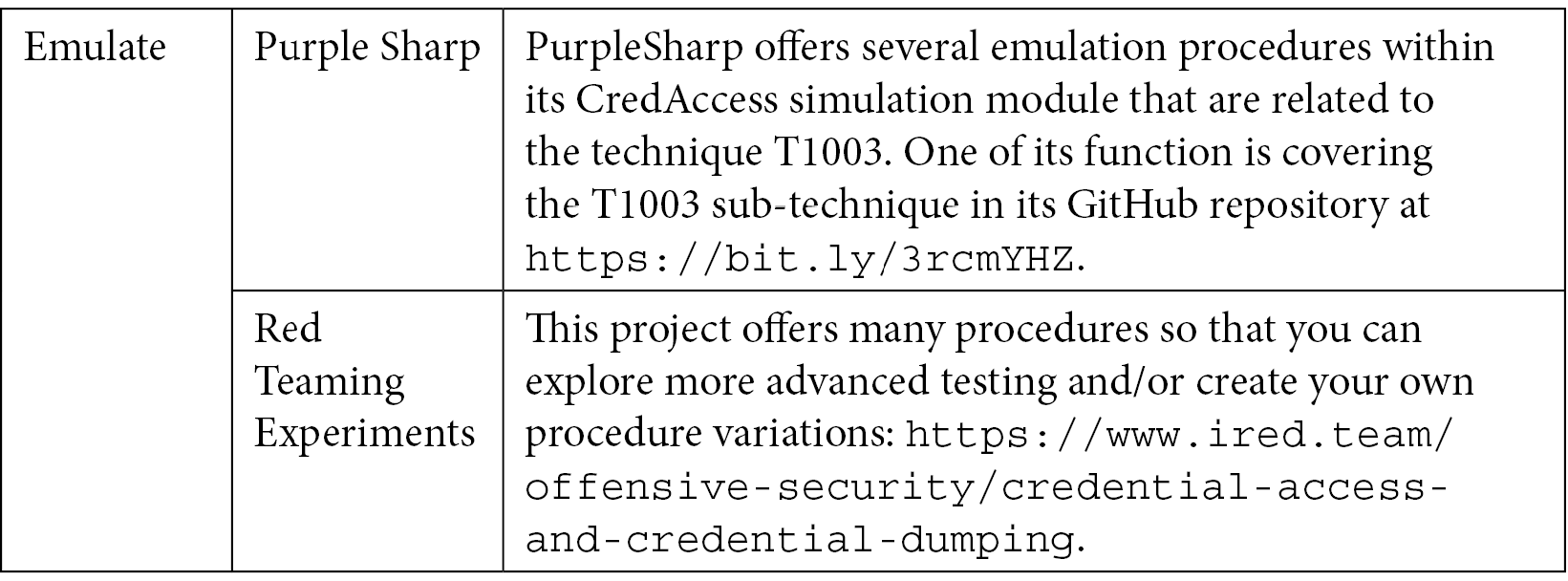
Table 10.11 – Purple Teaming T1003 – red
Now, let's look at the blue team part:
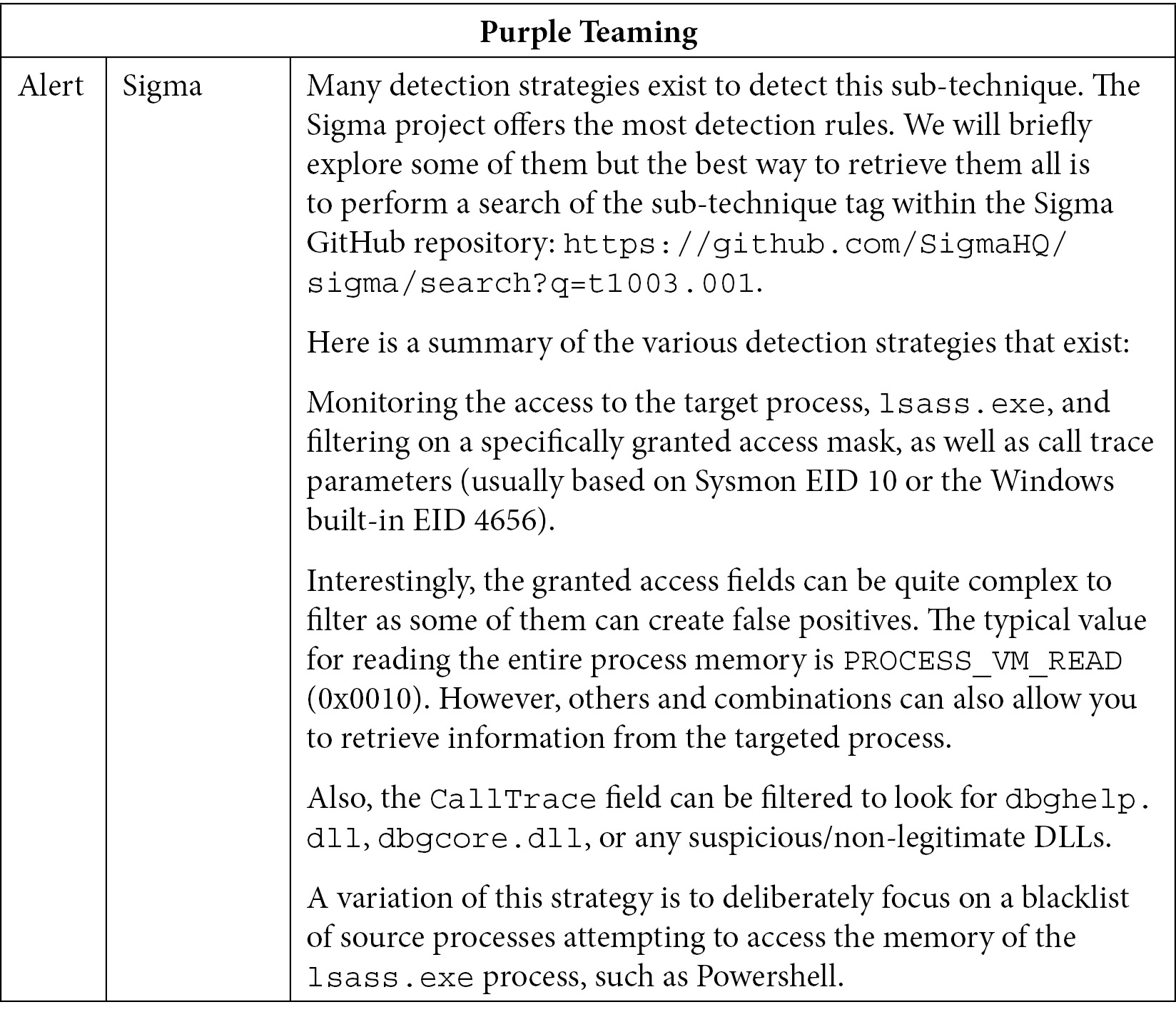
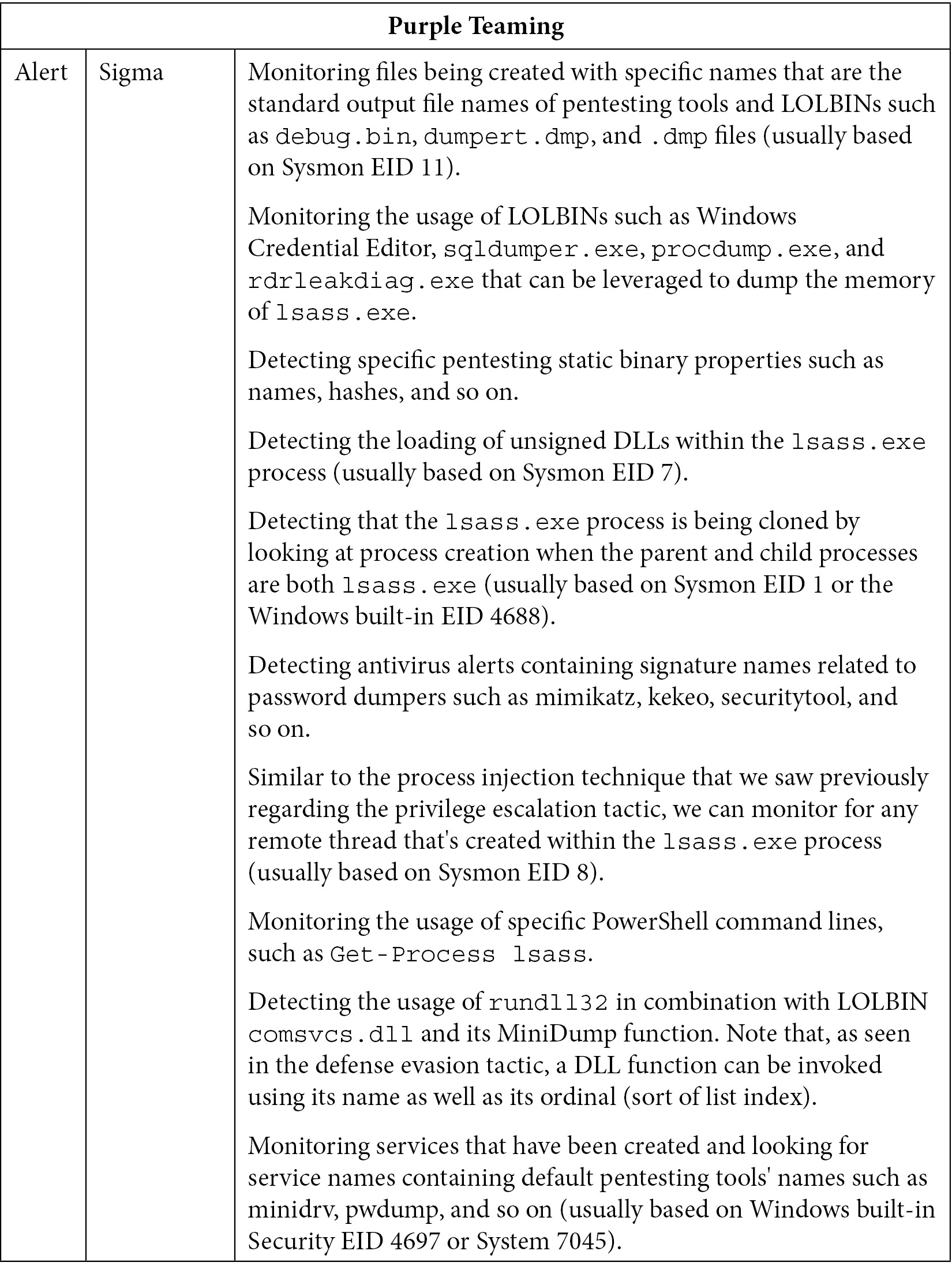
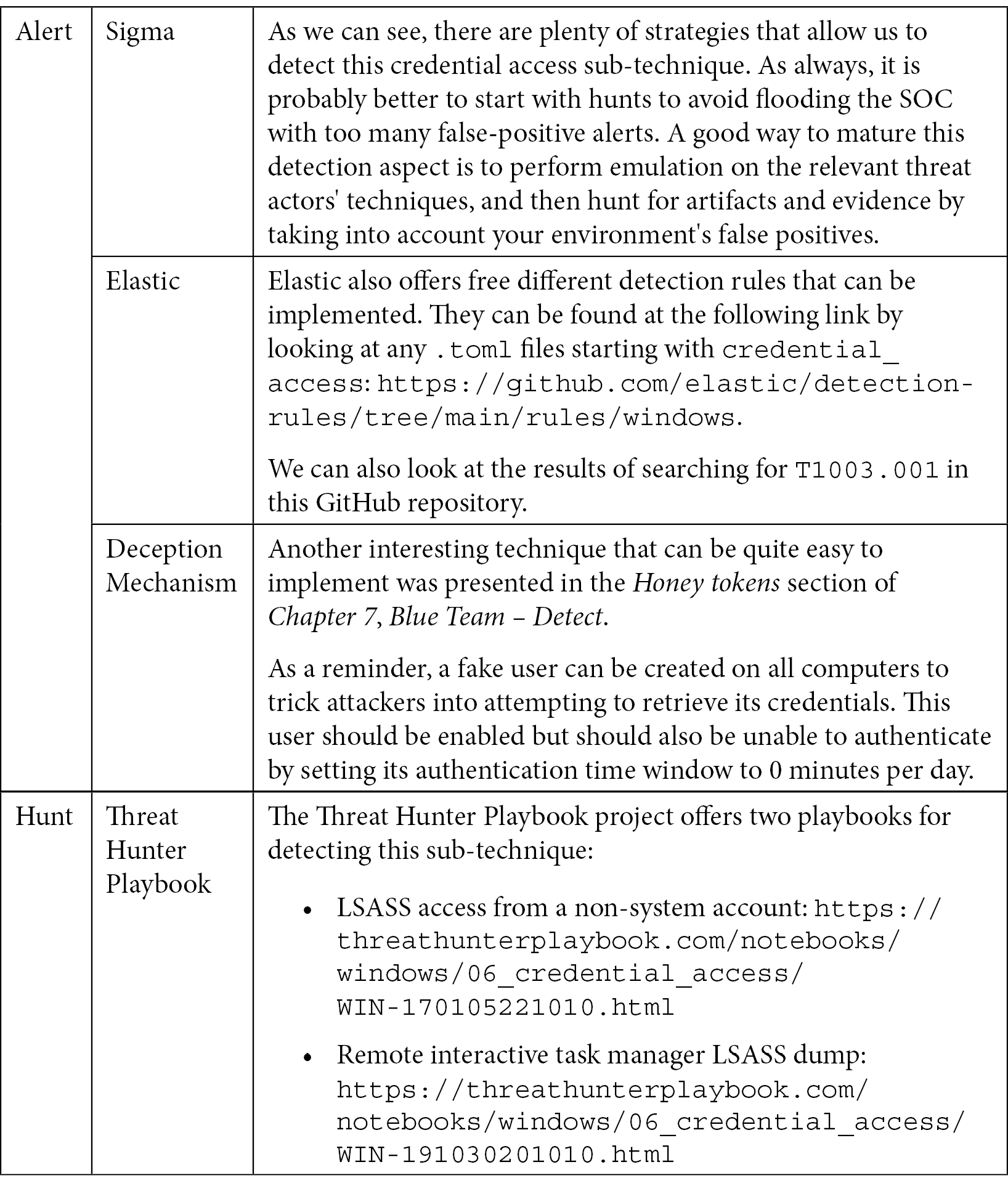
Table 10.12 – Purple Teaming T1003 – Blue
For ease of reading, we have split this table so that hardening is standalone:
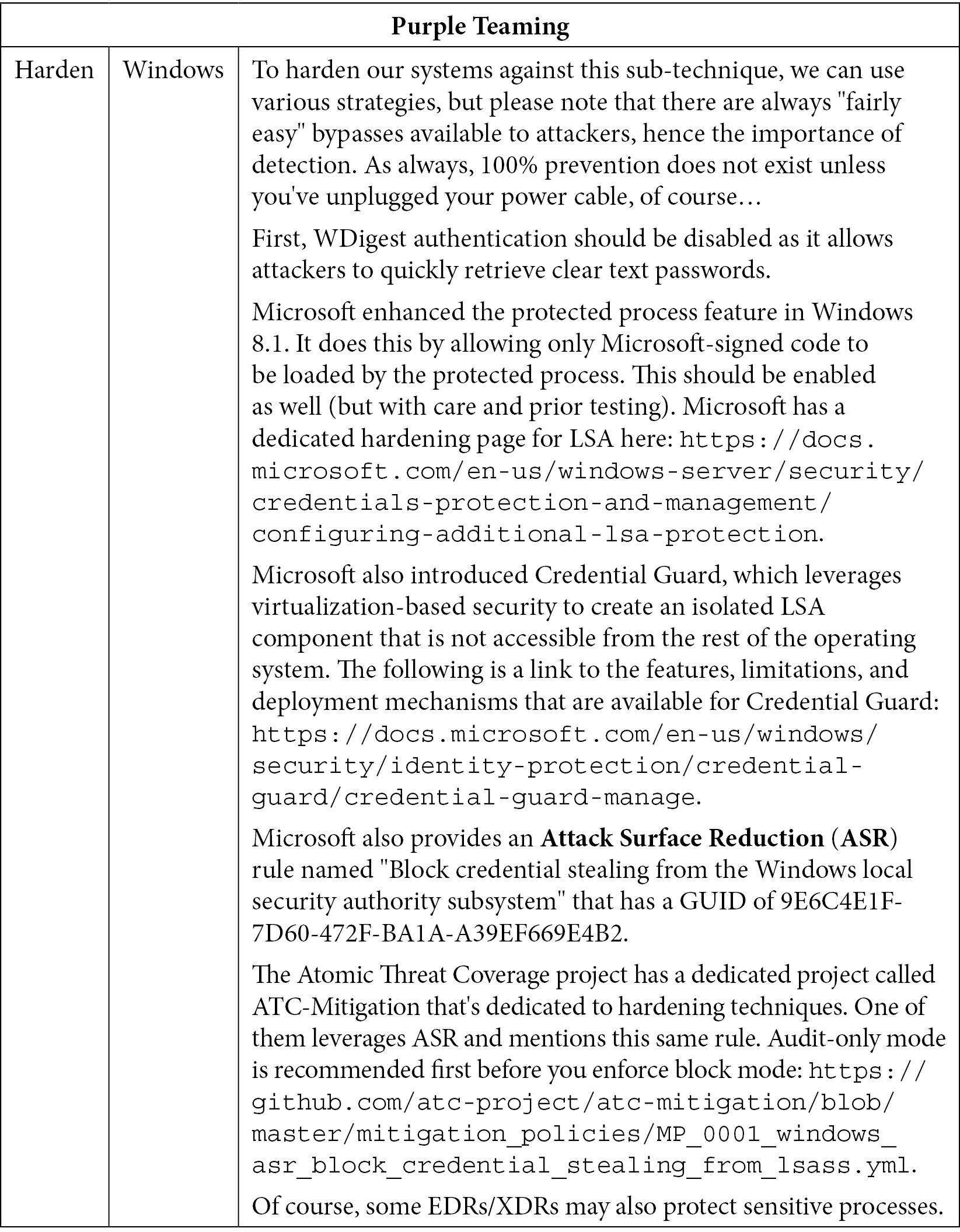
Table 10.13 – Purple Teaming T1003 – hardening
Now, let's see how attackers try to map our network and inventory our assets to identify their objectives and move laterally.
Discovery
When attackers penetrate a network, they usually don't have prior knowledge of the architecture and topology of our networks. Therefore, they must map the network and understand where our crown jewels are to achieve their objectives. This phase usually precedes the lateral movement phase as the attacker needs to figure out where to move. This tactic is also used to better identify the system to which they have access.
In this section, we will look at one technique that's recently been described by public threat intelligence reports: once an attacker has a foothold on a compromised system, they will try to discover other potential lateral movement paths using T1018 – Remote system discovery.
T1018 – Remote system discovery
This technique is widely used by most attackers. Once a host has been compromised, the attacker can usually access local credentials in the form of passwords, hashes, or tokens. From there, attackers are authenticated on the domain and can perform large discovery operations to prepare both lateral movements and privilege escalations; usage of the SharpHound tool is quite common nowadays to help achieve this. SharpHound, combined with BloodHound, can be used to search the shortest path to steal domain administrator tokens. Starting from a host, it enumerates all the domains in terms of computer objects and asks each computer or server which users are connected to it. ADFind is another tool often leveraged. After gathering this information, the attacker builds a full path from it that tells them which tokens to steal and reuse where until they find a domain admin token on a computer where a session has been opened. Let's look at the Purple Teaming table for this technique:
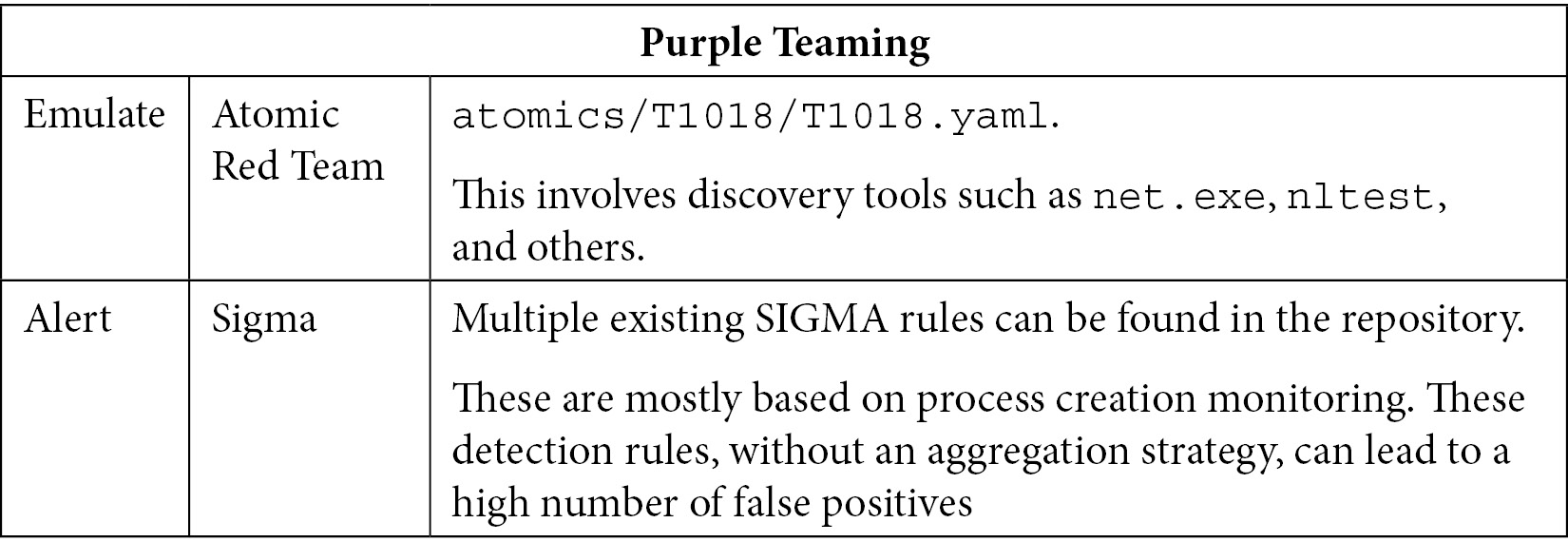
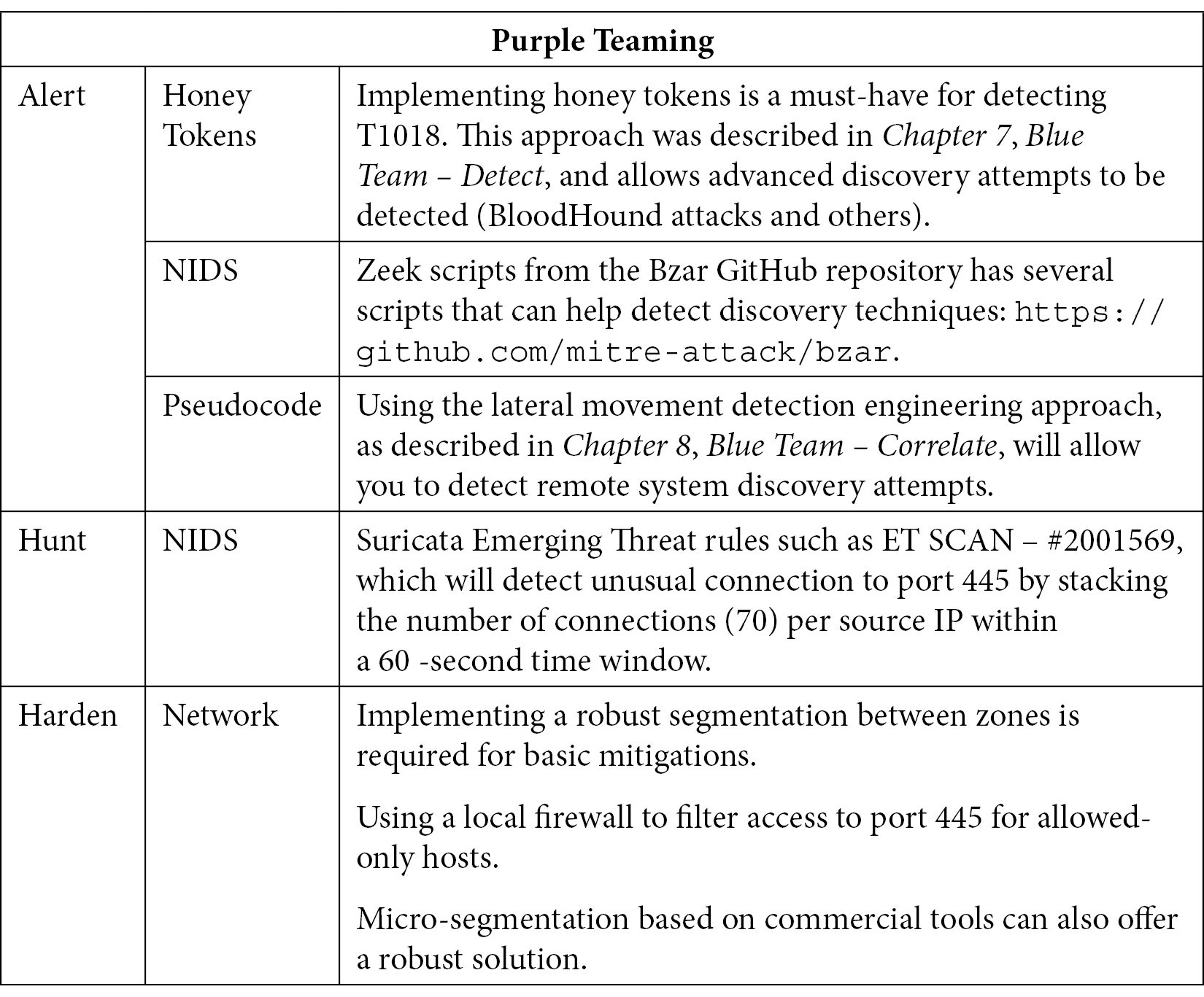
Table 10.14 – Purple Teaming T1018
This discovery technique relies on Active Directory environments, which means it's limited to Windows systems. Another discovery attempt can rely on opened network ports on remote systems. This is why we will also introduce T1046 – Network service scanning.
T1046 – Network service scanning
This technique is used by the vast majority of attackers in the world. It consists of scanning the network to detect up and running hosts and identifying the network services they are exposing. It is also often combined with a vulnerability scanner to identify vulnerabilities on these access ports:
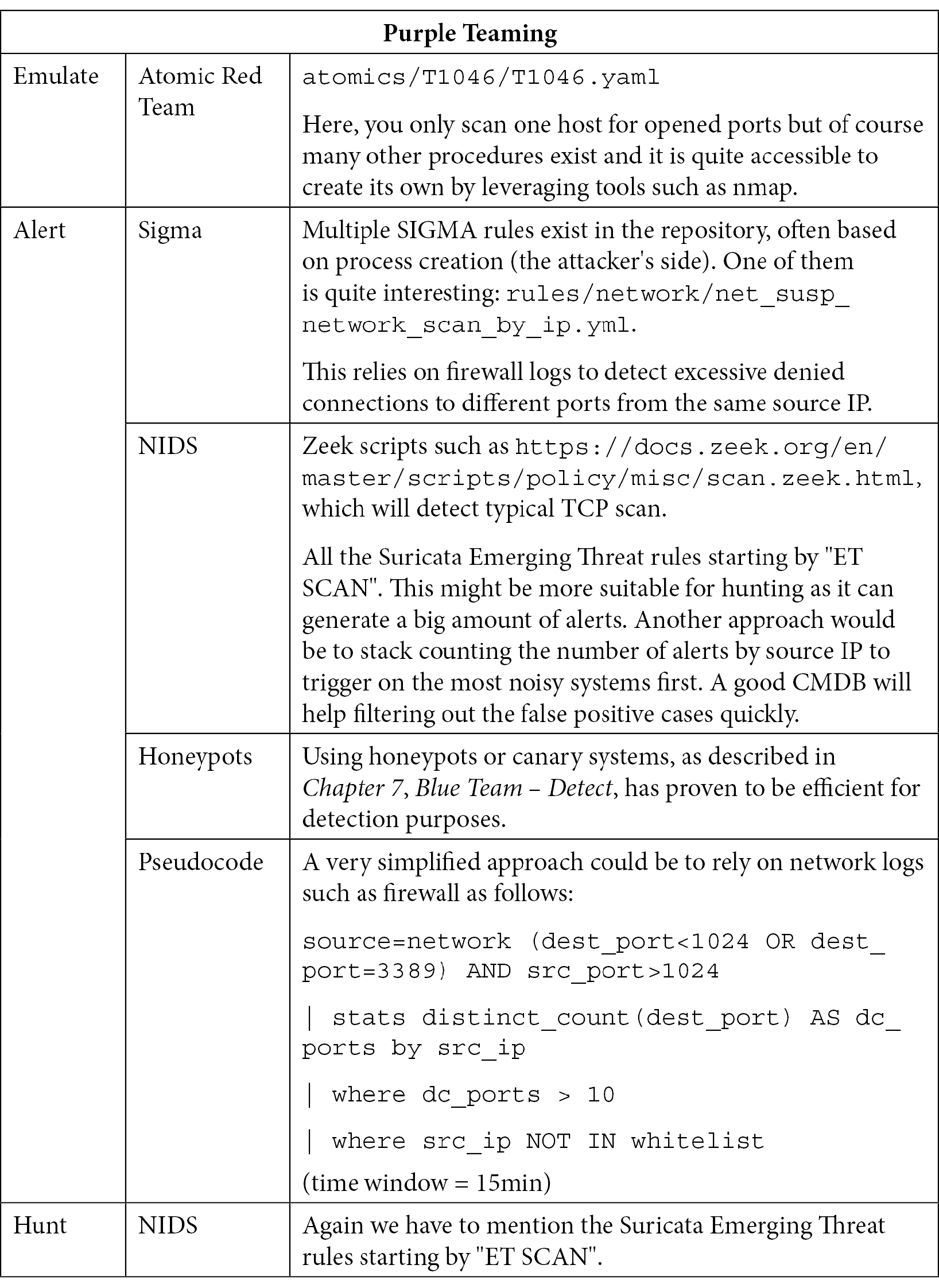
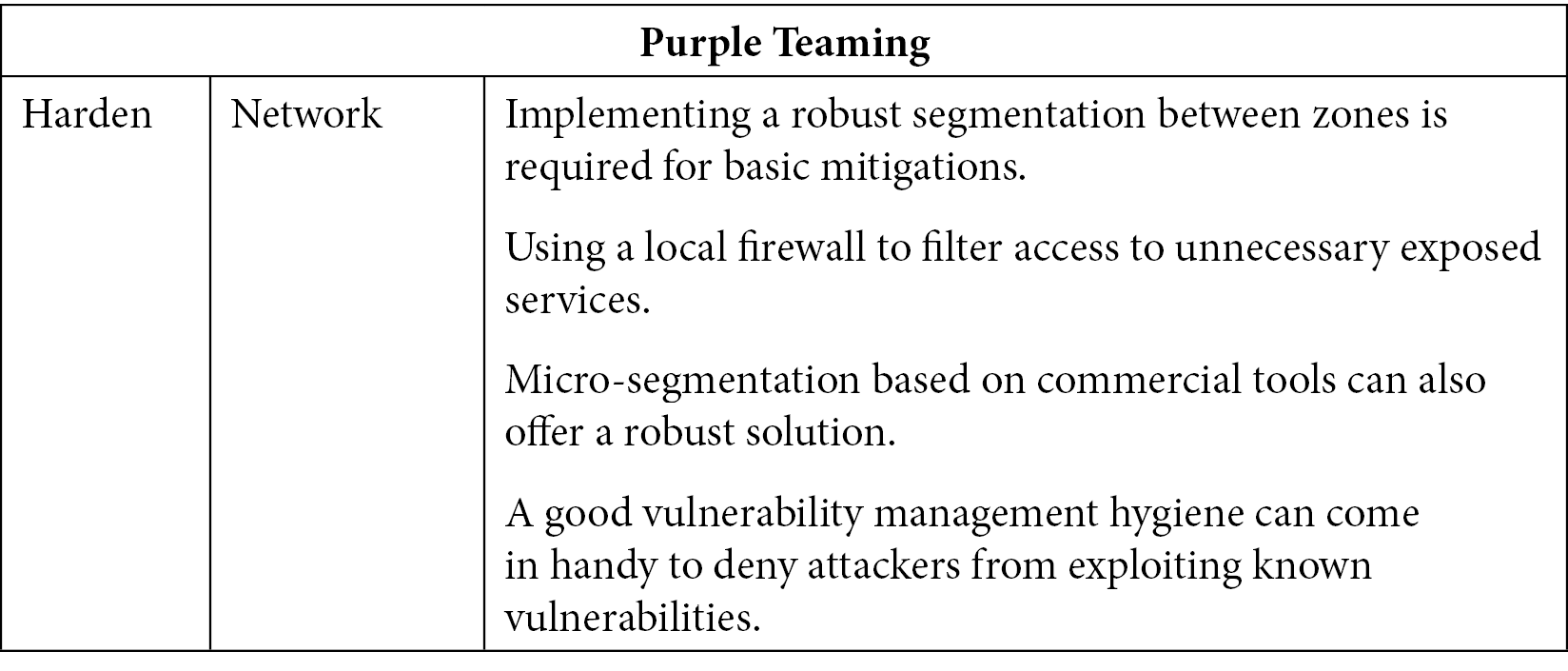
Table 10.15 – Purple Teaming T1046
The next step in the kill chain is lateral movement.
Lateral movement
To achieve their objectives, a threat actor will need to move within our network, allowing us to detect them. As we mentioned in the previous section, the attacker must map the network to know where to pivot inside our information system.
In this section, we will look at various sub-techniques related to the remote services technique, which is largely used by threat actors.
T1021 – Remote services
Once attackers obtain valid credentials, they will use them on all the assets they discovered in the discovery phase. The CTI taught us that they will mostly rely on the following:
- T1021.001 – Remote desktop protocol
- T1021.002 – SMB/Windows admin shares
- T1021.004 – SSH
The good news is that lateral movement detection is quite similar to discovery detection and even covers other lateral movement techniques (relying on WinRM, DCOM objects, and so on):
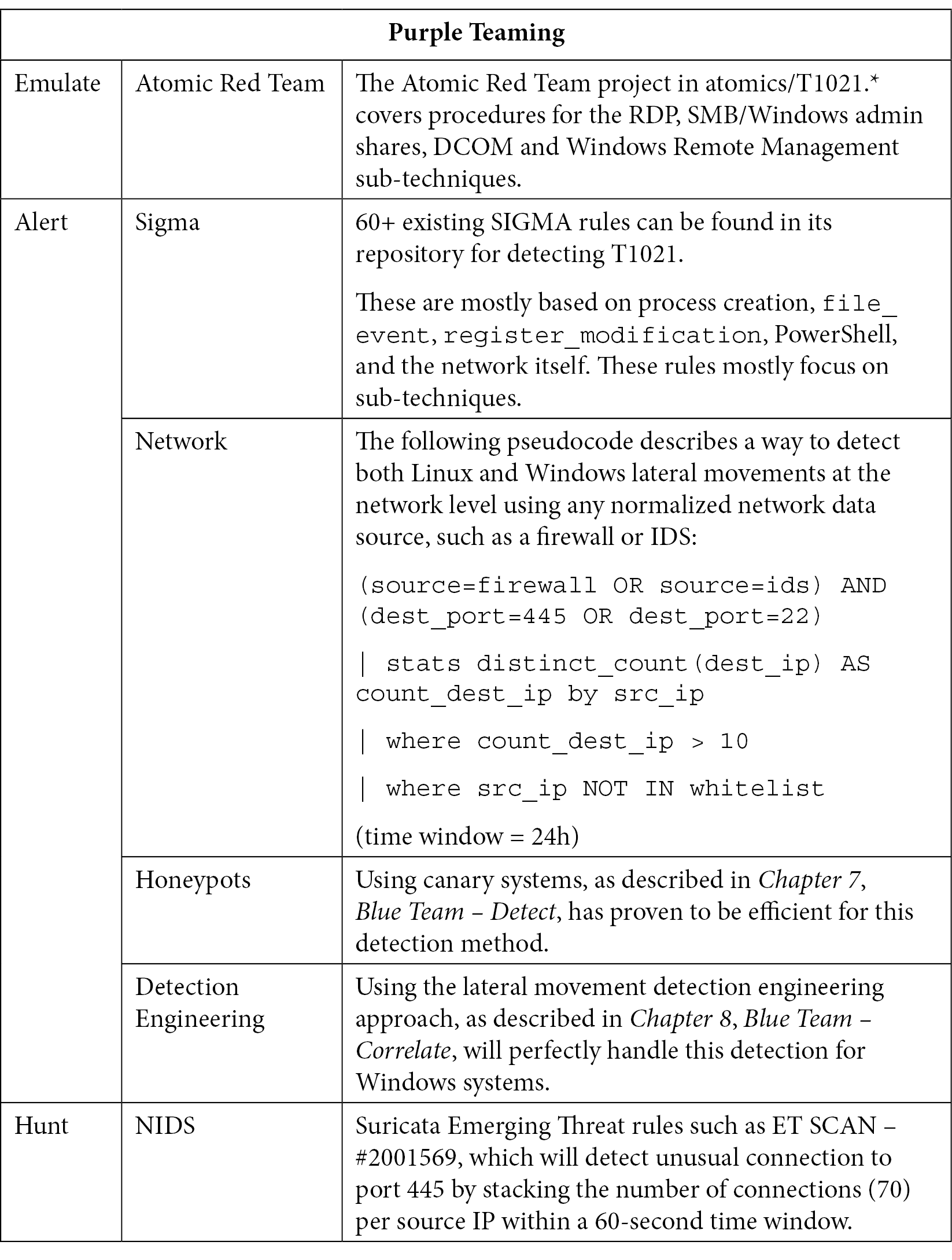
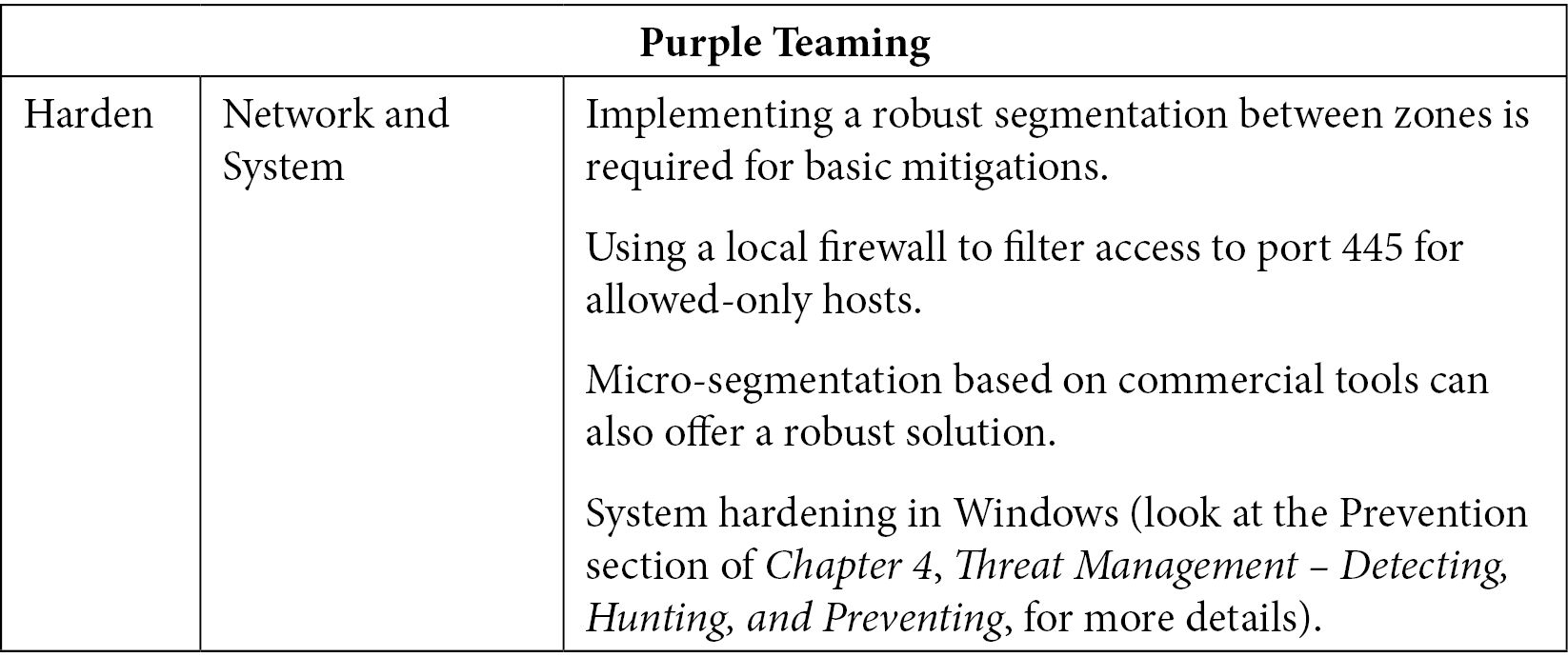
Table 10.16 – Purple Teaming T1021
Once lateral movement has been performed and the attackers have a bigger footprint in the infrastructure, they often collect valuable data.
Collection
Depending on their goal, a threat actor will likely start collecting the relevant information before exfiltrating the data. Of course, various types of information can be collected before exfiltration. These techniques are usually simple but can still be interesting to observe to detect an attacker. One of them that can be detected is known as T1560 – Archive collected data.
T1560 – Archive collected data
When an attacker needs to exfiltrate data, they will usually have to compress it. This can be done legitimately but not in certain conditions, such as out of office periods or when using command-line parameters that use specific paths that are used by APT groups:
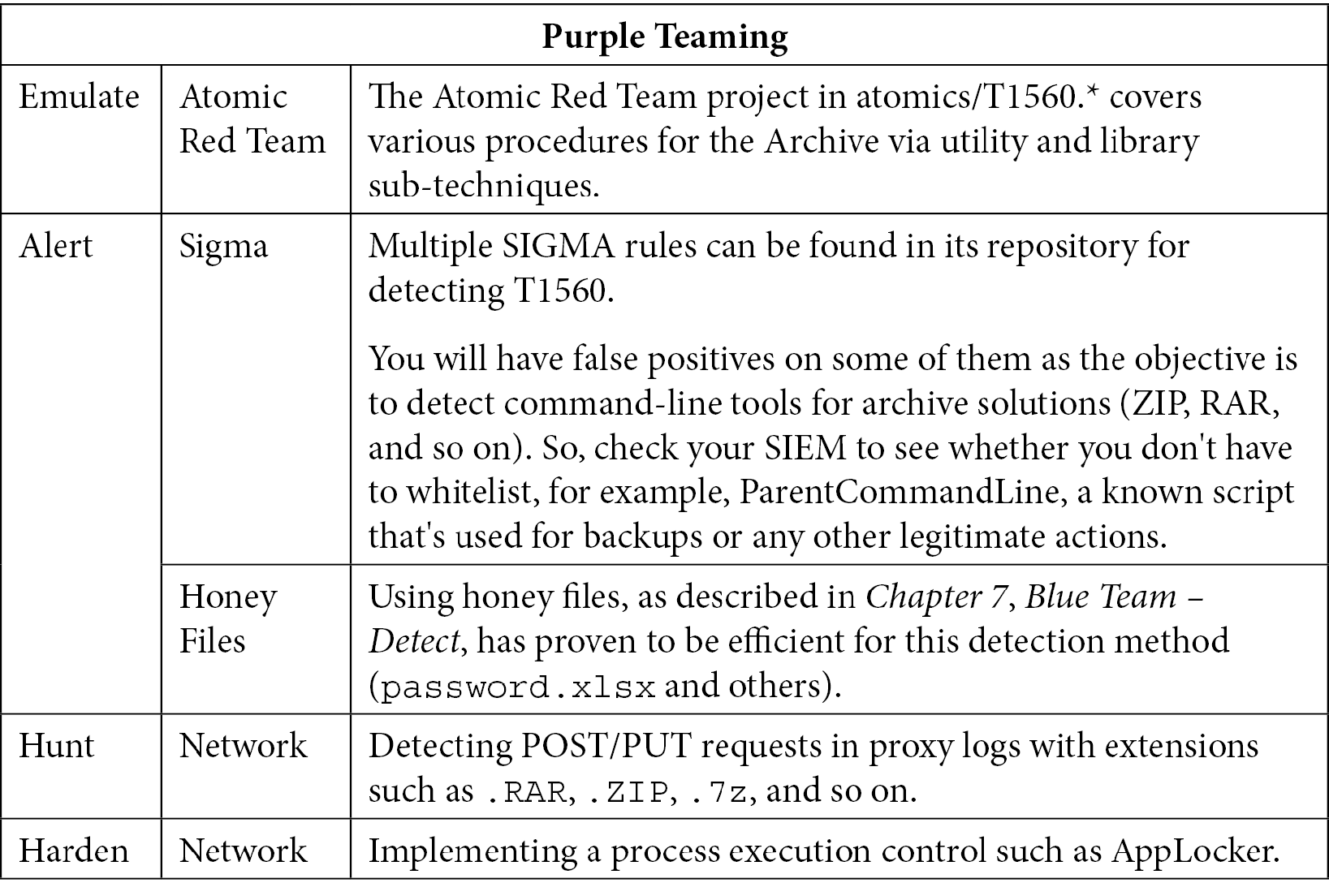
Table 10.17 – Purple Teaming T1560
Command and Control (C2)
Command and Control (C2) refers to a server that's owned by the attacker that's used to communicate and remotely control the compromised systems. This step of the kill chain is continuous through the operation.
T1071 – Application layer protocol
As we've already discussed in this book, especially in Chapter 5, Red Team Infrastructure, attackers usually rely on C2 servers to manage their victims and industrialize exploitations. These servers can use existing protocol application layers such as HTTP, DNS, SMTP, and so on. It even goes deeper by injecting the C2 traffic inside what looks like standard activities. A good example of this approach is Malleable C2 (https://github.com/rsmudge/Malleable-C2-Profiles/tree/master/normal), a collection of add-ons for the Cobalt Strike C2 that allows the attacker to disguise C2 traffic in fake Amazon or Wikipedia traffic, fake certificates for OCSP verification, or simply inside DNS traffic, which is generally hard to detect. Many APT groups use these techniques, which is why it is essential to ensure we can catch or block them by simulating their activities:
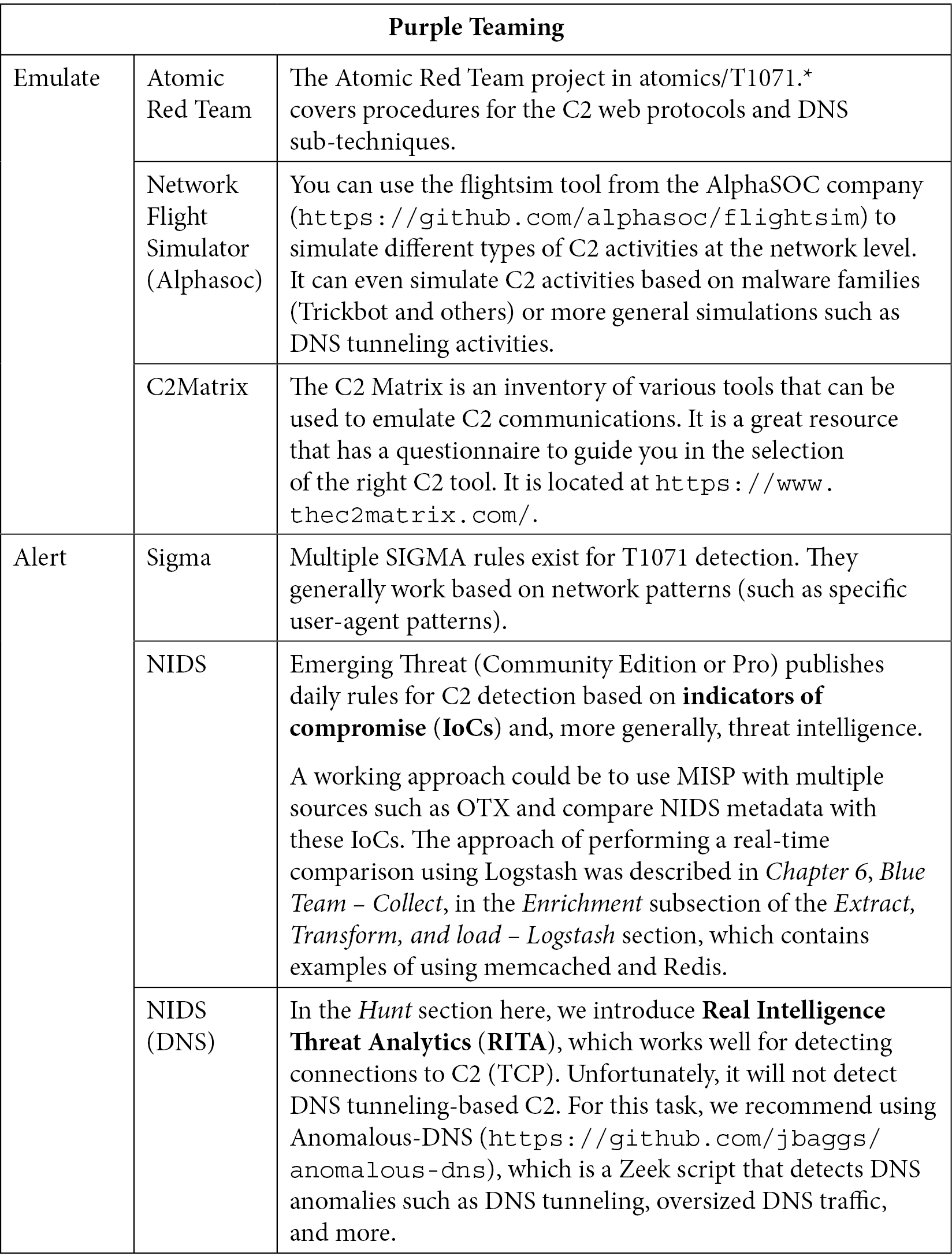
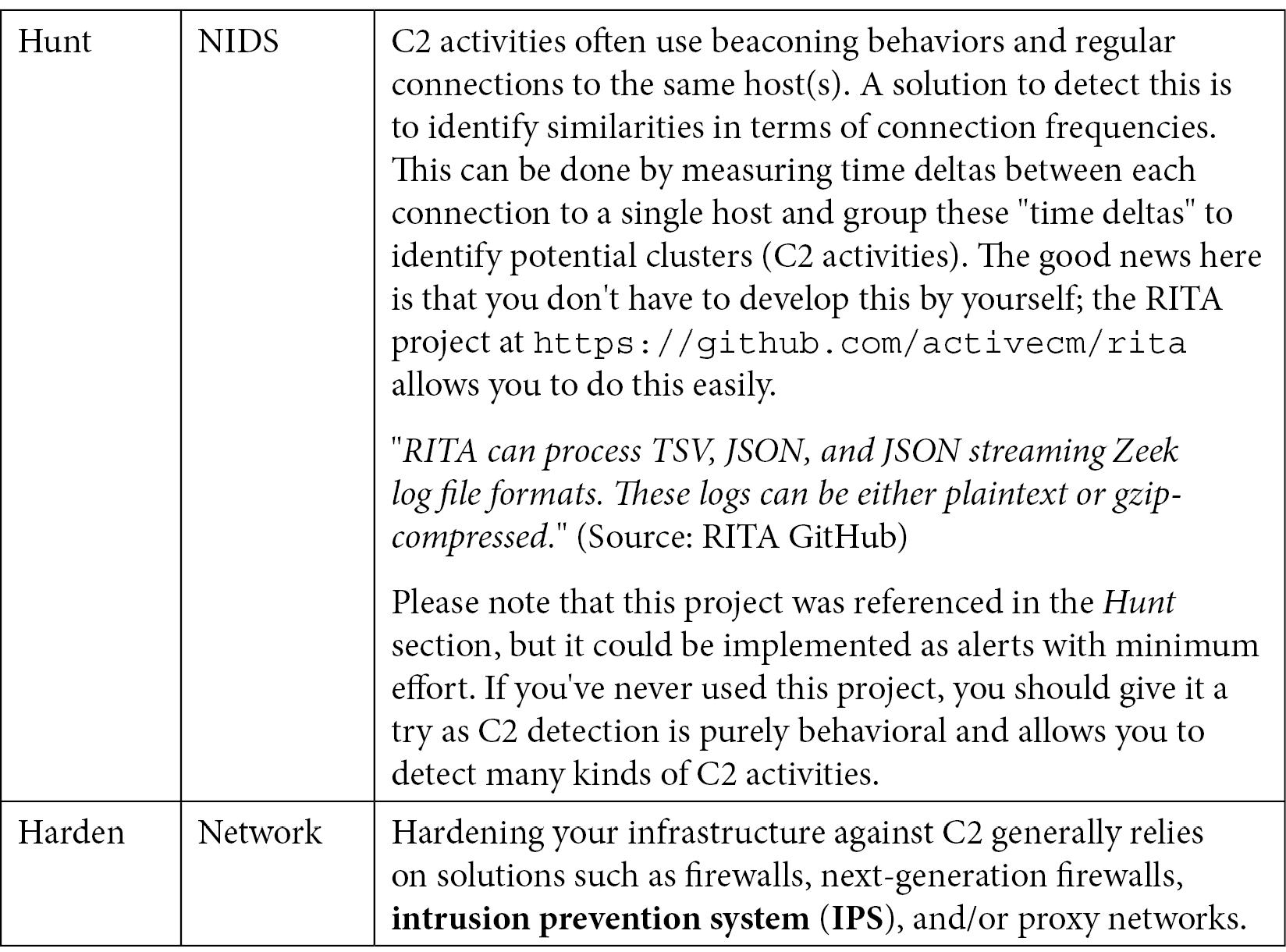
Table 10.18 – Purple Teaming T1071
The best way to ensure a maximum degree of detection should be based on hunting and alerting as C2 can use both standard and non-standard protocols.
Exfiltration
As its name suggests, this tactic helps describe the various techniques that are leveraged by the attacker to transfer the collected information and files out of the compromised network. In the past, exfiltration was not used and implemented much. Attackers would steal information such as credentials and accounting information, but this is a lightweight volume of information. On the other hand, advanced attacks oriented toward espionage stole and exfiltrated a much bigger volume of information. But today, with the increase in ransomware attacks, we have seen attackers starting to steal much more data, simply to increase the income that's generated by the attack. Simply asking for the victim to pay was not very interesting, but stealing information to ask for a second ransom to avoid the data being publicly published was. This created a second stage for the attack where the exfiltration stage is a key component.
In this section, we will look at some common web protocol techniques, as well as how the C2 channel can be used for both controlling remote compromised systems as well as exfiltrating data.
T1041 – Exfiltration over C2 channel
As we saw in Chapter 5, Red Team Infrastructure, and explained regarding the T1071 technique, more and more attacks involve the usage of C2 servers. Thus, frameworks and solutions are following this trend and implementing exfiltration features in their code. Once the communication on the beach host has been established and used over the chosen protocols, exfiltrating data over those protocols is trivial (receiving outputs from executed commands on a host is already a data transfer). This is why detection heavily relies on the techniques that we detailed in the Command and Control (C2) section.
Nevertheless, this time, the attackers will need to send a lot of data in a short period from one internal host to the external C2 server. This will often result in a burst or spike in the network volume for the chosen protocol. This is exactly what defenders could leverage to create detection rules. Some network technologies can summarize the volume of communication between different IPs. These logs could be exploited to perform hunting or even alerting use cases. Also, IDS technologies could be a real asset for summing up all the data that has been exchanged between the internal and external IPs.
This will require some fine-tuning and whitelisting as several services could create false-positive detections, such as VOIPs or legitimate uploads (these issues could be reduced by comparing the amounts of data in both directions – sessions where the volume of outgoing data is far more superior could also be worth checking). However, focusing on the specific protocols that are commonly used by C2 solutions is a solid start. Finally, for specific protocols such as DNS, we can review the number of requests for a given host or destination.
Now, let's look at another sub-technique that's used by ransomware gangs to use web services to exfiltrate data.
T1567 – Exfiltration over web service
Now, let's see how web services can be abused to exfiltrate data from a compromised network. This technique is especially handy for large volumes of data as it can blend in with user traffic. It is used by a lot of threat actor families, from advanced and manual attackers to automated malware and ransomware gangs. It is also highly reliable as it relies on very well-maintained tools. The same tools are very difficult to detect as they are legitimate and trusted software. Most of the solutions on the market also rely on secure protocols and are hosted in trusted assets. We always want to detect a breach before attackers reach this step.
With the advent of cloud solutions, more and more people store and save all their files and data on public cloud services. Thus, companies have allowed these types of connections and synchronization. Therefore, attackers are exploiting this flaw to upload stolen data onto cloud storage. This is especially true for ransomware gangs, which are stealing data before encrypting the entire network, to then ask for a second ransom for not publishing the stolen data.
Even on the endpoints, attackers may have different options to launch their copy of the freshly stolen data. For instance, they can use OneDrive's share drive mapping mechanism, tools such as rclone, which can be used to connect to more than 40 cloud products and platforms, or even use Filezilla to upload data to an SFTP server:
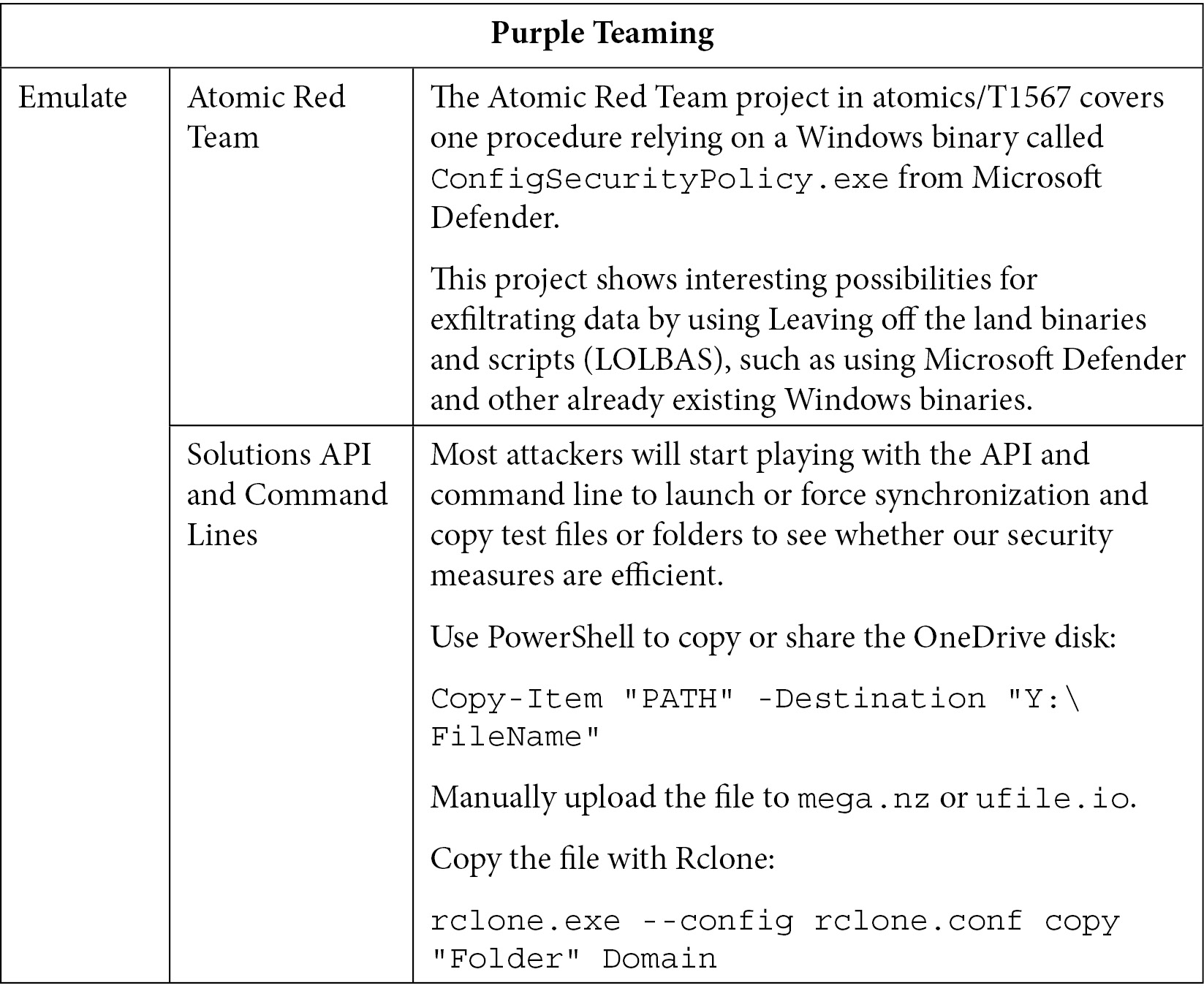
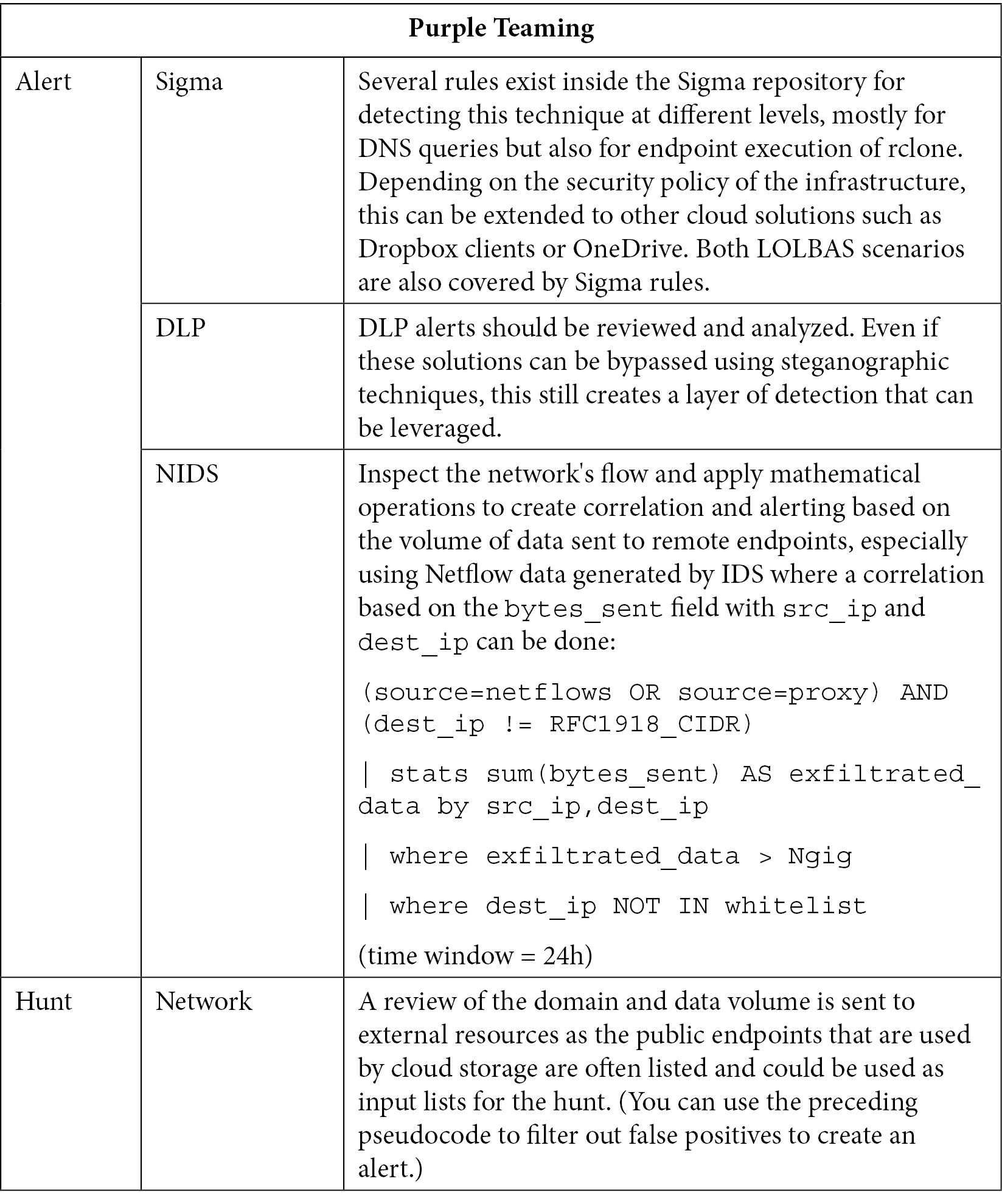

Table 10.19 – Purple Teaming T1567
As we explained earlier, these techniques could be very difficult to detect, so prevention and hardening should be implemented as soon as possible. Deploying DLP solutions and actively blocking or sinkholing public cloud resources could make a real difference in avoiding data exfiltration. This is also applicable to the other techniques that were not mentioned in this section.
In case of an attack, when all the important and desired data has been exfiltrated, we can now move on to our last action and activity.
Impact
One of the most recently added tactics by MITRE, the impact tactic is listed last as it often refers to the final action that's performed by, for example, ransomware – that is, encrypting the data. This tactic aims at describing the techniques that are used by the attacker to sabotage, such as wiper malware, to increase their chance of success. We will now explore on the Impact tactic that is leveraged by attackers to reduce the resilience of organization against sabotage activities, T1490 - Inhibit system recovery.
T1490 – Inhibit system recovery
This technique is mostly used by cybercriminals to create denial of service attacks and keep data and systems from being restored by administrators by deleting existing backups or backup functionalities. The most common motivation for this technique is monetary in the form of ransomware activities, where attackers will ask for money to allow data to be restored using the private key they used for encryption as the usual backups and recovery points will be unavailable. We've also seen wipers leveraging this technique for pure disruption during political conflicts:
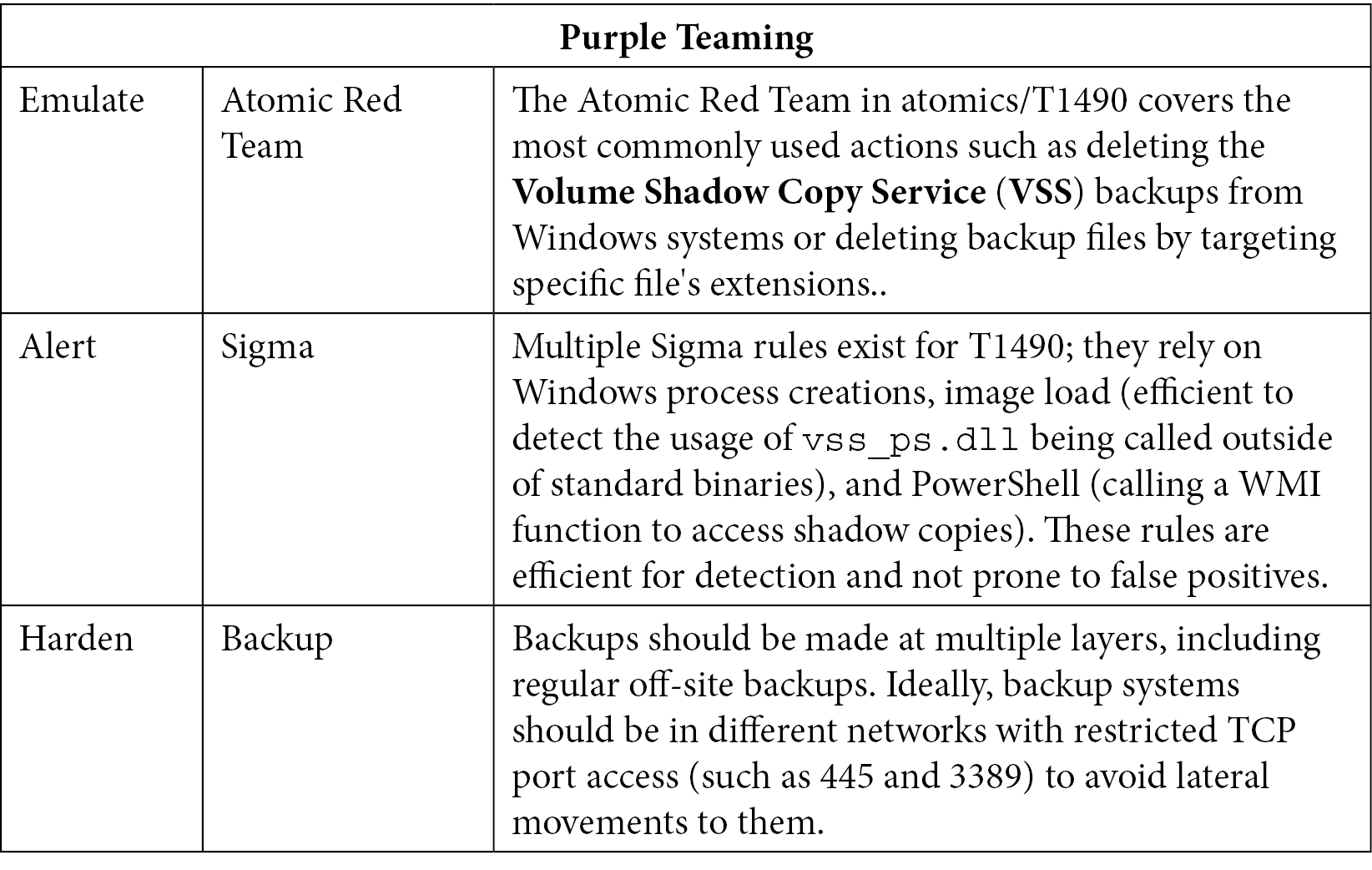
Table 10.20 – Purple Teaming T1490
To conclude, prevention is better (it is the end goal) but not always possible and requires maturity. Again, this emphasizes the need for a proactive approach where prevention is not sufficient and detection is mandatory to handle threats before they reach their final objective.
Summary
By reading this chapter, you should have a better understanding of the MITRE ATT&CK structure and the trendiest attack techniques that are used. You should have benefitted from the Purple Teaming approach we took for each technique as it should have given you experience in the detection and prevention strategy. The next chapter is dedicated to how to use adversary emulation frameworks and BAS solutions to apply Purple Teaming approaches with more and more automation in mind.
