In this age of digital information, a secret agent must be able to handle computer networks with ease. The intricate details of protocols and network packets are still shrouded in mystery to most people. With this chapter, you'll gain the advantage by simply picking up and looking closer at the network signals that surround all of us every day.
We'll start off by analyzing the Wi-Fi traffic around the house, and then we'll map out your local network in more detail so that you can pick out an interesting target for your network pranks. You'll not only learn how to capture, manipulate, and spy on your target's network traffic but also how to protect yourself and your network from mischief.
When analyzing Wi-Fi networks in particular, we have to take the borderless nature of radio signals into account. For example, someone could be parked in a car outside your house running a rouge access point and tricking the computers inside your home to send all their traffic through this nefarious surveillance equipment. To be able to detect such attacks, you need a way of monitoring the airspace around your house.
Kismet is a Wi-Fi spectrum and traffic analyzer that relies on your Wi-Fi adapter's ability to enter something called monitor mode. You should be aware that not all adapters and drivers support this mode of operation. Your best bet is to look for an adapter based on the Atheros chipset, but Kismet will try to detect and use any adapter—just give yours a try and let others know about it on the Raspberry Pi forums (http://www.raspberrypi.org/phpBB3/).
Since your Wi-Fi adapter will be busy monitoring the airwaves, you'll want to work directly on the Pi itself with keyboard and monitor or login to the Pi over a wired connection. See the Setting up point-to-point networking section of Chapter 5, Taking your Pi Off-road, if you would like to set up a direct wired connection without a router.
We'll have to build Kismet ourselves from source code as no package is available in the Raspbian repository.
- First, add some developer headers and code libraries that Kismet relies on:
pi@raspberrypi ~ $ sudo apt-get install libncurses5-dev libpcap-dev libpcre3-dev libnl-3-dev libnl-genl-3-dev libcap-dev libwireshark-data - Next, we download the Kismet source code from the project's web page:
pi@raspberrypi ~ $ wget http://www.kismetwireless.net/code/kismet-2013-03-R1b.tar.gz - Now we extract the source tree and build the software using the following sequence of commands:
pi@raspberrypi ~ $ tar xvf kismet-2013-03-R1b.tar.gz pi@raspberrypi ~ $ cd kismet-2013-03-R1b pi@raspberrypi ~/kismet-2013-03-R1b $ ./configure --prefix=/usr --sysconfdir=/etc --with-suidgroup=pi pi@raspberrypi ~/kismet-2013-03-R1b $ make pi@raspberrypi ~/kismet-2013-03-R1b $ sudo make suidinstall
- The Kismet build process is quite lengthy and will eat up about an hour of the Pi's time. Once it's finished, you may exit the source directory and delete it:
pi@raspberrypi ~/kismet-2013-03-R1b $ cd .. && rm -rf kismet-2011-03-R2
When a Wi-Fi adapter enters the monitor mode, it means that it's not associated with any particular access point and is just listening for any Wi-Fi traffic that happens to whizz by in the air. On Raspbian, however, there are utility applications running in the background that try to automatically associate your adapter with Wi-Fi networks. We'll have to temporarily disable two of these helper applications to stop them from interfering with the adapter while Kismet is running.
- Open up
/etc/network/interfacesfor editing:pi@raspberrypi ~ $ sudo nano /etc/network/interfaces - Find the block that starts with
allow-hotplug wlan0and put a#character in front of each line, as done in the following:#allow-hotplug wlan0 #iface wlan0 inet manual #wpa-roam /etc/wpa_supplicant/wpa_supplicant.conf #iface default inet dhcp
Press Ctrl + X to exit and answer y when prompted to save the modified buffer, then press the Enter key to confirm the filename to write to. This will prevent the
wpa_supplicantutility from interfering with Kismet. - Next, open up
/etc/default/ifplugdfor editing:pi@raspberrypi ~ $ sudo nano /etc/default/ifplugd - Find the line that says
INTERFACESand change it fromautotoeth0, then find the line that saysHOTPLUG_INTERFACESand change it from"all"to"", as done in the following:INTERFACES="eth0" HOTPLUG_INTERFACES=""
Press Ctrl + X to exit and answer y when prompted to save the modified buffer, then Enter to confirm the filename to write to. This will prevent the
ifplugdutility from interfering with Kismet. - Now reboot your Pi, once logged back in, you can verify that your adapter has not associated with any access points, using the following command:
pi@raspberrypi ~ $ iwconfig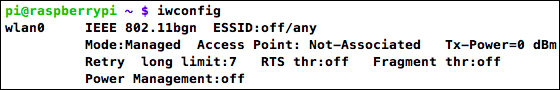
Wi-Fi adapter showing no associated access point
Kismet has the option of geographically mapping access points using a connected GPS. If you have a GPS that you'd like to use with Kismet, read the Tracking the Pi's whereabouts using GPS section of Chapter 5, Taking your Pi Off-road, to learn how to set up your GPS adapter, then continue reading from here.
Kismet is also capable of alerting you of new network discoveries using sound effects and synthesized speech. The SoX and eSpeak software from Chapter 2, Audio Antics, works well for these purposes. In case you haven't got them installed, use the following command to add them to your system now:
pi@raspberrypi ~ $ sudo apt-get install sox libsox-fmt-mp3 espeak
Another very important function of Kismet is to generate detailed logfiles. Let's create a directory to hold these files using the following command:
pi@raspberrypi ~ $ mkdir kismetlogs
Before we start Kismet, we need to open up the configuration file to adjust a few settings to our liking, using the following command:
pi@raspberrypi ~ $ sudo nano /etc/kismet.conf
We will go through the configuration and make stops to explain or change options, from top to bottom:
logprefix: Uncomment and change the line to readlogprefix=/home/pi/kismetlogsso that the logfiles generated by Kismet will be stored in a predictable location.ncsource: Uncomment and change the line to readncsource=wlan0:forcevap=false,validatefcs=trueso that Kismet knows what Wi-Fi interface to use for monitoring. There are many options for this directive and Kismet should pick sensible defaults for the most part, but we've specified two options here that have proved necessary in some cases on the Pi.gps: Change this line to readgps=falseif you don't have a GPS attached, otherwise leave it as it is and check that yourgpsdis up and running.
The Kismet application is actually made up of a separate server component and client interface, which means that you could let the Pi run only the Kismet server and then attach a client interface to it from another computer.
In this case, we'll run both server and client on the Pi, using the following command:
pi@raspberrypi ~ $ kismet
Note
Attention Mac users
If all you see is a black screen when starting Kismet, there's a problem with the terminal type that the Terminal app claims to support. What you need to do is open Preferences… located under the Terminal drop-down menu. Under the Settings panel, select the Profile marked as Default (usually the Basic profile) and look under the Advanced tab. In the drop-down menu for Declare terminal as:, select xterm. Now quit your Terminal and open it again and your Kismet experience should be more colorful.
You'll be greeted by a colorful console interface and a series of pop up dialogs asking you questions about your setup. Use your Tab key to switch between answers and press the Enter key to select. The first question about color just tweaks the color scheme used by the Kismet interface depending on your answer. Answer Yes to the second question about starting the Kismet server, then accept the default options for the Kismet server and select Start.
This is the crucial point where you'll find out if your particular Wi-Fi adapter will successfully enter monitoring mode so that Kismet can work its magic. If your adapter doesn't support the monitor mode, it will tell you so on the Kismet Server Console.
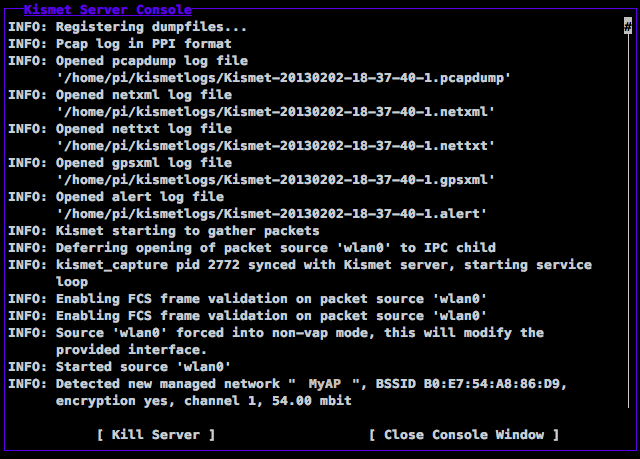
Kismet server starting up
When you see messages about new detected networks starting to pop up in the log, you know that everything is working fine and you may close the server console by pressing the Tab key to select Close Console Window and then press the Enter key.
You're now looking at the main Kismet screen, which is composed of different View areas with the Network List being the most prominent. You'll see any number of access points in the near vicinity and should be able to spot your own access point in the list.
The right-hand side of the screen is the General Info area, which provides a grand total overview of the Kismet session, and the Packet Graph across the middle provides a real-time activity monitor of the packet capture process.
The Status area at the bottom contains the latest messages from the Kismet Server Console and makes it easy to spot when new access points are discovered and added to the list.
To toggle the drop-down menu at the top of the screen, press the ~ key (usually located under the Esc key), and then use your arrow keys to navigate the menus and press the Enter key to select. Press the same ~ key to close the menu. There are also underlined letters and shortcut letters that you can use to navigate faster through the menus.
Let's look at the Sort menu. When you start out, the Network List is set to Auto-fit sorting. To be able to select individual access points in the list for further operations, you need to choose one of the available sorting methods. A good choice is Packets (descending) since it makes the most active access points visible at the top of the list.
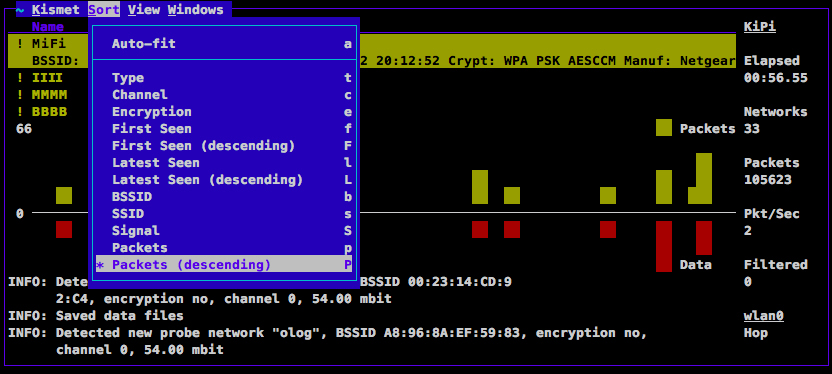
Kismet showing the sort menu
Now you'll be able to use your arrow keys in the Network List to select your access point and get a closer look at the connected computers by viewing the Client List from the View or Windows drop-down menu. Each Wi-Fi adapter associated with the access point has a unique hardware identifier called a MAC address. While these addresses can be faked (spoofed), it does give you an idea of how many computers are actively sending and receiving network packets on your network as indicated by the ! character in front of active MACs. Just keep in mind that the access point itself appears in the list as a Wired/AP type.
Most aspects of the Kismet user interface can be changed from the Preferences panel under the Kismet drop-down menu. To add sound effects or synthesized speech, select the Audio… option. Use your Tab and Enter keys to enable Sound and/or Speech. To make the speech work, select Configure Speech and change the Speech Player command to espeak. Now close the dialogs and your changes should take effect immediately.
Kismet not only monitors the Wi-Fi airspace, it also includes some Intrusion Detection System (IDS) functionality. When Kismet detects something fishy going on, it will let you know with special alert messages (and an optional siren sound effect). To help Kismet detect the rouge access point attack we mentioned in the introduction to this section, we need to specify the correct MAC address of our access point in the Kismet configuration file.
You can obtain the MAC of your access point through Kismet (verify that it stops sending packets when you turn it off to be sure it's really your access point). Now open up the Kismet configuration file for editing:
pi@raspberrypi ~ $ sudo nano /etc/kismet.conf
Locate the two example lines starting with apspoof= and comment them out. Then add your own line below according to the following format:
apspoof=RougeAPAlert:ssid="[AP Name]",validmacs="[MAC address]"
Replace [AP Name] with the name (SSID) of your access point and [MAC address] with the MAC of your access point, then exit nano and save the configuration.
Whenever Kismet detects any inconsistencies involving your access point, you'll receive alerts in the Kismet Server Console and under the special Alerts window.
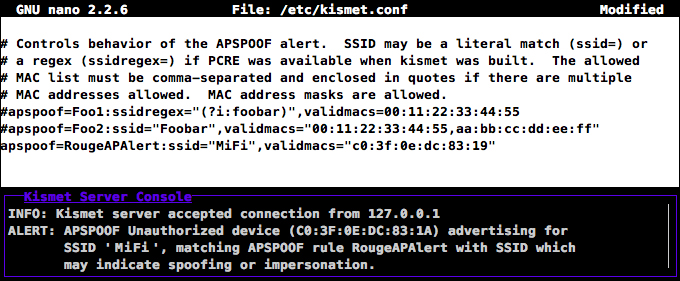
Kismet showing a rouge AP alert
To use Kismet primarily as an attack detector, it's recommended that you lock the channel to that of your access point. By default, Kismet will "hop" between different channels (frequency ranges) to try to cover as wide a spectrum of airspace as possible. To lock the channel, first obtain the channel of your access point from the Ch column of the Network List, and then select Config Channel… from the Kismet drop-down menu. Now check the Lock option, type the channel number of your AP, and select Change. The channel indicator in the lower-right corner will change from hop to your channel number.
This concludes our Kismet crash course; we'll cover how to analyze the captured network traffic that we logged to ~/kismetlogs later, in the Analyzing packet dumps with Wireshark section.
While Kismet gave us a broad overview of the Wi-Fi airspace around your home, it's time to get an insider's perspective of what your network looks like.
For the rest of this chapter, you can stay associated with your access point or connected to your router via Ethernet as usual. You'll need to revert any changes you did to the /etc/default/ifplugd and /etc/network/interfaces files earlier during the Kismet section. Then reboot your Pi and check that you are indeed associated with your access point using the iwconfig command.

Wi-Fi adapter associated with the MiFi access point
We'll be using the highly versatile Nmap application to gather information about everything that lives on your network. Let's install Nmap together with two other packages that will come in handy:
pi@raspberrypi ~ $ sudo apt-get install nmap xsltproc elinks
Nmap as well as the other applications we'll be using in this chapter will want to know what IP address or range of addresses to focus their attention on. Nmap will gladly start scanning the entire Internet if you tell it to, but that's neither practical nor helpful to you or the Internet. What you want to do is pick a range from the private IPv4 address space that is in use on your home network.
There are the following three IP address blocks reserved for use on private networks:
10.0.0.0 - 10.255.255.255(Class A network)172.16.0.0 - 172.31.255.255(Class B network)192.168.0.0 - 192.168.255.255(Class C network)
The Class C network is the most common range for home routers, with 192.168.1.1 being a typical IP address for the router itself. If you're unsure of the range in use on your network, you can look at the IP address and route information that was handed to the Wi-Fi interface by the DHCP service of your router:
pi@raspberrypi ~ $ ip addr show wlan0 pi@raspberrypi ~ $ ip route show
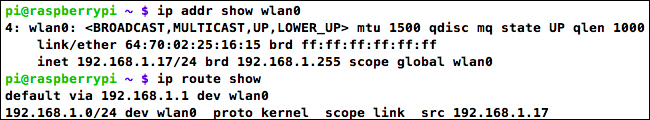
Wi-Fi interface in the 192.168.1.0/24 address range
The Wi-Fi interface as shown in the previous screenshot has been handed an IP address in the 192.168.1.0/24 range, which is a shorter way (called CIDR notation) of saying between 192.168.1.0 and 192.168.1.255. We can also see that the default gateway for the Wi-Fi interface is 192.168.1.1. The default gateway is where the Wi-Fi interface sends all its traffic to talk to the Internet, which is very likely to be the IP address of your router. So if you find that your interface has been given, for example 10.1.1.20, the IP addresses of the other computers on your network are most likely somewhere in the 10.1.1.1 to 10.1.1.1.254 range. Now that we know what range to scan, let's see what Nmap can find out about it.
The simplest, yet surprisingly useful, scan technique offered by Nmap is called the
List Scan. It's one way of finding computers on the network by doing a host name lookup for each IP address in the range that we specify, without sending any actual network packets to the computers themselves. Try it out using the following command, but replace [target] with a single IP address or range:
pi@raspberrypi ~ $ sudo nmap -v -sL [target]
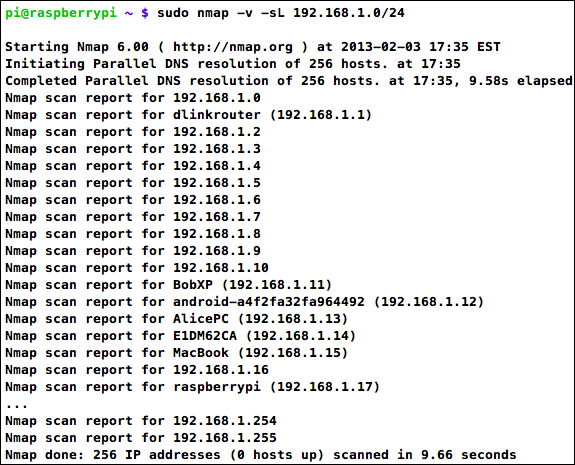
Nmap performing a List Scan
We always want to run Nmap with sudo, since Nmap requires root privileges to perform most of the scans. We also specify -v for some extra verbosity and -sL to use the List Scan technique. At the end comes the target specification, which can be a single IP address or a range of addresses. We can specify ranges using the short CIDR notation such as in the preceding screenshot, or with a dash in each group (called octets) of the address. For example, to scan the first 20 addresses, we could specify 192.168.1.1-20.
The List Scan tells us which IP address is associated with what host name, but it doesn't really tell us if the computer is up and running at this very moment. For this purpose, we'll move on to the next technique—the Ping Scan . In this mode, Nmap will send out packets to each IP in the range to try to determine whether the host is alive or not. Try it out using the following command:
pi@raspberrypi ~ $ sudo nmap -sn [target]
You'll get a list of all the computers that are currently running, along with their MAC address and the hardware manufacturer of their network adapter. On the last line, you'll find a summary of the total number of IP addresses scanned and how many of them are alive.
The other functions offered by Nmap can be viewed by starting nmap without arguments. To give you a taste of the powerful techniques available, try the following series of commands:
pi@raspberrypi ~ $ sudo nmap -sS -sV -sC -O -oX report.xml [target] pi@raspberrypi ~ $ xsltproc report.xml -o report.html pi@raspberrypi ~ $ elinks report.html
This nmap command might take a while to finish depending on the number of computers on your network. It launches four different scanning techniques: -sS for Port Scanning, -sV for Service
Version Detection, -sC for Script Scan, and -O for
OS Detection. We've also specified -oX to get a detailed report in the XML format, which we then transform to an HTML document, viewable on the console with the Elinks web browser. Press Q to quit Elinks when you're done viewing the report.
