Now that we have a better idea of the computer behind each IP address, we can begin to target the network traffic itself as it flows through our network.
For these experiments we'll be using an application called Ettercap. The act of listening in on network traffic is commonly known as sniffing and there are several great sniffer applications to choose from. What sets Ettercap apart is its ability to combine man-in-the-middle attacks with networking sniffing and a bunch of other useful features, making it an excellent tool for network mischief.
You see, one obstacle that sniffers have to overcome is how to obtain network packets that aren't meant for your network interface. This is where Ettercap's man-in-the-middle attack comes into play. We will launch an ARP poisoning attack that will trick any computer on the network into sending all its network packets through the Pi. Our Pi will essentially become the man in the middle, secretly spying on and manipulating the packets as they pass through.
Let's install the command-line version of Ettercap using the following command:
pi@raspberrypi ~ $ sudo apt-get install ettercap-text-only
Before we begin, make a few small adjustments to the Ettercap configuration file:
pi@raspberrypi ~ $ sudo nano /etc/etter.conf
Find the two lines that read ec_uid = 65534 and ec_gid = 65534. Now change the two lines to read ec_uid = 0 and ec_gid = 0. This changes the user/group ID used by Ettercap to the root user. Next, find the line that starts with remote_browser and replace mozilla with elinks, then save the configuration and exit nano.
For our first Ettercap experiment, we'll try to capture every single host name lookup made by any computer on the local network. For example, your browser makes a host name lookup behind the scenes when you visit a website for the first time. Use the following command to start sniffing:
pi@raspberrypi ~ $ sudo ettercap -T -i wlan0 -M arp:remote -V ascii -d //53
Depending on the level of activity on your network, the messages could be flooding your screen or trickle in once in a while. You can verify that it is indeed working by opening up a command prompt on any computer on the network and trying to ping a made-up address, for example:
C:> ping ahamsteratemyrockstar.com
The address should show up as part of a DNS request (UDP packet to port 53) in your Ettercap session.
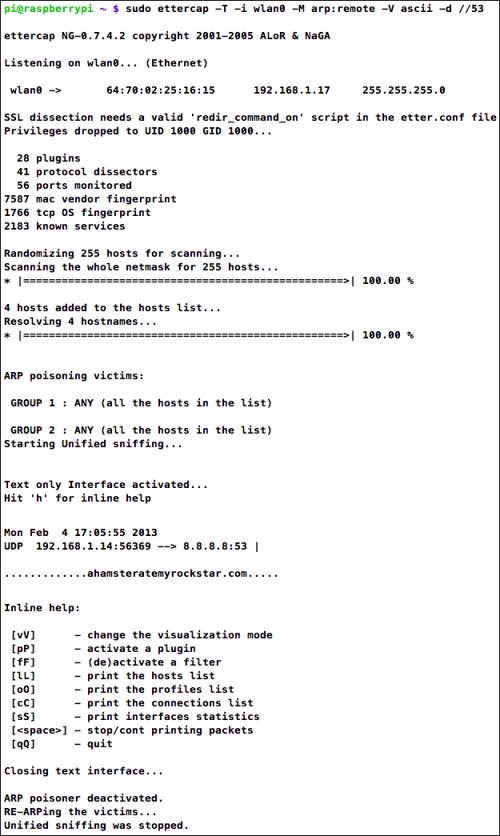
Ettercap sniffing for DNS requests
Note that Ettercap is in "interactive mode" here. You can press the H key to get a menu with several interesting key commands to help you control the session. It's very important that you quit Ettercap by pressing the Q key. This ensures that Ettercap will "clean up" your network after the ARP poisoning attack.
Let's go over the arguments we passed on the command line: The -T is for the interactive text mode and -i wlan0 means we want to use the Wi-Fi interface for sniffing—use eth0 to sniff on a wired connection. The -M arp:remote specifies that we'd like to use an ARP poisoning man-in-the-middle attack, the -V ascii dictates how Ettercap will display the network packets to us, and -d specifies that we would prefer to read host names instead of IP addresses. Last comes the target specification, which is of the form MAC address/IP address/Port number. So for example /192.168.1.1/80 will sniff traffic to/from 192.168.1.1 on port number 80 only. Leaving something out is the same as saying "all of them". You may also specify ranges, for example, /192.168.1.10-20/ will sniff the ten IPs from 192.168.1.10 to 192.168.1.20. Often you'll want to specify two targets, which is excellent for watching all traffic between two hosts, the router and one computer for example.
Before we move on to the next example, we need to talk about encryption. As long as the network packets are sent in plaintext (unencrypted—in the clear), Ettercap is able to dissect and analyze most packets. It will even catch and report the usernames and passwords used to log in to common network services. For example, if a web browser is used to log in to your router's administration interface over regular unencrypted HTTP, Ettercap will spit out the login credentials that were used immediately.
This all changes with encrypted services such as the HTTPS protocol in your web browser and OpenSSH. While Ettercap is able to log these encrypted packets, it can't get a good look at the contents inside. There are some experimental features in Ettercap that will try to trick web browsers with fake SSL certificates, but this will usually result in a big red warning from your browser saying that something is wrong. If you still want to experiment with these techniques, uncomment the redir_command_on and redir_command_off directives under the if you use iptables header in the Ettercap configuration file.
After experimenting with Ettercap and understanding the implications of unencrypted communications, you might reach the conclusion that we need to encrypt everything! and you'd be absolutely right—welcome to the club and tell your friends! Fortunately, several large web service companies such as Google and Facebook have started to switch over to encrypted HTTPS traffic by default.
For our next example, we will capture and log all communications between the router and one specific computer on your network. Use the following command but replace [Router IP] with the IP address of your router and [PC IP] with the IP address of one particular computer on your network:
pi@raspberrypi ~ $ sudo ettercap -q -T -i wlan0 -M arp:remote -d -L mycapture /[Router IP]/ /[PC IP]/
Here, we're still in interactive mode and can use the key commands, but we've also specified the -q flag for quiet mode. This prevents packets from flooding our screen, but we will still receive notices about captured login credentials. The -L mycapture argument enables the logging mechanism and will produce two logfiles – mycapture.eci, containing only information and captured login credentials, and mycapture.ecp containing all the raw network packets.
The logfiles can then be filtered and analyzed in different ways with the etterlog command. For example, to print out all HTTP communications with Google, use the following command:
pi@raspberrypi ~ $ sudo etterlog -e "google.com" mycapture.ecp
Use etterlog --help to get a list of all the different options for manipulating the logfiles.
Ettercap offers additional functionality in the form of plugins that can be loaded from interactive mode with the P key or directly on the command line using the -P argument. We'll be looking at the sneaky
remote_browser plugin that allows us to create a "shadow browser" that mimics the surfing session of the browser on a remote computer. When the remote computer surfs to a site, the plugin will instruct your elinks to also go to that site.
To try this out, you need to start elinks first in one terminal session, as root:
pi@raspberrypi ~ $ sudo elinks
Then we start Ettercap, with -P remote browser, in another terminal session:
pi@raspberrypi ~ $ sudo ettercap -q -T -i wlan0 -M arp:remote -P remote_browser /[Router IP]/ /[PC IP]/
As soon as Ettercap picks up a URL request from the sniffed PC, it will report this on the Ettercap console and your Elinks browser should follow along. Press the H key in elinks to access the history manager, and Q to quit elinks.
