Understanding Security Policies
A security policy is a written document that provides the organization with a high-level view of the security goals of an organization. Chapter 9 presented and contrasted the differences among policies, standards, guidelines, and procedures. Recall that the policies are the high-level, authoritative documents. Standards document criteria such as a proven norm or method and may specify requirements for a process or a technology, but the organization chooses what standards to follow. Guidelines provide recommendations for members of an organization, but they are not mandatory, and procedures provide the action steps to accomplish tasks.

EXAM TIP Policies provide the high-level authority for an organization. They are authoritative in nature and provide the direction for the creation of guidelines and procedures.
An organization often has several security policies, with a single security policy driving the others. For example, Figure 12-1 shows the relationship between an organization’s security policy and other supporting policies. For instance, the security policy can mandate the creation of an acceptable use policy and require users to review and acknowledge the policy periodically. The organization then creates an acceptable use policy to support this requirement. Similarly, the security policy may mandate that the organization must be able to continue to operate critical functions in the case of an emergency. The business continuity plan identifies critical functions with a business impact analysis and uses disaster recovery plans to respond to specific emergencies.
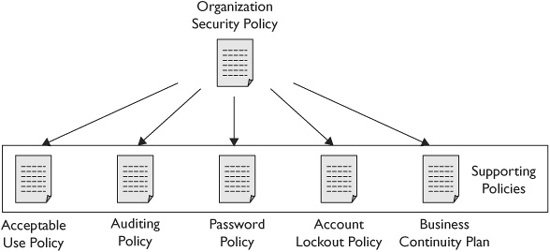
Figure 12-1 An organization security policy and supporting policies

TIP A security policy can be an overall security policy for an organization. Organizations can also create security policies for individual systems that define the system and the protections related to the system. This section is focused on creating a security policy for an organization.
Senior management creates or at least endorses the organization’s security policy. The policy reflects the culture of the organization and provides the overall direction for security. Others within the organization use the security policy as an authoritative document to implement controls to enforce and follow the requirements of the security policy.
Security policies are an important first step to provide security within an organization, but they aren’t the final step by any means. After senior management has approved the security policies, they must be implemented and enforced.
Security Policy Characteristics
An organization’s security policy is a single written document. It’s not uncommon for a security policy to be between 10 and 50 pages long depending on the size of the organization.
There is no definitive source that defines the contents of a security policy. In other words, a security policy in one organization can look completely different from the security policy for another organization. However, security policies will often have several of the characteristics described in the following text:


NOTE Chapter 11 covered data classifications in greater depth. It included discussion of the common classifications used in the U.S. government and classifications commonly used in private organizations.



TIP Items in this list are not mandatory items to include within a security policy, and the list is not all-inclusive. However, the list does provide a good cross-section of topics that many organizations include.
Enforcing Security Policies
Of course, security policies are useful only if they are implemented and enforced. This is one of the reasons that senior management must endorse and support security policies. If not, they become meaningless pieces of paper. There are multiple methods of enforcing security policies.
Figure 12-2 shows multiple methods used to enforce security policies. These are the same security methods covered throughout this book. For example, Chapter 2 covered authentication and access controls; Chapter 7 covered risk management topics; and Chapter 9 covered several different types of management, technical, and operational controls.
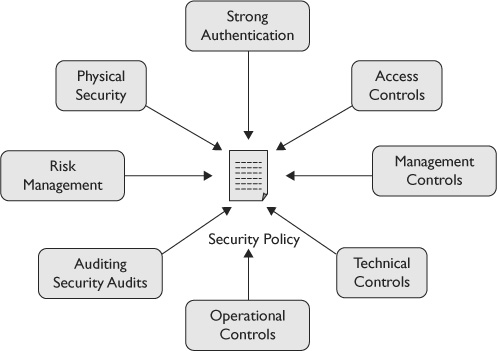
Figure 12-2 Enforcing a security policy

TIP The elements shown in Figure 12-2 aren’t meant to be a complete list. However, they do help illustrate that an organization uses multiple methods to support a security policy.
These elements work together to provide a defense-in-depth security solution by increasing the overall security posture of the organization. Although this book’s discussion is organized as if the controls (such as strong authentication and access controls) come first, it’s worth stressing that normally the security policy comes first. In other words, the security policy drives the security controls that an organization uses to enforce the security policy, and these controls support the overall mission of the organization.
Value of a Security Policy
A security policy, when it is well crafted and understood by members of the organization, provides the obvious value of increasing security and security awareness. However, there are also some less obvious benefits.
Security Policies Are Not Mandatory
Organizations are not normally required to have security policies, although they can be mandated by a higher authority. For example, organizations processing credit card data may be required to have a security policy though the Payment Card Industry Data Security Standard (PCIDSS). If an organization isn’t required to have a security policy through a higher authority, it may consider a security policy too expensive or too time-consuming. However, the lack of a security policy can often cost more in the long run.
Without a policy providing guidance, employees make their own decisions, which can often result in wasted efforts, rework, and ultimately higher costs. Employees must use their own judgment on what they think is valuable to the organization. For example, an employee would attempt to determine what data is most important and how to protect it (or not protect it). At the very least, these decisions will be inconsistent and can easily result in the loss of both confidentiality and availability of critical data.
For example, if IT personnel don’t recognize the value of research and development data, they may not use strong access controls to protect it or back it up. An attacker may be able to hack into the system easily and steal the data, or a common hardware failure may result in the loss of a significant amount of research data. Both scenarios can result in the organization losing a significant amount of money.
It’s also worth noting that if an organization doesn’t have a security policy, it may be susceptible to other legal problems, including liability issues. For example, if an organization doesn’t have an acceptable usage policy and an employee uses a computer to hack into other systems or networks, the company can be held liable. Similarly, if an employee accesses pornography, another employee can claim sexual harassment and the company may be held liable.
If the security policy is able to prevent or at least reduce security incidents, it can protect an organization against direct financial losses as well as indirect losses through damage to its reputation.

NOTE Chapter 11 provided examples of data breaches to Epsilon Marketing and the Sony PlayStation Network; these examples demonstrate direct and indirect losses. When the Sony PlayStation Network was shut down for a couple of days, Sony suffered immediate losses of revenue, representing direct losses. It also had to spend a great deal of money and resources answering demands from government officials and trying to assure customers that Sony was taking steps to protect customer data.
Even if a security incident occurs, the security policy may limit the organization’s liability. As an example, consider two organizations that are attacked. The attack exploits a zero-day vulnerability and results in the loss of customer data. One organization doesn’t have a security policy and its security practices are not well documented. A second organization does have a security policy, and has a significant amount of documentation showing that it regularly follows security practices. The first company will be more vulnerable to litigation claiming that it has not taken steps to protect customer data, while the second company may be able to demonstrate that it did everything it could to prevent losses, so its liability should be limited.
Similarly, when employees sign security policies (such as acceptable usage policies) acknowledging their contents, they can be held accountable to follow the security policies. Organizations that monitor user activity often state so in acceptable usage policies, along with descriptions of acceptable usage of company IT systems. The majority of employees won’t knowingly violate security policies. However, some employees may purposely try to circumvent the security policies, which can cause additional harm to an organization. For example, if an employee surfs pornographic sites using a company computer (counter to the acceptable usage policy), fellow employees may see the objectionable material and raise sexual harassment issues. In the absence of a policy, the company may be liable for the sexual harassment. With a policy in place, the company can hold the offending employee accountable.

EXAM TIP An acceptable usage policy (sometimes called an acceptable use policy) ensures that users know what is acceptable use of computers and networks. Organizations commonly require users to review and acknowledge these types of policies regularly, such as once a year.
Understanding Code of Ethics
Chapter 1 covered the Code of Ethics required by (ISC)2. As you’ll recall, you must subscribe to this Code of Ethics to earn and keep the SSCP certification. It includes items such as protecting society, acting honorably, providing diligent and competent service, and advancing and protecting the profession.
However, the (ISC)2 doesn’t have a corner on ethics. Many organizations also have established an ethics statement to inform its members of their responsibilities related to the organization and its customers. If an employee senses a conflict between what he or she is being told to do and the organization’s ethics, that employee has a responsibility to raise this internally within the organization rather than reporting it externally. On the other hand, if the organization attempts to resolve the issue internally but is ignored, the organization may have a legal obligation to report the issues externally. For example, Chapter 11 mentioned the Enron scandal, where corruption was evident all the way to the CEO, and executives who participated in the corruption faced jail time.

EXAM TIP Employees have an obligation to abide by the ethics of their employer. In other words, employees have an implied loyalty to their employer as long as they remain employed.
It’s unlikely that any security policy will cover every possible issue that can present itself within IT security. This is where ethics come in. They provide a framework of norms and principles of correct conduct beyond the security policies. With this in mind, members of an organization have a responsibility to ensure that secure practices are still followed, even if there isn’t a specific policy that covers a particular challenge.
One example worth stressing is that even if an organization doesn’t have a policy specifically stating that attackers should not be attacked, the organization’s IT professionals still should not attack them, unless that is a direct part of their job. For example, if an attacker launches a SYN flood attack on one of your servers, you may be able to analyze the logs and determine the source of the attack based on the IP address. You may be tempted to launch an attack against the attacker, but this is not ethical.
First, the attacker may be spoofing an IP address so that even though you think you know where the attack originated, you may be attacking an innocent company that was hijacked by the attacker. Second, when you launch an attack, you are escalating the situation. If you block the attack, the attack stops and is over. If you attack back, the attacker may take it personally and launch multiple malicious attacks against your company for days, months, or even years afterward.
Policy Awareness
A policy that is hidden away in a desk is barely more useful than no policy at all. After an organization creates and approves a security policy, personnel need to be aware of its contents. There are multiple ways of advertising a security policy, but it’s also important to recognize what information is relevant to employees.
Different members of an organization require different levels of understanding of a security policy. In other words, some topics need to be completely understood by all employees, while some topics may need to be understood only by IT staff.
For example, all employees must be aware of an acceptable usage policy. The acceptable usage policy identifies a user’s responsibilities related to the usage of an organization’s IT systems. Employees may be required to read and acknowledge this on an annual basis and can be held accountable for its requirements.
Then again, regular employees don’t need to know the details of a two-factor authentication system required for remote access. The policy may dictate that two-factor authentication is required if users access the network using a virtual private network (VPN), and that the IT staff must design and implement authentication using smart cards with usernames and passwords for VPN access. Users who never use VPNs may never know about the policy requirement, and even users who do use VPNs don’t need to understand the technical details of multifactor authentication as long they know they must use a smart card with their username and password.

EXAM TIP Some common methods used to increase user awareness of relevant security policy elements include training, warning banners, and posters. At the very least, the policy must be accessible to employees.
Easy-to-Read Language
The policy should be written in language that is simple to understand. If the policy is too complex for the target audience to understand, they very likely will not follow the policy. To give a simple example, you can tell users to use complex passwords, but without explaining what a complex password is, they may not follow the policy.
In this case, the policy could define a complex password as having at least eight characters and including at least one character in each of the four character types (uppercase, lowercase, numbers, and symbols). Users can understand these requirements and follow the policy without any problem.
Warning Banners
One of the ways that you can let users know of the relevant contents of a security policy is with warning banners. Each time that a user logs on to a system, a warning banner can provide details on the network, a definition of an authorized user, and an expectation of privacy.
For example, many organizations regularly monitor user activity. A warning banner can remind users that their activity is being monitored to detect improper or illicit use of computer systems and networks. The warning banner could also list penalties for noncompliance with the acceptable usage policy. These warning banners remind users of their responsibilities and help serve as a deterrent.
Training Sessions
Some elements of a security policy may require training to implement. Training can be targeted to different individuals based on the type of training. For example, an incident response team may require dedicated training to ensure they are able to respond to incidents and limit the potential damage.
On the other hand, some training may be required for all personnel. Phishing attacks have gone through several changes over the years, and periodically reminding employees of current phishing attacks (such as spear phishing) can be useful. Many organizations provide this type of training using online methods. For example, users can access the training via an internal website.
Security Flyers and Posters
Some organizations use security flyers and posters to raise security awareness and remind people of the security policies. The goal is often to get the users to recognize that security is their responsibility too, not just something the company does.
Updating Security Policies
A security policy is expected to be a dynamic document. It isn’t something that is created once and never revisited. The business will change as time moves forward, and, likewise, threats and vulnerabilities will change.
It’s important to schedule a review of security policy on a regular basis, such as once a year. During this review, the organization can examine changes to determine whether the security policy warrants an update. Changes in the industry, business practices, laws, threats, and many other aspects may require changes in the security policy.

EXAM TIP Security policies should be updated regularly, such as once a year. If an organization’s security policy is updated, supporting policies should also be reviewed to ensure that they still provide the necessary support.
Additionally, an organization will often reexamine a security policy after a security incident. For example, if a security breach results in the loss of valuable data to an organization, it should examine the security policy and supporting practices. The goal is to determine whether the existing policy was adequate or if a change is needed.

