Defining Risk
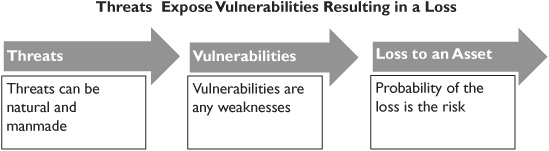
The simple definition of risk is the probability or likelihood of a threat exploiting a vulnerability and resulting in a loss. A threat is any activity that can be a possible danger. A vulnerability is a weakness, and a loss represents a negative event for an organization. Figure 7-1 shows the basic components of risk.
A common formula used to represent risk is:
Risk = Threat * Vulnerability
When the threat and the vulnerability are combined (a threat exploits a vulnerability), it results in a loss. More significant threats or vulnerabilities can easily result in higher losses from the risks. In other words, some risks have higher impacts. However, if you can reduce the vulnerabilities, you reduce risk, resulting in lower potential losses.

TIP It’s rarely possible to reduce threats. You can’t stop an attacker from attacking, but by reducing vulnerabilities, you reduce the attacker’s chances of success. In other cases, you can reduce the impact of the risk to limit losses.
For example, malware represents a threat to any computer. If a computer does not have antivirus (AV) protection, it is vulnerable to malware threats. If a virus did infect an unprotected system, it could modify, destroy, or steal data, representing a loss to the owner of the computer. An organization could mitigate, or reduce, the vulnerability by using AV software and keeping it up to date.

EXAM TIP Risk mitigation is the practice of reducing risk. The primary method of reducing risk is to reduce or eliminate vulnerabilities by implementing safeguards or controls.
Total risk is the combined risk to all of the organization’s assets, including all the threats and vulnerabilities. Total risk also includes the value of these assets.
NIST
The U.S. National Institute of Standards and Technology (NIST) includes a Computer Security Division, and an Information Technology Laboratory (ITL) within that division. The ITL performs research to advance the development and productive use of information technology and regularly publishes documents known as Special Publications (SPs). The SP 800 series of reports include the results of this research performed in collaboration with industry, government, and academic organizations.
You can review a full list of the NIST ITL SP 800 series documents here: http://csrc.nist.gov/publications/PubsSPs.html. You can also download any of these documents as PDF files from this page. The following are some of the commonly quoted SP 800 series documents:
• SP 800-127, Guide to Securing WiMAX Wireless Communications
• SP 800-124, Guidelines on Cell Phone and PDA Security
• SP 800-123, Guide to General Server Security
• SP 800-122, Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
• SP 800-115, Technical Guide to Information Security Testing and Assessment
• SP 800-113, Guide to SSL VPNs
• SP 800, Guide to Storage Encryption Technologies for End User Devices
• SP 800-97, Establishing Wireless Robust Security Networks: A Guide to IEEE 802.11i
• SP 800-94, Guide to Intrusion Detection and Prevention Systems (IDPS)
• SP 800-83, Guide to Malware Incident Prevention and Handling
• SP 800-77, Guide to IPsec VPNS
• SP 800-64, Rev 2 Security Considerations in the System Development Life Cycle
• SP 800-61, Rev 1 Computer Security Incident Handling Guide
• SP 800-58, Security Considerations for Voice Over IP Systems
• SP 800-41, Rev 1 Guidelines on Firewalls and Firewall Policy
• SP 800-30, Risk Management Guide for Information Technology Systems
A significant benefit of these documents is that they are freely available to the public. Anyone can download and use these documents when creating an IT security program (or when studying IT security).
It’s also worth mentioning that the NIST ITL is not the same thing as the Information Technology Infrastructure Library (ITIL). ITIL is a set of five books published by the United Kingdom’s Office of Government Commerce documenting IT practices for successful operations. The ITIL books are not freely available and retail as a set for over $500, making them unaffordable to many people. There is an associated set of ITIL certifications based on the ITIL books.
There aren’t any direct certifications associated with the NIST ITL SP documents. However, the content is often used as an authoritative source for security certifications such as the SSCP and CISSP exams.
NIST SP 800-30, Risk Management Guide for Information Technology Systems, defines risk in a couple of different ways:
Risk is a function of the likelihood of a given threat-source’s exercising a particular potential vulnerability, and the resulting impact of that adverse event on the organization.
Risk is the net negative impact of the exercise of a vulnerability, considering both the probability and the impact of occurrence. Risk management is the process of identifying risk, assessing risk, and taking steps to reduce risk to an acceptable level.
While these definitions are more technical, they do repeat the common themes of threats, vulnerabilities, impacts, and losses. Or more specifically, when a threat exploits a vulnerability, it results in a loss and different losses can result in different impacts.
Identifying Threats
Threats are any type of activity or event that can result in a loss of confidentiality, integrity, or availability to a system. Threats can be internal or external, natural or manmade, and even intentional or accidental.

TIP Chapter 1 presented the concepts of confidentiality, integrity, and availability. To recap, maintaining confidentiality means that unauthorized individuals don’t have access to data or systems. Maintaining integrity means that unauthorized individuals can’t modify data and systems. Maintaining availability means that that data and systems are up and operational when needed.
NIST SP 800-30 formally identifies a threat as follows:
The potential for a threat-source to exercise (accidentally trigger or intentionally exploit) a specific vulnerability.
Additionally, it identifies a threat-source as follows:
Either (1) intent and method targeted at the intentional exploitation of a vulnerability or (2) a situation and method that may accidentally trigger a vulnerability.
Internal threats are from employees, contractors, or any other personnel granted access to an organization’s resources. They can also be from hardware or software controlled by the organization, such as a failed air conditioner unit or software with undiscovered bugs. If the air conditioning system fails, systems can overheat and fail, resulting in loss of availability. Undiscovered software bugs can cause an application to fail, corrupt data, or allow unauthorized personnel to access data. In contrast, external threats are from anything outside of the organization’s control.
Natural causes include weather events such as lightning storms, hurricanes, tornadoes, and floods, and can include nonweather events such as earthquakes or tsunamis. Threats can also be manmade, such as from attackers launching denial-of-service attacks or criminals writing malware to steal data.
Chapter 5 covered many different types of attacks that can be classified as intentional threats. On the other hand, accidental threats can also result in losses. For example, if someone spills coffee onto a laptop, it can easily ruin it. Similarly, if someone accidentally kills the power or cuts the communications cables to key systems, it results in a loss of availability.

TIP While IT security topics often stress the intentional threats, it’s important to realize steps need to be taken to protect systems from accidental threats also. If a building’s environmental controls fail, resulting in a loss air conditioning, it can result in damaged equipment. Servers get hot. If they are not kept cool, they can overheat and fail. Because of this, many organizations will power down servers when air conditioning fails to protect the equipment, but this results in an immediate loss of availability.
Understanding Vulnerabilities
Vulnerabilities are any weaknesses in a system, network, or infrastructure. NIST SP 800-30 defines a vulnerability as follows:
A flaw or weakness in system security procedures, design, implementation, or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or a violation of the system’s security policy.
If these flaws or weaknesses can be exploited by a threat, it results in a loss. Some examples of vulnerabilities include the following:
• Poor or nonexisting AV protection Antivirus software needs to be installed on each system and kept up to date. If systems don’t have AV protection, malware can infect one or more systems, resulting in damaging losses.
• Terminated employees If employee accounts are not disabled or deleted after an employee is terminated, the account can be used to attack a system. The employee may be able to access the system and cause damage, or another employee may use the account to perform actions that will be logged and attributed to the terminated employee.
• Weak access controls If strong authentication and authorization controls are not implemented, unauthorized individuals will be able to access, modify, and/or destroy data.
• Poor or nonexisting change-management practices An unintentional side effect of making a change to a system is that the change causes one or more problems. Strong change-management practices examine prospective changes to predict the side effects and mitigate problems before the change is implemented.
• Poor hardening practices Systems should be hardened, or made more secure from their default configuration. This includes changing defaults such as default passwords, implementing firewalls, keeping operating systems and applications up to date with patches, and more.
• Lack of redundancies for key systems Any single point of failure can result in an outage of an entire system if it doesn’t include fault-tolerance capabilities. Redundancies can be added for disk drives, servers, communications lines, power and air conditioning, and even entire sites or locations.
• Uneducated users Social engineers can trick uneducated users into giving up key information. On the other hand, once users understand the tactics used by social engineers, they can easily foil the attacker’s attempts.

TIP The preceding list is by no means complete, but it does provide some common examples of vulnerabilities. An important point to remember about any vulnerability is that you can reduce weaknesses by implementing controls or safeguards. By reducing the vulnerabilities, you reduce the possibility of the risk resulting in a loss.
Threats often exploit the weakest link in your organization, and once a threat exploits a vulnerability, the damage is done. The way to minimize losses is to identify potential vulnerabilities and reduce them. Chapter 8 presents vulnerability assessments and how they can be used within an overall security program.
Understanding Impact
The level of the risk is based on the impact. In some cases, the impact is negligible, and if so, the risk is considered a low priority. In other cases, the impact can be quite high, making the risk a very high priority.
Risk assessments consider the impact of the risk, although they use different methods. Quantitative and qualitative risk assessments are presented later in this chapter. A quantitative risk assessment uses costs and monetary values to identify the impact. A qualitative risk assessment uses subjective opinions of experts.
