Exploring Wireless Technologies
Wireless technologies have become quite popular in the past decade. With a wireless network, computers connect to each other and network devices by transmitting data over the airwaves. There are four primary IEEE 802.11 standards currently in use. Table 3.2 outlines the base frequency and maximum speeds of each.


NOTE The speed is the maximum speed in ideal conditions. However, the speed is reduced the farther away the wireless devices are from each other. The speed is also reduced from obstructions such as walls or from interference from EMI or RFI.
A wireless network includes wireless devices, such as laptops or smaller portable devices, and either a wireless access point (WAP) or a wireless router. A wireless access point provides a bridge for wireless clients to a wired network. For example, Figure 3-12 shows a wireless access point for an organization with one user connecting to the WAP with a smartphone while another user is connecting with a laptop. Once connected, the wireless clients are able to access any resources in the network, just as other wired clients can.

Figure 3-12 Wireless users connecting to a network via a WAP
Wireless routers include additional capabilities beyond the WAP and are commonly used in small offices and home offices (SOHOs). Specifically, a wireless router can include the following capabilities:
• WAP Provides a bridge for wireless clients to the wired network.
• DHCP Provides both wired and wireless clients with TCP/IP configuration information, such as an IP address, subnet mask, the address of DNS, and more.
• NAT Translates between private IP addresses used internally and public IP addresses used on the Internet.
• Routing Provides basic routing between the internal network and the Internet. The wireless router is the default gateway for all internal clients.
• Basic firewall Provides basic firewall capabilities to filter traffic, but the capabilities can differ substantially from one brand to another.
Figure 3-13 shows an example of a wireless router. In this figure, you can see that the wireless router is also providing additional services for both wired and wireless clients. All clients access the Internet via this wireless router.
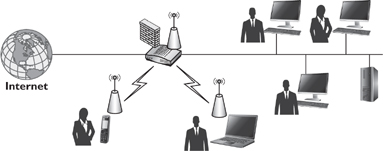
Figure 3-13 Wireless users connecting to a network via a wireless router
Wireless systems typically transmit in multiple directions (omnidirectional) at the same time. The area where the signal can be received is referred to as the wireless footprint. Within an organization, the footprint can be reduced by obstructions such as walls or devices transmitting EMI or RFI.
However, an attacker can extend the footprint of a wireless network by using a receiver with a directional antenna. For example, it’s possible to hook up something as simple as a can to a wireless antenna and then point the can toward the wireless transmitter. Some tests have shown that an attacker can do this to capture transmissions of wireless networks more than a mile away.
Comparing WEP, WPA, and WPA2
Because wireless technologies transmit data over the air using radio waves, it’s easy for an attacker to capture the data with a wireless receiver. This can be as simple as installing a wireless sniffer on a laptop that includes wireless capabilities. For example, Kismet is a wireless sniffer application available via the Internet. An attacker can download and install it, and then sit in a parking lot of an organization capturing wireless transmissions.
However, if the wireless transmissions are secured, it makes it much more difficult for an attacker to gain any usable information from these transmissions. The three primary security protocols are Wired Equivalent Privacy (WEP), Wi-Fi Protected Access (WPA), and Wi-Fi Protected Access 2 (WPA2).
WEP was the first security algorithm used for 802.11 wireless networks. Although the goal was to provide the same level of privacy on a wireless network as users could achieve on a wired network, it failed. WEP has several security issues and has been replaced with WPA and WPA2.

EXAM TIP WEP should not be used at all due to how insecure it is. At the very least, WPA should be used. WPA2 is better, but it isn’t supported on legacy hardware. WPA-Personal and WPA2-Personal use a pre-shared key. WPA-Enterprise and WPA2-Enterprise use an 802.1x authentication server providing a higher level of security.
WPA was introduced as a replacement for WEP. The goal was to provide better security immediately for wireless using the existing hardware devices. In other words, users running WEP could switch over to WPA without purchasing new wireless adapters, wireless access points, or wireless routers. Although WPA was much better than WEP, it wasn’t intended to be a permanent replacement.
Instead, WPA2 was created as a permanent replacement and is formalized as IEEE 802.11i. WPA2 requires different hardware, but at this point, the Wi-Fi Alliance requires that all new hardware support WPA2 in order to be Wi-Fi-certified. The Wi-Fi Alliance is a global non-profit organization that has helped standardize wireless technologies.
WPA originally used only Temporal Key Integrity Protocol (TKIP). TKIP could use the same hardware as WEP, but provided significantly more security than WEP. WPA2 can use either Advanced Encryption Standard (AES) or TKIP, and at this point, many WPA implementations also support AES. AES is a widely embraced encryption algorithm that is known to be highly secure and efficient.
Both WPA and WPA2 can operate in either Personal or Enterprise mode. These modes are described in the following sections.
WPA-Personal and WPA2-Personal
WPA-Personal and WPA2-Personal use a pre-shared key (PSK). This is a password or passphrase of 8 to 63 characters. WPA then uses this PSK to create an encryption key, and wireless traffic is encrypted and decrypted with this key. It’s worth noting that the PSK isn’t the encryption key itself, but instead other cryptographic functions are used to create the key.

TIP This encryption key is used by either AES or TKIP for symmetric encryption. Symmetric encryption and AES are explored in greater depth in Chapter 14.
The same PSK must be entered on the WAP or wireless router, and each of the wireless devices. For example, Figure 3-14 shows one of the setup pages for a Linksys wireless router. The key is entered as IWillBeSSCPCertified. You can also see that AES is selected.

Figure 3-14 Configuring security for a wireless router
WPA-Enterprise and WPA2-Enterprise
An organization can increase security with wireless networks by adding an 802.1x authentication server and using Enterprise mode. The authentication server is sometimes referred to as a Remote Dial-in User Authentication Service (RADIUS) server. Both WPA and WPA2 support Enterprise mode.

EXAM TIP Enterprise mode requires an 802.1x authentication server and increases security by requiring clients to authenticate before access is granted.
When an 802.1x authentication server is added, the clients are required to authenticate (such as with a username and password) prior to being granted access to the network. In contrast, in Personal mode, users only need to know the PSK. Additionally, clients don’t need to enter a PSK. Instead, the encryption keys are created and assigned to the clients automatically.
An 802.1x authentication server will often be configured to check an authentication database on another server. For example, in a Microsoft domain, the 802.1x authentication server can check a user’s credentials via a domain controller hosting Active Directory Domain Services.
Although the focus in this section is to use an 802.1x authentication server to authenticate wireless clients, 802.1x authentication servers can also be used to authenticate other clients. For example, it can be used to authenticate DHCP clients prior to providing TCP/IP configuration information.
Wireless Device Administrator Password
Wireless devices commonly have a web-based administration program that you can access with a basic web browser. Figure 3-14 showed one administration page, and Figures 3-15 and 3-16, which appear later in this chapter, show some other administration pages. The two common IP addresses used are 192.168.0.1 or 192.168.1.1. When you connect, you’ll be prompted to provide the name of the administrator account and the administrator password.
You can check the manual (or the Internet) for the default name and password if necessary. A common combination is admin (for the administrator account) and admin (as the password), although there are many variations.
One of the important steps in securing a wireless device is to change this password from the default. Ideally, you’ll change it to a strong password or passphrase. If you don’t, it’s possible an attacker driving by your wireless network may see it, log in using the defaults, and modify your network. An attacker can actually lock you completely out of your network until you reset the wireless device to factory defaults.

TIP Wardriving is the practice of driving around with a wireless receiver (such as a laptop with a wireless NIC) and looking for wireless networks.
Wireless Service Set Identifier
Wireless networks are identified by a service set identifier (SSID). In other words, the SSID is the name of the wireless network. Many wireless devices have default SSIDs, but newer ones often require the user to enter the name of the SSID as part of the setup process. For example, some common SSIDs for older wireless routers were Linksys (for Linksys systems) and Netgear (for Netgear devices).
An SSID can be almost any name you want, although it can’t be longer than 32 characters. It’s a user-friendly name, but you don’t necessarily want to make it user-friendly to attackers. For example, if your wireless network includes secret financial data, you probably don’t want to call it SecretFinancialData.
Figure 3-15 shows the configuration page for a Linksys wireless router with the SSID entered as SSCPWireless. You can also see that the Wireless SSID Broadcast is set to enable. When the wireless device is set to enable wireless SSID broadcasting, it regularly broadcasts messages with the SSID name. This enables other wireless devices in range of the broadcast to easily identify the wired network, and if they have security configured the same as the wireless router, the SSID broadcast allows these other devices to connect easily.
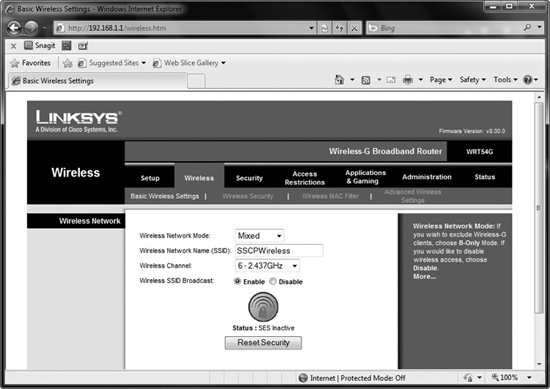
Figure 3-15 Configuring the SSID
An ongoing discussion related to the SSID is whether you should enable or disable SSID broadcasting. Many people originally recommended disabling SSID broadcasting to hide the network. However, this really doesn’t provide any security. Even though this stops the normal SSID broadcasts used by other wireless devices, it doesn’t prevent the device from actually broadcasting its SSID. An attacker with a wireless sniffer (such as Kismet) can easily capture key packets and discover the SSID, even when SSID broadcasting is disabled.
MAC Filtering
Most wireless devices also provide the ability to filter connections based on MAC addresses. For example, Figure 3-16 shows a configuration page for a wireless router with a Wireless MAC Filter set to Enable. Theoretically, this will allow you to identify specific computers (based on their MAC addresses) that are allowed to connect while blocking all computers from connecting.

Figure 3-16 Enabling a MAC filter
However, it’s quite simple to spoof the MAC address of a system. An attacker with a wireless sniffer can identify the MAC addresses that are connecting with a wireless network. Armed with this knowledge, the attacker can then use software to change the wireless MAC address of the attacker’s system and then connect.
In theory, MAC filtering as a security precaution sounds good. In practice, it’s easily beatable. The best protection you can use is WPA2. If you have a choice and can configure an 802.1x authentication server, use WPA2-Enterprise instead of WPA2-Personal (WPA2-PSK).
Bluetooth
Bluetooth is a wireless technology used for small wireless networks commonly called personal area networks (PANs). Bluetooth is used with smaller wireless devices such as a phone and an earpiece and microphone. Users can wear a Bluetooth-enabled earpiece while keeping a Bluetooth phone in their pocket.
Devices have to be paired with each other before they will communicate. Pairing is done by changing the devices to discovery mode so that they can easily locate each other and connect. Once they are paired, discovery mode should be disabled. If discovery mode is left enabled, an attacker can pair with the devices and take them over. It’s relatively easy for a user running Linux to exploit a Bluetooth device left in discovery mode.
The following are three well-known types of Bluetooth attacks:
• Bluesnarfing A hacker that is able to pair with a Bluetooth device such as a smartphone can access data on the phone. The attacker can make phone calls, send and receive text messages, read and write contact information, connect to the Internet, and even eavesdrop on phone conversations. The attacker must be close to the phone (usually within 30 feet).
• Bluebugging In some instances, an attacker is able to access a smartphone and issue specific commands to it. This enables the attacker to make phone calls, send messages, read and write data, connect to the Internet, and eavesdrop on conversations. Although the attack allows the attacker to perform the same actions that can be done by Bluesnarfing, Bluebugging uses different techniques.
• Bluejacking Compared to Bluesnarfing and Bluebugging, Bluejacking is relatively harmless. It allows users to send business cards to other phones, but it does not involve modifying a phone’s data.
Radio-Frequency Identification
Radio-frequency identification (RFID) is used for identification, tracking, asset management, and inventory control. Products are “tagged” with an RFID tag, which is a small electronic device that marks the product. RFID readers can then read the tag to get information about the product.
RFID tags can be either active (with a battery) or passive (without a battery). Active RFID tags are constantly transmitting. A passive RFID tag works similarly to how proximity cards work for authentication. An RFID reader can excite the electronics on the RFID tag and cause the tag to transmit its information.

TIP Proximity cards were described in more depth in Chapter 2 within the “Something You Have” subsection of the “Three Factors of Authentication” section.
GSM
Global System for Mobile Communications (GSM) began as a European standard for 2G, or digital cellular, networks in 1982. As a comparison, 1G refers to the analog communications that came out in the 1980s and 2G refers to the digital technologies that came out in the 1990s. The GSM standard was widely embraced and has since grown into a large family of technologies used in mobile communications.
GSM has is a standard used in 219 countries (including the United States). The GSM Association (GSMA) includes almost 800 mobile operators and 200 other companies that help standardize, deploy, and promote the GSM standard.
3G
3G refers to the third generation of standards for wireless access used by mobile phones and mobile telecommunications. 3G provides higher transmission speeds for mobile communications, comparable to broadband speeds that wired users have. Speeds up to 3 Mbps are common. Users can surf the Web with a mobile phone and access other web-based services such as e-mail.
Improvements of 3G are sometimes dubbed as 3.5G and 3.75G. They use High Speed Packet Access (HSPA), and in many cases users can get in more 20 MB/s download times. However, not everyone can achieve these high rates of downloads. Worse, when large numbers of cellular users are operating in the same area, all users have reduced speeds because they’re competing for the same bandwidth.
WiMAX
Worldwide Interoperability for Microwave Access (WiMAX) is a standard based on IEEE 802.16. IEEE 802.16 is officially known as Wireless MAN, but is commercially known as WiMAX. WiMAX provides broadband wireless coverage to large areas or metropolitan area networks (MANs).
For example, a WiMAX fixed station can provide wireless access for up to 30 miles. In comparison, wireless local networks using 802.11 are limited to about 300 feet. Many providers have created WiMAX networks around the world and users can rent access to the networks. WiMAX provides speeds up to 40 MB/s for wireless connections. Future versions are expected to offer speeds up to 1 GB/s.
NFC
Near field communication (NFC) is a technology available on many smart phones that allows users to make purchases with a cell phone. For example, if you have an NFC-enabled smart phone, you can make a purchase at a store by simply tapping your smart phone on the NFC reader or waving it close to the reader. Similarly, users can share information with each other by identifying the information to share and tapping the two devices together.
It uses similar technology as a proximity card (described in Chapter 2), allowing devices to communicate with each other when they are in close proximity. Data is transmitted and received only between short distances, identified as a near field. Additionally, this data is encrypted providing some protection.
Of course, if you add your credit information to your NFC-enabled smart phone, it does make the risk of losing your phone that much greater. If someone steals such information, they can wave and tap it during a massive shopping spree that will be billed on your credit card.
Protecting Mobile Devices
The primary vulnerabilities with mobile devices occur if they are lost. If someone finds or steals a mobile device, that person may be able get some valuable information. With this in mind, there are several things that users can do to protect themselves. These include the following:
• Password protect devices Most devices support password protection. Users must enter a password or personal identification number (PIN) to unlock the device to use it. If the device is stolen, this password makes it more difficult for the thief to access the data.
• Encrypt data Many devices support data encryption. If a thief does get a phone, the encryption provides confidentiality by restricting the thief’s access to the data.
• Remote wipe Some devices support remote wipe. This allows the owner to send a command to a lost device to delete all the data off of the device. The command will delete cached data, such as cached passwords, along other data such as information in the user’s contact list.
• Enable GPS Many devices support global positioning system (GPS) location services. If the device is lost, the user can use the GPS service to determine its location.

EXAM TIP Mobile devices are easily lost. Because they can often contain valuable data, it’s important to know the different methods available to protect data. Password protection and data encryption are valuable if done before the device is lost. Remote wipe and GPS are valuable after the device is lost.
Chapter Review
The OSI Model is a framework for connecting multiple computers to each other. It was developed by the ISO and it has seven layers. The layers, listed from layer 1 to layer 7, are physical, data link, network, transport, session, presentation, and application. The TCP/IP Model (also called the DOD Model) is similar to the OSI Model, but it has fewer layers. RFCs 1122 and 1123 identify four layers of the OSI Model, but some references in the SSCP CIB identify five layers.
Two important protocols operate on the transport layer (layer 4). They are TCP and UDP. TCP is connection-oriented and establishes sessions with a three-way handshake. UDP is connectionless and doesn’t use a three-way handshake to establish a session. Instead, UDP uses its best effort to just send the data. Other protocols can work with either TCP or UDP, depending on the protocol’s needs. For example, FTP uses TCP for guaranteed delivery, while TFTP uses UDP.
Network configurations include bus, star, and token ring. In a bus configuration, all devices are connected together with a common shared connection and both ends of the configuration must be terminated. A bus is cheap initially but very difficult to troubleshoot, increasing the total cost of ownership. A star configuration is much more common and uses a central device such as a router or a switch. All devices connect to each other via the central device in a star. A token ring configuration uses a logical token and devices in the ring can transmit only when they have the token. Token ring configurations are slower and don’t scale well, although some networks use FDDI due to the increased speed of fiber.
TCP/IP includes a full suite of protocols beyond TCP and UDP that are used by computers on the Internet and on many internal networks. You’re not expected to be an expert on all of the protocols in the suite for the SSCP exam, but you should be familiar with many of them. Additionally, you should know which protocols are required and which are optional. For example, ARP is used to resolve IP addresses to MAC addresses and must be running to transfer data on a network. ICMP is used for diagnostics and is useful when it’s running, although it is often disabled to thwart attacks that use ICMP. Application protocols such as those used for e-mail (SMTP, POP3, and IMAP4) or FTP are required only when the system is running an application that needs the protocol. If the protocol is not needed, it should not be enabled.
Many protocols present security risks because they transfer data in an unencrypted, clear-text format. An attacker with a sniffer can capture these transmissions and read the data. For example, FTP and Telnet transfer usernames, passwords, and data in clear text. Secure protocols such as SSH or IPsec can encrypt these data transmissions.
Both TCP and UDP can use any of 65,536 ports (numbered from 0 to 65,535). Ports 0 to 1023 are defined as well-known ports and are mapped to specific protocols by IANA. For example, SSH uses port 22, HTTP uses port 80, and SMTP uses port 25. You should be able to identify the port used by many common protocols.
Different network architectures provide different levels of trust. For example, an intranet is used internally within an organization and provides the highest level of trust. The Internet is external and has the least level of trust. A DMZ is used to host Internet-facing servers that are accessible by anyone on the Internet, and an extranet is used to host Internet-facing servers that are accessible only by trusted entities such as a business partner. Internal clients use private IP addresses, and public IP addresses are used on the Internet. NAT translates IP addresses from public to private and from private back to public.
Wireless networks allow clients to connect using radio-wave transmissions. These radio-wave transmissions are the easiest to capture and intercept (compared to transmissions on wired networks), but some basic security steps can increase the security of a wireless network. WEP is older and should not be used. WPA was an immediate replacement for WEP and was compatible with existing hardware. WPA2 is the best and is formally defined by 802.11i. WPA originally used TKIP, but many WPA systems also support AES. WPA2 uses AES by default, but can also use TKIP. Both WPA and WPA2 can use Personal mode (with a pre-shared key) or Enterprise mode. Enterprise mode requires an 802.1x authentication server.
Smaller wireless devices use technologies such as GSM, 3G, WiMax, and NFC. Several methods can be used to protect these devices if they are lost. Methods include password-protecting the devices, encrypting data on them, using remote wipe to delete data on lost devices, and enabling GPS to locate lost devices.
Questions
1. Which of the following transmission types are the easiest to capture with a sniffing tool?
A. Fiber-optic connections
B. Shielded twisted pair cable
C. Unshielded twisted pair cable
D. Wireless
2. TCP provides guaranteed delivery of data. What is used to create the TCP session?
A. Best effort
B. Three-way handshake
C. IP
D. Packet sequencing
3. Which of the following protocols is connection-oriented?
A. IP
B. RIP
C. TCP
D. UDP
4. What layer of the OSI Model can provide nonrepudiation?
A. Application
B. Transport
C. Network
D. Physical
5. Which one of the following network topologies is susceptible to loss of availability of the entire network from a single break in the cable?
A. Star
B. Bus
C. Token ring with MSAU
D. FDDI
6. What is the protocol ID of IPsec’s ESP?
A. 1
B. 6
C. 50
D. 51
7. Which of the following transmission types sends traffic from one computer to multiple other computers on different subnets?
A. Multicast
B. Broadcast
C. Unicast
D. ICMP
8. Which of the following protocols does not encrypt the traffic?
A. SSH
B. FTP
C. IPsec
D. SSL
9. What is the well-known port for SSH?
A. 20
B. 21
C. 22
D. 23
10. What is the well-known port for HTTPS?
A. 80
B. 88
C. 443
D. 1701
11. Of the following choices, which one is a valid IPv6 address?
A. fe80:0000:0000:0000:a3b4:045d:2376:b95f:77f5.
B. fe80:0000:0000:0000:045d:2376:b95f:77f5.
C. 192.175.256.2
D. 192.168.1.5
12. Of the following choices, what maps a single registered IP address with a single private unregistered IP address on a one-to-one basis?
A. PAT
B. Dynamic NAT
C. Static NAT
D. Ultimate NAT
13. Which of the following is the best choice to secure a wireless network?
A. Disable SSID broadcasts
B. Enable MAC filtering
C. Enable WEP
D. Enable WPA
14. What is required to support WPA2-Enterprise?
A. An 802.11 wireless server
B. An 802.1x authentication server
C. A pre-shared key (PSK)
D. Layer 3 switches
15. Of the following choices, what should not be used to secure wireless transmissions?
A. WPA
B. WPA2
C. WEP
D. AES
16. Of the following choices, what does not represent a risk related to Bluetooth devices?
A. Bluejacking
B. Bluesnarfing
C. Bluebugging
D. Bluediscoverying
17. You want to ensure that data on a mobile device is protected against loss of confidentiality if the user loses the device. What could be done before issuing the device to the user?
A. Use GPS.
B. Remove password protection.
C. Execute remote wipe.
D. Encrypt the data.
18. A user has lost a mobile device that has valuable data stored on it. What can be used to protect the data on this lost device?
A. Encrypt the data.
B. Use remote wipe.
C. Enable GPS.
D. Enable password protection.
Answers
1. D. Wireless transmissions are the easiest to capture with a sniffing tool because they are transmitted using radio waves. Fiber-optic cables are the most difficult to tap, but twisted pair are relatively easy to tap (although still not as easy as wireless).
2. B. A three-way handshake establishes a TCP session. The client sends a SYN packet, the server replies with a SYN/ACK packet, and the client then replies with an ACK packet. UDP uses best-effort delivery and does not guarantee delivery. IP uses TCP for guaranteed delivery and does not create the TCP session. Packet sequencing is another feature of TCP, but it does not create the TCP session.
3. C. TCP is connection-oriented. IP uses TCP to provide a connection-oriented session but is not connection-oriented itself. RIP is a routing protocol and is not connection-oriented. UDP is connectionless.
4. A. Nonrepudiation can be provided at the application layer with digital signatures. The transport layer provides reliable end-to-end communications. The network layer provides routing information. The physical layer works with bits and bit streams.
5. B. A single break in a cable in a bus configuration can take down the entire network. A break in a cable in the star topology affects only the device connected with that cable. A break in a token ring with a multistation access unit (MSAU) topology affects only a single device. Fiber Distributed Data Interface (FDDI) uses two rings for fault tolerance.
6. C. IPsec ESP has a protocol ID of 50. ICMP is 1, TCP is 6, and IPsec’s AH is 51.
7. A. Multicast transmissions (such as those using IGMP) send data from one computer to multiple other computers on a network. Broadcast sends data from one computer to all other computers on the subnet. Unicast sends data from one computer to one other computer. ICMP is used for diagnostics, such as with ping and pathping.
8. B. FTP sends data (including a user’s credentials) across a network in clear text. SSH, IPsec, and SSL are all encryption protocols used to encrypt data on the wire.
9. C. SSH uses port 22. FTP uses ports 20 and 21. Telnet uses port 23.
10. C. HTTPS uses port 443. HTTP uses port 80. Kerberos uses port 88. L2TP uses port 1701.
11. B. An IPv6 address has 128 bits and is commonly represented with eight groups of four hexadecimal characters (not nine groups). IPv4 addresses are expressed in dotted decimal format, but only numbers between 0 and 255 (not 256) are valid.
12. C. Static NAT maps a single registered (public) IP address with a single private (unregistered) IP address. Dynamic NAT maps private IP addresses to one of many public IP addresses. PAT is a form of dynamic NAT that uses ports. There is no such thing as ultimate NAT.
13. D. WPA is a security algorithm for wireless devices that provides a strong layer of protection. SSID broadcast doesn’t provide much (if any) security because an attacker can still detect the SSID even when SSID broadcasting is disabled. MAC filtering provides a modest security gain, but it is easily beaten because MAC addresses can be spoofed. WEP has been superseded by WPA and WPA2 and should not be used today.
14. B. An 802.1x authentication server is used with WPA2-Enterprise to ensure that only clients that can authenticate are able to access the wireless network. There’s no such thing as an 802.11 wireless server. A PSK is used for WPA/WPA2-Personal. Wireless technologies do not require layer 3 switches.
15. C. WEP should not be used since it is not secure and has been replaced by WPA and WPA2. WPA2 is the most secure. WPA2 and some newer implementations of WPA support AES for encryption.
16. D. There is no such thing as Bluediscoverying. However, a Bluetooth device is susceptible to Bluejacking, Bluesnarfing, and Bluebugging attacks.
17. D. Encryption of data is always valuable to prevent loss of confidentiality, as long as the data is encrypted before the device is lost. Global positioning system (GPS) can be used to locate a device after it is lost. Enabling password protection can prevent access to the device, but removing password protection doesn’t provide any protection. Remote wipe can be used to wipe all the data from a device after it is lost.
18. B. Remote wipe can be used to wipe all the data from a device after it is lost. Encryption of data is always valuable to prevent loss of confidentiality, but it can’t be done after the device is lost. Global positioning system (GPS) can be used to locate a device if it is enabled on a device, but it can’t be enabled after it is lost. Enabling password protection can prevent access to the device, but it can’t be enabled after it is lost.
