Understanding Firewalls
Chapter 3 introduced firewalls when describing differences between the Internet, an intranet, an extranet, and a demilitarized zone (DMZ). Firewalls filter the traffic that is allowed into or out of a network. They can be dedicated physical devices primarily filtering traffic, and they can also be software running on a system such as a desktop computer.
Basic packet filtering firewalls filter the traffic by examining each individual packet. More advanced firewalls filter the traffic by examining the overall session or actual protocol commands embedded in the packets. Additionally, firewalls can be network-based, providing protection for an entire network of systems, or host-based, providing protection for a single operating system.
Packet Filtering Firewall
A packet filtering firewall filters traffic by examining the contents of a packet. More specifically, a packet filtering firewall can filter traffic based on IP addresses, subnet addresses, ports, some protocols, or any combination of these:

EXAM TIP A packet filtering firewall uses access control lists (ACLs) to filter the traffic. ACLs can be created to filter the traffic based on source or destination IP addresses, subnet addresses, entire domains, ports, and/or protocols.
• IP addresses Each packet contains the source and destination IP address. A packet filter can examine this data and either block or allow traffic to or from specific IP addresses. For example, if an attacker is launching an attack from a specific IP address, traffic from that IP address can be blocked.
• Subnet addresses In addition to filtering specific IP addresses, you can also filter entire subnets. For example, the network ID of 192.168.1.0/24 could be used to block or allow IP addresses from 192.168.1.1 through 192.168.1.254.
• Ports Well-known ports (ports from 0 to 1023) are used to identify many protocols. For example, the well-known port for the Simple Mail Transport Protocol (SMTP) is port 25. By allowing traffic through port 25 (or opening port 25), you are effectively allowing SMTP traffic.

TIP Chapter 3 covered ports in more depth and included a table listing many commonly used ports.
• Some protocols Many protocols are identified by a protocol ID embedded in the IP header. The protocol ID for ICMP is 1, IGMP is 2, TCP is 6, UDP is 17, IPsec AH is 50, and IPsec ESP is 51. A firewall can filter traffic based on the protocol ID. For example, a firewall can block all ICMP traffic (such as pings) by blocking protocol ID 1.
• A combination of IP addresses, ports, or protocols Any combination of IP addresses, ports, or protocols can be used. For example, consider Figure 4-2, which shows an e-mail server within a DMZ (named mail1) and another e-mail server in the intranet (named mail2). Firewall 1 can be configured so that SMTP traffic (using port 25) can go only to the mail1 server (using IP address 192.168.1.25). Similarly, Firewall 2 can be configured so that e-mail traffic is allowed only between mail1 and mail2. However, unless additional rules are added, SMTP traffic directly from the Internet will not be allowed through both Firewall 1 and Firewall 2 to mail2.

Figure 4-2 E-mail server within a DMZ
A packet filtering firewall often uses an implicit deny policy. All traffic is blocked (implicit deny) unless there is a rule in the ACL that explicitly allows the traffic. This is achieved by placing one of the following statements at the end of the ACL:
• deny any
• deny any any
The rule used is dependent on the router brand and model, but the most important point is that this is the last rule in the list. If a previous rule doesn’t explicitly allow the traffic, this rule will block it. If you place this rule first in the list, it will ignore any other rules in the ACL and deny all traffic.

TIP Most routers and packet filtering firewalls will automatically use a deny any or deny any any rule even if the rule hasn’t been typed into the ACL. In other words, you may not see the rule in the ACL, but the rule is being enforced.
Although a packet filtering firewall is effective at blocking individual packets, it can be difficult to maintain when a large number of ACLs are added. Additionally, a large number of ACLs can negatively impact performance because each packet must be compared against each ACL.
Many organizations use a simple packet filtering firewall at their boundary to the Internet. They do so by adding ACLs to an external screening router. Although such a firewall doesn’t provide all the capabilities of a more advanced firewall appliance, it can be effective for smaller organizations.
Stateful Inspection Firewall
A stateful inspection firewall allows a firewall to filter traffic using much more than just individual packets. Instead, it monitors the complete session. A stateful inspection firewall identifies active connections as they are created and monitors the status of these connections in a state table within the firewall.
As an example, a TCP session begins with the three-way handshake. The stateful firewall uses this three-way handshake to identify that a session has started between two systems. The firewall can then monitor the traffic between the systems. Even though UDP connections don’t start with a three-way handshake, a stateful inspection firewall can still identify active UDP connections and track the state of the connection.

TIP Only traffic that is part of an active connection or that is initiating a new connection is allowed by a stateful inspection firewall. It will reject traffic that is not part of an active connection or that is initiating a new connection.
A stateful inspection firewall is aware of what is expected from different communication sessions. When a session starts, it will dynamically open ports based on the needs of the connections, and when the session completes, it will dynamically close ports.
In comparison, the packet filtering firewall is a stateless firewall. It cannot determine whether a packet is part of an ongoing session between two systems or whether the packet is from an attacker trying to probe or attack a system.
Application Firewall
An application firewall includes different elements for different applications. For example, it would have an HTTP proxy to examine web traffic, an SMTP proxy to examine e-mail traffic, an FTP proxy to examine FTP traffic, and so on. Each proxy has the ability to analyze specific traffic for the protocol that it is monitoring and understands the individual protocol commands. For example, an HTTP proxy can interpret Get and Put commands used to retrieve and write web page elements, and the proxy can be configured to allow or block specific commands.

TIP An application firewall is also known as an application proxy firewall and an application gateway firewall.
Although the application firewall does provide effective filtering for individual applications or protocols (such as HTTP, SMTP, and FTP), it requires a separate component for each individual protocol. If the firewall must filter many different protocols, this process can be extensive and negatively impact performance. However, if the firewall is being used only to filter a few protocols, it is manageable and can be highly efficient.
Application firewalls are often used with packet filtering. For example, the packet filtering firewall can drop packets for protocols that aren’t desired based on the port, while the application proxy firewall can perform deep inspection of traffic for protocols that are allowed.
Defense Diversity
Chapter 1 introduced the concept of defense in depth. A solid security program includes multiple layers of security so that even if one layer breaks down, other layers still provide protection. Similarly, defense diversity can be used when implementing a DMZ by using firewalls from two separate vendors.
For example, consider Figure 4-3. The firewall separating the Internet from the DMZ is from Cisco and the firewall separating the DMZ from the intranet is from Microsoft. Because the DMZ was created by firewalls from two different vendors, it is using defense diversity. Both are susceptible to vulnerabilities, and both are regularly updated as vulnerabilities become known.

Figure 4-3 Implementing defense diversity with a DMZ
At any time, an attacker could discover a previously unknown vulnerability on either firewall. If both firewalls are the same model from the same vendor, both firewalls will be susceptible to the same vulnerability at the same time. However, if both firewalls are from different vendors, it is less likely that both will be subject to a particular vulnerability at the same time. Defense diversity with the DMZ firewalls provides an extra layer of protection for the internal network.

EXAM TIP A DMZ is typically created with two firewalls. Using firewalls from two separate vendors provides defense diversity for the DMZ.
Additionally, defense diversity requires the attacker to have more skills and knowledge in order to exploit both firewalls. For example, an attacker may have extensive expertise with the Cisco router, but very little on the Microsoft router. Fewer attackers will have the same level of expertise on firewalls from different vendors.
Comparing Network-based and Host-based Firewalls
Firewalls are often classified as either network-based or host-based. A network-based firewall provides protection for a network, while a host-based firewall provides protection for a single host. As an example, consider Figure 4-4. The two firewalls used to create the DMZ are network-based firewalls and are filtering all traffic coming into or out of the network.
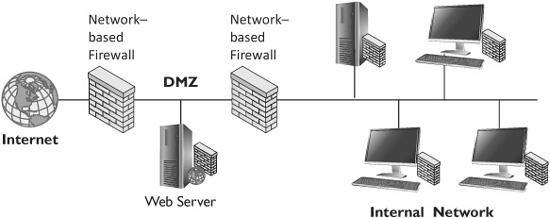
Figure 4-4 Network with host-based and network-based firewalls
Additionally, each internal system is running a host-based firewall that filters traffic coming into or out of the computer’s network interface card (NIC). Both servers and desktop operating systems can run a host-based firewall as an additional application. As an example, many antivirus vendors now include firewalls as part of a comprehensive security suite.

TIP Some operating systems include built-in host-based firewalls running as additional software. For example, current Microsoft desktop and server products include the Windows Firewall, which is enabled by default.
Most organizations use both network-based and host-based firewalls. The network-based firewall filters and blocks malicious traffic coming from the Internet. Internal host-based firewalls block malicious traffic that may be released internally.
For example, a user may unknowingly have a home computer infected with a virus. When transferring files from home to work with a USB flash drive, the user can infect the work computer just by inserting the USB flash drive into the work computer. This virus may then have a worm component that tries to locate and infect other systems on the network. However, if other systems have host-based firewalls installed, they can block the worm.
