Exploring Computer Forensics
Computer forensics is the science of examining and inspecting computer systems for evidence about an event or crime. The examination includes recovering data stored on or transmitted by any electronic device. The goal is to identify and recover evidence while ensuring that it is preserved so that it can be analyzed.
You’ve probably watched one of the CSI television shows where detectives use crime scene investigation (CSI) techniques to piece together the elements of a crime. Computer forensics use investigation techniques to try to piece together evidence to investigate computer abuse or computer crime.
First Responders and Preserving the Scene
Preserving the evidence is extremely important in a computer forensics investigation. If the evidence is not preserved, the analysis can’t be verified and can be considered tainted. Tainted evidence can be misleading and indicate that innocent people are guilty and that guilty people are innocent. If the evidence isn’t preserved it loses its value and can’t be used in a court of law.
Along these lines, many organizations recommend that computers be disconnected from a network as an initial step in a computer investigation. This isolates the system and prevents remote access. It prevents someone from remotely clearing logs or deleting data on the system. It’s also an important step to take if a system is suspected of being infected with malware, such as a worm, that may infect other systems on the network.
In the medical field, the first responder is the first medically trained person to arrive on the scene of an incident that requires medical knowledge. It can include Emergency Medical Services (EMS), Emergency Medical Technicians (EMTs), police, firefighters, or other personnel.
In the IT field, the first responder is the first forensics-trained person on the scene. This may be someone with advanced forensics training. It can also be an IT administrator who understands the basics of preserving forensics evidence and can manage the scene until a forensics expert arrives.
Medical first responders aren’t expected to have the same level of knowledge as a doctor. Instead, they’re expected to have enough knowledge to stabilize an injured person’s health until a more qualified professional arrives, or they are able to transport the injured person. Similarly, IT first responders aren’t expected to have the same level of knowledge as full-time forensics experts. However, they should know the basics of handling evidence, preserving the scene, and maintaining a chain of custody. You may be the first responder at the scene of an incident, so these are also basics you should understand.

EXAM TIP First responders are the first forensics-trained personnel on the scene of a computer incident. One of their primary responsibilities is the preservation of evidence.
Three Phases of a Computer Forensics Investigation
A computer forensics investigation is typically described as occurring in three phases of acquiring, authenticating, and analyzing the evidence as shown in Figure 13-1. IT professionals need to be aware of the three phases and understand their role if an incident occurs. For example, if IT professionals sound the alarm to report an incident, they need to know what their responsibilities are related to protecting the evidence prior to security professionals arriving to secure the evidence.
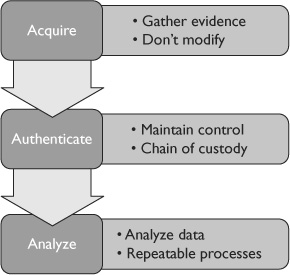
Figure 13-1 Three phases of a computer forensic investigation

EXAM TIP The ultimate goal of a computer forensics specialist is to acquire, authenticate, and analyze electronic evidence. It’s extremely important that evidence is not modified during this process.
Acquire the Evidence
In the acquisition phase, the investigators collect the evidence. It’s very easy to modify the evidence during this phase, so extra steps need to be taken to ensure that the evidence is preserved. For example, if you just open a file, you modify it because the file now shows a new access time.
Forensics experts use bit copy or drive imaging tools to capture the contents of a drive without modifying the data. This copy is known as a forensics duplicate image. In addition to copying data, this process includes copying free and slack space on the drive or partition. The copy must be an exact bit-by-bit copy of the original in order for it to be considered forensically sound. For example, Figure 13-2 shows the overall process of copying a drive. The original drive isn’t analyzed but instead the copy is examined. If the original data needs to be examined again, the forensics expert can create another copy of the original drive. Additionally, the original drive remains available as evidence in a court of law if required.
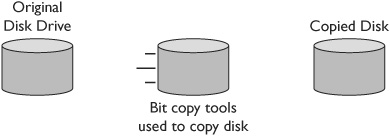
Figure 13-2 Using bit copy tools to capture drive contents
Other tools are available that can read and copy data from volatile memory. Volatile memory is any memory that requires power to keep the contents and these tools ensure that the data isn’t lost. Of course, the tools must be used before the system is powered down.

EXAM TIP It’s important that anyone who responds to an incident does not access any files on a system, or power a system down. These steps can modify or destroy evidence that may be valuable for an investigation. Before examining hard drives, you should be copy them using a bit copy tool.
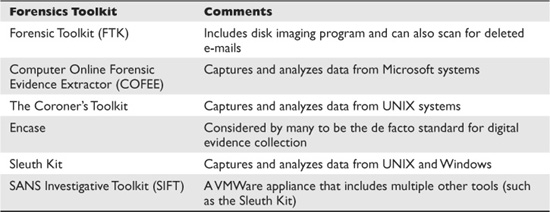
Years ago, there weren’t many tools available for computer forensics. However, more and more tools are being developed and are available to computer investigators. These tools allow investigators to capture data more efficiently, with less loss, and less effort. Table 13-1 shows some of the tools that are available.
Table 13-1 Common Forensics Toolkits
Authenticate the Evidence
As soon as evidence is collected, investigators create a chain of custody. This ensures that the evidence is never out of the investigators’ control and subject to tampering. A chain of custody shows exactly where a piece of evidence is from the point that it has been collected until it is disposed.
The chain of custody documents who obtained evidence, where it was obtained, when it was obtained, and how it was controlled since it was first collected. It provides proof that the evidence has been controlled since it was obtained and records every interaction with the evidence since it was obtained. Legal experts often use chain-of-custody forms to document the control of evidence. In the absence of a chain-of-custody form, control of the evidence can be questioned and the evidence may not be usable.

EXAM TIP Chain-of-custody documents provide proof that evidence has been protected. Without the chain of custody document, the validity of the evidence can be questioned and its usefulness negated.
In contrast, if an investigator acquires a laptop as evidence but then left it on a desk or in a desk drawer, anyone with access to the desk may be able access the laptop and modify or corrupt the data. The goal in the authentication phase is to ensure that the evidence is controlled and provide proof that it is controlled. Even if no one actually tampered with the laptop while it was in the desk drawer, without proof that a chain of custody was followed, the laptop may not be admissible as evidence in a court of law.
You can also authenticate files and drives by comparing a hash value of the original to a hash value of the copy. Hashing is explored in more depth in Chapter 14, but in short, a hashing algorithm creates a hash, which is simply a number. As long as the file or the drive has not been modified the hash will be the same. By comparing the hashes and ensuring they are the same, you can prove that it is a true forensic copy.
Analyze the Evidence
In the last phase of a computer investigation, the forensics experts analyze the evidence. One of the key requirements in this phase is to use repeatable processes by analyzing copies of the data whenever possible.
The science of computer forensics has advanced significantly in the last few years. There are many more college degrees and college courses focused on this science, and several specialized certifications are also available. Additionally, analysts in this field have much more sophisticated tools available that just weren’t available a mere ten years ago. For example, many of the tool suites mentioned in the “Acquire the Evidence” section also include tools used for analysis.
Forensic Evidence Guiding Principles
The International Organization on Computer Evidence (IOCE) holds periodic conferences and provides an international forum for law enforcement agencies to exchange information on computer investigation and digital forensic issues. The IOCE documented the following principles, which have been adopted by several countries around the world.
These principles are:
• When dealing with digital evidence, all of the general forensic and procedural principles must be applied.
• Upon seizing digital evidence, an agency must ensure that its actions do not change that evidence.
• When it is necessary for a person to access original digital evidence, that person should be trained for the purpose.
• All activity relating to the seizure, access, storage or transfer of digital evidence must be fully documented, preserved, and available for review.
• An individual is responsible for all actions taken with respect to digital evidence whilst the digital evidence is in his or her possession.
• Any agency that is responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles.

NOTE You don’t need to memorize these principles for the SSCP exam. However, they do provide a good overview of guidelines for anyone involved in the collection of evidence.
Volatile Data
Volatile data is data that will be lost if a system is powered down. Random access memory (RAM) is an example of volatile data and it often holds valuable data related to recent activity on a system that can be used in an investigation.
However, if the system is powered down before this data is collected, the data is lost. Several computer forensics tools are available that can capture volatile data before the system is shut down. There is very little possibility of retrieving information from volatile RAM after power has been removed.

EXAM TIP Systems that need to be investigated should not be powered down until an investigator has an opportunity to gather data. Data in volatile RAM can be captured with forensics tools before system is powered down, but once the system is powered down, this data is lost.
In contrast, some data on a system is persistent data. Persistent data is stored on a hard drive or other types of media such as optical discs or USB flash drives. Persistent data is retained even when a system is powered down.