JAAS Security
The Java Authentication and Authorization Service, as its name implies, consists of two main components: authentication and authorization components. The authentication is performed in a pluggable fashion because JAAS implements the standard Pluggable Authentication Module (PAM) framework, which is common on Unix platforms. This allows application code to be independent from the underlying security realm in the physical environment. Therefore, any new authentication mechanism can be plugged in as a module (similar to a driver) into the JAAS framework. Sample authentication mechanisms exist today for JNDI, Unix, and Windows NT.
After the user executing the code has been authenticated, the JAAS authorization component uses the access control model to protect access to sensitive resources. JAAS authorization is a user-based authorization with fine-grain permissions. Figure 19.4 illustrates JAAS architecture components.
Figure 19.4. JAAS architecture.

JAAS provides a means to enforce access controls based on where code came from and who signed it. JAAS is applied to all the Java 2 platform including applets, servlets, and EJBs.
JAAS Concepts
The JAAS API is provided by the javax.security package. The key JAAS class is Subject, which represents a grouping of related information for a single entity such as a person, organization, or a program. It encompasses the entity's principals, public credentials, and private credentials. The LoginContext interface is used to authenticate a Subject. Table 19.2 summarizes the interfaces and classes used in the java.security package.
The LoginContext represents the initial security context established in the application code, and encapsulates the underlying security realm. The main methods of the LoginContext interface are login(), logout(), and getSubject(). The main exception of the security package is LoginException.
The LoginModule class abstracts the authentication mechanism, and is similar to the driver or adapter that the JAAS API uses to access a particular authentication mechanism or realm. The EJB developer does not usually interface directly with the LoginModule unless it's required to develop a customized module for a new mechanism. The container provider is usually responsible for providing a LoginModule for each supported security realm.
After the Subject is authenticated, the access controls can be placed on that Subject by invoking the doAs() method of the Subject class. The doAs() method associates the specified Subject with the current security context. If the Subject has the necessary access controls, the action is completed; however, if the Subject does not have the necessary access controls, a security exception is raised.
During authentication, the Subject is populated with associated identities, or principals. A Subject may have many principals. For example, a student may have the name principal Laura Ghaly, the Social Security number principal 11-222-3333, and the user ID principal lghaly, all of which help distinguish this Subject from other Subjects. The Subject class provides a method getPrincipals() to query all of them.
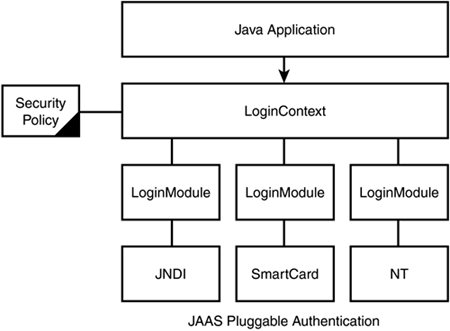
Figure 19.5. JAAS pluggable authentication.
The following example utilizes the doAs() method. We assume that a LoginContext has authenticated a Subject with the principal named Laura Ghaly.
// JAAS Authentication and Authorization
import java.security.*;
public class JAASClient extends Object {
public static void main(){
// Establish an initial security context
LoginContext logCtx = new LoginContext("Laura Ghaly");
// Authenticate the subject by try to login
try{
logCtx.login();
System.out.println("Login succeeded");
} catch (LoginException le) {
System.out.println("Login failed");
}
// Retrieve the authenticated subject from the context
Subject laura = logCtx.getSubject();
Subject.doAs(laura, new SimpleAction());
// Perform the SimpleAction as the authenticated subject: laura
// Try to logout after finish
try{
logCtx.logout();
System.out.println("Logout succeeded");
} catch (LoginException le) {
System.out.println("Logout failed");
}
}
In the preceding example, the security context will be propagated from the current code to the instantiated Java class SimpleAction on behalf of the principal Laura Ghaly.
