Chapter 17
Ten (or So) Ways to Make Your Phone Secure
IN THIS CHAPTER
![]() Keeping your phone in one piece
Keeping your phone in one piece
![]() Avoiding losing your phone in the first place
Avoiding losing your phone in the first place
![]() Protecting yourself if you do lose your phone
Protecting yourself if you do lose your phone
Back in the “old” days, it sure was frustrating to have your regular-feature phone lost or stolen. You would lose all your contacts, call history, and texts. Even if you backed up all your contacts, you would have to reenter them in your new phone. What a hassle.
Do I have your attention? Think of what would happen if someone were to get access to your PC at home or at work. He or she could wreak havoc on your life.
A malevolent prankster could send an email from your work email address under your name. It could be a rude note to the head of your company. It could give phony information about a supposedly imminent financial collapse of your company to the local newspaper. It could be a threat to the U.S. president, generating a visit from the Secret Service.
Here’s the deal: If you have done anything with your smartphone as described in this book past Chapter 3, I expect you’ll want to take steps to protect your smartphone. This is the burden of having a well-connected device. Fortunately, most of the steps are simple and straightforward.
Using a Good Case
The Samsung Galaxy S20 is sleek and beautiful. The Galaxy S20 has a really cool design that draws attention from people walking by. Plus, the front is made of Gorilla Glass from Corning. This stuff is super-durable and scratch-resistant.
So why am I telling you to cover this all up? It’s like buying a fancy dress for a prom or wedding and wearing a coat all night. Yup. It’s necessary for safe mobile computing.
There are lots of choices for cases. The most popular are made of silicone, plastic, or leather. There are different styles that meet your needs from many manufacturers.
Samsung offers several good options, as shown in Figure 17-1.

FIGURE 17-1: Samsung cases for the Galaxy S20E, S20, and S20+.
Otterbox is a brand that has been making cases for multiple levels of protection. The Defender Series for the Galaxy S20, its highest level of protection, is seen in black in Figure 17-2. You can get other levels of protection with more colors if you prefer.

FIGURE 17-2: Otterbox cases for the Samsung Galaxy S20, S20+, and S20 Ultra.
You don’t just use a good case so that you can hand off a clean used phone to the next lucky owner. A case makes it a little less likely that you will lose your phone. Your Galaxy S20 in its naked form is shiny glass and metal, which are slippery. Cases tend to have a higher coefficient of friction and prevent your phone from slipping out of your pocket when you take a ride in an Uber car.
More significantly, a case protects your phone against damage. If your phone is damaged, you have to mail it or bring it to a repair shop. The problem is that many people who bring their phones in for repair don’t wipe the personal information off their devices. You really hope that the repair shop can pop off the broken piece, pop on a new one, and send you on your way. It’s rarely that easy. Typically, you need to leave your phone in the hands of strangers for some period of time. For the duration of the repair, said strangers have access to the information on your phone.
The good news is that most workers who repair phones are professional and will probably ignore any information from the phone before they start fixing it.
However, are you sure that you want to trust the professionalism of a stranger? Also, do you really want the hassle of getting a new phone? Probably not, so invest in a good case and screen cover. There are many options for different manufacturers of cases. Be sure to shop around to come up with the ideal combination of protection and style right for you.
Putting It on Lockdown
Let’s start with the basics of the Lock Screen. When you leave your phone alone for a while, or when you’re doing something and you want to do something else, you can briefly press the power button to turn off the screen. This saves some power. Depending on what you want to do, you can make it easy or hard to return to using your phone by using the Lock Screen. The thinking is that you rarely lose your phone, or have it stolen when you’re actively using it. It typically disappears when you leave it alone for a while.
To protect the information you keep on your phone, your S20 has the option of a Lock Screen on which, in most circumstances, you need to prove to the phone that you’re you, and not some evildoer or a nosy family member. Figure 17-3 shows you a typical, and stylish, Lock Screen.

FIGURE 17-3: The Lock Screen.
The most basic effort you can take to protect your phone is to put some kind of a screen lock on your phone. If you’re connected to a corporate network, the company may have a policy that specifies what you must do to access your corporate network. Otherwise, you have seven choices, listed here in increasing degrees of security:
- None (as in your phone will open up to whatever was there before the screen image went dark).
- Unlock the Lock Screen with a simple swipe across the screen.
- Unlock with a pattern that you swipe on the screen.
- Unlock with a PIN.
- Unlock with facial recognition.
- Unlock with a password.
- Unlock with your fingerprint.
You can select any of these options in the Lock Screen option in Settings. Here’s what you do:
-
Tap the Settings icon.
This should be old hat by now.
-
Tap the Biometrics and Security link.
This brings up the options seen in Figure 17-4. You set some of the options mentioned in the preceding list and others when you follow the next instruction. This can be a little confusing, but bear with me while I explain your options and tell you where to go.
-
Tap the Screen Lock Type link.
This brings up the options seen in Figure 17-5. Each option prompts you through what it needs before establishing your security selection.

FIGURE 17-4: The Lock Screen options.

FIGURE 17-5: The Screen Lock options.
Preparing for your Screen Lock option
Regardless of what Screen Lock you choose, I recommend that you have ready the following choices at hand:
- An unlock pattern
- A PIN
- A password
- Your fingerprint
- Your face
To clarify definitions, a PIN is a series of numbers. In this case, the PIN is four digits. A password is a series of numbers, upper- and lowercase letters, and sometimes special characters, and is typically longer than four characters. A PIN is pretty secure, but a password is usually more secure. Have them both ready, but decide which one you would prefer to use.
Selecting among the Screen Lock options
The first option of skipping the whole lock screen thing altogether is your choice. Good luck with that one <sarcasm alert!>.
The second option, unlocking your phone with a swipe, fools exactly no one and doesn’t slow anyone down. Rather than just having the Home screen appear, your phone tells you to swipe your finger on the screen to get to the Home screen. This is about as secure as waving at intruders and tossing them your phone, wallet, and keys. The only reason to choose this over the first option is that you like to see, on occasion, the abstract image shown in Figure 17-3. Let’s keep going.
I recommend drawing out a pattern as the minimum screen-lock option. This is quick and easy. Tap the Pattern option on the screen seen in Figure 17-6 to get started. The phone asks you to enter your pattern and then asks you to enter it again. It then asks you to enter a PIN in case you forget your pattern.
The unlock pattern is a design that you draw with your finger on a nine-dot screen, as shown in Figure 17-6.
The image on the right in Figure 17-6 happens to include all nine dots. You do not need to use all the dots. The minimum number of dots you must touch is four. The upper limit is nine because you can touch each dot only once. As long as you can remember your pattern, feel free to be creative.

FIGURE 17-6: The unlock patterns: The blank screen and a sample pattern.
Each time you enter a Screen Lock option, two things may happen:
- If you’ve already entered a Screen Lock option, it may ask you to enter it. For example, if you’ve put in a pattern and you want to add a PIN, it may ask you to enter that pattern. This helps prevent someone from messing with your Screen Lock.
- After you enter your PIN, password, or whatever, your phone may ask if you want to save the pattern to your Samsung Account, as shown in Figure 17-7. It can’t hurt, so you may as well do it.
FIGURE 17-7: The option to back up your patterns.
The next two options on the Screen Lock screen, PIN and Password, are more secure, but only as long as you avoid the obvious choices. If you insist upon using the PIN “0000” or “1111” or the word “password” as your password, don’t waste your time. It’s standard operating procedure within the typical den of thieves to try these sequences first. That’s because so many people use these obvious choices.
Entering your face
Facial recognition is even easier! From the Settings page, tap the Biometrics and Security link. This brings up the screen shown in Figure 17-8.

FIGURE 17-8: The Biometrics and Security screen.
Tap the Face Recognition link. You’ll be prompted to hold the phone toward your face. The recognition screens are shown in Figure 17-9. They work remarkably fast.

FIGURE 17-9: The facial recognition screens for Mona Lisa.
Entering your fingerprints
Using your fingerprint to unlock your phone is very convenient and very effective. There are a few hoops you need to make this happen. You need to give your phone enough views of the finger you will use, which can be whichever finger you like, so that it is sure that it is you. It also wants to make sure that you, and only you, have stored a fingerprint. Your phone can store multiple fingers. Any of your fingers will work, so have at it.
Here’s what you do:
-
Tap the toggle option next to the Fingerprints option shown in Figure 17-8.
The leftmost screen in Figure 17-10 appears.
-
Press the fingerprint icon on the screen if you have an S20 or S20+. Run your finger over the Power button on the right side if you have an S20E.
Keep following the directions on the screen for how it wants you to move until you reach 100 percent. The screen in the middle of Figure 17-10 will eventually get tired of telling you to press hard, cover the sensor, and move the position of your finger. Before you know it, you’re at 100 percent.
Enjoy this keen sense of accomplishment, because in a moment, you will be asked if you want to put in another finger. I suggest that if you used your index finger, you should add your thumb.
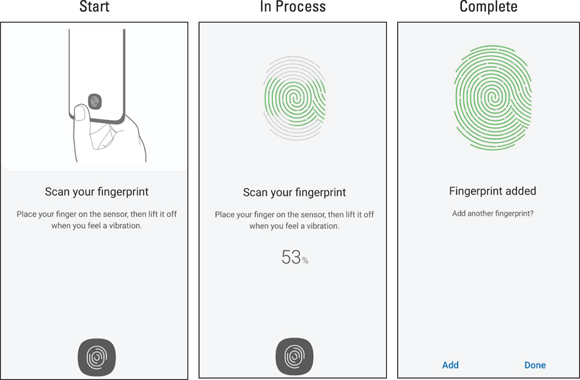
FIGURE 17-10: The Fingerprints registration screen.
Your fingerprints are now in memory and ready to let you get to your home page with a quick press or swipe. Give it a try. It is very slick!
Encrypting Your SD Card
This is an option to protect the data on your device. It’s an exceptionally secure option: It scrambles every file on your microSD card into gibberish, which it rapidly descrambles when you need the information. This sounds great; in practice, however, there are some important considerations to think about.
First, all this scrambling and descrambling takes processing power away from other things, such as running the apps. The loss is hardly noticeable in most cases — your phone is awash in processing power — but you never know when it may come back to bite you.
If you encrypt your SD card and then forget your password, your SD card is toast. You won’t be able to use these files ever again. Likewise, if you ever need to reset your phone to factory default settings, it won’t remember how to talk to this SD card. Once again, toast is the word to describe the SD card and the data on it.
If you’re sure that encryption is for you, here are the steps:
- From the Settings screen, select the Biometrics and Security option.
-
Tap the Encrypt SD Card link.
Doing so brings up the warning screen, as shown in Figure 17-11.
As the screen says, have your battery nicely charged, say, at 80 percent or higher, and an hour set aside when you don’t need to use your phone.
-
Tap the Encrypt SD Card option.
And off it goes… .
Keep in mind that this encryption is just for the data on your SD card. This does not touch the data that is stored on your phone.

FIGURE 17-11: The encryption warning screen.
Using Knox to Make Your Phone as Secure as Fort Knox
It doesn’t matter whether you bought the phone at a retail store or your company supplied it to you. The fact of the matter is that company data that resides on your phone belongs to your employer. You probably signed a document (now sitting in your HR file) that states that you agree with this arrangement.
This policy is necessary for the company because it has a financial and legal obligation to protect company data, particularly if it pertains to individual customers. Like it or not, this obligation trumps your sense of privacy over the phone you bought and (still) pay for. If this really gets under your skin, you can always carry two smartphones: one for business and one for personal use. This solves the problem, but it’s a hassle.
However, there is a better way. Samsung has a highly skilled group that has developed a secure system called Knox. Knox logically divides your phone into two modes: one for business use and the other for your personal use. You tap an icon, and you’re in business mode. You tap another icon, and you’re in personal mode. Switching between the two is instant, and Knox keeps the information from each mode separate.
When it is available, Knox comes with three capabilities for the employer:
- Security for the Android OS
- Limitations on the apps that access the business side of your phone
- Remote mobile-device management
This arrangement means that your employer can remotely control the business apps and potentially wipe the data on the business side at its discretion — but it has nothing to do with your personal information. The personal side remains your responsibility.
Being Careful with Bluetooth
In Chapter 3, I looked at syncing your phone with Bluetooth devices. I did not mention the potential for security risk at that point. I do it now.
Some people are concerned that people with a radio scanner can listen in on their voice calls. This was possible, but not easy, in the early days of mobile phone use. Your Galaxy S20 can use only digital systems, so picking your conversation out of the air is practically impossible.
Some people are concerned that a radio scanner and a computer can pick up your data connection. It’s not that simple. Maybe the NSA could get some of your data that way using complicated supercomputing algorithms, but it’s much easier for thieves and pranksters to use wired communications to access the accounts of the folks who use “0000” as their PIN and “password” or “password1” as their password.
Perhaps the greatest vulnerability your phone faces is called bluejacking, which involves using some simple tricks to gain access to your phone via Bluetooth.
Do a test: The next time you’re in a public place, such as a coffee shop, a restaurant, or a train station, turn on Bluetooth. Tap the button that makes you visible to all Bluetooth devices and then tap Scan. While your Bluetooth device is visible, you’ll see all the other Bluetooth devices in your vicinity. You’ll probably find lots of them. If not, try this at an airport. Wow!
If you were trying to pair with another Bluetooth device, you’d be prompted to see whether you’re willing to accept connection to that device. In this case, you are not.
However, a hacker will see that you are open for pairing and take this opportunity to use the PIN 0000 to make a connection. When you’re actively pairing, your Bluetooth device won’t accept an unknown device’s offer to pair. But if your device is both unpaired and visible, hackers can fool your Bluetooth device and force a connection.
After a connection is established, all your information is available to the hackers to use as they will. Here are the steps to protect yourself:
- Don’t pair your phone to another Bluetooth device in a public place. Believe it or not, crooks go to public places to look for phones in pairing mode. When they pair with a phone, they look for interesting data to steal. It would be nice if these people had more productive hobbies, like Parkour or searching for Bigfoot. However, as long as these folks are out there, it is safer to pair your Bluetooth device in a not-so-public place.
- Make sure that you know the name of the device with which you want to pair. You should pair only with that device. Decline if you are not sure or if other Bluetooth devices offer to connect.
- Shorten the default time-out setting. The default is that you will be visible for two minutes. However, you can go into the menu settings and change the option for Visible Time-out to whatever you want. Make this time shorter than two minutes. Don’t set it to Never Time Out. This is like leaving the windows open and the keys in the ignition on your Cadillac Escalade. A shorter time of visibility means that you have to be vigilant for less time.
- From time to time, check the names of the devices that are paired to your device. If you don’t recognize the name of a device, click the Settings icon to the right of the unfamiliar name and unpair it. Some damage may have been done by the intruder, but with any luck, you’ve nipped it in the bud.
Here’s an important point: When handled properly, Bluetooth is as secure as can be. However, a few mistakes can open you up to human vermin with more technical knowledge than decency. Don’t make those mistakes, and you can safely enjoy this capability, knowing that all the data on your phone is safe.
Protecting against Malware
One of the main reasons application developers write apps for Android is that Google doesn’t have an onerous preapproval process for a new app to be placed in the Play Store. This is unlike the Apple App Store or Microsoft Windows Phone Store, where each derivation of an app must be validated.
Many developers prefer to avoid bureaucracy. At least in theory, this attracts more developers to do more stuff for Android phones.
However, this approach does expose users like you and me to the potential for malware that can, inadvertently or intentionally, do things that are not advertised. Some of these “things” may be minor annoyances, or they could really mess up your phone (for openers).
Market forces, in the form of negative feedback, are present to kill apps that are badly written or are meant to steal your private data. However, this informal safeguard works only after some poor soul has experienced problems — such as theft of personal information — and reported it.
Rather than simply avoiding new apps, you can download apps designed to protect the information on your phone. These are available from many of the firms that make antivirus software for your PC. Importantly, many of these antivirus applications are free. If you want a nicer interface and some enhanced features, you can pay a few dollars, but it isn’t necessary.
Examples include NQ Mobile Security and Antivirus, Lookout Security and Antivirus, Kaspersky Mobile Security, and Norton Security Antivirus. If you have inadvertently downloaded an app that includes malicious software, these apps will stop that app.
Downloading Apps Only from Reputable Sources
Another way to avoid malware is to download mobile software only from trustworthy websites. This book has focused exclusively on the Google Play Store. You can download Android apps for your phone from a number of other reputable sites, including Amazon Appstore and GetJar.
Keep in mind that these stores are always on the lookout to withdraw applications that include malicious software. Google uses an internally developed solution it calls Bouncer to check for malicious software and remove it from the Play Store. Other mobile software distribution companies have their own approaches to addressing this problem. The problem is that policing malicious software is a hit-or-miss proposition.
As a rule, you should hesitate to download an Android app unless you know where it has been. You are safest if you restrict your app shopping to reputable companies. Be very skeptical of any other source of an Android app.
Rescuing Your Phone When It Gets Lost
Other options allow you to be more proactive than waiting for a Good Samaritan to reach out to your home phone or email if you lose your phone.
There are apps that help you find your phone. Here are a few several “lost it” scenarios and some possible solutions for your quandary:
-
You know that you lost your phone somewhere in your house. You would try calling your own number, but you had your phone set to Vibrate Only mode.
Solution: Remote Ring. By sending a text to your phone with the “right” code that you preprogrammed when you set up this service, your phone will ring on its loudest setting, even if you have the ringer set to Vibrate Only.
 If you know that your phone is in your house, the accuracy of GPS isn’t savvy enough to tell you whether it’s lost between the seat cushions of your couch or in the pocket of your raincoat. That’s where the Remote Ring feature comes in handy.
If you know that your phone is in your house, the accuracy of GPS isn’t savvy enough to tell you whether it’s lost between the seat cushions of your couch or in the pocket of your raincoat. That’s where the Remote Ring feature comes in handy. -
You lost your phone while traveling and have no idea whether you left it in a taxi or at airport security.
Solution: Map Current Location. This feature allows you to track, within the accuracy of the GPS signal, the location of your phone. You need access to the website of the company with which you arranged to provide this service, and it will show you (on a map) the rough location of your phone.
Here is where having an account with Samsung comes in handy. Hopefully, you signed up for a Samsung Account when you first got your phone. If you did, you’re signed up for the Find My Mobile at http://findmymobile.samsung.com. Figure 17-12 shows the Find My Mobile PC screen.

FIGURE 17-12: The Samsung Find My Mobile PC screen.
You can see from this screen that my phone is at 935 Pennsylvania Ave. NW, Washington, DC, which happens to be the headquarters for the FBI. All you need to do is get to a PC and sign in to your Samsung account (unless your phone is at the FBI). You can tell your phone to ring by clicking on Ring My Device. You can have the PC bring up a map by clicking Locate My Device.
I suggest trying these out before you lose your phone the first time.
Wiping Your Device Clean
As a last-ditch option, you can use Find My Mobile (see preceding section) to remotely disable your device or wipe it clean. Here are some of the possible scenarios:
-
You were robbed, and a thief has your phone.
Solution: Remote Lock. After your phone has been taken, this app allows you to create a four-digit PIN that, when sent to your phone from another mobile phone or a web page, locks down your phone. This capability is above and beyond the protection you get from your Screen Lock and prevents further access to applications, phone, and data.
 If you know that your phone was stolen — that is, not just lost — do not try to track down the thief yourself. Get the police involved and let them know that you have this service on your phone — and that you know where your phone is.
If you know that your phone was stolen — that is, not just lost — do not try to track down the thief yourself. Get the police involved and let them know that you have this service on your phone — and that you know where your phone is. -
You’re a very important executive or international spy. You stored important plans on your phone, and you have reason to believe that the “other side” has stolen your phone to acquire your secrets.
Solution: Remote Erase. Also known as Remote Wipe, this option resets the phone to its factory settings, wiping out all the information and settings on your phone.
 You can’t add Remote Erase after you’ve lost your phone. You must sign up for your Samsung service beforehand. It’s not possible to remotely enable this capability to your phone. You need to have your phone in hand when you download and install either a lock app or a wipe app.
You can’t add Remote Erase after you’ve lost your phone. You must sign up for your Samsung service beforehand. It’s not possible to remotely enable this capability to your phone. You need to have your phone in hand when you download and install either a lock app or a wipe app.
