Chapter 12
SET for E-Commerce Transactions
The Secure Electronic Transaction (SET) is a protocol designed for protecting credit card transactions over the Internet. It is an industry-backed standard that was formed by MasterCard and Visa (acting as the governing body) in February 1996. To promote the SET standard throughout the payments community, advice and assistance for its development have been provided by IBM, GTE, Microsoft, Netscape, RSA, SAIC, Terisa, and Verisign.
SET relies on cryptography and X.509 v3 digital certificates to ensure message confidentiality and security. SET is the only Internet transaction protocol to provide security through authentication. It combats the risk of transaction information being altered in transit by keeping information securely encrypted at all times and by using digital certificates to verify the identity of those accessing payment details. The specifications of and ways to facilitate secure payment card transactions on the Internet are fully explored in this chapter.
12.1 Business Requirements for SET
This section describes the major business requirements for credit card transactions by means of secure payment processing over the Internet. They are listed below:
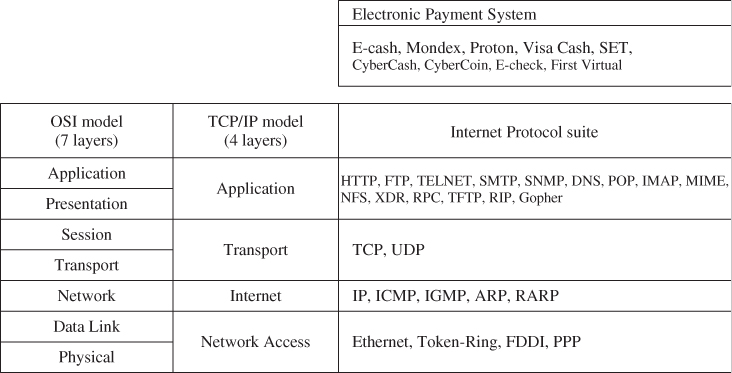
Figure 12.1 TCP/IP model and Internet Protocol suite. OSI, Open Systems Interconnect (seven layers); TCP/IP, Transmission Control Protocol/Internet Protocol (four layers).
12.2 SET System Participants
The participants in the SET system interactions are described in this section. A discrepancy is found between an SET transaction and a retail or mail order transaction: in a face-to-face retail transaction, electronic processing begins with the merchant or the acquirer, but in an SET transaction, the electronic processing begins with the cardholder.
- Cardholder. In the electronic commerce environment, consumers or corporate purchasers interact with merchants on personal computers over the Internet. A cardholder is an authorized holder of a payment card that has been issued by an issuer. In the cardholder's interactions, SET ensures that the payment card account information remains confidential.
- Issuer. An issuer is a financial institution (a bank) that establishes an account for a cardholder and issues the payment card. The issuer guarantees payment for authorized transactions using the payment card.
- Merchant. A merchant is a person or an organization that offers goods or services for sale to the cardholder. Typically, these goods or services are offered via a Web site or by e-mail. With SET, the merchant can offer its cardholders secure electronic interactions. A merchant that accepts payment cards must have a relationship with an acquirer (a financial institution).
- Acquirer. An acquirer is the financial institution that establishes an account with a merchant and processes payment card authorization and payments. The acquirer provides authentication to the merchant that a given card account is active and that the proposed purchase does not exceed the credit limit. The acquirer also provides electronic transfer of payments to the merchant's account. Subsequently, the acquirer is reimbursed by the issuer over some sort of payment network for electronic funds transfer (EFT).
- Payment gateway. A payment gateway acts as the interface between a merchant and the acquirer. It carries out payment authorization services for many card brands and performs clearing services and data capture. A payment gateway is a device operated by the acquirer or a designated third party that processes merchant payment messages (PMs), including payment instructions from cardholders. The payment gateway functions as follows: it decrypts the encoded message, authenticates all participants in atransaction, and reformats the SET message into a format compliant with the merchant's point of sale system. Note that issuers and acquirers sometimes choose to assign the processing of payment card transactions to third-party processors.
- Certification Authority. A CA is an entity that is trusted to issue X.509 v3 public-key certificates for cardholders, merchants, and payment gateways. The success of SET will depend on the existence of a CA infrastructure available for this purpose. The primary functions of the CA are to receive registration requests, process and approve/decline requests, and issue certificates. A financial institution may receive, process, and approve certificate requests for its cardholders or merchants and forward the information to the appropriate payment card brand(s) to issue the certificates. An independent Registration Authority (RA) that processes payment card certificate requests and forwards them to the appropriate issuer or acquirer for processing. The financial institution (issuer or acquirer) forwards approved requests to the payment card brand to issue the certificates.
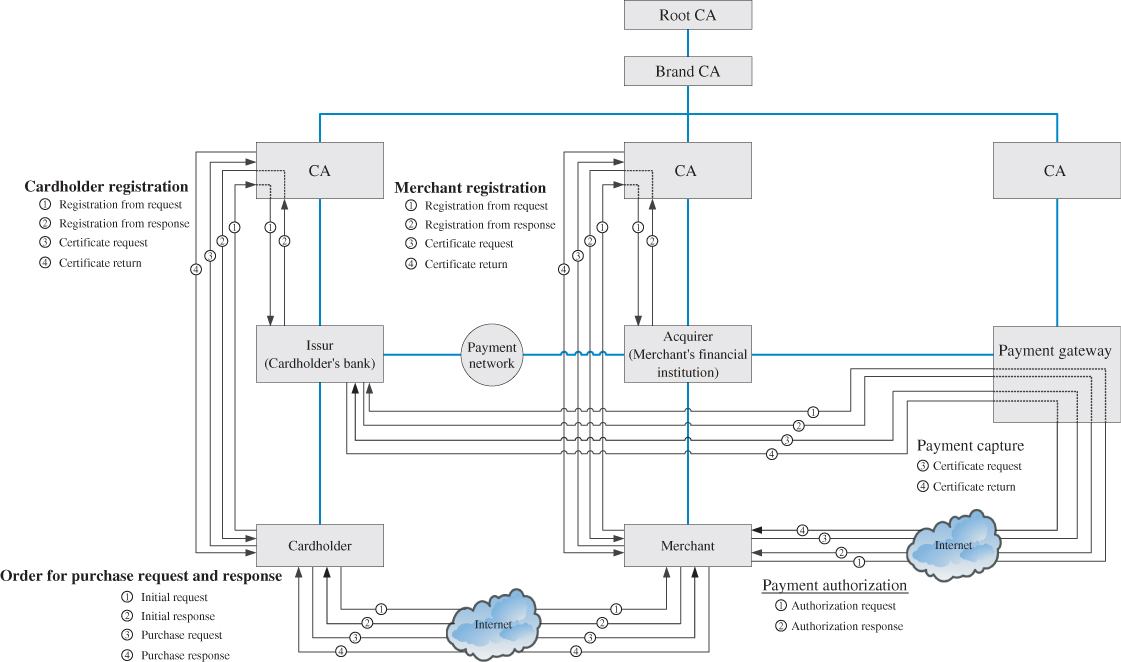
Figure 12.2 illustrates the SET hierarchy which reflects the relationships between the participants in the SET system, described in the preceding paragraphs. In the SET environment, there exists a hierarchy of CAs. The SET protocol specifies a method of trust chaining for entity authentication. This trust chain method entails the exchange of digital certificates and verification of the public keys by validating the digital signatures of the issuing CA. As indicated in Figure 12.2, this trust chain method continues all the way up to the root CA at the top of the hierarchy.
Figure 12.2 The SET transaction hierarchy indicating the relationships between the participants.
12.3 Cryptographic Operation Principles
SET is the Internet transaction protocol providing security by ensuring confidentiality, data integrity, authentication of each party, and validation of the participant's identity. To meet these requirements, SET incorporates the following cryptographic principles:
- Confidentiality. This is ensured by the use of message encryption. SET relies on encryption to ensure message confidentiality. In SET, message data is encrypted with a random symmetric key which is further encrypted using the recipient's public key. The encrypted message along with this digital envelope is sent to the recipient. The recipient decrypts the digital envelope with a private key and then uses the symmetric key in order to recover the original message.
- Integrity. This is ensured by the use of a digital signature. Using the public/private-key pair, data encrypted with either key can be decrypted with the other. This allows the sender to encrypt a message using the sender's private key. Any recipient can determine that the message came from the sender by decrypting the message using the sender's public key. With SET, the merchant can be assured that the order it received is what the cardholder entered. SET guarantees that the order information is not altered in transit. Note that the roles of the public and private keys are reversed in the digital signature process where the private key is used to encrypt for signature and the public key is used to decrypt for verification of signature.
- Authentication. This is also ensured by means of a digital signature, but it is further strengthened by the use of a CA. When two parties conduct business transactions, each party wants to be sure that the other is authenticated. Before a user B accepts a message with a digital signature from a user A, B wants to be sure that the public key belongs to A. One way to secure delivery of the key is to utilize a CA to authenticate that the public key belongs to A. A CA is a trusted third party that issues digital certificates. Before it authenticates A's claims, a CA could supply a certificate that offers a high assurance of personal identity. This CA may require A to confirm his or her identity prior to issuing a certificate. Once A has provided proof of his or her identity, the CA creates a certificate containing A's name and public key. This certificate is digitally signed by the CA. It contains the CA's identification information, as well as a copy of the CA's public key. To get the most benefit, the public key of the CA should be known to as many people as possible. Thus, by trusting a single key, an entire hierarchy can be established in which one can have a high degree of trust.
The SET protocol utilizes cryptography to provide confidentiality of information, ensure payment integrity, and ensure identity authentication. For authentication purposes, cardholders, merchants, and acquirers (financial institutions) will be issued with digital certificates by their sponsoring CAs. The certificates are digital documents attesting to the binding of a public key to an individual user. They allow verification of the claim that a given public key does indeed belong to a given individual user.
12.4 Dual Signature and Signature Verification
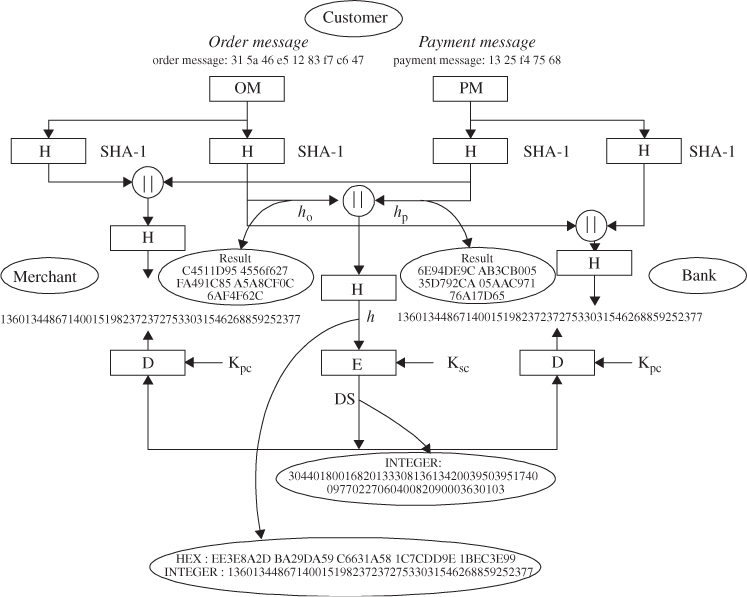
SET introduced a new concept of digital signature called dual signatures (DSs). A DS is generated by creating the message digest of two messages: order digest and payment digest. Referring to Figure 12.3, the customer takes the hash codes (message digests) of both the order message (OM) and PM by using the SHA-1 algorithm. These two hashes, ![]() and
and ![]() , are then concatenated and the hash code h of the result is taken. Finally, the customer encrypts (via RSA) the final hash code with his or her private key,
, are then concatenated and the hash code h of the result is taken. Finally, the customer encrypts (via RSA) the final hash code with his or her private key, ![]() , creating the DS. Computation of the DS is shown as follows:
, creating the DS. Computation of the DS is shown as follows:

Figure 12.3 Dual signature and order/payment message authentication.

![]()
Since SHA-1 sequentially processes blocks of 512 bits, that is, sixteen 32-bit words, the message padding must attach to the message block to ensure that a final padded message becomes a multiple of 512 bits. The 160-bit message digest can be computed from hashing the 512-bit padded message by the use of SHA-1. The padded OM and PM messages are, respectively,


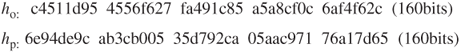
Figure 12.4 Computational analysis for the dual signature relating to Example 12.1.

![]()
Transforming this resulting hash into decimal numbers yields:
![]()
The concatenated two hashes become the input to the SHA-1 hash function. Thus, the resulting hash code h is RSA encrypted with the customer's private key ![]() in order to obtain the DS.
in order to obtain the DS.

![]()
This is the DS formula. Now, the DS represented in RSA-encrypted decimals can be computed as:
![]()
- Merchant's signature verification. Since the merchant has the customer's public key
 , the merchant can decrypt the DS by making use of
, the merchant can decrypt the DS by making use of 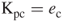 as follows:
as follows:
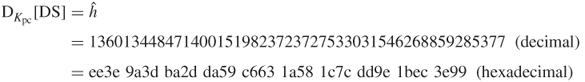 Now assume that the merchant is in possession of the OM and the message digest for the PM
Now assume that the merchant is in possession of the OM and the message digest for the PM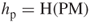 . Then, the merchant can compute the following quantity:
. Then, the merchant can compute the following quantity: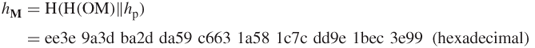 Since
Since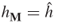 is proved, the merchant has received OM and verified the signature.
is proved, the merchant has received OM and verified the signature. - Bank's signature verification. Similarly, if the bank is in possession of DS, PM, the message digest
 for OM, and the customer's public key
for OM, and the customer's public key  , then it can compute the following quantity:
, then it can compute the following quantity:
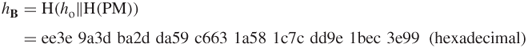 Since these two quantities are equal,
Since these two quantities are equal, , then the bank has verified the signature upon received PM.
, then the bank has verified the signature upon received PM.
12.5 Authentication and Message Integrity
When user A wishes to sign the plaintext information and send it in an encrypted message (ciphertext) to user B, the entire encryption process is as configured in Figure 12.5. The encryption/decryption processes for message integrity consist of the following steps.
Figure 12.5 Encryption/Decryption overview for message integrity.
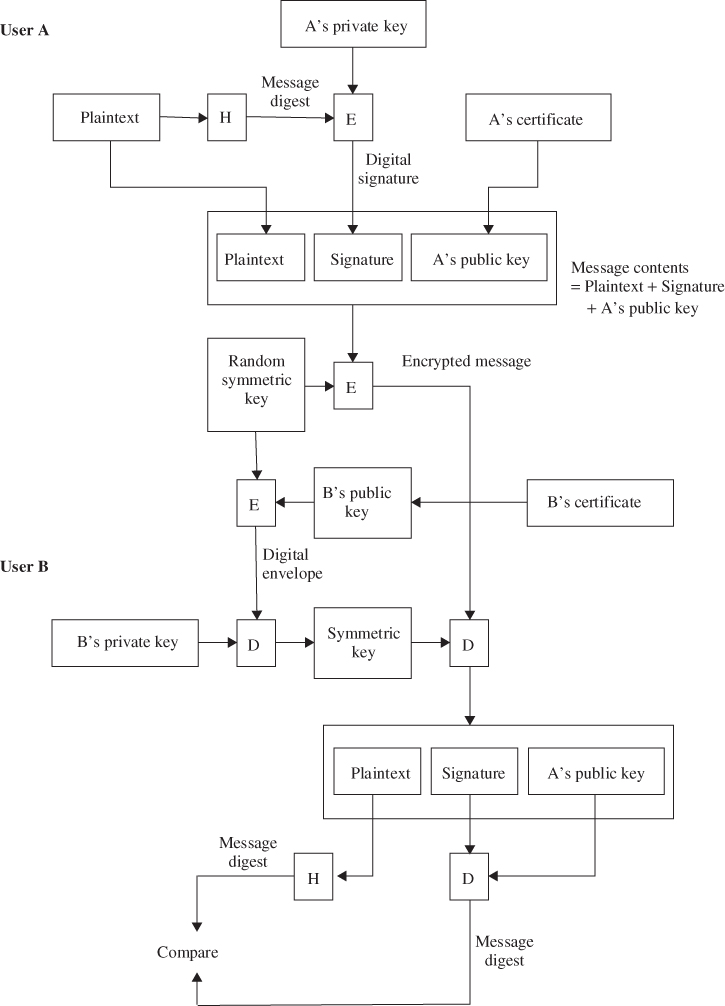
- User A sends the plaintext through a hash function to produce the message digest that is used later to test the message integrity.
- A then encrypts the message digest with his or her private key to produce the digital signature.
- Next, A generates a random symmetric key and uses it to encrypt the plaintext, A's signature, and a copy of A's certificate, which contains A's public key. To decrypt the plaintext later, user B will require a secure copy of this temporary symmetric key.
- B's certificate contains a copy of his or her public key. To ensure secure transmission of the symmetric key, A encrypts it using B's public key. The encrypted key, called the digital envelope, is sent to B along with the encrypted message itself.
- A sends a message to B consisting of the DES-encrypted plaintext, signature and A's public key, and the RSA-encrypted digital envelope.
- B receives the encrypted message from A and decrypts the digital envelope with his or her private key to retrieve the symmetric key.
- B uses the symmetric key to decrypt the encrypted message, consisting of the plaintext, A's signature, and A's public key retrieved from A's certificate.
- B decrypts A's digital signature with A's public key that is acquired from A's certificate. This recovers the original message digest of the plaintext.
- B runs the plaintext through the same hash function used by A and produces a new message digest of the decrypted plaintext.
- Finally, B compares his or her message digest to the one obtained from A's digital signature. If they are exactly the same, B confirms that the message content has not been altered during transmission and it was signed using A's private key. If they are not the same then the message either originated somewhere else or was altered after it was signed. In that case, B discards the message.
![]()
The 160-bit message digest is computed from hashing the 512-bit padded plaintext by the use of SHA-1 as follows:
![]()
User A picks two random primes ![]() and
and ![]() . Compute the product
. Compute the product ![]() and
and ![]() . Suppose the A's public key is
. Suppose the A's public key is ![]() . Then, A's private key
. Then, A's private key ![]() is computed using the extended Euclidean algorithm as:
is computed using the extended Euclidean algorithm as:
![]()
A's private key is used to sign (encrypt) the 160-bit message digest h to produce the digital signature ![]() :
:
![]()
Now, the message contents consist of the plaintext P, signature ![]() , and A's public key
, and A's public key ![]() as follows:
as follows:
![]()
A generates a random symmetric key K:
![]()
Using this symmetric key, A encrypts the concatenated message contents as:
![]()
and then sends them to user B.
Assume that B's public key, ![]() , is obtained from B's certificate. The symmetric key K is encrypted with B's public key to generate the digital envelope, which is computed as:
, is obtained from B's certificate. The symmetric key K is encrypted with B's public key to generate the digital envelope, which is computed as:
![]()
B's private key ![]() is computed using the extended Euclidean algorithm as:
is computed using the extended Euclidean algorithm as:
![]()
The symmetric key K is recovered by decrypting the digital envelope with B's private key ![]() .
.
![]()
Using the recovered symmetric key, the encrypted message contents are decrypted to obtain the message contents (![]() ). The message digest is computed by decrypting the recovered signature with A's public key, and it results in:
). The message digest is computed by decrypting the recovered signature with A's public key, and it results in:
![]()
Next, the message digest is obtained using the SHA-1 hash function of the recovered plaintext. It results in the following message digest:
![]()
Thus, the MIC is completely accomplished because these two message digests are identical. Figure 12.6 gives full details of the MIC relating to this example.
Figure 12.6 Message integrity check relating to Example 12.2.

12.6 Payment Processing
This section describes several transaction protocols needed to securely conduct payment processing by utilizing the cryptographic concepts introduced in Sections 12.5. The best detailed overview of SET specification appears in Book 1: Business Description issued in May 1997 by MasterCard and Visa. The following descriptions of secure payment processing are largely based on this book of the SET specification.
Figure 12.7 shows an overview of secure payment processing and it is worth looking at the outlines of several transaction protocols before reading the following detailed discussion.
Figure 12.7 Overall picture of payment processing.

12.6.1 Cardholder Registration
The cardholder must register with a CA before sending SET messages to the merchant. The cardholder needs a public/private-key pair for use with SET. The scenario of cardholder registration is described in the following.

- The cardholder sends the initiate request to the CA.
- Once the initiate request is received from the cardholder, the CA generates the response and digitally signs it by generating a message digest of the response and encrypting it with the CA's private key.
- The CA sends the initiate response along with the CA certificate to the cardholder.
- The cardholder receives the initiate response and verifies the CA certificate by traversing the trust chain to the root key.
- The cardholder verifies the CA certificate by decrypting it with the CA's public key and comparing the result with a newly generated message digest of the initiate response.
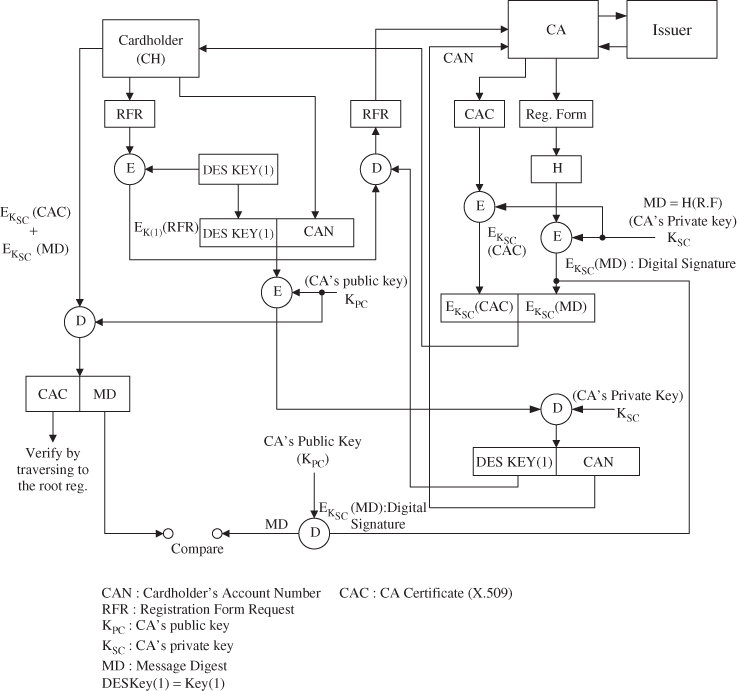
- The cardholder generates the registration form request.
- The cardholder encrypts the SET message with a random symmetric key (No. 1). The DES key, along with the cardholder's account number, is then encrypted with the CA's public key.
- The cardholder transmits the encrypted registration form request to the CA.
- The CA decrypts the symmetric DES key (No. 1) and cardholder's account number with the CA's private key. The CA then decrypts the registration form request using the symmetric DES key (No. 1).
- The CA determines the appropriate registration form and digitally signs it by generating a message digest of the registration form and encrypting it with the CA's private key.
- The CA sends the registration form and the CA certificate to the cardholder.
- The cardholder receives the registration form and verifies the CA certificate by traversing the trust chain to the root key.
- The cardholder verifies the CA's signature by decrypting it with the CA's public key and comparing the result with a newly generated message digest of the registration form. The cardholder then completes the registration form.
- The cardholder generates the certificate request, including the information entered into the registration form.
- The cardholder creates a message with request, the cardholder's public key and a newly generated symmetric key (No. 2), and digitally signs it by generating a message digest of the cardholder's private key.
- The cardholder encrypts the message with a randomly generated symmetric key (No. 3). This symmetric key, along with the cardholder's account information, is then encrypted with the CA's public key.
- The cardholder transmits the encrypted certificated request messages to the CA.
- The CA decrypts the No. 3 symmetric key and cardholder's account information with the CA's private key and then decrypts the certificate request using this symmetric key.
- The CA verifies the cardholder's signature by decrypting it with the cardholder's public key and comparing the result with a newly generated message digest of the certificate requested.
- The CA verifies the certificate request using the cardholder's account information and information from the registration form.
- Upon verification, the CA creates the cardholder certificate, digitally signing it with the CA's private key.
- The CA generates the certificate response and digitally signs it by generating a message digest of the response and encrypting it with the CA's private key.
- The CA encrypts the certificate response with the No. 2 symmetric key from the cardholder request.
- The CA transmits the certificate response to the cardholder.
- The cardholder verifies the certificate by traversing the trust chain to the root key.
- The cardholder decrypts the response using the symmetric key (No. 2) saved from the cardholder request process.
- The cardholder verifies the CA's signature by decrypting it with the CA's public key and comparing the result with a newly generated message digest of the response.
- The cardholder stores the certificate and information from the response for future e-commerce use.
12.6.2 Merchant Registration
Merchants must register with a CA before they can receive SET payment instructions from cardholders. In order to send SET messages to the CA, the merchant must have a copy of the CA's public key which is provided in the CA certificate. The merchant also needs the registration form from the acquirer. The merchant must identify the acquirer to the CA. The merchant registration process consists of five steps as follows: (i) The merchant requests the registration form; (ii) the CA processes this request and sends the registration form; (iii) the merchant requests certificates after receiving the registration certificates; (iv) the CA creates certificates; and (v) the merchant receives certificates.
The detailed steps for the merchant registration are described in what follows.
- The merchant sends the initiate request of the registration form to the CA. To register, the merchant fills out the registration form with information such as the merchant's name, address, and ID.
- The CA receives the initiate request.
- The CA selects an appropriate registration form and digitally signs it by generating a message digest of the registration form and encrypting it with the CA's private key.
- The CA sends the registration form along with the CA certificate to the merchant.
- The merchant receives the registration form and verifies the CA certificate by traversing the trust chain to the root key.
- The merchant verifies the CA's signature by decrypting it with the CA's public key and comparing the result with a newly computed message digest of the registration form.
- The merchant creates two public/private-key pairs for use with SET: key encryption and signature.
- The merchant generates the certificate request.
- The merchant creates the message with request and both merchant public keys and digitally signs it by generating a message digest of the certificate request and encrypting it with the merchant's private key.
- The merchant encrypts the message with a random symmetric key (No. 1). This symmetric key, along with the merchant's account data, is then encrypted with the CA's public key.
- The merchant transmits the encrypted certificate request message to the CA.
- The CA decrypts the symmetric key (No. 1) and the merchant's account data with the CA's private key and then decrypts the message using the symmetric key (No. 1).
- The CA verifies the merchant's signature by decrypting it with the merchant's public key and comparing the result with a newly computed message digest of the certificate request.
- The CA confirms the certificate request using the merchant information.
- Upon verification, the CA creates the merchant certificate digitally signing the certificate with the CA's private key.
- The CA generates the certificate response and digitally signs it by generating a message digest of the response and encrypting it with the CA's private key.
- The CA transmits the certificate response to the merchant.
- The merchant receives the certificate response from the CA. The merchant decrypts the digital envelope to obtain the symmetric key. This key is used to decrypt the registration response containing the certificates.
- The merchant verifies the certificates by traversing the trust chain to the root key.
- The merchant verifies the CA's signature by decrypting it with the CA's public key and comparing the result with a newly computed message digest of the certificate response.
- The merchant stores the certificates and information from the response for use in future e-commerce transactions.
12.6.3 Purchase Request
The purchase request exchange should take place after the cardholder has completed browsing, selecting, and ordering. Before the end of this preliminary phase occurs, the merchant sends a completed order form to the cardholder (customer). In order to send SET messages to a merchant, the cardholder must have a copy of the certificates of the merchant and the payment gateway. The message from the cardholder indicates which payment card brand will be used for the transaction. The purchase request exchange consists of four messages: initiate request, initiate response, purchase request, and purchase response. The detailed discussions that follow describe each step fully.
- The cardholder sends the initiate request to the merchant.
- The merchant receives the initiate request.
- The merchant generates the response and digitally signs it by generating a message digest of the response and encrypting it with the merchant's private key.
- The merchant sends the response along with the merchant and payment gateway certificates to the cardholder.
- The cardholder receives the initiate response and verifies the certificates by traversing the trust chain to the root key.
- The cardholder verifies the merchant's signature by decrypting it with the merchant's public key and comparing the result with a newly computed message digest of the response.
- The cardholder creates the OM using information from the shopping phase and PM. At this step, the cardholder completes payment instructions.
- The cardholder generates a dual signature for the OM and the PM by computing the message digests of both, concatenating the two digests, computing the message digest of the result, and encrypting it using the cardholder's private key.
- The cardholder generates a random symmetric key (No. 1) and uses it to encrypts the PM. The cardholder then encrypts his or her account number as well as the random symmetric key used to encrypt the PM in a digital envelope using the payment gateway's key.
- The cardholder transmits the OM and the encrypted PM to the merchant.
- The merchant verifies the cardholder certificate by traversing the trust chain to the root key.
- The merchant verifies the cardholder's DS on the OM by decrypting it with the cardholder's public key and comparing the result with a newly computed message digest of the concatenation of the message digests of the OM and PM.
- The merchant processes the request, including forwarding the PM to the payment gateway for authorization.
- The merchant creates the purchase response including the merchant signature certificate and digitally signs it by generating a message digest of the purchase response and encrypting it with the merchant's private key.
- The merchant transmits the purchase response to the cardholder.
- If the transaction was authorized, the merchant fulfills the order to the cardholder.
- The cardholder verifies the merchant signature certificate by traversing the trust chain to the root key.
- The cardholder verifies the merchant's digital signature by decrypting it with the merchant's public key and comparing the result with a newly computed message digest of the purchase response.
- The cardholder stores the purchase response.
12.6.4 Payment Authorization
During the processing of an order from a cardholder, the merchant authorizes the transaction. The authorization request and the cardholder payment instructions are then transmitted to the payment gateway.
- The merchant creates the authorization request.
- The merchant digitally signs an authorization request by generating a message digest of the authorization request and encrypting it with the merchant's private key.
- The merchant encrypts the authorization request using a random symmetric key (No. 2), which in turn is encrypted with the payment gateway public key.
- The merchant transmits the encrypted authorization request and the encrypted PM from the cardholder purchase request to the payment gateway.
- The gateway verifies the merchant certificate by traversing the trust chain to the root key.
- The payment gateway decrypts the digital envelope of the authorization request to obtain the symmetric encryption key (No. 2) with the gateway private key. The gateway then decrypts the authorization request using the symmetric key (No. 2).
- The gateway verifies the merchant's digital signature by decrypting it with the merchant's public key and comparing the result with a newly computed message digest of the authorization request.
- The gateway verifies the cardholder's certificate by traversing the trust chain to the root key.
- The gateway decrypts the symmetric key (No. 1) and the cardholder account information with the gateway private key. It uses the symmetric key to decrypt the PM.
- The gateway verifies the cardholder's DS on the PM by decrypting it with the cardholder's public key and comparing the result with a newly computed message digest of the concatenation of the message digest of the OM and the PM.
- The gateway ensures consistency between the merchant's authorization request and the cardholder's PM.
- The gateway sends the authorization request through a financial network to the cardholder's financial institution (issuer).
- The gateway creates the authorization response message and digitally signs it by generating a message digest of the authorization response and encrypting it with the gateway's private key.
- The gateway encrypts the authorization response with a new randomly generated symmetric key (No. 3). This key is then encrypted with the merchant's public key.
- The gateway creates the capture token and digitally signs it by generating a message digest of the capture token and encrypting it with the gateway's private key.
- The gateway encrypts the capture token with a new symmetric key (No. 4). This key and the cardholder account information are then encrypted with the gateway's public key.
- The gateway transmits the encrypted authorization response to the merchant.
- The merchant verifies the gateway certificate by traversing the trust chain to the root key.
- The merchant decrypts the symmetric key (No. 3) with the merchant's private key and then decrypts the authorization response using the symmetric key (No. 3).
- The merchant verifies the gateway's digital signature by decrypting it with the gateway's public key and comparing the result with a newly computed message digest of the authorization response.
- The merchant stores the encrypted capture token and envelope for later capture processing.
- The merchant then completes processing of the purchase request and the cardholder's order by shipping the goods or performing the services indicated in the order.
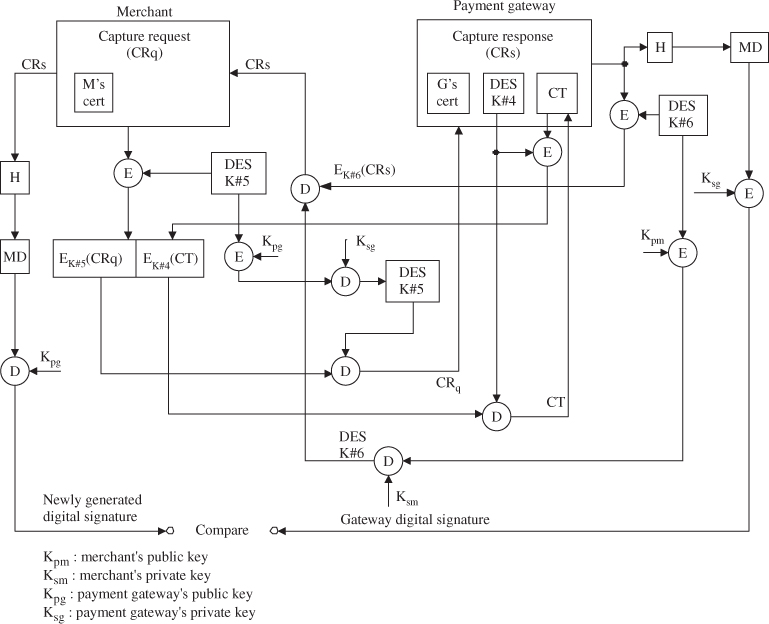
12.6.5 Payment Capture
After completing the processing of an order from a cardholder, the merchant will request payment. The merchant generates and signs a capture request, which includes the final amount of the transaction, the transaction identifier from the OM, and other information about the transaction. A merchant's payment capture process will be described in detail in the following.
- The merchant creates the capture request.
- The merchant embeds the merchant certificate in the capture request and digitally signs it by generating a message digest of the capture request and encrypting it with the merchant's private key.
- The merchant encrypts the capture request with a randomly generated symmetric key (No. 5). This key is then encrypted with the payment gateway's public key.
- The merchant transmits the encrypted capture request and encrypted capture token previously stored from the authorization response to the payment gateway.
- The gateway verifies the merchant certificate by traversing the trust chain to the root key.
- The gateway decrypts the symmetric key (No. 5) with the gateway's private key and then decrypts the capture request using the symmetric key (No. 5).
- The gateway verifies the merchant's digital signature by decrypting it with the merchant's public key and comparing the result with a newly computed message digest of the capture request.
- The gateway decrypts the symmetric key (No. 4) with the gateway's private key and then decrypts the capture token using the symmetric key (No. 4).
- The gateway ensures consistency between the merchant's capture request and the capture token.
- The gateway sends the capture request through a financial network to the cardholder's issuer (financial institution).
- The gateway creates the capture response message, including the gateway signature certificate, and digitally signs it by generating a message digest of the capture response and encrypting it with the gateway's private key.
- The gateway encrypts the capture response with a newly generated symmetric key (No. 6). This key is then encrypted with the merchant's public key.
- The gateway transmits the encrypted capture response to the merchant.
- The merchant verifies the gateway certificate by traversing the trust chain to the root key.
- The merchant decrypts the symmetric key (No. 6) with the merchant's private key and then decrypts the capture response using the symmetric key (No. 6).
- The merchant verifies the gateway's digital signature by decrypting it with the gateway's public key and comparing the result with a newly generated message digest of the capture response.
Figure 12.10 shows an overview of payment capture consisting of the merchant's capture request and the gateway's capture response.
Figure 12.10 Payment capture process.