Denial-of-Service (DoS) attacks, which aim to prevent access to network resources, can be devastating and difficult to protect against. Typical DoS attacks involve flooding the network with traffic choking the transmission lines and preventing other legitimate users from accessing services on the network.
DoS attacks can target many different layers of the network. In order to understand the risk of a DoS attack to a wireless network, you must first understand the difference between various types of DoS attacks.
An application-layer DoS is accomplished by sending large amounts of otherwise legitimate requests to a network-aware application, such as sending a large amount of page requests to a web server, swamping the server process. The goal of this type of attack is to prevent other users from accessing the service by forcing the server to fulfill an excessive number of transactions. The network itself may still be usable, but since the web server process cannot respond to the users, access to service is denied. (This can occasionally happen, innocently, when a web site receives a sudden boost in popularity due to a link from a high-traffic site, such as http://slashdot.org.)
A transport-layer DoS involves sending many connection requests to a host. This type of attack is typically targeted against the operating system of the victim’s computer. A typical attack in this category is a SYN flood. In a SYN flood (SYN packets are the first step of a TCP connection), an attacker sends an excessive number of TCP connection requests to a host hoping to overwhelm the operating system’s ability to track active TCP sessions. Most operating systems have a limit to the number of connections per second they will accept and a limit on the maximum number of connections they will maintain. A successful SYN flood will overwhelm the operating system on one of these two limits, thereby denying access to the services running on that host. As is the case in the application-based DoS, the network is usually still functional, but the target host is unresponsive.
A network-layer DoS is accomplished by sending a large amount of data to a network. This type of attack targets the network infrastructure of the victim. For example, an attacker may send 100 Mb/s of data to a network that can only transmit 10 Mb/s. The victim network obviously cannot retransmit all the data being sent to it, so the network equipment is forced to drop packets. This excessive traffic may also cause high loads on the CPUs within the network equipment itself, causing further network problems.
A typical network-based DoS attack is a ping flood. An attacker generates massive amounts of ICMP traffic destined for the victim network. (ICMP packets are used for management functions such as querying the availability and services of a host.) This usually saturates the victim’s WAN links. By cutting off the victim’s LAN from the rest of the Internet, the attacker has denied access to any services that reside on the victim’s LAN.
A data-link DoS can target either a host or a network. Data-link attacks are launched to disable the ability of hosts to access the local network even though the hosts are still connected. An example of this would be flooding a non-switched Ethernet network with invalid frames. An attacker (or sometimes a malfunctioning NIC) can send repeated frame headers with no payload. These headers are rebroadcast to all hosts on the network and effectively tie up the medium. Data-link DoS attacks are not common on wired networks because most networking gear has the intelligence to prevent data-link attacks from propagating to hosts on the network.
A physical-layer DoS involves severing a host’s connection to the network in some fashion. Physical attacks are not common in wired networks because they involve having direct access to the transmission medium involved in the victim’s network. For instance, WAN circuits are typically buried underground and are difficult to access. LANs reside inside of buildings, making them difficult targets as well. An example of an unintentional physical DoS attack is the dreaded backhoe DoS. Backhoe attacks are common in areas of heavy construction where a large piece of equipment (like a backhoe) is digging near buried data cables. One wrong move by the backhoe operator can sever thousands of telecommunications lines, potentially taking down many services.
At the application and transport layers, there is nothing fundamentally different between DoS attacks on wireless and wired networks. However, there are critical differences in the interaction between the network, data-link, and physical layers that increase the risk of a DoS attack on a wireless network.
A physical DoS attack against a wired network requires very close proximity to the victim host. This is not the case with a wireless network. The medium is everywhere and attackers can launch a physical attack from much farther distances. Instead of being inside of a building to perform a physical DoS attack against a LAN, an attacker can be outside of the building. Unlike a wired network where there is usually evidence of a physical attack (destroyed cabling, removed cable, attackers on video surveillance cameras), there are no visible signs that something has changed.
The 802.11 PHY specifications define a limited range of frequencies for communication. The 802.11 devices that use a specific PHY are constrained to these frequency ranges. An attacker can create a device that will saturate the 802.11 frequency bands with noise. If the attacker can create enough RF noise to reduce the signal-to-noise ratio to an unusable level, then the devices within range of the noise will be effectively taken offline. The devices will not be able to pick out the valid network signal from all of the random noise being generated and therefore will be unable to communicate.
Creating a device that produces a lot of noise at 2.4 GHz is relatively easy and inexpensive to construct. However, there are several common commercial devices available today that can easily take down a wireless network. Unfortunately, many 2.4 GHz cordless phones that can be purchased in electronics stores have the capability to take an 802.11b network offline. While not a refined electronic weapon, these phones can interfere or completely disable a WLAN. Cordless phones use several different modulation techniques and can overlap on the frequencies used by 802.11b. This overlapping is simply noise to an 802.11b radio. The cordless-phone-induced noise can drop the SNR enough to bring down any WLAN network nearby.
Tip
For Christmas one year, Bruce and his wife bought each other 2.4 GHz phones to replace their older 900 MHz models. After installing the phones, they noticed that they had many unexplained network outages. They also noticed an audible crackling noise on the phones. After reading the specs on the phone, they were able to set the phones to a different part of the ISM range than the frequencies they had chosen for their 802.11b network. This got rid of the interference and the outages. However, they learned the hard way that wireless technology is not necessarily plug-and-play.
There are also problems with a DoS from other networking protocols. In particular, Bluetooth uses the same ISM band as 802.11b and 802.11g. The DSSS modulation in 802.11b is susceptible to interference from the modulation used in Bluetooth networks. While there are potential solutions to prevent Bluetooth from stepping on 802.11b transmissions, large-scale Bluetooth deployments may still interfere to the point of inoperability with 802.11b networks. As time passes, the 2.4 GHz ISM band will become more crowded, making unintended DoS attacks against 802.11b networks commonplace. Sirius and XM satellite radio, who have spectrum bordering the ISM band, have complained that ISM-band devices may cause interference with their ground based repeaters and satellites.
At the data-link layer, ubiquitous access to the medium again creates new opportunities for DoS attacks. Even with WEP turned on, an attacker has access to the link layer information and can perform some DoS attacks. Without WEP, the attacker has full access to manipulate associations between stations and access points to terminate access to the network.
If an AP is incorrectly utilizing diversity antennas, an attacker can potentially deny access to clients associated to the AP. The use of diversity antennas is intended to compensate for multi-path fade. However, diversity antennas are sometimes used to cover more area with an AP by using antennas that cover disparate physical regions.
Tip
Antenna diversity is a mechanism where a single radio uses multiple antennas to overcome multi-path fade. A radio signal usually has many different paths to get to an antenna due to reflections of the signal off walls, trees, desks, etc. A radio using diversity antennas will sample a client transmission from all attached antennas and determine which antenna has the highest quality signal. The radio will then use that antenna to send and receive traffic destined for that station.
If the diversity antennas do not cover the same region of space, an attacker can deny service to associated stations by exploiting this improper setup, as shown in Figure 2-2. If diversity antennas A and B are attached to an AP, they are setup to cover both sides of the wall independently. Alice is on the left side of the wall, so the AP will choose antenna A for the sending and receiving frames. Bob is on the opposite side of the wall from Alice and will therefore send and receive frames with antenna B. Bob can take Alice off the network by changing his MAC address to be the same as Alice’s. Then Bob can guarantee that his signal is stronger on antenna B than Alice’s signal on antenna A by using a amplifier or other enhancement mechanism. Once Bob’s signal has been detected as the stronger signal on antenna B, the AP will send and receive frames for the MAC address on antenna B. As long as Bob continues to send traffic to the AP, Alice’s frames will be ignored.
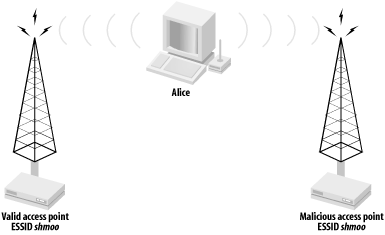
If a client is not using WEP authentication (or an attacker has knowledge of the WEP key), then the client is vulnerable to DoS attacks from spoofed APs. Clients can generally be configured to associate with any access point or to associate to an access point in a particular ESSID. If a client is configured to associate to any available AP, it will select the AP with the strongest signal regardless of the ESSID. If the client is configured to associate to a particular ESSID, it will select the AP in the ESSID with the strongest signal strength.
Either way, a malicious AP can effectively black-hole traffic from a
victim by spoofing the desired AP. For example, if a client is
configured to associate to APs in the SSID
shmoo, the client will look for all available
APs in that SSID. It will then associate with the AP for which it has
the strongest signal. A malicious AP with the SSID of
shmoo can make sure it has the strongest signal
by using a larger or directional antenna, signal amplifier, etc., as
shown in Figure 2-3. The client will associate to
the malicious AP, and the malicious AP can drop or monitor all
traffic sent to it by the client.
If a network allows any client to associate, it is vulnerable to a network-level DoS attack. Since an 802.11 network is a shared medium, a malicious user can flood the network with traffic, denying access to other devices associated to the affected access point. As an example, an attacker can associate to a victim 802.11b network and send an ICMP flood to the gateway. While the gateway may be able to withstand the amount of traffic, the shared bandwidth of the 802.11b infrastructure is easily saturated. Other clients associated to the same AP as the attacker will have a very difficult time sending packets.
Given the relatively slow speed of 802.11b networks, a network DoS may happen inadvertently due to large file transfers or bandwidth-intense applications. A few bandwidth-hungry applications on a WLAN can hamper access for all associated stations. With the deployment of higher-speed WLAN technologies, these unintentional attacks will become less frequent.