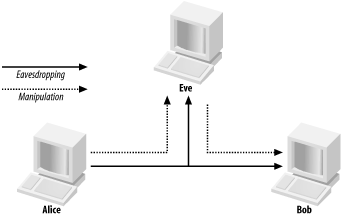
Man-in-the-middle (MITM) attacks have two major forms: eavesdropping and manipulation. Eavesdropping occurs when an attacker receives a data communication stream. This is not so much a direct attack as much as it is a leaking of information. An eavesdropper can record and analyze the data that he is listening to. A manipulation attack requires the attacker to not only have the ability to receive the victim’s data but then be able to retransmit the data after changing it, as shown in Figure 2-4.
MITM attacks on a wired network generally require access to a network that the victim’s traffic transits. This can mean physical access to a wire to “tap” into the wire for interception. It can also mean being on the same LAN as the victim and forcing traffic to go through the attacker’s host. An attacker can force traffic through a malicious machine on a LAN by performing an ARP poisoning attack.
In a wireless network, eavesdropping is easy because wireless communications are not easily confined to a physical area. A nearby attacker can receive the radio waves on the wireless network without any substantial effort or equipment. All frames sent across the wireless medium can be examined in real time or stored for later examination.
Several layers of encryption can and should be implemented to obscure transmitted data in an effort to prevent attackers from gleaning useful information from the network traffic. Since the ability of an attacker to eavesdrop on wireless communications is fait accompli, the data-link encryption mechanism WEP was developed. If the traffic is not protected at the data-link layer using WEP, then the higher layer security mechanisms must be used to protect the data. If a security mechanism such as IPsec, SSH, or SSL is not used for transmission then the application data is available to anyone with an antenna in the area without any further effort.
Unfortunately, several flaws in WEP have been uncovered as discussed in Section 1.6. Even with WEP turned on, a determined attacker can potentially log gigabytes worth of WEP-protected traffic in an effort to post-process the data and break the protection. These weaknesses in WEP drastically increase the risk due to eavesdropping. If WEP is cracked, there is great deal of sensitive data that is passed across networks with no further encryption, such as a user who accesses his mail using the POP or IMAP protocols. These protocols are widely deployed without any form of encryption for authentication or data transport, putting the users at risk when using a wireless network.
Manipulation takes eavesdropping a step further. An attacker who can successfully manipulate data on a network can effectively send data masquerading as a victim computer. Using ARP poisoning, an attacker can force traffic through a malicious machine. This malicious machine may, for example, change the content of emails, instant messages, or database transactions. The malicious machine can also choose not to forward packets along, effectively denying use of the network from the victim.