Until very recently, a firewall has been the frontline security device in most networks. Attacks have historically been launched against layer 3 or above. Firewalls have advanced over the years, evolving from glorified IP access lists to stateful, application aware security devices. With the wide-scale deployment of wireless networks, suddenly layer 1 and layer 2 security has become a hot topic. A wireless access point and wireless client must be able to defend themselves and their resources in an attempt to retain the integrity of the network.
This does not mean that firewalls have become less important in the bounds of a wireless network. Quite the contrary, a firewall, serving as a layer 3 gateway, is a critical piece of a wireless network. Not only must it defend against conventional attacks over the Internet, it must also protect itself and the networks it controls from unauthorized access originating from a hostile wireless network. A gateway is the first line of defense from an attacker who has complete physical and logical access.
The first thing to consider when deploying a gateway that will face a wireless network is how it will fit into your overall network architecture. It is tempting to simply plug an access point into an existing wired network and use your existing firewall to secure it. This is a recipe for trouble. By placing your access point in the same broadcast domain as your other critical services, you give an attacker a direct connection to any machine on the wired network. Figure 10-1 shows an insecure placement of a bridging access point. The attacker is behind your firewall. Unless your access point is acting as a transparent firewall between the wired and wireless segments, enforcing access control becomes a difficult proposition.
Even with host-based access control on all hosts on the wired network, an attacker can still launch an ARP spoofing attack against the network. For a complete discussion of ARP spoofing, see ARP Poisoning. An attacker, in an ARP spoofing attack, can serve as a man in the middle between two wired hosts. He can effectively pull packets off the wired network and force them to go across the wireless network.
To provide access control and minimize the risks of layer 2 attacks, the access point should be connected to its own interface on the gateway. Figure 10-2 shows the preferred architecture for a wireless network to be attached to a gateway. The figure also shows the corresponding IP address used in the examples in the chapters that follow.
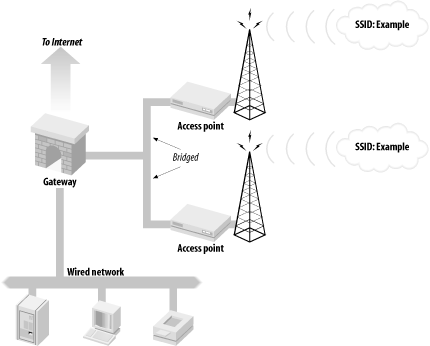
Some networks may require multiple access points to cover the desired area. Ideally, all of the access points will be in the same service set and be located on the same subnet so users have transparent roaming capability. To provide a single point of security policy enforcement yet still allow roaming, your gateway should act as a transparent bridging firewall between the multiple interfaces servicing the wireless interfaces. Figure 10-3 shows an example of a bridging firewall connected to multiple networks in the same service set. In general, there is no reason for hosts associated to different access points to talk to each other. There will be no service offered from the workstations attached to the wireless network, so traffic between workstations may be an attack. A bridging firewall gives you the capability to limit inter-station traffic.