Access points come in all shapes and sizes. Most access points deployed today are firmware devices running a proprietary operating system. These access points are usually inexpensive yet reliable. Unfortunately, securing these access points can be a challenge as they have very few security-specific options and are generally not very flexible.
Linux, FreeBSD, and OpenBSD machines can be converted to access points with the proper drivers and configuration options. Access points running on general-purpose operating systems provide much more flexibility to meet the challenges of specific security requirements. However, like any host, these machines must be properly secured and monitored to prevent attackers from compromising the host or the network.
This chapter will show you general techniques for locking down access
points for secure use. It will also show you how to setup Linux,
FreeBSD, and OpenBSD to run in HostAP mode,
turning the machine into a full-fledged access point.
Tip
Mac OS X also has a feature called Airport Software Base Station.
Enabling this provides a peer-to-peer 802.11b network, not a BSS
network like a regular AP or HostAP as discussed
in this chapter.
Several security features are common across most access point vendors. The manner in which these features are configured vary from vendor to vendor. Please consult the documentation that came with your access point to determine the correct method. None of the features mentioned offer are bulletproof security, but they raise the bar substantially for an attacker.
Even though the crypto underlying WEP has been
broken, it is still important to configure WEP for several reasons.
Primarily, it serves as a reasonably strong barrier against the
casual attacker. Raw 802.11 frames can be captured via
tcpdump on almost any platform. Without WEP, it
is trivial to sniff traffic, determine layer 3 gateways, and gain
access to the network. By enabling WEP, you are forcing the attacker
to crack your WEP key to accomplish the same tasks. The tools used to
crack WEP are substantially more difficult to use than
tcpdump, as well as take a fair bit of time to
run. A person will likely not sit in a car in your parking lot for
the many hours it will take to capture enough traffic to crack your
WEP encryption.
Secondly, there may be legal reasons why running WEP is a good idea. For the record, the authors are not lawyers, however, based on our years of work in the security field we have read about enough legal battles to know a good legal practice when we see it. Typically a systems operator must place a “No Trespassing” sign of some nature on a resource to prevent a hacker from “accidentally” breaking into a system. With telnet, this can be accomplished with a login banner to the effect of “Authorized Users only. Unauthorized access will be logged and prosecuted.” This is a clearly worded warning to would-be attackers that the system is private. In a court of law, this type of statement will remove an attacker’s defense of ignorance. WEP is the wireless analog to a telnet login banner. By enabling WEP on your network, you are putting up a sign to attackers that your system is off limits and you have a reasonable expectation of privacy. If an attacker goes through the trouble of cracking your WEP key, then they are obviously aware they are breaking into a system that they have no right being in. In the event that you catch the attacker, your use of WEP may help in your prosecution.
When configuring WEP, always use 128-bit keys if possible. As time passes and WEP is refined, the key size will likely continue to increase. As a rule, use the largest key size your hardware can bear without performance impact.
Also, many WEP implementations allow for entry of four different WEP keys at one time. This allows you as an administrator to create a WEP key rotation policy. The frequency of key rotation is a function of the amount of data transmitted on the network, the number of users on the network, and the paranoia of the administrator.
Only one key can be used to transmit at any given time. However by
entering four keys in, you can implement a key rotation schedule. For
example, give your users four new keys at the first of the month.
Tell the users to transmit with key[0] for the
first week, then key[1] for the second,
key[2] for the third, then
key[3] for the fourth. The clients and AP can
understand packets encrypted with any of the four keys so the users
do not need to change their transmit keys at exactly the same time.
If you want to force them to change, you can change the key at
location X on the AP. At that point, the users who are still
encrypting with key[X] are unable to talk on the
network anymore. Generally, they will notice this problem and contact
someone to get the new keys.
Most access points also have MAC address filtering capabilities. This feature can be configured in an open or closed manner. In an open MAC filter, the MAC addresses listed are prevented from accessing the network. In a closed MAC filter, only the listed addresses are allowed to access the network. A closed filter is the more secure option as only known cards are permitted. Keeping track of MAC addresses can be difficult in a network of any size. If you are planning to install a large network, you may be able to request cards from your wireless vendor with sequential MAC addresses to make filtering easier.
Warning
Many wireless cards on the market allow the MAC address to be changed
by the user. This is usually a trivial change accessed via the driver
GUI in Windows or ifconfig in Linux/FreeBSD. An
attacker who is snooping your network for traffic could easily change
his card’s MAC address to match a host that he knows
is currently allowed through the filter. Again, like WEP, MAC
filtering has failings, but it continues to raise the bar.
Most access points offer several means of administration. Common administration access methods are through telnet, HTTP, or a serial/USB connection. Telnet administration should be avoided, and disabled if possible, since passwords will transit the network in the clear. If supported by the access point, limit administration traffic to the wired side of the network. For smaller networks, or when remote administration of access points is not needed, disable the online administration entirely and use the serial connection. Many access points have had security problems with their administration servers, so they should be disabled if you are not going to need to access them.
Your access point may be able
to log critical events to a central log host via
syslog. Configure your access point to log to a
central server (possibly your firewall) and examine what is logged.
You may see events such as system restarts, failed authentication
attempts, and new associations. Using swatch (as
discussed in Chapter 4), you can monitor and alert
on events you deem important. Examining associations can be
especially useful and interesting. Individual users that are
war-driving your access point will leave their first audit trail as
they associate. Depending on your gateway auditing (discussed in
Chapter 10), you will see even more footprints as
they work their way out of your network.
Some
access points will allow an SNMP trap host to be configured in place
of a log host. A trap is an SNMP message caused
by a critical event on the device. A trap will typically contain the
same type of information has a log entry for an event logged via
syslog. You may need to configure a password on
your trap host and access point in order for the trap to be accepted
by the trap host.
This
option is called something different by almost every vendor.
Basically it refers to the ability to require WEP authentication to
access the network. An open
network is a network that does not require any
authentication at all. A station makes an association request and
that request is granted. A closed
network requires a WEP authenticated
association. Without WEP, the requesting station is denied access. A
mixed environment will allow unauthenticated or
authenticated access to the network. A closed network is obviously
the best choice for ensuring authentication of clients. However, you
may need to run in mixed mode when troubleshooting station
connectivity
issues.
SNMP is a very powerful protocol for managing network-connected devices. Every firmware-based access point I have used, from the lowest priced consumer grade AP to expensive ISP quality kits, had some manner of SNMP interface. Most access points are configured either via an SNMP interface or a web interface. Even the access points with a web interface have had an SNMP system for remote monitoring.
SNMP employs the concept of
managers and agents.
Managers are centralized hosts that make SNMP
requests to devices that run agents. The agents
then process the request and send response data back to the manager.
Agents can also send traps. An example of a SNMP manager and agents
is shown in Figure 9-1.
SNMP Version 1 is the most commonly deployed version of SNMP. SNMP V1 allows for two types of access: read-only (RO) or read-write (RW). Community strings control the different types of access. Community strings are really nothing more than passwords to access the SNMP functionality of your device. Treat them as passwords and do not give them out to others. Also, be sure to change your default SNMP community string that ships with your access point. There are many web sites on the Internet that list the defaults settings for all known access points including community strings and IP addresses. By leaving your access point with the default community string, you are practically inviting a war driver to change your AP’s settings.
Warning
SNMP V1 is a cleartext protocol. There is no inherent encryption to protect the traffic. Do not manage your wireless access point from the wireless interface. By managing the AP through the wired interface, you greatly reduce the chances of someone intercepting your community string.
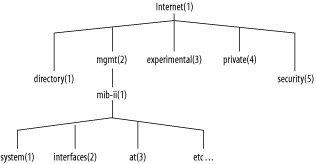
The type of information that a manager can get and set on a remote device is stored in the Management Information Base (MIB). A MIB is a hierarchy of object descriptions, which is shown in Figure 9-2, that can be understood by an SNMP manager. Each object has a unique Object Identifier (OID), which can be expressed numerically via the object’s descriptor or in alphanumeric strings via the object’s name.
For instance, there is an OID that represents the uptime of the system. This object can be represented by name or description:
- Name
.iso.org.dod.internet.mgmt.mib-2.system.sysUpTime.0
- Description
.1.3.6.1.2.1.1.3.0
Most of the existing SNMP managers assume they are dealing only with
OIDs in the MIB-II tree. Therefore,
.iso.org.dod.internet.mgmt.mib-2.system.sysUpTime.0
can also be referenced as simply
system.sysUpTime.0.
Vendors may have device-specific MIBs that can be loaded up into your SNMP manager. These MIBs typically define data that provides a customized view into proprietary parts of your device. These MIBs are generally available on your vendor’s web site.
The 802.11 suite of protocols have their own MIB available from the IEEE. The MIB has subtrees to allow monitoring of the MAC and PHY layers as well as station-specific parameters. This MIB can be downloaded from the IEEE web site at http://standards.ieee.org/getieee802/802.11.html.
There are several different tools you can use for SNMP monitoring, depending on your requirements for scripting, ease of use, or expandability. At the very least you should experiment with each access point you purchase to see what information is available from your device.
net-snmp
is
a SNMP implementation that has been under development for many years.
The project was formally known as ucd-snmp.
net-snmp contains various utilities including an
extensible SNMP agent, SNMP libraries, a suite of tools to get and
set data on managed devices, trap tools, and a MIB browser.
net-snmp is available from http://net-snmp.sourceforge.net/. Follow the
directions in the current distribution for compiling and installing.
A complete discussion of net-snmp is outside the
scope of this book. However, there are a few tools that are very
useful when performing audits of access points. You can retrieve a
specific OID using the snmpget command. To
retrieve the uptime of a system at 192.168.0.2
with a community string of public, issue the following command:
bash$ snmpget 192.168.0.2 public system.sysUpTime.0 system.sysUpTime.0 = Timeticks: (196741426) 22 days, 18:30:14.26
This is
great if you know the OID of the data you want. However, you may want
to see all of the data the device is capable of returning. The
snmpwalk command will walk an entire section of
a MIB tree. For instance, to walk the IP MIB subtree on the same
host, use the following:
bash$ snmpwalk 192.168.0.2 public ip ip.ipForwarding.0 = not-forwarding(2) ip.ipDefaultTTL.0 = 255 ip.ipInReceives.0 = Counter32: 113896 ip.ipInHdrErrors.0 = Counter32: 0 ip.ipInAddrErrors.0 = Counter32: 0 ip.ipForwDatagrams.0 = Counter32: 0 ...
Walking a MIB tree can generate a lot of data, so you may want to
redirect output to a file to examine. A vendor may expose a lot of
information via a device’s SNMP interface. Look for
information such as association tables, DHCP lease information, and
error rates. You should be able to generate Perl or shell scripts
using snmpget to monitor values you deem
important.
Warning
The SNMP agent that runs on some access points may be buggy. We encountered quite a few access points that crashed when we walked the entire MIB tree. Not only is this annoying, but it can also be a denial-of-service attack vector for a malicious user. If your SNMP agent causes your AP to crash during a walk, contact your vendor’s technical support. They are generally helpful in getting a fixed firmware version released.
Scotty
is a set of TCL extensions for network
monitoring. Scotty allows for rapid network
monitoring application development via a very robust suite of tools
and APIs. tkined is a graphical framework for
creating network maps and graphical monitoring tools.
tkined is very extensible yet powerful out of
the box. Scotty/tkined can be downloaded from
http://wwwhome.cs.utwente.nl/~schoenw/scotty/.
Follow the build and installation instructions that come with the
current distribution.
tkined is a great tool for networking monitoring
for a small network because it requires very little expertise to get
up and running. However, because it is so extensible it can scale to
handle very large networks. tkined can be
configured to alarm on high and low thresholds, such as when an error
rate on a wireless network becomes excessive. It can also graph
time-dependant variables such as network utilization of free
processor time. Figure 9-3 shows an access point
with wireless network traffic being monitored and the SNMP
configuration screen open.