45
3
The Information
Security Program
and How a Security
Assessment Fits In
An information security program is the umbrella heading for all security measures
a company has in place. An information security program can contain many elements
including physical security, system security, and internal controls that can touch
virtually every part of an organization. Information security programs can vary
significantly by organization. Some companies might have an extensive and formal-
ized information security program based on a well-thought-out information security
strategy, but another organization’s idea of information security might be some
physical security and password management. It varies greatly, and you will likely
run into different scenarios as you conduct security assessments. This chapter will
discuss the key elements of information security programs and how security assess-
ments fit into the overall security picture. Understanding what an information secu-
rity program is will develop a good foundation for discussing security assessment
methodology, as much of what you will evaluate during an assessment will be the
information security program. The recommendations you make at the end of the
security assessment will be to enhance the overall information security program.
Therefore, it is important to understand the key elements of an information security
program before discussing the methodology.
WHAT IS AN INFORMATION SECURITY PROGRAM?
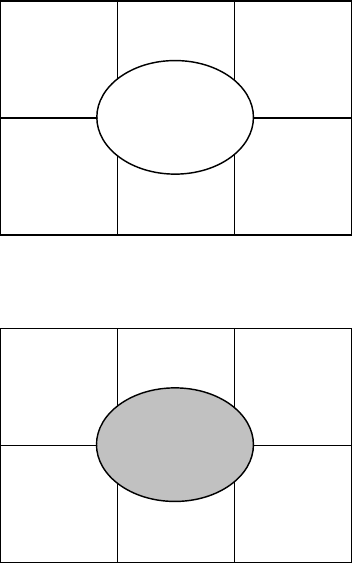
An information security program has seven key elements, as illustrated in Figure
3.1. The security strategy is the focal point; it drives the rest of the program. Each
of the areas is critical to the success of the information security program and will
be discussed in greater detail in subsequent sections. After discussing these key
elements, we will discuss how the security assessment process fits in with the concept
of the information security program.
S
ECURITY
S
TRATEGY
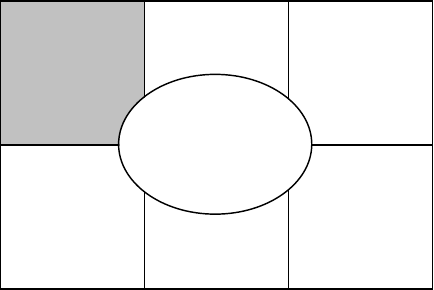
At a high level, the security strategy is what drives the rest of the information security
program. It consists of understanding the security risks a company is facing and
developing the most cost-effective way to protect the company’s information assets.
AU1706_book.fm Page 45 Wednesday, July 28, 2004 11:06 AM
46
A Practical Guide to Security Assessments
Cost-effective implies evaluating the risks and impacts and then determining the
best way to address those risks.
In Figure 3.2, the security strategy is in the center because it represents the basis
for everything that is done from a security perspective. The security strategy should
be well thought out by key stakeholders in an organization and driven by the needs of
the business — i.e., the business requirements of an organization should be the basis
of the security strategy. Security measures should be aligned with an organization’s
risks to help ensure that information security resources are allocated appropriately.
Some examples of things to consider when developing a security strategy
include:
• Identifying critical data and determining the impact to the business if it
is compromised (e.g., data is destroyed, unauthorized individuals gain
access to data)
• Identifying critical applications and determining the impact if the appli-
cation was not available
• Ensuring that any regulations with information security requirements are
properly addressed
FIGURE 3.1
Information security program.
FIGURE 3.2
Security strategy.
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 46 Wednesday, July 28, 2004 11:06 AM
The Information Security Program and How a Security Assessment Fits In
47
These and a host of other areas should be discussed when developing the security
strategy of an organization. The key aspect of the security strategy is alignment,
which is essentially determining the security risks facing a company and developing
cost-effective security solutions to address them. The aim of the information is not
to mitigate 100 percent of the security risk; rather, it is to reduce the risk to an
acceptable level where the company is effectively managing the risk.
As with the other areas of the business, funds are limited, and part of the challenge
in developing a security strategy is to determine the best use of the available funds.
In these tough economic times, spending is scrutinized, so risks and potential impacts
to the business must be clearly articulated when determining what security measures
a company is going to take. Risks should be quantified if possible, and financial
measurements such as ROI (Return on Investment) for potential security measures
should be calculated.
As you consider these points when developing a security strategy, remember
that there is some element of risk that the organization will have to accept. The
challenge is to achieve the right balance between security and an acceptable level
of risk
.
S
ECURITY
P
OLICIES
AND
P
ROCEDURES
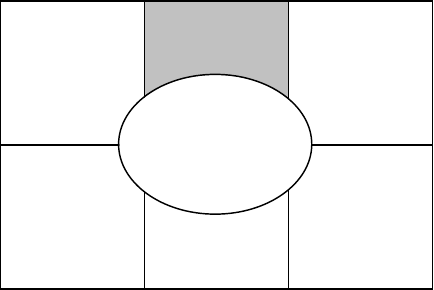
Once the security strategy is developed, the first step in implementing it is to develop
security policies (Figure 3.3). Policies are high-level requirements that are designed
to meet the goals of the information security strategy. They are management’s
representation of what security measures need to be in place for effective information
security.
Although the security strategy was a very high-level set of requirements that set
the direction for the information security program, security policies are the first step
in implementing the security strategy. As a result, developing good security policies
requires a more detailed understanding of business processes, critical technologies, and
FIGURE 3.3
Security policies and procedures.
Security
Policies &
Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 47 Wednesday, July 28, 2004 11:06 AM
48
A Practical Guide to Security Assessments
critical data. Good security policies are tailored to address the specific security risks
facing the company. These risks are the starting point for developing the security
policies.
Security policies should be developed with input from both business process
owners and technology owners. The input from the business side is critical because
the business will play a significant role in driving what is done from an information
security perspective. Depending on how a company is organized, this input is
important also because it is the business units that may be ultimately responsible
for funding the implementation of security policies and other security initiatives.
Security policies are generally developed with input from both business and tech-
nology owners to ensure that the policies are both feasible and reasonable with
respect to addressing the specific security risks the company is facing.
Some standard security policies that almost every company has include Backup
and Recovery, Data Retention, Acceptable Use, etc. There are also some policy areas
such as Business-to-Business and Business-to-Consumer that many companies do
not have. The policies you end up developing will depend on the business process
and technology analysis of the company.
Once security policies are developed, they must be implemented by developing
procedures. This is an important concept and it brings us to the distinction between
policies and procedures. Where policies tell “what” needs to be done, procedures
tell “how” to do it. To clearly understand what policies and procedures are, it is
valuable to highlight some of the key differences:
• In the same way that policies were the next step after the development
of the security strategy, procedures are the next step after development of
policies.
• Policies tend to be global in nature, but procedures may be at a more
granular level in the organization (e.g., at the department or business unit
level).
Security policies by themselves do not tell users how to implement that policy.
For example, a monitoring policy might say, “system logs should be reviewed
periodically.” Based on this policy, users do not necessarily know “how” to review
logs or what “periodic” review means. In this case, there may be a procedure that
goes through the step-by-step process of how to review the logs, what to look for,
and how frequent the review should be. Notice that the policy can leave a fair amount
of latitude for interpretation. This is necessary because different groups within a
company may implement policies differently based on their specific requirements.
For example, one group might review system logs on a daily basis, but another group
might review them on a weekly basis. Both frequencies, daily and weekly, are
interpretations of “periodic.”
Policies will tend to remain relatively static, although procedures will vary based
on technology, organization, resources, and other requirements. For example, pro-
cedures related to ID administration will vary depending on what technology is used
(e.g., Microsoft, Novell), but the ID administration policy requirements should not
AU1706_book.fm Page 48 Wednesday, July 28, 2004 11:06 AM
The Information Security Program and How a Security Assessment Fits In
49
really change. The policy might say that users must change passwords on a regular
basis. The “procedure” for making users change passwords periodically will differ
for each system.
Policies only tend to change when there are fundamental changes to the business
or some external driver exists, such as new legislation that might mandate certain
things. For example, companies that have just begun to engage in commerce over
the Internet will have to make additions to their security policy to reflect the risks
of doing business in this way. Procedures, on the other hand, are much more dynamic
in nature and can change more often. Changes in the organizational structure,
technologies used, and business processes can potentially result in modifications to
procedures.
One of the key benefits of both policies and procedures is that they clearly define
roles and responsibilities and thus bring some accountability to security processes.
Without documented policies and procedures, it is difficult to hold someone account-
able for a process.
The other key aspect to remember with security policies and procedures is that
someone (or a group of people) must own the responsibility of maintaining them.
The value of these documents diminishes significantly once they become out of date.
S
ECURITY
O
RGANIZATION
The security organization (Figure 3.4) is the group that ensures that the information
security program is followed and maintained. The “security organization” does not
necessarily mean that a separate group ensures that security requirements are carried
out; rather it means that there are people who are assigned in different capacities to
ensure that the information security program is followed and maintained.
Typical people in a security organization could include a Chief Security Officer
(CSO), security analysts, and system administrators with some security-related
responsibilities. Some of the key responsibilities of the security organization include
the following:
FIGURE 3.4
Security organization.
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 49 Wednesday, July 28, 2004 11:06 AM
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
