1
1
Introduction
Over the past few years, information security has evolved from a technology issue
to a boardroom issue. Companies are affected every day by security-related incidents
such as network intrusions, viruses, or denial-of-service attacks. Some of these
incidents are reported but many probably are not. Business is becoming increasingly
dependent on technology and the Internet to the point where some businesses would
come to a screeching halt if they did not have it. This is particularly true in larger
companies, where the ability to communicate and access information is the lifeblood
of the business.
For example, if you ask a manager in a multinational Fortune 500 company how
long the company could remain productive without having e-mail service or being
able to access critical data, you will likely be told that it is not very long. If you ask
that same manager what the impact would be if unauthorized persons gained access
to the company’s critical data or electronic mail, you will get an answer ranging
from “not good” to “significant embarrassment to the company or legal troubles.”
What would happen if critical data was changed without anyone’s knowledge? If
this happened, the company might be working with erroneous data that could affect
operations. Even this fairly simplistic example illustrates why it is critical to secure
information to ensure its confidentiality, integrity, and availability.
The need to secure information is becoming greater all the time as we leverage
technology to automate functions, as more data becomes electronic, and as compa-
nies become increasingly reliant on the Internet as an integral part of their informa-
tion technology (IT) infrastructure. Businesses are becoming increasingly connected
because business-to-business relationships are helping companies drive efficiencies
and shorten the supply chain. E-commerce is gaining acceptance as more people
buy goods and services online, resulting in an increasing number of companies
having a presence on the Web. With these relationships, a host of security issues
must be addressed.
Today, solutions that address specific security risks are available. For example,
companies have a firewall or a network-based intrusion detection system in place
to address perimeter security. The architecture of the intrusion detection system may
have been designed to protect a certain network segment and some critical machines.
For many companies, intrusion detection and firewalls are solutions that have been
implemented without thinking about them from a business perspective. Take the case
of a company where intrusion detection is in place, but no one is looking at alerts or
updating the system to reflect the latest attack signatures, and the company did not
involve people from the business to identify what data warranted protection, so no
assurance exists that the intrusion detection system is even protecting critical data.
In this case, the intrusion detection system is doing very little to secure critical assets
or the perimeter of the network. If the business issues were examined, the same
AU1706_book.fm Page 1 Wednesday, July 28, 2004 11:06 AM
2
A Practical Guide to Security Assessments
company might have designed the solution differently and considered an outsourcing
option or having additional resources. This example is an illustration of security
solutions being implemented without considering the business — i.e., security is not
always considered a business issue
.
For many companies, information security is an
IT issue and something to which people on the operations side of the house do not
really pay attention. This is the case even though operations personnel “own” critical
data and are the ones who are dependent on IT systems. Our dependence on the
security and availability of information and systems necessitates a more holistic
view of information security — one in which personnel from both operations and IT
are actively engaged to find the best use of resources to secure critical data and ensure
that mission-critical business processes are secure. We must look at risks and develop
cost-effective security solutions that are commensurate with risk. As the information
security discipline evolves, it must be considered in light of the business and the
associated risks. As we implement security solutions, we need to take a step back
and ask questions such as:
• Does the security solution address what are we trying to protect?
• What is the value to the business of what we are protecting?
• Does the security solution mitigate identified security risks?
With budgets as tight as they are today, security spending must deliver good
ROI (Return on Investment) and adequately protect the information assets of the
company. Spending on security, like spending on other areas of the business, must
be justified.
To look at information security in terms of delivering good ROI and protecting
against identified risks, a risk-based approach to information security is required,
which is a slight change for many companies. The first steps in taking such an
approach are to understand what the risks are and developing solutions to address
those risks — i.e., conducting a security assessment. The purpose of this book is to
present a methodology for conducting a security assessment. The central aspect of
the methodology is the importance of understanding the business and using that as
the basis for determining the security risks. The methodology is vendor and tech-
nology neutral. It is process focused and can be used in any environment.
Security assessment methodology is a topic that deserves attention because it is
arguably the most important element of a successful information security program.
Without a quality security assessment, no assurance exists that the true security risks
a company is facing have been identified. As a result, any information security
program that is implemented will provide little assurance that the company is secure.
In addition, any money invested in an information security program without having
a good understanding of the business and the security risks it is facing is a potential
misuse of resources.
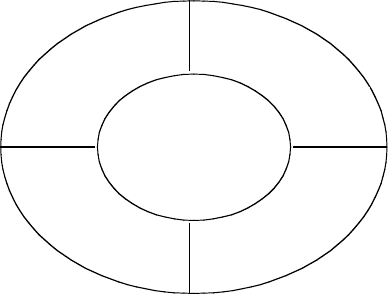
Figure 1.1 illustrates the relationship between the security assessment process
and the overall information security program. As shown, the security assessment process
drives the rest of the information security program. The security assessment is
basically an analysis of the organization’s security risks. The results of the assess-
ment drive the other components of the information security program — i.e., policies,
AU1706_book.fm Page 2 Wednesday, July 28, 2004 11:06 AM
Introduction
3
procedures, technology, and audit. Because these components are all based on the
security assessment, it is critical that the results of the security assessment accurately
represent the security risks that an organization is facing. The methodology presented
in this book will provide information security practitioners a structured methodology
for conducting a security assessment as well as some questionnaires (in the appen-
dices) to help facilitate the security assessment process.
This book goes through each step of the methodology and is divided into two
sections, including the methodology and the questionnaires, to help facilitate security
assessments. Below is a brief chapter-by-chapter summary:
Chapter 1.
Introduction
Chapter 2. Evolution of Information Security —
This chapter provides some
background on information security and historical perspective before dis-
cussing security assessment methodology. The chapter discusses some
trends and events that have made information security a significant issue.
Chapter 3. The Information Security Program and How a Security Assessment
Fits In —
This chapter focuses on the critical elements of an information
security program and the role of a security assessment in that program.
Chapter 4. Planning a Security Assessment —
This chapter discusses Phase 1
of the methodology, which comprises all aspects of the planning phase
including developing the scope of an assessment, obtaining support from
stakeholders, and setting expectations of the client whose environment will
be subject to the assessment.
Chapter 5. Initial Information Gathering —
This chapter discusses Phase 2
of the methodology, which includes different ways to research an organi-
zation before the fieldwork phase of an assessment occurs. This chapter
references some free and publicly available sources of information that can
be used to gain familiarity with the company. In this phase, you will also
discuss the preparation of question sets to be used when you meet the client,
which occurs during the next phase.
FIGURE 1.1
Components of an information security program.
POLICIES
PROCEDURES
TE
C
H
NO
L
OG
Y
AUDIT
SECURITY
ASSESSMENT
AU1706_book.fm Page 3 Wednesday, July 28, 2004 11:06 AM
4
A Practical Guide to Security Assessments
Chapter 6. Business Process Evaluation —
This chapter discusses Phase 3
of the methodology, which is gaining an understanding of the business and
evaluating the core business processes. This chapter discusses the process
of interviewing business process owners and what questions you should be
asking personnel to gain information that would be useful in a security
assessment. It also discusses the use of questionnaires and other techniques
to gain information from business process owners. The main objectives of
this phase are to gain an understanding of the business and the core business
processes, identify process-related risks, and identify the critical technolo-
gies that support core business processes, which will be reviewed in detail
in the next phase.
Chapter 7. Technology Environment —
This chapter discusses Phase 4 of the
methodology, which is the technology evaluation. Based on the material
covered in Chapter 6, you should now have a good feel for what technology
is critical to the business. This chapter walks the reader through the process
of assessing the technology that is critical to the business along with some
of the associated techniques. Similar to the last chapter, this chapter dis-
cusses the use of questionnaires and other techniques to gain information
from technology owners.
Chapter 8. Risk Assessment and Final Presentation —
This chapter discusses
the final phase of the methodology, which is to perform the formal risk
analysis, develop recommendations, and present the final report. The chap-
ter discusses a process for performing the risk analysis by calculating a risk
score. This calculation takes into account a number of factors related to
risk, including potential impact to the business, the probability of a security
breach, and the existing controls to mitigate the risks. This chapter also
discusses the importance of the final report, as it is the only tangible work
product resulting from the assessment.
Chapter 9. Information Security Standards
— At this point, the discussion
of the methodology is complete. This chapter discusses some key standards
that are relevant for information security. Some of the standards discussed
include International Standards Organization (ISO) 17799 and COBIT.
Chapter 10. Information Security Legislation —
This chapter contains short
descriptions of key recent legislation that has a bearing on information
security. It is important to be well informed about these laws, as they might
affect the company where you are conducting a security assessment.
Appendices. Security Questionnaires —
The Appendices contain question-
naires to help information security practitioners in conducting security
assessments. Questionnaires for key areas of information security are
included, as well as generic questionnaires designed to help you gather
information in the early stages of a security assessment. These question-
naires are structured to provide “guidance” so that practitioners understand
the relevance of a given question. They can be modified to meet the needs
of the specific company where a security assessment is being performed.
AU1706_book.fm Page 4 Wednesday, July 28, 2004 11:06 AM
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
