50
A Practical Guide to Security Assessments
• Updating security policies as required
•Working with business process owners to ensure that security-related
procedures are kept up to date
•Evaluating new initiatives and determining whether they have any security
implications
•Working with application developers to ensure that security is being built
into applications
•Working in an “enforcement” type of role to help ensure compliance with
the information security program
• Monitoring new security vulnerabilities and determining steps to protect
the company from them
For a security organization to be successful, it is important to have someone
who is high enough in management so that potential issues can be properly escalated
and so that the security organization has some clout. The CSO position, which many
companies now have, sometimes has the required level of influence. It depends on
whom the CSO reports to in upper management and where the CSO sits in the
overall organizational structure. There is a huge difference between having a CSO
who reports to a Chief Financial Officer and a CSO who reports to an Information
Technology (IT) Manager. Where management level positions of security fit in the
overall management chain has a bearing on how influential the security organization
is. This factor is related to executive support, which is discussed in the next section.
Another factor that influences the success of the security organization is the
culture of the company. Some companies are very security conscious; all employees
understand the importance of information security, and the level of compliance with
security policies is high. In these companies, upper management tends to be very
security conscious and there tends to be a strong security organization. In other cases
where security is not necessarily a priority, you might find the lack of a security
organization or one that has little authority or influence. In these companies, the
security organization must continually show why security is important to the business.
E
XECUTIVE
S
UPPORT
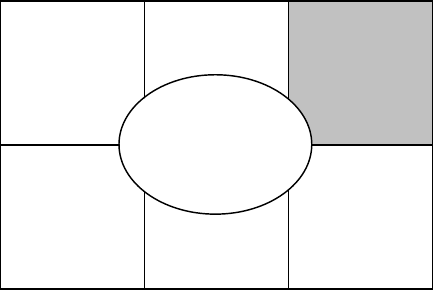
Executive support (Figure 3.5) refers to upper management and their general attitude
towards information security. When upper management is supportive of security and
related initiatives, the security environment tends to be strong because that same
attitude trickles down to all employees. Without executive support, any effort,
whether information security or any other initiative, is very difficult. With executive
support, activities are driven from the top versus from lower levels. From a security
perspective, it is very difficult if not impossible to drive information security initi-
atives from lower levels in the organization. Remember that security does not make
the typical employee’s life easier. In fact, security initiatives tend to create more
work for people. Some employees may even feel that security processes that create
more work are more of a nuisance than anything else. Without executive support, it
is difficult to convince someone that security processes are important. After all, how
AU1706_book.fm Page 50 Wednesday, July 28, 2004 11:06 AM
The Information Security Program and How a Security Assessment Fits In
51
do you answer someone who tells you, “My manager doesn’t have to do this, why
do I?”
If employees of a company see that executives do not care about security, they
probably will not care about it either. Even if there are policies and procedures,
they are not followed because there is no management support for them. If employees
do not “have” to do something, they will not — i.e., if they do not have to perform
a process in a secure way, they will not. Strong executive support can change this
attitude. Executive support for information security helps to instill a culture where
information security is considered important and people know they have to do their
part or else face some negative consequence. Without this support, there is a risk of
noncompliance and difficulty in enforcing existing security policies because employ-
ees will not take information security seriously.
Executive support can be demonstrated by participation in training and awareness
programs, where a company executive speaks to employees about the importance
of information security. Executives can also support information security efforts by
serving as a point of escalation in cases of noncompliance with security policies.
Managers and other employees will be much more apt to follow security policies if
they know that noncompliance might result in a reprimand from an executive of the
company. Escalation ties back into the CSO concept and where security management
sits in an organization. There is a better chance of security being taken seriously if
the management responsible for it has access to people at the executive level. This
type of access allows security issues to be escalated to levels where significant
decisions can be made.
T
RAINING
AND
A
WARENESS
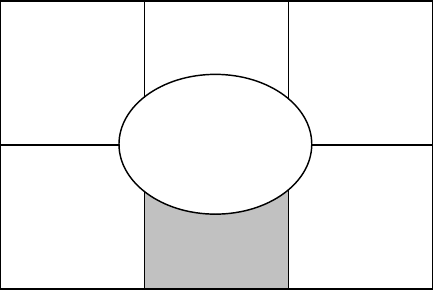
Regardless of what security policies and procedures are documented, employees
will not necessarily be compliant with them unless they are aware of them and are
provided training as necessary (Figure 3.6). Besides providing the initial communi-
cation of the information security program, training and awareness on a regular basis
FIGURE 3.5
Executive support.
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 51 Wednesday, July 28, 2004 11:06 AM

52
A Practical Guide to Security Assessments
help to ensure that people are constantly being reminded of their responsibilities
from an information security perspective. Remembering that information security is
“everyone’s” responsibility, it is critical to provide training and awareness so that
average employees understand what they need to do and so that they have an
opportunity to ask any questions if they do not understand. The chances of success
of the information security program can be significantly enhanced by a good training
and awareness campaign.
Training and awareness can be very challenging based on the number of people
in the organization and the organization’s complexity. Keep in mind that all employ-
ees do not need all of the training and awareness. Employees should be given training
on the various aspects of the information security program that impact them. There
will be some cases where training might be appropriate for everyone (e.g., impor-
tance of having strong passwords, acceptable use) and other cases where it might
be appropriate only for a select group of individuals (e.g., training related to backups
and offsite storage might only be relevant for IT personnel and a few business unit
personnel who are data owners). A targeted program is an effective way to provide
training and awareness in a cost-effective manner.
Some training and awareness delivery methods to consider include instructor-
led training, manuals, online training, and documented processes. For instructor-led
training, it is critical that qualified people deliver the training. A bad instructor can
ruin a course and turn people off, but a good instructor can make people understand
and motivate them. There are also some “regular” opportunities to give training and
awareness — e.g., acceptable use policies related to Internet, e-mail, etc. could be
discussed with employees when they first start as part of their orientation and then
on an annual basis as a reminder. Another method to promote awareness is to provide
employees easy access to security-related information such as policies and proce-
dures. An easy way to provide this type of access is to leverage the company intranet.
If the content is kept current, employees will refer to it if they have any questions
regarding security, which will lead to greater levels of compliance.
FIGURE 3.6
Training and awareness.
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 52 Wednesday, July 28, 2004 11:06 AM
The Information Security Program and How a Security Assessment Fits In
53
T
OOLSETS
IT environments are very complex, and security vulnerabilities are numerous. Sys-
tems must be checked on a regular basis to ensure that they are in compliance with
best practice standards — e.g., servers should be checked to ensure that they have
certain security settings in place and the appropriate patches. For most companies,
checking manually to the level of detail required is just not feasible. It is virtually
impossible to maintain a secure environment without having the proper toolsets
(Figure 3.7) to automate some of these enforcement functions. Toolsets are empha-
sized as a separate element of an information security program because in today’s
environment, it is very difficult to enforce technical security manually. Some of the
functions must be automated.
One of the areas where tools are critical is ensuring that servers and other systems
are properly hardened. Although manual procedures can be used in some cases to
check compliance, it is far more efficient to use tools to automate some tasks. This
technical compliance effort, which the proper toolsets facilitate, is a critical part of
the overall information security program. Some of the key compliance areas where
tools are important include:
•Vulnerability assessment tools for the IT infrastructure
•Tools to check patch levels
•Tools that check password strength
•Vendor-specific tools to check specific systems (e.g., Microsoft Baseline
Security Analyzer used to audit Windows machines)
• Application security assessment tools to ensure that applications do not
have vulnerable code
•Tools to parse through logs to facilitate easier analysis
The list above is by no means all-inclusive; it does, however, show the need for
tools. The work that the tools listed above can accomplish would be virtually
FIGURE 3.7
Toolsets.
Security Policies
& Procedures
Security
Organization
Executive
Support
EnforcementToolsets
Training and
Awareness
Security
Strategy
AU1706_book.fm Page 53 Wednesday, July 28, 2004 11:06 AM
54
A Practical Guide to Security Assessments
impossible for an average IT staff to do manually. This clearly underscores the
importance of toolsets.
Tools are available both commercially and in the form of freeware and shareware.
In some cases, companies might have the expertise to develop their own custom
tools. The type of tools you use in your environment will be influenced by a number
of factors, some of which include what is being run on the network, existing security
policies, budget (for purchasing tools), and the level of expertise of the people who
will be using the tools. The tools you use are a matter of preference. The trend today
is to use some combination of commercially available tools, custom-developed tools,
and freeware/shareware, for three reasons:
First, some wonderful tools that are free and community supported provide
much of the functionality that a company would want. Some of the most
widely respected security tools, such as Nmap and Nessus, are available
for free.
Second, most companies have budget constraints, and so if some good tools
can be had for nothing, companies will certainly take advantage of it. Some
companies do take a hard line on downloading tools from the Internet
because there is no assurance that they are not corrupted. Also, with free-
ware, there is no recourse — freeware is taken on the basis of “try at your
own risk.” It all depends on the company.
Third, companies want to protect themselves against people who would
potentially break into their systems (i.e., hackers). In most cases, hackers
are using freely available tools to do most of their work. Using these same
tools helps companies simulate what a hacker would do and use that to
protect themselves.
E
NFORCEMENT
Enforcement (Figure 3.8) is the final yet critical component of an information
security program. Enforcement in the context of an information security program
consists of actively ensuring that information security policies and procedures are
followed. Enforcement can take place using manual procedures or can be automated
using functionality available in existing systems (e.g., strong password policies can
be enforced automatically in systems such as Microsoft Windows 2000). To the
extent that enforcement can be automated, it should be because this results in greater
compliance. Manual enforcement of security policies and procedures is a bit more
difficult. The security organization, as discussed earlier, would have people carry
out these enforcement activities. Besides these individuals, the IT audit part of an
internal audit department would likely conduct some enforcement-related activities
as well. For enforcement to be successful, strong upper management support for
good security practices is necessary. Without management support, enforcement has
no “teeth.” Auditors or other members of a security organization may try to enforce
security policies and procedures and not get very far because no repercussions for
noncompliance exist. Conversations with people in different companies have uncov-
ered numerous stories of where business groups are given a report that documents
AU1706_book.fm Page 54 Wednesday, July 28, 2004 11:06 AM
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
