If your only previous exposure to computing is to previous versions of the Macintosh operating system (Mac OS) or Microsoft Windows, you’ve probably noticed that Mac OS X is very different indeed. If you’re familiar with the “classic” Mac OS, you’ve probably noticed that with Mac OS X you don’t need to preallocate how much memory a program uses, and that programs in the background run without any noticeable degradation in performance. If you have used either Mac OS or Windows, you’ve surely noticed that Mac OS X does not crash as much as these other operating systems — in fact, for most users it doesn’t crash at all! In this chapter, we’ll see why Mac OS X is so different.
The Mac OS X environment is built on top of the Unix operating system and the Mach kernel. Together, they form a powerful computing infrastructure that is part of what Apple calls Darwin . In addition to the Mach and Unix services, Darwin includes the Mac OS X networking and (multiple integrated) filesystems.
An operating system is the master control program that loads and runs other programs and controls a computer’s input and output systems, such as the keyboard, display, and disk drives. Multitasking operating systems such as Mach allow more than one program to run at the same time on the same computer; the operating system automatically arbitrates between the various programs that are waiting to run, letting one program run for a few milliseconds, then another, then another. Each program gets its own time slice of system resources.
In addition to dividing the CPU resources between different programs that want to run, the operating system divides up the computer’s memory and controls access to the computer’s input and output devices. For example, the operating system makes sure that mouse events are sent to the correct programs, even if more than one program is prepared to receive mouse events at a given instant.
Another important function of the operating system is to prevent running programs from interfering with each other. This is called memory protection . Without such protection, a wayward program could affect other programs or other users, delete important files, or even crash the entire computer system (users of Apple’s Mac OS 9 and Microsoft Windows 98 are used to frequent crashes).
The Unix operating system was developed in the early 1970s at AT&T Bell Labs. The creators of Unix sought to create a flexible computing environment in which they could get useful work done by putting together a complex system from simple building blocks. They also wanted to create a portable operating system — that is, an operating system that could run just as easily on computers made by a variety of different vendors. (At the time, practically every computer ran an operating system that had been written specifically for that computer. It was extremely rare for computers from different companies — and sometimes from the same company — to run compatible systems.)
Unix was hugely successful. In the 1970s and 1980s, it spread throughout academia and to many research labs. But it was also a bit of an outlaw system, because no computer companies actually sanctioned Unix to be run on their hardware. Digital Equipment Corporation, for example, had been known to tell customers that running Unix voided the warranty on Digital’s PDP and VAX minicomputers. Instead of Unix, Digital wanted its customers to run their proprietary RSTS, RT11, and VMS operating systems.
Things changed for Unix in the 1980s, when engineers at Sun Microsystems, Inc. and a number of other companies took Motorola’s new 68000 series of microprocessors and used them to create a new kind of computer — the engineering workstation . Because these companies didn’t have the millions of dollars to create their own operating systems, they decided instead to license Unix.
With the success of the workstation vendors, Unix went mainstream. Today it is the basis of systems sold by Sun, Compaq, Hewlett-Packard, IBM, and many other firms. Unix is also the basis for a variety of free operating systems, including Linux, FreeBSD, and NetBSD.
In the 1980s, Digital funded a project at Carnegie Mellon University to develop a new operating system for a supercomputer that Digital was creating. The group at CMU decided to build an operating system that was designed for extraordinarily high performance: most operations would be memory-mapped, the system was optimized for high-speed communication between processes, and the operating system would be multithreaded so that it could run on computers with multiple processors. When Digital canceled its supercomputer, the CMU group decided to rename the operating system "Mach” and to continue development. Avie Tevanian, now Apple’s Senior Vice President of Software Engineering, was one of the lead developers of the system.
The Mach operating system consists of a kernel and a system support environment. One layer up from the hardware, the Mach kernel manages the computer’s memory and schedules computing time for the various programs that are ready to run.
The kernel implements virtual memory , a system that uses the computer’s hard disk to simulate a much larger block of random-access memory (RAM). Virtual memory is transparent to running programs (although it can slow them down considerably, because hard-disk access is thousands of times slower than RAM access). A program that needs a 10-MB block of memory simply allocates a 10-MB block of memory; the kernel automatically shuffles data from the computer’s internal memory to the hard disk and back, as necessary. This is called swapping or paging .
The Mach kernel oversees the creation of processes , or running programs. Mach further allows each process to create additional “lightweight” processes, called threads, which run independently of each other but within the same program. Threads simplify writing programs that do more than one thing at the same time.
Mach also provides a highly efficient system of interprocess communication using Mach messages . These messages can be sent from one thread to another, between processes, or even from one computer to another across the network.
Sitting on top of the Mach kernel is the operating system support environment, which runs a version of the 4.4BSD (Berkeley Software Distribution) Unix system. The Berkeley Unix system provides Cocoa with access to hard disks and floppy disks through the Unix and HFS filesystems, networking using either TCP/IP or AppleTalk, support for the network filesystems, and a variety of other important features.
Mac OS X’s Unix environment also contains all of the device drivers for managing the computer’s hardware devices, including the keyboard, the screen, the serial ports, and the USB and FireWire buses. Unix is an intimate part of Cocoa, and it is therefore important to understand how it manages users and processes. We’ll discuss these in the following sections.
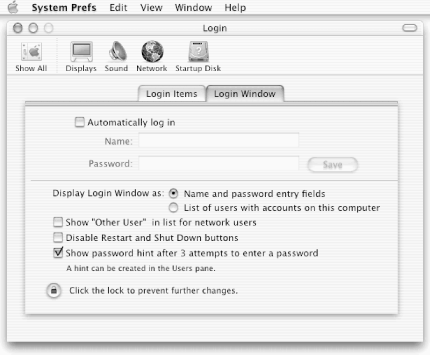
Everyone who uses a computer running Mac OS X has a username. When you log in, your username gets translated into a unique number called your user identifier , or UID. (If you don’t have to log into your Mac OS X computer in order to use it, your computer has been set to “auto-login” to a particular user account. For details, look at the Login Window pane of the System Preferences application, shown in Figure 9-1.)
Unix also uses some special system users for a variety of special purposes:
These users are not actually people who log in, but merely different UIDs used to run background processes with different kinds of privileges.
Mac OS X largely insulates you from needing to know about the superuser and other user accounts. Some control panes that allow you to make significant system changes have a small “lock” icon at the bottom that you need to click in order to confirm that you really wish to modify the setting. Other control panes allow you to click the lock to prevent settings from being further modified (see Figure 9-1). Sometimes a superuser or other password is required to “open” the lock and enable settings to be modified.
When you create multiple users on the same Cocoa computer, the Cocoa administration utilities make sure that each user has his or her own UID. Having different UIDs prevents users from seeing each other’s private files. Normally, this administrative task is taken care of by the Mac OS X’s NetInfo (network administrative information) system.
Mach is a multitasking operating system. Every task that the computer performs at any given moment (such as the Window Server, the Finder, or the TextEdit application) has an associated process. The process is the operating system’s fundamental tool for controlling the computer. You can generally think of the terms process and running program as synonymous, but be careful: some applications create more than one process (as we’ll see in the next chapter). You can also run more than one copy of a single program at a time, in which case you’ll have only one program but two (or more) processes (we’ll demonstrate that in the next chapter as well).
The Mach kernel assigns every running process a unique number called the process identifier , or PID. The first process that runs when the computer starts up is called init ; this process is given the number 1. Any process can fork , and by doing so, create a new process. All of the processes on your computer are descendants of process number 1. Mach process numbers can range from 1 to 32767, and the kernel guarantees that no two active processes will ever have the same number.