Chapter 26. Backing Up and Restoring Cisco IOS Software and Configurations
This chapter provides information and commands concerning the following topics:
![]() Viewing the Cisco IOS File System
Viewing the Cisco IOS File System
![]() Commonly used URL prefixes for Cisco network devices
Commonly used URL prefixes for Cisco network devices
![]() Deciphering IOS image filenames
Deciphering IOS image filenames
![]() Backing up configurations to a TFTP server
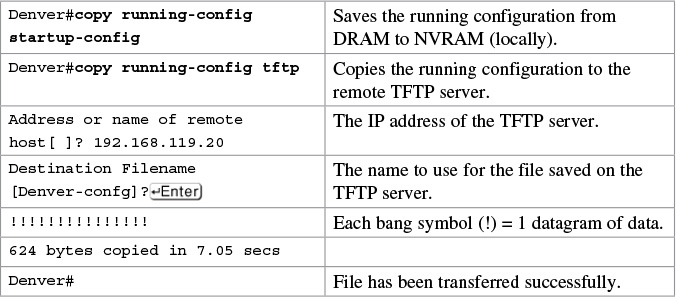
Backing up configurations to a TFTP server
![]() Restoring configurations from a TFTP server
Restoring configurations from a TFTP server
![]() Backing up the Cisco IOS Software to a TFTP server
Backing up the Cisco IOS Software to a TFTP server
![]() Restoring/upgrading the Cisco IOS Software from a TFTP server
Restoring/upgrading the Cisco IOS Software from a TFTP server
![]() Restoring the Cisco IOS Software from ROM Monitor mode using Xmodem
Restoring the Cisco IOS Software from ROM Monitor mode using Xmodem
![]() Restoring the Cisco IOS Software using the ROM Monitor environmental variables and tftpdnld command
Restoring the Cisco IOS Software using the ROM Monitor environmental variables and tftpdnld command
![]() Configuring a Secure Copy Server
Configuring a Secure Copy Server
![]() Verifying and Troubleshooting Secure Copy
Verifying and Troubleshooting Secure Copy
![]() Configuration Example: Using Secure Copy
Configuration Example: Using Secure Copy
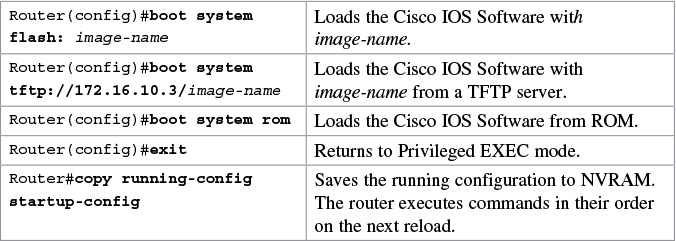
Boot System Commands
Tip
If you enter boot system flash first, that is the first place the router goes to look for the Cisco IOS Software. If you want to go to a TFTP server first, make sure that the boot system tftp command is the first command you enter.
If the configuration has no boot system commands, the router defaults to loading the first valid Cisco IOS image in flash memory and running it. If no valid Cisco IOS image is found in flash memory, the router attempts to boot from a network TFTP server. After six unsuccessful attempts of locating a network TFTP server, the router loads into ROMmon mode.
The Cisco IOS File System
Note
The Cisco IOS File System (IFS) provides a single interface to all the file systems available on a routing device, including the flash memory file system; network file systems such as TFTP, Remote Copy Protocol (RCP), and FTP; and any other endpoint for reading and writing data, such as NVRAM, or the running configuration. The Cisco IFS minimizes the required prompting for many commands. Instead of entering in an EXEC-level copy command and then having the system prompt you for more information, you can enter a single command on one line with all necessary information.
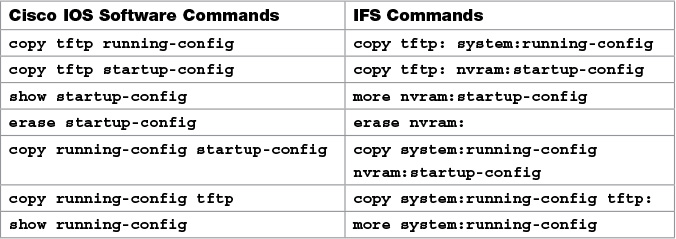
Viewing the Cisco IOS File System
Note
The Cisco IOS File System uses a URL convention to specify files on network devices and the network. Many of the most commonly used URL prefixes are also available in the Cisco IOS File System.
Commonly Used URL Prefixes for Cisco Network Devices

Deciphering IOS Image Filenames
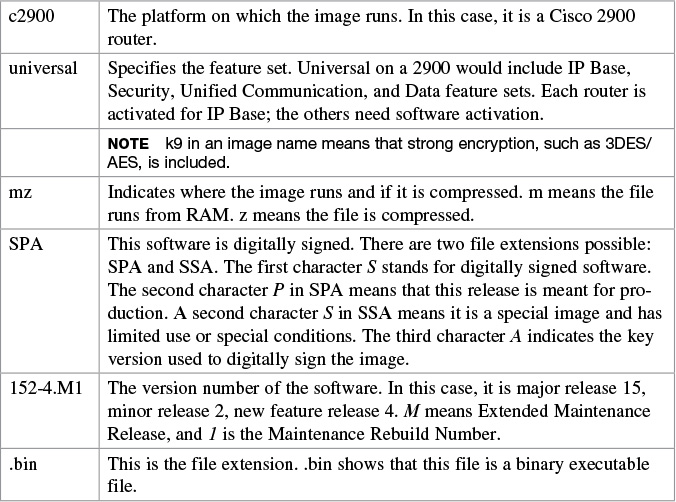
Although it looks long and complex, there is a reason that Cisco names its IOS images the way that it does. It is important to understand the meaning behind an IOS image name so that you can correctly choose which file to work with.
There are different parts to the image filename, as follows:
c2900-universalk9-mz.SPA.152-4.M1.bin
Note
The Cisco IOS naming conventions, meanings, content, and other details are subject to change.
Note
You can also use the preceding sequence for a copy startup-config tftp command sequence.
Restoring Configurations from a TFTP Server
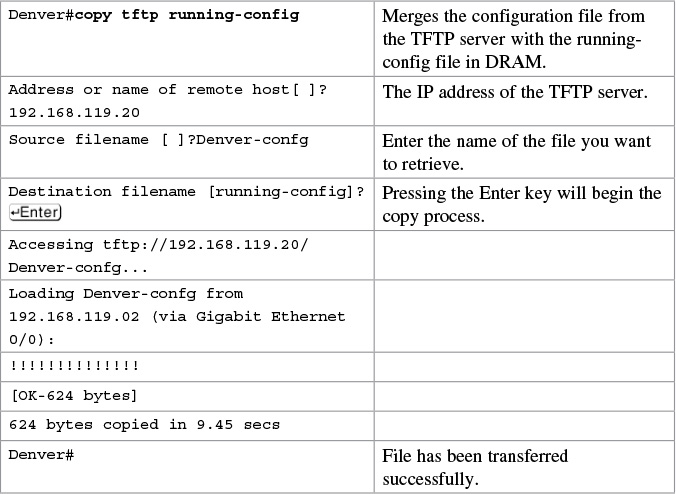
Note
You can also use the preceding sequence for a copy tftp startup-config command sequence.
Note
When copying a file into a configuration file, the no shutdown command does not carry over into the configuration file. You must enable the interfaces with the no shutdown command.
Restoring/Upgrading the Cisco IOS Software from a TFTP Server
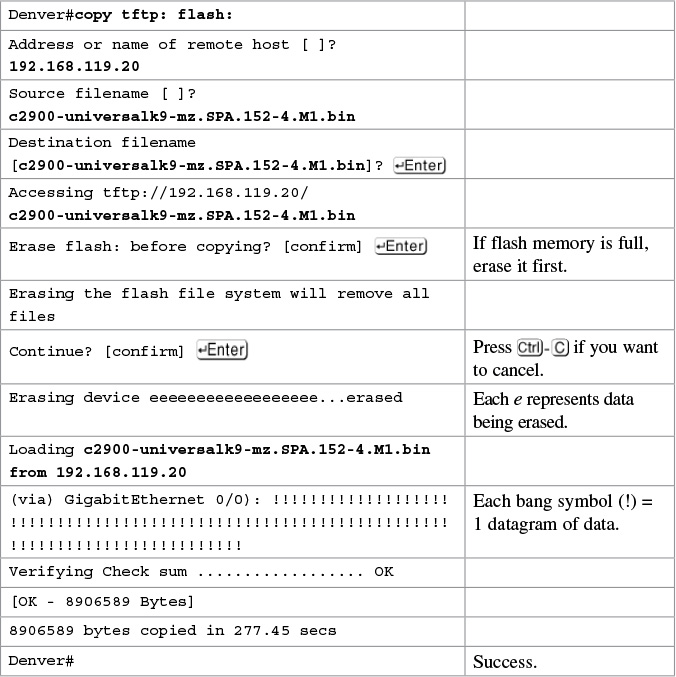
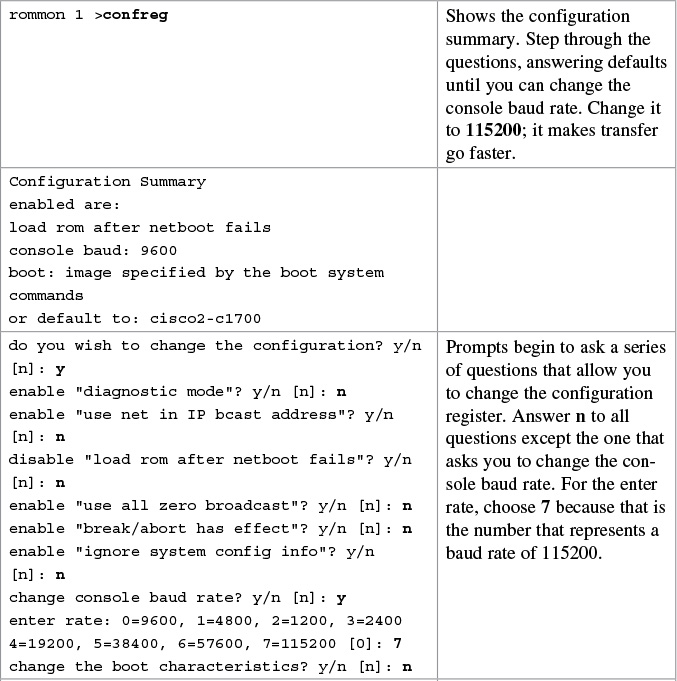
Restoring the Cisco IOS Software from ROM Monitor Mode Using Xmodem
The output that follows was taken from a 1720 router. Some of this output might vary from yours, depending on the router model you are using.


Restoring the Cisco IOS Software Using the ROM Monitor Environmental Variables and tftpdnld Command
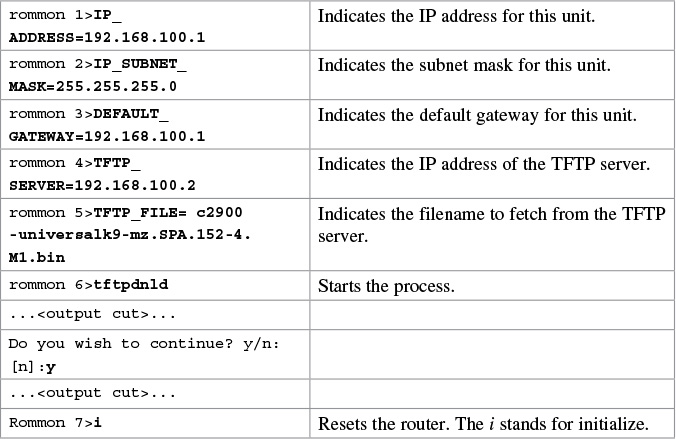
Caution
Commands and environmental variables are case sensitive, so be sure that you have not accidentally added spaces between variables and answers.
Secure Copy
The Secure Copy (SCP) feature provides a secure and authenticated method for copying device configurations or device image files. SCP relies on Secure Shell (SSH). SCP allows a user with appropriate authorization to copy any file that exists in the Cisco IOS File System (IFS) to and from a device by using the copy command.
Note
Before enabling SCP, you must correctly configure SSH, authentication, and authorization on the device and replace Telnet with SSH on the vty ports. See Chapter 25, “Device Hardening,” for the commands needed to configure SSH.
Because SCP relies on SSH for its secure transport, the device must have a Rivest, Shamir, and Adelman (RSA) key pair.
Configuring a Secure Copy Server

Verifying and Troubleshooting Secure Copy

Configuration Example: Using Secure Copy
The following example shows the commands for using SCP to transfer an IOS image from flash to a remote host that supports SSH.
Note
Your router does not need to be set up as an SCP server for this transfer to work. You need only to have SSH configured.
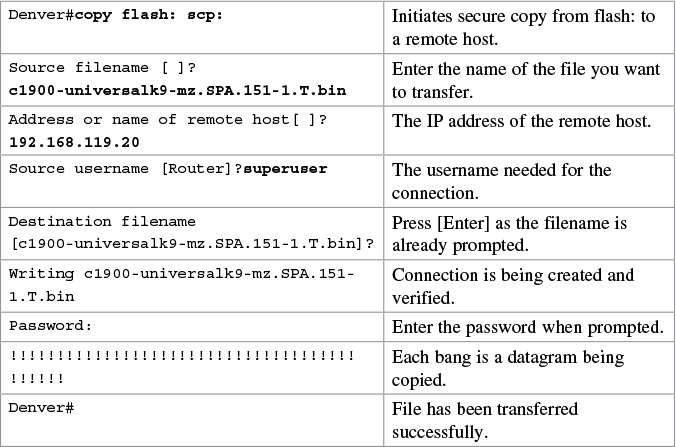
As with any use of the copy command, you can enter some of the specific details into the command itself:
Denver#copy flash:c1900-universalk9-mz.SPA.151-1.T.bin
scp://[email protected]/
Note
When using SCP, you cannot enter the password into the copy command; you must enter it when prompted.