Chapter 30. Device Monitoring
This chapter provides information about the following topics:
![]() Simple Network Management Protocol
Simple Network Management Protocol
![]() Network Time Protocol configuration
Network Time Protocol configuration
Device Monitoring
Network administrators need to be able to perform more than just the configuration of network devices. They need to be able to monitor network devices to ensure that the network is operating as efficiently as possible and to identify potential bottlenecks or trouble spots. The following sections deal with protocols that can help monitor a network.
Simple Network Management Protocol
Simple Network Management Protocol (SNMP) is the most commonly used network management protocol.
If SNMP is not required on a router, you should turn it off by using the no snmp-server command at the global configuration mode prompt.
Edmonton(config)#no snmp-server
Note
Cisco IOS software supports three different versions of SNMP:
1. SNMPv1—Defined originally in RFC 1157. Security is based upon community strings.
2. SNMPv2c—An experimental protocol originally defined in RFCs 1901, 1905, and 1906. It uses the same community-based security model of SNMPv1.
3. SNMPv3—Version 3 of SNMP. An interoperable standards-based protocol originally defined in RFCs 2273 to 2275. SNMPv3 provides secure access to devices by a combination of authenticating and encrypting packets over the network.
Note
You must configure the SNMP agent (your Cisco device) to use the version of SNMP supported by the management station. An agent can communicate with multiple managers; you can configure Cisco IOS software to support communications with one management station using SNMPv1, one using SNMPv2c and another using SNMPv3.
Note
Beginning with SNMPv3, methods to ensure the secure transmission of data between manager and agent were added. You can now define a security policy per group or limit IP addresses to which its members can belong. You will now have to define encryption, hashing algorithms, and passwords for each user.
Table 30-1 shows the different SNMP security models.
Tip
The SNMP security levels are as follows:
![]() noAuthNoPriv—Authenticates SNMP messages using a community string. No encryption is provided.
noAuthNoPriv—Authenticates SNMP messages using a community string. No encryption is provided.
![]() authNoPriv—Authenticates SNMP messages using either HMAC with MD5 or SHA-1. No encryption is provided.
authNoPriv—Authenticates SNMP messages using either HMAC with MD5 or SHA-1. No encryption is provided.
![]() authPriv—Authenticates SNMP messages by using either HMAC-MD5 or SHA. It encrypts SNMP messages using DES, 3DES, or AES.
authPriv—Authenticates SNMP messages by using either HMAC-MD5 or SHA. It encrypts SNMP messages using DES, 3DES, or AES.
![]() priv—Does not authenticate SNMP messages. Encrypts only DES or AES.
priv—Does not authenticate SNMP messages. Encrypts only DES or AES.
Tip
If SNMPv3 cannot be used, secure SNMPv1 or SNMPv2 by using uncommon, complex community strings and by enabling read-only access.
Tip
If community strings are also used for SNMP traps, they must be different from community strings for get and set methods. This is considered best practice.
Configuring SNMP
Note
There is no specific command used to enable SNMP. The first snmp-server command that you enter enables the supported versions of SNMP.

Note
A community string is like a password. In the case of the first command, the community string grants you access to SNMP.
Securing SNMPv1 or SNMPv2


Configuration Backups
It is important to keep a copy of a router’s configuration in a location other than NVRAM. Automated jobs can be set up to copy configurations from the router at regular intervals to local or remote file systems.

To create an archive copy manually, use the archive config command from EXEC mode:
Edmonton#archive config
Tip
When the write-memory command is enabled, the copy running-config startup-config command triggers an archive to occur.
Implementing Logging
Network administrators should implement logging to get the insight into what is occurring in their network. When a router reloads, all local logs are lost, so it is important to implement logging to an external destination. These next sections deal with the different mechanisms that you can use to configure logging to a remote location.
Configuring Syslog

Syslog Message Format
The general format of syslog messages generated on Cisco IOS Software is as follows:
seq no:timestamp: %facility-severity-MNEMONIC:description

Syslog Severity Levels
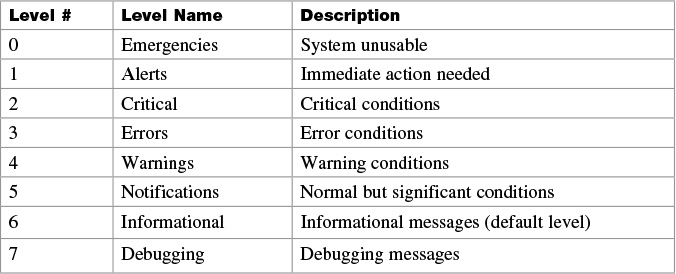
Table 30-2 shows the eight levels of severity in logging messages.
Setting a level means you will get that level and everything numerically below it. Level 6 means you will receive messages for levels 0 through 6.
Syslog Message Example
The easiest syslog message to use as an example is the one that shows up every time you exit from global configuration back to privileged EXEC mode. You have just finished entering a command, and you want to save your work, but after you type exit you see something like this:
Edmonton(config)#exit
Edmonton#
*Jun 23:22:45:20.878: %SYS-5-CONFIG_I: Configured from console by console
Edmonton#
(Your output will differ depending on whether you have sequence numbers or time/date stamps configured).
So what does this all mean?
![]() No sequence number is part of this message.
No sequence number is part of this message.
![]() The message occurred at June 23, at 22:45:20.878 (or 10:45 PM, and 20.878 seconds).
The message occurred at June 23, at 22:45:20.878 (or 10:45 PM, and 20.878 seconds).
![]() It is a sys message, and it is level 5 (a notification).
It is a sys message, and it is level 5 (a notification).
![]() It is a config message; specifically, the configuration occurred from the console.
It is a config message; specifically, the configuration occurred from the console.
Configuring NetFlow
NetFlow is an application for collecting IP traffic information. It is used for network accounting and security auditing.
Caution
NetFlow consumes additional memory. If you have limited memory, you might want to preset the size of the NetFlow cache to contain a smaller number of entries. The default cache size depends on the platform of the device.

NetFlow exports data in UDP in one of five formats: 1, 5, 7, 8, 9. Version 9 is the most versatile, but it is not backward compatible with Versions 5 or 8.
Verifying NetFlow
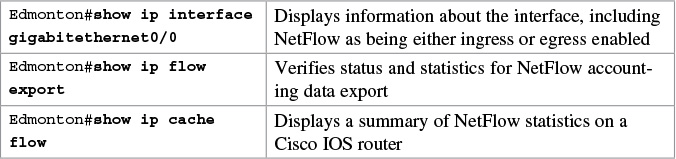
Note
The show ip cache flow command is useful for seeing which protocols use the highest volume of traffic and between which hosts this traffic flows.
Network Time Protocol
Most networks today are being designed with high performance and reliability in mind. Delivery of content is, in many cases, guaranteed by service-level agreements (SLA). Having your network display an accurate time is vital to ensuring that you have the best information possible when reading logging messages or troubleshooting issues.
Network Time Protocol Configuration
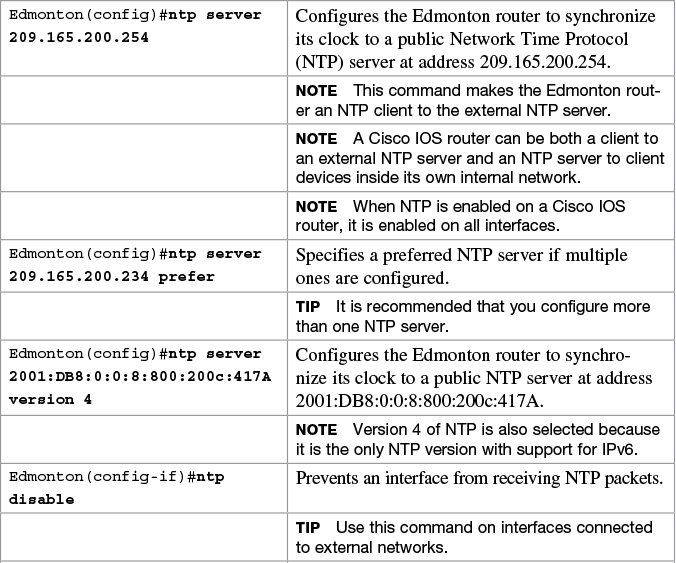

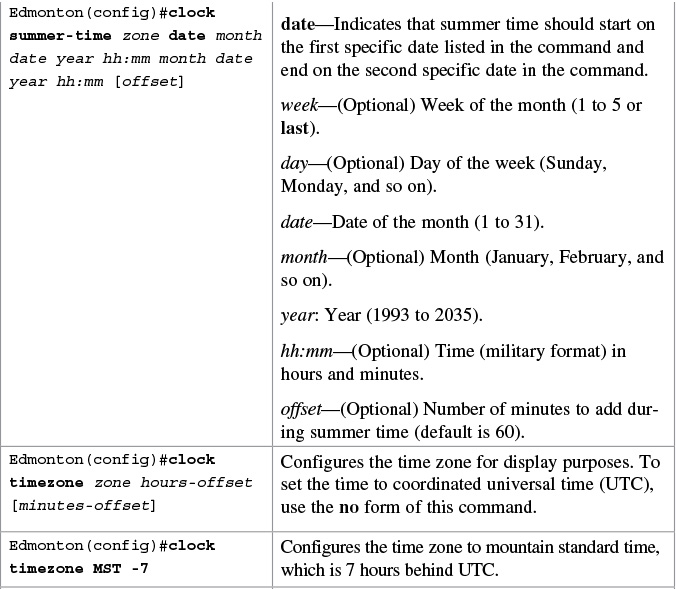
When a local device is configured with the ntp master command, it can be identified by a syntactically correct but invalid IP address. This address is in the form of 127.127.x.x. The master synchronizes with itself and uses the 127.127.x.x address to identify itself. This address is displayed with the show ntp associations command and must be permitted via an access list if you are authenticating your NTP servers.
Verifying NTP

Setting the Clock on a Router
Note
It is important to have your routers display the correct time for use with time stamps and other logging features.
If the system is synchronized by a valid outside timing mechanism, such as an NTP, or if you have a router with a hardware clock, you do not need to set the software clock. Use the software clock if no other time sources are available.

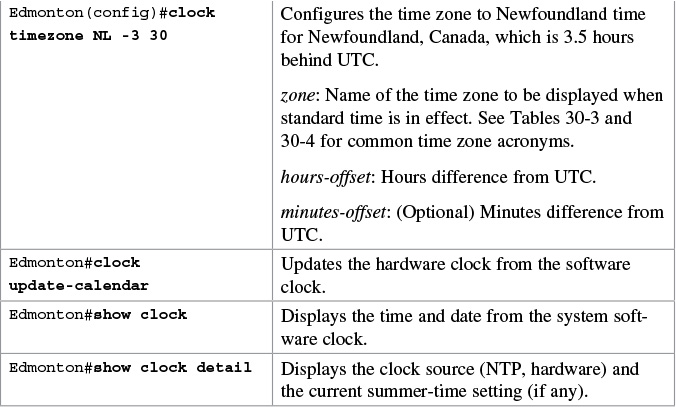
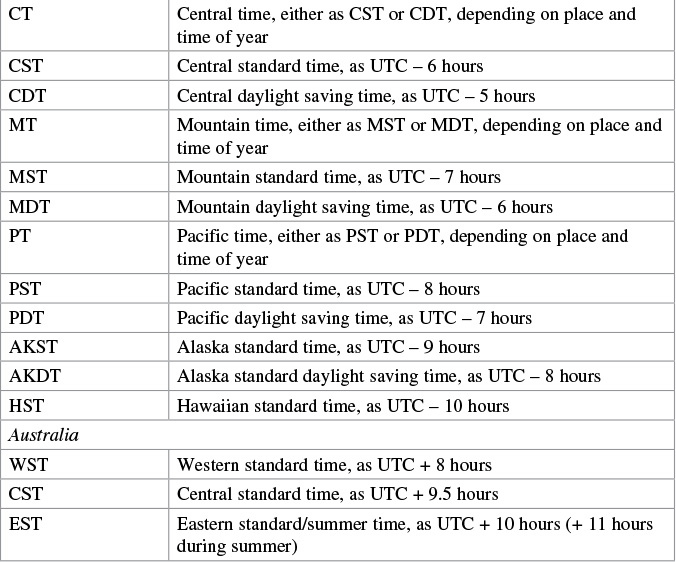
Table 30-3 shows the common acronyms used for setting the time zone on a router.
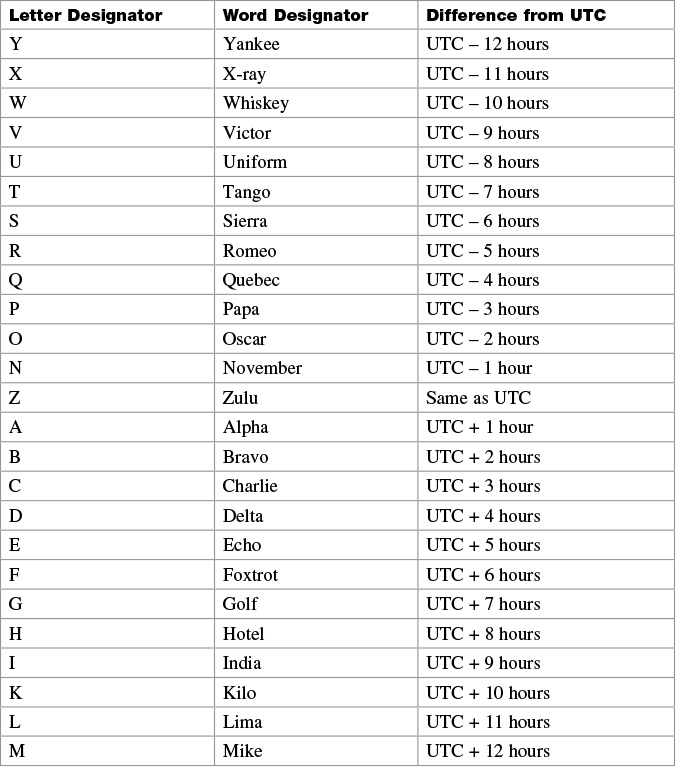
Table 30-4 lists an alternative method for referring to time zones, in which single letters are used to refer to the time zone difference from UTC. Using this method, the letter Z indicates the zero meridian, equivalent to UTC, and the letter J (Juliet) refers to the local time zone. Using this method, the international date line is between time zones M and Y.