Chapter 29. IOS Tools
This chapter provides information and commands concerning the following topics:
![]() Configuring a device to accept a remote Telnet connection
Configuring a device to accept a remote Telnet connection
![]() Using Telnet to remotely connect to other devices
Using Telnet to remotely connect to other devices
![]() Internet Control Message Protocol redirect messages
Internet Control Message Protocol redirect messages
![]() Examples of using the ping and the extended ping commands
Examples of using the ping and the extended ping commands
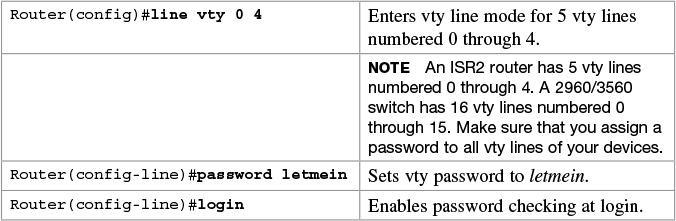
Configuring a Device to Accept a Remote Telnet Connection
Note
The ability to telnet into a Cisco device is part of every Cisco IOS. You only need to assign passwords to allow a remote connection into a device.
Note
A device must have two passwords for a remote user to be able to make changes to the configuration:
![]() Line vty password
Line vty password
![]() enable or enable secret password
enable or enable secret password
Without the enable or enable secret password, a remote user will only be able to get to user mode, not to privileged EXEC mode. Remember that without an enable or enable secret password set, a user logged in through the console will still access privileged EXEC mode. But a remote user needs one of these passwords to gain access. This is extra security.
Using Telnet to Remotely Connect to Other Devices
The following five commands all achieve the same result: the attempt to connect remotely to the router named Paris at IP address 172.16.20.1.

Any of the preceding commands lead to the following configuration sequence:

Verifying Telnet

The following configuration creates a big security hole. Never use it in a live production environment. Use it in the lab only!
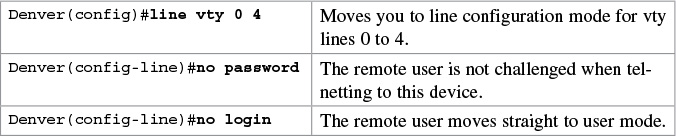
Note
A device must have two passwords for a remote user to be able to make changes to the configuration:
![]() Line vty password (or have it explicitly turned off; see the preceding Caution)
Line vty password (or have it explicitly turned off; see the preceding Caution)
![]() Enable or enable secret password
Enable or enable secret password
Without the enable or enable secret password, a remote user will only be able to get to user mode, not to privileged mode. This is extra security.
Internet Control Message Protocol Redirect Messages
Internet Control Message Protocol (ICMP) is used to communicate to the original source the errors encountered while routing packets and to exercise control on the traffic. Routers use ICMP redirect messages to notify the hosts on the data link that a better route is available for a particular destination.

The ping Command
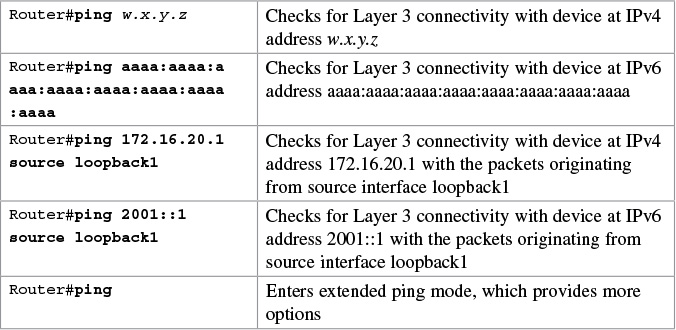
The following table describes the possible ping output characters.

Examples of Using the ping and the Extended ping Commands
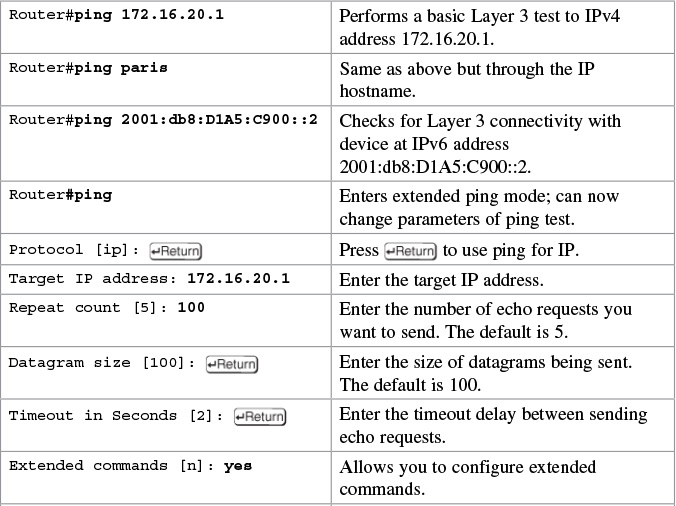
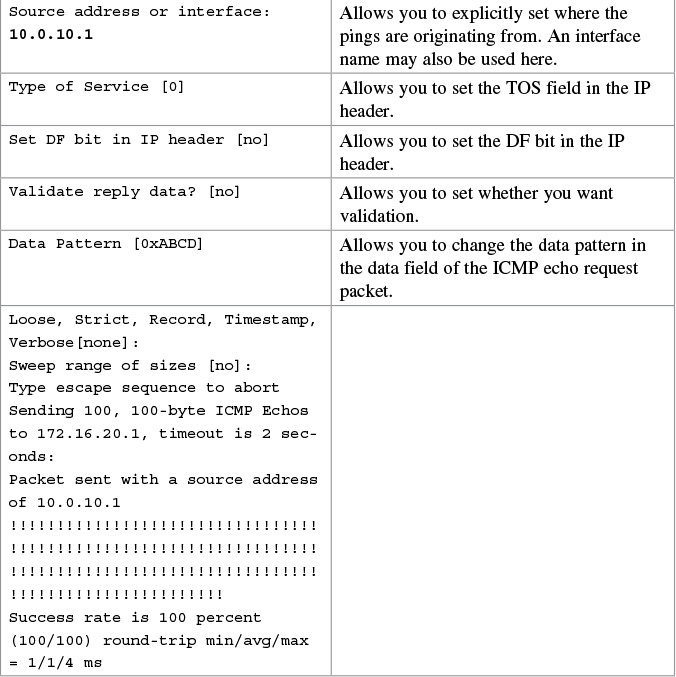
If you want to interrupt the ping operation, use the ![]() keystroke combination. This ends the operation and returns you to the prompt.
keystroke combination. This ends the operation and returns you to the prompt.
The traceroute Command
The traceroute command (or tracert in Windows) is a utility that allows observation of the path between two hosts.

Note
In Windows operating systems, the command to allow observation between two hosts is tracert:
C:Windowssystem32>tracert 172.16.20.1
C:Windowssystem32>tracert 2001:DB8:c:18:2::1
