Chapter 4. Information Security Governance and Risk Management
This chapter covers the following topics:
• Security principles and terms: Principles and terms discussed include CIA, vulnerability, threat, threat agent, risk, exposure, countermeasure, due care, due diligence, job rotation, and separation of duties.
• Security frameworks and methodologies: Frameworks and methodologies discussed include ISO/IEC 27000 series, CobiT, NIST 800-53, COSO, ITIL, Six Sigma, and CMMI.
• Risk assessment: Assessment topics discussed include information and asset (tangible/intangible) value and cost, quantitative risk analysis, qualitative risk analysis, steps in risk assessment, total risk versus residual risk, and handling risk.
• Risk management principles: Principles discussed include risk management policy, risk management team, and risk analysis team.
• Information security governance components: Components include policies, procedures, standards, guidelines, baselines, and information classification and life cycle.
• Security governance roles and responsibilities: Roles and responsibilities discussed include board of directors, high-level management, CEO/CFO/CIO/CPO/CSO, audit committee, data owner, data custodian, system owner, system administrator, security administrator, security analyst, application owner, supervisor, user, auditor, third-party governance, and personnel security.
• Security awareness and training: Topics include the why, when, how, and who of security awareness and training.
• Security budget, metrics, and effectiveness: Topics include understanding a security budget, understanding security metrics, and measuring security effectiveness.
Information security governance involves the principles, frameworks, and methods that establish criteria for protecting information assets, including security awareness. Risk management allows organizations to identify, measure, and control organizational risks. These two facets ensure that security controls that are implemented are in balance with the operations of the organization. Each organization must develop a well-rounded, customized security program that addresses the needs of the organization while ensuring that the organization exercises due care and due diligence in its security plan.
Security professionals must take a lead role in their organization’s security program and act as risk advisors to management. In addition, security professionals must ensure that they understand current security issues and risks, governmental and industry regulations, and security controls that can be implemented. Security is an ever-evolving, continuous process, and security professionals must be watchful.
In this chapter, you will see learn how to use the information security governance and risk management components to assess risks, implement controls for identified risks, monitor control effectiveness, and perform future risk assessments.
Foundation Topics
Security Principles and Terms

When assessing and implementing information security governance and risk management, you should always understand the following concepts:
• Threat
• Risk
• Exposure
• Due care
CIA
The three fundamentals of security are confidentiality, integrity, and availability (CIA). Most security issues result in a violation of at least one facet of the CIA triad. Understanding these three security principles will help security professionals ensure that the security controls and mechanisms implemented protect at least one of these principles.
Confidentiality ensures that data is protected from unauthorized disclosure. Integrity ensures that data is accurate and reliable. Availability ensures that data is accessible when and where it is needed. A balanced security approach should be implemented to ensure that all three facets are considered when security controls are implemented. When implementing any control, you should identify the facet that the control addresses. For example, RAID addresses data availability, file hashes address data integrity, and encryption addresses data confidentiality. A balanced approach ensures that no facet of the CIA triad is ignored.
Vulnerability
A vulnerability is an absence or weakness of a countermeasure that is in place. Vulnerabilities can occur in software, hardware, or personnel. An example of a vulnerability is unrestricted access to a folder on a computer. Most organizations implement a vulnerability assessment to identify vulnerabilities.
Threat
A threat is the next logical progression in risk management. A threat occurs when vulnerability is identified or exploited. Using the earlier example, a threat would occur when an attacker identified the folder on the computer that has an inappropriate or absent access control list (ACL).
Threat Agent
A threat is carried out by a threat agent. Continuing with the example, the attacker who takes advantage of the inappropriate or absent ACL is the threat agent. Keep in mind, though, that threat agents can discover and/or exploit vulnerabilities. Not all threat agents will actually exploit an identified vulnerability.
Risk
A risk is the probability that a threat agent will exploit a vulnerability and the impact if the threat is carried out. The risk in the vulnerability example would be fairly high if the data residing in the folder is confidential. However, if the folder only contains public data, then the risk would be low. Identifying the potential impact of a risk often requires security professionals to enlist the help of subject matter experts.
Exposure
An exposure occurs when an organizational asset is exposed to losses. If the folder with the inappropriate or absent ACL is compromised by a threat agent, the organization is exposed to the possibility of data exposure and loss.
Countermeasure
A countermeasure reduces the potential risk. Countermeasures are also referred to as safeguards or controls. Three things must be considered when implementing a countermeasure: vulnerability, threat, and risk. For our example, a good countermeasure would be to implement the appropriate ACL and to encrypt the data. The ACL protects the integrity of the data, and the encryption protects the confidentiality of the data.
Countermeasures or controls come in many categories and types. The categories and types of controls are discussed in depth in Chapter 2.
All the aforementioned security concepts work together in a relationship that is demonstrated in Figure 4-1.
Figure 4-1. Security Concept Cycle

Due Care and Due Diligence
Due care and due care are legal terms. Due care means that an organization took all reasonable measures to prevent security breaches and also took steps to mitigate damages caused by successful breaches. This includes making sure that the correct policies, procedures, and standards are in place and being followed. Due diligence means that an organization investigated all vulnerabilities. This includes performing the appropriate audits and assessments to ensure that the organization is protected. Both of these legal terms have bearing on the security governance and risk management process.
Job Rotation
Job rotation ensures that more than one person fulfills the job tasks of a single position within an organization. This job rotation ensures that more than one person is capable of performing those tasks, providing redundancy. It is also an important tool in helping an organization to recognize when fraudulent activities have occurred.
Separation of Duties
Separation of duties ensures that one person is not capable of compromising organizational security. Any activities that are identified as high risk should be divided into individual tasks, which can then be allocated to different personnel or departments. When an organization implements adequate separation of duties, collusion between two or more personnel would be required to carry out fraud against the organization. Split knowledge, a variation of separation of duties, ensures that no single employee knows all the details to perform a task. An example would be two individuals knowing parts of a safe combination. Another variation is dual control, which requires that two employees must be available to complete a specific task to complete the job. An example is two managers being required to turn keys simultaneously in separate locations to launch a missile.
Security Frameworks and Methodologies

Many organizations have developed security management frameworks and methodologies to help guide security professionals. These frameworks and methodologies include security program development standards, enterprise and security architect development frameworks, security controls development methods, corporate governance methods, and process management methods. This section discusses the following frameworks and methodologies and explains where they are used:
• TOGAF
• DoDAF
• MODAF
• SABSA
• CobiT
• NIST
• COSO
• ITIL
• CMMI
• Top-down versus bottom-up approach
ISO/IEC 27000 Series
International Organization for Standardization (ISO), often incorrectly referred to as the International Standards Organization, joined with the International Electrotechnical Commission (IEC) to standardize the British Standard 7799 (BS7799) to a new global standard that is now referred to as ISO/IEC 27000 Series. ISO 27000 is a security program development standard on how to develop and maintain an information security management system (ISMS).

The 27000 Series includes a list of standards, each of which addresses a particular aspect of ISMS. These standards are either published or in development. The following standards are included as part of the ISO/IEC 27000 Series at the time of this writing:
• 27000: Published overview of ISMS and vocabulary
• 27001: Published ISMS requirements
• 27002: Published code of practice for information security management
• 27003: Published ISMS implementation guidelines
• 27004: Published ISMS measurement guidelines
• 27005: Published information security risk management guidelines
• 27006: Published requirements for bodies providing audit and certification of ISMS
• 27007: Published ISMS auditing guidelines
• 27008: Published auditor of ISMS guidelines
• 27010: Published information security management for inter-sector and inter-organizational communications guidelines
• 27011: Published telecommunications organizations information security management guidelines
• 27013: Published integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1 guidance
• 27014: In-development information security governance guidelines
• 27015: Published financial services information security management guidelines
• 27016: In-development ISMS organizational economics guidelines
• 27017: In-development cloud computing services information security control guidelines based on ISO/IEC 27002
• 27018: In-development code of practice for public cloud computing services data protection controls
• 27019: In-development energy industry process control system ISMS guidelines based on ISO/IEC 27002
• 27031: Published information and communication technology readiness for business continuity guidelines
• 27032: Published cybersecurity guidelines
• 27033-1: Published network security overview and concepts
• 27033-2: Published network security design and implementation guidelines
• 27033-3: Published network security threats, design techniques, and control issues guidelines
• 27034-1: Published application security overview and concepts
• 27034-2: In-development application security organization normative framework guidelines
• 27034-3: In-development application security management process guidelines
• 27034-4: In-development application security validation guidelines
• 27034-5: In-development application security protocols and controls data structure guidelines
• 27034-6: In-development security guidance for specific applications
• 27035: Published information security incident management guidelines
• 27035-1: In-development information security incident management principles
• 27035-2: In-development information security incident response readiness guidelines
• 27035-3: In-development computer security incident response team (CSIRT) operations guidelines
• 27036-1: In-development information security for supplier relationships overview and concepts
• 27036-2: In-development information security for supplier relationships common requirements guidelines
• 27036-3: In-development information and communication technology (ICT) supply chain security guidelines
• 27036-4: In-development information security for supplier relationships outsourcing security guidelines
• 27037: Published digital evidence identification, collection, acquisition, and preservation guidelines
• 27038: In-development information security digital redaction specification
• 27039: In-development intrusion detection systems (IDS) selection, deployment, and operations guidelines
• 27040: In-development storage security guidelines
• 27042: In-development digital evidence analysis and interpretation guidelines
• 27044: In-development security information and event management (SIEM) guidelines
• 27799: Published information security in health organizations guidelines
These standards are developed by the ISO/IEC bodies, but certification or conformity assessment is provided by third parties.
Zachman Framework
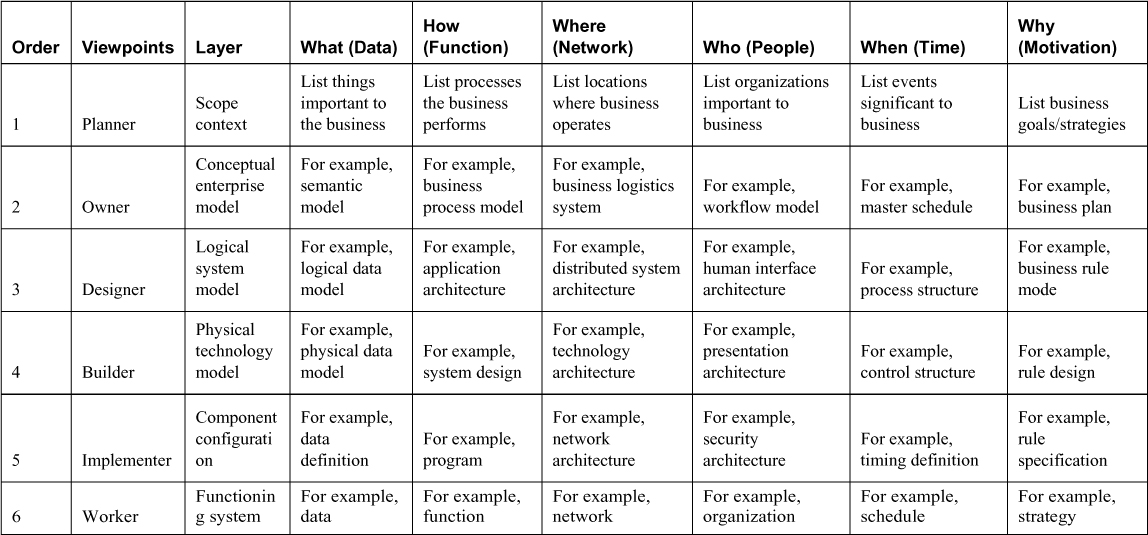
The Zachman framework, an enterprise architecture framework, is a two-dimensional classification system based on six communication questions (What, Where, When, Why, Who, and How) that intersect with different views (Planner, Owner, Designer, Builder, Subcontractor, and Actual System). This system allows analysis of an organization to be presented to different groups in the organization in ways that relate to the groups’ responsibilities. Although this framework is not security oriented, using this framework helps you to relay information for personnel in a language and format that is most useful to them (see Table 4-1).
Table 4-1. Zachman Framework Matrix with Examples
The Open Group Architecture Framework (TOGAF)
TOGAF, another enterprise architecture framework, helps organizations design, plan, implement, and govern an enterprise information architecture. TOGAF is based on four inter-related domains: technology, applications, data, and business.
Department of Defense Architecture Framework (DoDAF)
DoDAF is an architecture framework that organizes a set of products under four views: operational view (OV), system view (SV), technical standards view (TV), and all view (AV). It is used to ensure that new Department of Defense technologies integrate properly with the current infrastructures.
British Ministry of Defence Architecture Framework (MODAF)
MODAF is an architecture framework that divides information into seven viewpoints: strategic viewpoint (StV), operational viewpoint (OV), service-oriented viewpoint (SOV), systems viewpoint (SV), acquisition viewpoint (AcV), technical viewpoint (TV), and all viewpoint (AV).
Note
Organizations should select the enterprise architecture framework that represents the organization in the most useful manner based on the needs of the stakeholders.
Sherwood Applied Business Security Architecture (SABSA)
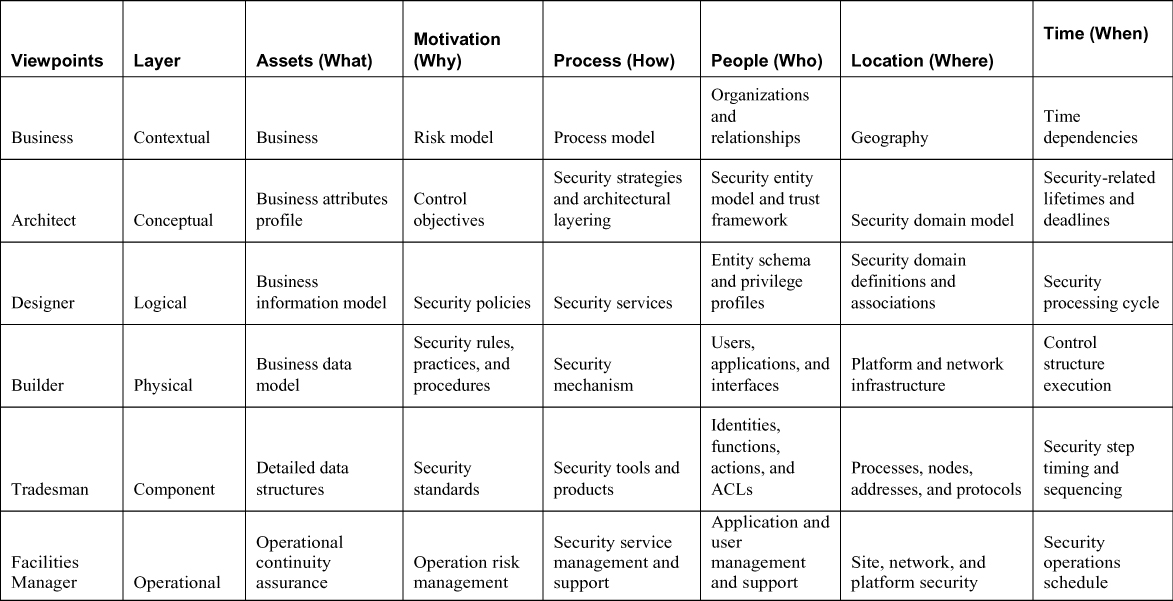
SABSA is an enterprise security architecture framework that is similar to the Zachman framework. It uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). It is a risk-driven architecture. See Table 4-2.
Table 4-2. SABSA Framework Matrix
Control Objectives for Information and related Technology (CobiT)
CobiT is a security controls development framework that uses a process model to subdivide IT into four domains: Plan and Organize (PO), Acquire and Implement (AI), Deliver and Support (DS), and Monitor and Evaluate (ME). These four domains are further broken down into 34 processes. CobiT aligns with the ITIL, PMI, ISO, and TOGAF frameworks and is mainly used in the private sector. See Figure 4-2.
Figure 4-2. CobiT 4.0 Framework

National Institute of Standards and Technology (NIST) Special Publication (SP)
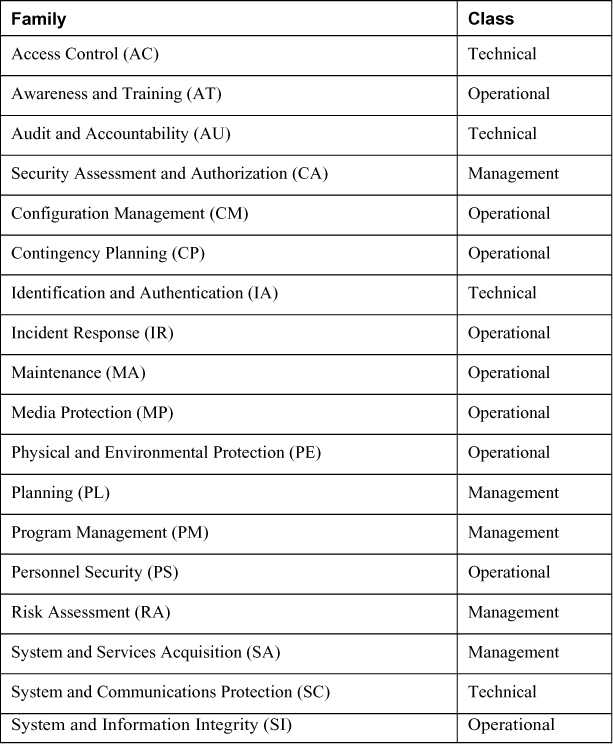
NIST SP 800-53 is a security controls development framework developed by the NIST body of the U.S. Department of Commerce. SP 800-53 divides the controls into three classes: technical, operational, and management. Each class contains control families or categories.

Table 4-3 lists the NIST SP 800-53 control families.
Table 4-3. NIST SP 800-53 Control Families
NIST 800-55 is an information security metrics framework that provides guidance on developing performance measuring procedures with a U.S. government viewpoint.
Committee of Sponsoring Organizations (COSO) of the Treadway Commission Framework
COSO is a corporate governance framework that consists of five interrelated components: control environment, risk assessment, control activities, information and communication, and monitoring. CobiT was derived from the COSO framework. COSO is for corporate governance; CobiT is for IT governance.
Information Technology Infrastructure Library (ITIL)
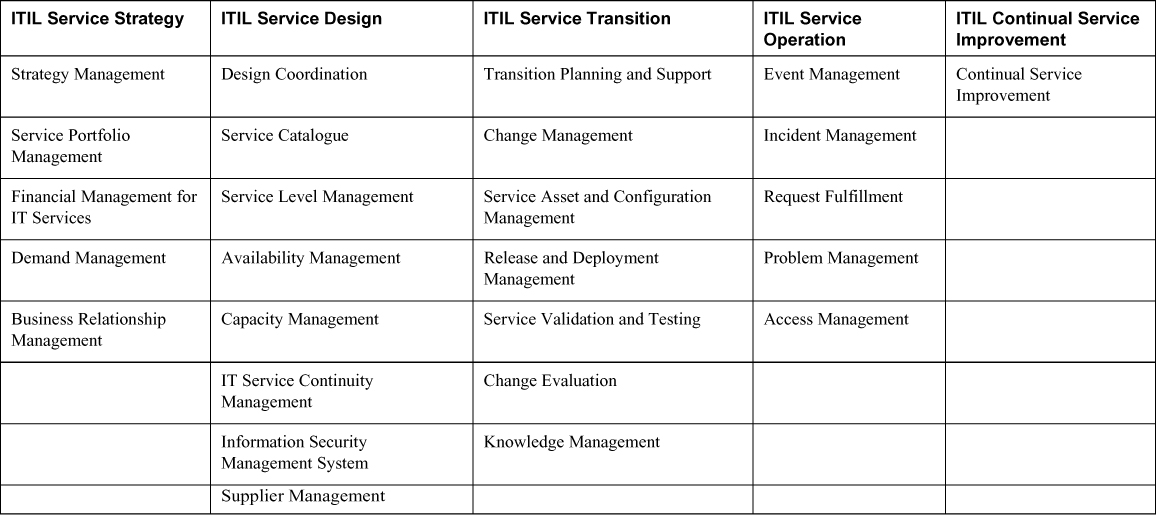
ITIL is a process management development standard developed by the Office of Management and Budget in OMB Circular A-130. ITIL has five core publications: ITIL Service Strategy, ITIL Service Design, ITIL Service Transition, ITIL Service Operation, and ITIL Continual Service Improvement. These five core publications contain 26 processes. Although ITIL has a security component, it is primarily concerned with managing the service-level agreements between an IT department or organization and its customers. As part of the OMB Circular A-130, an independent review of security controls should be performed every three years.
Table 4-4 lists the five ITIL version 3 core publications and the 26 processes within them.
Table 4-4. ITIL v3 Core Publications and Processes
Six Sigma
Six Sigma is a process improvement standard that includes two project methodologies that were inspired by Deming’s Plan/Do/Check/Act cycle. The DMAIC methodology includes Define, Measure, Analyze, Improve, and Control. The DMADV methodology includes Define, Measure Analyze, Design, and Verify. Six Sigma was designed to identify and remove defects in the manufacturing process, but can be applied to many business functions, including security.
Figures 4-3 and 4-4 show both of the Six Sigma methodologies.


Capability Maturity Model Integration (CMMI)
Capability Maturity Model Integration (CMMI) is a process improvement approach that addresses three areas of interest: product and service development (CMMI for development), service establishment and management (CMMI for services), and product service and acquisition (CMMI for acquisitions). CMMI has five levels of maturity for processes: Level 1 Initial, Level 2 Managed, Level 3 Defined, Level 4 Quantitatively Managed, and Level 5 Optimizing. All processes within each level of interest are assigned one of the five levels of maturity.
Note
No organization will implement all the aforementioned frameworks or methodologies. Security professionals should help their organization pick the framework that best fits the needs of the organization.
Top-Down versus Bottom-Up Approach
In a top-down approach, management initiates, supports, and directs the security program. In a bottom-up approach, staff members develop a security program prior to receiving direction and support from management. A top-down approach is much more efficient than a bottom-up approach because management’s support is one of the most important components of a security program.
Security Program Life Cycle
Any security program has a continuous life cycle and should be assessed and improved constantly. The security program life cycle includes the following steps:
1. Plan and Organize: Includes performing risk assessment, establishing management and steering committee, evaluating business drivers, and obtaining management approval.
2. Implement: Includes identifying and managing assets, managing risk, managing identity and access control, training on security and awareness, implementing solutions, assigning roles, and establishing goals.
3. Operate and Maintain: Includes performing audits, carrying out tasks, and managing service-level agreements.
4. Monitor and Evaluate: Include reviewing auditing and logs, evaluating security goals, and developing improvement plans for integration into Plan and Organize steps.
Figure 4-5 shows a diagram of the security program life cycle.
Figure 4-5. Security Program Life Cycle

Risk Assessment
A risk assessment is a tool used in risk management to identify vulnerabilities and threats, assess the impact of those vulnerabilities and threats, and determine which controls to implement. Risk assessment or analysis has four main goals:
• Identify assets and asset value.
• Identify vulnerabilities and threats.
• Calculate threat probability and business impact.
• Balance threat impact with countermeasure cost.
Prior to starting the risk assessment, management and the risk assessment team must determine which assets and threats to consider. This process determines the size of the project. The risk assessment team must then provide a report to management on the value of the assets considered. Management can then review and finalize the asset list, adding and removing assets as it sees fit, and then determine the budget of the risk assessment project.
If a risk assessment is not supported and directed by senior management, it will not be successful. Management must define the risk assessment’s purpose and scope and allocate the personnel, time, and monetary resources for the project.

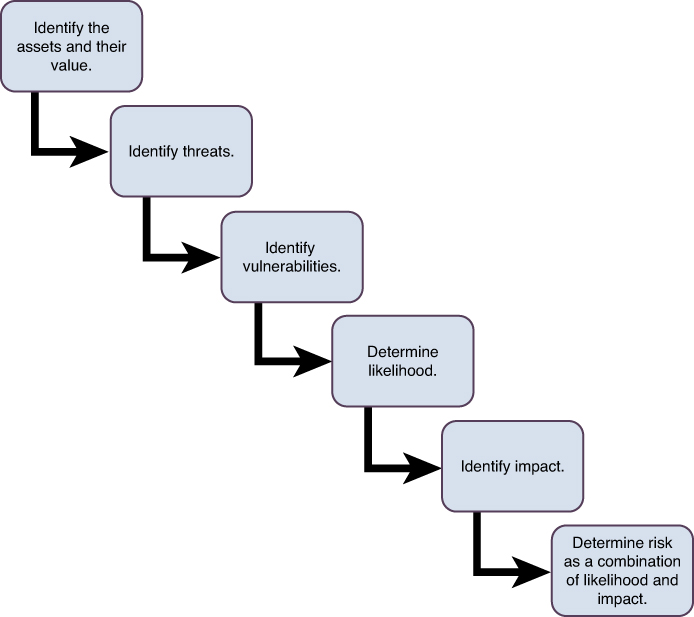
According to NIST SP 800-30, common information-gathering techniques used in risk analysis include automated risk assessment tools, questionnaires, interviews, and policy document reviews. Keep in mind that multiple sources should be used to determine the risks to a single asset. The NIST SP 800-30 identifies the following steps in the risk assessment process:
1. Identify the assets and their value.
2. Identify threats.
3. Identify vulnerabilities.
4. Determine likelihood.
5. Identify impact.
6. Determine risk as a combination of likelihood and impact.
Figure 4-6 shows the risk assessment process according to NIST SP 800-30.
Figure 4-6. NIST SP 800-30 Risk Assessment Process
Information and Asset (Tangible/Intangible) Value and Costs
As stated earlier, the first step of any risk assessment is to identify the assets and determine the asset value. Assets are both tangible and intangible. Tangible assets include computers, facilities, supplies, and personnel. Intangible assets include intellectual property, data, and organizational reputation. The value of an asset should be considered in respect to the asset owner’s view. The six following considerations can be used to determine the asset’s value:
• Value to owner
• Work required to develop or obtain the asset
• Costs to maintain the asset
• Damage that would result if the asset were lost
• Cost that competitors would pay for asset
• Penalties that would result if asset was lost
After determining the value of the assets, you should determine the vulnerabilities and threats to each asset.
Vulnerabilities and Threats Identification

When determining vulnerabilities and threats to an asset, considering the threat agents first is often easiest. Threat agents can be grouped into the following six categories:
• Human: Includes both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel.
• Natural: Includes floods, fires, tornadoes, hurricanes, earthquakes, or other natural disaster or weather event.
• Technical: Includes hardware and software failure, malicious code, and new technologies.
• Physical: Includes CCTV issues, perimeter measures failure, and biometric failure.
• Environmental: Includes power and other utility failure, traffic issues, biological warfare, and hazardous material issues (such as spillage).
• Operational: Includes any process or procedure that can affect CIA.
When the vulnerabilities and threats have been identified, the loss potential for each must be determined. This loss potential is determined by using the likelihood of the event combined with the impact that such an event would cause. An event with a high likelihood and a high impact would be given more importance than an event with a low likelihood and a low impact. Different types of risk analysis, including quantitative risk analysis and qualitative risk analysis, should be used to ensure that the data that is obtained is maximized.
Quantitative Risk Analysis
A quantitative risk analysis assigns monetary and numeric values to all facets of the risk analysis process, including asset value, threat frequency, vulnerability severity, impact, safeguard costs, and so on). Equations are used to determine total and residual risks. The most common equations are for single loss expectancy (SLE) and annual loss expectancy (ALE).

The SLE is the monetary impact of each threat occurrence. To determine the SLE, you must know the asset value (AV) and the exposure factor (EF). The EF is the percent value or functionality of an asset that will be lost when a threat event occurs. The calculation for obtaining the SLE is as follows:
SLE = AV × EF
For example, an organization has a Web server farm with an AV of $20,000. If the risk assessment has determined that a power failure is a threat agent for the Web server farm and the exposure factor for a power failure is 25%, the SLE for this event equals $5,000.

The ALE is the expected risk factor of an annual threat event. To determine the ALE, you must know the SLE and the annualized rate of occurrence (ARO). The ARO is the estimate of how often a given threat might occur annually. The calculation for obtaining the ALE is as follows:
ALE = SLE × ARO
Using the previously mentioned example, if the risk assessment has determined that the ARO for the power failure of the Web server farm is 50%, the ALE for this event equals $2,500.
Using the ALE, the organization can decide whether to implement controls or not. If the annual cost of the control to protect the Web server farm is more than the ALE, the organization could easily choose to accept the risk by not implementing the control. If the annual cost of the control to protect the Web server farm is less than the ALE, the organization should consider implementing the control.
Keep in mind that even though quantitative risk analysis uses numeric value, a purely quantitative analysis cannot be achieved because some level of subjectivity is always part of the data. In our example, how does the organization know that damage from the power failure will be 25% of the asset? This type of estimate should be based on historical data, industry experience, and expert opinion.
An advantage of quantitative over qualitative risk analysis is that quantitative uses less guesswork than qualitative. Disadvantages of quantitative risk analysis include the difficulty of the equations, the time and effort needed to complete the analysis, and the level of data that must be gathered for the analysis.
Qualitative Risk Analysis
Qualitative risk analysis does not assign monetary and numeric values to all facets of the risk analysis process. Qualitative risk analysis techniques include intuition, experience, and best practice techniques, such as brainstorming, focus groups, surveys, questionnaires, meetings, interviews, and Delphi. Although all of these techniques can be used, most organizations will determine the best technique(s) based on the threats to be assessed. Experience and education on the threats are needed.
Each member of the group who has been chosen to participate in the qualitative risk analysis uses his experience to rank the likelihood of each threat and the damage that might result. After each group member ranks the threat possibility, loss potential, and safeguard advantage, data is combined in a report to present to management.
Advantages of qualitative over quantitative risk analysis include qualitative prioritizes the risks and identifies areas for immediate improvement in addressing the threats. Disadvantages of qualitative risk analysis include all results are subjective and a dollar value is not provided for cost-benefit analysis or for budget help.
Note
When performing a risk analysis, all organizations will experience issues with any estimate they obtain. This lack of confidence in an estimate is referred to as uncertainty and is expressed as a percentage. Any reports regarding a risk assessment should include the uncertainty level.
Most risk analysis includes some hybrid use of both quantitative and qualitative risk analysis. Most organizations favor using quantitative risk analysis for tangible assets and qualitative risk analysis for intangible assets.
Safeguard Selection

The most common criteria for choosing a safeguard is the cost effectiveness of the safeguard or control. Planning, designing, implementing, and maintenance costs need to be included in determining the total cost of a safeguard. To calculate a cost-benefit analysis use the following equation:
(ALE before safeguard) – (ALE after safeguard) – (annual cost of safeguard) = safeguard value
To complete this equation, you have to know the revised ALE after the safeguard is implemented. Implementing a safeguard can improve the ARO but will not completely do away with it. In the example mentioned earlier in the “Quantitative Risk Analysis” section, the ALE for the event is $2,500. Let’s assume that implementing the safeguard reduces the ARO to 10%, so the ALE after the safeguard is calculated as: $5,000 × 10% or $500. You could then calculate the safeguard value for a control that costs $1,000 as follows:
$2,500 – $500 – $1,000 = $1,000
Knowing the corrected ARO after the safeguard is implemented is necessary for determining the safeguard value. A legal liability exists if the cost of the safeguard is less than the estimated loss that would occur if the threat is exploited.
Maintenance costs of safeguards are not often fully considered during this process. Organization should fully research the costs of maintaining safeguards. New staff or extensive staff training often must occur to properly maintain a new safeguard. In addition, the cost of the labor involved must be determined. So the cost of a safeguard must include the actual cost to implement plus any training costs, testing costs, labor costs, and so on. Some of these costs might be hard to identify but a thorough risk analysis will account for these costs.
Total Risk versus Residual Risk
Total risk is the risk that an organization could encounter if it decides not to implement any safeguards. As you already know, any environment is never fully secure so you must always deal with residual risk. Residual risk is risk that is left over after safeguards have been implemented. Residual risk is represented using the following equation:
Residual risk = total risk – countermeasures
This equation is considered to be more conceptual than for actual calculation.
Handling Risk

Risk reduction is the process of altering elements of the organization is response to risk analysis. After an organization understands its total and residual risk, it must determine how to handle the risk. The following four basic methods are used to handle risk:
• Risk avoidance: Terminating the activity that causes a risk or choosing an alternative that is not as risky.
• Risk transfer: Passing the risk on to a third party, including insurance companies.
• Risk mitigation: Defining the acceptable risk level the organization can tolerate and reducing the risk to that level.
• Risk acceptance: Understanding and accepting the level of risk as well as the cost of damages that can occur.
Risk Management Principles
After the risk assessment is complete, the organization must manage the risk. This step involves implementing and maintaining the safeguards. In addition, the organization must decide on any future risk analysis that occurs because risk analysis should be carried out on a regular basis. Risk management involves developing and maintaining a risk management policy and maintaining a risk management and risk analysis team.
Risk Management Policy
Senior management must commit to the risk management process. The risk management policy is a formal statement of senior management’s commitment to risk management. The policy also provides risk management direction.
A risk management policy must include the overall risk management plan and list the risk management team and must specifically list the risk management team objectives, responsibilities and roles of the risk management team, acceptable level of risk, risk identification process, risk and safeguards mapping, safeguard effectiveness monitoring process and targets, and future risk analysis plans and tasks.
Risk Management Team
Depending on the size of the organization, the risk management team might be an actual team of employees or might consist only of a single team member. For any organization, the team’s goal is to protect the organization and its assets from risk in the most cost-effective way. Because in most cases the risk management team members are not dedicated solely to risk management, senior management must specifically put a resource allocation measure in place to ensure the success of the risk management process.
Management must also ensure that the members of the risk management team, particularly the team leader, be given the necessary training and tools for risk management. In larger organizations, the team leader should be able to dedicate the majority of his time to the risk management process.
Risk Analysis Team
To perform the most comprehensive risk analysis, the risk analysis team must consist of a representative from as many departments and as many employment levels as possible. Having a diverse risk analysis team ensures that risks from all areas of the organization can be determined.
If the risk analysis team cannot contain members from all departments, the members must interview each department to understand all the threats encountered by that department. During the risk analysis process, the risk analysis team should determine the threat events that could occur, the potential impact of the threats, the frequency of the threats, and the level of confidence in the information gathered.
Information Security Governance Components
Within an organization, information security governance consists of several components that are used to provide comprehensive security management. Data and other assets should be protected mainly based on their value and sensitivity. Strategic plans guide the long-term security activities (3–5 years or more). Tactical plans achieve the goals of the strategic plan and are shorter in length (6–18 months).
Because management is the most critical link in the computer security chain, management approval must be obtained as part of the first step in forming and adopting an information security policy. Senior management must complete the following steps prior to the development of any organizational security policy:
• Define the scope of the security program.
• Identify all the assets that need protection.
• Determine the level of protection that each asset needs.
• Determine personnel responsibilities.
• Develop consequences for noncompliance with the security policy.
By fully endorsing an organizational security policy, senior management accepts the ownership of an organization’s security. High-level polices are statements that indicate senior management’s intention to support security.
After senior management approval has been obtained, the first step in establishing an information security program is to adopt an organizational information security statement. The organization’s security policy comes from this organizational information security statement. The security planning process must define how security will be managed, who will be responsible for setting up and monitoring compliance, how security measures will be tested for effectiveness, who is involved in establishing the security policy, and where the security policy is defined.

Security professionals must understand how information security components work together to form a comprehensive security plan. Information security governance components include:
• Policies
• Information classification and life cycle
Policies
A security policy dictates the role of security as provided by senior management and is strategic in nature, meaning it provides the end result of security. Policies are defined in two ways: the level in the organization at which they are enforced and the category to which they are applied. Policies must be general in nature, meaning they are independent of a specific technology or security solution. Policies outline goals but do not give any specific ways to accomplish the stated goals. All policies must contain an exception area to ensure that management will be able to deal with situations that might require exceptions.
Policies are broad and provide the foundation for development of standards, baselines, guidelines, and procedures, all of which provide the security structure. Administrative, technical, and physical access controls fill in the security structure complete the security program.
The policy levels used in information security are organizational security policies, system-specific security policies, and issue-specific security policies. The policy categories used in information security are regulatory security policies, advisory security policies, and informative security policies. The policies are divided as shown in Figure 4-7.
Figure 4-7. Levels and Categories of Security Policies

Organizational Security Policy
An organizational security policy is the highest level security policy adopted by an organization. Business goals steer the organizational security policy. An organizational security policy contains general directions and should have the following components:
• Define overall goals of security policy.
• Define overall steps and importance of security.
• Define security framework to meet business goals.
• State management approval of policy, including support of security goals and principles.
• Define all relevant terms.
• Define security roles and responsibilities.
• Address all relevant laws and regulations.
• Identify major functional areas.
• Define compliance requirements and noncompliance consequences.
An organizational security policy must be supported by all stakeholders and should have high visibility for all personnel and be discussed regularly. In addition, it should be reviewed on a regular basis and revised based on the findings of the regular review. Each version of the policy should be maintained and documented with each new release.
System-specific Security Policy
A system-specific security policy addresses security for a specific computer, network, technology, or application. This policy type is much more technically focused than an issue-specific security policy. It outlines how to protect the system or technology.
Issue-specific Security Policy
An issue-specific security policy addresses specific security issues. Issue-specific policies include e-mail privacy policies, virus checking policies, employee termination policies, no expectation of privacy policies, and so on. Issue-specific policies support the organizational security policy.
Policy Categories
Regulatory security policies address specific industry regulations, including mandatory standards. Examples of industries that must consider regulatory security policies include healthcare facilities, public utilities, and financial institutions.
Advisory security policies provide instruction on acceptable and unacceptable activities. In most cases, this policy is considered to be strongly suggested, not compulsory. This type of policy usually gives examples of possible consequences if users engage in unacceptable activities.
Informative security policies provide information on certain topics and act as an educational tool.
Standards
Standards describe how policies will be implemented within an organization. They are mandatory actions or rules that are tactical in nature, meaning they provide the steps necessary to achieve security. Just like policies, standards should be regularly reviewed and revised.
Baselines
A baseline is a reference point that is defined and captured to be used as a future reference. Although capturing baselines is important, using those baselines to assess the security state is just as important. Even the most comprehensive baselines are useless if they are never used.
Capturing a baseline at the appropriate point in time is also important. Baselines should be captured when a system is properly configured and fully updated. When updates occur, new baselines should be captured and compared to the previous baselines. At that time, adopting new baselines based on the most recent data might be necessary.
Guidelines
Guidelines are recommended actions that are much more flexible than standards, thereby providing allowance for circumstances that can occur. Guidelines provide guidance when standards do not apply.
Procedures
Procedures embody all the detailed actions that personnel are required to follow and are the closest to the computers and other devices. Procedures often include step-by-step lists on how policies, standards, and guidelines are implemented.
Information Classification and Life Cycle
Data should be classified based on its value to the organization and its sensitivity to disclosure. Assigning a value to data allows an organization to determine the resources that should be used to protect the data. Resources that are used to protect data include personnel resources, monetary resources, access control resources, and so on. Classifying data allows you to apply different protective measures. Data classification is critical to all systems to protect the confidentiality, integrity, and availability (CIA) of data.
After data is classified, the data can be segmented based on its level of protection needed. The classification levels ensure that data is handled and protected in the most cost-effective manner possible. An organization should determine the classification levels it uses based on the needs of the organization. A number of commercial business and military and government information classifications are commonly used.
The information life cycle should also be based on the classification of the data. Organizations are required to retain certain information, particularly financial data, based on local, state, or government laws and regulations.
Commercial Business Classifications

Commercial businesses usually classify data using four main classification levels, listed from highest sensitivity level to lowest:
1. Confidential
2. Private
3. Sensitive
4. Public
Data that is confidential includes trade secrets, intellectual data, application programming code, and other data that could seriously affect the organization if unauthorized disclosure occurred. Data at this level would only be available to personnel in the organization whose work relates to the data’s subject. Access to confidential data usually requires authorization for each access. Confidential data is exempt from disclosure under the Freedom of Information Act. In most cases, the only way for external entities to have authorized access to confidential data is as follows:
• After signing a confidentiality agreement
• When complying with a court order
• As part of a government project or contract procurement agreement
Data that is private includes any information related to personnel, including human resources records, medical records, and salary information, that is only used within the organization. Data that is sensitive includes organizational financial information and requires extra measures to ensure its CIA and accuracy. Public data is data that would not cause a negative impact on the organization.
Military and Government Classifications

Military and governmental entities usually classify data using five main classification levels, listed from highest sensitivity level to lowest:
1. Top Secret
2. Secret
3. Confidential
4. Sensitive but unclassified
5. Unclassified
Data that is top secret includes weapon blueprints, technology specifications, spy satellite information, and other military information that could gravely damage national security if disclosed. Data that is secret includes deployment plans, missile placement, and other information that could seriously damage national security if disclosed. Data that is confidential includes patents, trade secrets, and other information that could seriously affect the government if unauthorized disclosure occurred. Data that is sensitive but unclassified includes medical or other personal data that might not cause serious damage to national security but could cause citizens to question the reputation of the government. Military and government information that does not fall into any of the other four categories is considered unclassified and usually has to granted to the public based on the Freedom of Information Act.
Information Life Cycle
All organizations need procedures in place for the retention and destruction of data. Data retention and destruction must follow all local, state, and government regulations and laws. Documenting proper procedures ensures that information is maintained for the required time to prevent financial fines and possible incarceration of high-level organizational officers. These procedures must include both retention period and destruction process.
Security Governance Responsibilities and Roles
Although all organizations have layers of responsibility within the organization, computer security is generally considered the responsibility of everyone in the organization. This section covers the responsibilities of the different roles within an organization.
Board of Directors
An organization’s board of directors includes individuals who are elected by shareholders to ensure that the organization is run properly. The loyalty of the board of directors should be to the shareholders, not high-level management. Members of the board of directors should maintain their independence from all organizational personnel, especially if the Sarbanes-Oxley (SOX) Act or Gramm-Leach-Bliley Act (GLBA) applies to the organization.
Note
All laws that are pertinent to the CISSP exam are discussed in Chapter 10, “Legal, Regulations, Investigations, and Compliance.” Keep in mind that for testing purposes security professionals only need to understand the types of organizations and data that these laws affect.
Senior officials, including the board of directors and senior management, must perform their duties with the care that ordinary, prudent people would exercise in similar circumstances. This is known as the prudent-man rule. Due care and due diligence, discussed earlier in this chapter, also affect members of the board of directors and high-level management.
Management
High-level management has the ultimate responsibility for preserving and protecting organizational data. High-level management includes the CEO, CFO, CIO, CPO, and CSO. Other management levels, including business unit managers and business operations managers, have security responsibilities as well.
The chief executive officer (CEO) is the highest managing officer in any organization and reports directly to the shareholders. The CEO must ensure that an organization grows and prospers.
The chief financial officer (CFO) is the officer responsible for all financial aspects of an organization. Although structurally the CFO might report directly to the CEO, the CFO must also provide financial data for the shareholders and government entities.
The chief information officer (CIO) is the officer responsible for all information systems and technology used in the organization and reports directly to the CEO or CFO. The CIO usually drives the effort to protect company assets, including any organizational security program.
The chief privacy officer (CPO) is the officer responsible for private information and usually reports directly to the CIO. As a newer position, this role is still considered optional but is becoming increasingly popular, especially in organizations that handle lots of private information, including medical institutions, insurance companies, and financial institutions.
The chief security officer (CSO) is the officer that leads any security effort and reports directly to the CEO. Although this role is considered optional, this role must solely be focused on security matters. Its independence from all other roles must be maintained to ensure that the organization’s security is always the focus of the CSO.
Business unit managers provide departmental information to ensure that appropriate controls are in place for departmental data. Often business unit managers are classified as the data owner for all departmental data. Some business unit managers have security duties. For example, the business operations department manager would be best suited to oversee the security policy development.
Audit Committee
An audit committee evaluates an organization’s financial reporting mechanism to ensure that financial data is accurate. This committee performs an internal audit and engages independent auditors as needed. Members of this committee must obtain appropriate education on a regular basis to ensure that they can oversee financial reporting and enforce accountability in the financial processes.
Data Owner
The main responsibility of the data or information owner is to determine the classification level of the information he owns and to protect the data for which he is responsible. This role approves or denies access rights to the data. However, the data owner usually does not handle the implementation of the data access controls.
The data owner role is usually filled by an individual who understands the data best through membership in particular business unit. Each business unit should have a data owner. For example, a human resources department employee better understands the human resources data than an accounting department employee.
Data Custodian
The data custodian implements the information classification and controls after they are determined by the data owner. Although the data owner is usually an individual who understands the data, the data custodian does not need any knowledge of the data beyond its classification levels. Although a human resources manager should be the data owner for the human resources data, an IT department member could act as the data custodian for the data.
System Owner
A system owner owns one or more systems and must ensure that the appropriate controls are in place on those systems. Although a system has a single system owner, multiple data owners can be responsible for the information on the system. Therefore, system owners must be able to manage the needs of multiple data owners and implement the appropriate procedures to ensure that the data is secured.
System Administrator
A system administrator performs the day-to-day administration of one or more systems. These day-to-day duties include adding and removing system users and installing system software.
Security Administrator
A security administrator maintains security devices and software, including firewalls, antivirus software, and so on. The main focus of the security administrator is security, whereas the main focus of a system administrator is the system availability and the main focus of the network administrator is network availability. The security administrator reviews all security audit data.
Security Analyst
A security analyst analyzes the security needs of the organization and develops the internal information security governance documents, including policies, standards, and guidelines. The role focuses on the design of security, not its implementation.
Application Owner
An application owner determines the personnel who can access an application. Because most applications are owned by a single department, business department managers usually fill this role. However, the application owner does not necessarily perform the day-to-day administration of the application. This responsibility can be delegated to a member of the IT staff because of the technical skills needed.
Supervisor
A supervisor manages a group of users and any assets owned by this group. Supervisors must immediately communicate any personnel role changes that affect security to the security administrator.
User
A user is any person who accesses data to perform their job duties. Users should understand any security procedures and policies for the data to which they have access. Supervisors are responsible for ensuring that users have the appropriate access rights.
Auditor
An auditor monitors user activities to ensure that the appropriate controls are in place. Auditors need access to all audit and event logs to verify compliance with security policies. Both internal and external auditors can be used.
Third-Party Governance
For many organizations, a third party ensures that an organization complies with industry or governmental standards and regulations. This third party performs analysis of organizational operations and any other area dictated by the certifying or regulating organization. The third party reports all results of its findings to the certifying or regulating organization. The contract with the third party should stipulate that any findings or results should only be communicated with the organization that is being analyzed and with the regulating organization.
A member of high-level management usually manages this process so that the third party is given access as needed. As part of this analysis, the third party might need to perform an onsite assessment, a document exchange, or a process/policy review.
Onsite Assessment
An onsite assessment involves a team from the third party. This team needs access to all aspects of the organization under regulation. This assessment might include observing employees performing their day-to-day duties, reviewing records, reviewing documentation, and other tasks. Management should delegate a member of management to which the team can make formal requests.
Document Exchange/Review
A document exchange/review involves transmitting a set of documents to the third party. The process used for the document exchange must be secure on both ends of the exchange.
Process/Policy Review
A process/policy review focuses on a single process or policy within the organization and ensures that the process or policy follows regulations.
Personnel Security (Screening, Hiring, and Termination)
Personnel are responsible for the vast majority of security issues within an organization. For this reason, it is vital that an organization implement the appropriate personnel security policies. Organizations should have personnel security policies in place that includes screening, hiring, and termination policies.
Personnel screening should occur prior to the offer of employment and might include a criminal background check, work history, background investigations, credit history, driving records, substance-abuse testing, and education and licensing verification. Each organization should determine the screening needs based on the organization’s needs and the perspective personnel’s employment level.
Personnel hiring procedures should include signing all the appropriate documents, including government-required documentation, no expectation of privacy statements, and non-disclosure agreements (NDAs). Organizations usually have a personnel handbook and other hiring information that must be communicated to the employee. The hiring process should include a formal verification that the employee has completed all the training. Employee IDs and passwords are issued at this time.
Personnel termination must be handled differently based on whether the termination is friendly or unfriendly. Procedures defined by the human resources department can ensure that the organizational property is returned, user access is removed at the appropriate time, and exit interviews are completed. With unfriendly terminations, organizational procedures must be proactive to prevent damage to organizational assets. Therefore, unfriendly termination procedures should include system and facility access termination prior to employee termination notification as well as security escort from the premises.
Management must also ensure that appropriate security policies are in place during employment. Separation of duties and job rotation was covered earlier in this chapter. Another management control is mandatory vacations, which requires that employees taken their vacations and that another employee performs their job duties during that vacation time. Some positions might require employment agreements to protect the organization and its assets even after the employee is no longer with the organization. These agreements can include NDAs, non-compete clauses, and code of conduct and ethics agreements.
Security Awareness Training
Security awareness training, security training, and security education are three terms that are often used interchangeably but they are actually three different things. Awareness training reinforces the fact that valuable resources must be protected by implementing security measures. Security training teaches personnel the skills to enable them to perform their jobs in a secure manner. Awareness training and security training are usually combined as security awareness training, which improves user awareness of security and ensures that users can be held accountable for their actions. Security education is more independent and is targeted at security professionals who require security expertise to act as in-house experts for managing the security programs. Awareness training is the what, security training is the how, and security education is the why.
Security awareness training should be developed based on the audience. In addition, trainers must understand the corporate culture and how it will affect security. The audiences you need to consider when designing training include high-level management, middle management, technical personnel, and regular staff.
For high-level management, the security awareness training must provide a clear understanding of potential risks and threats, effects of security issues on organizational reputation and financial standing, and any applicable laws and regulations that pertain to the organization’s security program. Middle management training should discuss policies, standards, baselines, guidelines, and procedures, particularly how these components map to the individual departments. Also middle management must understand their responsibilities regarding security. Technical staff should receive technical training on configuring and maintaining security controls, including how to recognize an attack when it occurs. In addition, technical staff should be encouraged to pursue industry certifications and higher education degrees. Regular staff needs to understand their responsibilities regarding security so that they perform their day-to-day tasks in a secure manner. With regular staff, providing real-world examples to emphasize proper security procedures is effective.
Personnel should sign a document that indicates they have completed the training and understand all the topics. Although the initial training should occur when personnel is hired, security awareness training should be considered a continuous process, with future training sessions occurring annually at a minimum.
Security Budget, Metrics, and Effectiveness
The CSO or other designated high-level manager prepares the organization’s security budget, determines the security metrics, and reports on the effectiveness of the security program. This officer must work with other subject matter experts (SMEs) to ensure that all security costs are accounted for, including development, testing, implementation, maintenance, personnel, and equipment. The budgeting process requires an examination of all risks and ensures that security projects with this best cost-benefit ratio are implemented. Project that take longer than 12–18 months are long-term and strategic and require more resources and funding to complete.
Security metrics provide information on both short- and long-term trends. By collecting these metrics and comparing them on a day-to-day basis, a security professional can determine the daily workload. When the metrics are compared over a longer period of time, the trends that occur can help to shape future security projects and budgets. Procedures should state who will collect the metrics, which metrics will be collected, when the metrics will be collected, and what the thresholds are that will trigger corrective actions. Security professionals should consult with the information security governance frameworks listed earlier in this chapter, particularly ISO/IEC 27004 and NIST 800-55, for help in establishing metrics guidelines and procedures.
Although the security team should analyze metrics on a daily basis, periodic analysis of the metrics by a third party can ensure the integrity and effectiveness of the security metrics by verifying the results of the internal team. Data from the third-party should be used to improve the security program and security metrics process.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 4-5 lists a reference of these key topics and the page numbers on which each is found.
Table 4-5. Key Topics for Chapter 4
Complete the Tables and Lists from Memory
Print a copy of CD Appendix A, “Memory Tables,” or at least the section for this chapter, and complete the tables and lists from memory. Appendix B, “Memory Tables Answer Key,” includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
risk management
confidentiality
integrity
availability
vulnerability
threat
threat agent
risk
exposure
countermeasure
safeguard
due care
due diligence
job rotation
separation of duties
split knowledge
dual control
tangible assets
intangible assets
quantitative risk analysis
qualitative risk analysis
SLE
AV
EF
ALE
ARO
total risk
residual risk
risk avoidance
risk transfer
risk mitigation
risk acceptance
strategic plans
tactical plans
policy
organizational security policy
system-specific security policy
issue-specific security policy
regulatory security policy
advisory security policy
informative security policy
standard
baseline
guideline
procedure.
Review Questions
1. What is a vulnerability?
a. the entity that carries out a threat
b. when an organizational asset is exposed to losses
c. an absence or weakness of a countermeasure that is in place
d. a control that reduces risk
2. Which ISO/IEC standard gives an overview and vocabulary of information security management?
a. ISO/IEC 27000
b. ISO/IEC 27001
c. ISO/IEC 27002
d. ISO/IEC 27003
3. Which framework uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual)?
a. Six Sigma
b. SABSA
c. ITIL
d. ISO/IEC 27000 series
4. What is the first stage of the security program life cycle?
a. Plan and Organize
b. Implement
c. Operate and Maintain
d. Monitor and Evaluate
5. Which group of threat agents includes hardware and software failure, malicious code, and new technologies?
a. human
b. natural
c. environmental
d. technical
6. Which term indicates the monetary impact of each threat occurrence?
a. ARO
b. ALE
c. EF
d. SLE
7. What is risk avoidance?
a. risk that is left over after safeguards have been implemented
b. terminating the activity that causes a risk or choosing an alternative that is not as risky
c. passing the risk on to a third party
d. defining the acceptable risk level the organization can tolerate and reducing the risk to that level
8. Which security policies provide instruction on acceptable and unacceptable activities?
a. informative security policies
b. regulatory security policies
c. system-specific security policies
d. advisory security policies
9. What is the highest military security level?
a. Confidential
b. Top Secret
c. Private
d. Sensitive
10. Which organization role determines the classification level of the information to protect the data for which he is responsible?
a. data owner
b. data custodian
c. security administrator
d. security analyst
Answers and Explanations
1. c. A vulnerability is an absence or weakness of a countermeasure that is in place. A threat occurs when a vulnerability is identified or exploited. A threat agent is the entity that carries out a threat. Exposure occurs when an organizational asset is exposed to losses. A countermeasure or safeguard is a control that reduces risk.
2. a. The ISO/IEC 27000 standard gives an overview and vocabulary of information security management. The ISO/IEC 27001 standard lists information security requirements. The ISO/IEC 27002 standard gives the code of practice for information security management. The ISO/IEC 27003 standard gives implementation guidelines for information security management.
3. b. SABSA uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). Six Sigma is a process improvement standard that includes two project methodologies that were inspired by Deming’s Plan/Do/Check/Act cycle. ITIL is a process management development standard that has five core publications: ITIL Service Strategy, ITIL Service Design, ITIL Service Transition, ITIL Service Operation, and ITIL Continual Service Improvement. ISO/IEC 27000 series includes a list of standards, each of which addresses a particular aspect of information security management.
4. a. The four stages of the security program life cycle, in order, are as follows:
1. Plan and Organization
2. Implement
3. Operate and Maintain
4. Monitor and Evaluate
5. d. Technical threat agents include hardware and software failure, malicious code, and new technologies. Human threat agents include both malicious and non-malicious insiders and outsiders, terrorists, spies, and terminated personnel. Natural threat agents include floods, fires, tornadoes, hurricanes, earthquakes, or other natural disaster or weather event. Environmental threat agents include power and other utility failure, traffic issues, biological warfare, and hazardous material issues (such as spillage).
6. d. SLE indicates the monetary impact of each threat occurrence. ARO is the estimate of how often a given threat might occur annually. ALE is the expected risk factor of an annual threat event. EF is the percent value or functionality of as asset that will be lost when a threat event occurs.
7. b. Risk avoidance is terminating the activity that causes a risk or choosing an alternative that is not as risky. Residual risk is risk that is left over after safeguards have been implemented. Risk transfer is passing the risk on to a third party. Risk mitigation is defining the acceptable risk level the organization can tolerate and reducing the risk to that level.
8. d. Advisory security policies provide instruction on acceptable and unacceptable activities. Informative security policies provide information on certain topics and act as an educational tool. Regulatory security policies address specific industry regulations, including mandatory standards. System-specific security policies address security for a specific computer, network, technology, or application.
9. b. Military and governmental entities classify data using five main classification levels, listed from highest sensitivity level to lowest:
Top Secret
Secret
Confidential
Sensitive but unclassified
Unclassified
Commercial businesses classify data using four main classification levels, listed from highest sensitivity level to lowest:
Confidential
Private
Sensitive
Public
10. a. The data owner determines the classification level of the information to protect the data for which he is responsible. The data custodian implements the information classification and controls after they are determined. The security administrator maintains security devices and software. The security analyst analyzes the security needs of the organizations and develops the internal information security governance documents.
