Appendix B. Memory Table Answer Key
Chapter 2
Authentication methods are divided into three broad categories:
• Knowledge factor authentication: Something a person knows
• Ownership factor authentication: Something a person has or possesses
• Characteristic factor authentication: Something a person is
The types of passwords that you should be familiar with include:
• Standard word or simple passwords: As the name implies, these passwords consist of single words that often include a mixture of upper- and lowercase letters. The advantage of this password type is that it is easy to remember. A disadvantage of this password type is that it is easy for attackers to crack or break, resulting in a compromised account.
• Combination passwords: This password type uses a mix of dictionary words, usually two unrelated words. These are also referred to as composition passwords. Like standard word passwords, they can include upper- and lowercase letters and numbers. An advantage of this password is that it is harder to break than simple passwords. A disadvantage is that it can be hard to remember.
• Static passwords: This password type is the same for each login. It provides a minimum level of security because the password never changes. It is most often seen in peer-to-peer networks.
• Complex passwords: This password type forces a user to include a mixture of upper- and lowercase letters, numbers, and special characters. For many organizations today, this type of password is enforced as part of the organization’s password policy. An advantage of this password type is that it is very hard to crack. A disadvantage is that it is harder to remember and can often be much harder to enter correctly than standard or combination passwords.
• Passphrase passwords: This password type requires that a long phrase be used. Because of the password’s length, it is easier to remember but much harder to attack, both of which are definite advantages. Incorporating upper- and lowercase letters, numbers, and special characters in this type of password can significantly increase authentication security.
• Cognitive passwords: This password type is a piece of information that can be used to verify an individual’s identity. This information is provided to the system by answering a series of questions based on the user’s life, such as favorite color, pet’s name, mother’s maiden name, and so on. An advantage to this type is that users can usually easily remember this information. The disadvantage is that someone who has intimate knowledge of the person’s life (spouse, child, sibling, and so on) might be able to provide this information as well.
• One-time passwords: Also called a dynamic password, this type of password is only used once to log in to the access control system. This password type provides the highest level of security because passwords are discarded when they are used.
• Graphical passwords: Also called CAPTCHA passwords, this type of password uses graphics as part of the authentication mechanism. One popular implementation requires a user to enter a series of characters in the graphic displayed. This implementation ensures that a human is entering the password, not a robot. Another popular implementation requires the user to select the appropriate graphic for his account from a list of graphics given.
• Numeric passwords: This type of password includes only numbers. Keep in mind that the choices of a password are limited by the number of digits allowed. For example, if all passwords are 4 digits, then the maximum number of password possibilities is 10,000, from 0000 through 9999. After an attacker realized that only numbers are used, cracking user passwords would be much easier because the possibilities would be known.
Password management considerations include, but might not be limited to
• Password life: How long the password will be valid. For most organization, passwords are valid for 60 to 90 days.
• Password history: How long before a password can be reused. Password policies usually remember a certain number of previously used passwords.
• Authentication period: How long a user can remain logged in. If a user remains logged in for the period without activity, the user will be automatically logged out.
• Password complexity: How the password will be structured. Most organizations require upper- and lowercase letters, numbers, and special characters.
• Password length: How long the password must be. Most organization require 8–12 characters.
When considering biometric technologies, security professionals should understand the following terms:
• Enrollment time: The process of obtaining the sample that is used by the biometric system. This process requires actions that must be repeated several times.
• Feature extraction: The approach to obtaining biometric information from a collected sample of a user’s physiological or behavioral characteristics.
• Accuracy: The most important characteristic of biometric systems. It is how correct the overall readings will be.
• Throughput rate: The rate at which the biometric system will be able to scan characteristics and complete the analysis to permit or deny access. The acceptable rate is 6–10 subjects per minute. A single user should be able to complete the process in 5–10 seconds.
• Acceptability: Describes the likelihood that users will accept and follow the system
• False rejection rate (FRR): A measurement of valid users that will be falsely rejected by the system. This is called a Type I error.
• False acceptance rate (FAR): A measurement of the percentage of invalid users that will be falsely accepted by the system. This is called a Type II error. Type II errors are more dangerous than Type I errors.
• Crossover error rate (CER): The point at which FRR equals FAR. Expressed as a percentage, this is the most important metric.
Table 2-1. Administrative (Management) Controls

Table 2-2. Logical (Technical) Controls
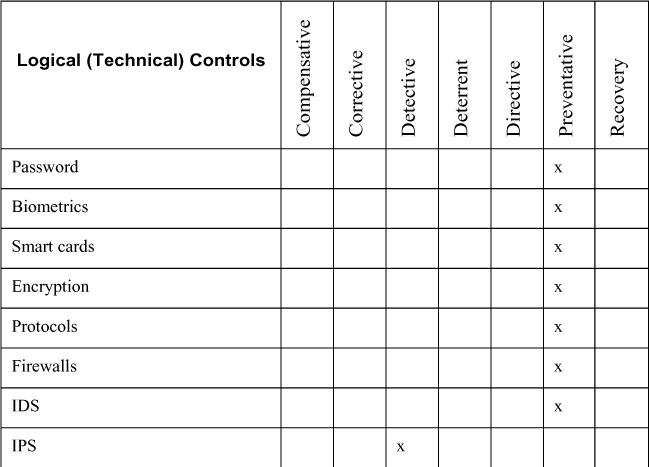
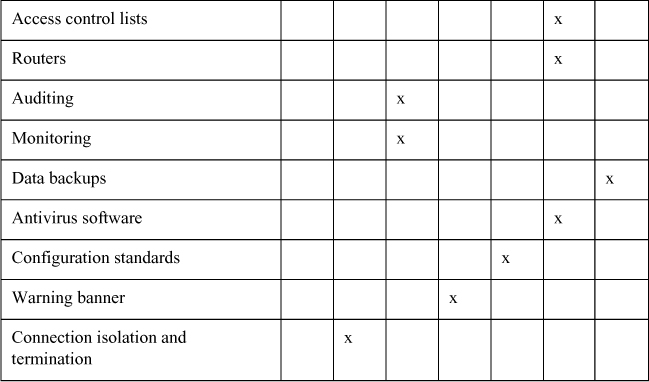

IDS implementations are furthered divided into the following categories:
Signature-based: This type of IDS analyzes traffic and compares it to attack or state patterns, called signatures that reside within the IDS database. It is also referred to as a misuse-detection system. Although this type of IDS is very popular, it can only recognize attacks as compared with its database and is only as effective as the signatures provided. Frequent updates are necessary. The two main types of signature-based IDSs are
Pattern-matching: The IDS compares traffic to a database of attack patterns. The IDS carries out specific steps when it detects traffic that matches an attack pattern.
Stateful-matching: The IDS records the initial operating system state. Any changes to the system state that specifically violate the defined rules result in an alert or notification being sent.
Anomaly-based: This type of IDS analyzes traffic and compares it to normal traffic to determine whether said traffic is a threat. It is also referred to as a behavior-based or profile-based system. The problem with this type of system is that any traffic outside of expected norms is reported, resulting in more false positives than signature-based systems. The three main types of anomaly-based IDSs are
The IDS samples the live environment to record activities. The longer the IDS is in operation, the more accurate a profile that will be built. However, developing a profile that will not have a large number of false positives can be difficult and time consuming. Thresholds for activity deviations are important in this IDS. Too low a threshold results in false positives, whereas too high a threshold results in false negatives.
Protocol anomaly-based: The IDS has knowledge of the protocols that it will monitor. A profile of normal usage is built and compared to activity.
Traffic anomaly-based: The IDS tracks traffic pattern changes. All future traffic patterns are compared to the sample. Changing the threshold will reduce the number of false positives or negatives. This type of filter is excellent for detecting unknown attacks, but user activity might not be static enough to effectively implement this system.
Rule- or heuristic-based: This type of IDS is an expert system that uses a knowledge base, inference engine, and rule-based programming. The knowledge is configured as rules. The data and traffic is analyzed, and the rules are applied to the analyzed traffic. The inference engine uses its intelligent software to “learn.” If characteristics of an attack are met, alerts or notifications trigger. This is often referred to as an IF/THEN or expert system.
The following are the four classes of malware you should understand:
• Virus: Any malware that attaches itself to another application to replicate or distribute itself.
• Worm: Any malware that replicates itself, meaning that it does not need another application or human interaction to propagate.
• Trojan horse: Any malware that disguises itself as a needed application while carrying out malicious actions.
• Spyware: Any malware that collects private user data, including browsing history or keyboard input.
Chapter 4
Table 4-1. Zachman Framework Matrix with Examples

Table 4-2. SABSA Framework Matrix
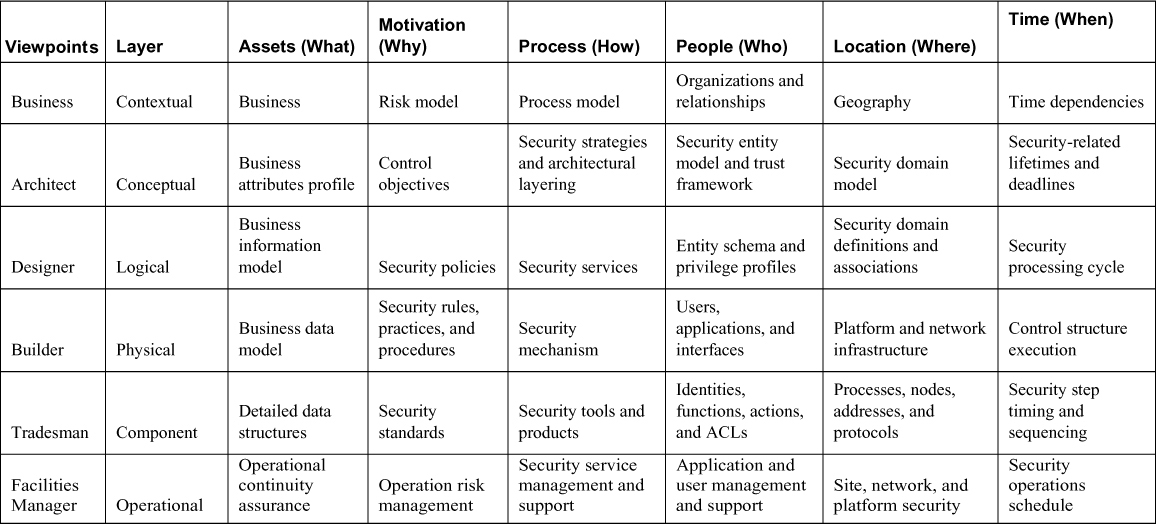
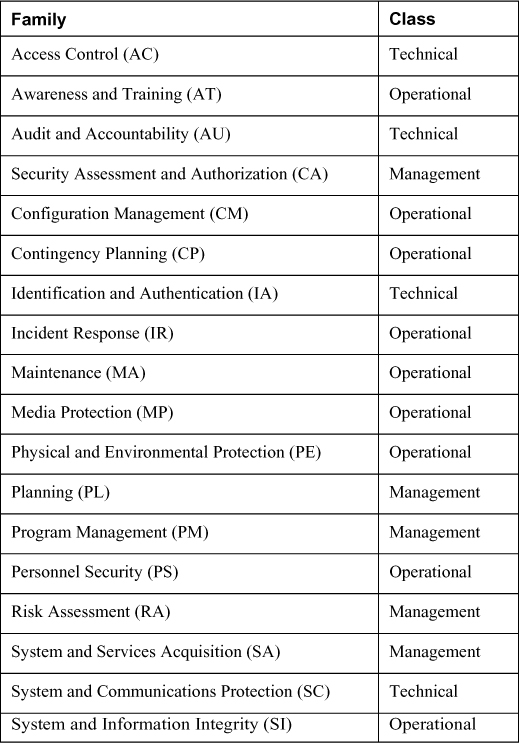
Table 4-3. NIST SP 800-53 Control Families
Chapter 5
When working with relational database management systems, you should understand the following terms:
• Relation: Fundamental entity in a relational database in the form of a table.
• Tuple: A row in a table.
• Attribute: A column in a table.
• Schema: Description of a relational database.
• Record: Collection of related data items.
• Base relation: In SQL, a relation that is actually existent in the database.
• View: The set of data available to a given user. Security is enforced through the use of these.
• Degree: The number of columns in a table.
• Cardinality: The number of rows in a relation.
• Domain: The set of allowable values that an attribute can take.
• Primary key: Columns that make each row unique.
• Foreign key: An attribute in one relation that has values matching the primary key in another relation. Matches between the foreign key to the primary key are important because they represent references from one relation to another and establish the connection among these relations.
• Candidate key: An attribute in one relation that has values matching the primary key in another relation.
• Referential integrity: Requires that for any foreign key attribute, the referenced relation must have a tuple with the same value for its primary key.
The following list shows virus types along with a brief description of each.
• Boot sector: These infect the boot sector of a computer and either overwrite files or install code into the sector so the virus initiates at startup.
• Parasitic: This virus attaches itself to a file, usually an executable file, and then delivers the payload when the program is used.
• Stealth: This virus hides the modifications that it is making to the system to help avoid detection.
• Polymorphic: This virus makes copies of itself, and then makes changes to those copies. It does this in hopes of avoiding detection from antivirus software.
• Macro: These infect programs written in Word, Basic, Visual Basic, or VBScript that are used to automate functions. These viruses infect Microsoft office files. They are easy to create because the underlying language is simple and intuitive to apply. They are especially dangerous in that they infect the operating system itself. They also can be transported between different operating systems because the languages are platform independent.
• Multipartite: These viruses can infect both program files and boot sectors.
Chapter 6
• Encryption: The process of converting data from plaintext to ciphertext. Also referred to as enciphering.
• Decryption: The process of converting data from ciphertext to plaintext. Also referred to as deciphering.
• Key: A parameter that controls the transformation of plaintext into ciphertext or vice versa. Determining the original plaintext data without the key is impossible. Keys may be both public and private. Also referred to as a cryptovariable.
• Synchronous: When encryption or decryption occurs immediately.
• Asynchronous: When encryption or decryption requests are processed from a queue. This method utilizes hardware and multiple processors in the process.
• Symmetric: An encryption method whereby a single private key both encrypts and decrypts the data. Also referred to as private or secret key encryption.
• Asymmetric: An encryption method whereby a key pair, one private key and one public key, performs encryption and decryption. One key performs the encryption, whereas the other key performs the decryption. Also referred to as public key encryption.
• Digital signature: A method of providing sender authentication and message integrity. The message acts an input to a hash function, and the sender’s private key encrypts the hash value. The receiver can perform a hash computation on the received message to determine the validity of the message.
• Hash: A one-way function that reduces a message to a hash value. A comparison of the sender’s hash value to the receiver’s hash value determines message integrity. If the resultant hash values are different, then the message has been altered in some way, provided that both the sender and receiver used the same hash function.
• Digital certificate: An electronic document that identifies the certificate holder.
• Plaintext: A message in its original format. Also referred to as cleartext.
• Ciphertext: An altered form of a message that is unreadable without knowing the key and the encryption system used. Also referred to as a cryptogram.
• Cryptosystem: The entire cryptographic process, including the algorithm, key, and key management functions. The security of a cryptosystem is measured by the size of the keyspace and available computational power.
• Cryptanalysis: The science of decrypting ciphertext without prior knowledge of the key or cryptosystem used. The purpose of cryptanalysis is to forge coded signals or messages that will be accepted as authentic signals or messages.
• Key clustering: Occurs when different encryption keys generate the same ciphertext from the same plaintext message.
• Keyspace: All the possible key values when using a particular algorithm or other security measure. A 40-bit key would have 240 possible values, whereas a 128-bit key would have 2128 possible values.
• Collision: An event that occurs when a hash function produces the same hash value on different messages.
• Algorithm: A mathematical function that encrypts and decrypts data. Also referred to as a cipher.
• Cryptology: The science that studies encrypted communication and data.
• Encoding: The process of changing data into another form using code.
• Decoding: The process of changing an encoded message back into its original format.
• Transposition: The process of shuffling or reordering the plaintext to hide the original message. Also referred to as permutation. For example, AEEGMSS is a transposed version of MESSAGE.
• Substitution: The process of exchanging one byte in a message for another. For example, ABCCDEB is a substituted version of MESSAGE.
• Confusion: The process of changing a key value during each round of encryption. Confusion is often carried out by substitution. Confusion conceals a statistical connection between the plaintext and ciphertext. Claude Shannon first discussed confusion.
• Diffusion: The process of changing the location of the plaintext within the ciphertext. Diffusion is often carried out using transposition. Claude Shannon first introduced diffusion.
• Avalanche effect: The condition where any change in the key or plaintext, no matter how minor, will significantly change the ciphertext. Horst Feistel first introduced avalanche effect.
• Work factor: The amount of time and resources that would be needed to break the encryption.
• Trapdoor: A secret mechanism that allows the implementation of the reverse function in a one-way function.
• One-way function: A mathematical function that can be more easily performed in one direction than in the other.
Table 6-1. Symmetric Algorithm Strengths and Weaknesses

Table 6-2. Asymmetric Algorithm Strengths and Weaknesses
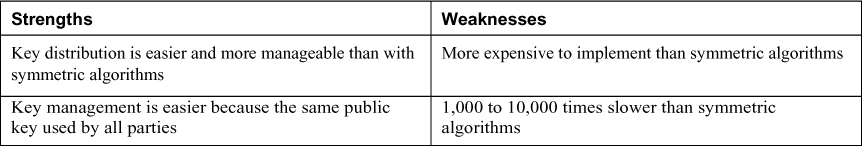
3DES comes in the following four modes:
• 3DES-EEE3: Each block of data is encrypted three times, each time with a different key.
• 3DES-EDE3: Each block of data is encrypted with the first key, decrypted with the second key, and encrypted with the third key.
• 3DES-EEE2: Each block of data is encrypted with the first key, encrypted with the second key, and finally encrypted again with the first key.
• 3DES-EDE2: Each block of data is encrypted with the first key, decrypted with the second key, and finally encrypted again with the first key.

Table 6-3. Symmetric Algorithms Key Facts
Chapter 7
Table 7-2. Security Model Summary
Chapter 8
Chapter 9
The four main steps of the BIA are as follows:
1. Identify critical processes and resources.
2. Identify outage impacts, and estimate downtime.
3. Identify resource requirements.
4. Identify recovery priorities.
As part of determining how critical an asset is, you need to understand the following terms:
• Maximum tolerable downtime (MTD): The maximum amount of time that an organization can tolerate a single resource or function being down. This is also referred to as maximum period time of disruption (MPTD).
• Mean time to repair (MTTR): The average time required to repair a single resource or function when a disaster or disruption occurs.
• Mean time between failure (MTBF): The estimated amount of time a device will operate before a failure occurs. This amount is calculated by the device vendor. System reliability is increased by a higher MTBF and lower MTTR.
• Recovery time objective (RTO): The shortest time period after a disaster or disruptive event within which a resource or function must be restored to avoid unacceptable consequences. RTO assumes that an acceptable period of downtime exists. RTO should be smaller than MTD.
• Work recovery time (WRT): The difference between RTO and MTD, which is the remaining time that is left over after the RTO before reaching the maximum tolerable.
• Recovery point objective (RPO): The point in time to which the disrupted resource or function must be returned.
For the CISSP exam, you should be familiar with the following electronic backup terms and solutions:
• Electronic vaulting: Copies files as modifications occur. This method occurs in real time.
• Remote journaling: Copies the journal or transaction log offsite on a regular schedule. This method occurs in batches.
• Tape vaulting: Creates backups over a direct communication line on a backup system at an offsite facility.
• Hierarchical storage management (HSM): Stores frequently accessed data on faster media and less frequently accessed data on slower media.
• Optical jukebox: Stores data on optical disks and uses robotics to load and unload the optical disks as needed. This method is ideal when 24/7 availability is required.
• Replication: Copies data from one storage location to another. Synchronous replication uses constant data updates to ensure that the locations are close to the same, whereas asynchronous replication delays updates to a predefined schedule.
High-availability terms and techniques that you must understand include the following:
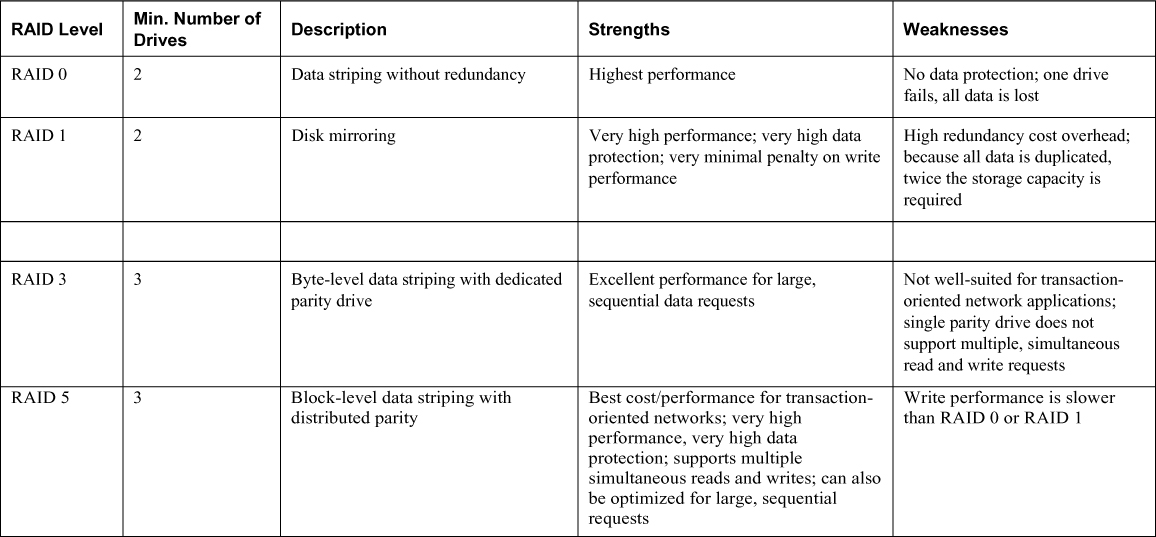
• Redundant Array of Independent Disks (RAID): A hard drive technology in which data is written across multiple disks in such a way that a disk can fail and the data can be quickly made available from remaking disks in the array without restoring a backup tape.
• Storage area network (SAN): High-capacity storage devices that are connected by a high-speed private network using storage-specific switches.
• Failover: The capacity of a system to switch over to a backup system if a failure in the primary system occurs.
• Failsoft: The capability of a system to terminate non-critical processes when a failure occurs.
• Clustering: Refers to a software product that provides load-balancing services. With clustering, one instance of an application server acts as a master controller and distributes requests to multiple instances using round-robin, weighted round-robin or least-connections algorithms.
• Load balancing: Refers to a hardware product that provides load-balancing services. Application delivery controllers (ADCs) support the same algorithms, but also use complex number-crunching processes, such as per-server CPU and memory utilization, fastest response times, and so on, to adjust the balance of the load. Load-balancing solutions are also referred to as farms or pools.
