Chapter 11. Physical (Environmental) Security
This chapter covers the following topics:
• Geographical threats: Covers threats related to geography, including internal, external, natural, man-made, system, and politically motivated.
• Site and facility design: Describes defense models and concepts related to a secure site or facility such as Crime Prevention through Environmental Design (CPTED), layered defense models, physical security plans, and facility selection issues.
• Perimeter security: Discusses the protection of the facility perimeter including gates, fences, perimeter intrusion protection, lighting, patrol forces, and perimeter access control.
• Building and internal security: Surveys important issues inside the facility such as doors, locks, biometrics, glass entries, visitor control, equipment room, and work area protection.
• Environmental security: Topics include fire protection, power supply, HVAC, water leakage and flooding, and the proper use of environmental alarms.
• Equipment security: Discusses proper corporate procedures designed to protect equipment, includes discussion on safes and vaults.
• Personnel privacy and safety: Covers guidelines for maintaining personnel privacy and safety alongside security.
Many of the threats we have discussed are logical in nature; that is, they are attacks that can take place over a network. However, throughout this book the importance of preventing physical access to assets has been emphasized. This chapter undertakes a final and complete treatment of preventing intentional and unintentional damage to facilities, equipment, and people.
Foundation Topics
Geographical Threats
Many threats are a function of the geographic location of the office or facility. This section discusses a wide variety of threats and issues, some of which only apply to certain areas. The security professional must be prepared to anticipate and mitigate those issues.
Internal versus External Threats
When talking about threats to the physical security of assets we can frame the conversation by threats that appear from outside the organization and those that come from within the organization. Many of the mitigation techniques discussed in the following sections are designed to address maintaining perimeter security or access to the building or room, whereas other techniques are designed to address threats from those who might have some access to the room or building.
For example, an electric fence surrounding the facility is designed to prevent access to the building by those who should not have any access (an external threat), whereas a door lock system on the server room that requires a swipe of the employee card is designed to prevent access by those who are already in the building (an internal threat). Keep this in mind as you read the following sections.
Natural Threats
Many of the physical threats that must be addressed and mitigated are caused by the forces of nature. Building all facilities to withstand the strongest hurricanes, tornadoes, and earthquakes is not economically feasible because in many areas these events happen infrequently if ever. What can be done is to make a realistic assessment of the historical weather conditions of an area and perform a prudent cost benefit analysis to determine which threats should be addressed and which should be accepted. This section discusses some of the major natural threats.
Hurricane/Tropical Storm
In certain areas hurricanes and tropical storms are so frequent and unpredictable that all buildings are required to be capable of withstanding the more moderate instances of these storms. In other areas doing that makes no sense even though these storms do occur from time to time. The location of the facility should dictate how much is spent in mitigating possible damages from these events.
Tornadoes
Although events of the last few years might seem to contradict this, over the long haul certain areas are more prone to tornadoes than others as well. A study of the rate and severity of tornadoes in an area from a historical perspective can help to determine measures that make sense for a particular location.
Note
In recent tornado outbreaks, many cell phone towers were knocked out completely. In rural areas especially, communication with loved ones was next to impossible. In the Alabama tornado outbreak in April, 2001, it took many individuals up to 72 hours to locate loved ones because of lack of communications. You can see how this loss of communication would affect a company, school, or even a hospital.
Earthquakes
Earthquakes should be treated in the same way as hurricanes, tropical storms, and tornadoes; that is, the location of the specific facility dictates the amount of preparation and the measures to take to address this risk. For example, facilities in California might give this issue more attention than those in the southeastern United States where these events are extremely rare.
Floods
Always take flooding into consideration because it is an event that can occur with the right circumstances just about anywhere. If at all possible, keep computing systems and equipment off the floor, and build server rooms and wiring closets on raised floors to help prevent damage that could occur in even a small flood.
System Threats
Some of the threats that exist are not from the forces of nature but from failures in systems that provide basic services, such as electricity and utilities. Although these problems can sometimes arise from events of nature, in this section we discuss guidelines for preparing and dealing with these events, which can occur in any location and in any type of weather conditions.
Electrical
Electricity is the lifeline of the organization and especially in regard to computing systems, outages are not only an inconvenience, but they can also damage equipment and cause loss of data. Moreover, when the plug is pulled, to a large degree the enterprise grinds to a halt in today’s world.
For this reason all mission-critical systems should have Uninterruptable Power Supplies (UPS) that can provide power on a short-term basis until the system can be cleanly shut down. In cases where power must be maintained for longer than a matter of minutes, make onsite generators available to provide the power to keep systems running on a longer term basis until power is restored.
Noise, humidity, and brownouts are also issues that affect the electricity supply. The recommended optimal relative humidity range for computer operations is 40% to 60%. Critical systems must be protected from both power sags and surges. Neither is good for equipment. Line conditioners placed between the system and the power source can help to even out these fluctuations and prevent damage.
Finally, the most prevalent cause of computer center fires is electrical distribution systems. Checking these systems regularly can identify problems before they occur.
Communications
Protecting the physical security of communication, such as email, telephone, and fax systems, is a matter of preventing unauthorized access to the physical communication lines (cables and so on) and physical and logical access to equipment used to manage these systems.
For example, in the case of email, the email servers should be locked away and access to them over the network must be tightly controlled with usernames and complex passwords.
In the case of fax machines, implementing policies and procedures can prevent sensitive faxes from becoming available to unauthorized persons. In some cases, preventing certain types of information from being transmitted with faxes might be necessary.
Many phone systems now have been merged into the data network using Voice over IP (VoIP). With these systems, routers and switches might be involved in managing the phone system and should be physically locked away and logically protected from network access in the same fashion as email servers. Because email and VoIP both use the data network, ensure that cabling is not exposed to tampering and malicious destruction.
Some additional considerations that can impact disaster recovery are
• Maintain fault tolerant connections to the Internet, such as when the primary connection is T1 but there is a backup dial-up or satellite connection.
• Establish phone connections to employees besides primary organizational phone connections. Know cell phone and home numbers for employee notification.
• Establish radio communications over the entire campus with repeater antennas to provide communication during emergencies. Many primary forms of communication (such as phone lines and cell phones) can go down.
Note
To learn more about disasters and disaster recovery, refer to Chapter 9, “Business Continuity and Disaster Recovery.”
Utilities
Some utilities systems, such as gas and water, can be routed into the facility through ducts and tunnels that might provide an unauthorized entry point to the building. Such ducts and tunnels that offer this opportunity should be monitored with sensors and access control mechanisms.
Any critical parts of the systems where cut-off valves and emergency shutdown systems are located should be physically protected from malicious tampering. In some cases covering and protecting these valves and controls using locking cages might be beneficial.
Man-Made Threats
Although many of the physical threats we face are a function of natural occurrences and random events, some of them are purposeful. This section explores some of the physical threats faced from malicious and careless humans. These threats come from both external forces and internal forces.
Explosions
Explosions can be both intentional and accidental. Intentional explosions can occur as a result of political motivation (covered in more detail in the section “Politically Motivated Threats”) or they can simply be vandalism. Accidental explosions can be the result of a failure to follow procedures and the failure of physical components.
With regard to intentional explosions, the best defense is to prevent access to areas where explosions could do significant damage to the enterprise’s operational components, such as server rooms, wiring closets, and areas where power and utilities enter the building. When an intentional explosion occurs, typically thought has been given to locating the explosive where the most harm can be done, so those areas should get additional physical protection.
Fire
Fires can happen anywhere and thus are a consideration at all times. Later in this chapter you will learn about both fire suppression and fire detection techniques. Address the threat of fire in the contexts of both an accident and an intentional attack. An auxiliary station alarm might be beneficial in many cases. This mechanism automatically causes an alarm originating in a data center to be transmitted over the local municipal fire or police alarm circuits for relaying to both the local police/fire station and the appropriate headquarters.
Fires can be classified using a standard system as shown in the following list. Later in this chapter we talk about the proper extinguisher or suppression system for each type.


With respect to construction materials, according to (ISC)2, all walls must have a two-hour minimum fire rating in an information processing facility. Knowing that the most prevalent cause of computer center fires is electrical distribution systems is also useful. Regardless of the fire source, the first action to take is evacuating all personnel.
Vandalism
Vandalism in most cases results in defacement of walls, bathrooms, and such, but when critical components are accessible, it can impact operations. Cut cables and smashed devices are reasons stressed in preventing physical access to these components.
Even when all measures have been taken, vandalism can still cause problems. For example, a purposefully plugged toilet can flood a floor and damage equipment if undetected.
Fraud
In the context of physical security, fraud involves gaining access to systems, equipment, or the facility through deception. For example, a person who enters the facility posing as a serviceman or a person who tailgates and follows an employee through the card system are both forms of fraudulent physical access. Physical access control systems become critical to preventing this type of fraud and the damage it can lead to.
Theft
Preventing physical theft of company assets depends on preventing physical access to the facility. Physical theft is the risk that will most likely affect confidentiality, integrity, and availability. For assets that leave the facility, such as laptops, give thought to protecting sensitive data that might exist on them through the use of encryption, preferably through encrypted drives.
Collusion
Collusion occurs when two employees work together to accomplish a theft of some sort that could not be accomplished without their combined knowledge or responsibilities. In several chapters, you have read about using proper separation of duties to prevent a single person from controlling enough of a process to hide their actions.
Limiting the specific accesses of operations personnel forces an operator into collusion with an operator of a different category to have access to unauthorized data. Collusion is much less likely to occur from a statistical standpoint than a single person operating alone. When you consider this fact the tradeoff in exchanging one danger for another is justified.
Politically Motivated Threats
Although it might seem at times like much more politically motivated threats exist today, these threats have always existed. The enterprise is often unwillingly dragged into these confrontations if they are seen as a contributing to whatever the issue of the day might be. These threats can be costly in terms of lost productivity, destruction of company assets, and even physical danger to employees and officers of the company. This section covers some of the major ways these threats can manifest themselves along with measures to take that can lessen or mitigate the risk they present.
Strikes
Although strikes might be the least dangerous of the threats in this list they can still damage the enterprise. In countries like the United States, basic rules of order have been established that prevent the worst of the possible outcomes, but even then an orderly strike can cost productivity and can hurt the image of the company. In other countries strikes can be much more dangerous, especially when other political issues become intertwined with the monetary issues.
Riots
Riots often occur seemingly out of nowhere, although typically an underlying issue explodes at some single incident. These events can be very dangerous as large mobs will often participate in activities that none of the individuals would normally do on their own. Often times the enterprise is seen as a willing participant in some perceived slight or wrong suffered by the rioters. In that case the company and its assets become a large and somewhat easy target.
Civil Disobedience
Civil disobedience is the intentional refusal to obey certain laws, demands, and commands of a government and is commonly, though not always, defined as being nonviolent resistance. One of the typical by-products of this is a disruption of some process to bring attention to the perceived injustice of the law or rule being broken.
It might also manifest itself as an action against some practice by the enterprise that might not be illegal but might be seen by some groups as harmful in some way. When this is the case the physical security of the facility becomes important as in some cases some action might be taken to harm the facility.
Terrorist Acts
Increasingly the threats of terrorist activity have caused a new focus on not only the security of facilities both at home and abroad but also of the physical safety of workers and officers. In many cases certain industries have found it beneficial to include emergency planning designed to address terrorist acts. Reactions to common scenarios are rehearsed to ensure the best possible outcome in the case of an attack.
Bombing
Bombing of facilities or company assets, once a rare occurrence, are no longer so in many parts of the world today. Increasingly the enterprise is driven to include such considerations as local disturbance levels and general political unrest in an area before company sites are chosen. In many cases the simple threat of a bomb is enough to engage evacuation plans that are both costly and disruptive. Despite this, evacuation plans that address terrorist threats and bombings have become an integral part of any security policy, especially in certain parts if the world.
Note
To learn more about disasters and disaster recovery, refer to Chapter 9, “Business Continuity and Disaster Recovery.”
Site and Facility Design
For many forward-thinking organizations, physical security considerations begin during site selection and design. These companies have learned that building in security than is easier patching the security after the fact. In this section site selection and site building practices that can lead to increased physical security are covered.
Layered Defense Model
All physical security should be based in a layered defense model. In such a model, reliance should not be based on any single physical security concept but on the use of multiple approaches that support one another. The theory is that if one tier of defense (say, for example, perimeter security) fails that another layer will serve as a backup (such as locks on the server room door). Laying the concepts discussed in this chapter can strengthen the overall physical security.
CPTED
Crime Prevention through Environmental Design (CPTED) refers to designing the facility from the ground up to support security. It is actually a broad concept that can be applied to any project (housing developments, office buildings, and retail establishments). It addresses the building entrance, landscaping, and interior design. It aims to create behavioral effects that reduce crime. The three main strategies that guide CPTED are covered in this section.

Natural Access Control
The natural access control concept applies to the entrances of the facility. It encompasses the placement of the doors, lights, fences, and even landscaping. It aims to satisfy security goals in the least obtrusive and aesthetically appealing manner. A single object can be designed in many cases to fulfill multiple security objectives.
For example, many buildings have bollards or large posts in the front of the building with lights on them. These objects serve a number of purposes. They protect the building entrance from cars being driven into it. The lights also brighten the entrance and discourage crime, and finally they can guide people to the entrance.
Natural access control also encourages the idea of creating security zones in the building. These areas may be labeled, and then card systems can be used to prevent access to more sensitive areas. This concept also encourages a minimization of entry points and a tight control over those entry points. It also encourages a separate entrance in the back for suppliers that is not available or highly visible to the public.
Natural Surveillance
Natural surveillance is the use of physical environmental features to promote visibility of all areas and thus discourage crime in those areas. The idea is to encourage the flow of people such that the largest possible percentage of the building is always populated, because people in an area discourage crime. It also attempts to maximize the visibility of all areas.
Natural Territorials Reinforcement
The goal of natural territorials reinforcement is to create a feeling of community in the area. It attempts to extend the sense of ownership to the employees. It also attempts to make potential offenders feel that their activities are at risk of being discovered. This is often implemented in the form of walls, fences, landscaping, and light design.
Physical Security Plan
Another important aspect of site and facility design is the proper convergence between the physical layout and the physical security plan. Achieving all the goals of Crime Prevention Through Environmental Design is not always possible, and in cases where gaps exist, the physical security plan should include policies and/or procedures designed to close any gaps. The plan should address the following issues.
Deter Criminal Activity
Both the layout and supporting policies should deter criminal activity. For example, as many areas as possible should be open and easily seen. There should be a minimum of isolated and darkened areas. Signage that indicates cameras or onsite monitoring and the presence of guards can also serve as deterrents.
Delay Intruders
Another beneficial characteristic of the physical security plan is to add impediments to entry, such as locks, fences, and barriers. Any procedures that slow and monitor the entry of people into the facility can also help. The more delay the intruder encounters, the less likely he is to choose the facility and the more likely he is to be caught.
Detect Intruders
Systems and procedures should be in place that allow for criminal activity to be detected. Motion sensors, cameras, and the like are all forms of intruder detection. Logging all visitors could also be a form of deterrence.
Assess Situation
The plan should identify specific personnel and actions to be taken when an event occurs. Compiling a list of incident types that indicate an acceptable response, response time, and contact names might be beneficial. Written plans developed ahead of time will provide a much more effective and consistent response.
Respond to Intrusions and Disruptions
The plan should also attempt to anticipate and develop appropriate responses to intruders and to common disruptions (power outages, utility problems, and so on). Although anticipating every potential event is impossible, creating a list covering possible intrusions and disruptions should be doable. Scripted responses can then be developed to ensure a consistent and predictable response to these events from all personnel.
Facility Selection Issues
When an organization moves to a new facility or enlarges an existing one, it is a great opportunity to include physical security issues in the site selection process or in the expansion plan. In this section we’ll look at some critical items to consider if this opportunity presents itself.
Visibility
The amount of visibility desired depends on the organization and the processes being carried out at the facility. In some cases having high visibility of the location to help promote the brand or for convenience of customers is beneficial. In other cases a lower profile is desired when sensitive operations are taking place. When this is the case, the likelihood of eavesdropping from outside the facility through windows should be considered. Considering common areas is also important. If possible these areas should not be isolated or darkened. Place them in visible areas with lighting to discourage crime. This includes hallways, parking lots, and other shared areas.
Surrounding Area and External Entities
Considering the environment in which the facility is located is also important. What type of neighborhood is it? Is it an area that has a high crime rate, or is it isolated? Isolation can be good, but it also invites crime that might go undetected for a longer period of time. Also consider the distance to police stations, medical facilities, and fire stations as well. Finally, consider the nature of the operations of the surrounding businesses. Do they pose any sort of threat to your operations?
Accessibility
The ease with which employees and officers can access the facility is a consideration. What are the traffic conditions that the employees will encounter? If this is a new facility replacing an old one, is it inconvenient for the bulk of the employees? Do you risk losing employees over the commute? Is this location convenient to transportation options, such as train stations and airports? If lots of travel is required by your employees, accessibility could be important. If you often host employees from other locations on a temporary basis or host business partners, are safe accommodations nearby?
Construction
The materials used to construct the facility are another critical issue. But the issues to consider here do not stop at simply the makeup of the walls and ceilings, although that is crucial. It should also take into consideration the support systems built into the building. A complete list of items to look at includes
• Walls
• Doors
• Ceilings
• Windows
• Flooring
• HVAC
• Power source
• Fire detection and suppression
Some special considerations include the following:
• According to (ISC)2, all walls must have a two-hour minimum fire resistant rating.
• Doors must resist forcible entry.
• Location and type of fire suppression systems should be known.
• Flooring in server rooms and wiring closets should be raised to help mitigate flooding damage.
• Backup and alternate power sources should exist.
• Separate AC units must be dedicated and air quality/humidity should be controlled for data centers and computer rooms.
Internal Compartments
In many areas of a facility, partitions are used to separate work areas. These partitions although appearing to be walls are not full walls in that that they do not extend all the way to the ceiling. When this construction approach is combined with a drop ceiling, also common in many buildings, an opportunity exists for someone to gain access to an adjoining room through the drop celling. All rooms that need to be secured, such as server rooms and wiring closets, should not have these types of walls.
Computer and Equipment Rooms
While we are on the subject of rooms that contain equipment to which physical access should be controlled, such as those that contain sensitive servers and crucial network gear, computer and equipment rooms should be locked at all times and secured and fitted with the following safeguards:
Locate computer and equipment room in the center of the building, when possible.
Computer and equipment rooms should have a single access door or point of entry.
Avoid the top floors of building for computer and equipment rooms.
Install and frequently test fire detection and suppression systems.
Install raised flooring.
Install separate power supplies for computer and equipment rooms when possible.
Use only solid doors.
Perimeter Security
When considering the perimeter security of a facility taking a holistic approach, sometimes known as the concentric circle approach, is sometimes helpful (see Figure 11-1). This approach relies on creating layers of physical barriers to information.
Figure 11-1. Concentric Circle Approach
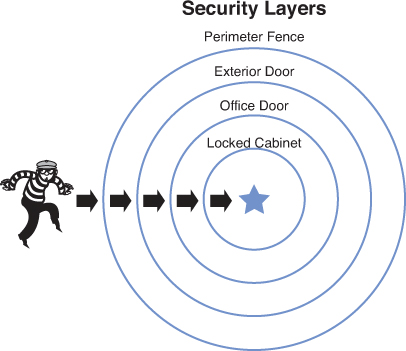
In this section we’ll look at implementing this concept in detail.
Gates and Fences
The outermost ring in the concentric circle approach is comprised of the gates and fences that surround the facility. Within that are interior circles of physical barriers, each of which has its own set of concerns. In this section, considerations for barriers (bollards), fences, gates, and walls are covered.
Barriers (Bollards)
Barriers called bollards have become quite common around the perimeter of new office and government buildings. These are short vertical posts placed at the building’s entrance way and lining sidewalks that help to provide protection from vehicles that might either intentionally or unintentionally crash into or enter the building or injure pedestrians. They can be made of many types of materials. The ones shown in Figure 11-2 are stainless steel.
Figure 11-2. Stainless Steel Bollards

Fences
Fencing is the first line of defense in the concentric circle paradigm. When selecting the type of fencing to install, consider the determination of the individual you are trying to discourage. Use the following guidelines with respect to height:

• Three to four feet tall fences deter only casual intruders.
• Six to seven feet tall fences are too tall to climb easily.
• Eight feet and taller fences deter more determined intruders, especially when augmented with razor wire.
Gates
Gates can be weak points in a fence if not handled correctly. Gates are rated by the Underwriters Laboratory in the following way. Each step up in class requires additional levels of protection.

Class 1: Residential use
Class 2: Commercial usage
Class 3: Industrial usage
Class 4: Restricted area
Walls
In some cases walls might be called for around a facility. When that is the case, and when perimeter security is critical, intrusion detection systems can be deployed to alert you of any breaching of the walls. These type of systems are covered in more detail in the next section.
Perimeter Intrusion Detection
Regardless of whether you use fences or walls, or even if you decide to deploy neither of these impediments, you can significantly reduce your exposure by deploying one of the following types of perimeter intrusion detection systems. All the systems described next are considered physical intrusion detection methods.
Infrared Sensors
Passive infrared systems (PIR) operate by identifying changes in heat waves in an area. Because the presence of an intruder would raise the temperature of the surrounding air particles, this system alerts or sounds an alarm when this occurs.
Electromechanical Systems
Electromechanical systems operate by detecting a break in an electrical circuit. For example, the circuit might cross a window or door and when the window or door is opened the circuit is broken, setting off an alarm of some sort. Another example might be a pressure pad placed under the carpet to detect the presence of individuals.
Photoelectric Systems
Photometric or photoelectric systems operate by detecting changes in the light and thus are used in windowless areas. They send a beam of light across the area and if the beam is interrupted (by a person, for example) the alarm is triggered.
Acoustical Detection Systems
Acoustical systems use strategically placed microphones to detect any sound made during a forced entry. These systems only work well in area where there is not a lot of surrounding noise. They are typically very sensitive, which would cause many false alarms in a loud area, such as a door next to a busy street.
Wave Motion Detector
These devices generate a wave pattern in the area and detect any motion that disturbs the wave pattern. When the pattern is disturbed an alarm sounds.
Capacitance Detector
These devices emit a magnetic field and monitor that field. If the field is disrupted, which will occur when a person enters the area, the alarm will sound.
CCTV
Closed-circuit television system (CCTV) uses sets of cameras that can either be monitored in real time or can record days of activity that can be viewed as needed at a later time. In very high security facilities, these are usually monitored. One of the main benefits of using CCTV is that it increases the guard’s visual capabilities. Guards can monitor larger areas at once from a central location. CCTV is a category of physical surveillance, not computer/network surveillance.
Lighting
One of the best ways to deter crime and mischief is to shine a light on the areas of concern. In this section we’ll look at some types of lighting and some lighting systems that have proven to be effective. Lighting is considered a physical control for physical security.
Types of Systems
The security professional must be familiar with several types of lighting systems:
• Continuous lighting: An array of lights that provide an even amount of illumination across an area
• Standby lighting: A type of system that illuminates only at certain times or on a schedule
• Movable lighting: Lighting that can be repositioned as needed
• Emergency lighting: Lighting systems with their own power source to use when power is out
Types of Lighting
A number of options are available when choosing the illumination source or type of light. The following are the most common choices:
• Fluorescent: Very low pressure mercury-vapor gas-discharge lamp that uses fluorescence to produce visible light.
• Mercury vapor: Gas discharge lamp that uses an electric arc through vaporized mercury to produce light
• Sodium vapor: Gas-discharge lamp that uses sodium in an excited state to produce light
• Quartz lamps: A lamp consisting of an ultraviolet light source, such as mercury vapor, contained in a fused-silica bulb that transmits ultraviolet light with little absorption
Regardless of the light source, it will be rated by its feet of illumination. When positioning the lights you must take this rating into consideration. For example if a controlled light fixture mounted on a 5-meter pole can illuminate an area 30 meter in diameter, for security lighting purposes, the distance between the fixtures should be 30 feet. Moreover, there should be extensive exterior perimeter lighting of entrances or parking areas to discourage prowlers or casual intruders.
Patrol Force
An excellent augmentation to all other detection systems is the presence of a guard patrolling the facility. This option offers the most flexibility in reacting to whatever occurs. One of the keys to success is adequate training of the guards so they are prepared for any eventuality. There should be a prepared response for any possible occurrence. One of the main benefits of this approach is that guards can use discriminating judgment based on the situation, which automated systems cannot do.
Access Control
When granting physical access to the facility, a number of guidelines should be followed with respect to record keeping. Every successful and unsuccessful attempt to enter the facility, including those instances where admission was granted, should be recorded as follows:
• Date and time
• Specific entry point
• User ID employed during the attempt
Building and Internal Security
Although perimeter security is important, security within the building is also important as prescribed in the concentric circle model. This section covers issues affecting the interior of the facility.
Doors
A variety of door types and door materials can be used in buildings. They can either be hollow, which are used inside the building or solid, typically used at the edge of the building and in places where additional security is required. Some door types with which the security professional should familiar and prepared to select for protection are
• Vault doors: Leading into walk-in safes or security rooms
• Personnel doors: Used by humans to enter the facility
• Industrial doors: Large doors that allow access to larger vehicles
• Vehicle access doors: Doors to parking building or lots
• Bullet-resistant doors: Doors designed to withstand firearm
Door Lock Types
Door locks can either be mechanical or electronic. Electric locks or cipher locks use a key pad that required the correct code to open the lock. These are programmable and organizations that use them should change the password frequently. Another type of door security system is a proximity authentication device, with which a programmable card is used to deliver an access code to the device either by swiping the card or in some cases just being in the vicinity of the reader. These devices typically contain the following Electronic Access Control (EAC) components:
• An electromagnetic lock
• A credential reader
• A closed door sensor
Turnstiles and Mantraps
Two special types of physical access control devices, mantraps, and turnstiles, require mention as well. Although you might be familiar with a turnstile, which can be opened by scanning or swiping an access card, a mantrap is an unusual system with which you might not be familiar.
A mantrap is a series of two doors with a small room between them. The user is authenticated at the first door and then allowed into the room. At that point additional verification occurs (such as a guard visually identifying the person) and then she is allowed through the second door. These doors are typically used only in very high security situations. Mantraps also typically require that the first door is closed, prior to enabling the second door to open. Figure 11-3 shows a mantrap design.
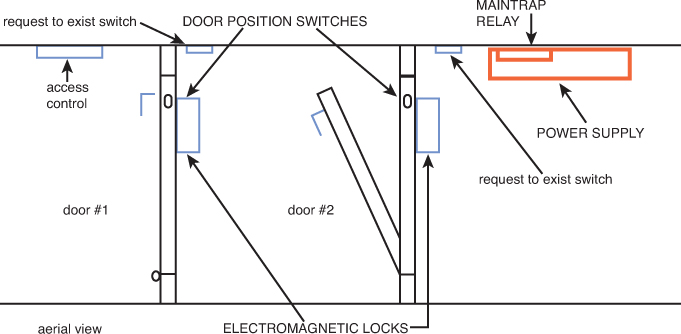
Locks
Locks are also used in places other than doors, such as protecting cabinets and securing devices. Types of mechanical locks with which you should be familiar are
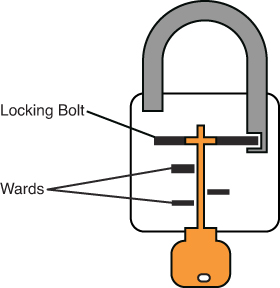
Warded locks: These have a spring-loaded bolt with a notch in it. The lock has wards or metal projection inside the lock with which the key will match and enable opening the lock. A warded lock design is shown in Figure 11-4.
Tumbler locks: These have more moving parts than the warded lock, and the key raises the lock metal piece to the correct height. A tumbler lock design is shown in Figure 11-5.

Combination locks: These require rotating the lock in a pattern that, if correct, lines the tumblers up, opening the lock. A combination lock design is shown in Figure 11-6.

In the case of device locks, laptops are the main item that must be protected because they are so easy to steal. Laptops should never be left in the open without being secured to something solid with a cable lock. These are vinyl-coated steel cables that connect to the laptop and then lock around an object.
Biometrics
The highest level of physical access control and the most expensive to deploy is a biometric device. Biometric devices were covered extensively in Chapter 2, “Access Control.”
Glass Entries
Glass entryways include windows, glass doors, and glass walls, which have become common in many facilities. The proper glass must be selected for the situation. You should be familiar with the following types of glass:
• Standard: Used in residential area and is easily broken
• Tempered: Creating by heating the glass, which gives it extra strength
• Acrylic: Made of polycarbonate acrylic, is much stronger than regular glass but produces toxic fumes when burned
• Laminated: Two sheets of glass with a plastic film between, which makes breaking it more difficult
In areas where regular glass must be used but security is a concern, glass can be used that is embedded with wire to reduce the likelihood of breaking and entering. An even stronger option is to supplement the windows with steel bars.
Visitor Control
Some system of identifying visitors and controlling their access to the facility must be in place. The best system is to have a human present to require all visitors to sign in before entering. If that is unfeasible, another option is to provide an entry point at which visitors are presented with a locked door and a phone that can be used to call and request access. Either of these methods helps to prevent unauthorized persons from simply entering the building and going where they please.
Another best practice with regard to visitors is to always accompany a contractor or visitor to their destination to help ensure they are not going where they shouldn’t. In low security situations this practice might not be necessary but is recommended in high security areas. Finally, log all visits as discussed in the “Access Control” section earlier in this chapter.
Equipment Rooms
Lock any areas where equipment is stored, and control access to them. Having a strict inventory of all equipment so theft can be discovered is also important. For data centers and server rooms, the bar is raised even higher. There will more on this topic later in this section.
Work Areas
Some system should be in place to separate areas by security. Some specific places where additional security measures might be required are discussed in this section. Most of these measures apply to both visitors and employees. Prohibiting some employees from certain areas might be beneficial.
Secure Data Center
Data centers must be physically secured with lock systems and should not have drop ceilings. Some additional considerations for rooms that contain lots of expensive equipment are
• They should not be located on top floors or in basements.
• An off switch should be located near the door for easy access.
• Separate HVAC for these rooms is recommended.
• Environmental monitoring should be deployed to alert of temperature or humidity problems.
• Floors should be raised to help prevent water damage.
• All systems should have a UPS with the entire room connected to a generator.
Restricted Work Area
The facility might have areas that must be restricted to only the workers involved, even from other employees. In these cases physical access systems must be deployed using smart cards, proximity readers, keypads, or any of the other physical access mechanism described in this book.
Environmental Security
Although most considerations concerning security revolve around preventing mischief, preventing damage to data and equipment from environmental conditions is also the responsibility of the security team because it addresses the availability part of the CIA triad. In this section some of the most important considerations are covered.
Fire Protection
Fire protection has a longer history than many of the topics discussed in this book, and while the traditional considerations concerning preventing fires and fire damage still hold true, the presence of sensitive computing equipment requires different approaches to detection and prevention, which is the topic of this section.
Fire Detection
Several options are available for fire detection. You should be familiar with the following basic types of fire detection systems:
• Smoke activated: Operates using a photoelectric device to detect variations in light caused by smoke particles
• Heat activated (also called heat-sensing): Operates by detecting temperature changes. These can either alert when a predefined temperatures is met or alert when the rate of rise is a certain value.
• Flame actuated: Optical devices that “look at” the protected area. They generally react faster to a fire than non-optical devices do.
Fire Suppression
Although certainly fire extinguishers (covered earlier in this chapter) are a manual form of fire suppression, other more automated systems also exist. You should be familiar with the following sprinkler system types:
• Wet pipe: Use water contained in pipes to extinguish the fire. In some areas the water might freeze and burst the pipes, causing damage. These are also not recommended for rooms where equipment will be damaged by the water.
• Dry pipe: In this system the water is not held in the pipes but in a holding tank. The pipes hold pressurized air, which is reduced when fire is detected allowing the water to enter the pipe and the sprinklers. This minimizes the chance of an accidental discharge. Figure 11-7 shows a comparison of a wet and dry system.
Figure 11-7. Wet and dry pipe systems

• Preaction: Operates like a dry pipe system except that the sprinkler head holds a thermal-fusible link that must be melted before the water is released. This is currently the recommended system for a computer room.
• Deluge: Allows large amounts of water to be released into the room, which obviously makes this not a good choice where computing equipment will be located.
At one time, fire suppression systems used Halon gas, which works well by suppressing combustion through a chemical reaction. However, these systems are no longer used because they have been found to damage the ozone layer.
EPA-approved replacements for Halon include:
• Water
• Argon
• NAF-S-III
Another fire suppression system that can be used in computer rooms that will not damage computers and is safe for humans is FM-200.
Power Supply
The power supply is the lifeblood of the enterprise and all of its equipment. In this section we’ll look common power issues and some of the prevention mechanisms and mitigation techniques that will allow the company to continue to operate when power problems arise.
Types of Outages
When discussing power issues you should be familiar with the following terms:
• Surge: A prolonged high voltage
• Brownout: A prolonged drop in power that is below normal voltage
• Fault: A momentary power outage
• Blackout: A prolonged power outage
• Sags: A momentary reduction in the level of power
However, possible power problems go beyond partial or total loss of power. Power lines can introduce noise and interfere with communications in the network. In any case where large electric motors or source of certain types of light, such as florescent lighting, are present, shielded cabling should be used to help prevent Radio Frequency Interference (RFI) and Electromagnetic Interference (EMI).
Preventative Measures
Procedures to prevent static electricity from damaging components should also be observed. Some precautions to take are
• Use anti-static sprays.
• Maintain proper humidity levels.
• Use anti-static mats and wrist bands.
To protect against dirty power (sags and surges) and both partial and total power outages, the following devices can be deployed:
• Power conditioners: Go between the wall outlet and the device and smooth out the fluctuations of power delivered to the device, protecting against sags and surges.
• Uninterruptible power supplies (UPS): Go between the wall outlet and the device and use a battery to provide power if the source from the wall is lost.
HVAC
The heating and air conditioning systems are not just there for the comfort of the employees. The massive amounts of computing equipment deployed by most enterprises are even more dependent on these systems than the humans. They won’t complain; they’ll just stop working. Computing equipment and infrastructure devices like routers and switches do not like the following conditions:
• Heat: Excessive heat causes reboots and crashes
• Humidity: Causes corrosion problems with connections
• Low humidity: Dry conditions encourage static electricity, which can damage equipment
With respect to temperature some important facts to know are:
• At 100 degrees damage starts occurring to magnetic media; in fact, floppy diskettes are the moist susceptible to this.
• At 175 degrees, damage starts occurring to computers and peripherals.
• At 350 degrees, damage starts occurring to paper products.
In summary, the conditions need to be perfect for these devices. It is for this reason that AC units should be dedicated to the information processing facilities and on a separate power source than the other HVAC systems.
Water Leakage and Flooding
As much as computing systems dislike heat, they dislike water even more. It also can cause extensive damage to flooring, walls, and the facility foundation. Water detectors should be placed under raised floors and over dropped ceilings so that leaks in the ceiling and water under the floors are detected before they cause a problem.
Speaking of raised floors, in areas such as wiring closets, data centers, and server rooms, all floors should be raised to provide additional margin for error in the case of rising water.
Environmental Alarms
An error that causes a system to be vulnerable because of the environment in which it is installed is called an environmental error. Considering the various challenges presented by the environmental demands placed on the facility by the computing equipment and the costs of failing to address these needs, it behooves the enterprise to have some system that alerts when environmental conditions are less than desirable. An alert system such as a hygrometer, which monitors humidity, should be in place in areas where sensitive equipment resides. The system should also monitor temperature as well. These types of controls are considered physical controls.
Equipment Security
The physical security of the equipment has been stressed throughout this book. This section discusses corporate procedures concerning equipment and media and the use of safes and vaults for protecting other valuable physical assets.
Corporate Procedures
Physical security of equipment and media should be designed into the security policies and procedures of the company. These procedures should address the following issues.
Tamper Protection
It should not be possible for unauthorized persons to access and change the configuration of any devices. This means additional measures, such as the ones in the remainder of this section, should be followed to prevent this. Tampering incudes defacing, damaging, or changing the configuration of a device. Integrity verification programs should be used by applications to look for evidence of data tampering, errors, and omissions.
Encryption
Encrypting sensitive data stored on devices can help to prevent the exposure of the data in the event of a theft or in the event of inappropriate access of the device. Cryptography and encryption concepts are covered extensively in Chapter 6.
Inventory
Recognizing when items are stolen is impossible if no item count or inventory system exists. All equipment should be inventoried, and all relevant information about each device should be maintained and kept up to date. Maintain this information both electronically and in hard copy.
Physical Protection of Security Devices
Security devices, such as firewalls, NAT devices, and intrusion detection and prevention systems, should receive the most attention because they relate to physical and logical security.
Beyond this, devices that can be easily stolen, such as laptops, tablets, and smartphones, should be locked away. If that is not practical, then lock these types of devices to a stationary object. A good example of this is the cable locks used with laptops.
Tracking Devices
When the technology is available, tracking of small devices can be used to help mitigate loss of both devices and their data. Many smartphones now include tracking software that allow you to locate the device after it has been stolen or lost by using either cell tower tracking or GPS. Deploy this technology when available.
Another useful feature available on these same types of devices is a remote wipe feature. This allows sending a signal to a stolen device instructing it to wipe out the data contained on the device. Finally these devices typically also come with the ability to remotely lock the device when misplaced.
Portable Media Procedures
Strict control of the use of portable media devices can help prevent sensitive information from leaving the network. This includes floppy disks, CDs, DVDs, flash drives, thumb drives, and external hard drives. Although written rules should be in effect about the use of these devices, using security policies to prevent the copying of data to these media types is also possible. Allowing the copying of data to these drive types as long as the data is encrypted is also possible. If these functions are provided by the network operating system, you should deploy it.
Safes, Vaults, and Locking
With respect to protecting physical assets such as laptops smartphones, tablets, and so on, nothing beats locking the devices away. In cases where it is possible to do so, lockable cabinets are a good solution for storing these devices. In addition to selecting the proper lock (locks are discussed earlier in this chapter) all equipment should be inventoried, and a system devised for maintaining these counts as the devices come and go.
Some items require even more protection than a locked cabinet. Keep important legal documents and any other items of extreme value in a safe or a vault for the added protection these items require. Fire-proof safes and vaults can provide protection for contents even during a fire.
Personnel Privacy and Safety
The human resources are the most important assets the organization possesses. You might recall that in the event of a fire, the first action to always take is to evacuate all personnel. Their safety comes before all other considerations. Although equipment and in most cases the data can be recovered, human beings can neither be backed up nor replaced.
An Occupant Emergency Plan (OEP) provides coordinated procedures for minimizing loss of life or injury and protecting property damage in response to a physical threat. In a disaster of any type, personnel safety is the first concern.
Note
More information on occupant safety can be found in Chapter 9, “Business Continuity and Disaster Recovery Planning.”
The organization is responsible for protecting the privacy of each individual’s information, especially as it relates to personnel and medical records. Although this expectation of privacy does not necessarily and usually does not extend to their activities on the network, both federal and state laws hold organizations responsible for the release of this type of information with violations resulting in heavy fines and potential lawsuits that result if the company is found liable.
Note
More information on legal considerations regarding privacy appears in Chapter 10, “Legal, Regulations, Investigations, and Compliance.”
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple of choices for exam preparation: the exercises in this chapter” and the exam simulation questions on the CD-ROM.
Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 11-1 lists a reference of these key topics and the page numbers on which each is found.

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
system threats
natural threats external threats
internal threats
man-made threats
auxiliary station alarm
Class A extinguisher
Class B extinguisher
Class C extinguisher
Class D extinguisher
Class K extinguisher
collusion
civil disobedience
Crime Prevention Through Environmental Design (CPTED)
Natural Access Control
Natural Surveillance
Natural Territorials Reinforcement
Class 1 gate
Class 2 gate
Class 3 gate
passive infrared systems (PIR)
electromechanical systems
photometric system
acoustical systems
wave motion detector
capacitance detector
closed circuit television system (CCTV)
continuous lighting
sodium vapor lighting
quartz lamp lighting
proximity authentication device
standard glass
tempered glass
acrylic glass
laminated glass
smoke-activated sensor
heat-activated sensor
flame-actuated sensor
wet pipe extinguisher
dry pipe extinguisher
preaction extinguisher
deluge extinguisher
uninterruptible power supplies (UPS)
Review Questions
1. Which of the following is an example of preventing an internal threat?
a. a door lock system on the server room
b. an electric fence surrounding the facility
c. armed guards outside the facility
d. parking lot cameras
2. Which of the following is not an example of a natural threat?
a. flood
b. bombing
c. earthquake
d. tornado
3. Which of the following is a system threat?
a. loss of utilities
b. bombing
c. earthquake
d. tornado
4. What is the recommended optimal relative humidity range for computer operations?
a. 10%–30 %
b. 20%–40 %
c. 30%–50 %
d. 40%–60 %
5. What is the most prevalent cause of computer center fires?
a. human error
b. electrical distribution systems
c. lighting systems
d. arson
6. Which of the following is not an example of a man-made threat?
a. bombing
b. arson
c. flood
d. collusion
7. Which of the following extinguishers is designed to address electrical equipment fires?
a. Class A
b. Class B
c. Class C
d. Class D
8. Class K extinguishers are designed to address what type of fire?
a. cooking oil or fat
b. flammable liquids
c. combustible metals
d. ordinary combustibles
9. Which of the following is not a politically motivated threat?
a. power outage
b. bombing
c. strike
d. civil disobedience
10. Which of the following is not one of the three main strategies that guide CPTED?
a. Natural Access Control
b. Natural Surveillance Reinforcement
c. Natural Territorials Reinforcement
d. Natural Surveillance
Answers and Explanations
1. a. An electric fence surrounding the facility is designed to prevent access to the building by those who should not have any access (an external threat), whereas a door lock system on the server room that requires a swipe of the employee card is designed to prevent access by those who are already in the building (an internal threat).
2. b. A bombing is an example of a man-made threat.
3. a. Some of the threats that exist are not from the forces of nature but from failures in systems that provide basic services such as electricity and utilities.
4. d. The recommended optimal relative humidity range for computer operations is 40% to 60%.
5. b. The most prevalent cause of computer center fires is electrical distribution systems. These systems should be checked regularly to identify problems before they occur.
6. c. Floods are a natural threat.
7. c. Class C extinguishers are designed to address electrical equipment fires.
8. a. Class K extinguishers are designed to address cooking oil or fat fires.
9. a. Power outage is a system threat.
10. b. The three strategies are Natural Access Control, Natural Territorials Reinforcement, and Natural Surveillance.
