Chapter 9
Wireless LAN Security Basics
The following CWTS exam objectives are covered in this chapter:
- 6.1 Identify and describe the following legacy WLAN security technologies
- SSID Hiding
- WEP
- MAC Filtering
- 6.2 Understand the basic operation of and implementation best practices for the following WLAN security technologies
- WPA and WPA2-Personal
- WPA and WPA2-Enterprise
- 802.1X/EAP
- AAA and RADIUS
- Encryption - TKIP/CCMP
- 6.3 Understand the basic functions and implementation best practices for the following WLAN security technologies
- Role based access control (RBAC)
- Virtual private networking (VPN)
- Wireless intrusion prevention systems (WIPS)
- Captive portals
- Network management and monitoring systems
Security in many ways means defining your level of acceptable risk and protecting yourself to at least that level. This can vary greatly based on industry, budget, and the types and ages of devices supported. Security is a very important part of wireless networking, just as it is in any other type of computer networking or information technology. When the IEEE 802.11 standard was first ratified back in 1997, it addressed a basic security concept called Wired Equivalent Privacy (WEP). However, this security solution was considered weak and was easily compromised early on. In this chapter, we will look at some of the legacy wireless LAN security technologies used with standards-based wireless networking, including:
We will also take a look at some of the vulnerabilities of these legacy technologies and see why they should not be used for securing a wireless LAN. You will learn about some of the newer security methods available based on the IEEE 802.11i amendment and now included in the IEEE 802.11-2012 standard. These security methods are also part of the Wi-Fi Alliance certifications, WPA and WPA 2.0. We will explore small office/home office (SOHO) security solutions and enterprise-level security solutions. These include:
In Chapter 2, “Introduction to Wireless Local Area Networking,” we discussed some of the certifications available from the Wi-Fi Alliance that pertain to wireless LAN security. This chapter will explore further some of the concepts of passphrase, preshared key, and 802.1X/EAP. We will also discuss encryption methods such as TKIP and CCMP, which are ways to scramble computer data and are used with wireless LANs.
One thing that is often overlooked is security from a remote location, such as a wireless hotspot. In this chapter, you will learn about virtual private networking (VPN) solutions and how they can be used to secure wireless connections for users connecting to the corporate network from a remote wireless network. Wireless intrusion prevention systems (WIPS) are also becoming popular in today's wireless LAN world. If WIPS is implemented correctly, these solutions can provide a wealth of information as well as protection for your network infrastructure and wireless devices. Finally, we will look at basic functions and implementation best practices for role-based access control (RBAC), captive portals, and network management and monitoring systems.
Introducing IEEE 802.11 Wireless LAN Security
The importance of computer network security is often underestimated, and wireless LAN security is no different. “I don't understand why I need to secure my access point.” “I don't have anything on my computer that would be of interest to anybody other than me.” “I tried to enable security on my wireless, but I couldn't get it to work so I just turned it off.” These are some of the common excuses many technical support engineers or consultants used to hear from people when it came to wireless security. In the early days of IEEE 802.11 wireless networking, security was weak. This led to much vulnerability, which in turn made wireless networking not a very attractive solution for many enterprise deployments, especially those concerned about security.
With the improvements in standards-based wireless LAN security, partly thanks to the Wi-Fi Alliance certifications as well as the IEEE 802.11i amendment to the standard, wireless LANs have become a major part of many enterprise networks in all industries and businesses. Because wireless networks are inherently unbounded, it is possible to have more security protecting wireless communication than what is used to secure most wired LANs. This is the case in many wireless LAN implementations.
Wireless LAN Threats and Intrusion
Computer networks have always been the target of various types of intrusion techniques. Wireless networks are no different—in fact, wireless networks are more vulnerable to intrusion because the communication is not bounded by any physical media such as an Ethernet cable. This key vulnerability in wireless networking is the use of the air, a shared unbounded medium. The level of security applied to a wireless network will depend on a couple of factors:
- What are you trying to protect?
- What are you trying to prevent?
There are many security concerns related to wireless networking. Some of these concerns arise because wireless LANs use radio frequency for communication and the open air as the medium. Others are a threat to either wired or wireless networks. The following list identifies some of these concerns and threats:
- Eavesdropping
- Radio frequency denial of service (DoS)
- Media access control (MAC) address spoofing
- Hijacking
- Man-in-the-middle attacks
- Peer-to-peer attacks
- Encryption cracking
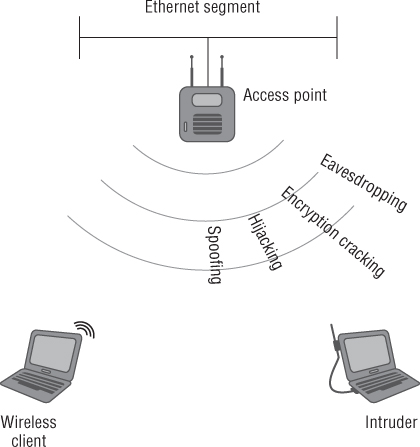
Although many of these threats or methods of intrusion are common, advanced security solutions such as wireless intrusion prevention systems (WIPS) are available to help discover and mitigate some of them. Figure 9.1 illustrates some of the vulnerabilities with wireless networking.
Figure 9.1 Wireless LANs are subject to many potential security threats.
![]()
IEEE 802.11 Standard Security
Even though wireless LAN security has greatly increased over the years, it is important to understand the original IEEE 802.11 standard as it relates to wireless LAN security. It is important to be aware of some of the basics or building blocks prior to getting into more sophisticated areas of security. From a security viewpoint, the original standard addressed two areas of security: authentication and data privacy. Both of these are common components of computer network security. In computer networking, authentication is defined as a way of confirming an identity; basically, it determines that you are who you say you are. Data privacy is ensuring that information or data is understandable only by the individuals or groups it is intended for, the sender and the intended receiver.
One way many people may think of authentication is to supply a username and password in order to log onto a computer. Another would be to supply the appropriate logon before performing an activity like Internet banking. To review from Chapter 8, “Wireless LAN Terminology and Technology,” the original IEEE 802.11 standard addresses two types of authentication: open system authentication and shared-key authentication. These authentication types are different from the examples described earlier, which most people are familiar with. IEEE 802.11 authentication is performed by the wireless LAN protocol and, except for shared-key authentication, does not require user intervention.
IEEE 802.11 Open System Authentication
To review from Chapter 8, this type of authentication is a two-step process, a two-frame exchange, and is one of the simplest ways to provide an authentication process. IEEE 802.11 open system authentication cannot fail except for circumstances such as a network adapter having a bad device driver. This authentication is what is known as a null authentication, which for the most part means it doesn't really authenticate anything at all. For example, if a wireless client device such as a notebook computer wants to join the wireless network, it will “ask” the access point if it can authenticate, and the access point will always accept.
IEEE 802.11 Shared-Key Authentication
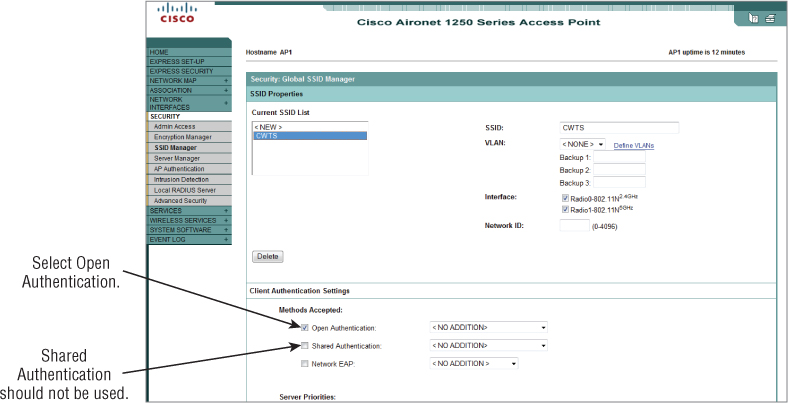
Also discussed in Chapter 8, IEEE 802.11 shared-key authentication is a four-step process, not to be confused with WPA or WPA2 personal mode, which uses a preshared key for authentication. The main difference between open system and shared-key authentication is that with shared-key authentication, Wired Equivalent Privacy (WEP) is required in order for it to function correctly. This is because shared-key authentication uses WEP for both 802.11 authentication and for data payload encryption. But WEP is not secure, so it makes shared-key authentication weak and vulnerable to intrusion. WEP was intended only to protect wireless network users against casual eavesdropping and for authentication with shared key. Figure 9.2 shows how to set either open system or shared-key authentication on an enterprise-grade access point.
Figure 9.2 Cisco 1250 series IEEE 802.11n wireless access points SSID security settings
Early Wireless LAN Security Technologies
Because of the way security was defined in the original IEEE 802.11 standard, manufacturers of wireless LAN equipment were able to design different ways a user could secure a wireless LAN. But even though these methods looked good on paper, they did not do much to provide a good security solution. Some of these common wireless LAN security methods and legacy security solutions discussed here are:
- Service set identifier (SSID) hiding (closed network)
- Media access control (MAC) filtering
- Wired Equivalent Privacy (WEP)
If some of these are considered legacy wireless LAN security methods, why is it important to discuss them? You need to understand these solutions because there are still some wireless network implementations that may use some or all of them as part of a wireless security solution. Because standards-based wireless LAN technology has been around for over a decade, many early adopters had no choice but to use these security techniques. Over the years, wireless LAN security has improved tremendously; however, it is a fact that some of these early adopters still have legacy wireless devices that will not support the latest and greatest security technology such as WPA or WPA2. Therefore these solutions may still currently play a role in the wireless network infrastructure.
The Service Set Identifier
As you'll recall from Chapter 8, the service set identifier (SSID) is a logical name for the wireless network and was designed to be used for wireless device segmentation. The SSID will allow wireless devices such as notebook computers to identify and connect to a wireless LAN using the discovery phase, which includes the passive and active scanning processes. There are a couple of ways this connection can be accomplished. Passive scanning occurs when the wireless client device listens for beacons frames. The SSID is specified in a beacon frame in the SSID information element. As discussed in Chapter 8, the beacon frame is an advertisement of the wireless network. The beacon frame by default is set to broadcast at about 10 times a second. The beacon frame will advertise the SSID of the wireless network during this interval.
You can specify that the SSID of the wireless LAN be joined in the wireless client software utility of the connecting wireless device. In this case, a wireless client will send a probe request frame with the intent of joining that particular network. The IEEE 802.11 standard requires access points to respond to all probe requests that have a matching SSID or what is known as a wildcard SSID (an SSID with a value of 0), also referred to as a null SSID. A wildcard SSID is used when a client device does not specify the SSID in the wireless client software utility. If a wireless client device is scanning or looking for a wireless network to join, they will see the wireless network because the beacon frame is broadcasting the SSID. Most manufacturers of SOHO and enterprise access points provide the option not to broadcast the SSID in beacon frames. This is commonly known as disabling the SSID broadcast, SSID hiding, or a closed network and is discussed in the next section.
SSID Hiding
Most manufacturers of IEEE 802.11 wireless LAN equipment provide the capability to disable SSID broadcasting, as shown in Figure 9.3. Another term for this process is SSID hiding. SSID hiding allows a user to remove the SSID that would normally appear in broadcast beacon frames. If the SSID is not being broadcast, the wireless network may not be seen by the wireless client devices that do not have that wireless network's SSID specified in their client software utility. If somebody knows the SSID, they would be able to enter it into their wireless client device software and then be able to connect to the wireless network.
Figure 9.3 The Motorola RFS6000 wireless LAN controller allows you to disable SSID broadcast.
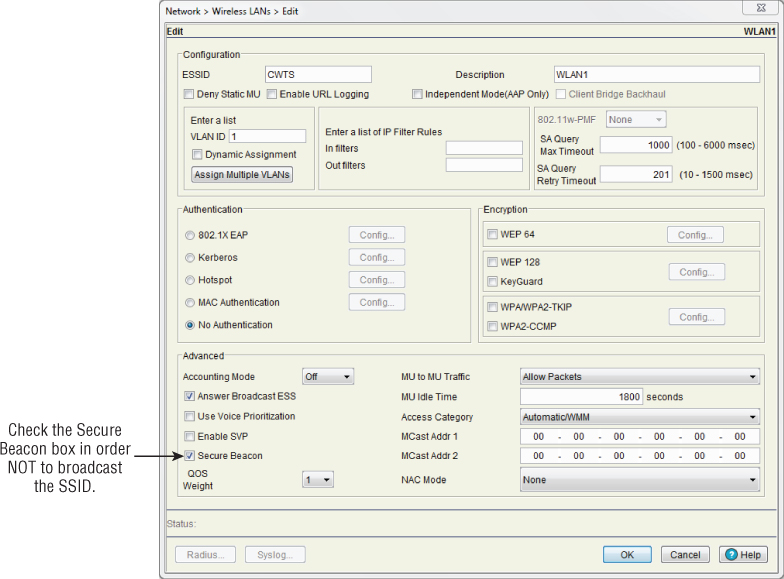
In the early days of wireless networking, people would hide the SSID, believing that would secure the network because it was not visible to devices passively scanning for a network to join. This was a misconception, because even though the SSID is not being broadcast in these beacon frames, it can still be identified in other wireless frames, such as the probe response frame. This means that anyone with a wireless scanning utility such as a packet analyzer would be able to determine the SSID of a wireless network by monitoring the frames that are sent through the air. Therefore, hiding the SSID should not be used as a way to secure a wireless network.
Hiding the SSID is sometimes used to prevent the wireless network from being seen by those who should not be connecting to it. Many organizations will hide the SSIDs of all the wireless networks except for the open guest network. This is sometimes done to help reduce unnecessary technical support calls from someone who may try to connect to a wireless LAN that they do not have access to. However, this method is not intended to secure the wireless network.
The Media Access Control Address
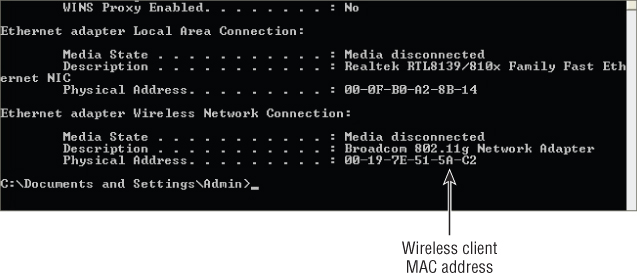
To review, the media access control (MAC) address is a unique hardware identifier of a computer network device. This 6-byte address is the Layer 2 address that allows frames to be sent to and received from a device. Figure 9.4 shows the MAC address of a wireless network adapter viewed with ipconfig.exe. An important point here is that the MAC address is unique, and no two network devices should ever have the same Layer 2 MAC address. In a wireless network, MAC addresses are easily visible to anyone using a wireless packet analyzer or wireless network scanning software utility. These addresses are required for a network device to send and receive information; therefore, they cannot be encrypted and are visible to anyone with the knowledge to view them.
Figure 9.4 The Windows command-line utility ipconfig.exe will display MAC addresses.
MAC Address Filtering
Since IEEE 802.11 wireless LAN device technology operates at the lowest two layers of the OSI model, the Physical layer and the Data Link layer, the MAC address plays a big role in wireless networking. Manufacturers of wireless LAN equipment provide a feature known as MAC address filtering. Its purpose is to either allow or disallow access to the wireless network by restricting which MAC addresses can IEEE 802.11 authenticate and associate to a wireless network. Figure 9.5 is an example of how to apply a MAC address filter on an access point.
Figure 9.5 Linksys WRT54G MAC filter setup
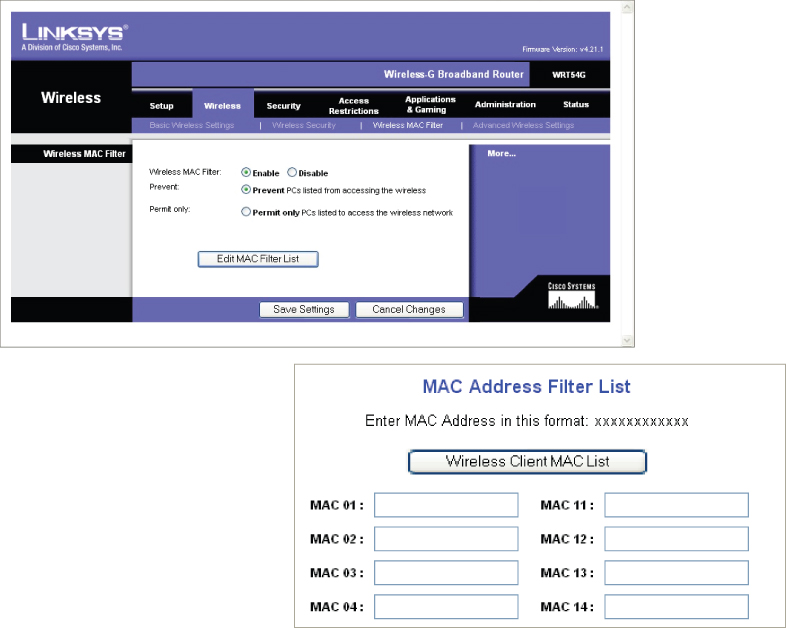
This looks great on paper but is a weak security feature, because it can be easily compromised. Remember, wireless networks use the air as their access medium to communicate, and radio frequency is what exchanges the information between devices. So if an intruder were to monitor the air with a tool such as a wireless packet analyzer or wireless scanning utility software program, they would be able to see all the wireless traffic within hearing range of their wireless device. Because wireless LAN devices communicate with each other using MAC addressing, all of these addresses would be visible to whoever wants to see them.
MAC Address Spoofing
Because MAC addresses are visible to anyone who wants to take the time to see them by using the correct software utility, they create a potential problem for those who implemented MAC address filtering. An intruder can easily perform a task called MAC address spoofing. This involves tricking the wireless device into thinking its unique MAC address is something other than what is encoded in the actual network card.
There are several ways for an intruder to accomplish MAC address spoofing. It can be done with software programs such as SMAC or within the computer operating system—for example, in the Microsoft Windows Registry. All options and configuration settings in the Windows operating system are stored in this hierarchical database known as the Windows Registry. If someone wanted to spoof the MAC address of a wireless network adapter using this database, they might (depending on the adapter) be able to enter a new MAC address value in the device driver's configuration, which would then be stored in the Windows Registry. Another option is to change the Windows Registry value directly using the Registry Editor tool built into Windows. This would be considered a modifiable MAC address. MAC addresses may also be stored in a configuration file, and in nonvolatile memory. Keep in mind that changing the MAC address in the Registry or in a configuration file changes only the software reference that the operating system sees and uses. It does not change what is known as the burned-in address (BIA) or the hard-coded address, which is unmodifiable.
IEEE 802.11 Authentication and Data Encryption
As discussed earlier in this chapter, authentication is defined as validating an identity. Authentication also gives the capability to control access to a system. In the original IEEE 802.11 standard, this is accomplished by using either IEEE 802.11 open system or shared-key authentication. Since open system authentication is a null authentication method and except for special circumstances it cannot fail, the wireless device will always authenticate. IEEE 802.11 shared-key authentication, on the other hand, uses Wired Equivalent Privacy (WEP) for wireless device authentication as well as for data payload encryption. Encryption is the process of modifying information from its original form to make it unreadable except by those who know the technique or the method in which the data was modified. In the original IEEE 802.11 standard, data encryption was accomplished by using WEP. In order for a device to pass information across an access point, it must first IEEE 802.11 authenticate, and then associate.
About Wired Equivalent Privacy
From a security perspective, one major drawback to any wireless network is the fact that all information, including data payload, travels through the air from one device to another. This makes wireless LANs vulnerable to eavesdropping and inherently less secure than bounded networking using other networking technology such as Ethernet. With IEEE 802.11 open system authentication, all information is broadcast through the air in plain text. What this means is that anyone with knowledge of how to use a wireless packet analyzer or other wireless scanning software program can easily see all the information that is passing between devices through the air.
WEP was designed as a way to protect wireless networking from casual eavesdropping. The original IEEE 802.11 standard states that the use of WEP is optional. The manufacturer supplies the capability, but it is up to the user of the wireless device to implement it.
In wireless LANs, WEP can be used in one of two ways: with IEEE 802.11 open system authentication to encrypt the data only or with shared-key authentication, which is used for wireless device authentication and for data encryption. The original standard specified only 64-bit WEP, which consists of a 40-bit key plus 24-bit WEP initialization vector (IV).
How to Use WEP
WEP is fairly simple to implement. It requires all wireless devices to have the same WEP key. The WEP key can be either 64-bit or 128-bit; however, the standard required only 64-bit WEP. One disadvantage to WEP is that it uses static keys, which means all wireless devices—access points, bridges, and client stations—must have the same key and the key must be manually entered into them. Any time the key is changed, it must be changed on all of the wireless device that are on the same SSID. No matter which you use, 64-bit WEP or 128-bit WEP, you are still only using a 24-bit IV. 64-bit WEP uses a 40-bit secret key and a 24-bit IV. 128-bit WEP uses a 104-bit secret key but still only the 24-bit IV, making both vulnerable to the same attacks. Gathering a number of these IVs allows an attacker to crack your key in minutes.
![]()
Figure 9.6 shows configuring an enterprise-grade access point for WEP. Table 9.1 describes the characteristics of the two types of WEP keys.
Figure 9.6 Cisco 1250 series IEEE 802.11n wireless access point WEP key settings
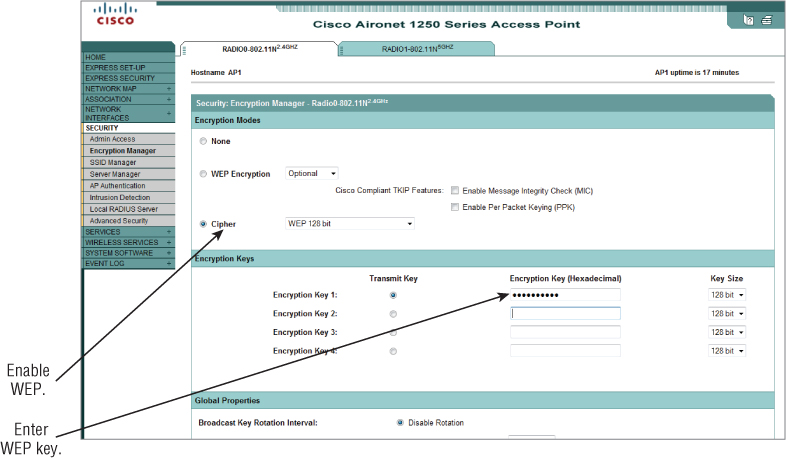
Table 9.1 Characteristics of the two types of WEP keys
| Key length | # of ASCII characters | # of hex characters |
| 64 bit | 5 | 13 |
| 128 bit | 10 | 26 |
One major disadvantage of using WEP is that it was compromised early on and is therefore not secure. It is easy to capture data using a wireless packet analyzer; with a little knowledge and correct software utilities, cracking a WEP key is a simple feat. This made WEP a weak security solution, but it was pretty much the only solution available at the time of early IEEE 802.11 wireless networking.
With today's newer and more sophisticated software tools and technology, WEP can be cracked easily and quickly. WEP will be discussed in more detail in the section “IEEE 802.11 Encryption Methods” later in this chapter.
IEEE 802.11 SOHO and Enterprise Security Technologies
The IEEE 802.11i amendment to the standard provided much improvement in the ways wireless LANs can be secured. Enterprise-based wireless LANs are now capable of the most up-to-date security solutions available in the industry. This amendment to the standard introduced what is known as the Robust Secure Network (RSN). In order for wireless LAN equipment to create an RSN, it must be RSN capable or 802.11i compliant, which means it will optionally support Temporal Key Integrity Protocol (TKIP) and it must also support Counter Mode with Cipher-Block Chaining Message Authentication Code Protocol (CCMP). The Wi-Fi Alliance has released several certifications that pertain to wireless networking: WPA and WPA 2.0 for SOHO and enterprise deployments, and WPS for the home user.
![]()
Wi-Fi Protected Setup PIN-Based or Push-Button Configuration Wireless Security
Many manufacturers of SOHO-grade wireless LAN equipment have adopted either PIN-based or push-button wireless security. Both of these solutions simplify the process of securing a wireless network either for the SOHO environment or for home-based users. As discussed in Chapter 2, the Wi-Fi Alliance has branded a certification for push-button and PIN-based security called Wi-Fi Protected Setup. The Wi-Fi Protected Setup certification (WPS) addresses both of these solutions.
![]()
PIN-Based Security
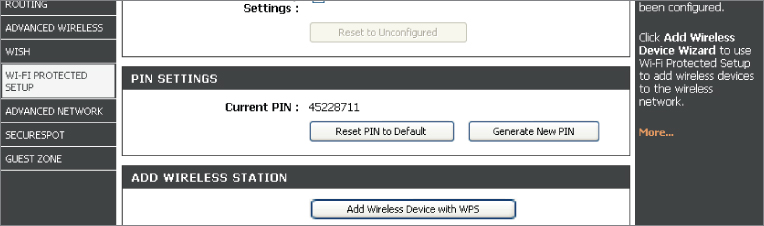
Personal identification number (PIN) functionality is required in order for a wireless device to be Wi-Fi Protected Setup (WPS) certified. PIN-based security requires a unique PIN to be entered on all devices that will be part of the same secure wireless network. A PIN will come as either a fixed label or sticker on a device, or it can be dynamically generated in the setup utility and shown on the computer screen. It is important to understand the difference between a PIN and a passphrase, password, shared key, or preshared key. A PIN is a number; the acronym spelled out means “personal identification number.” Therefore a PIN will only consist of numbers. Passphrases and the others may contain combinations of numbers, letters, and special characters. The registrar device in the case of a wireless LAN is the access point. The access point will detect when a new wireless device that supports WPS is in radio range. When this device tries to join the network, the registrar will prompt the user to enter the unique PIN. Once the PIN is entered, the process authenticates the device and encrypts the network data sent to and from the device. Figure 9.7 shows an example of PIN-based wireless security.
Figure 9.7 D-Link wireless access point with PIN-based security
Push-Button Configuration Security
Push-button security or push-button configuration (PBC) allows users to configure wireless LAN security with “the push of a button,” making setting up wireless security a one-step process. When a user pushes a hardware button on the wireless residential gateway (wireless router) and clicks a software button in the software utility for the network adapter installed in the client device wanting to associate, push-button security creates a connection between the devices, configures the network's SSID, and turns on security. This allows a secure connection among all devices that are part of the wireless network. Figure 9.8 shows an example of push-button security. The Linksys version of push-button security is called SecureEasySetup (SES).
Figure 9.8 Linksys WRT54G wireless residential gateway/router with push-button security (SES)
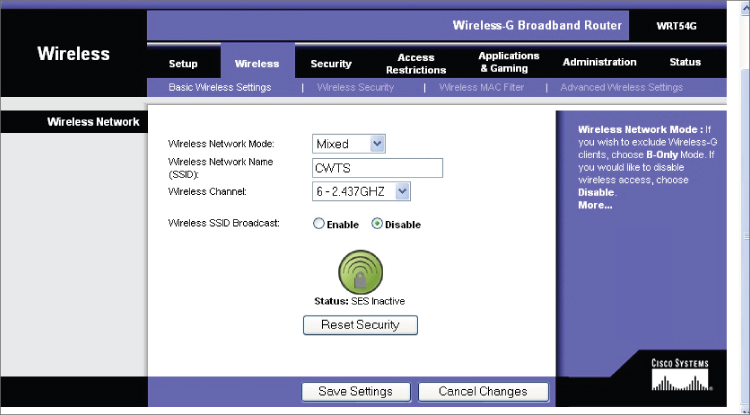
In order to use SES, all devices, including the wireless residential gateway/router and the wireless client adapters, must support the feature. First a button is pushed on the wireless residential gateway/router; then a button (a software setting in the wireless client utility) is clicked on the wireless device(s). Usually in less than a minute the process is complete and all devices have a secure connection. Only those devices within radio frequency hearing range that are participating in the process will become part of the secure network.
Support for both PIN and PBC configurations is required for access points; client devices at a minimum must support PIN. A third, optional method, near field communication (NFC) tokens, is also supported. A USB flash drive (memory card or solid-state storage drive with a USB interface) may be used to store and transfer credentials. Many SOHO equipment manufacturers have Wi-Fi Protected Setup-certified devices on the market today. Some include:
- Belkin
- Broadcom
- D-Link
- Linksys
- Netgear
- TRENDnet
- ZyXEL

Wi-Fi Protected Access and WPA2 Personal Security
Passphrase-based security was designed with the SOHO or home-based user in mind. This type of security allows a user to create a very secure wireless LAN solution without the experience or knowledge necessary to configure enterprise-level components such as an 802.1X/EAP and a RADIUS server. Passphrase-based security requires all wireless devices that are part of the same wireless network to have the same 256-bit preshared key (PSK) in order to securely communicate. The capability to derive a secure key of this length would be a daunting task; to ease the burden of having to create a long secure key, the passphrase was introduced. This works by requiring the user to enter a strong passphrase on all wireless devices that are part of the same wireless LAN to be secured. The benefit of a passphrase is it can be a sequence of words or other text that is memorable only to the user who created it. After the passphrase is entered into the device, with the help of an electronic algorithm from the IEEE 802.11i amendment, it will create a 256-bit preshared key.
Passphrase Characteristics
The characteristics of the passphrase are as follows:
- It consists of 8 to 63 ASCII (case sensitive) or 64 hexadecimal characters.
- It creates a 256-bit preshared key.
- The longer and more random the passphrase, the more secure it will be.
- Weak passphrases can be compromised.

Figure 9.9 shows how to configure a passphrase on a SOHO access point.
Figure 9.9 D-Link wireless access point preshared key passphrase settings
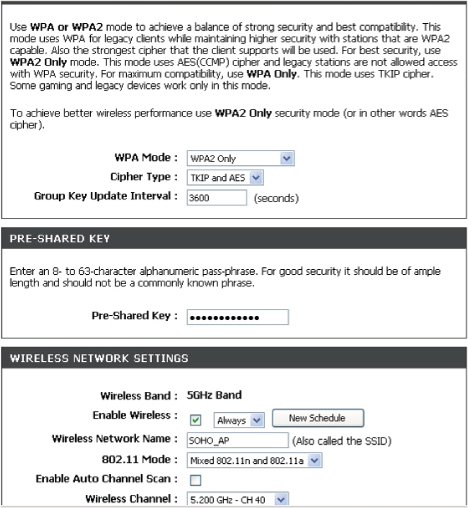
WPA and WPA2 Enterprise Security
Concerned about problems connected with MAC address filtering and WEP, the industry drove the development of additional, improved wireless security solutions. One of these solutions also operates at Layer 2 and is an IEEE standard. This advanced enterprise-level solution is known as IEEE 802.1X, also called user-based security. User-based security allows an administrator to restrict access to a wireless network and its resources by creating users in a centralized database. Anyone trying to join the network will be required to authenticate as one of the users by supplying a valid username and password. After successful authentication, the user will be able to gain access to resources for which they have permissions. This type of mutual authentication is more secure than the previously mentioned passphrase security method.
IEEE 802.1X/EAP
IEEE 802.1X/EAP consists of two different components used together to form an enterprise computer network security solution. IEEE 802.1X/EAP is defined in the IEEE 802.11-2012 Standard but was originally part of the IEEE 802.11i amendment. We'll first discuss the IEEE 802.1X standard and then Extensible Authentication Protocol (EAP). Then we'll combine the technology and terms to form IEEE 802.1X/EAP.
IEEE 802.1X
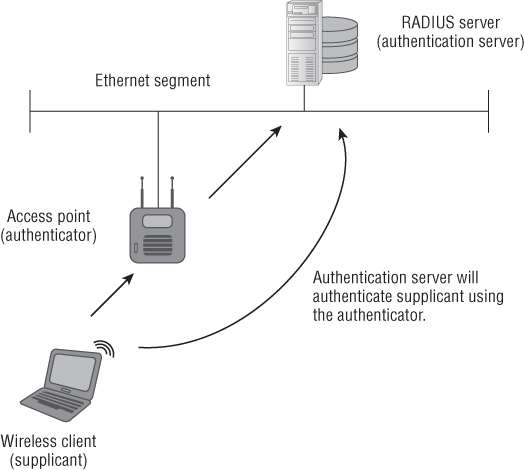
IEEE 802.1X is a port-based access control method and was designed to work with IEEE 802.3 Ethernet wired networks. However, this standard was adapted into the wireless world as an alternative, more powerful solution to legacy 802.11 wireless LAN security technologies. Wireless devices that use 802.1X technology are identified using different terminology than that used in IEEE 802.11 standards-based wireless networking:
- Supplicant (wireless client device)
- Authenticator (wireless access point)
- Authentication server RADIUS or AAA authentication server)
Figure 9.10 illustrates the 802.1X/EAP process for a wireless LAN.
Figure 9.10 Wireless LAN client authenticating to a RADIUS server using IEEE 802.1X/EAP
Extensible Authentication Protocol
IEEE 802.1X is a framework that allows for an authentication process. The authentication process used with IEEE 802.1X is Extensible Authentication Protocol (EAP). The IEEE 802.1X standard will employ some EAP type to complete this process. Many types of EAP are available in the industry that can be used with IEEE 802.11 wireless networking. These vary from proprietary solutions to very secure standard solutions. Examples of some popular EAP types include:
- EAP-TLS
- TTLS (EAP-MSCHAPv2)
- PEAP (EAP-MSCHAPv2)
- EAP-FAST
These and other EAP types allow a user to authenticate to a wireless network in several ways, including credentials such as username/password or certificate-based authentication.
![]()
IEEE 802.1X and EAP Together: IEEE 802.1X/EAP
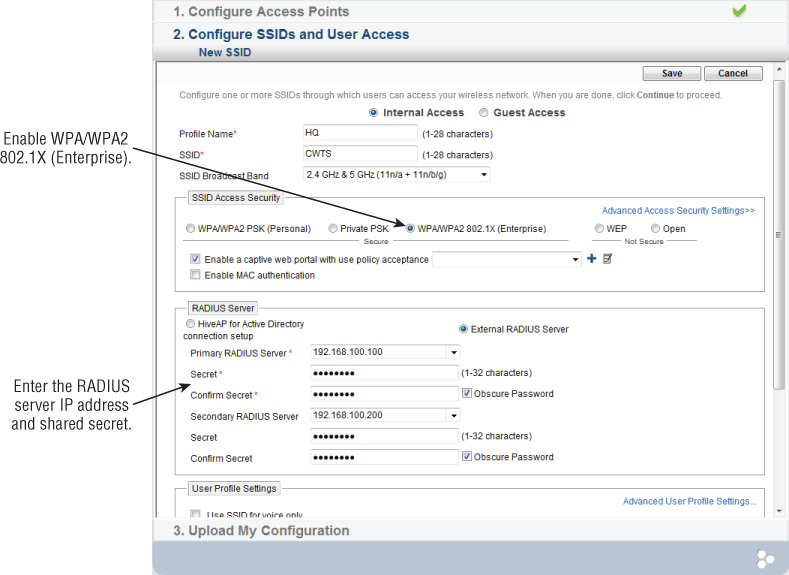
Now it is time to put these two parts together to form the IEEE 802.1X/EAP authentication process. This authentication process is typically used for enterprise-level security but can be and is sometimes used in smaller wireless installations. As mentioned earlier, a variety of EAP types are available in the industry that work very well with IEEE 802.11 wireless LAN deployments. The EAP type chosen will depend on the environment in which the wireless LAN is used. EAP types vary in specifications, costs, and complexity. Figure 9.11 shows IEEE 802.1X/EAP configuration on a cloud-based wireless network management system.
Figure 9.11 Aerohive HiveManager Online cloud-based IEEE 802.1X/EAP configuration screen
Remote Authentication Dial-In User Service
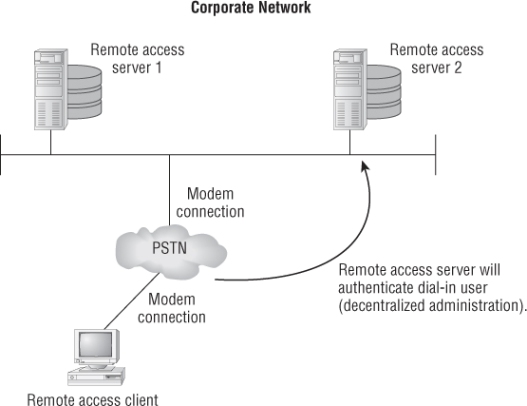
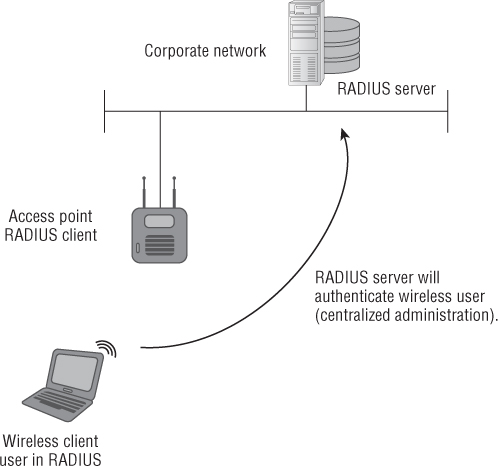
Remote Authentication Dial-In User Service (RADIUS) is a networking service that provides centralized authentication and administration of users. RADIUS started as a way to authenticate and authorize dial-up networking users. A remote user would dial up to a network using the public switched telephone network (PSTN) and a modem. A modem from a modem pool on the receiver side would answer the call. The user would then be prompted by a remote access server to enter a username and password in order to authenticate. Once the credentials were validated, the user would then have access to any resources for which they had permissions. Figure 9.12 illustrates the remote access service authentication mechanism.
In this example, the remote access client would be the computer dialing into the network, and the remote access server would be the one performing the authentication for the dial-up user. As computer networks grew in size and complexity and remote access technology improved, there was a need to optimize the process on the remote access server side. This is where RADIUS provides a solution. RADIUS took decentralized remote access services databases and combined them into one central location, allowing for centralized user administration and centralized management. It eased the burden of having to manage several databases and optimized administration of remote access services.
Figure 9.12 Remote user authenticating to a remote access server (RAS)
A company does not need a large number of RADIUS servers. For a small to medium-sized company, one RADIUS server should be sufficient (with a backup if possible). Larger enterprise organizations may need several RADIUS servers across the entire wide area network. In wireless networking, the wireless access point can act as a RADIUS client, which means it will have the capability to accept requests from wireless client devices and forward them to the RADIUS server for authentication. Figure 9.13 shows this configuration.
As Figure 9.13 shows, the remote access client is now the wireless access point. The wireless client device is authorized as a user in the database of the RADIUS server. The RADIUS server is the authenticating server or database. A RADIUS server may also be known as an authentication, authorization, and accounting (AAA) server. In this configuration, it will authenticate users and provide access to the resources for which they have permissions. In addition, it will keep track of all transactions by accounting.
Authentication, Authorization, and Accounting
The Authentication, Authorization, and Accounting (AAA) protocol provides a framework to allow secure access and authorization as well as keep track of the user's activities on a computer network including wireless networks. AAA is commonly part of a RADIUS server's functionality. The three components that work together in the AAA protocol are:
- Authentication
- Authorization
- Accounting
Figure 9.13 Wireless access point configured as a RADIUS client device
The First Part of AAA—Authentication
As you learned earlier in this chapter, authentication is defined as a way of confirming or validating an identity; for the most part it validates that you are who you say you are. Enterprise IEEE 802.11 wireless networks commonly use IEEE 802.1X/EAP or user-based authentication technology. In addition to username and passwords, wireless networks may also use other authentication methods, including digital certificates and smart cards, to name a few.
The Second Part of AAA—Authorization
For wireless networking, authorization provides access to network resources that a wireless device or user has the appropriate permissions or rights to use. These permissions could be tied to an individual user object but can also be tied to a group object. After a user authenticates, the AAA protocol will then allow for the authorization process. Authorization can be on a per-user or per-group basis. In IEEE wireless networking technology, authorization is commonly used for wireless LAN functionality, including bandwidth controls, time restrictions/controls, and quality of service (QoS) policies.
The Third Part of AAA—Accounting
Accounting is the last part or third “A” in the Authentication, Authorization, and Accounting (AAA) protocol. Accounting will keep track of every place on the network a user visits or everything done on the network. Basically, it monitors all network activity. This can be used for something as simple as tracking resource usage for software or hardware upgrade purposes or for technology budgeting purposes. Accounting can be used to determine what technology different areas of the organization are using and how they will be able to contribute to the cost of this technology.
IEEE 802.11 Encryption Methods
In the most basic sense, encryption consists of taking information and scrambling it so only the sender and intended recipient that know the encryption method are able to decipher the encrypted information. In addition to authenticating and verifying an identity, encryption also needs to be considered for wireless networking. In the IEEE 802.11 standard, three different encryption mechanisms can be used on a wireless network to protect data traffic:
- Wired Equivalent Privacy (WEP)
- Temporal Key Integrity Protocol (TKIP)
- Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP)
Wired Equivalent Privacy
As discussed earlier in this chapter, Wired Equivalent Privacy (WEP) was an optional encryption method specified in the original IEEE 802.11 standard. WEP was only intended to protect wireless network users against casual eavesdropping and for IEEE 802.11 shared-key authentication. As discussed, this encryption method is considered legacy and was compromised early on, making it a weak solution to use with modern wireless networks. With early deployments of standards-based wireless networking, WEP was the only solution available, which made it very popular. At that time, the capability to crack WEP was available but that did not mean anyone could do it. Initially, cracking WEP required a large amount of data, some knowledge of the process, and usually a software program to extract the WEP key. Newer technology has made cracking WEP a very simple process. WEP can be cracked in minutes rather than hours, days, or weeks and almost anyone can do it. The fact that WEP is available in two key lengths—64-bit or 128-bit—makes no difference to the experienced intruder. WEP uses the RC4 stream cipher for bit-level encryption. The problem with WEP does not lie in RC4 but in how it was used in the encryption process. One reason WEP is vulnerable to intrusion is because of something called an initialization vector (IV). The 24-bit IV is broadcast in the clear or unencrypted. This being the case, it exposes a weakness in the way WEP was designed, thereby allowing it to be compromised.
There are many software programs available to allow someone with limited knowledge to be able to crack WEP. As mentioned earlier, newer, more sophisticated tools allow WEP to be cracked in minutes. If a wireless network has the capability of more advanced security such as 802.11i, WPA, or WPA 2.0, one of those should be used instead of WEP. An appropriate device upgrade path should be evaluated in order to eliminate the use of WEP in any capacity on the wireless network.
Temporal Key Integrity Protocol
Temporal Key Integrity Protocol (TKIP) was designed as a firmware upgrade to WEP. TKIP added several enhancements to the WEP algorithm and was the foundation for the Wi-Fi Protected Access (WPA) certification from the Wi-Fi Alliance. These enhancements include:
- Per-packet key mixing of the IV to separate IVs from weak keys
- A dynamic rekeying mechanism to change encryption and integrity keys
- 48-bit IV and IV sequence counter to prevent replay attacks
- Message Integrity Check (MIC) to prevent forgery attacks
- Use of the RC4 stream cipher, thereby allowing backward compatibility with WEP
Configuring a wireless network to use TKIP is a fairly straightforward process. It can be accomplished either by using the web interface available on most SOHO access points or by using the web interface or command-line interface for enterprise-level access points. For the wireless client devices, TKIP will be configured through the client software utility. Some older wireless hardware devices may not support TKIP. If this is the case, replacement of the hardware will be necessary in order to take advantage of newer security solutions. Figure 9.14 shows how to configure TKIP using WPA on a wireless LAN controller.
![]()
Counter Mode with Cipher Block Chaining Message Authentication Code Protocol
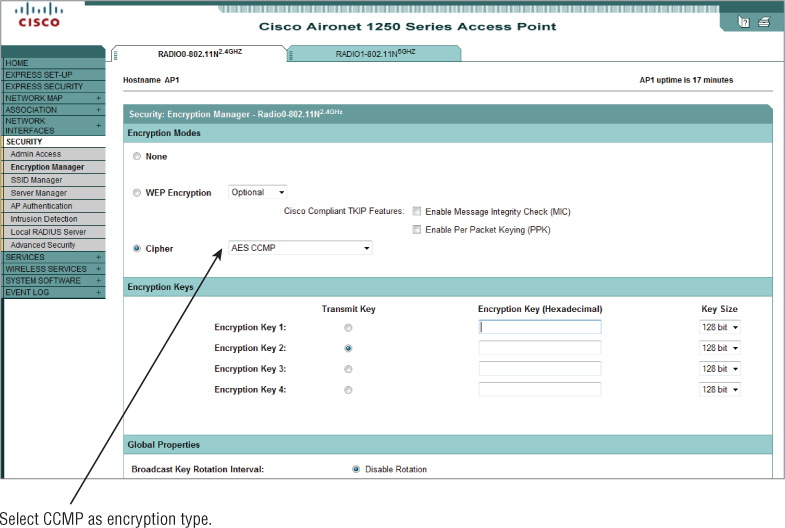
Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) is a mandatory part of the IEEE 801.11i amendment, now in the IEEE 802.11-2012 standard and part of Wi-Fi Protected Access 2.0 (WPA2) certification from the Wi-Fi Alliance. CCMP uses the Advanced Encryption Standard (AES) algorithm block cipher. CCMP is mandatory for robust security network (RSN) compliance. If an RSN is required to comply with an industry or governmental regulation, CCMP must be used. CCMP is also intended as a replacement to TKIP. Because of the strong encryption CCMP provides, it may require replacement of legacy hardware. In some cases, it may use a separate chip to perform computation-intensive AES ciphering.
Configuration of CCMP is similar to that of TKIP, discussed earlier. The main difference with CCMP is that older hardware may not support it and it is a stronger encryption solution. Figure 9.15 shows configuring the CCMP method using WPA2.
Figure 9.14 Motorola RFS6000 wireless LAN controller security configuration screen
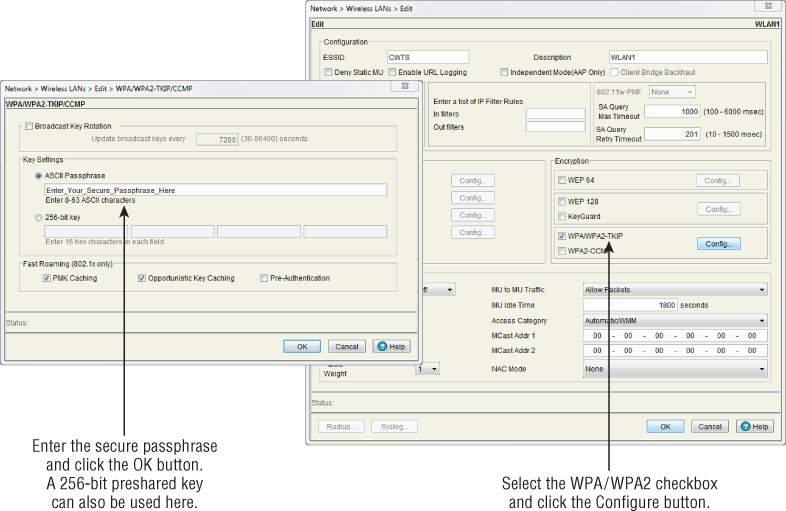
Figure 9.15 Cisco 1250 series IEEE 802.11n wireless access point security configuration selection
Some of the security technologies we just discussed are part of the Wi-Fi Alliance interoperability testing for standards-based wireless LAN equipment. As mentioned in Chapter 2, equipment certified for both WPA and WPA2 can function in either personal or enterprise modes. Table 9.2 shows the details of both WPA and WPA 2 certifications.
Table 9.2 Details of the Wi-Fi Alliance WPA and WPA 2 certifications
| Wi-Fi Alliance security method | Authentication method | Encryption/cipher method |
| WPA - Personal | Passphrase | TKIP/RC4 |
| WPA - Enterprise | IEEE 802.1X/EAP | TKIP/RC4 |
| WPA 2 - Personal | Passphrase | CCMP/AES or TKIP/RC4 (optional) |
| WPA 2 - Enterprise | IEEE 802.1X/EAP | CCMP/AES or TKIP/RC4(optional) |
Role-Based Access Control
Role-based access control (RBAC) is a way of restricting access to only authorized users. This access is from authentication based on specific roles rather than user identities. It was designed to ease the task of security administration on large networks. RBAC has characteristics similar to those of a common network administration practice—the creation of users and groups. RBAC may also fit well under the authorization part of AAA because it has very similar characteristics.
To give a user on a computer network access to a network resource, best practices recommend creating a group object, assigning the group permissions to the resource, and then adding the user object to the group. This method allows any user who is a member of the group to be granted access to the resource. Role-based access control can be used for various activities users may perform while connected to a wireless LAN, including limiting the amount of throughput, enforcing time restrictions, or controlling access to specific resources such as the Internet.
Let's look at an example. Your organization consists of several departments that use resources available on the wireless network. The departments are sales, engineering, and accounting. Each department has specific requirements for what and when they need to access from the wireless LAN. This is where RBAC would be a great fit. If the network administrator wanted to restrict access to the wireless LAN for the sales department from 8:00 a.m. to 5:00 p.m., she could create a role using this feature. If the engineering department was using too much bandwidth, a role could be created to restrict throughput for that department. These are a couple of examples where RBAC can work with a wireless LAN.
Virtual Private Networking
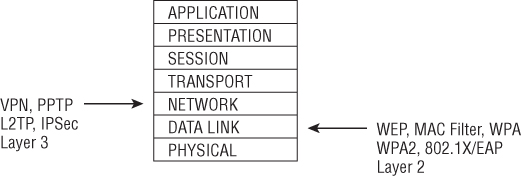
Virtual private networking (VPN) is the capability to create private communications over a public network infrastructure such as the Internet. The security solutions discussed earlier in this chapter are Layer 2 security solutions; that is, all such solutions work at Layer 2 of the OSI model. By contrast, VPNs are Internet Protocol-based—they typically operate at Layer 3 of the OSI model but some will work at Layer 2. Figure 9.16 illustrates VPN technology in relationship to the OSI model.
Figure 9.16 OSI model representation of a Layer 3 VPN security solution
Prior to the ratification of the IEEE 802.11i amendment to the standard, VPN technology was prevalent in enterprise deployments as well as in remote access security. Since Layer 2 security solutions have become stronger (mostly thanks to the 802.11i amendment and the Wi-Fi Alliance WPA and WPA2 certifications), VPN technology is not as widely used within enterprise LANs. However, VPN still remains a powerful security solution for remote access in both wired and wireless networking.
VPNs consist of two parts—tunneling and encryption. Figure 9.17 illustrates a VPN tunnel using the Internet. A standalone VPN tunnel does not provide data encryption, and VPN tunnels are created across Internet Protocol (IP) networks. In a very basic sense, VPNs use encapsulation methods where one IP frame is encapsulated within a second IP frame. The encryption of VPNs is performed as a separate function.
Figure 9.17 Representation of a VPN tunnel
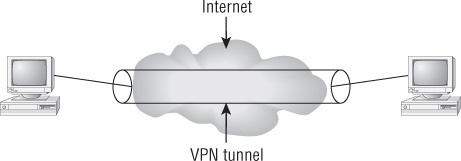
![]()
Two common types of VPN protocols are:
- Point-to-Point Tunneling Protocol (PPTP)
- Layer 2 Tunneling Protocol (L2TP)
Point-to-Point Tunneling Protocol
Developed by a vendor consortium that included Microsoft, Point-to-Point Tunneling Protocol (PPTP) was very popular because of its ease of configuration and was included in all Microsoft Windows operating systems starting with Windows 95. PPTP uses Microsoft Point-to-Point Encryption (MPPE-128) Protocol for encryption. This process provides both tunneling and encryption capabilities for the user's data.
![]()
Layer 2 Tunneling Protocol
Layer 2 Tunneling Protocol (L2TP) is the combination of two different tunneling protocols: Cisco's Layer 2 Forwarding (L2F) and Microsoft's Point-to-Point Tunneling Protocol (PPTP). L2TP defines the tunneling process, which requires some level of encryption in order to function. With L2TP, a popular choice of encryption is Internet Protocol Security (IPSec), which provides authentication and encryption for each IP packet in a data stream. Since L2TP was published in 1999 as a proposed standard and because it is more secure than PPTP, L2TP has gained much popularity and for the most part is a replacement for PPTP. L2TP/IPSec is a very common VPN solution in use today. PPTP should not be used when L2TP is available.
Components of a VPN Solution
A VPN solution consists of three components:
- Client side (endpoint)
- Network infrastructure (public or private)
- Server side (endpoint)
In many cases, both client side and server side are known as VPN endpoints. The infrastructure in many cases is a public access network such as the Internet. The client-side endpoint typically consists of software, allowing it to be configured for the VPN. This software is available at a nominal cost from a variety of manufacturers. Newer Microsoft Windows operating systems include VPN client software for both PPTP and L2TP. Figure 9.18 shows a VPN client configuration screen.
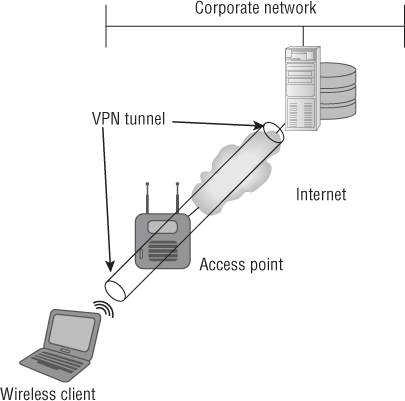
Wireless LAN client devices have the capability to be a VPN client endpoint. The VPN can terminate either at an access point or across the Internet to the corporate network. Figure 9.19 shows a common example of a wireless client device connecting to a wireless hotspot to access the corporate network.
Figure 9.18 Microsoft Windows 7 Professional built-in VPN client utility configuration
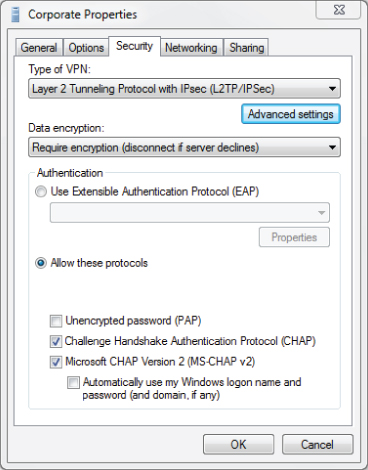
Figure 9.19 Wireless LAN client using a wireless hotspot to connect to a corporate office using VPN technology
In Exercise 9.1, you will explore the built-in VPN client software utility in Windows 7 Professional.
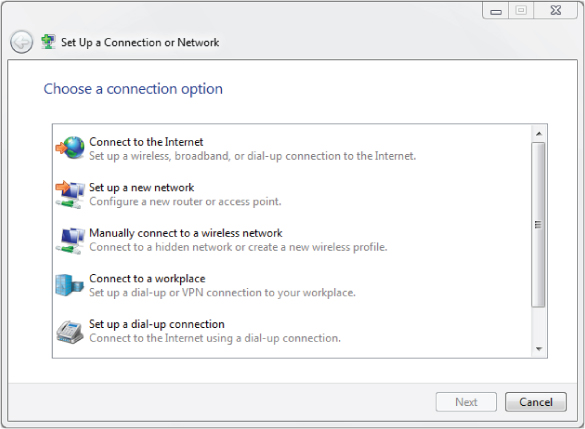
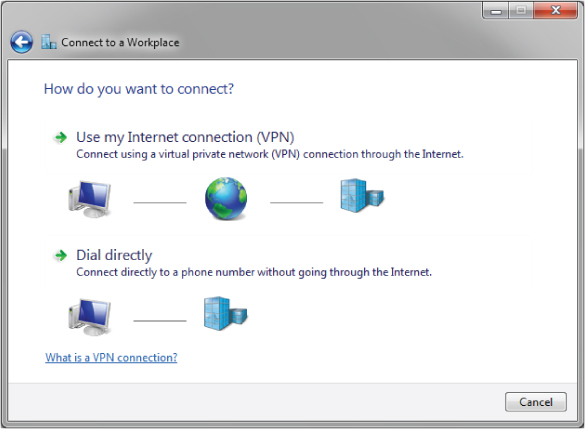
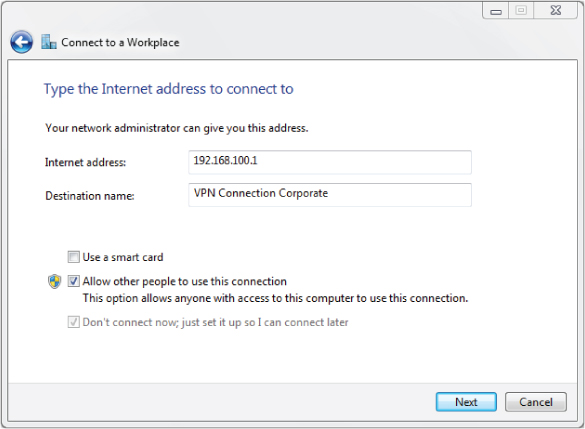
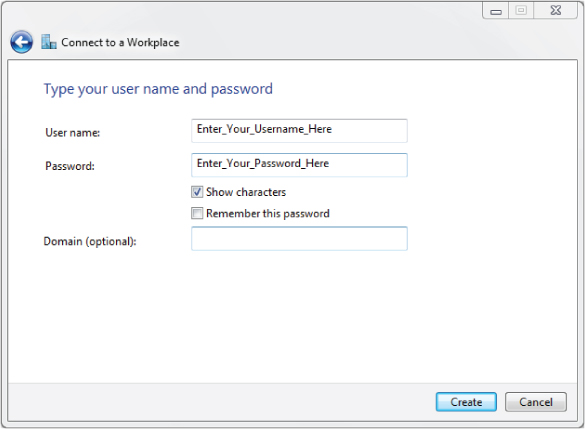
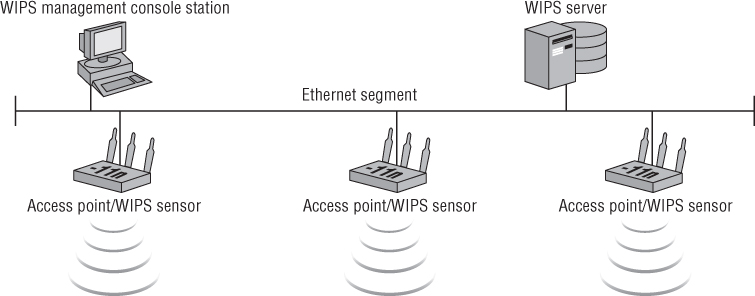
The Wireless Intrusion Prevention System
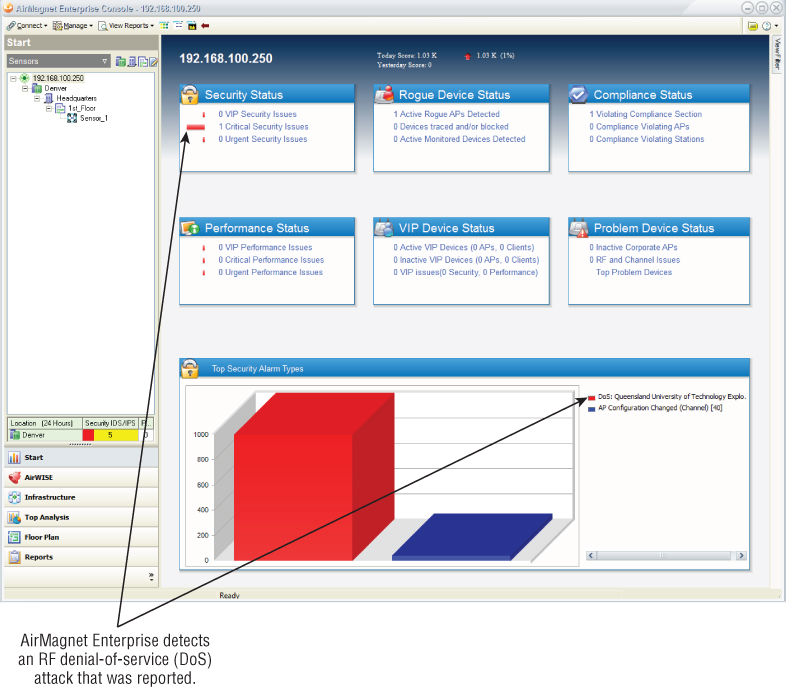
In wireless networking, a wireless intrusion prevention system (WIPS) is a software/hardware solution that monitors the radio waves and, using a wireless hardware sensor, can report captured information to software to be recorded in a server database (this differs from other network monitoring and management systems discussed later in this chapter). The WIPS solution will then be able to take the appropriate countermeasures to prevent wireless network intrusions. These countermeasures are based on identifying the intrusion by comparing the captured information to an intrusion signature database within the WIPS server. Figure 9.20 shows a WIPS dashboard that displays a Layer 1 radio frequency jamming denial of service (DoS) attack that was recorded.
Figure 9.20 AirMagnet Enterprise dashboard
There are many advantages to using a WIPS. Some of them include:
- Captures information by 24×7 monitoring
- Detects threats to the wireless infrastructure such as DoS attacks and rogue access points
- Notifies you about threats through a variety of mechanisms
- Supports integrated spectrum analysis
- Includes elaborate reporting systems
- Ensures compliance with corporate security policy and legislative compliance
- Retains data for forensic investigation
- Uses hardware sensors for monitoring
WIPS Configuration and Maintenance
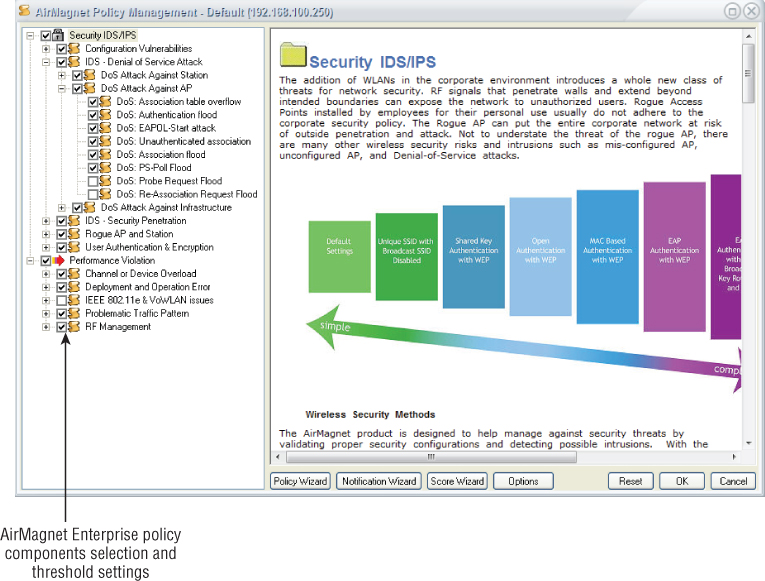
Although a WIPS solution is a valuable tool to use for wireless LAN monitoring and detection/mitigation of wireless intrusions, it needs to be set up, configured, and maintained correctly. Installing a WIPS system without setting the appropriate thresholds and baselines may result in unreliable or unusable collections of information. For example, if an organization is concerned about deauthentication attacks, such as forcing a “deauthentication storm” (sending many consecutive deauthentication frames), this setting will need to be enabled on the WIPS system with the appropriate threshold setting in order to be detected. Remember from Chapter 8 that deauthentication occurs when an existing authentication is no longer valid, and it can be caused by a wireless LAN device logging off from the current connection or roaming to a different BSS. If an intruder sends just a couple of deauthentication frames to a wireless device in an attempt to force them to reauthenticate, and thus perform a hijack attack, the activity may fall under the threshold set for the deauthentication frames that are monitored and could be missed. The bottom line is that proper setup, configuration, and maintenance of a WIPS system all need to be carefully considered. Figure 9.21 shows the policy setup screen for a WIPS.
Figure 9.21 AirMagnet Enterprise WIPS policy configuration
Overlay and Integrated WIPS Technology
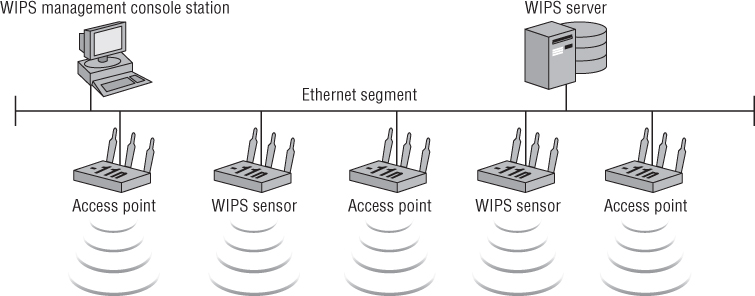
A WIPS requires hardware sensors for monitoring and sending the data to the WIPS server. These sensors can be dedicated devices (only used for monitoring) or can share functionality with the wireless access points. The terminology used for these WIPS sensors is:
- Overlay WIPS sensors
- Integrated WIPS sensors
Overlay WIPS Sensors
Overlay WIPS sensors are dedicated wireless devices that have physical characteristics similar to those of wireless access points but are only used for scanning the air and sending data to a WIPS server. These devices are passive and will not interfere with other wireless LAN devices such as access points. This type of sensor does not need to be implemented on a 1:1 deployment. In other words you do not need one WIPS sensor with every one access point. WIPS sensors are commonly installed in a 1:3 or 1:4 ratio. Figure 9.22 shows how a WIPS overlay solution uses dedicated sensors.
Figure 9.22 The WIPS overlay installation uses separate devices.
It is best to check with the WIPS manufacturer to determine the recommended number of dedicated sensors. Some wireless site survey software tools will specify the number and locations of the sensors required, based on the wireless network design. One disadvantage to the overlay solution is extra cost for the dedicated sensors. Some manufacturers allow a wireless access point to run as a dedicated sensor; for these, the cost would be the same as the wireless access point.
Integrated WIPS Sensors
Integrated WIPS sensors are part of a wireless access point's functionality. An integrated sensor may have a dedicated radio for full-time WIPS monitoring, or it may share a radio with the access point for part-time WIPS monitoring. A dedicated WIPS radio that is built into the wireless access point will be able to monitor the air and send data directly to the WIPS server full time. This would be the radio's only function. One benefit to this type of sensor is that the cost will be less than that of the overlay system, because it does not requires separate dedicated WIPS sensors. However, the cost may be a little higher than if it were only an access point because of the additional radio for the WIPS capability. The other type of integrated WIPS sensor is the one that shares a radio with the access point. The downside to this is that the WIPS monitoring will only be part-time and will not be able to capture everything that is going on. Figure 9.23 shows a WIPS integrated solution, consisting of a WIPS sensor and access point in the same device (wireless access point).
Figure 9.23 WIPS integrated solution sensor radio built into a wireless access point
![]()
Making the decision to use an overlay or integrated WIPS may be a tough one. It may come down to what you are trying to prevent and what you are trying to protect. It may also come down to cost. The bottom line is this: If you are planning to install a WIPS, evaluate the advantages and disadvantages of each type carefully. One of the main goals of a WIPS is to enforce functional (technical) corporate security policy 24/7/365.
The Captive Portal
A captive portal is a process that redirects a user to an authentication source of some type before they will be allowed wireless network access. This authentication source in the form of a web page will require a user to “authenticate” in some way and may include the following:
- Enter user credentials (username and password).
- Input payment information.
- Agree to terms and conditions.
When one or more of these methods is complete, a wireless device will then be able to access the network and use whatever resources they have permission to access. Most if not all public access wireless networks should have some type of captive portal enabled. This will help to protect both the provider (host) and the user of the wireless network. At a minimum, requiring the user to agree to terms and conditions via a captive portal should be implemented.
Most enterprise-grade wireless access points, including cooperative access points and wireless LAN controllers, have “built-in” captive portal capabilities that are fairly straightforward to implement.
Wireless Network Management and Monitoring Systems
Wireless network management and monitoring systems are software- or hardware-based solutions that allow a wireless network engineer to both control and administer wireless infrastructure devices and collect information that may be used to troubleshoot and resolve wireless LAN issues. The information collected may consist of either Physical Layer information (radio frequency) or Data Link Layer information (wireless LAN frames).
In the early days of standards-based IEEE 802.11 wireless networking, only autonomous access points for the most part were available; there was no centralized management or control. (Autonomous access points are discussed in Chapter 2.) To manage these infrastructure devices, you would need to configure each device separately. This could be done by connecting either through the command-line interface or a web-based interface, and individual configuration worked well if only a few infrastructure devices were installed.
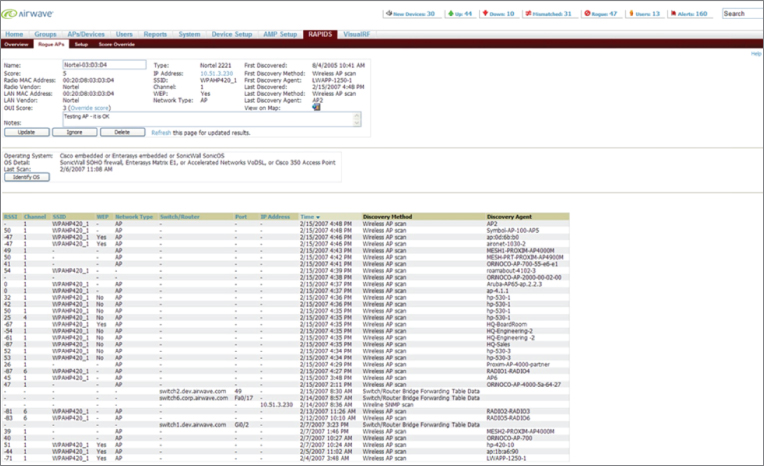
However, as the need for wireless LAN technology grew, so did the number of devices or access points. Managing a large number of infrastructure devices manually was not feasible. This is where the wireless network management system (WNMS) evolved. The WNMS is a centralized solution that was originally available in either software form to run on a server or hardware form to run as a standalone network appliance. (We'll look at a third option, cloud-based WNMS solutions, next.) A WNMS would allow a network engineer to manage and control the entire wireless LAN centrally. These centralized management systems are available from many manufacturers for use with their own infrastructure devices and are available as vendor-neutral solutions to work with many different manufacturers' equipment. A WNMS may also incorporate WIPS technology for a complete wireless network management, monitoring, and security solution. Figure 9.24 shows a WNMS dashboard.
Figure 9.24 Aruba Networks Airwave Wireless Network Management Software Platform
WNMS: Software, Hardware, or Cloud?
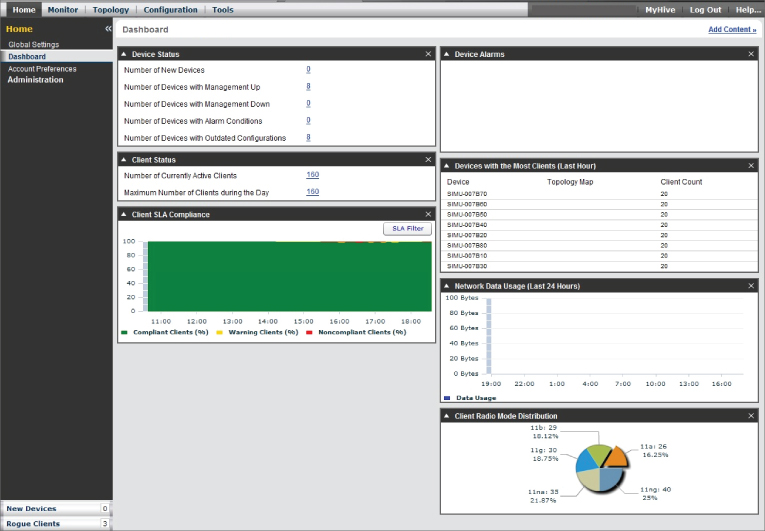
As you just learned, a WNMS is available in different forms—software that will run on a server, hardware that will run on a dedicated appliance, and now cloud-based WNMS solutions. This newest option is growing in popularity. With the evolution of standards-based wireless LAN technology, the wireless LAN controller worked as a substitute for WNMS, offering control and management of the complete wireless LAN infrastructure. However, as the wireless networks continued to grow, so did the need for a WNMS. Figure 9.25 shows a cloud-based wireless network management system.
Figure 9.25 Aerohive HiveManager NMS cloud-based WNMS
Listed here are some of the WNMS solutions available from various manufacturers:
| Manufacturer | Solution | Description |
| Aerohive | HiveManager NMS | Cloud-based, public or private cloud using a virtual machine |
| Aruba Networks | AirWave | Also vendor-neutral or multivendor |
| Cisco Systems | Cisco Wireless Control System (WCS) | |
| Hewlett Packard | HP Intelligent Management Center (IMC) | |
| Meraki | Cloud-based | |
| Motorola | AirDefense Services Platform (ADSP) | Hardware appliance or virtual machine |
| Xirrus | Xirrus Management System (XMS) | Software-, appliance-, or cloud-based |
Keep in mind that some manufacturers allow management of both wireless and wired infrastructures from one platform, creating a “unified” management of the entire network.
Wireless Network Monitoring
In addition to wireless network management solutions, you need to understand wireless network monitoring solutions. These monitoring solutions are in addition to the WIPS you learned about earlier in this chapter. They allow a wireless network engineer to monitor the performance of a wireless network at the Physical layer and the Data Link layer for both troubleshooting and security information gathering purposes.
Physical Layer Monitoring
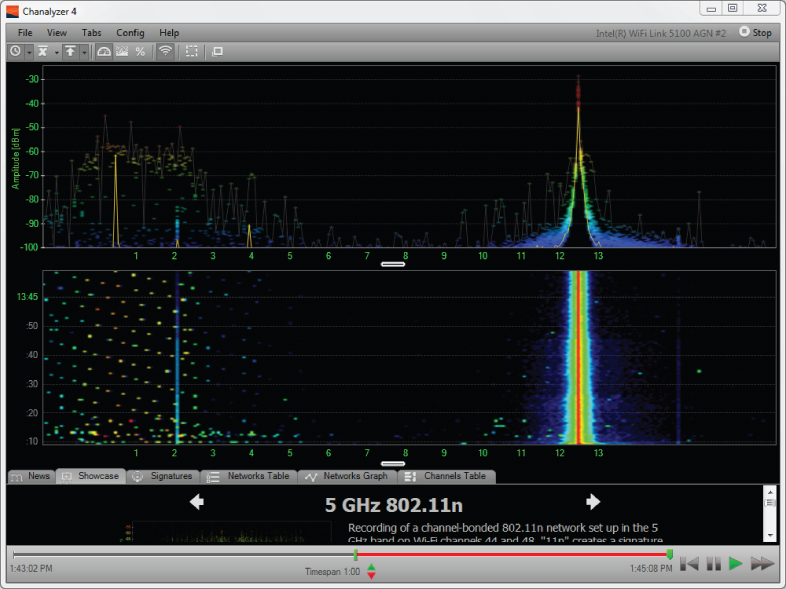
Physical Layer monitoring allows the wireless network engineer to see what is happening in the air as it relates to radio frequency. This is usually accomplished with the use of a spectrum analyzer, which allows an engineer to “see” the radio frequency and thus detect potential interference issues and also security issues. Interference from both wireless LAN devices and other wireless devices such as two-way radios or microwave ovens will be visible with the help of a spectrum analyzer. The spectrum analyzer will also detect Layer 1 security issues such as a narrow-band or wide-band radio frequency denial-of-service (DoS) attack. Figure 9.26 shows how a spectrum analyzer can see the Physical layer information and detect potential security threats.
Figure 9.26 The MetaGeek Chanalyzer spectrum analyzer shows an RF DoS attack using a narrow-band jamming device.
Some manufacturers of wireless LAN spectrum analyzers are:
| Manufacturer | Solution | Comments |
| AirMagnet/Fluke Networks | Spectrum XT | |
| Cisco Systems | Cisco Spectrum Expert | Formerly Cognio |
| Fluke Networks | AirCheck Wi-Fi Tester | Handheld device |
| MetaGeek | Chanalyzer |
Data Link Layer Monitoring
Data Link layer monitoring means looking at the Layer 2 information; it allows a network engineer to view the wireless LAN frames that traverse the air and provides the opportunity to view both potential performance and security issues. Protocol analysis tools allow the engineer to view both frame exchanges and frame decoding by expanding on the captured wireless frames. From a security point of view, these tools can provide valuable wireless network information for both the wireless network engineer as well as a potential intruder. The wireless network engineer will be able to find potential security configuration issues that could open the door to intruders. If an intruder were to capture wireless frames, such as the preshared key 4-way handshake, they might (depending on how strong the passphrase is) be able to use a dictionary attack software program and determine the passphrase; this would allow them to gain access to the wireless network and potentially see a user's encrypted data.
Some wireless LAN analyzers are able to capture and reconstruct TCP/IP frames and reconstruct a session and allow web pages to be seen or email messages to be read directly from the captured wireless frames. Keep in mind that this is possible on an open wireless network or one on which the intruder has been able to capture the frames that allow them to access the wireless LAN and to decode the data frames. Some common wireless LAN protocol analyzers are:
| Manufacturer | Solution | Comments |
| AirMagnet/Fluke Networks | WiFi Analyzer | |
| MetaGeek | Eye P.A. | |
| Tamosoft | Commview for WiFi | |
| Wildpackets | OmniPeek Network Analyzer | |
| Wireshark | Formerly Ethereal |
Some of these packet analyzers (among others) will perform wireless LAN analysis and work with wired LANs.

![]()
Industry Regulatory Compliance
It is very important for companies, organizations, and businesses that collect private or personal information from individuals to secure that information appropriately. In recent years, there have been several legislative regulations that various businesses are required to conform to. This legislation regulates how data is handled for businesses such as health care, retail, financial, and others. Plans for complying with them are known as legislative compliances. When using wireless networks, companies must verify any additional requirements from a security perspective that may be needed when dealing with regulatory compliance. This section briefly describes some of these legislative compliance requirements.
PCI Compliance
PCI stands for Payment Card Industry and is a regulation requiring companies to adhere to security standards created to protect card information pertaining to financial transactions. According to the PCI Standards Council, in order to be PCI-compliant a company must meet the following six requirements:
- Build and maintain a secure network.
- Protect cardholder data.
- Maintain a vulnerability management program.
- Implement strong access control measures.
- Regularly monitor and test networks.
- Maintain an information security policy.
![]()
HIPAA Compliance
HIPAA is the abbreviation for the United States Health Insurance Portability and Accountability Act of 1996. The goal of HIPAA is to provide standardized mechanisms for electronic data exchange, security, and confidentiality of all healthcare-related computer information and data. HIPAA consists of two parts:
- HIPAA, Title I
- HIPAA, Title II
If someone loses or changes their job, Title I of HIPAA protects their health insurance coverage.
In the information technology industries, Title II is what most people mean when they refer to HIPAA; it establishes mandatory regulations that require extensive changes to the way that healthcare providers conduct business by securing computer information and data.
![]()
Summary
In this chapter, we briefly discussed network intrusion and the impact it can have on a wireless LAN. We also took a look at IEEE 802.11 security methods and a quick review from Chapter 8 of the authentication types defined in the IEEE 802.11 standard, open system and shared key. We explored some of the IEEE 802.11 WLAN security technologies, including:
- SSID hiding
- MAC address filtering
- Wired Equivalent Privacy (WEP)
We discussed the vulnerabilities in each of these solutions. We showed an example of how the SSID could be hidden from view and also discussed why this is not a good security method—because other wireless frames contain the SSID, and it can be found even though it is removed from a beacon frame. You saw how MAC address filtering can be spoofed using freeware utilities downloadable from the Internet or through the computer operating system. We also looked at the last of three security solutions, WEP, and illustrated how it could be compromised; as you learned, it is a weak wireless security solution.
In addition to the legacy security solutions, we explored some of the more modern solutions:
- Passphrase/preshared key
- Push-button or PIN-based configuration
- 802.1X/EAP
- RADIUS and AAA
You learned that encryption consists of taking information and scrambling it so that only the sender and the intended recipient, who know the algorithm, will be able to decipher the data. We looked at three types of encryption used in IEEE 802.11 wireless networking:
- WEP
- TKIP
- CCMP
Role-based access control (RBAC) is a component for administration of wireless networks that allows access and authorization based on individual groups and users and other parameters.
We also discussed virtual private networking (VPN), commonly a Layer 3 solution that provides a secure connection over a public infrastructure such as the Internet. You saw how VPN technology can be a solution for wireless network users from a remote location to access corporate or other networks from a hotspot or other unsecured wireless LAN. We also compared PPTP and L2TP and discussed the differences between them. PPTP using MS-CHAP version 2 is not a good security solution for wireless LANs, because the authentication can be captured and potentially compromised through a dictionary attack.
You saw how a captive portal can be used to redirect a user to a web authentication page requiring authentication or an agreement of terms and conditions prior to getting network access.
Products are available for enterprise wireless LANs that will monitor the airwaves 24/7 and record all activity detected by the wireless sensors. We discussed these solutions, known as a wireless intrusion prevention system (WIPS), which have the capability to detect and react to a potential intrusion on the wireless network. You learned that WIPS sensors are available in an overlay or integrated technology. Wireless network management systems (WNMS) are available in software-, hardware-, or cloud-based solutions. A WNMS will allow for centralized management and control of the wireless and possibly wired infrastructure. A WNMS may have some WIPS capability.
We also addressed the functionality and features of these solutions. Finally, we discussed regulatory compliances such as the Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry (PCI), and the importance of securing computer data for industries such as healthcare, retail, and financial.
Exam Essentials
Review Questions
1. Which security methods do IEEE 802.11n access points support? (Choose three.)
A. WPA Enterprise
B. WEP
C. PPTP
D. RBAC
E. MAC filters
F. IPSec
2. Both _____ and _____ are wireless LAN security methods that support shared key security. (Choose two.)
A. WPA2 Personal
B. WPA2 Enterprise
C. 802.1X/EAP
D. WEP
E. WPA Enterprise
3. Which security feature provides the strongest security for a home-based wireless network?
A. SSID hiding
B. Passphrase
C. MAC filters
D. 128-bit WEP
4. You need to attend a business meeting out of town that requires air travel. You are at the airport and have some extra time. While waiting to board your plane you decide to check your office email using an IEEE 802.11g wireless hotspot access point at the airport. In order to provide a secure connection, you would enable your notebook computer to use _____.
A. Passphrase security
B. WEP
C. A VPN to the corporate network
D. IEEE 802.1X/EAP to the corporate network
5. A _____ filter is used to allow or deny wireless barcode scanners access to an 802.11b/g network.
A. WEP
B. IPSec
C. SSID
D. RF
E. MAC
6. The security amendment to the IEEE 802.11 standard requires _____.
A. WEP
B. CCMP
C. TKIP
D. PPTP
E. VPN
7. Which process is a VPN solution intended to provide for users connecting to a network?
A. Secure Layer 3 transmissions over a public network infrastructure
B. Secure Layer 2 transmissions over a public network infrastructure
C. Secure Layer 3 transmissions over a corporate network infrastructure
D. Secure Layer 2 transmissions over a corporate network infrastructure
8. Which function does RBAC provide?
A. Restricts access to authorized users or groups
B. Provides access to only network administrators
C. Streamlines hardware installation
D. Allows users to install software
9. Hiding the service set identifier of a wireless LAN will require a user to _____ in order to gain access to the wireless network.
A. Enter a username and password when prompted
B. Call the help desk and ask for a new password
C. Enable the SSID broadcast on the client device
D. Know the SSID and enter it manually
10. Remote Authentication Dial-In User Service (RADIUS) requires users on a wireless network to perform what function?
A. Access the corporate network using only the PSTN and a modem.
B. Call in to the help desk service and request a username and password.
C. Enter a username and password that will be centrally administered.
D. Request remote assistance to help solve a software problem on a computer.
11. The IEEE 802.1X standard identifies the authenticator as another term for the _____ in wireless networking.
A. Client device
B. Access point
C. RADIUS server
D. EAP server
12. Which data encryption/authentication method is identified in the original IEEE 802.11 standard?
A. TKIP
B. AES
C. CCMP
D. WEP
E. EAP
13. You are a wireless network administrator monitoring the reports for a recently installed wireless intrusion prevention system. You receive an alert notifying you of high levels of RF activity detected from an access point operating as a sensor and currently set to channel 6. Which problem could be causing the alert? (Choose two.)
A. Interference from a neighboring access point
B. RF deauthentication storm
C. RF denial-of-service (DoS) attack
D. Misconfigured client workstation
E. RF encryption attack
14. The length of a WEP key is typically _____ or _____.
A. 5-bit, 10-bit
B. 13-bit, 26-bit
C. 64-bit, 128-bit
D. 128-bit, 256-bit
E. 192-bit, 256-bit
15. Which security solution is mandatory for client devices in order to be considered Wi-Fi Protected Setup certified?
A. WEP
B. PIN
C. WPA
D. PBC
E. TKIP
16. A newly configured wireless intrusion prevention system will _____.
A. Require a network administrator to monitor for intrusions
B. Automatically monitor the network for potential attacks
C. Require an administrator to manually shut down a rogue access point
D. Automatically notify a network administrator regarding a firmware upgrade
17. You are a network administrator and are asked for a security recommendation regarding older wireless 802.11-compliant VoIP handsets. The company does not have the budget to upgrade the equipment at this time. Which would be the best recommendation you could provide?
A. Don't worry about securing the handsets because voice transmissions cannot be deciphered.
B. Carefully plan a strategy using WEP and VLANs.
C. Use a VPN solution with L2TP/IPSec.
D. Use a CCMP/AES Layer 2 solution.
18. A weakness with MAC address filtering is that it allows an intruder to _____.
A. Crack the encryption.
B. Spoof an address.
C. Cause an RF DoS attack.
D. Steal user authentication.
19. What type of wireless network device is PIN-based security most commonly used with?
A. SOHO brands that support WPA 2.0
B. Enterprise brands that support WPA 2.0
C. SOHO brands that support WPS
D. Enterprise brands that support WPS
20. Layer 2 Tunneling Protocol commonly uses which encryption method?
A. IPSec
B. PPTP
C. AES
D. WEP
E. MPPE
